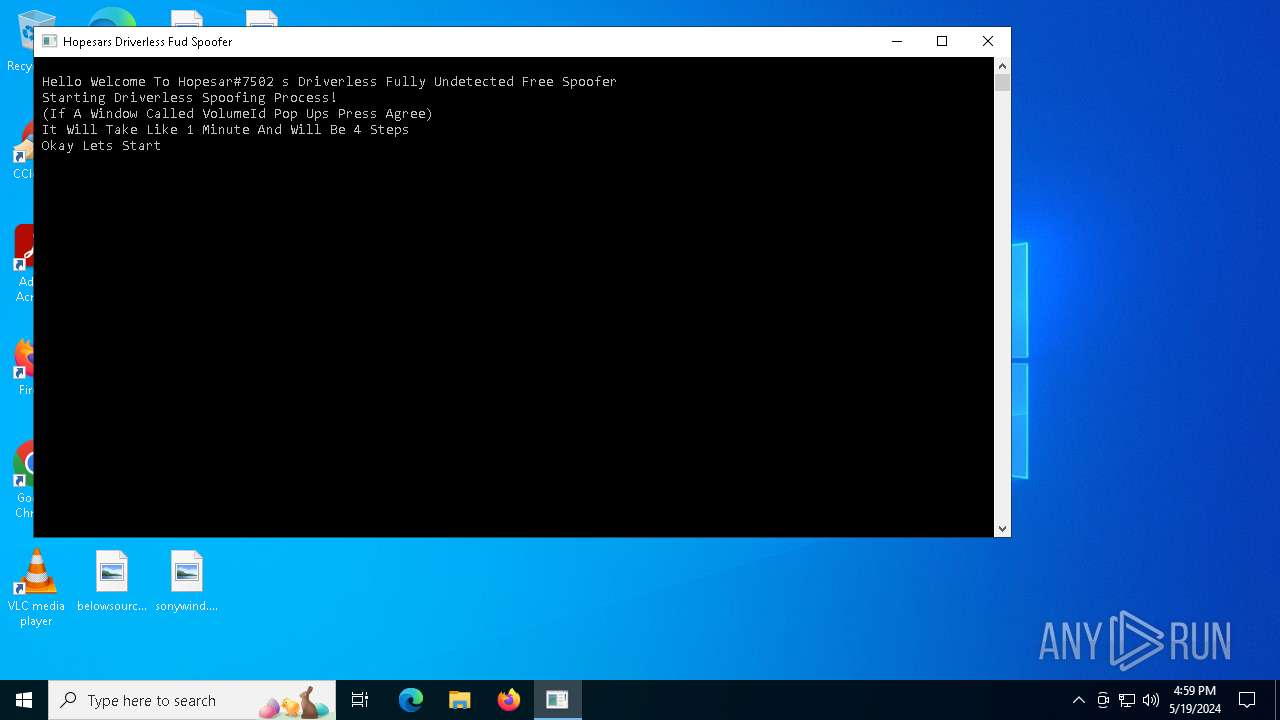
| File name: | ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe |
| Full analysis: | https://app.any.run/tasks/245db680-2a0b-420d-99ba-b881e7a33a3a |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2024, 16:59:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | BB9E44C4F1E985399723FB6EE3BDF99E |
| SHA1: | 8ACA80796EA6D39FCD2960653A4E1317AFC55D02 |
| SHA256: | CE6F2518C4ACAC57D81C8E44F4AADC6AB6DB69C01811C3DFCF076C29182D4B0C |
| SSDEEP: | 98304:NwAfdSzYERkRpLqrOlhAPK9amZrKCQjcXw7ChAHGRMZHZFhVBSxNVg3CpDhUJpxg:FaVAsBEx9Xl |
MALICIOUS
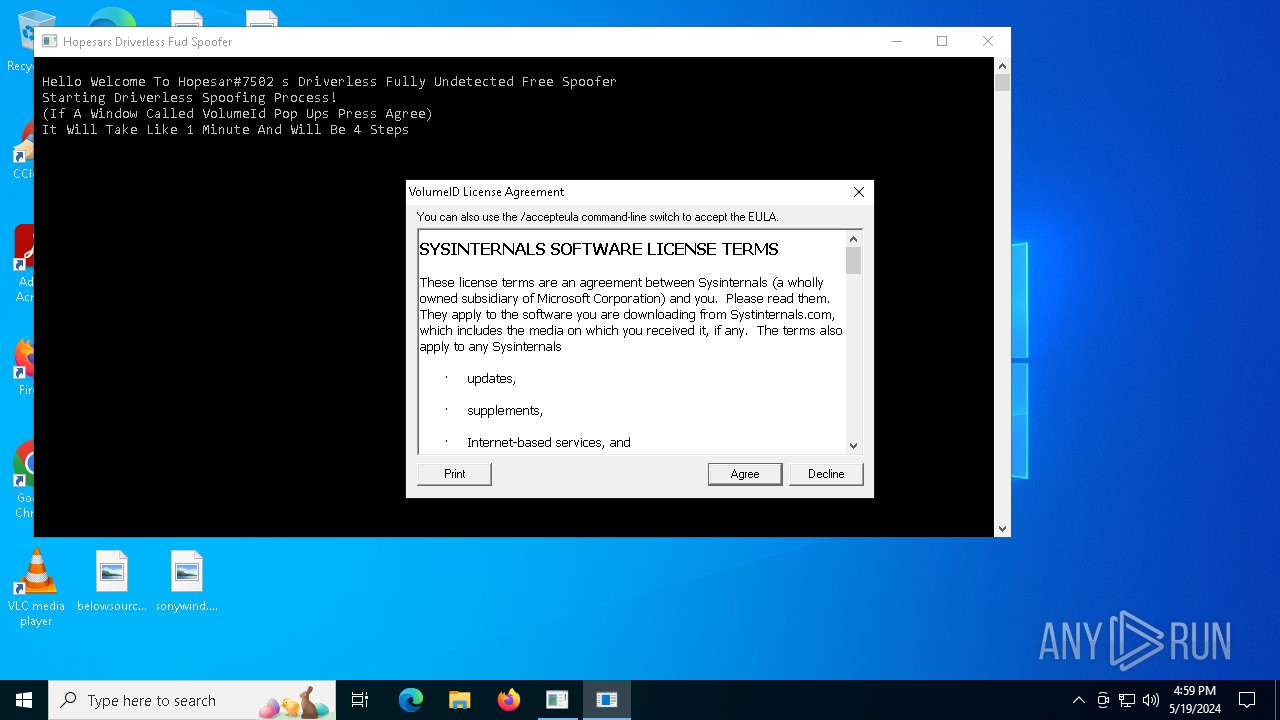
Drops the executable file immediately after the start
- powershell.exe (PID: 6392)
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
- HpsrSpoof.exe (PID: 6896)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
- conhost_sft.exe (PID: 6456)
Adds path to the Windows Defender exclusion list
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
SUSPICIOUS
Reads the date of Windows installation
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
- HpsrSpoof.exe (PID: 6896)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
Base64-obfuscated command line is found
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
Starts POWERSHELL.EXE for commands execution
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
Reads security settings of Internet Explorer
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
- HpsrSpoof.exe (PID: 6896)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
BASE64 encoded PowerShell command has been detected
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
Executable content was dropped or overwritten
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
- HpsrSpoof.exe (PID: 6896)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
- conhost_sft.exe (PID: 6456)
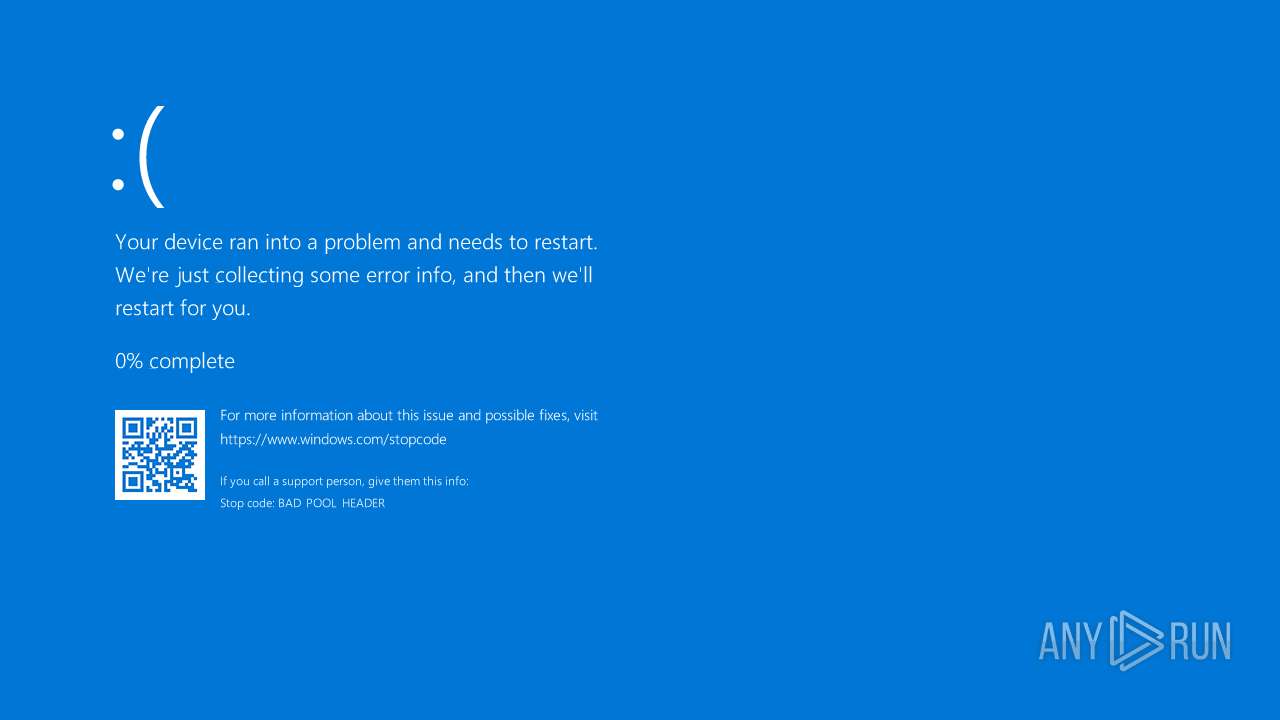
Drops a system driver (possible attempt to evade defenses)
- HpsrSpoof.exe (PID: 6896)
Executed via WMI
- schtasks.exe (PID: 4920)
- schtasks.exe (PID: 2684)
- schtasks.exe (PID: 4108)
- schtasks.exe (PID: 116)
- schtasks.exe (PID: 1108)
- schtasks.exe (PID: 5800)
- schtasks.exe (PID: 3172)
- schtasks.exe (PID: 6272)
- schtasks.exe (PID: 4360)
- schtasks.exe (PID: 3740)
- schtasks.exe (PID: 472)
- schtasks.exe (PID: 6256)
- schtasks.exe (PID: 1428)
- schtasks.exe (PID: 5012)
- schtasks.exe (PID: 4544)
Starts CMD.EXE for commands execution
- HpsrSpoof.exe (PID: 6896)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
The process creates files with name similar to system file names
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
Script adds exclusion path to Windows Defender
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 4500)
Starts application with an unusual extension
- cmd.exe (PID: 4500)
Executing commands from a ".bat" file
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
- HpsrSpoof.exe (PID: 6896)
Read disk information to detect sandboxing environments
- DevManView.exe (PID: 1848)
- DevManView.exe (PID: 2540)
- DevManView.exe (PID: 3044)
- DevManView.exe (PID: 3956)
- DevManView.exe (PID: 712)
- DevManView.exe (PID: 4108)
- DevManView.exe (PID: 3692)
- DevManView.exe (PID: 896)
- DevManView.exe (PID: 4288)
- DevManView.exe (PID: 3712)
- DevManView.exe (PID: 6240)
- DevManView.exe (PID: 6328)
- DevManView.exe (PID: 2288)
- DevManView.exe (PID: 7024)
- DevManView.exe (PID: 1016)
INFO
Checks supported languages
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
- HpsrSpoof.exe (PID: 6896)
- conhost_sft.exe (PID: 6996)
- Volumeid64.exe (PID: 7128)
- chcp.com (PID: 6784)
- DevManView.exe (PID: 2540)
- DevManView.exe (PID: 3956)
- DevManView.exe (PID: 3044)
- DevManView.exe (PID: 4108)
- DevManView.exe (PID: 896)
- DevManView.exe (PID: 4288)
- DevManView.exe (PID: 1848)
- DevManView.exe (PID: 3712)
- DevManView.exe (PID: 3692)
- DevManView.exe (PID: 6240)
- DevManView.exe (PID: 6328)
- DevManView.exe (PID: 7024)
- DevManView.exe (PID: 2288)
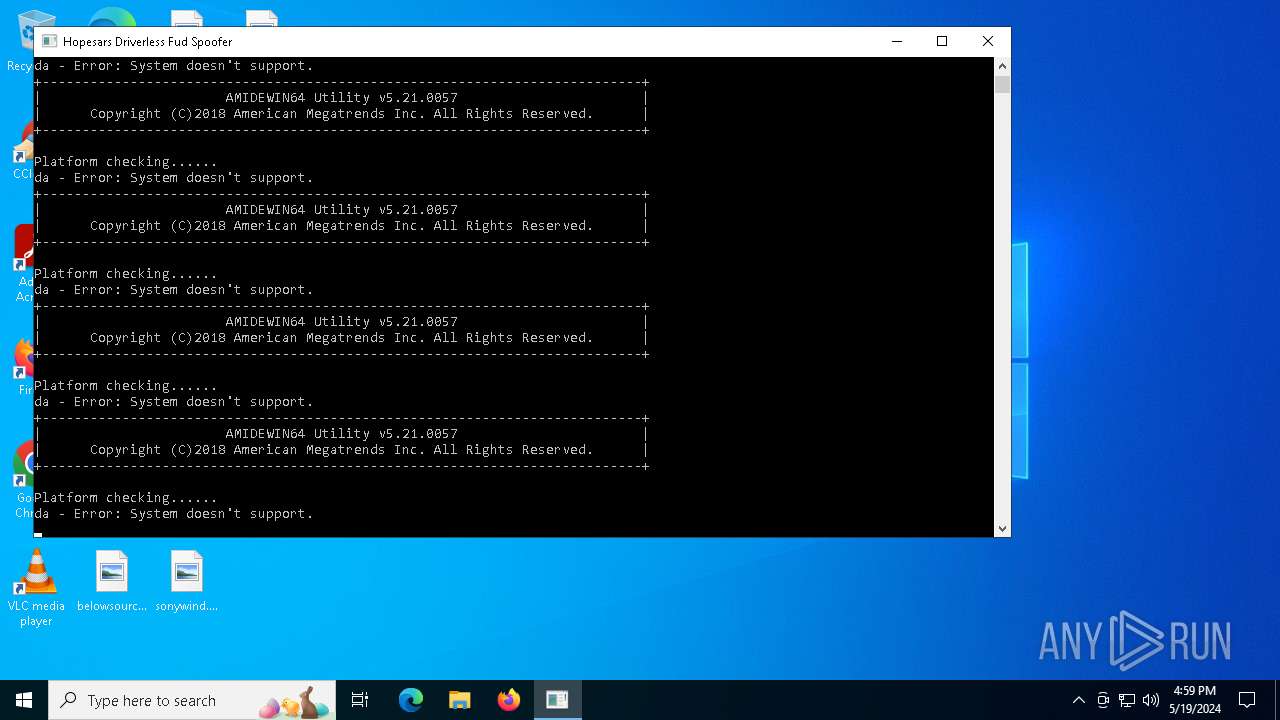
- AMIDEWINx64.exe (PID: 7064)
- AMIDEWINx64.exe (PID: 4432)
- AMIDEWINx64.exe (PID: 6300)
- AMIDEWINx64.exe (PID: 6200)
- DevManView.exe (PID: 1016)
- AMIDEWINx64.exe (PID: 6748)
- AMIDEWINx64.exe (PID: 4960)
- AMIDEWINx64.exe (PID: 5996)
- AMIDEWINx64.exe (PID: 6808)
- AMIDEWINx64.exe (PID: 6288)
- conhost_sft.exe (PID: 6456)
- DevManView.exe (PID: 712)
- AMIDEWINx64.exe (PID: 428)
- AMIDEWINx64.exe (PID: 5852)
- AMIDEWINx64.exe (PID: 4988)
- AMIDEWINx64.exe (PID: 6848)
- AMIDEWINx64.exe (PID: 6872)
- AMIDEWINx64.exe (PID: 6632)
- AMIDEWINx64.exe (PID: 4384)
- AMIDEWINx64.exe (PID: 1720)
- AMIDEWINx64.exe (PID: 3496)
- AMIDEWINx64.exe (PID: 6184)
Reads the computer name
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
- HpsrSpoof.exe (PID: 6896)
- Volumeid64.exe (PID: 7128)
- DevManView.exe (PID: 2540)
- DevManView.exe (PID: 3956)
- DevManView.exe (PID: 3044)
- DevManView.exe (PID: 1848)
- DevManView.exe (PID: 712)
- DevManView.exe (PID: 896)
- DevManView.exe (PID: 4108)
- DevManView.exe (PID: 4288)
- DevManView.exe (PID: 3692)
- DevManView.exe (PID: 6328)
- DevManView.exe (PID: 3712)
- DevManView.exe (PID: 6240)
- DevManView.exe (PID: 7024)
- DevManView.exe (PID: 2288)
- DevManView.exe (PID: 1016)
- AMIDEWINx64.exe (PID: 6200)
- AMIDEWINx64.exe (PID: 4432)
- AMIDEWINx64.exe (PID: 6300)
- AMIDEWINx64.exe (PID: 7064)
- AMIDEWINx64.exe (PID: 4960)
- AMIDEWINx64.exe (PID: 6748)
- AMIDEWINx64.exe (PID: 5996)
- AMIDEWINx64.exe (PID: 6808)
- AMIDEWINx64.exe (PID: 6288)
- conhost_sft.exe (PID: 6456)
- AMIDEWINx64.exe (PID: 428)
- AMIDEWINx64.exe (PID: 4988)
- AMIDEWINx64.exe (PID: 6632)
- AMIDEWINx64.exe (PID: 5852)
- AMIDEWINx64.exe (PID: 6848)
- AMIDEWINx64.exe (PID: 4384)
- AMIDEWINx64.exe (PID: 6872)
- AMIDEWINx64.exe (PID: 1720)
- AMIDEWINx64.exe (PID: 3496)
- AMIDEWINx64.exe (PID: 6184)
Process checks computer location settings
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
- HpsrSpoof.exe (PID: 6896)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
Creates files or folders in the user directory
- ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe (PID: 6652)
Creates files in the program directory
- HpsrSpoof.exe (PID: 6896)
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
Reads the machine GUID from the registry
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
- conhost_sft.exe (PID: 6456)
Reads Environment values
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
- Volumeid64.exe (PID: 7128)
- conhost_sft.exe (PID: 6456)
Reads product name
- Volumeid64.exe (PID: 7128)
Create files in a temporary directory
- sp_componentbrowserFontDriverPerf.exe (PID: 6956)
NirSoft software is detected
- DevManView.exe (PID: 2540)
- DevManView.exe (PID: 3956)
- DevManView.exe (PID: 712)
- DevManView.exe (PID: 3044)
- DevManView.exe (PID: 1848)
- DevManView.exe (PID: 4108)
- DevManView.exe (PID: 4288)
- DevManView.exe (PID: 3692)
- DevManView.exe (PID: 896)
- DevManView.exe (PID: 6328)
- DevManView.exe (PID: 3712)
- DevManView.exe (PID: 7024)
- DevManView.exe (PID: 2288)
- DevManView.exe (PID: 1016)
- DevManView.exe (PID: 6240)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6204)
- powershell.exe (PID: 6284)
- powershell.exe (PID: 6224)
- powershell.exe (PID: 6816)
- powershell.exe (PID: 6324)
- powershell.exe (PID: 6264)
Manual execution by a user
- powershell.exe (PID: 6188)
Checks proxy server information
- conhost_sft.exe (PID: 6456)
Disables trace logs
- conhost_sft.exe (PID: 6456)
Reads the software policy settings
- conhost_sft.exe (PID: 6456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 2048 |
| InitializedDataSize: | 6586368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1019700 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.0.0 |
| ProductVersionNumber: | 1.2.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileTitle: | HWID Spoofer |
| FileDescription: | - |
| FileVersion: | 1,2,0,0 |
| LegalCopyright: | - |
| LegalTrademark: | - |
| ProductName: | - |
| ProductVersion: | 1,2,0,0 |
Total processes
228
Monitored processes
112
Malicious processes
7
Suspicious processes
15
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | schtasks.exe /create /tn "IdleI" /sc MINUTE /mo 5 /tr "'C:\found.000\dir0001.chk\Idle.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 364 | "C:\Windows\System32\cmd.exe" /C C:\ProgramData\Microsoft\Windows\AMIDEWINx64.exe /SK 5%RANDOM%HP-TRGT%RANDOM%SL | C:\Windows\System32\cmd.exe | — | HpsrSpoof.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 16 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 428 | C:\ProgramData\Microsoft\Windows\AMIDEWINx64.exe /SK 54570HP-TRGT20085SL | C:\ProgramData\Microsoft\Windows\AMIDEWINx64.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 218 Modules
| |||||||||||||||
| 472 | schtasks.exe /create /tn "wininitw" /sc MINUTE /mo 8 /tr "'C:\Program Files\MSBuild\Microsoft\Windows Workflow Foundation\v3.0\wininit.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 712 | C:\\ProgramData\\Microsoft\\Windows\\DevManView.exe /uninstall "C:\" | C:\ProgramData\Microsoft\Windows\DevManView.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: DevManView Exit code: 0 Version: 1.75 Modules
| |||||||||||||||
| 896 | C:\\ProgramData\\Microsoft\\Windows\\DevManView.exe /uninstall "G:\" | C:\ProgramData\Microsoft\Windows\DevManView.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: DevManView Exit code: 0 Version: 1.75 Modules
| |||||||||||||||
| 1016 | C:\\ProgramData\\Microsoft\\Windows\\DevManView.exe /uninstall "WAN Miniport*" /use_wildcard"" | C:\ProgramData\Microsoft\Windows\DevManView.exe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: DevManView Exit code: 0 Version: 1.75 Modules
| |||||||||||||||
| 1108 | schtasks.exe /create /tn "explorere" /sc MINUTE /mo 14 /tr "'C:\found.000\dir0000.chk\explorer.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
122 148
Read events
122 089
Write events
59
Delete events
0
Modification events
| (PID) Process: | (6392) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6392) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6392) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6392) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6652) ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6652) ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6652) ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6652) ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6896) HpsrSpoof.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6896) HpsrSpoof.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
30
Suspicious files
3
Text files
29
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6392 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Z4FHL5C9JZY1R8MTGK6V.temp | — | |
MD5:— | SHA256:— | |||
| 6392 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:9EF875746A314208B799C7FB8790310D | SHA256:E40EDF18CBAF8F1BE952E1394649BC557FB6ABB6F4FF056E5AA210F7E67C1EFD | |||
| 6392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jcskg1xs.qdc.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6392 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1138ef.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6652 | ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe | C:\Users\admin\AppData\Roaming\HpsrSpoof.exe | executable | |
MD5:DD1313842898FFAF72D79DF643637DED | SHA256:81B27A565D2EB4701C404E03398A4BCA48480E592460121BF8EC62C5F4B061DF | |||
| 6392 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:0BE3A3FE34F6F5591E221620F48A867F | SHA256:90C86780A9A97A5E35C76C84A247ACCAEEB92472C77926DF1E2082B8D52C6389 | |||
| 6652 | ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe | C:\Users\admin\AppData\Roaming\sp_componentbrowserFontDriverPerf.exe | executable | |
MD5:547C9F5CA62183622587BD980B3487B0 | SHA256:FC553A09F397D4D405362AA8AEEEDE9487F16D12C9726F3EFD1D15CF3B11244A | |||
| 6652 | ce6f2518c4acac57d81c8e44f4aadc6ab6db69c01811c3dfcf076c29182d4b0c.exe | C:\Users\admin\AppData\Roaming\conhost_sft.exe | executable | |
MD5:5FA1594356EE7555D3CC6B2E2F3E7A93 | SHA256:DB833E7A4F16F5278813C3B17EC06175D5D5E706562813C478A3FEE7D4C3CAFD | |||
| 6896 | HpsrSpoof.exe | C:\ProgramData\Microsoft\Windows\amide.sys | executable | |
MD5:785045F8B25CD2E937DDC6B09DEBE01A | SHA256:37073E42FFA0322500F90CD7E3C8D02C4CDD695D31C77E81560ABEC20BFB68BA | |||
| 6896 | HpsrSpoof.exe | C:\ProgramData\Microsoft\Windows\Volumeid64.exe | executable | |
MD5:81A45F1A91448313B76D2E6D5308AA7A | SHA256:FB0D02EA26BB1E5DF5A07147931CAF1AE3D7D1D9B4D83F168B678E7F3A1C0ECD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
22
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.20.71.230:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5612 | svchost.exe | GET | 200 | 2.20.71.230:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5228 | RUXIMICS.exe | GET | 200 | 2.20.71.230:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5612 | svchost.exe | GET | 200 | 23.49.245.164:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5228 | RUXIMICS.exe | GET | 200 | 23.49.245.164:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.49.245.164:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 404 | 104.20.4.235:443 | https://pastebin.com/raw/qivZa09c | unknown | html | 687 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
5612 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5228 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5612 | svchost.exe | 2.20.71.230:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5228 | RUXIMICS.exe | 2.20.71.230:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5140 | MoUsoCoreWorker.exe | 2.20.71.230:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5612 | svchost.exe | 23.49.245.164:80 | www.microsoft.com | AKAMAI-AS | PT | unknown |
5228 | RUXIMICS.exe | 23.49.245.164:80 | www.microsoft.com | AKAMAI-AS | PT | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
pastebin.com |
| shared |