| File name: | Junit.zip |
| Full analysis: | https://app.any.run/tasks/756f7a8c-5d19-48d3-8be9-62bebdd57aa7 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2019, 16:00:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B9EA34681E1825F19723B90EF6D3053B |
| SHA1: | B380911DEAE942407FBD41BFDC5C931794455900 |
| SHA256: | CEA903FBD465CEB16CF743A424594DFA64595FFD14D86D2077FFD58AEDED0BFD |
| SSDEEP: | 49152:V8z2EGFoSXAO16WAddDMI7xCTljQ6B1HD5L2N7OlnN5oAEjsHst:VCGL1d/Q095CFOlnN5w |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 992)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 992)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:10:22 00:38:29 |
| ZipCRC: | 0x1f866908 |
| ZipCompressedSize: | 2244 |
| ZipUncompressedSize: | 6259 |
| ZipFileName: | Junit/build.gradle.kts |
Total processes
44
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
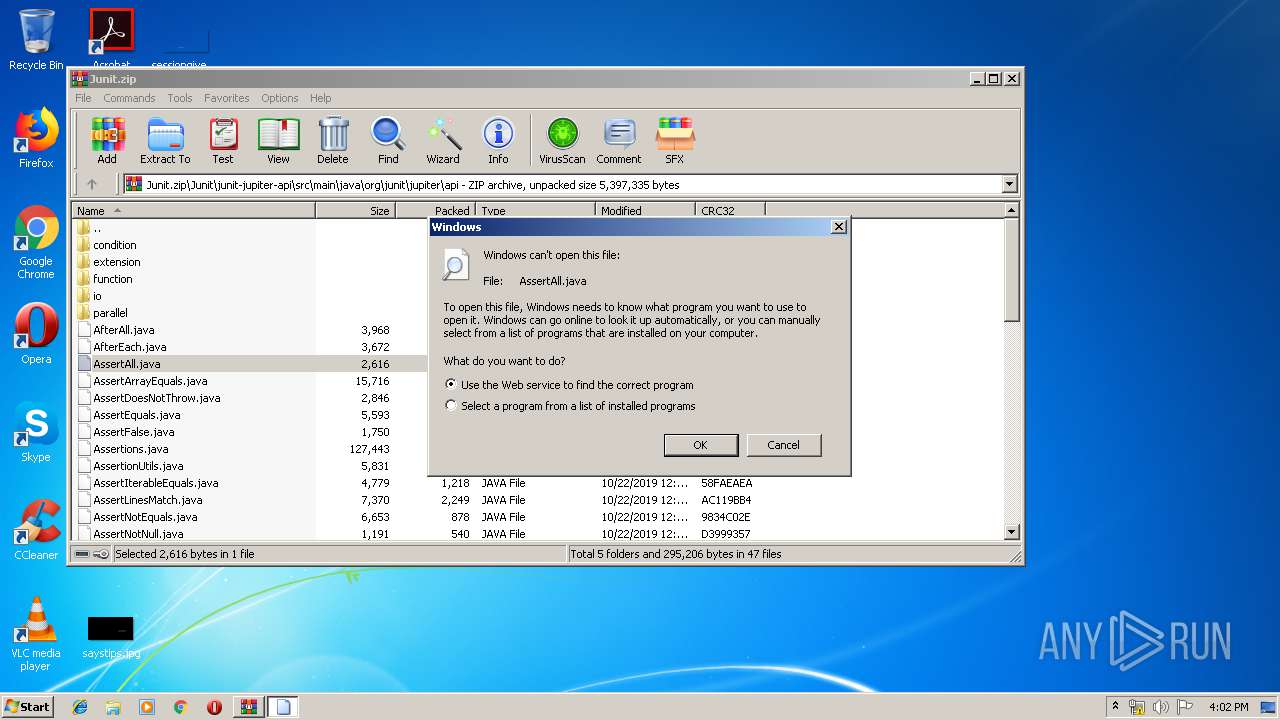
| 892 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa992.14307\AssertArrayEquals.java | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Junit.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2200 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa992.9456\gradlew.bat" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2376 | "java.exe" "-Xmx64m" "-Xms64m" "-Dorg.gradle.appname=gradlew" -classpath "C:\Users\admin\AppData\Local\Temp\Rar$DIa992.9456\\gradle\wrapper\gradle-wrapper.jar" org.gradle.wrapper.GradleWrapperMain | C:\ProgramData\Oracle\Java\javapath\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2472 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa992.13940\AssertAll.java | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2544 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa992.14037\AssertFalse.java | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2944 | java.exe -version | C:\ProgramData\Oracle\Java\javapath\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3960 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa992.14190\AssertionUtils.java | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
517
Read events
480
Write events
37
Delete events
0
Modification events
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Junit.zip | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
0
Suspicious files
0
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2376 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa992.14190\AssertionUtils.java | text | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa992.13940\AssertAll.java | text | |
MD5:— | SHA256:— | |||
| 2944 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa992.9456\gradlew.bat | text | |
MD5:EBBD0EECBF8C36AE45F0707B19247C7B | SHA256:87268485AC5C93F230997F2715A9831DCAAFB3A631C7A1646DCA2AFC2DBDA7F2 | |||
| 992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa992.14037\AssertFalse.java | text | |
MD5:— | SHA256:— | |||
| 992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa992.14307\AssertArrayEquals.java | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report