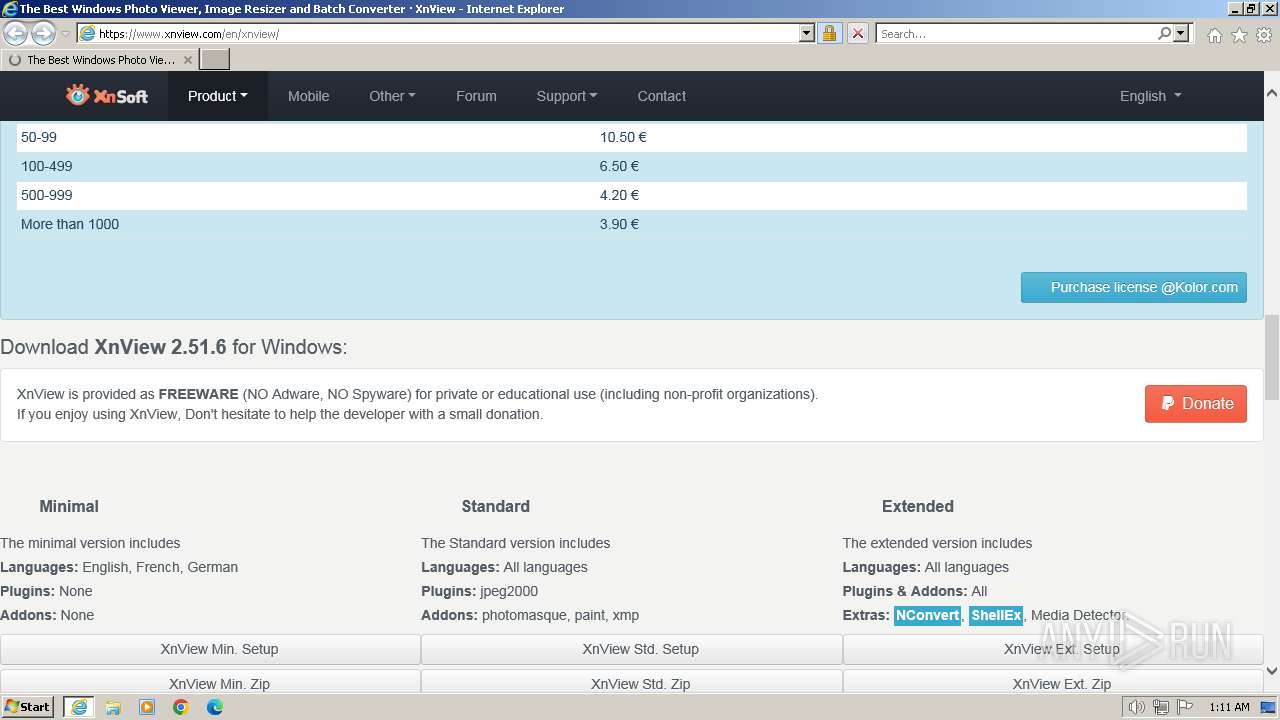
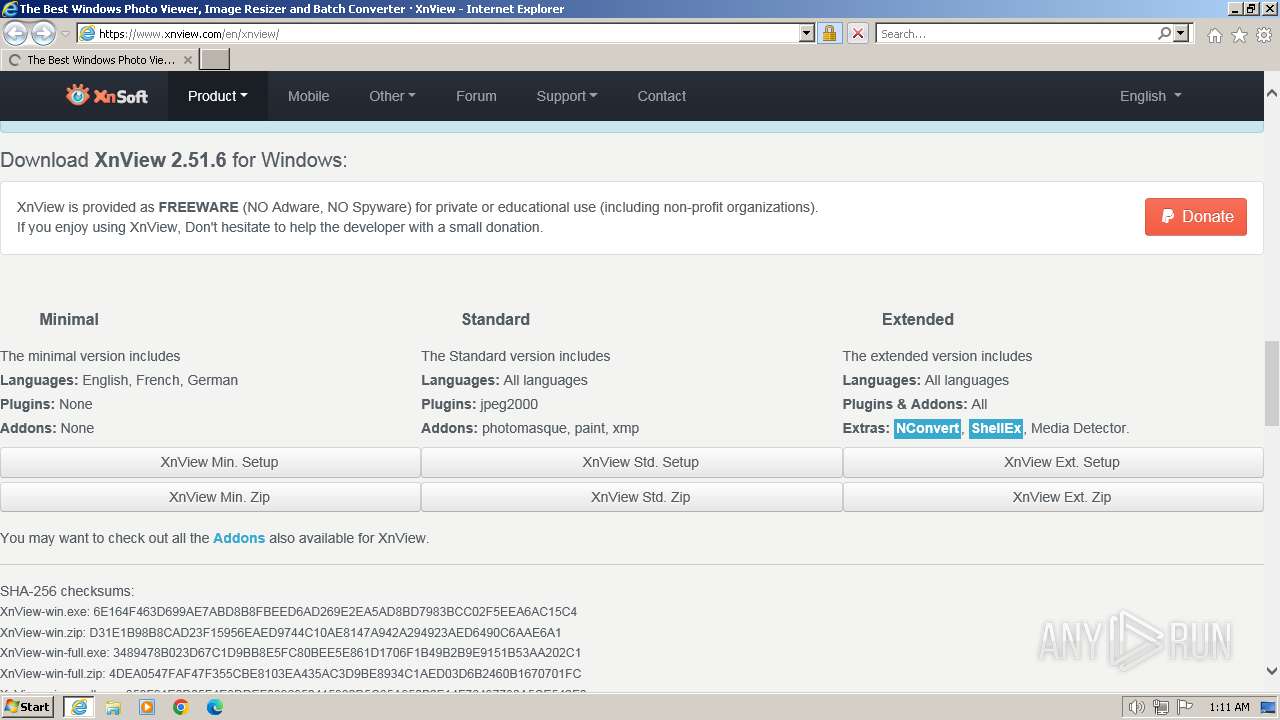
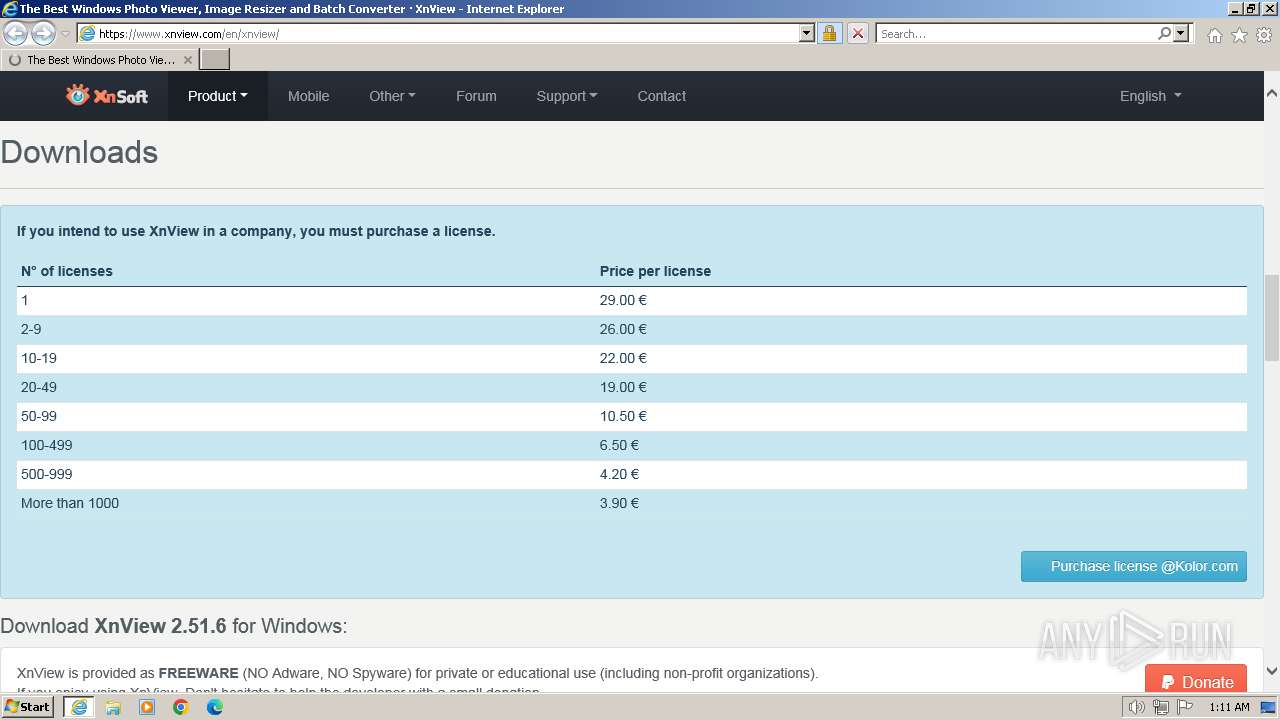
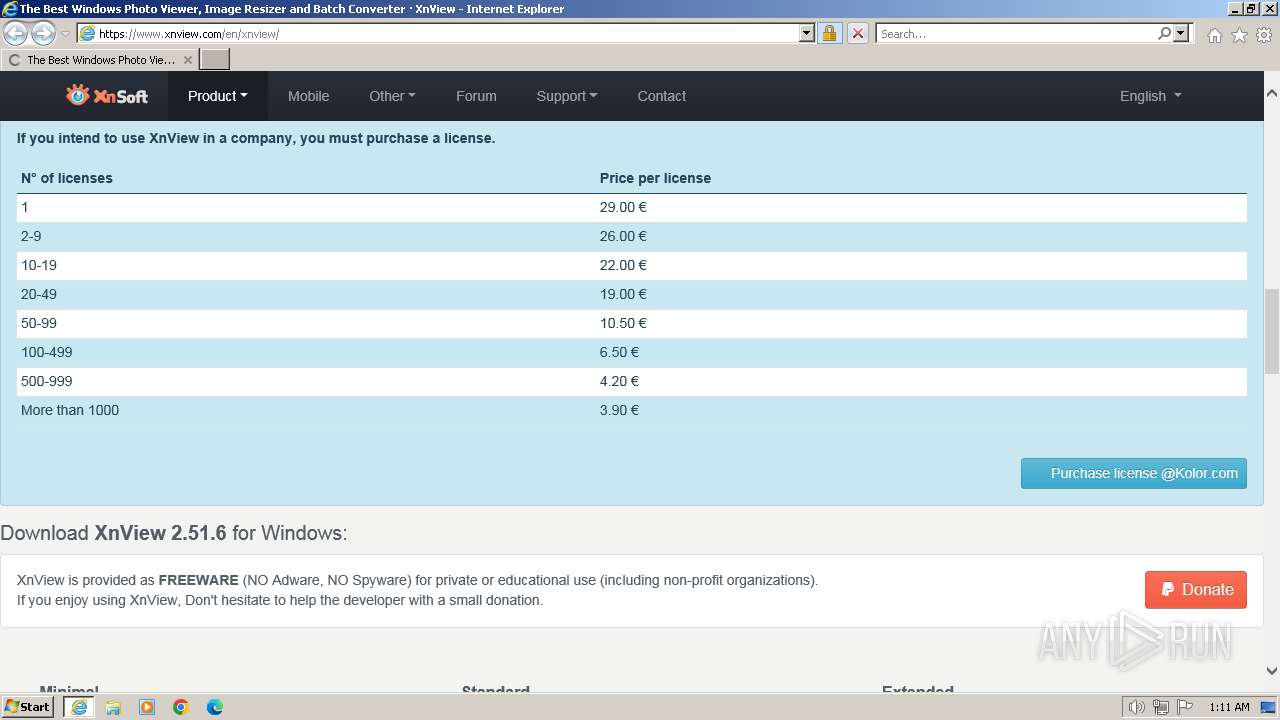
| URL: | https://www.xnview.com/en/xnview/ |
| Full analysis: | https://app.any.run/tasks/fc67caa6-43dc-4e8a-89d5-baf4312bd7c4 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2024, 00:11:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9B5E6496012A765E898FF154355B48D4 |
| SHA1: | D960D4B5D0DC764BD5A5611249A38DE147539010 |
| SHA256: | CE5F72D15C8867ACBB2D9724A5329E3953E53571F0EADBBED5C873A31D130440 |
| SSDEEP: | 3:N8DSLKyK1dLTD:2OL6dL3 |
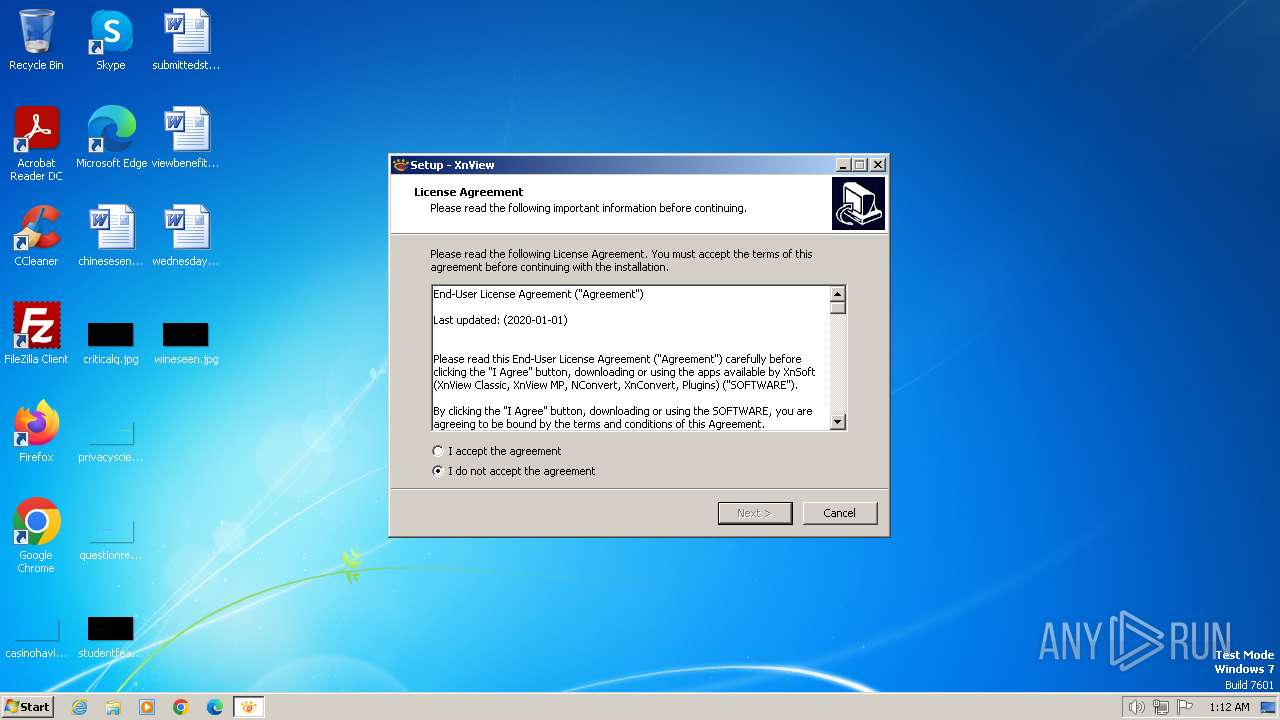
MALICIOUS
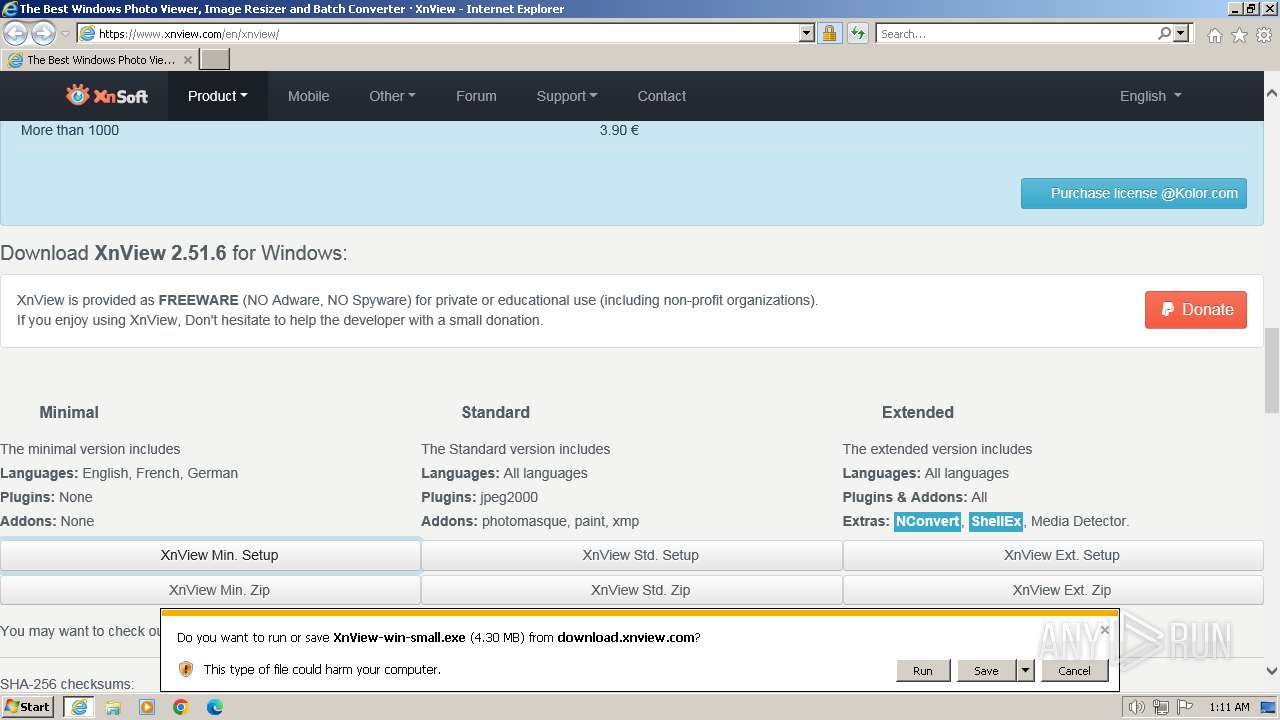
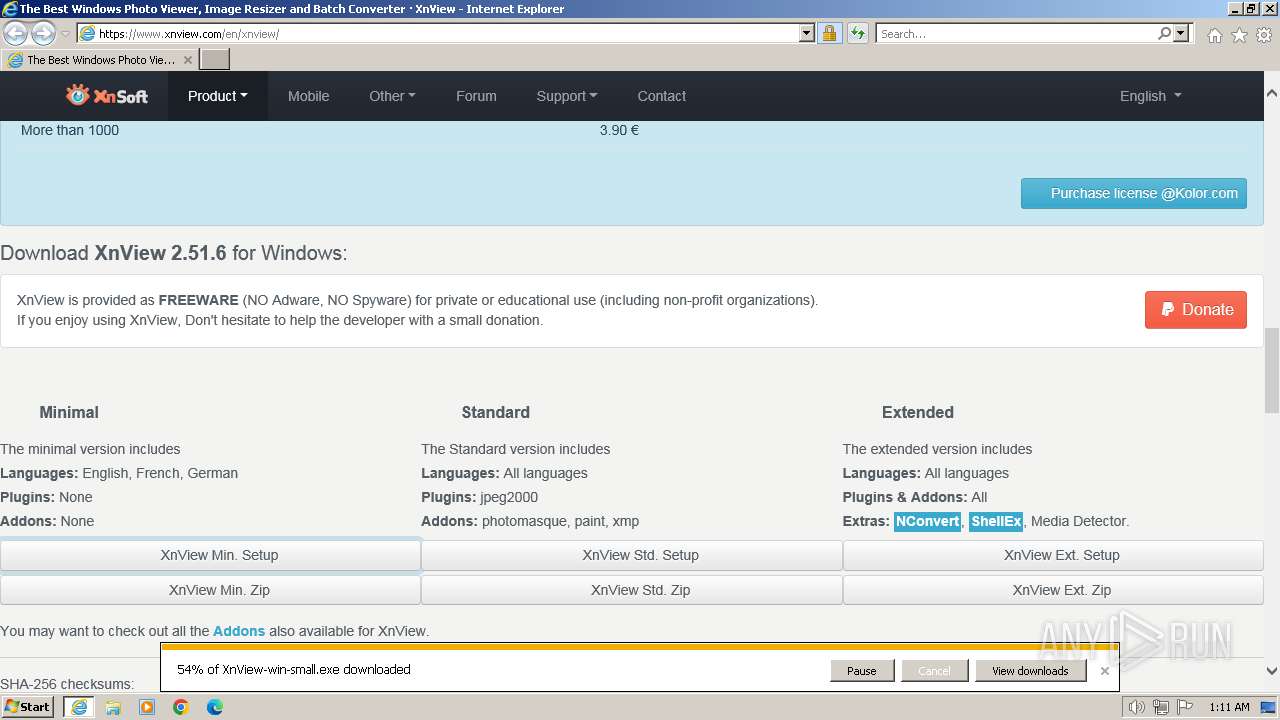
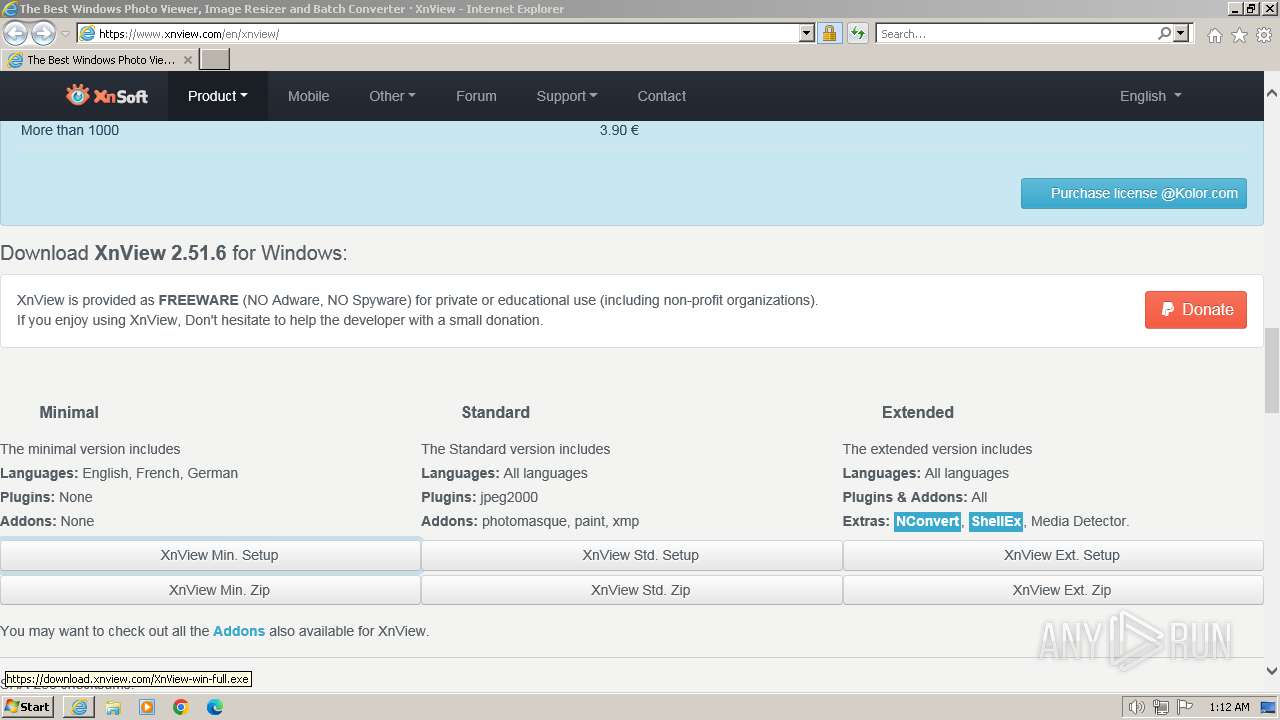
Drops the executable file immediately after the start
- XnView-win-small.exe (PID: 1556)
- XnView-win-small.tmp (PID: 2244)
- XnView-win-small.exe (PID: 2856)
SUSPICIOUS
Executable content was dropped or overwritten
- XnView-win-small.exe (PID: 1556)
- XnView-win-small.exe (PID: 2856)
- XnView-win-small.tmp (PID: 2244)
Process drops legitimate windows executable
- XnView-win-small.tmp (PID: 2244)
Reads the Windows owner or organization settings
- XnView-win-small.tmp (PID: 2244)
The process drops C-runtime libraries
- XnView-win-small.tmp (PID: 2244)
Creates file in the systems drive root
- xnview.exe (PID: 3944)
Non-standard symbols in registry
- XnView-win-small.tmp (PID: 2244)
Reads the Internet Settings
- xnview.exe (PID: 3944)
Reads security settings of Internet Explorer
- xnview.exe (PID: 3944)
Checks Windows Trust Settings
- xnview.exe (PID: 3944)
Reads settings of System Certificates
- xnview.exe (PID: 3944)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 3384)
- iexplore.exe (PID: 3768)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3768)
- iexplore.exe (PID: 3384)
Application launched itself
- iexplore.exe (PID: 3768)
The process uses the downloaded file
- iexplore.exe (PID: 3768)
Checks supported languages
- XnView-win-small.exe (PID: 1556)
- XnView-win-small.tmp (PID: 2888)
- XnView-win-small.exe (PID: 2856)
- XnView-win-small.tmp (PID: 2244)
- xnview.exe (PID: 3944)
- wmpnscfg.exe (PID: 1348)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3768)
Create files in a temporary directory
- XnView-win-small.exe (PID: 1556)
- XnView-win-small.exe (PID: 2856)
- XnView-win-small.tmp (PID: 2244)
Reads the computer name
- XnView-win-small.tmp (PID: 2888)
- XnView-win-small.tmp (PID: 2244)
- xnview.exe (PID: 3944)
- wmpnscfg.exe (PID: 1348)
Creates files or folders in the user directory
- xnview.exe (PID: 3944)
- XnView-win-small.tmp (PID: 2244)
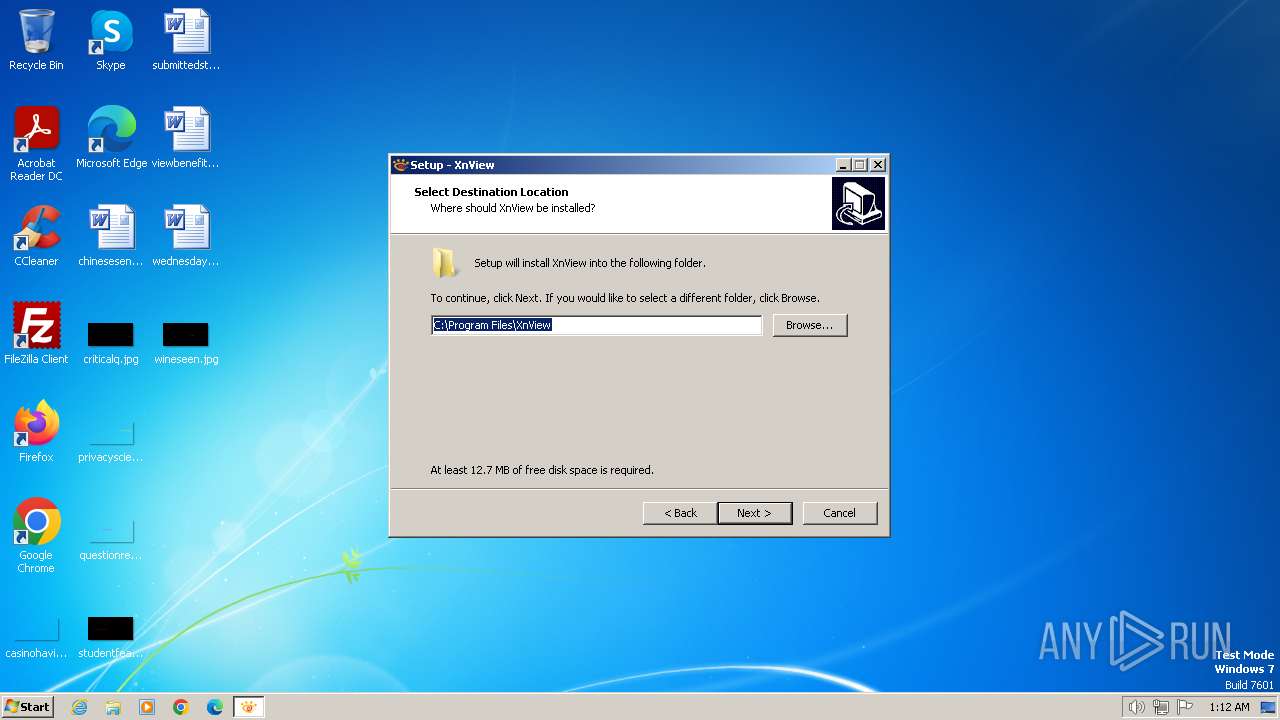
Creates files in the program directory
- XnView-win-small.tmp (PID: 2244)
Creates a software uninstall entry
- XnView-win-small.tmp (PID: 2244)
Reads the machine GUID from the registry
- xnview.exe (PID: 3944)
Checks proxy server information
- xnview.exe (PID: 3944)
Reads the software policy settings
- xnview.exe (PID: 3944)
Manual execution by a user
- wmpnscfg.exe (PID: 1348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
8
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
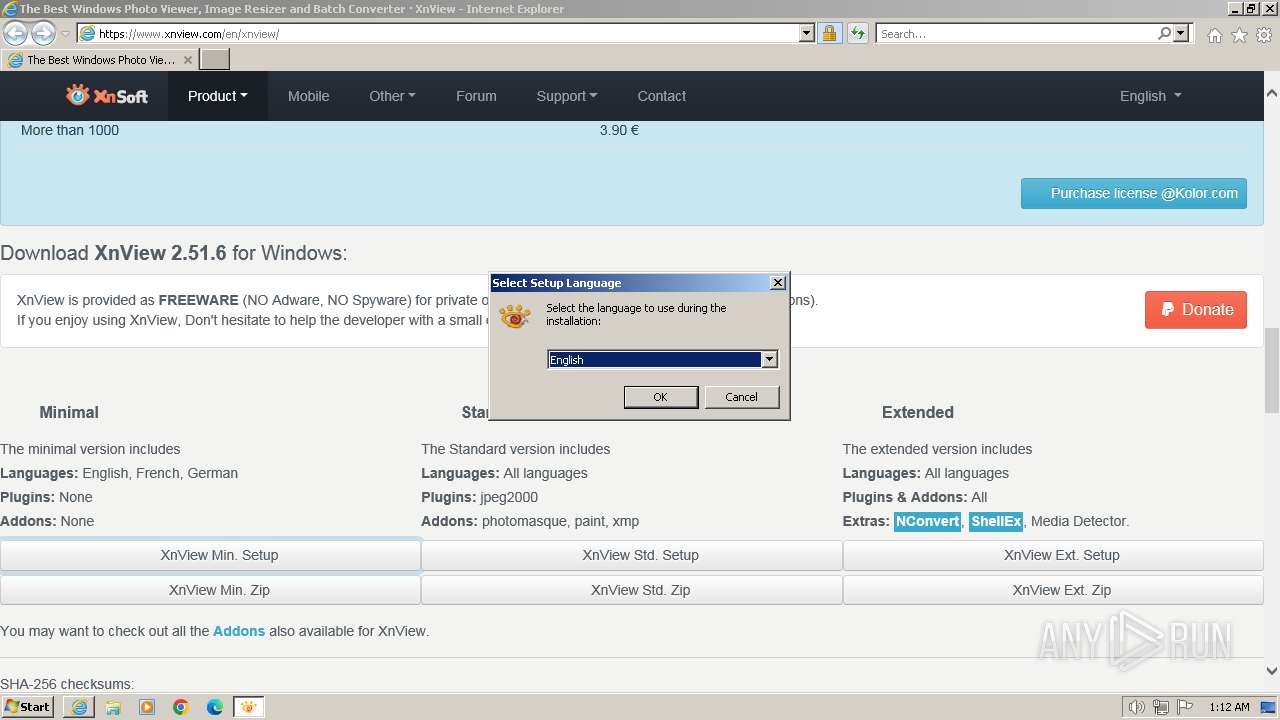
| 1556 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\XnView-win-small.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\XnView-win-small.exe | iexplore.exe | ||||||||||||
User: admin Company: Gougelet Pierre-e Integrity Level: MEDIUM Description: XnView Setup Exit code: 0 Version: 2.51.6 Modules
| |||||||||||||||
| 2244 | "C:\Users\admin\AppData\Local\Temp\is-Q6JPM.tmp\XnView-win-small.tmp" /SL5="$150190,4217442,79360,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\XnView-win-small.exe" /SPAWNWND=$1A0164 /NOTIFYWND=$E01CA | C:\Users\admin\AppData\Local\Temp\is-Q6JPM.tmp\XnView-win-small.tmp | XnView-win-small.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2856 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\XnView-win-small.exe" /SPAWNWND=$1A0164 /NOTIFYWND=$E01CA | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\XnView-win-small.exe | XnView-win-small.tmp | ||||||||||||
User: admin Company: Gougelet Pierre-e Integrity Level: HIGH Description: XnView Setup Exit code: 0 Version: 2.51.6 Modules
| |||||||||||||||
| 2888 | "C:\Users\admin\AppData\Local\Temp\is-JAAVT.tmp\XnView-win-small.tmp" /SL5="$E01CA,4217442,79360,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\XnView-win-small.exe" | C:\Users\admin\AppData\Local\Temp\is-JAAVT.tmp\XnView-win-small.tmp | — | XnView-win-small.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3384 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3768 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3768 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.xnview.com/en/xnview/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3944 | "C:\Program Files\XnView\xnview.exe" | C:\Program Files\XnView\xnview.exe | XnView-win-small.tmp | ||||||||||||
User: admin Company: XnView, http://www.xnview.com Integrity Level: MEDIUM Description: XnView Classic for Windows Version: 2.51.6 Modules
| |||||||||||||||
Total events
33 131
Read events
32 872
Write events
204
Delete events
55
Modification events
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31102226 | |||
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31102226 | |||
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3768) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
29
Suspicious files
89
Text files
334
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:A9FE3ED742394CA34B262E890015F602 | SHA256:ADB743EE1E391EF9C2BBF685FD37F2079F1482B46134521F18D5DC2C5777B057 | |||
| 3384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:FB9B156D82978722007040846A1BF404 | SHA256:854F548D238000022E8392CC506D2B6DFAD5554E7D89E387DCE472EC6CDA734B | |||
| 3384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1CB8D893D7F93B1B4318C2759A1ABCA2 | binary | |
MD5:52F554BF1C2D250F5C861BC0CB91BC62 | SHA256:271DB428C3314EC1F82448BA0C849F67662CF5CBBBB372832A8FD1EBD645302E | |||
| 3384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1CB8D893D7F93B1B4318C2759A1ABCA2 | der | |
MD5:F4A6C3950DE96667A25F321C710F5BAE | SHA256:997442D9694A6F80F94DB7004F4610F5E1A0F03EDC0613C50997B41C8653B0E6 | |||
| 3384 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\xnview[1].css | text | |
MD5:289F0E12C379F408BA76C7F4C7C43196 | SHA256:859A116F3252102903775C3B8081A5720A29B4F581217A7EAB5BAB9E9FE58597 | |||
| 3384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:1606FD438919CD2E511B2809DC86FDBF | SHA256:5641D740A89D9A632E0932C2361C35032BD6847C148732E2BC76392879986B4E | |||
| 3384 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:88E02173658DA1B28384047F7E788846 | SHA256:B6318633B9CAB24E8C4CA242B8FFD22E7B0C53D8B07A51F900D05A6CE3655274 | |||
| 3384 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\xnview-win-01[1].jpg | image | |
MD5:AD3C63C6C6280BA9EF70AE3511F6D94C | SHA256:00E48FC3C4B5B2BBC46D4B2D0F376A899023A2BFE878B79DBE0A672CBB4937F1 | |||
| 3384 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\xnview-win-03[1].jpg | image | |
MD5:837CF33FCB07E8063B9F72510DB4D6B8 | SHA256:C56DFC9CF86C9D029B5A224A33ADF4CB55900BD3B8A22990A21501CA896FEE58 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
44
DNS requests
21
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1080 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1c4d1b50b1a217ca | unknown | — | — | unknown |
3384 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5165cee59c1b8c9a | unknown | — | — | unknown |
3384 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?378b9923119ef80e | unknown | — | — | unknown |
3384 | iexplore.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
3384 | iexplore.exe | GET | 200 | 2.16.202.121:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPXXANcwmObdV1rKAzdQHNmyw%3D%3D | unknown | — | — | unknown |
3384 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | — | — | unknown |
3384 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
3384 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | — | — | unknown |
3384 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCromXb0vClRQmjvIVLThWU | unknown | — | — | unknown |
3384 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCcSoXi8aTt3gof4ejif2LL | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3384 | iexplore.exe | 178.33.105.203:443 | www.xnview.com | OVH SAS | FR | unknown |
3384 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3384 | iexplore.exe | 2.23.197.184:80 | x1.c.lencr.org | CW Vodafone Group PLC | GB | unknown |
3384 | iexplore.exe | 2.16.202.121:80 | r3.o.lencr.org | Akamai International B.V. | NL | unknown |
3384 | iexplore.exe | 172.217.23.106:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3384 | iexplore.exe | 104.16.89.20:443 | cdn.jsdelivr.net | CLOUDFLARENET | — | shared |
3384 | iexplore.exe | 142.250.184.200:443 | www.googletagmanager.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.xnview.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
fonts.googleapis.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3384 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
3384 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |