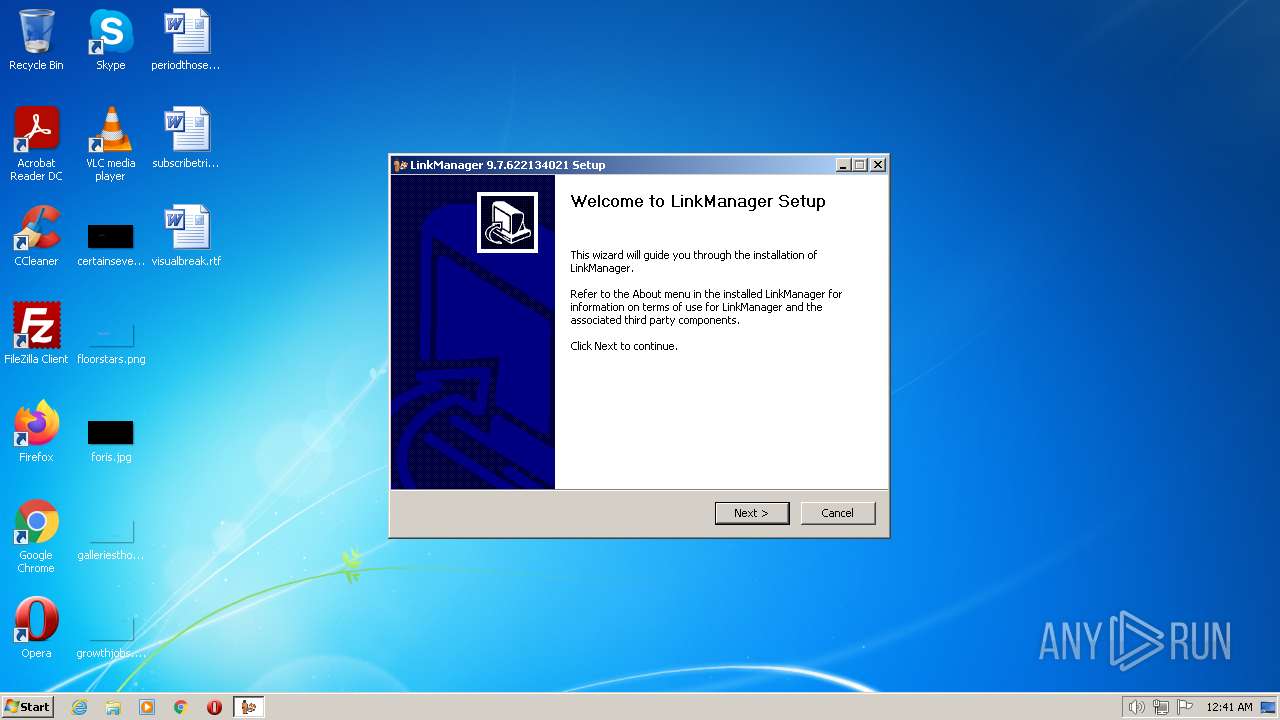
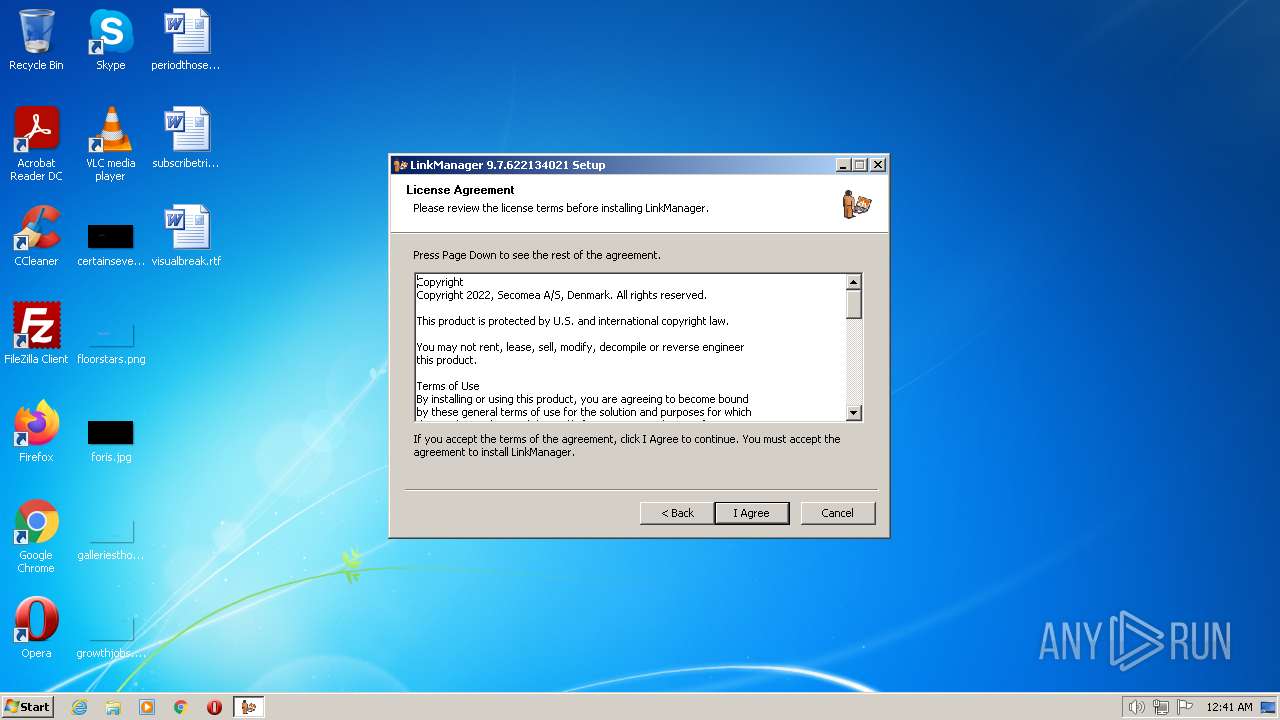
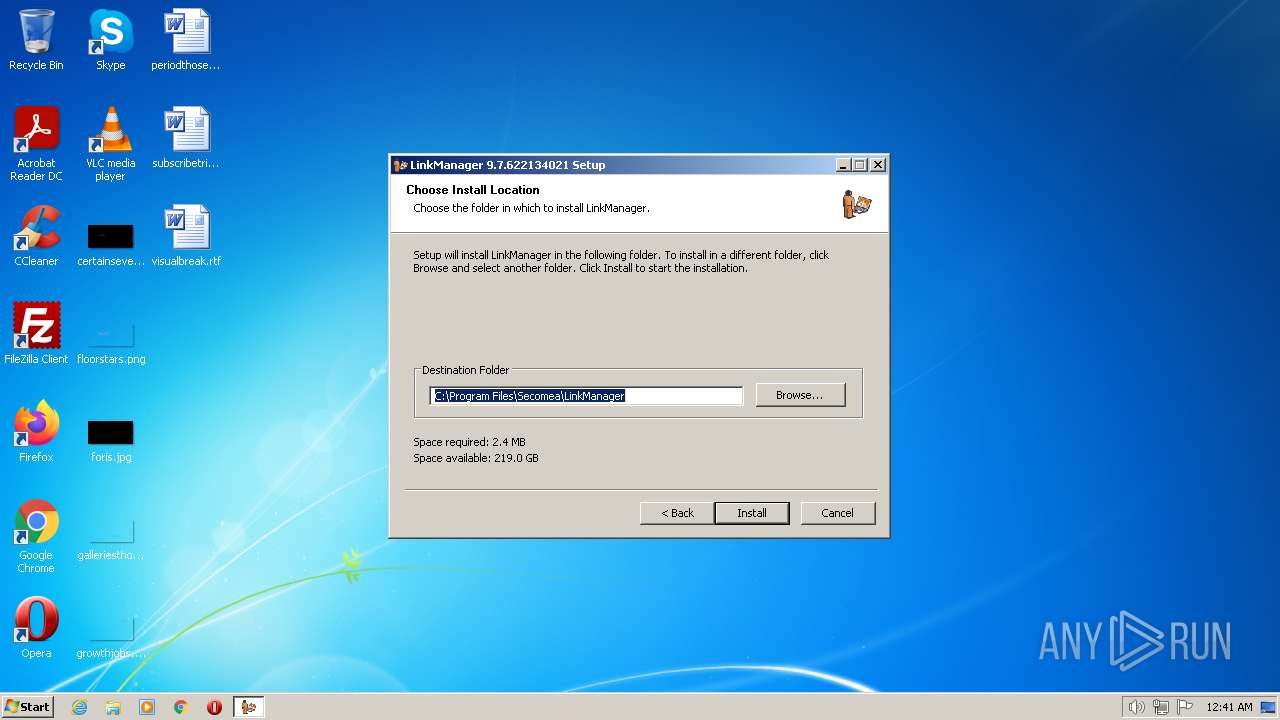
| File name: | v6051_LinkManager_9.7.622134021.exe |
| Full analysis: | https://app.any.run/tasks/3c65fec7-35b7-4d64-adb2-4809be5a0a71 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2022, 00:41:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 4733EECB733ED5AACF90D4541A6E6DDC |
| SHA1: | 3670C4C9021EF70299700F4109FBF3EBBD1C753D |
| SHA256: | CE9A51606F56A5136CEC7BFDB7AFDD2136F527FD1525DB5A73B42E5FDB04F331 |
| SSDEEP: | 24576:DrLUomRzRsiNJVvtLakCAkaB3A/7NLFYK1RwTV87R9ih2/iouO7tUUKY/ZO:zTmJR71dabCkFFRwSokiouOxPKY |
MALICIOUS
Drops the executable file immediately after the start
- v6051_LinkManager_9.7.622134021.exe (PID: 1592)
- v6051_LinkManager_9.7.622134021.exe (PID: 2472)
- LinkManager-x86-setup.exe (PID: 3364)
Application was dropped or rewritten from another process
- v6051_LinkManager_9.7.622134021.exe (PID: 2472)
- v6051_LinkManager_9.7.622134021.exe (PID: 3100)
- LinkManagerSVC.exe (PID: 912)
- LinkManagerSVC.exe (PID: 1820)
- LinkManagerSVC.exe (PID: 3272)
- tapmgr.exe (PID: 3284)
- tapmgr.exe (PID: 2024)
- LinkManager-x86-setup.exe (PID: 3364)
- usbip.exe (PID: 1444)
Loads dropped or rewritten executable
- LinkManager-x86-setup.exe (PID: 3364)
- v6051_LinkManager_9.7.622134021.exe (PID: 2472)
Starts NET.EXE for service management
- ns3C14.tmp (PID: 404)
Creates a writable file the system directory
- DrvInst.exe (PID: 2820)
- DrvInst.exe (PID: 1236)
- DrvInst.exe (PID: 2460)
- DrvInst.exe (PID: 1040)
- DrvInst.exe (PID: 1860)
- DrvInst.exe (PID: 1572)
SUSPICIOUS
Reads the Internet Settings
- v6051_LinkManager_9.7.622134021.exe (PID: 1592)
Executable content was dropped or overwritten
- v6051_LinkManager_9.7.622134021.exe (PID: 2472)
- v6051_LinkManager_9.7.622134021.exe (PID: 1592)
- LinkManager-x86-setup.exe (PID: 3364)
Drops a file with too old compile date
- v6051_LinkManager_9.7.622134021.exe (PID: 1592)
Creates a directory in Program Files
- LinkManager-x86-setup.exe (PID: 3364)
Creates a software uninstall entry
- LinkManager-x86-setup.exe (PID: 3364)
Executes as Windows Service
- LinkManagerSVC.exe (PID: 912)
Application launched itself
- LinkManagerSVC.exe (PID: 912)
Reads settings of System Certificates
- DrvInst.exe (PID: 2820)
- DrvInst.exe (PID: 1040)
- DrvInst.exe (PID: 1236)
- DrvInst.exe (PID: 2460)
- DrvInst.exe (PID: 1860)
- usbip.exe (PID: 1444)
- DrvInst.exe (PID: 1572)
Changes default file association
- LinkManager-x86-setup.exe (PID: 3364)
Checks Windows Trust Settings
- usbip.exe (PID: 1444)
Reads security settings of Internet Explorer
- usbip.exe (PID: 1444)
INFO
Checks supported languages
- v6051_LinkManager_9.7.622134021.exe (PID: 1592)
- v6051_LinkManager_9.7.622134021.exe (PID: 2472)
- LinkManager-x86-setup.exe (PID: 3364)
- ns3BA6.tmp (PID: 1640)
- ns3ABB.tmp (PID: 1412)
- LinkManagerSVC.exe (PID: 1820)
- ns3C14.tmp (PID: 404)
- LinkManagerSVC.exe (PID: 912)
- LinkManagerSVC.exe (PID: 3272)
- ns4676.tmp (PID: 3484)
- ns46F4.tmp (PID: 3248)
- tapmgr.exe (PID: 2024)
- tapmgr.exe (PID: 3284)
- ns4762.tmp (PID: 2068)
- ns4B0C.tmp (PID: 2696)
- ns4F53.tmp (PID: 1128)
- ns502F.tmp (PID: 3744)
- ns52FF.tmp (PID: 2664)
- ns55A0.tmp (PID: 1920)
- usbip.exe (PID: 1444)
Reads the computer name
- v6051_LinkManager_9.7.622134021.exe (PID: 1592)
- v6051_LinkManager_9.7.622134021.exe (PID: 2472)
- LinkManager-x86-setup.exe (PID: 3364)
- LinkManagerSVC.exe (PID: 1820)
- LinkManagerSVC.exe (PID: 912)
- LinkManagerSVC.exe (PID: 3272)
- usbip.exe (PID: 1444)
Creates files in the program directory
- v6051_LinkManager_9.7.622134021.exe (PID: 2472)
- LinkManager-x86-setup.exe (PID: 3364)
Reads security settings of Internet Explorer
- cscript.exe (PID: 2700)
Starts application with an unusual extension
- LinkManager-x86-setup.exe (PID: 3364)
Drops a file that was compiled in debug mode
- LinkManager-x86-setup.exe (PID: 3364)
- DrvInst.exe (PID: 2820)
- pnputil.exe (PID: 3080)
- pnputil.exe (PID: 1244)
- DrvInst.exe (PID: 1572)
Creates files in the driver directory
- DrvInst.exe (PID: 2820)
- DrvInst.exe (PID: 1040)
- DrvInst.exe (PID: 2460)
- DrvInst.exe (PID: 1236)
- DrvInst.exe (PID: 1860)
- DrvInst.exe (PID: 1572)
Executable content was dropped or overwritten
- DrvInst.exe (PID: 2820)
- pnputil.exe (PID: 1244)
- DrvInst.exe (PID: 1572)
- pnputil.exe (PID: 3080)
Drops the executable file immediately after the start
- pnputil.exe (PID: 3080)
- DrvInst.exe (PID: 2820)
- pnputil.exe (PID: 1244)
- DrvInst.exe (PID: 1572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 6 (93.8) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (2.3) |
| .exe | | | Win32 Executable (generic) (1.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.7) |
| .exe | | | Generic Win/DOS Executable (0.7) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 1992-Jun-19 22:22:17 |
| Detected languages: |
|
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 80 |
| e_cp: | 2 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | 15 |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | 26 |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 8 |
| TimeDateStamp: | 1992-Jun-19 22:22:17 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 4096 | 29228 | 29696 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.51167 |
DATA | 36864 | 536 | 1024 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.1517 |
BSS | 40960 | 43161 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.idata | 86016 | 2148 | 2560 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.17386 |
.tls | 90112 | 8 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rdata | 94208 | 24 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.20692 |
.reloc | 98304 | 1484 | 1536 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.44309 |
.rsrc | 102400 | 5120 | 5120 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 3.73967 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.03563 | 4264 | UNKNOWN | Russian - Russia | RT_ICON |
DVCLAL | 4 | 16 | UNKNOWN | UNKNOWN | RT_RCDATA |
PACKAGEINFO | 6.90278 | 172 | UNKNOWN | UNKNOWN | RT_RCDATA |
MAINICON | 1.7815 | 20 | UNKNOWN | Russian - Russia | RT_GROUP_ICON |
Imports
advapi32.dll |
advapi32.dll (#2) |
gdi32.dll |
kernel32.dll |
kernel32.dll (#2) |
kernel32.dll (#3) |
oleaut32.dll |
shell32.dll |
user32.dll |
user32.dll (#2) |
Total processes
83
Monitored processes
36
Malicious processes
15
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 404 | "C:\Users\admin\AppData\Local\Temp\nsi39C.tmp\ns3C14.tmp" net start LinkManagerSvc | C:\Users\admin\AppData\Local\Temp\nsi39C.tmp\ns3C14.tmp | — | LinkManager-x86-setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 824 | cmd /c start /w "" "C:\Program Files\Secomea\LinkManager\LinkManagerSvc.exe" -install | C:\Windows\system32\cmd.exe | — | ns3BA6.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 912 | "C:\Program Files\Secomea\LinkManager\LinkManagerSVC.exe" | C:\Program Files\Secomea\LinkManager\LinkManagerSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Secomea Integrity Level: SYSTEM Description: LinkManager Service Exit code: 0 Version: 9.7.622134021 Modules
| |||||||||||||||
| 1040 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{1766f826-0a36-340c-6481-0a0c21636741}\com0com.inf" "0" "68b2a3a9f" "000004B4" "WinSta0\Default" "000004AC" "208" "C:\Program Files\Secomea\LinkManager" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1128 | "C:\Users\admin\AppData\Local\Temp\nsi39C.tmp\ns4F53.tmp" "C:\Windows\System32\pnputil.exe" /i /a "C:\Program Files\Secomea\LinkManager\cncport.inf" | C:\Users\admin\AppData\Local\Temp\nsi39C.tmp\ns4F53.tmp | — | LinkManager-x86-setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1236 | DrvInst.exe "4" "4" "C:\Users\admin\AppData\Local\Temp\{4686d5d2-d21c-2cfa-c7fc-a143bf73e713}\cncport.inf" "0" "68b2a3a9f" "000004AC" "WinSta0\Default" "0000054C" "208" "C:\Program Files\Secomea\LinkManager" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1244 | "C:\Windows\System32\pnputil.exe" /i /a "C:\Program Files\Secomea\LinkManager\USBIPEnum.inf" | C:\Windows\System32\pnputil.exe | ns52FF.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft PnP Utility - Tool to add, delete and enumerate driver packages. Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1412 | "C:\Users\admin\AppData\Local\Temp\nsi39C.tmp\ns3ABB.tmp" cscript winfw.js add "Secomea LinkManagerTray" "C:\Program Files\Secomea\LinkManager\LinkManagerTray.exe" | C:\Users\admin\AppData\Local\Temp\nsi39C.tmp\ns3ABB.tmp | — | LinkManager-x86-setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1444 | .\usbip.exe -p" | C:\Program Files\Secomea\LinkManager\usbip.exe | — | ns55A0.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1572 | DrvInst.exe "2" "211" "ROOT\USB\0000" "C:\Windows\INF\oem7.inf" "usbipenum.inf:Standard.NTx86:USBIP_Device:7.2.0.17114:root\usbipenum" "6e92bf947" "000005E0" "000005F0" "000005DC" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
23 581
Read events
23 388
Write events
193
Delete events
0
Modification events
| (PID) Process: | (1592) v6051_LinkManager_9.7.622134021.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1592) v6051_LinkManager_9.7.622134021.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1592) v6051_LinkManager_9.7.622134021.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1592) v6051_LinkManager_9.7.622134021.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3364) LinkManager-x86-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{CDC7DCFD-42EE-4A59-A6F5-161155BAF7CB} |
| Operation: | write | Name: | DisplayName |
Value: Secomea LinkManager | |||
| (PID) Process: | (3364) LinkManager-x86-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{CDC7DCFD-42EE-4A59-A6F5-161155BAF7CB} |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Secomea\LinkManager\LinkManagerTray.exe | |||
| (PID) Process: | (3364) LinkManager-x86-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{CDC7DCFD-42EE-4A59-A6F5-161155BAF7CB} |
| Operation: | write | Name: | DisplayVersion |
Value: 9.7.622134021 | |||
| (PID) Process: | (3364) LinkManager-x86-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{CDC7DCFD-42EE-4A59-A6F5-161155BAF7CB} |
| Operation: | write | Name: | Publisher |
Value: Secomea A/S | |||
| (PID) Process: | (3364) LinkManager-x86-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{CDC7DCFD-42EE-4A59-A6F5-161155BAF7CB} |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Secomea\LinkManager\uninstall8.exe" | |||
| (PID) Process: | (3364) LinkManager-x86-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{CDC7DCFD-42EE-4A59-A6F5-161155BAF7CB} |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
Executable files
62
Suspicious files
58
Text files
5
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1592 | v6051_LinkManager_9.7.622134021.exe | C:\Users\admin\AppData\Local\Temp\3582-490\v6051_LinkManager_9.7.622134021.exe | executable | |
MD5:— | SHA256:— | |||
| 2472 | v6051_LinkManager_9.7.622134021.exe | C:\Program Files\LinkManager-x86-setup.exe | executable | |
MD5:— | SHA256:— | |||
| 1592 | v6051_LinkManager_9.7.622134021.exe | C:\MSOCache\All Users\{90140000-006E-0410-0000-0000000FF1CE}-C\DW20.EXE | executable | |
MD5:02EE6A3424782531461FB2F10713D3C1 | SHA256:EAD58C483CB20BCD57464F8A4929079539D634F469B213054BF737D227C026DC | |||
| 1592 | v6051_LinkManager_9.7.622134021.exe | C:\MSOCache\All Users\{90140000-006E-0407-0000-0000000FF1CE}-C\dwtrig20.exe | executable | |
MD5:CF6C595D3E5E9667667AF096762FD9C4 | SHA256:593E60CC30AE0789448547195AF77F550387F6648D45847EA244DD0DD7ABF03D | |||
| 1592 | v6051_LinkManager_9.7.622134021.exe | C:\MSOCache\All Users\{90140000-0100-0410-0000-0000000FF1CE}-C\setup.exe | executable | |
MD5:566ED4F62FDC96F175AFEDD811FA0370 | SHA256:E17CD94C08FC0E001A49F43A0801CEA4625FB9AEE211B6DFEBEBEC446C21F460 | |||
| 1592 | v6051_LinkManager_9.7.622134021.exe | C:\MSOCache\All Users\{90140000-006E-0419-0000-0000000FF1CE}-C\DW20.EXE | executable | |
MD5:02EE6A3424782531461FB2F10713D3C1 | SHA256:EAD58C483CB20BCD57464F8A4929079539D634F469B213054BF737D227C026DC | |||
| 1592 | v6051_LinkManager_9.7.622134021.exe | C:\MSOCache\All Users\{90140000-0100-0407-0000-0000000FF1CE}-C\setup.exe | executable | |
MD5:566ED4F62FDC96F175AFEDD811FA0370 | SHA256:E17CD94C08FC0E001A49F43A0801CEA4625FB9AEE211B6DFEBEBEC446C21F460 | |||
| 1592 | v6051_LinkManager_9.7.622134021.exe | C:\MSOCache\All Users\{90140000-006E-0416-0000-0000000FF1CE}-C\DW20.EXE | executable | |
MD5:02EE6A3424782531461FB2F10713D3C1 | SHA256:EAD58C483CB20BCD57464F8A4929079539D634F469B213054BF737D227C026DC | |||
| 1592 | v6051_LinkManager_9.7.622134021.exe | C:\MSOCache\All Users\{90140000-006E-041F-0000-0000000FF1CE}-C\DW20.EXE | executable | |
MD5:02EE6A3424782531461FB2F10713D3C1 | SHA256:EAD58C483CB20BCD57464F8A4929079539D634F469B213054BF737D227C026DC | |||
| 1592 | v6051_LinkManager_9.7.622134021.exe | C:\MSOCache\All Users\{90140000-006E-0411-0000-0000000FF1CE}-C\dwtrig20.exe | executable | |
MD5:CF6C595D3E5E9667667AF096762FD9C4 | SHA256:593E60CC30AE0789448547195AF77F550387F6648D45847EA244DD0DD7ABF03D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report