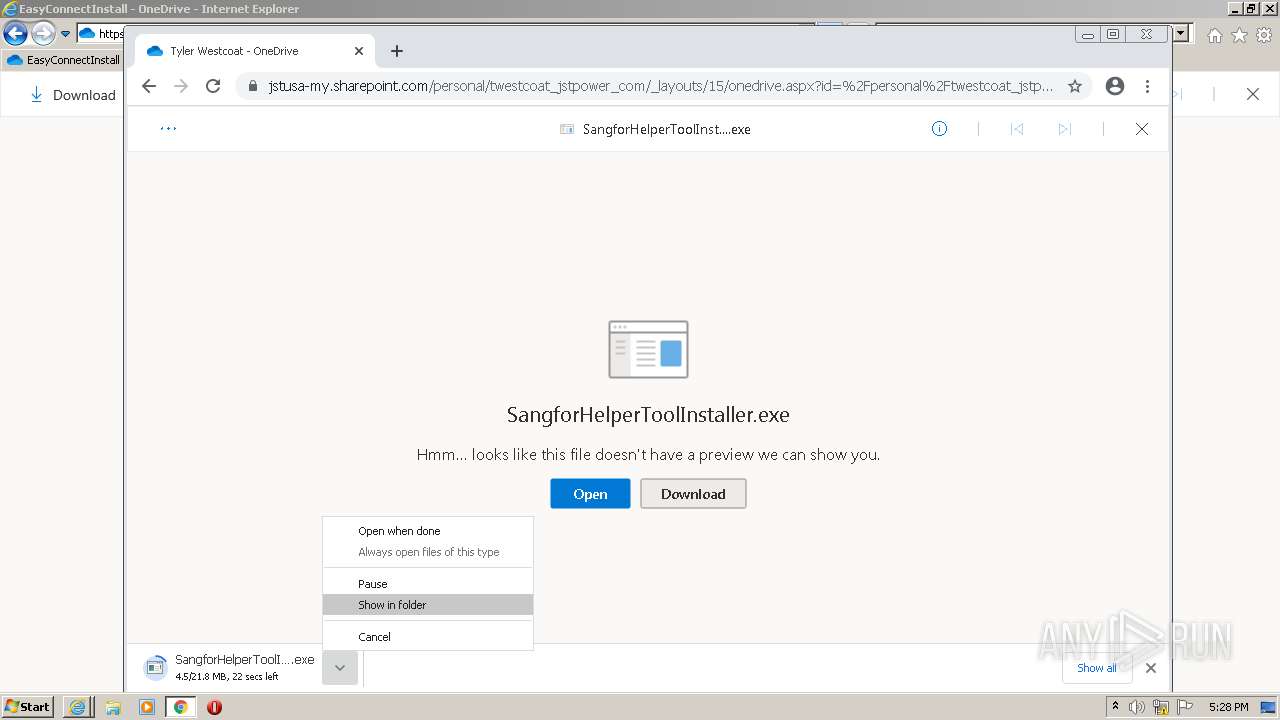
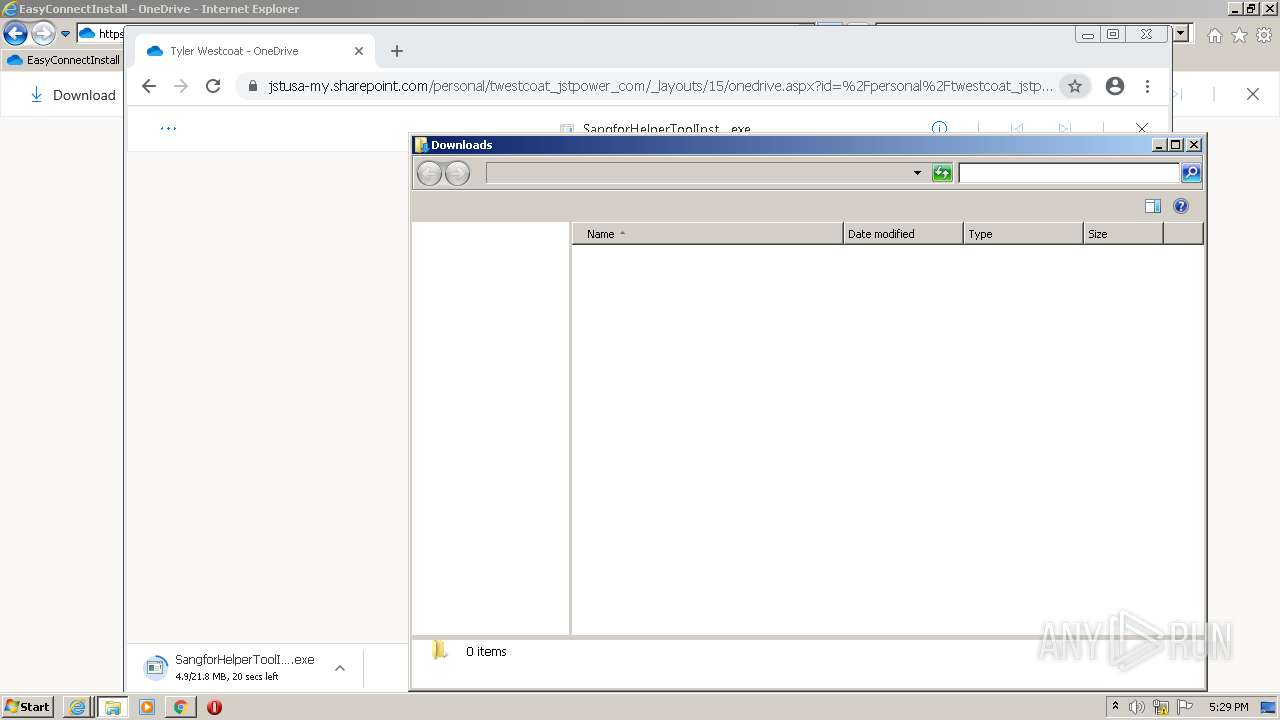
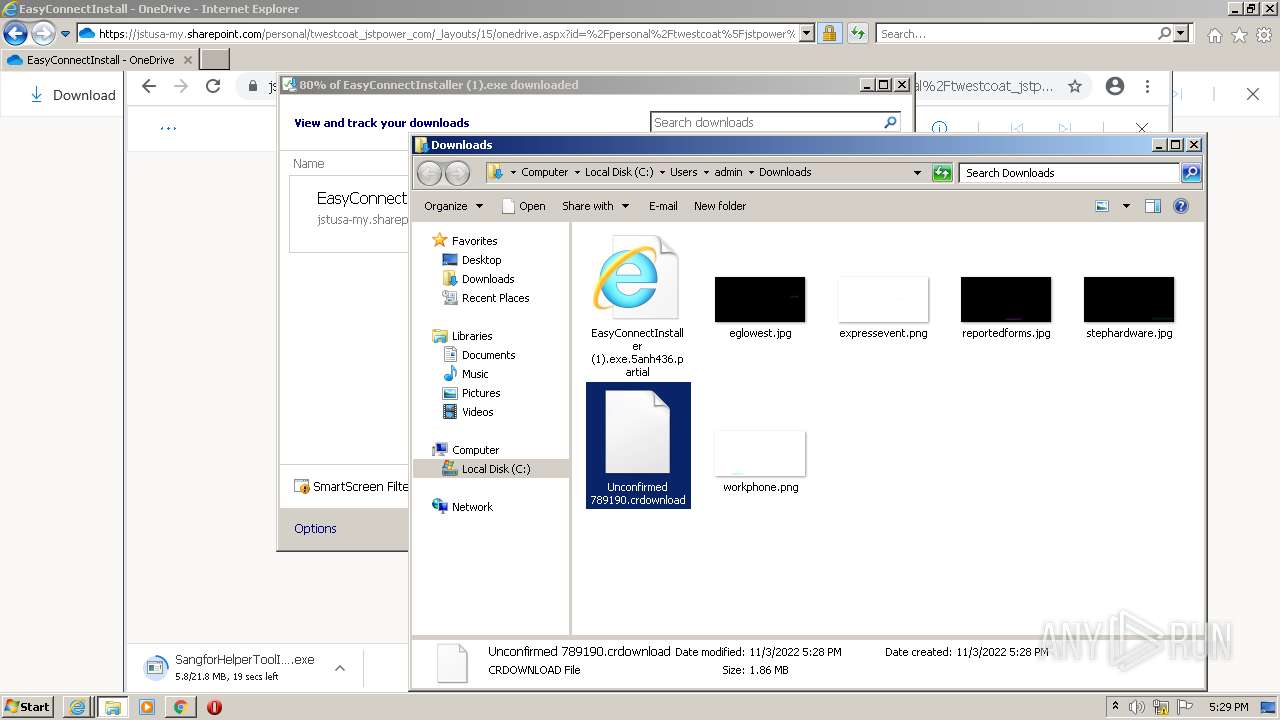
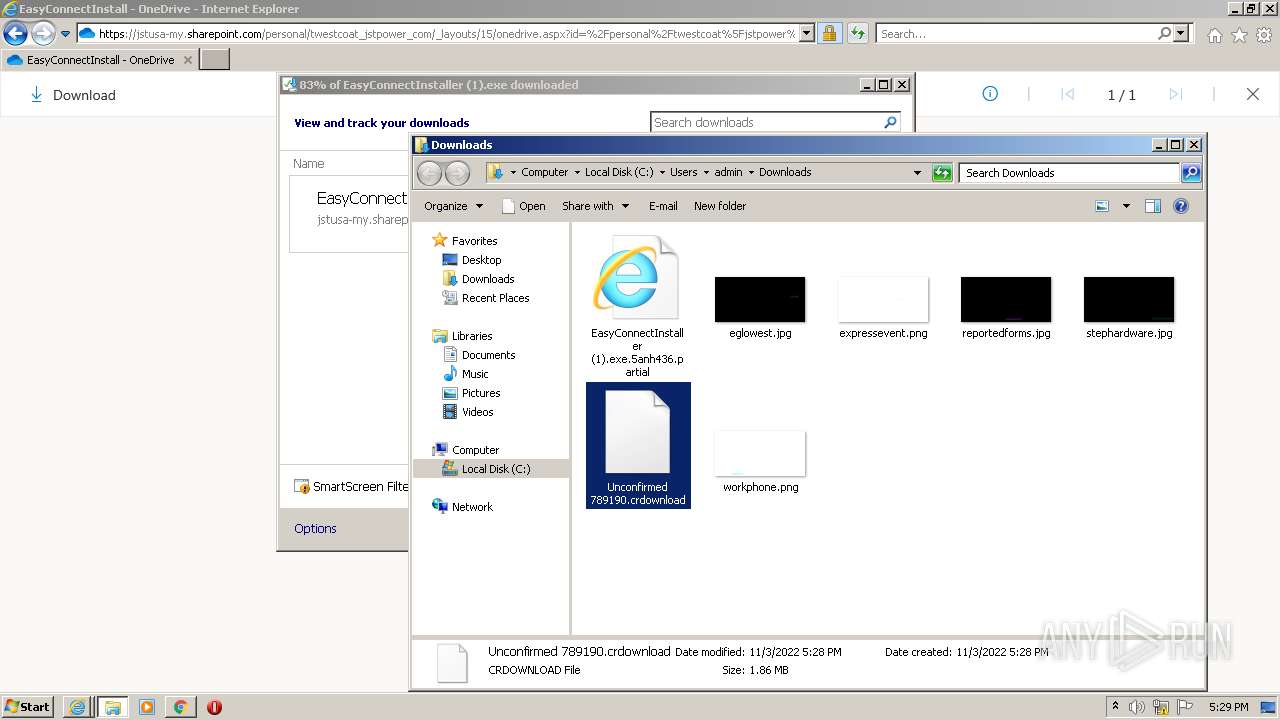
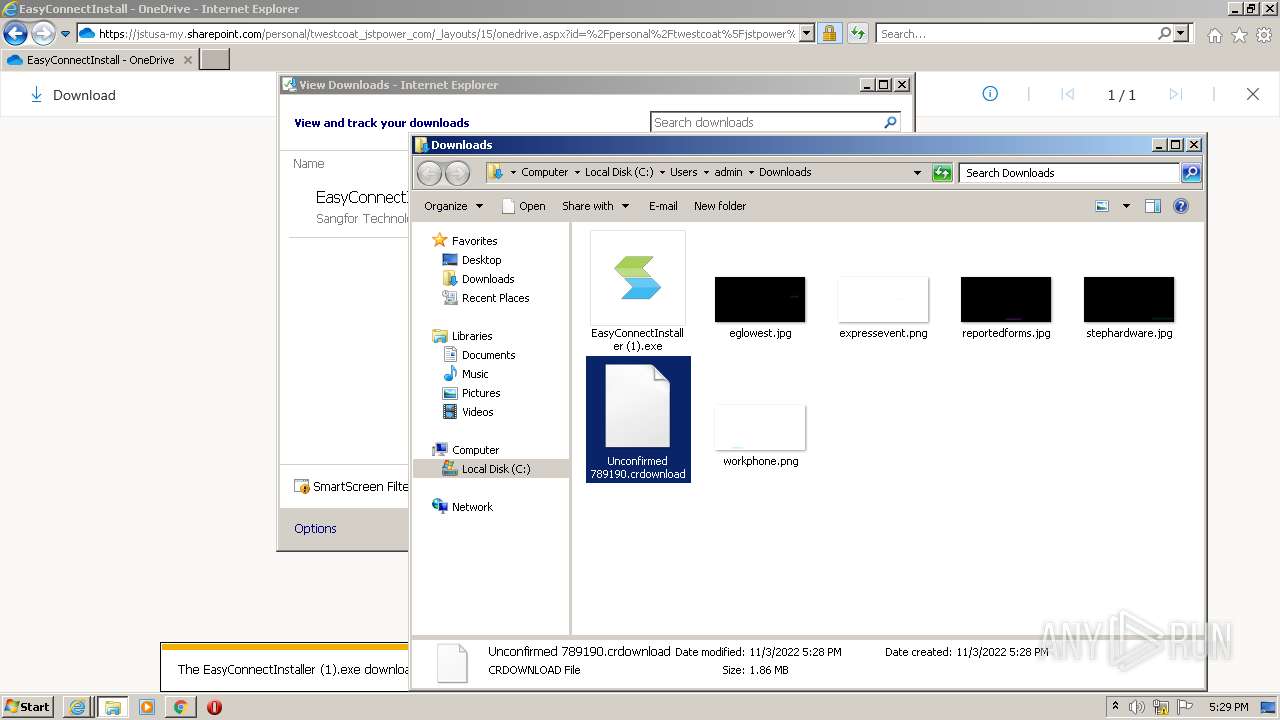
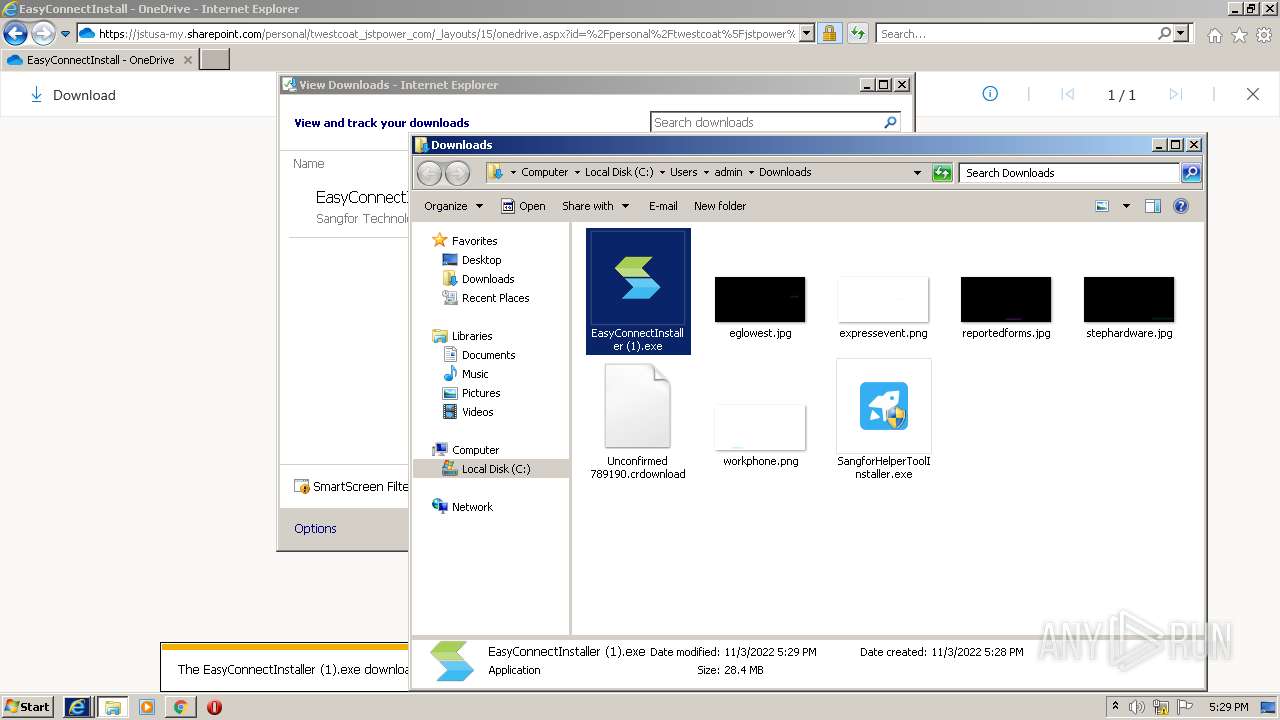
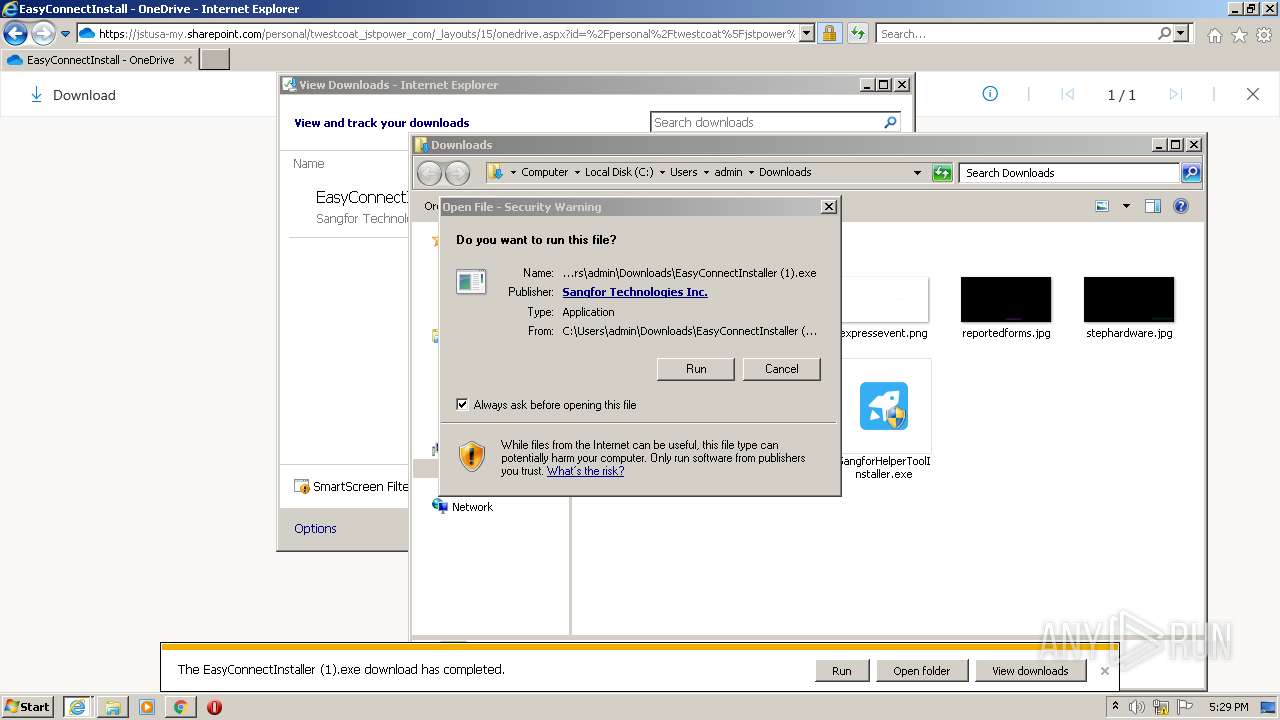
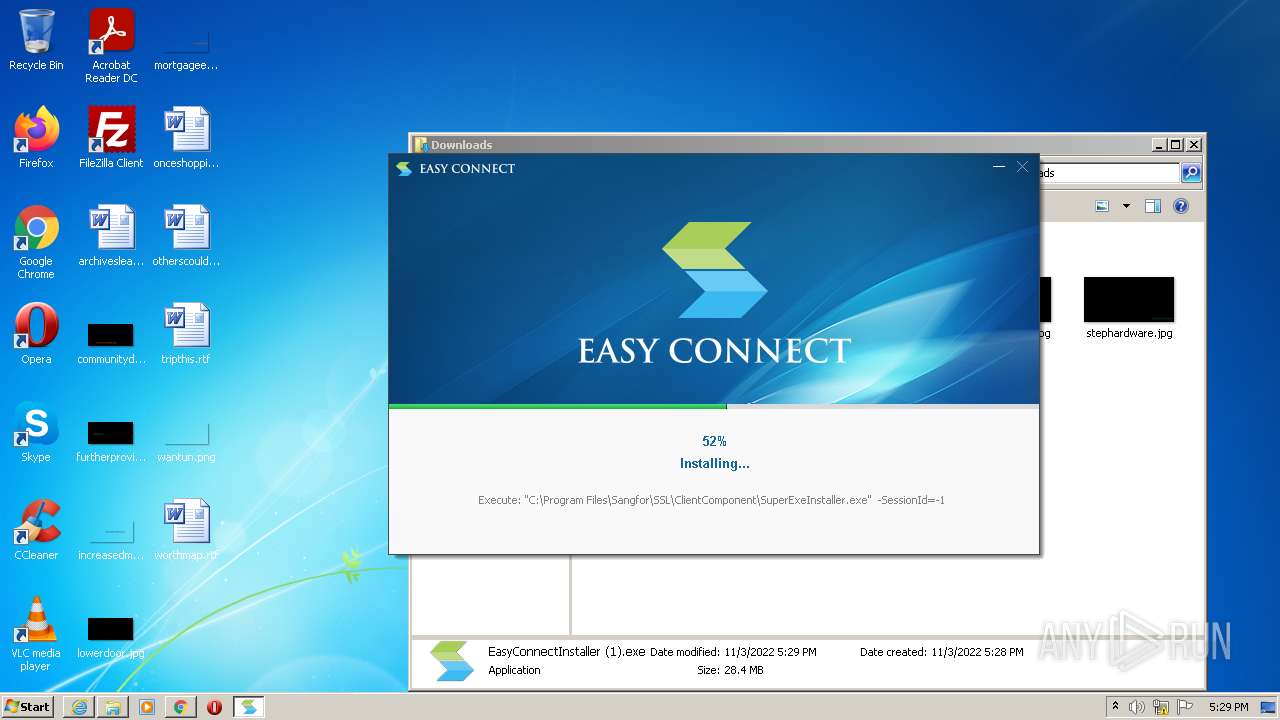
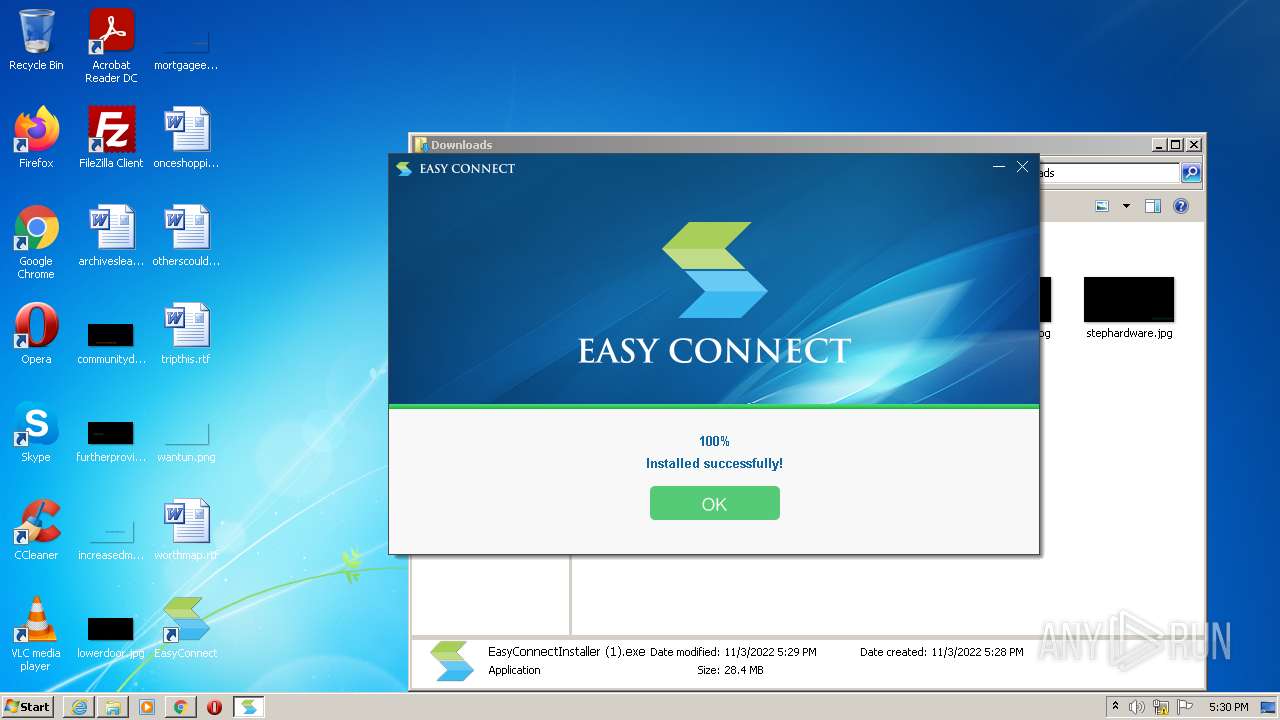
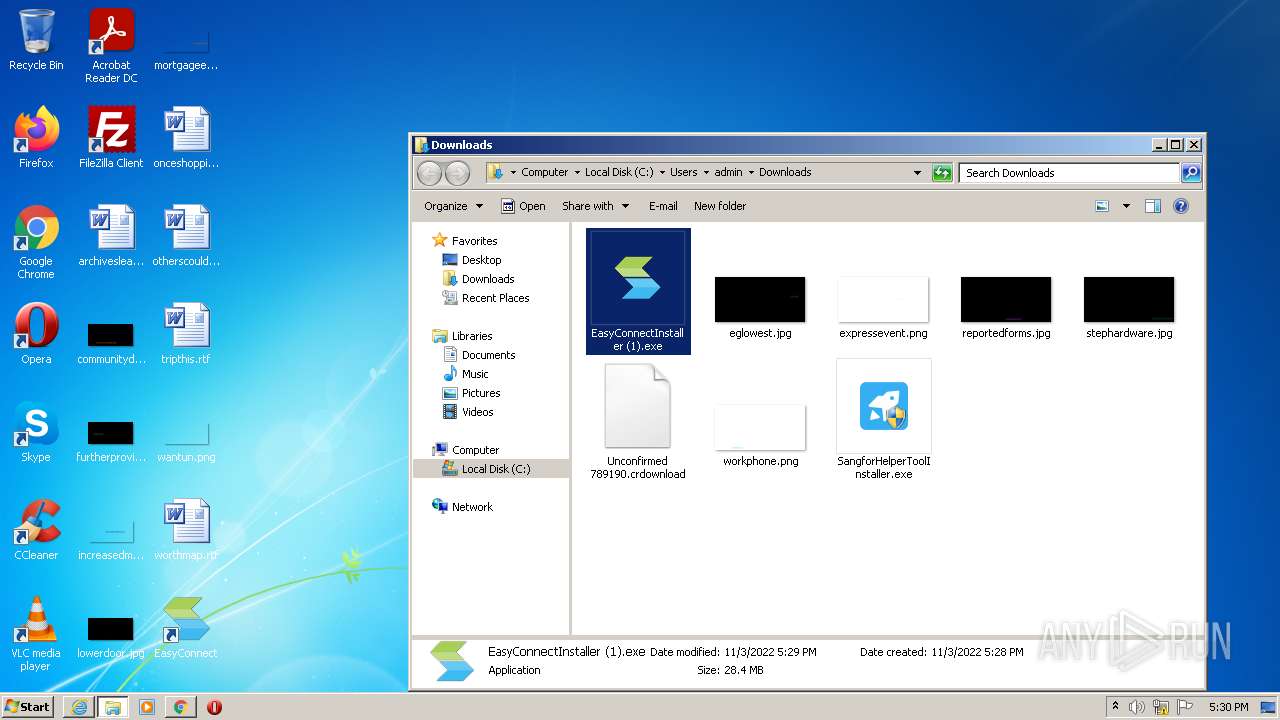
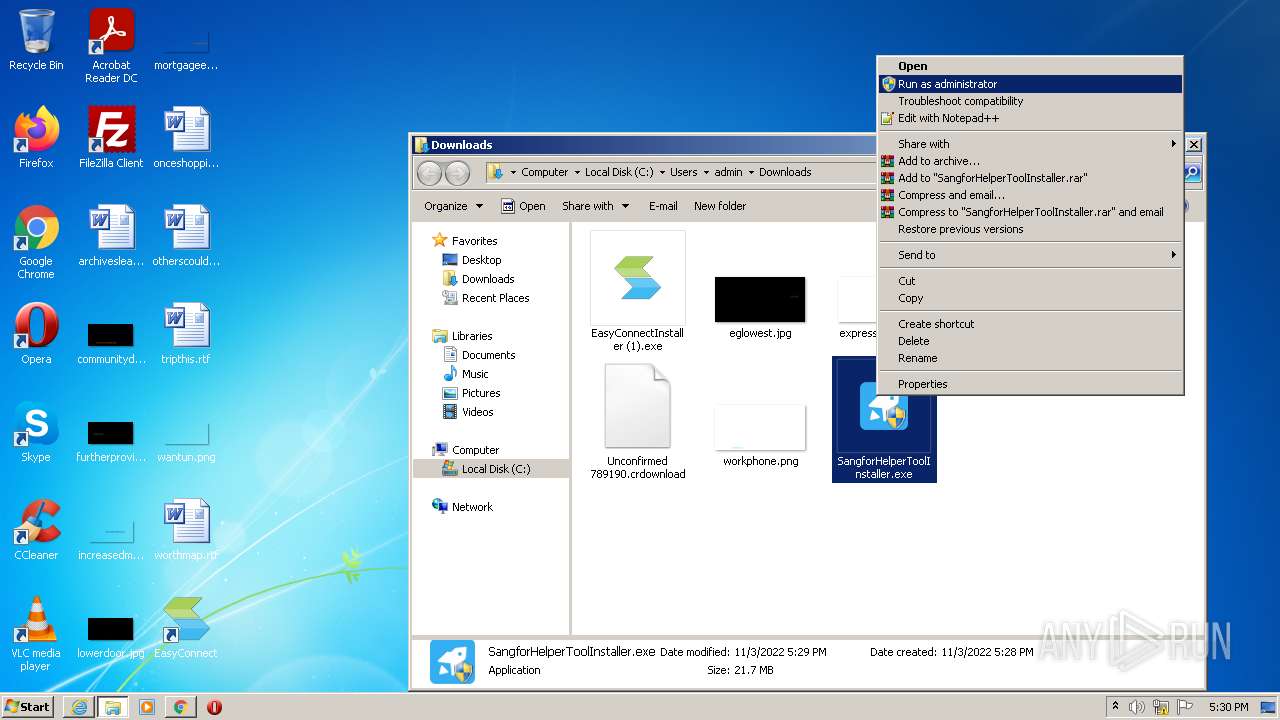
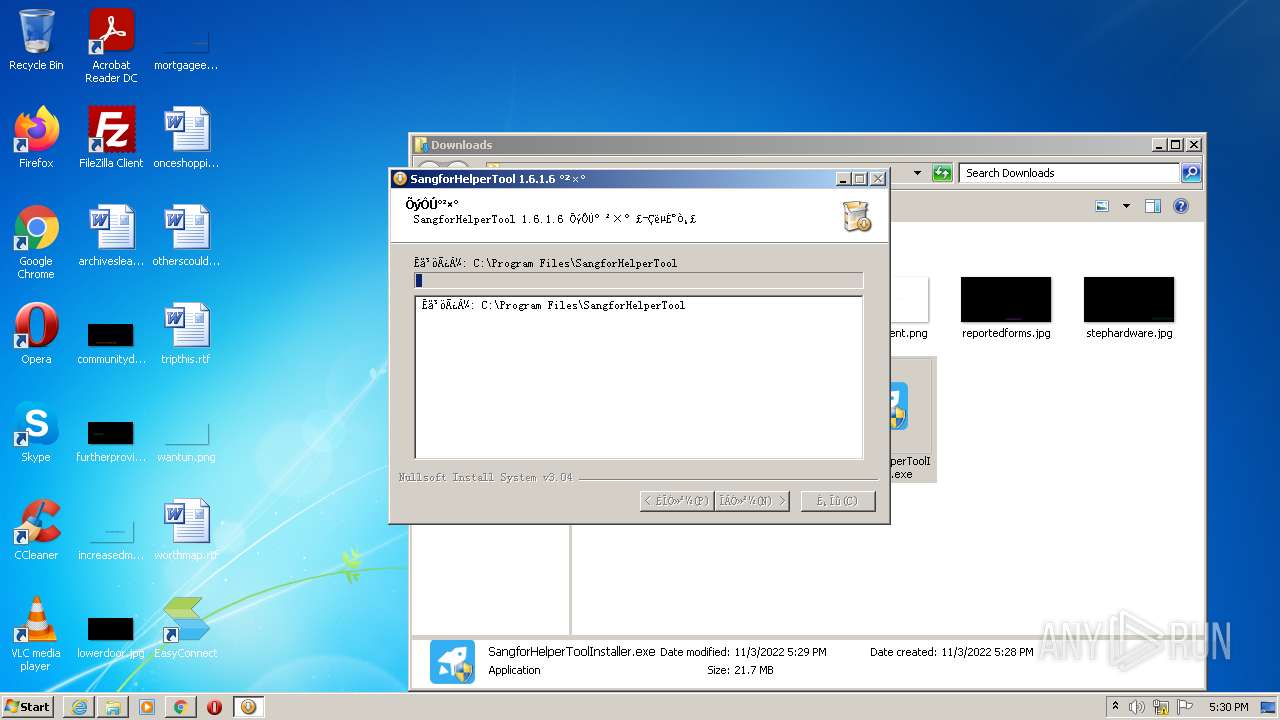
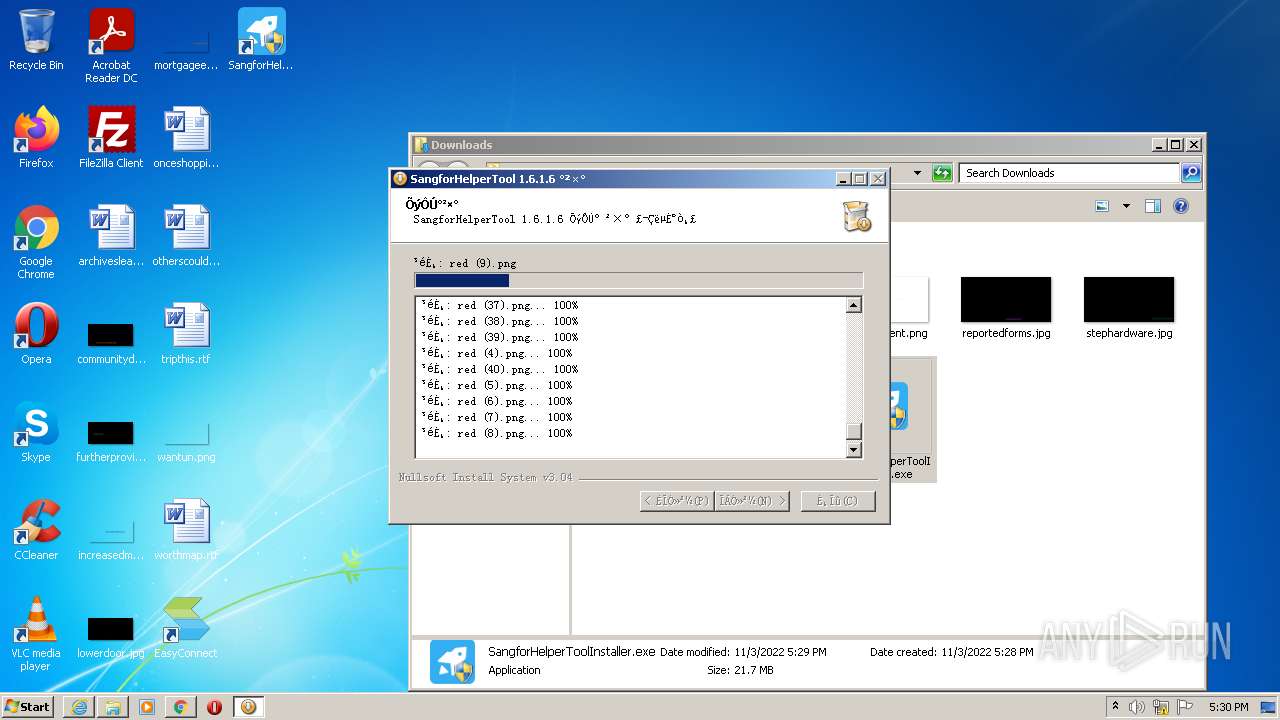
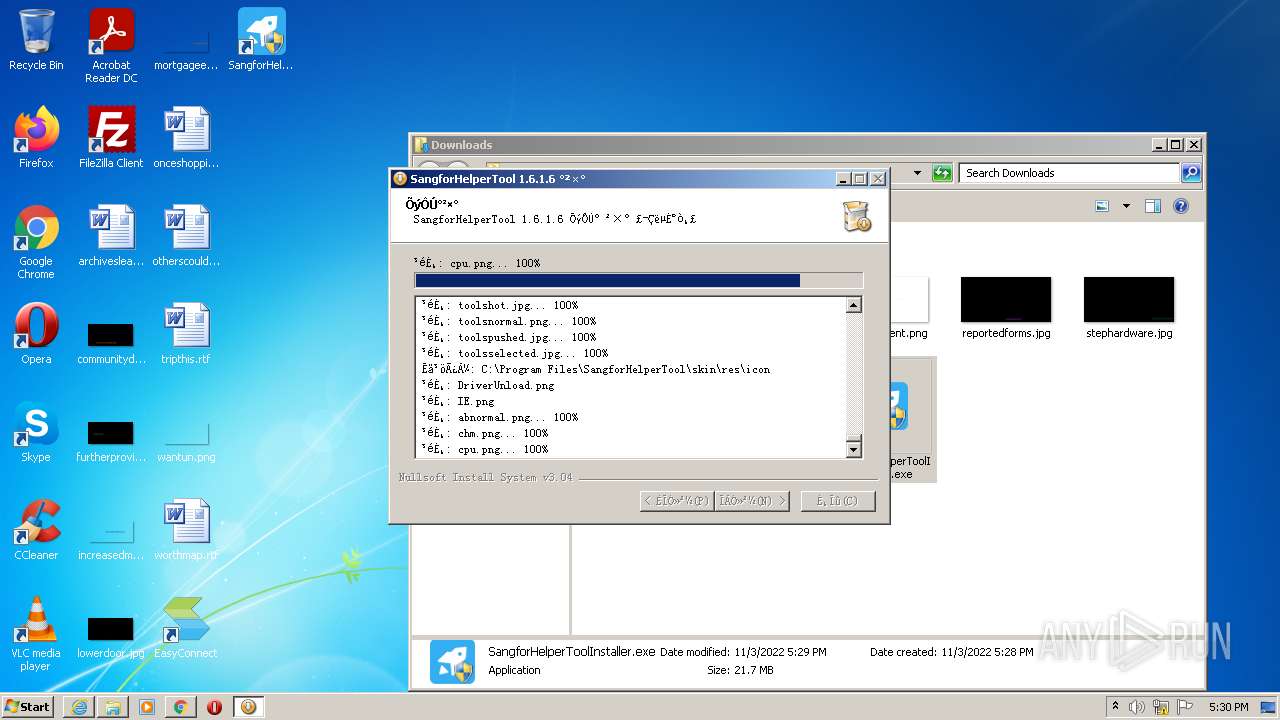
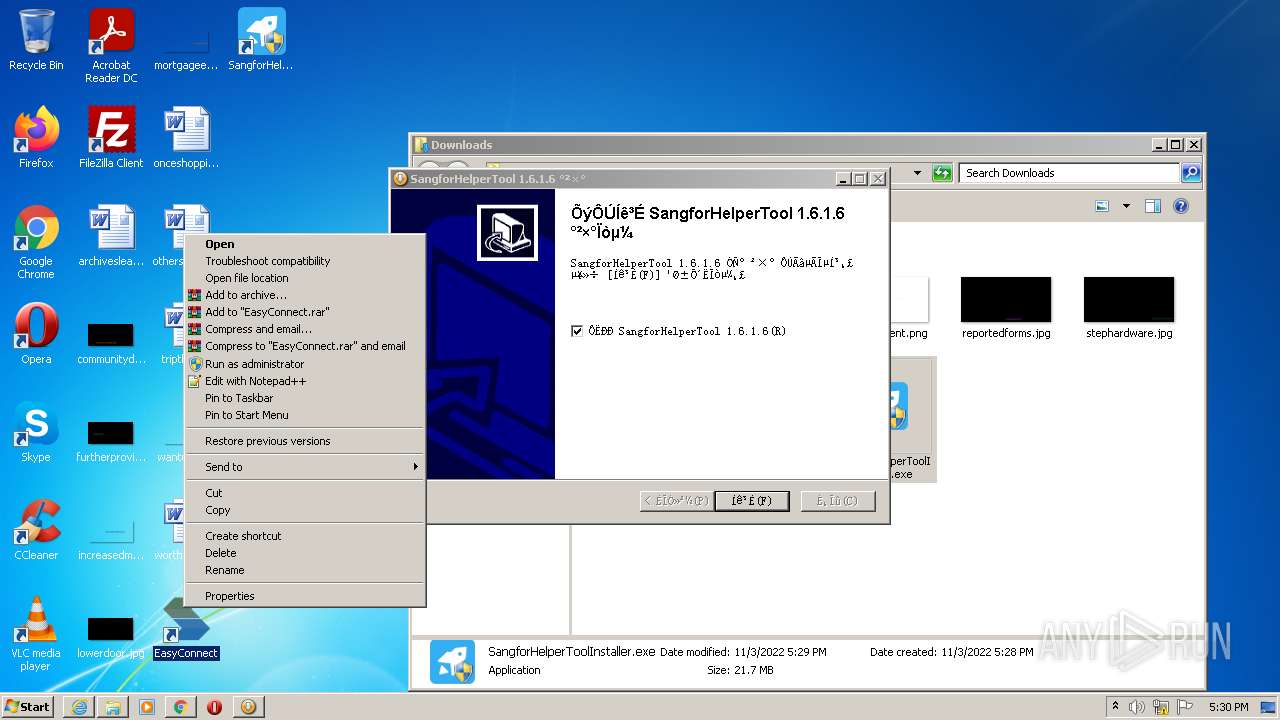
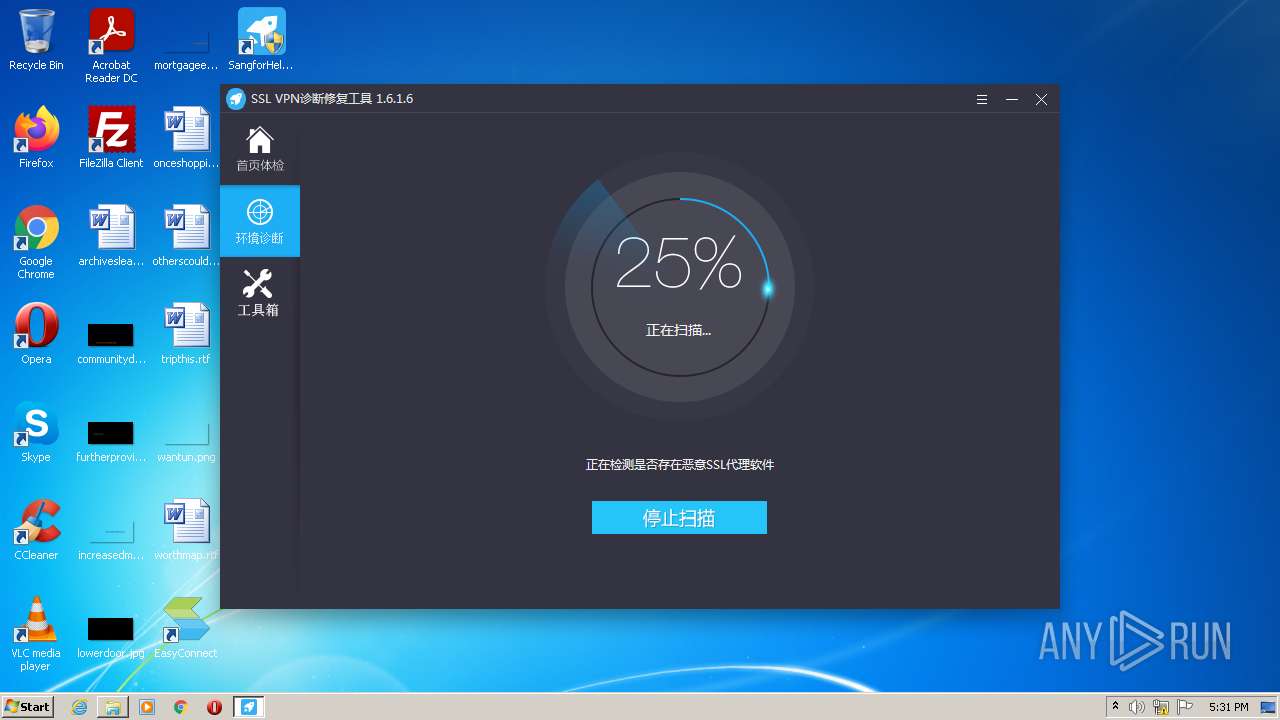
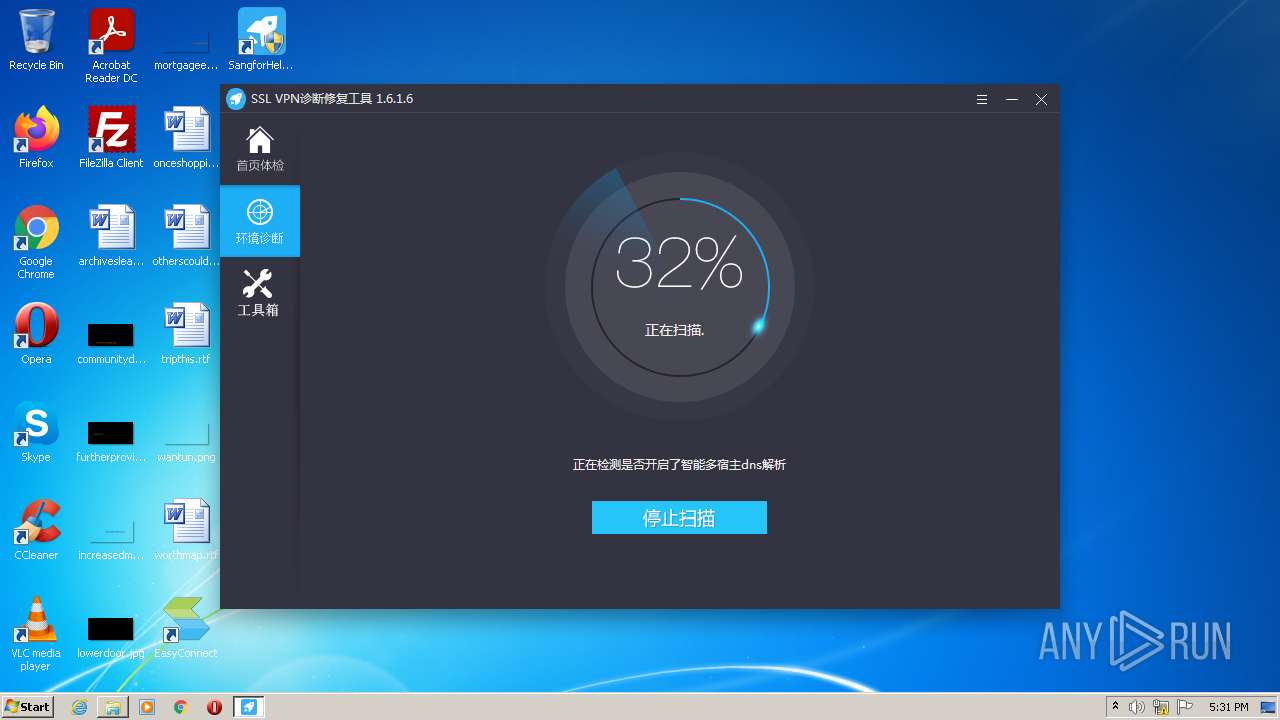
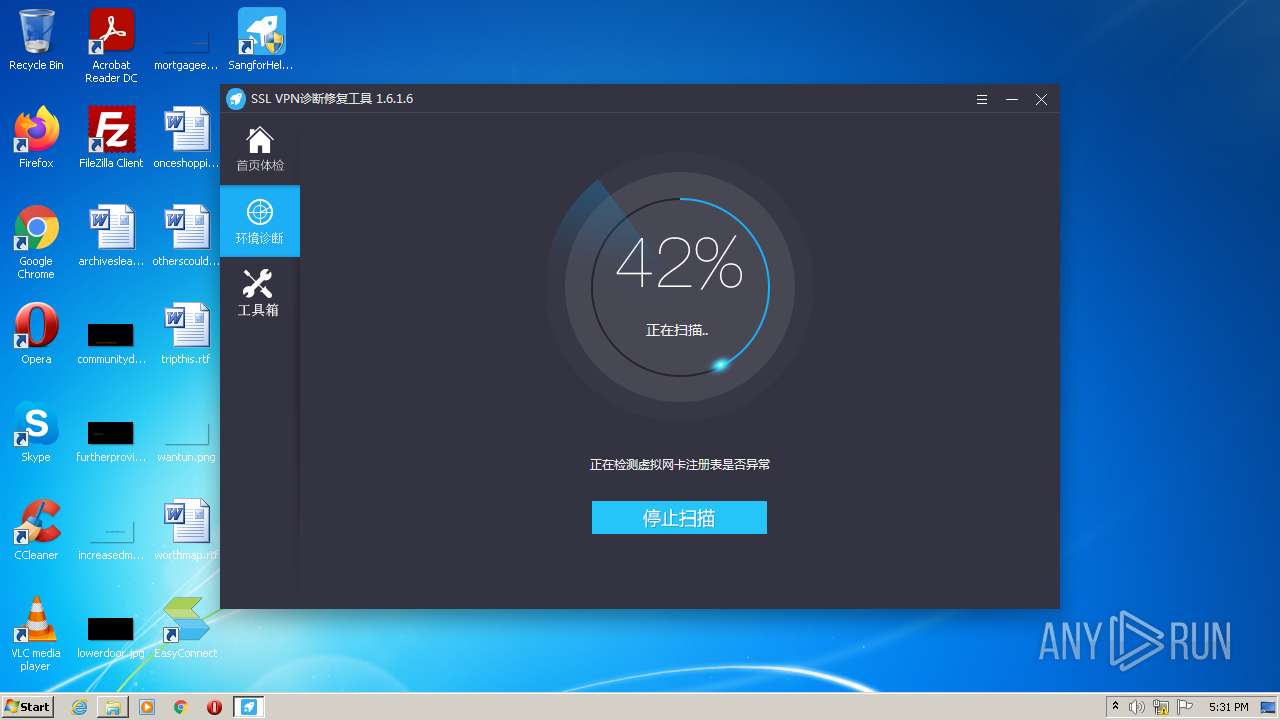
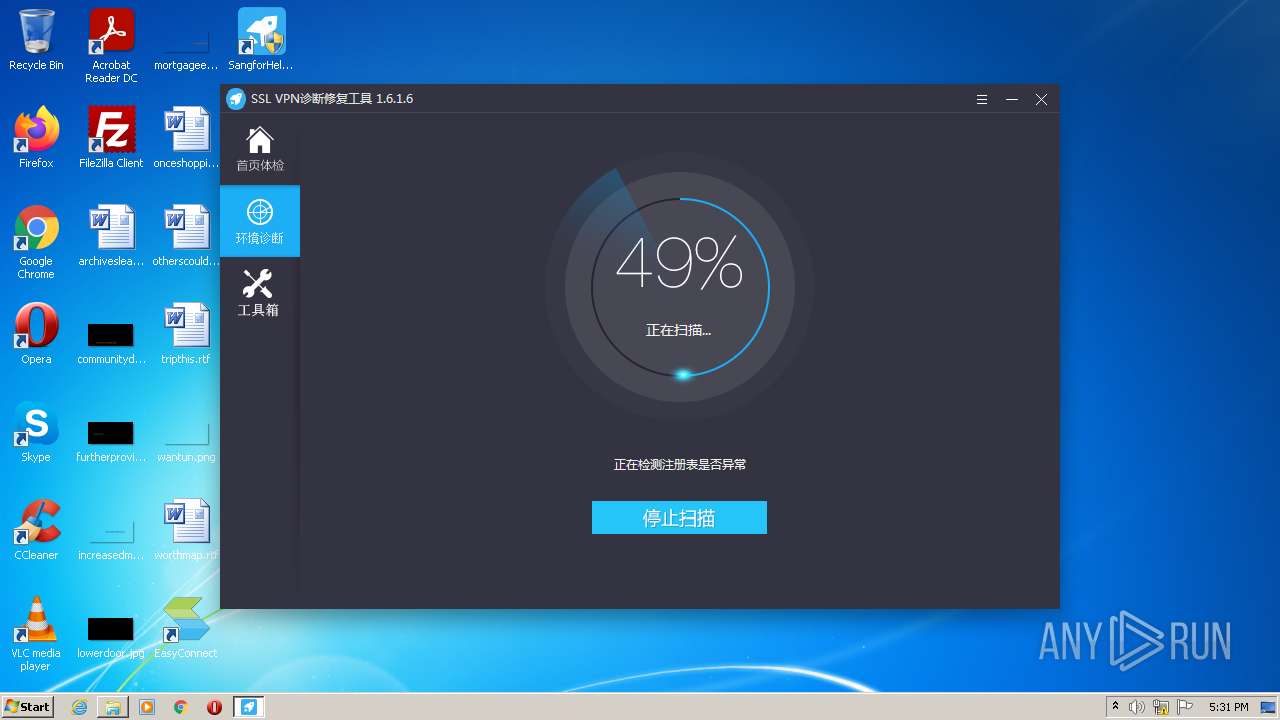
| URL: | https://jstusa-my.sharepoint.com/:u:/g/personal/twestcoat_jstpower_com/ERgMc2P5UOxFoPcC3nMsAUYBSg1RKDG9WKFzqQfeNuHL9g?e=Do54jH |
| Full analysis: | https://app.any.run/tasks/1a0da027-c19a-4c99-880e-20ea17b852fd |
| Verdict: | Malicious activity |
| Analysis date: | November 03, 2022, 17:27:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 13B99735FFF0752458D0AE001828DA6B |
| SHA1: | ED2B92B39D6C597739E45AF629521143EDCED7A2 |
| SHA256: | CE919D032154CD421E0CABDEA98E2B12BD2D1B0664B482B97E660B4390EE3B82 |
| SSDEEP: | 3:N8pUhjArL5kKVFSR6gfR6u273rA1QxLLi2CScBfx/b29cmtn:2uAfz8JR8k1QNm2t9can |
MALICIOUS
Application was dropped or rewritten from another process
- EasyConnectInstaller (1).exe (PID: 576)
- EasyConnectInstallerRaw.exe (PID: 2236)
- EasyConnectInstallerRaw.exe (PID: 1832)
- EasyConnectInstaller (1).exe (PID: 3628)
- Uninstall.exe (PID: 3708)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- SuperExeInstaller.exe (PID: 3380)
- Remove.exe (PID: 3592)
- Install.exe (PID: 2312)
- EasyConnectUIInstaller.exe (PID: 528)
- Remove.exe (PID: 3580)
- Install.exe (PID: 1616)
- SangforServiceClientInstaller.exe (PID: 3100)
- VC2010RedistX86UInstaller.exe (PID: 2228)
- SJobberInstaller.exe (PID: 3064)
- SangforUpdateInstaller.exe (PID: 668)
- SangforRAppInstaller.exe (PID: 3344)
- SangforUDProtect.exe (PID: 3840)
- InstallControl.exe (PID: 2248)
- SangforPWInstaller.exe (PID: 2380)
- DataParserInstaller.exe (PID: 3676)
- SangforPW.exe (PID: 532)
- SangforPW.exe (PID: 1556)
- VNICInstaller.exe (PID: 3072)
- ndiscleanup.x86.exe (PID: 2640)
- vacon.exe (PID: 3068)
- SetIPTime.exe (PID: 2536)
- ECBaseInstaller.exe (PID: 2464)
- ECAgentInstaller.exe (PID: 2776)
- SuperServiceInstaller.exe (PID: 1068)
- SangforHelperToolInstaller.exe (PID: 3728)
- SangforCSClient.exe (PID: 124)
- EasyConnect.exe (PID: 320)
- SangforPromote.exe (PID: 3260)
- EasyConnect.exe (PID: 2452)
- EasyConnect.exe (PID: 3900)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
- EasyConnect.exe (PID: 2916)
- EasyConnect.exe (PID: 3860)
- EasyConnect.exe (PID: 3028)
- DoTask.EXE (PID: 2964)
- DoTask.EXE (PID: 3028)
- DoTask.EXE (PID: 2568)
- DoTask.EXE (PID: 4048)
- DoTask.EXE (PID: 2424)
- DoTask.EXE (PID: 3056)
- DoTask.EXE (PID: 2268)
Drops the executable file immediately after the start
- EasyConnectInstaller (1).exe (PID: 576)
- EasyConnectInstaller (1).exe (PID: 3628)
- EasyConnectInstallerRaw.exe (PID: 1832)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- SuperExeInstaller.exe (PID: 3380)
- EasyConnectUIInstaller.exe (PID: 528)
- VC2010RedistX86UInstaller.exe (PID: 2228)
- SJobberInstaller.exe (PID: 3064)
- SangforServiceClientInstaller.exe (PID: 3100)
- SangforUpdateInstaller.exe (PID: 668)
- SangforPWInstaller.exe (PID: 2380)
- SangforRAppInstaller.exe (PID: 3344)
- DataParserInstaller.exe (PID: 3676)
- InstallControl.exe (PID: 2248)
- VNICInstaller.exe (PID: 3072)
- vacon.exe (PID: 3068)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
- SangforHelperTool.exe (PID: 1652)
- DoTask.EXE (PID: 2964)
Creates a writable file the system directory
- EasyConnectInstallerRaw.exe (PID: 1832)
- SangforCSClientInstaller.exe (PID: 3156)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- ECAgentInstaller.exe (PID: 2776)
Loads dropped or rewritten executable
- EasyConnectInstallerRaw.exe (PID: 1832)
- svchost.exe (PID: 868)
- SangforCSClientInstaller.exe (PID: 3156)
- DnsDriverInstaller.exe (PID: 2744)
- chrome.exe (PID: 1984)
- TcpDriverInstaller.exe (PID: 668)
- SangforPWInstaller.exe (PID: 2380)
- SangforUpdateInstaller.exe (PID: 668)
- chrome.exe (PID: 1788)
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 3256)
- SangforUDProtect.exe (PID: 3840)
- chrome.exe (PID: 2088)
- Explorer.EXE (PID: 1100)
- DllHost.exe (PID: 3736)
- VNICInstaller.exe (PID: 3072)
- DataParserInstaller.exe (PID: 3676)
- InstallControl.exe (PID: 2248)
- svchost.exe (PID: 1440)
- ECAgent.exe (PID: 3752)
- ECAgentInstaller.exe (PID: 2776)
- svchost.exe (PID: 712)
- SangforPromoteService.exe (PID: 3392)
- ECAgent.exe (PID: 3112)
- ctfmon.exe (PID: 736)
- ECAgent.exe (PID: 3360)
- chrome.exe (PID: 2204)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
- DllHost.exe (PID: 3212)
- EasyConnect.exe (PID: 320)
- SangforPromote.exe (PID: 3260)
- DllHost.exe (PID: 1132)
- SangforCSClient.exe (PID: 124)
- DllHost.exe (PID: 3768)
- EasyConnect.exe (PID: 2452)
- SangforHelperTool.exe (PID: 1652)
- EasyConnect.exe (PID: 3900)
- ECAgent.exe (PID: 2972)
- EasyConnect.exe (PID: 2916)
- ECAgent.exe (PID: 2780)
- EasyConnect.exe (PID: 3860)
- DllHost.exe (PID: 1776)
- DoTask.EXE (PID: 4048)
- EasyConnect.exe (PID: 3028)
- DllHost.exe (PID: 2392)
- DoTask.EXE (PID: 3056)
- DoTask.EXE (PID: 2268)
- explorer.exe (PID: 2768)
- Dwm.exe (PID: 1412)
- taskeng.exe (PID: 664)
- ECAgent.exe (PID: 2636)
- DllHost.exe (PID: 3812)
- NOTEPAD.EXE (PID: 2544)
- taskhost.exe (PID: 1172)
- ECAgent.exe (PID: 4056)
- NOTEPAD.EXE (PID: 412)
- WinRAR.exe (PID: 708)
- NOTEPAD.EXE (PID: 1032)
Changes the autorun value in the registry
- EasyConnectInstallerRaw.exe (PID: 1832)
- DrvInst.exe (PID: 824)
- svchost.exe (PID: 868)
- X86-all-rootsupd.exe (PID: 3068)
Steals credentials from Web Browsers
- ECAgent.exe (PID: 3112)
SUSPICIOUS
Reads settings of System Certificates
- Explorer.EXE (PID: 1100)
- SangforPW.exe (PID: 1556)
- vacon.exe (PID: 3068)
- DrvInst.exe (PID: 2132)
- ECAgent.exe (PID: 3360)
- SangforPromoteService.exe (PID: 3392)
- consent.exe (PID: 2176)
- SangforCSClient.exe (PID: 124)
- updroots.exe (PID: 1304)
- updroots.exe (PID: 2468)
- updroots.exe (PID: 4028)
- consent.exe (PID: 2972)
- ECAgent.exe (PID: 2780)
- ECAgent.exe (PID: 4056)
- SangforUDProtect.exe (PID: 3840)
- DrvInst.exe (PID: 824)
- updroots.exe (PID: 2636)
Drops a file with too old compile date
- EasyConnectInstaller (1).exe (PID: 576)
- EasyConnectInstaller (1).exe (PID: 3628)
- EasyConnectInstallerRaw.exe (PID: 1832)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- SuperExeInstaller.exe (PID: 3380)
- EasyConnectUIInstaller.exe (PID: 528)
- SangforServiceClientInstaller.exe (PID: 3100)
- SJobberInstaller.exe (PID: 3064)
- SangforCSClientInstaller.exe (PID: 3156)
- SangforUpdateInstaller.exe (PID: 668)
- SangforPWInstaller.exe (PID: 2380)
- SangforRAppInstaller.exe (PID: 3344)
- DataParserInstaller.exe (PID: 3676)
- VNICInstaller.exe (PID: 3072)
Executable content was dropped or overwritten
- EasyConnectInstaller (1).exe (PID: 576)
- EasyConnectInstaller (1).exe (PID: 3628)
- EasyConnectInstallerRaw.exe (PID: 1832)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- SuperExeInstaller.exe (PID: 3380)
- EasyConnectUIInstaller.exe (PID: 528)
- SangforServiceClientInstaller.exe (PID: 3100)
- VC2010RedistX86UInstaller.exe (PID: 2228)
- SJobberInstaller.exe (PID: 3064)
- SangforUpdateInstaller.exe (PID: 668)
- SangforPWInstaller.exe (PID: 2380)
- SangforRAppInstaller.exe (PID: 3344)
- DataParserInstaller.exe (PID: 3676)
- InstallControl.exe (PID: 2248)
- vacon.exe (PID: 3068)
- VNICInstaller.exe (PID: 3072)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- SangforHelperTool.exe (PID: 1652)
- DoTask.EXE (PID: 2964)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
Creates files in the Windows directory
- EasyConnectInstallerRaw.exe (PID: 1832)
- SangforCSClientInstaller.exe (PID: 3156)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- ECAgentInstaller.exe (PID: 2776)
Creates a directory in Program Files
- EasyConnectInstallerRaw.exe (PID: 1832)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- SuperExeInstaller.exe (PID: 3380)
- EasyConnectUIInstaller.exe (PID: 528)
- SangforServiceClientInstaller.exe (PID: 3100)
- SJobberInstaller.exe (PID: 3064)
- SangforPWInstaller.exe (PID: 2380)
- SangforUpdateInstaller.exe (PID: 668)
- SangforRAppInstaller.exe (PID: 3344)
- InstallControl.exe (PID: 2248)
- DataParserInstaller.exe (PID: 3676)
- VNICInstaller.exe (PID: 3072)
- ECBaseInstaller.exe (PID: 2464)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
Removes files from Windows the directory
- EasyConnectInstallerRaw.exe (PID: 1832)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- ECAgentInstaller.exe (PID: 2776)
Creates/Modifies COM task schedule object
- EasyConnectInstallerRaw.exe (PID: 1832)
- InstallControl.exe (PID: 2248)
The process checks if it is being run in the virtual environment
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
Process drops SQLite DLL files
- EasyConnectUIInstaller.exe (PID: 528)
Creates a software uninstall entry
- EasyConnectUIInstaller.exe (PID: 528)
- VNICInstaller.exe (PID: 3072)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
Starts application with an unusual extension
- SangforUpdateInstaller.exe (PID: 668)
- SangforPWInstaller.exe (PID: 2380)
- VNICInstaller.exe (PID: 3072)
Starts SC.EXE for service management
- ns75A8.tmp (PID: 3292)
- ns753A.tmp (PID: 3972)
- ns78E7.tmp (PID: 3556)
- ns79C4.tmp (PID: 3976)
- ns7956.tmp (PID: 3220)
Executes as Windows Service
- SangforPW.exe (PID: 1556)
- vssvc.exe (PID: 2076)
- SangforPromoteService.exe (PID: 3392)
Uses TASKKILL.EXE to kill process
- ns7617.tmp (PID: 3440)
Checks Windows Trust Settings
- SangforPW.exe (PID: 1556)
- SangforUDProtect.exe (PID: 3840)
- vacon.exe (PID: 3068)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- SangforPromoteService.exe (PID: 3392)
- SangforCSClient.exe (PID: 124)
Creates or modifies Windows services
- SangforPW.exe (PID: 1556)
Reads security settings of Internet Explorer
- vacon.exe (PID: 3068)
- SangforCSClient.exe (PID: 124)
Adds/modifies Windows certificates
- vacon.exe (PID: 3068)
- ECAgent.exe (PID: 3360)
- updroots.exe (PID: 4028)
- updroots.exe (PID: 1304)
- ECAgent.exe (PID: 2780)
- updroots.exe (PID: 2636)
- ECAgent.exe (PID: 4056)
- SangforPromoteService.exe (PID: 3392)
Creates files in the driver directory
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
Uses NETSH.EXE for network configuration
- SetIPTime.exe (PID: 2536)
Reads Internet Settings
- EasyConnect.exe (PID: 320)
- SangforCSClient.exe (PID: 124)
- SangforHelperTool.exe (PID: 1652)
- ECAgent.exe (PID: 2636)
Changes internet zones settings
- ECAgent.exe (PID: 2972)
- SangforHelperTool.exe (PID: 1652)
- ECAgent.exe (PID: 2636)
INFO
Manual execution by user
- chrome.exe (PID: 2088)
- EasyConnectInstaller (1).exe (PID: 576)
- EasyConnectInstaller (1).exe (PID: 3628)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3864)
- chrome.exe (PID: 2088)
- iexplore.exe (PID: 3256)
- chrome.exe (PID: 1984)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3864)
- chrome.exe (PID: 2088)
- iexplore.exe (PID: 3256)
- chrome.exe (PID: 1984)
Starts Internet Explorer
- Explorer.EXE (PID: 1100)
Application launched itself
- iexplore.exe (PID: 3256)
- chrome.exe (PID: 2088)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3256)
Reads security settings of Internet Explorer
- Explorer.EXE (PID: 1100)
- consent.exe (PID: 2176)
- consent.exe (PID: 2972)
Checks supported languages
- EasyConnectInstaller (1).exe (PID: 576)
- EasyConnectInstallerRaw.exe (PID: 1832)
- EasyConnectInstaller (1).exe (PID: 3628)
- Uninstall.exe (PID: 3708)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- Remove.exe (PID: 3592)
- DnsDriverInstaller.exe (PID: 2744)
- Install.exe (PID: 2312)
- Remove.exe (PID: 3580)
- Install.exe (PID: 1616)
- SuperExeInstaller.exe (PID: 3380)
- EasyConnectUIInstaller.exe (PID: 528)
- SangforServiceClientInstaller.exe (PID: 3100)
- VC2010RedistX86UInstaller.exe (PID: 2228)
- SJobberInstaller.exe (PID: 3064)
- ns74CD.tmp (PID: 3304)
- SangforPWInstaller.exe (PID: 2380)
- SangforUpdateInstaller.exe (PID: 668)
- ns7617.tmp (PID: 3440)
- ns77FC.tmp (PID: 1152)
- SangforPW.exe (PID: 532)
- ns78E7.tmp (PID: 3556)
- ns753A.tmp (PID: 3972)
- ns75A8.tmp (PID: 3292)
- ns7956.tmp (PID: 3220)
- ns79C4.tmp (PID: 3976)
- SangforRAppInstaller.exe (PID: 3344)
- SangforPW.exe (PID: 1556)
- SangforUDProtect.exe (PID: 3840)
- InstallControl.exe (PID: 2248)
- DataParserInstaller.exe (PID: 3676)
- VNICInstaller.exe (PID: 3072)
- ns80B4.tmp (PID: 3816)
- ndiscleanup.x86.exe (PID: 2640)
- vacon.exe (PID: 3068)
- ns8152.tmp (PID: 3780)
- DrvInst.exe (PID: 2132)
- SetIPTime.exe (PID: 2536)
- ECBaseInstaller.exe (PID: 2464)
- nsC7D1.tmp (PID: 3664)
- ECAgent.exe (PID: 3752)
- SuperServiceInstaller.exe (PID: 1068)
- ECAgentInstaller.exe (PID: 2776)
- SangforPromoteService.exe (PID: 3188)
- SangforPromoteService.exe (PID: 3392)
- SangforPromoteService.exe (PID: 2884)
- ECAgent.exe (PID: 3360)
- ECAgent.exe (PID: 3112)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
- SangforHelperToolInstaller.exe (PID: 3728)
- EasyConnect.exe (PID: 320)
- SangforCSClient.exe (PID: 124)
- SangforPromote.exe (PID: 3260)
- updroots.exe (PID: 1304)
- updroots.exe (PID: 2636)
- X86-all-rootsupd.exe (PID: 3068)
- updroots.exe (PID: 4028)
- updroots.exe (PID: 2468)
- EasyConnect.exe (PID: 2452)
- SangforHelperTool.exe (PID: 1652)
- DrvInst.exe (PID: 824)
- EasyConnect.exe (PID: 3900)
- EasyConnect.exe (PID: 2916)
- ECAgent.exe (PID: 2972)
- ECAgent.exe (PID: 2780)
- EasyConnect.exe (PID: 3860)
- EasyConnect.exe (PID: 3028)
- DoTask.EXE (PID: 4048)
- DoTask.EXE (PID: 3028)
- DoTask.EXE (PID: 2964)
- DoTask.EXE (PID: 2268)
- CheckFolderPermission.exe (PID: 3884)
- DoTask.EXE (PID: 3056)
- ECAgent.exe (PID: 2636)
- DoTask.EXE (PID: 2424)
- ECAgent.exe (PID: 4056)
- DoTask.EXE (PID: 2568)
Drops a file that was compiled in debug mode
- iexplore.exe (PID: 3256)
- EasyConnectInstallerRaw.exe (PID: 1832)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- SuperExeInstaller.exe (PID: 3380)
- EasyConnectUIInstaller.exe (PID: 528)
- VC2010RedistX86UInstaller.exe (PID: 2228)
- SangforServiceClientInstaller.exe (PID: 3100)
- SangforUpdateInstaller.exe (PID: 668)
- SangforPWInstaller.exe (PID: 2380)
- SangforRAppInstaller.exe (PID: 3344)
- DataParserInstaller.exe (PID: 3676)
- InstallControl.exe (PID: 2248)
- VNICInstaller.exe (PID: 3072)
- vacon.exe (PID: 3068)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- SangforHelperTool.exe (PID: 1652)
- DoTask.EXE (PID: 2964)
Creates files in the user directory
- EasyConnectInstaller (1).exe (PID: 576)
- EasyConnectInstaller (1).exe (PID: 3628)
- ECAgent.exe (PID: 3112)
- SangforHelperToolInstaller.exe (PID: 3728)
- EasyConnect.exe (PID: 320)
- SangforCSClient.exe (PID: 124)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
- SangforHelperTool.exe (PID: 1652)
- CheckFolderPermission.exe (PID: 3884)
Reads the computer name
- EasyConnectInstallerRaw.exe (PID: 1832)
- Uninstall.exe (PID: 3708)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- Install.exe (PID: 2312)
- DnsDriverInstaller.exe (PID: 2744)
- Install.exe (PID: 1616)
- EasyConnectUIInstaller.exe (PID: 528)
- SuperExeInstaller.exe (PID: 3380)
- SangforServiceClientInstaller.exe (PID: 3100)
- SJobberInstaller.exe (PID: 3064)
- SangforUpdateInstaller.exe (PID: 668)
- SangforPWInstaller.exe (PID: 2380)
- SangforPW.exe (PID: 532)
- SangforRAppInstaller.exe (PID: 3344)
- SangforPW.exe (PID: 1556)
- SangforUDProtect.exe (PID: 3840)
- DataParserInstaller.exe (PID: 3676)
- VNICInstaller.exe (PID: 3072)
- vacon.exe (PID: 3068)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- ECAgentInstaller.exe (PID: 2776)
- ECBaseInstaller.exe (PID: 2464)
- SangforPromoteService.exe (PID: 3188)
- SangforPromoteService.exe (PID: 2884)
- SangforPromoteService.exe (PID: 3392)
- SuperServiceInstaller.exe (PID: 1068)
- ECAgent.exe (PID: 3112)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
- EasyConnect.exe (PID: 320)
- SangforCSClient.exe (PID: 124)
- X86-all-rootsupd.exe (PID: 3068)
- SangforHelperTool.exe (PID: 1652)
- ECAgent.exe (PID: 2972)
- DoTask.EXE (PID: 4048)
- DoTask.EXE (PID: 3028)
- DoTask.EXE (PID: 2964)
- DoTask.EXE (PID: 3056)
- DoTask.EXE (PID: 2268)
- DoTask.EXE (PID: 2424)
- ECAgent.exe (PID: 2636)
- DoTask.EXE (PID: 2568)
Creates a file in a temporary directory
- EasyConnectInstallerRaw.exe (PID: 1832)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- SangforUpdateInstaller.exe (PID: 668)
- SangforPWInstaller.exe (PID: 2380)
- VNICInstaller.exe (PID: 3072)
- vacon.exe (PID: 3068)
- ECAgentInstaller.exe (PID: 2776)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
- X86-all-rootsupd.exe (PID: 3068)
- SangforHelperTool.exe (PID: 1652)
- CheckFolderPermission.exe (PID: 3884)
Process checks LSA protection
- EasyConnectInstallerRaw.exe (PID: 1832)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- EasyConnectUIInstaller.exe (PID: 528)
- SuperExeInstaller.exe (PID: 3380)
- SangforServiceClientInstaller.exe (PID: 3100)
- SJobberInstaller.exe (PID: 3064)
- SangforPWInstaller.exe (PID: 2380)
- SangforUpdateInstaller.exe (PID: 668)
- SangforPW.exe (PID: 1556)
- SangforRAppInstaller.exe (PID: 3344)
- SangforUDProtect.exe (PID: 3840)
- DataParserInstaller.exe (PID: 3676)
- VNICInstaller.exe (PID: 3072)
- vacon.exe (PID: 3068)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- ECBaseInstaller.exe (PID: 2464)
- ECAgentInstaller.exe (PID: 2776)
- SangforPromoteService.exe (PID: 3392)
- SuperServiceInstaller.exe (PID: 1068)
- ECAgent.exe (PID: 3360)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
- ECAgent.exe (PID: 3112)
- EasyConnect.exe (PID: 320)
- SangforCSClient.exe (PID: 124)
- SangforHelperTool.exe (PID: 1652)
- ECAgent.exe (PID: 2780)
- ECAgent.exe (PID: 4056)
Reads Environment values
- EasyConnectInstallerRaw.exe (PID: 1832)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- EasyConnectUIInstaller.exe (PID: 528)
- DrvInst.exe (PID: 824)
Creates files in the program directory
- EasyConnectInstallerRaw.exe (PID: 1832)
- SangforCSClientInstaller.exe (PID: 3156)
- TcpDriverInstaller.exe (PID: 668)
- DnsDriverInstaller.exe (PID: 2744)
- SuperExeInstaller.exe (PID: 3380)
- SangforServiceClientInstaller.exe (PID: 3100)
- SJobberInstaller.exe (PID: 3064)
- SangforUpdateInstaller.exe (PID: 668)
- EasyConnectUIInstaller.exe (PID: 528)
- SangforPWInstaller.exe (PID: 2380)
- SangforRAppInstaller.exe (PID: 3344)
- InstallControl.exe (PID: 2248)
- DataParserInstaller.exe (PID: 3676)
- VNICInstaller.exe (PID: 3072)
- ECBaseInstaller.exe (PID: 2464)
- ECAgentInstaller.exe (PID: 2776)
- SuperServiceInstaller.exe (PID: 1068)
- SangforHelperToolInstallerRaw.exe (PID: 1372)
- DoTask.EXE (PID: 2964)
Reads the machine GUID from the registry
- SangforPW.exe (PID: 1556)
- SangforUDProtect.exe (PID: 3840)
- VNICInstaller.exe (PID: 3072)
- vacon.exe (PID: 3068)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- SangforPromoteService.exe (PID: 3392)
- ECAgent.exe (PID: 3360)
- ECAgent.exe (PID: 3112)
- EasyConnect.exe (PID: 320)
- SangforCSClient.exe (PID: 124)
- SangforHelperTool.exe (PID: 1652)
- ECAgent.exe (PID: 2780)
- ECAgent.exe (PID: 4056)
Process checks SAM and SYSTEM backups
- SangforPW.exe (PID: 1556)
- SangforUDProtect.exe (PID: 3840)
- DrvInst.exe (PID: 2132)
- DrvInst.exe (PID: 824)
- SangforPromoteService.exe (PID: 3392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
196
Monitored processes
145
Malicious processes
56
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Sangfor\SSL\SangforCSClient\SangforCSClient.exe" EC | C:\Program Files\Sangfor\SSL\SangforCSClient\SangforCSClient.exe | EasyConnect.exe | ||||||||||||
User: admin Company: Sangfor Technologies Inc. Integrity Level: MEDIUM Description: SangforCSClient Exit code: 0 Version: 7,6,7,208 Modules
| |||||||||||||||
| 320 | "C:\Program Files\Sangfor\SSL\EasyConnect\EasyConnect.exe" /ShortCutAutoLogin | C:\Program Files\Sangfor\SSL\EasyConnect\EasyConnect.exe | Explorer.EXE | ||||||||||||
User: admin Company: Sangfor Technologies Inc. Integrity Level: MEDIUM Description: EasyConnect Exit code: 0 Version: 7,6,7,201 Modules
| |||||||||||||||
| 348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1040,8576645175113029103,3874309503420664113,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2884 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
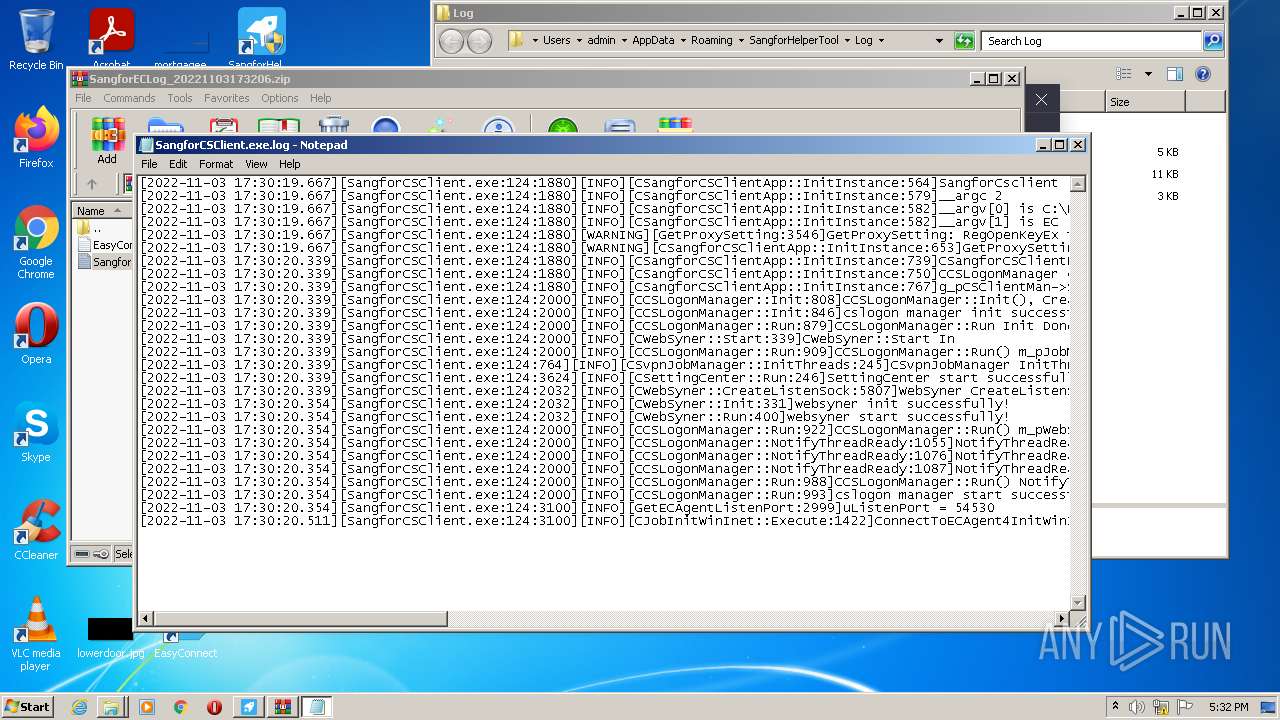
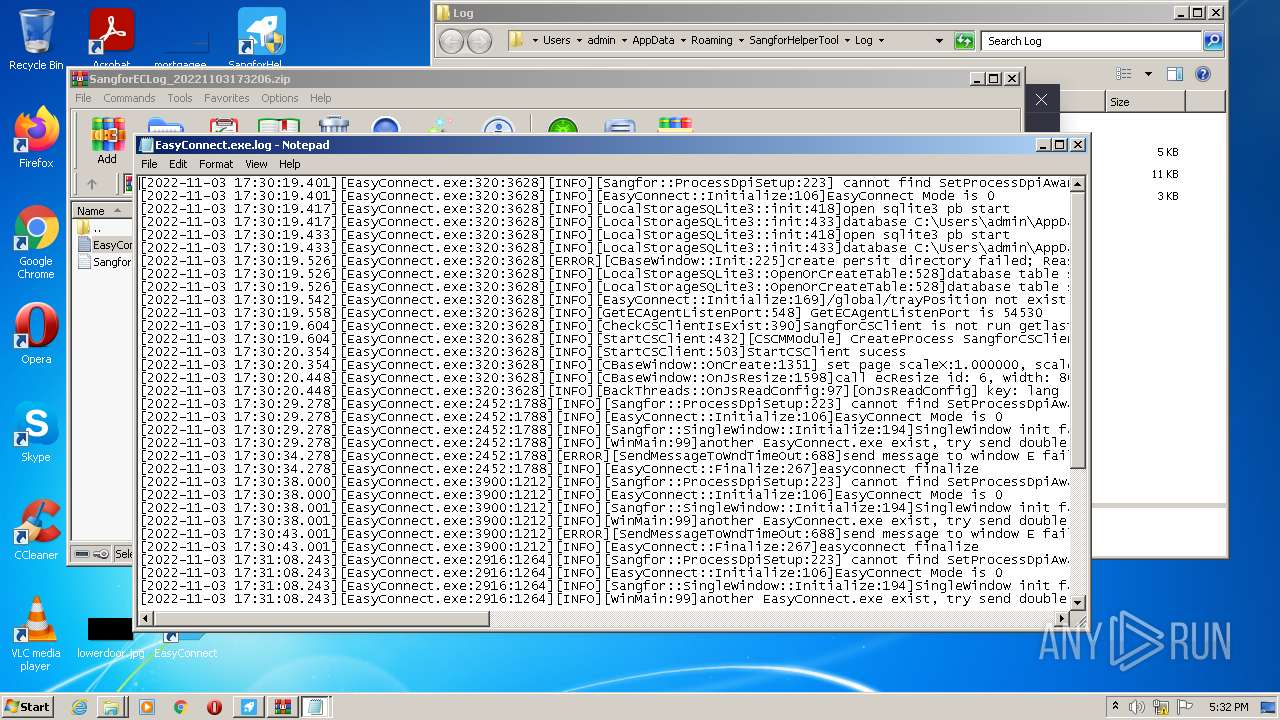
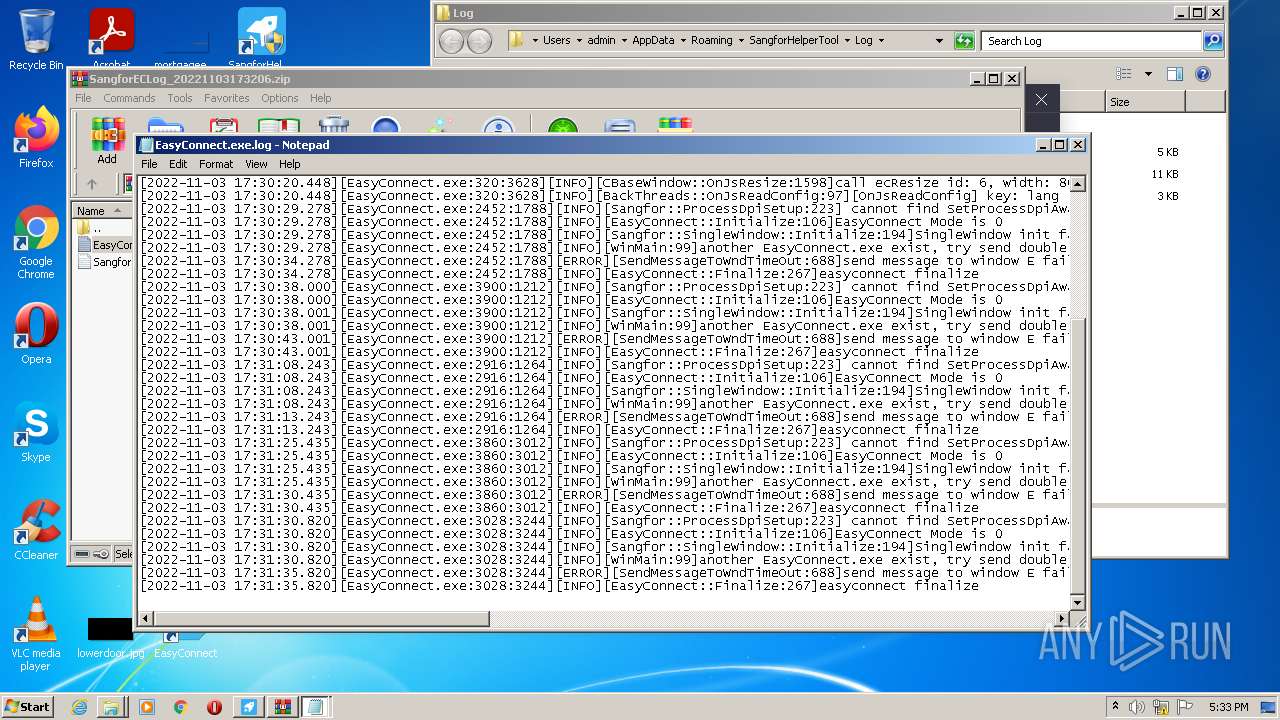
| 412 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa708.43279\EasyConnect.exe.log | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 528 | "C:\Program Files\Sangfor\SSL\ClientComponent\EasyConnectUIInstaller.exe" -SessionId=-1 | C:\Program Files\Sangfor\SSL\ClientComponent\EasyConnectUIInstaller.exe | EasyConnectInstallerRaw.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 528 | sc start SangforPW | C:\Windows\system32\sc.exe | — | ns78E7.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | "C:\Program Files\Sangfor\SSL\SangforPW\SangforPW.exe" /Service | C:\Program Files\Sangfor\SSL\SangforPW\SangforPW.exe | ns77FC.tmp | ||||||||||||
User: admin Company: Sangfor Technologies Inc. Integrity Level: HIGH Description: Sangfor Easyconnect Security Protect Service Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
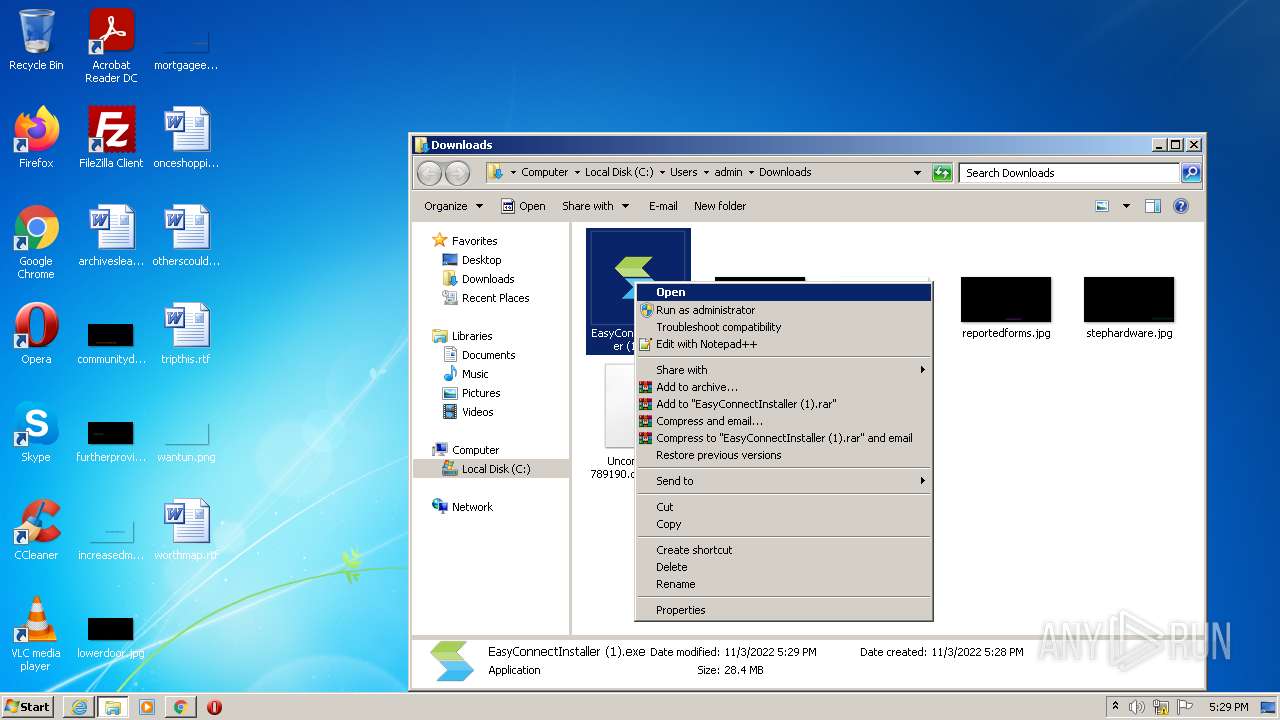
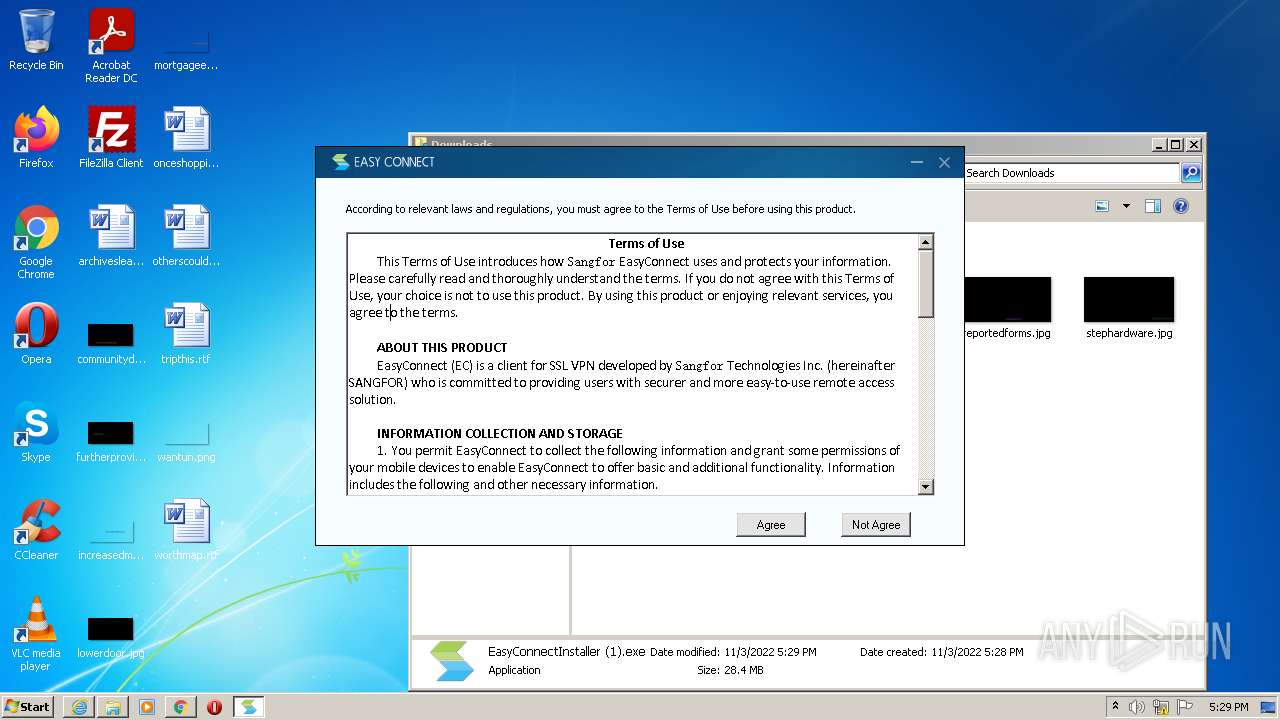
| 576 | "C:\Users\admin\Downloads\EasyConnectInstaller (1).exe" | C:\Users\admin\Downloads\EasyConnectInstaller (1).exe | Explorer.EXE | ||||||||||||
User: admin Company: Sangfor Technologies Inc. Integrity Level: MEDIUM Description: EasyConnect Exit code: 0 Version: 7, 6, 7, 0 Modules
| |||||||||||||||
| 664 | taskeng.exe {DB91E8D7-977A-400E-BA2C-A8ECB4D7B036} | C:\Windows\system32\taskeng.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | "C:\Program Files\Sangfor\SSL\ClientComponent\TcpDriverInstaller.exe" -SessionId=-1 | C:\Program Files\Sangfor\SSL\ClientComponent\TcpDriverInstaller.exe | EasyConnectInstallerRaw.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
118 401
Read events
113 817
Write events
3 999
Delete events
585
Modification events
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30994345 | |||
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30994345 | |||
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3256) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
159
Suspicious files
606
Text files
754
Unknown types
72
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1172 | taskhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat | — | |
MD5:— | SHA256:— | |||
| 712 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\~FontCache-S-1-5-21-1302019708-1500728564-335382590-1000.dat | — | |
MD5:— | SHA256:— | |||
| 3256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 3256 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:— | SHA256:— | |||
| 3256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_1941775A515122A167E3FBACF08992E1 | der | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\SQ2QM18I.txt | text | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\activitymonitor.min[1].js | text | |
MD5:— | SHA256:— | |||
| 1172 | taskhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\V01.log | binary | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\plt.listviewdataprefetch[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
115
DNS requests
46
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
3864 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
3256 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3864 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 46.0 Kb | whitelisted |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 46.0 Kb | whitelisted |
3864 | iexplore.exe | GET | 200 | 188.114.98.236:80 | http://ocsp.msocsp.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRSHuNsR4EZqcsD%2BrdOV%2BEZevGBiwQUtXYMMBHOx5JCTUzHXCzIqQzoC2QCExIAID0mTAYs5VcQIg4AAAAgPSY%3D | NL | der | 1.70 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.67 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 43.4 Kb | whitelisted |
3864 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEA8XGkjG8iOAkhjNLtbdwOg%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3864 | iexplore.exe | 13.107.136.9:443 | jstusa-my.sharepoint.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3864 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
3864 | iexplore.exe | 67.27.158.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | malicious |
3256 | iexplore.exe | 23.36.162.73:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
3256 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
3256 | iexplore.exe | 13.107.136.9:443 | jstusa-my.sharepoint.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3864 | iexplore.exe | 23.35.237.204:443 | shell.cdn.office.net | AKAMAI-AS | DE | unknown |
3864 | iexplore.exe | 188.114.98.236:80 | ocsp.msocsp.com | CLOUDFLARENET | NL | whitelisted |
— | — | 23.36.163.230:443 | res-1.cdn.office.net | Akamai International B.V. | DE | suspicious |
3864 | iexplore.exe | 40.126.32.76:443 | login.microsoftonline.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jstusa-my.sharepoint.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
shell.cdn.office.net |
| whitelisted |
ocsp.msocsp.com |
| whitelisted |
res-1.cdn.office.net |
| whitelisted |
res-2.cdn.office.net |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3864 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3864 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3864 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3864 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3864 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3864 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3864 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3864 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3864 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
Process | Message |
|---|---|
EasyConnectInstaller (1).exe | [EasyConnectInstallWrapper] [ExecCommand] ExecCommand "C:\Users\admin\AppData\Roaming\EasyConnect_21459\EasyConnectInstallerRaw.exe" |
EasyConnectInstaller (1).exe | [EasyConnectInstallWrapper] [ExecCommand] CreateProcess "C:\Users\admin\AppData\Roaming\EasyConnect_21459\EasyConnectInstallerRaw.exe" failed:740 |
EasyConnectInstaller (1).exe | [EasyConnectInstallWrapper] [main] ExecCommand C:\Users\admin\AppData\Roaming\EasyConnect_21459\EasyConnectInstallerRaw.exe failed Exit |
EasyConnectInstaller (1).exe | [EasyConnectInstallWrapper] [DeleteTempFilePath] RemoveDirectoryA szFilePath C:\Users\admin\AppData\Roaming\EasyConnect_21459 failed:145 |
EasyConnectInstaller (1).exe | [EasyConnectInstallWrapper] [ExecCommand] ExecCommand "C:\Users\admin\AppData\Roaming\EasyConnect_21479\EasyConnectInstallerRaw.exe" |
EasyConnectInstallerRaw.exe | In UninstallAllSessionControls |
EasyConnectInstallerRaw.exe | open registry(SOFTWARE\Sangfor\SSL\VPN\Sessions) failed, errcode = 2 |
EasyConnectInstallerRaw.exe | Out UninstallAllSessionControls |
EasyConnectInstallerRaw.exe | open registry(SOFTWARE\Sangfor\SSL\VPN\Sessions\IDTable) failed, errcode = 2 |
EasyConnectInstallerRaw.exe | open registry(SOFTWARE\Sangfor\SSL\SangforCSClient) failed, errcode = 2 |