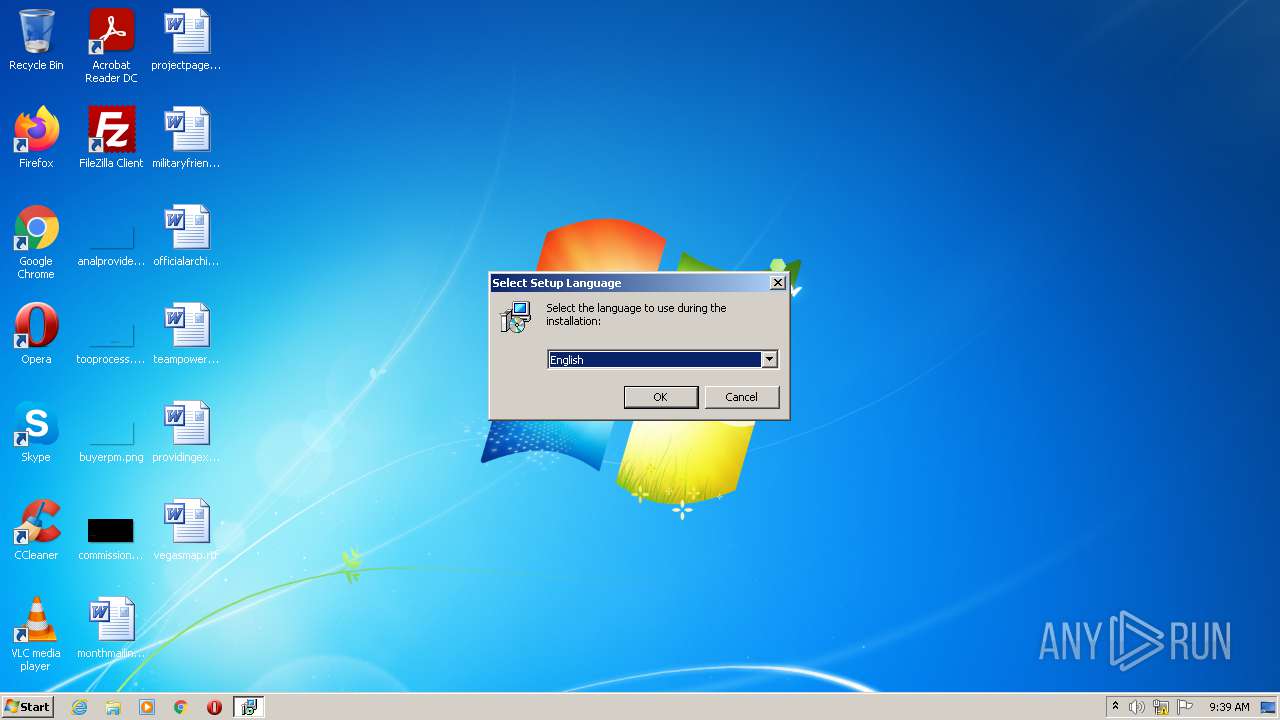
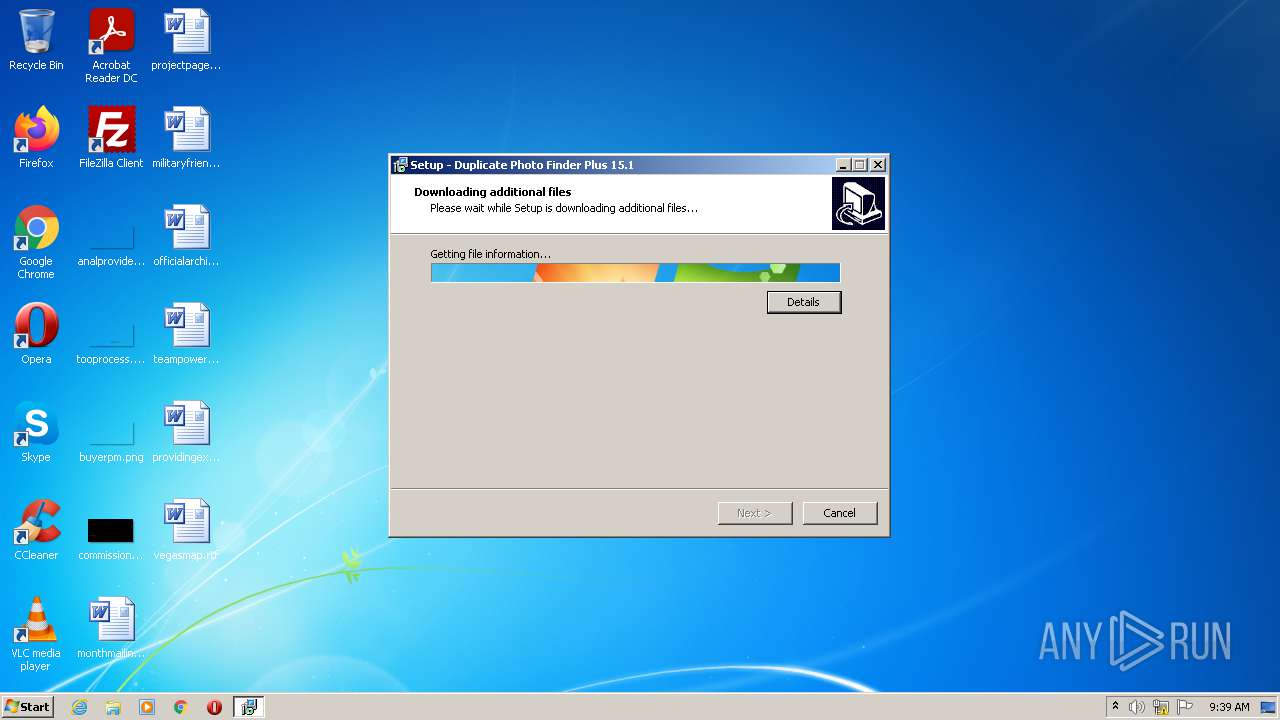
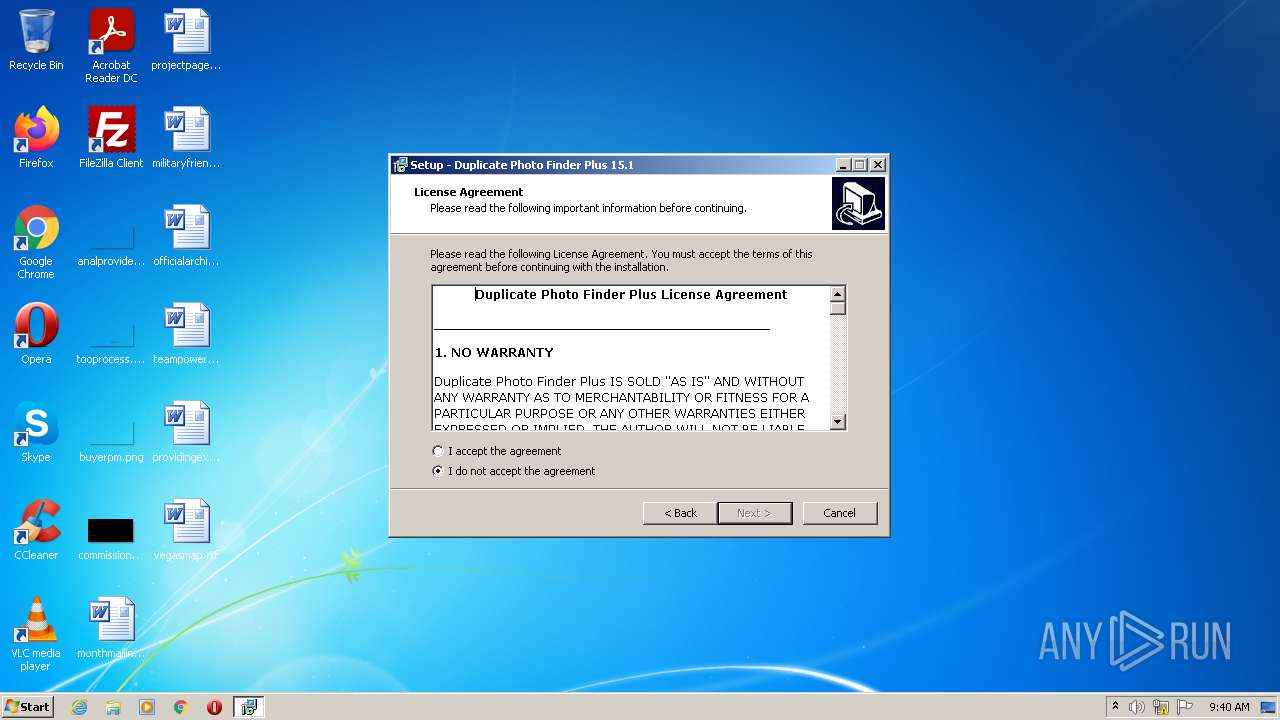
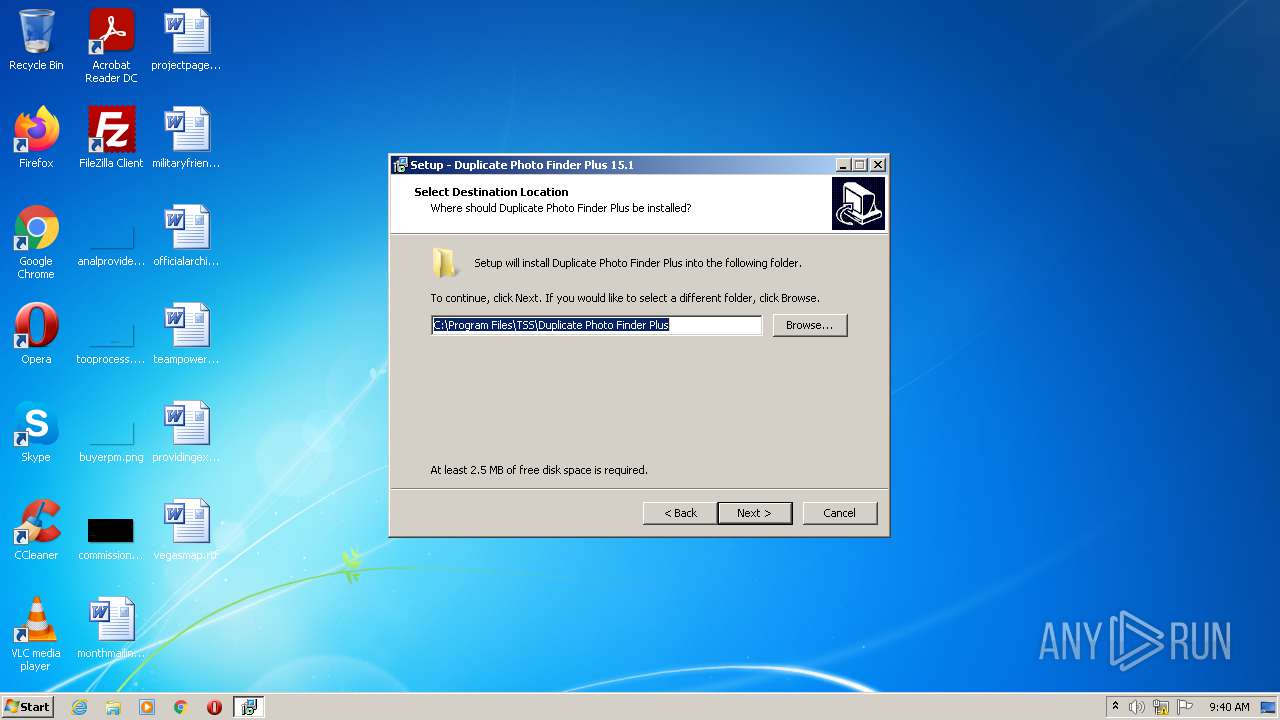
| File name: | duplicate-photo-finder-plus.exe |
| Full analysis: | https://app.any.run/tasks/c753df53-6b2a-4e92-b5e1-1966f973b8e1 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2021, 08:39:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CA46E898EA540932849435E5E56FF978 |
| SHA1: | 1403BF68EB8B940FA739504FFC003881FD617885 |
| SHA256: | CE982CACB2240152B7FA1E90A21848D939C2C11FF1058B8A446B09E996CFFC4A |
| SSDEEP: | 24576:d86isqKnwvAAAyhLqkEjALYz2WK7yA6F91BoQ9uZUR+zZdEG:p95wYvcLqky5zFAmpV9u1r |
MALICIOUS
Drops executable file immediately after starts
- duplicate-photo-finder-plus.exe (PID: 2144)
- duplicate-photo-finder-plus.exe (PID: 2268)
- spt_setup.tmp (PID: 2920)
- spt_setup.exe (PID: 2500)
SUSPICIOUS
Checks supported languages
- duplicate-photo-finder-plus.exe (PID: 2144)
- duplicate-photo-finder-plus.tmp (PID: 2728)
- duplicate-photo-finder-plus.tmp (PID: 1916)
- duplicate-photo-finder-plus.exe (PID: 2268)
- spt_setup.tmp (PID: 2920)
- spt_setup.exe (PID: 2500)
Reads the computer name
- duplicate-photo-finder-plus.tmp (PID: 1916)
- duplicate-photo-finder-plus.tmp (PID: 2728)
- spt_setup.tmp (PID: 2920)
Reads Windows owner or organization settings
- duplicate-photo-finder-plus.tmp (PID: 2728)
- spt_setup.tmp (PID: 2920)
Executable content was dropped or overwritten
- duplicate-photo-finder-plus.exe (PID: 2268)
- spt_setup.exe (PID: 2500)
- spt_setup.tmp (PID: 2920)
- duplicate-photo-finder-plus.tmp (PID: 2728)
- duplicate-photo-finder-plus.exe (PID: 2144)
Drops a file that was compiled in debug mode
- duplicate-photo-finder-plus.tmp (PID: 2728)
- spt_setup.tmp (PID: 2920)
Reads the Windows organization settings
- duplicate-photo-finder-plus.tmp (PID: 2728)
- spt_setup.tmp (PID: 2920)
INFO
Application was dropped or rewritten from another process
- duplicate-photo-finder-plus.tmp (PID: 2728)
- duplicate-photo-finder-plus.tmp (PID: 1916)
- spt_setup.exe (PID: 2500)
- spt_setup.tmp (PID: 2920)
Dropped object may contain Bitcoin addresses
- spt_setup.tmp (PID: 2920)
Loads dropped or rewritten executable
- spt_setup.tmp (PID: 2920)
- duplicate-photo-finder-plus.tmp (PID: 2728)
Checks Windows Trust Settings
- duplicate-photo-finder-plus.tmp (PID: 2728)
Reads settings of System Certificates
- duplicate-photo-finder-plus.tmp (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (45.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (20.9) |
| .exe | | | Win32 Executable (generic) (14.3) |
| .exe | | | Win16/32 Executable Delphi generic (6.6) |
| .exe | | | Generic Win/DOS Executable (6.3) |
EXIF
EXE
| ProductVersion: | |
|---|---|
| ProductName: | Duplicate Photo Finder Plus |
| LegalCopyright: | |
| FileVersion: | |
| FileDescription: | Duplicate Photo Finder Plus Setup |
| CompanyName: | TriSun Software Limited |
| Comments: | This installation was built with Inno Setup. |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 0.0.0.0 |
| FileVersionNumber: | 0.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | 6 |
| OSVersion: | 5 |
| EntryPoint: | 0x1181c |
| UninitializedDataSize: | - |
| InitializedDataSize: | 53760 |
| CodeSize: | 66560 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| TimeStamp: | 2018:06:14 15:27:46+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 14-Jun-2018 13:27:46 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | TriSun Software Limited |
| FileDescription: | Duplicate Photo Finder Plus Setup |
| FileVersion: | - |
| LegalCopyright: | - |
| ProductName: | Duplicate Photo Finder Plus |
| ProductVersion: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 14-Jun-2018 13:27:46 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000F25C | 0x0000F400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.37588 |
.itext | 0x00011000 | 0x00000FA4 | 0x00001000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.77877 |
.data | 0x00012000 | 0x00000C8C | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.30283 |
.bss | 0x00013000 | 0x000056BC | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00019000 | 0x00000E04 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.59781 |
.tls | 0x0001A000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0001B000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.204488 |
.rsrc | 0x0001C000 | 0x0000B200 | 0x0000B200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.14047 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.13965 | 1580 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.47151 | 1384 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 3.91708 | 744 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.91366 | 2216 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4091 | 2.56031 | 104 | UNKNOWN | UNKNOWN | RT_STRING |
4092 | 3.25287 | 212 | UNKNOWN | UNKNOWN | RT_STRING |
4093 | 3.26919 | 164 | UNKNOWN | UNKNOWN | RT_STRING |
4094 | 3.33268 | 684 | UNKNOWN | UNKNOWN | RT_STRING |
4095 | 3.34579 | 844 | UNKNOWN | UNKNOWN | RT_STRING |
4096 | 3.28057 | 660 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
43
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1916 | "C:\Users\admin\AppData\Local\Temp\is-RO5LJ.tmp\duplicate-photo-finder-plus.tmp" /SL5="$80130,633645,121344,C:\Users\admin\AppData\Local\Temp\duplicate-photo-finder-plus.exe" | C:\Users\admin\AppData\Local\Temp\is-RO5LJ.tmp\duplicate-photo-finder-plus.tmp | — | duplicate-photo-finder-plus.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2144 | "C:\Users\admin\AppData\Local\Temp\duplicate-photo-finder-plus.exe" | C:\Users\admin\AppData\Local\Temp\duplicate-photo-finder-plus.exe | Explorer.EXE | ||||||||||||
User: admin Company: TriSun Software Limited Integrity Level: MEDIUM Description: Duplicate Photo Finder Plus Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2268 | "C:\Users\admin\AppData\Local\Temp\duplicate-photo-finder-plus.exe" /SPAWNWND=$70146 /NOTIFYWND=$80130 | C:\Users\admin\AppData\Local\Temp\duplicate-photo-finder-plus.exe | duplicate-photo-finder-plus.tmp | ||||||||||||
User: admin Company: TriSun Software Limited Integrity Level: HIGH Description: Duplicate Photo Finder Plus Setup Exit code: 0 Version: Modules
| |||||||||||||||
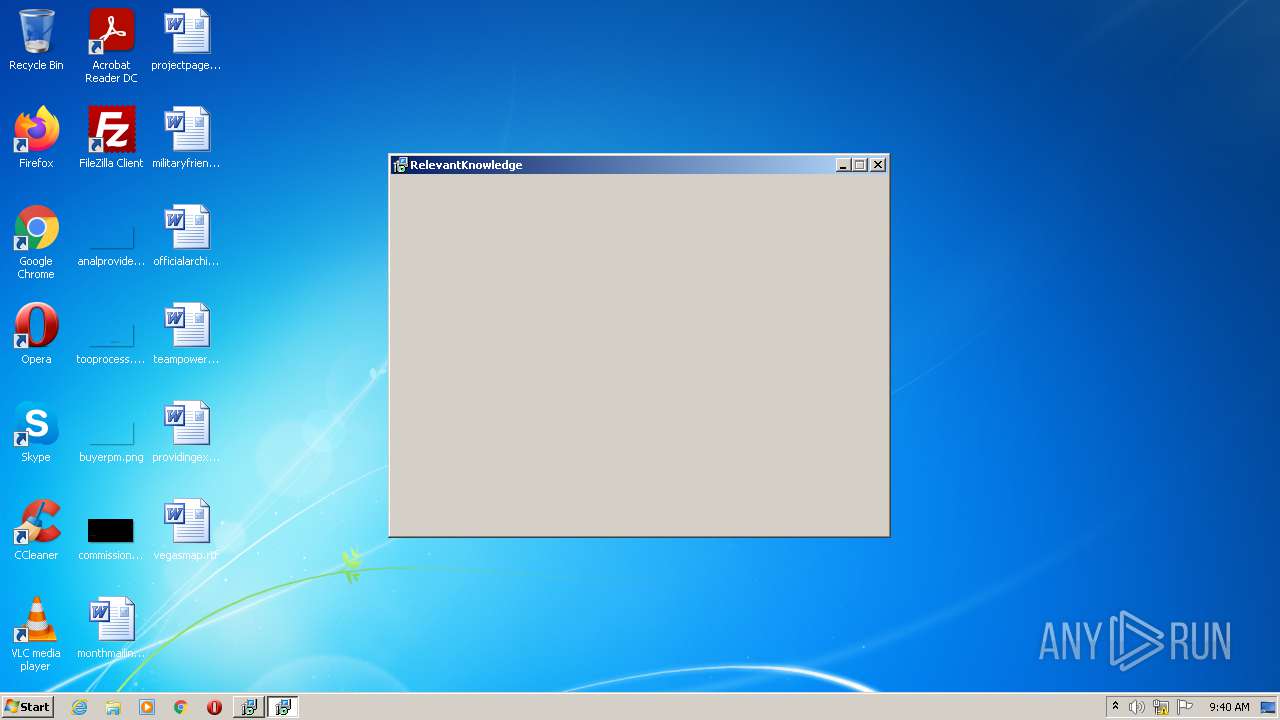
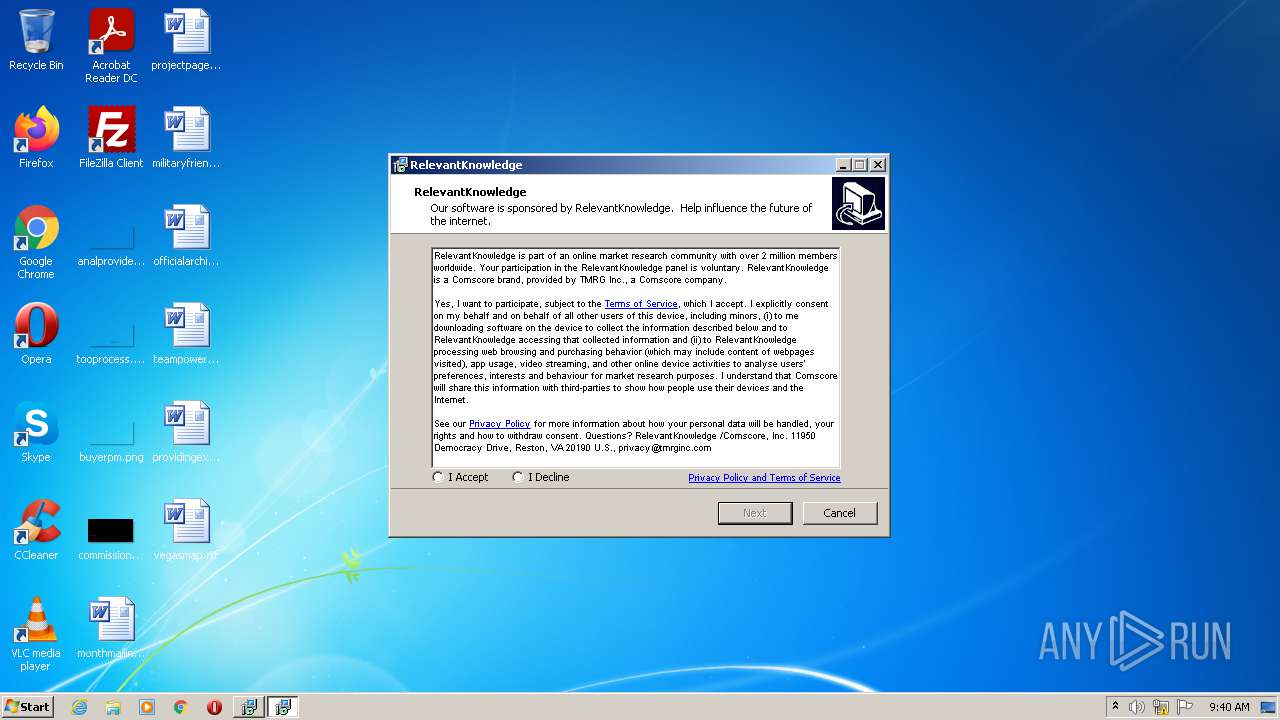
| 2500 | "C:\Users\admin\AppData\Local\Temp\is-UCAK3.tmp\spt_setup.exe" -c: 3037 -lang: 1 -tpi: dpfp | C:\Users\admin\AppData\Local\Temp\is-UCAK3.tmp\spt_setup.exe | duplicate-photo-finder-plus.tmp | ||||||||||||
User: admin Company: TMRG Integrity Level: HIGH Description: RelevantKnowledge Setup Setup Exit code: 0 Version: 1.1.0 Modules
| |||||||||||||||
| 2728 | "C:\Users\admin\AppData\Local\Temp\is-VACAE.tmp\duplicate-photo-finder-plus.tmp" /SL5="$150144,633645,121344,C:\Users\admin\AppData\Local\Temp\duplicate-photo-finder-plus.exe" /SPAWNWND=$70146 /NOTIFYWND=$80130 | C:\Users\admin\AppData\Local\Temp\is-VACAE.tmp\duplicate-photo-finder-plus.tmp | duplicate-photo-finder-plus.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2920 | "C:\Users\admin\AppData\Local\Temp\is-66N1F.tmp\spt_setup.tmp" /SL5="$70138,2022387,721408,C:\Users\admin\AppData\Local\Temp\is-UCAK3.tmp\spt_setup.exe" -c: 3037 -lang: 1 -tpi: dpfp | C:\Users\admin\AppData\Local\Temp\is-66N1F.tmp\spt_setup.tmp | spt_setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
5 932
Read events
5 892
Write events
40
Delete events
0
Modification events
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: A80A00008419D1D28B78D701 | |||
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 5CAAE74D93FFC2194490CF363F6843F3266AE238051B3030C30A9F4716F2BA35 | |||
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2728) duplicate-photo-finder-plus.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
9
Suspicious files
7
Text files
0
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2728 | duplicate-photo-finder-plus.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:— | SHA256:— | |||
| 2728 | duplicate-photo-finder-plus.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2728 | duplicate-photo-finder-plus.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 2728 | duplicate-photo-finder-plus.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:— | SHA256:— | |||
| 2728 | duplicate-photo-finder-plus.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_93E4B2BA79A897B3100CCB27F2D3BF4F | der | |
MD5:— | SHA256:— | |||
| 2268 | duplicate-photo-finder-plus.exe | C:\Users\admin\AppData\Local\Temp\is-VACAE.tmp\duplicate-photo-finder-plus.tmp | executable | |
MD5:34ACC2BDB45A9C436181426828C4CB49 | SHA256:9C81817ACD4982632D8C7F1DF3898FCA1477577738184265D735F49FC5480F07 | |||
| 2728 | duplicate-photo-finder-plus.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_93E4B2BA79A897B3100CCB27F2D3BF4F | binary | |
MD5:— | SHA256:— | |||
| 2728 | duplicate-photo-finder-plus.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:— | SHA256:— | |||
| 2728 | duplicate-photo-finder-plus.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FC5A820A001B41D68902E051F36A5282_A24DDAC17157FC38EE53B0899A172F7C | der | |
MD5:— | SHA256:— | |||
| 2728 | duplicate-photo-finder-plus.tmp | C:\Users\admin\AppData\Local\Temp\is-UCAK3.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
9
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2728 | duplicate-photo-finder-plus.tmp | GET | 200 | 143.204.101.124:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2728 | duplicate-photo-finder-plus.tmp | GET | 200 | 13.225.84.97:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2728 | duplicate-photo-finder-plus.tmp | GET | 200 | 205.185.216.42:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?650d3fb510ea064a | US | compressed | 4.70 Kb | whitelisted |
2728 | duplicate-photo-finder-plus.tmp | GET | 200 | 143.204.101.143:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAtQvBbyWXPf0hng54oxdZQ%3D | US | der | 471 b | whitelisted |
2728 | duplicate-photo-finder-plus.tmp | GET | 200 | 143.204.101.190:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2728 | duplicate-photo-finder-plus.tmp | 143.204.98.27:443 | dpd.securestudies.com | — | US | malicious |
2728 | duplicate-photo-finder-plus.tmp | 205.185.216.42:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
— | — | 13.225.84.97:80 | o.ss2.us | — | US | unknown |
— | — | 143.204.101.124:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
— | — | 143.204.101.143:80 | ocsp.sca1b.amazontrust.com | — | US | whitelisted |
2920 | spt_setup.tmp | 143.204.98.27:443 | dpd.securestudies.com | — | US | malicious |
2920 | spt_setup.tmp | 165.193.78.234:443 | post.securestudies.com | Savvis | US | malicious |
— | — | 143.204.101.190:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dpd.securestudies.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
post.securestudies.com |
| malicious |