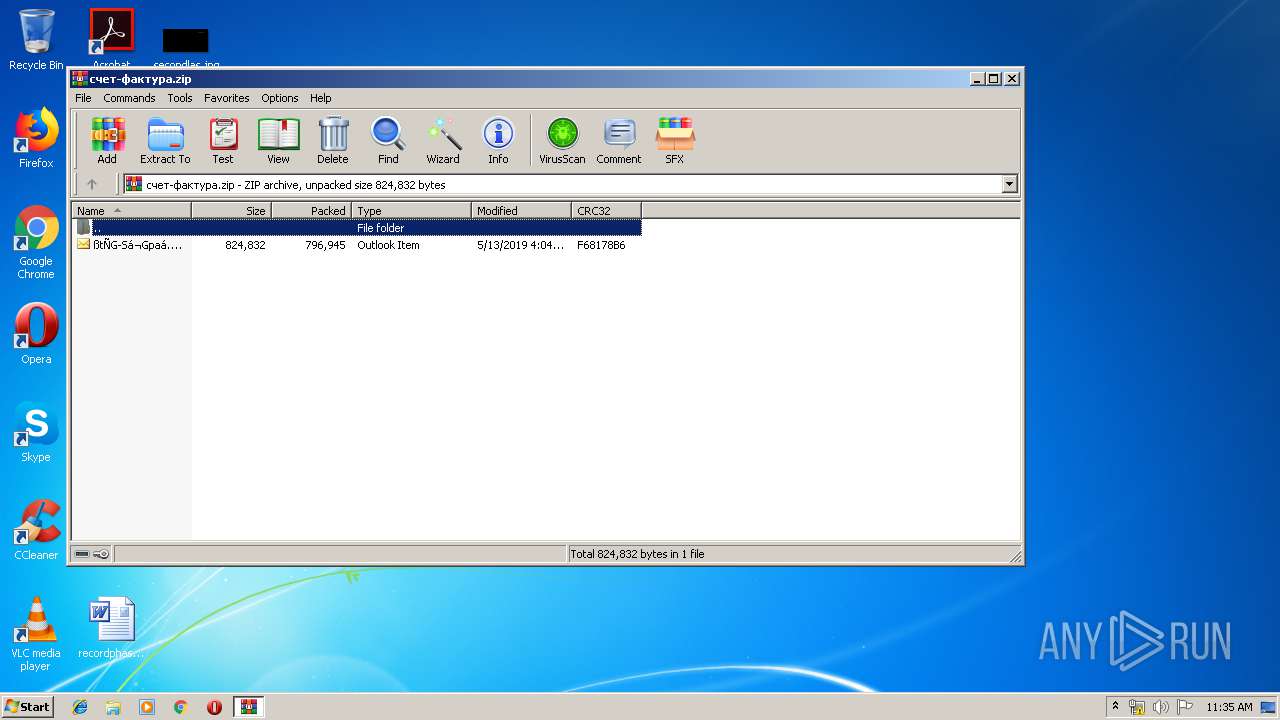
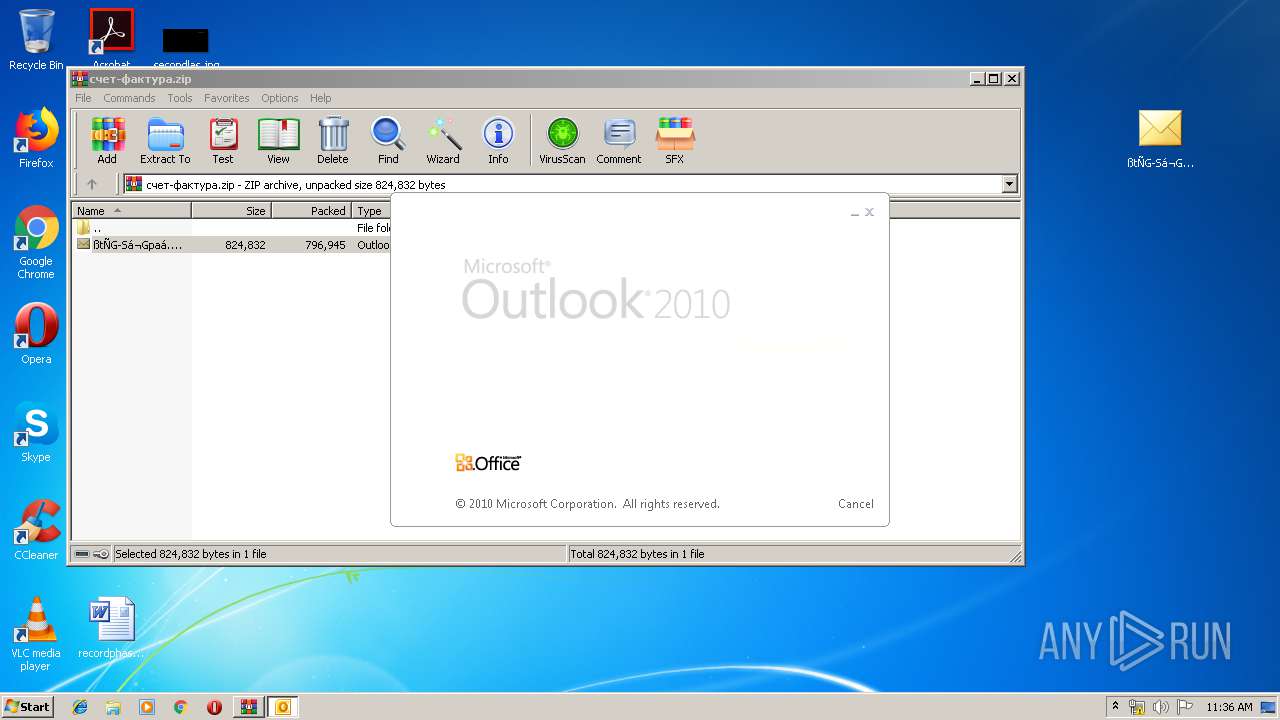
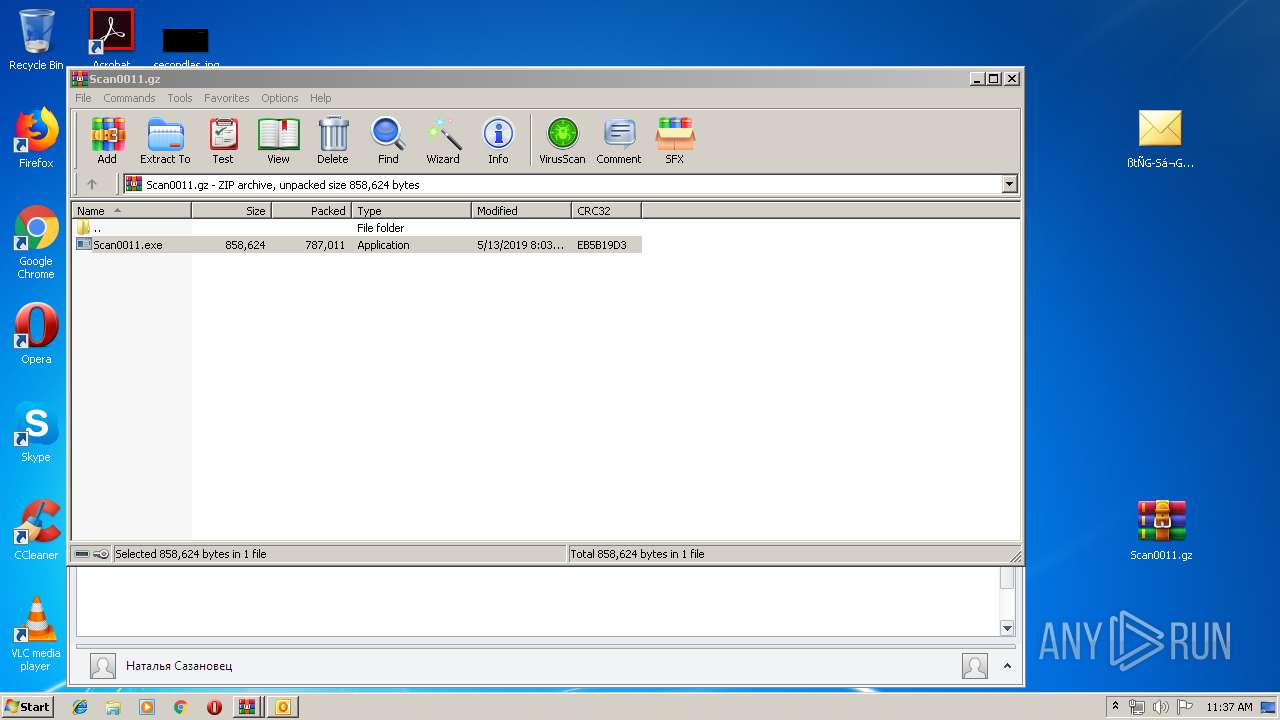
| File name: | счет-фактура.zip |
| Full analysis: | https://app.any.run/tasks/00392f48-c6ed-4623-a0d0-b009fa86d06d |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 10:35:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
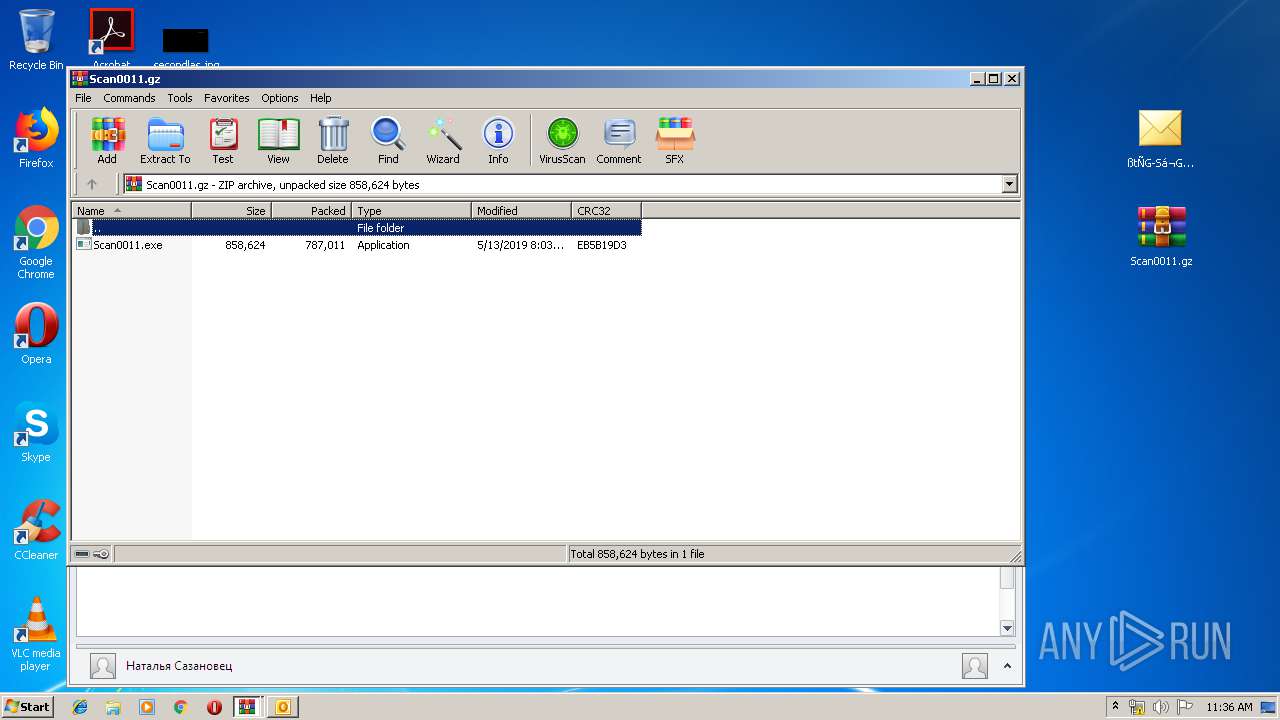
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D4488E2DD94998DED85BB1EEBACC0F4D |
| SHA1: | C3494C300128E5F6BC8C9DFA422FB58E93C1BE30 |
| SHA256: | CE4F79971942C98DEBDA949CDAEFBA7B9163D7327613041C263A193EAE060195 |
| SSDEEP: | 24576:rdgq0KKtPQSxXqwHWl1DG2UQaSPI4LjS8BA/A1E9On0xpk:rdg5KKtWyWlMnTDyKx6 |
MALICIOUS
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 3444)
- RegSvcs.exe (PID: 2524)
Application was dropped or rewritten from another process
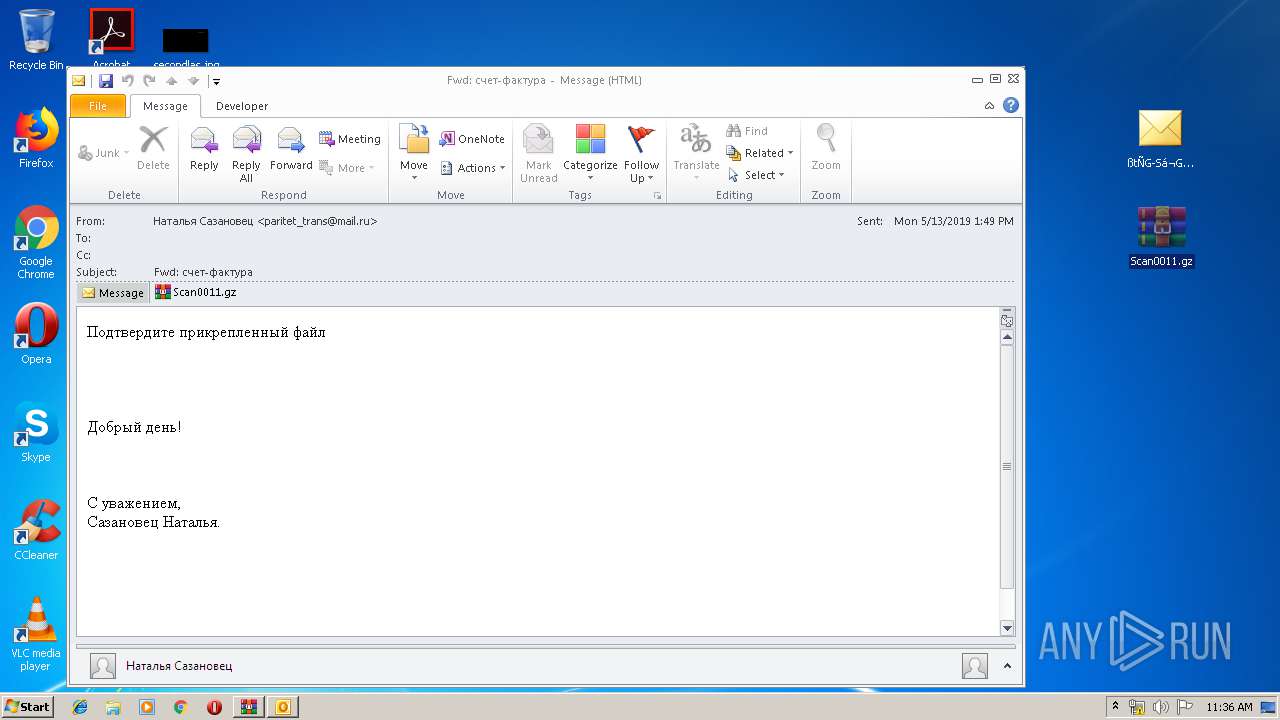
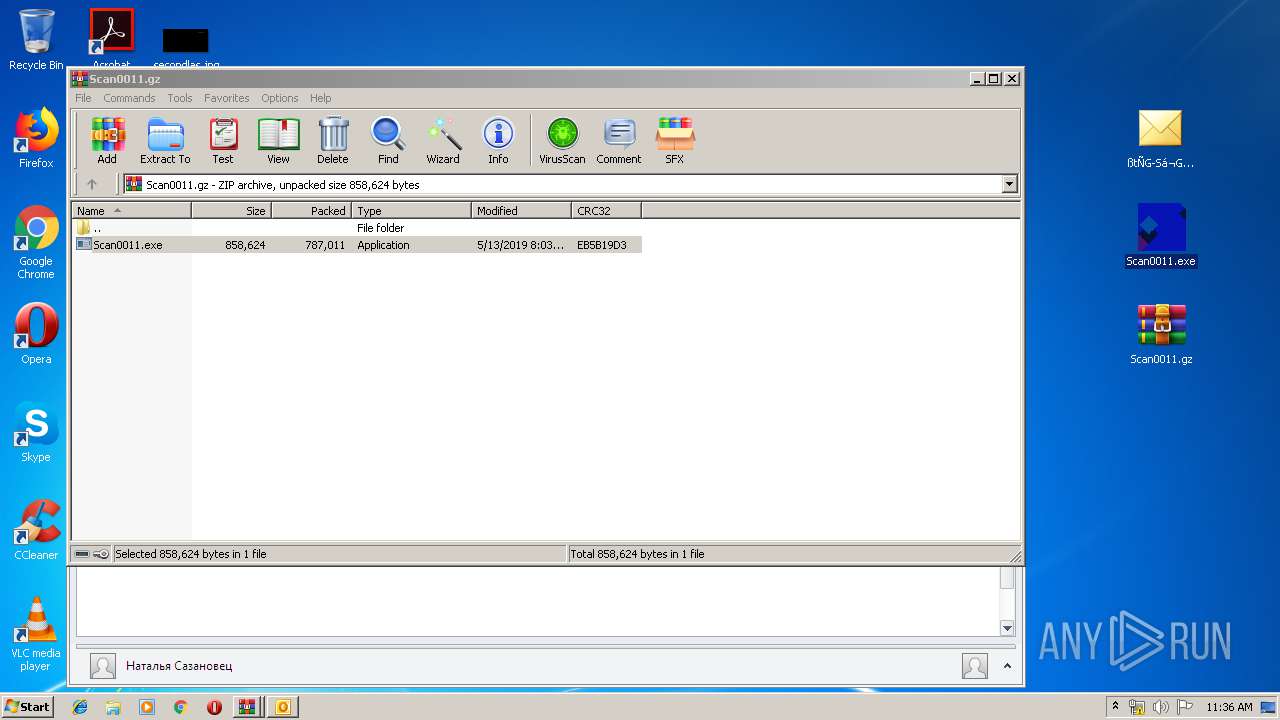
- Scan0011.exe (PID: 1560)
- Scan0011.exe (PID: 2836)
SUSPICIOUS
Reads Windows Product ID
- RegSvcs.exe (PID: 3444)
- RegSvcs.exe (PID: 2524)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3548)
- RegSvcs.exe (PID: 3444)
Reads Environment values
- RegSvcs.exe (PID: 3444)
- RegSvcs.exe (PID: 2524)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3812)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3548)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3548)
Reads settings of System Certificates
- RegSvcs.exe (PID: 3444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:05:13 16:04:05 |
| ZipCRC: | 0xf68178b6 |
| ZipCompressedSize: | 796945 |
| ZipUncompressedSize: | 824832 |
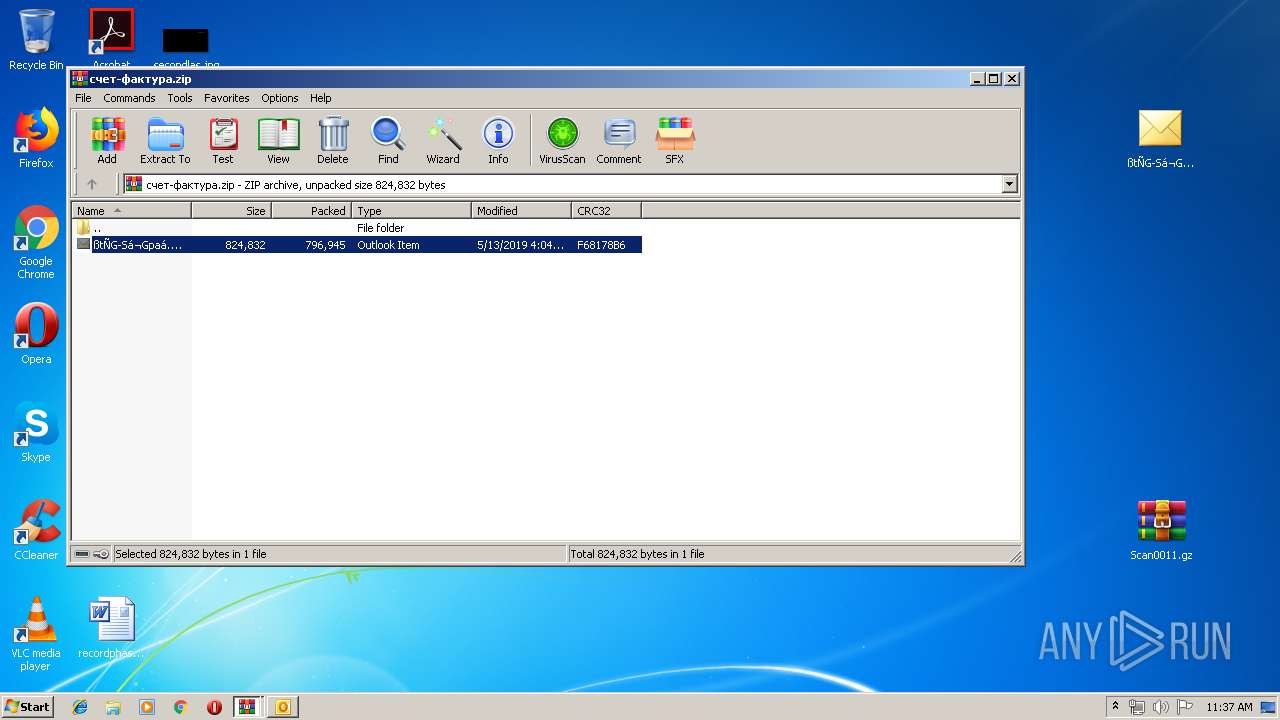
| ZipFileName: | ????-䠪????.msg |
Total processes
48
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1560 | "C:\Users\admin\Desktop\Scan0011.exe" | C:\Users\admin\Desktop\Scan0011.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2524 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | Scan0011.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2836 | "C:\Users\admin\Desktop\Scan0011.exe" | C:\Users\admin\Desktop\Scan0011.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
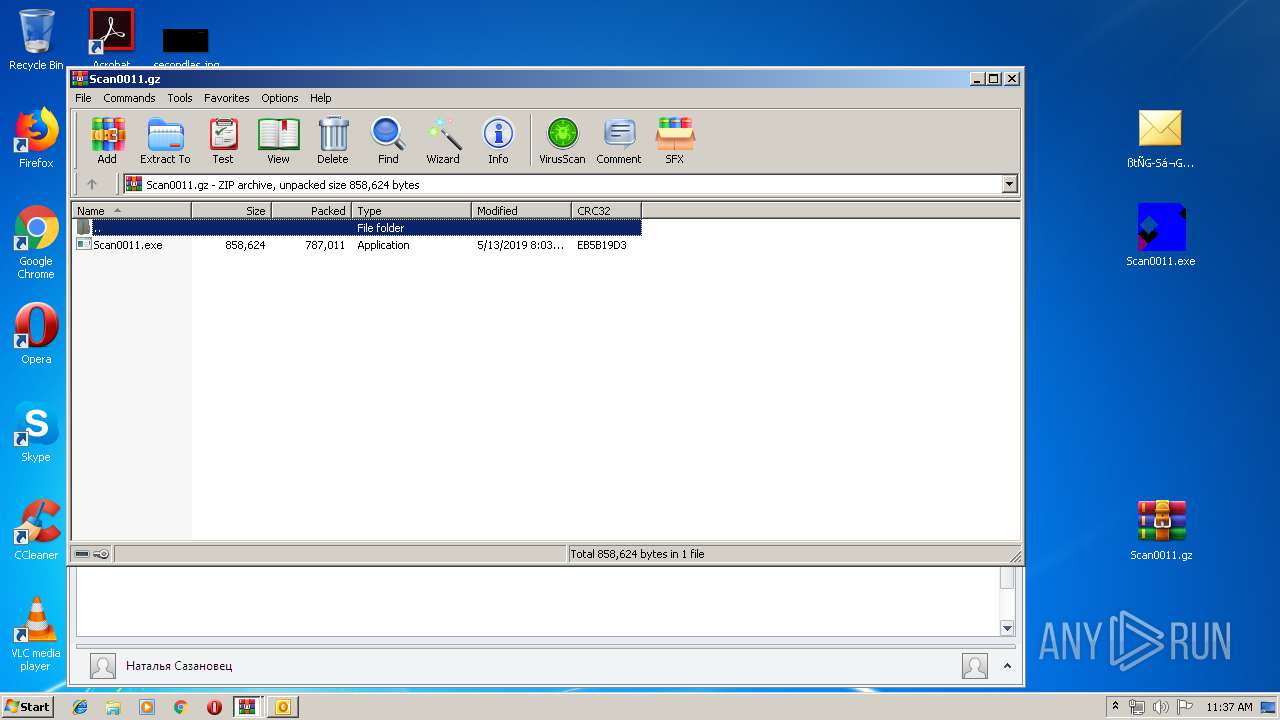
| 3208 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Scan0011.gz" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3324 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\счет-фактура.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3444 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | Scan0011.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 4294967295 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
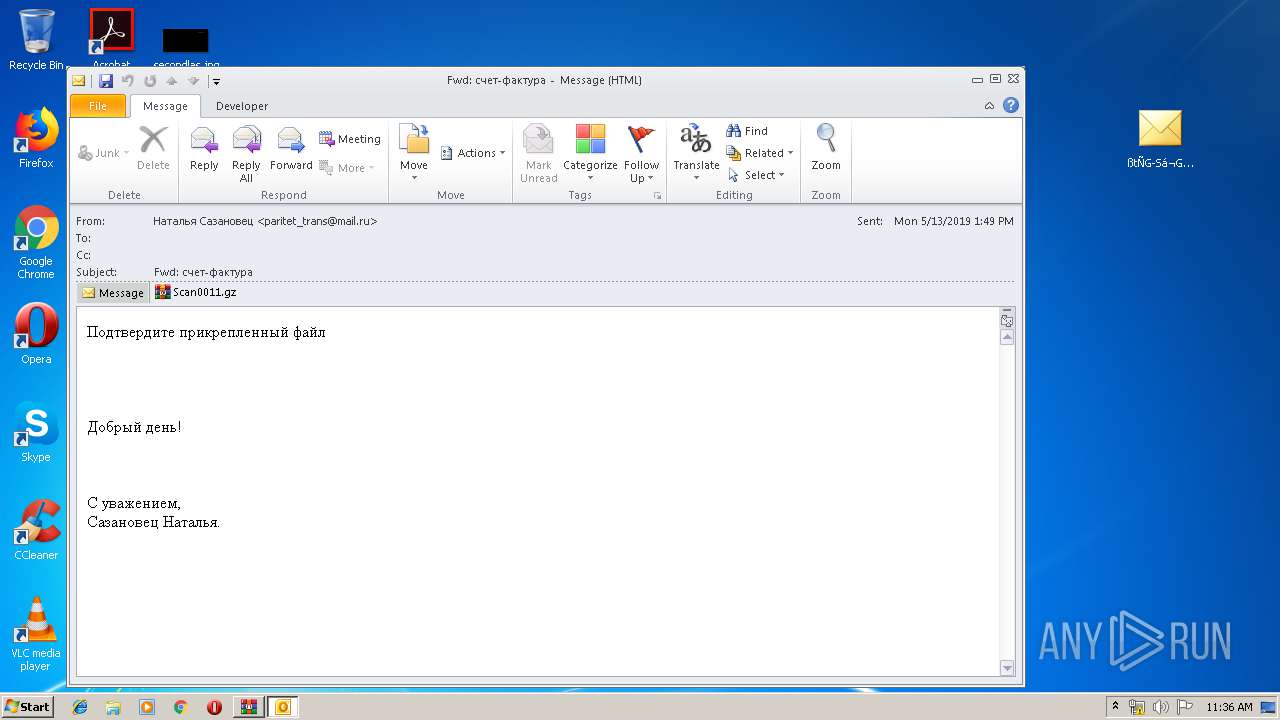
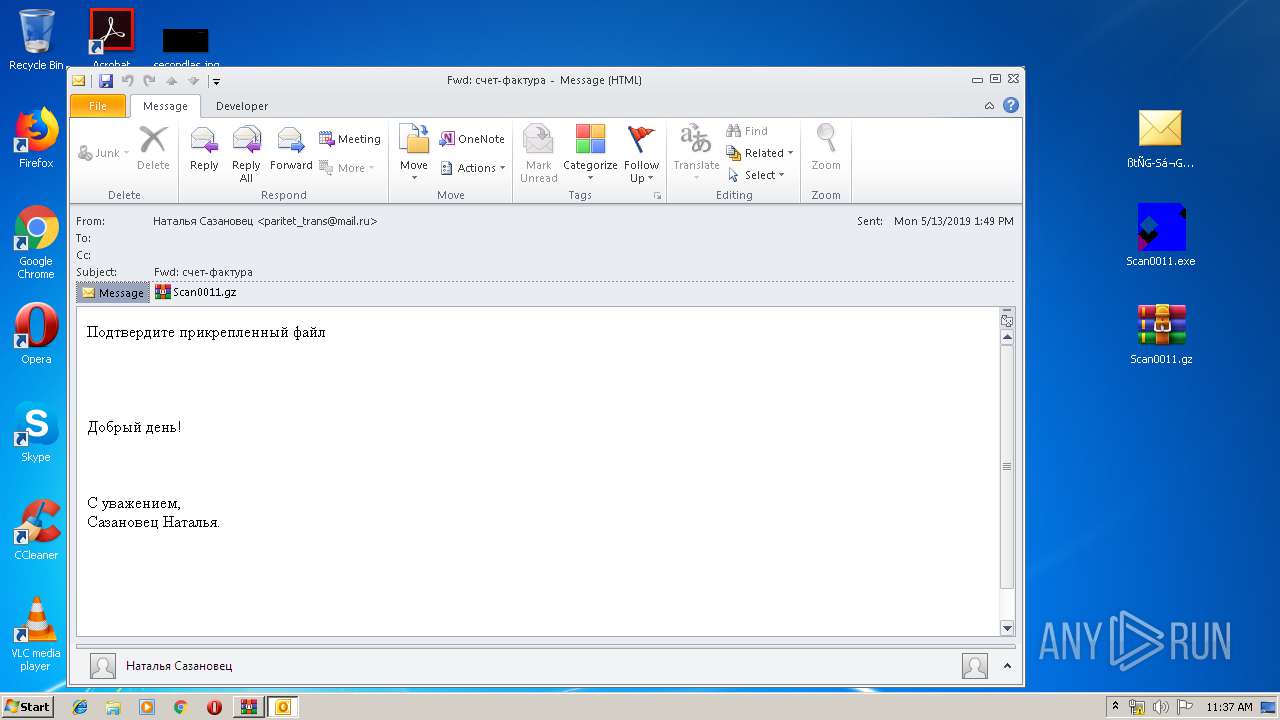
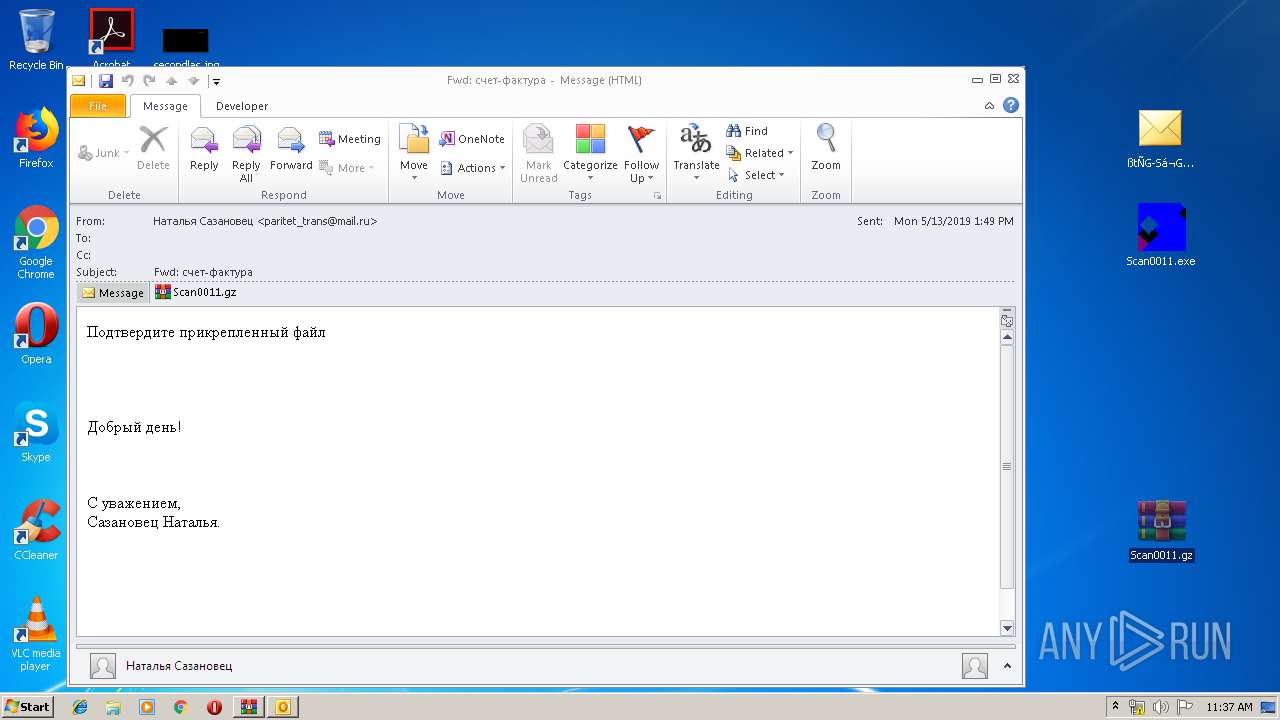
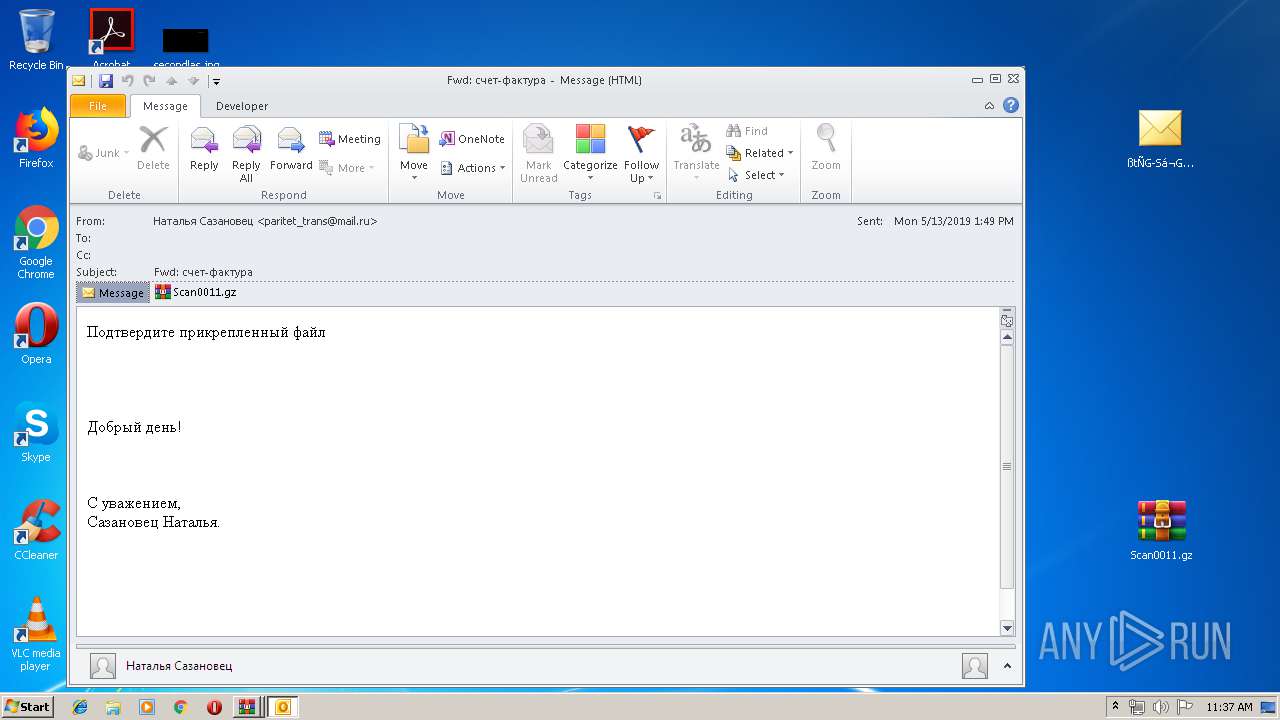
| 3548 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\Desktop\ßtÑG-Sá¬Gpaá.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
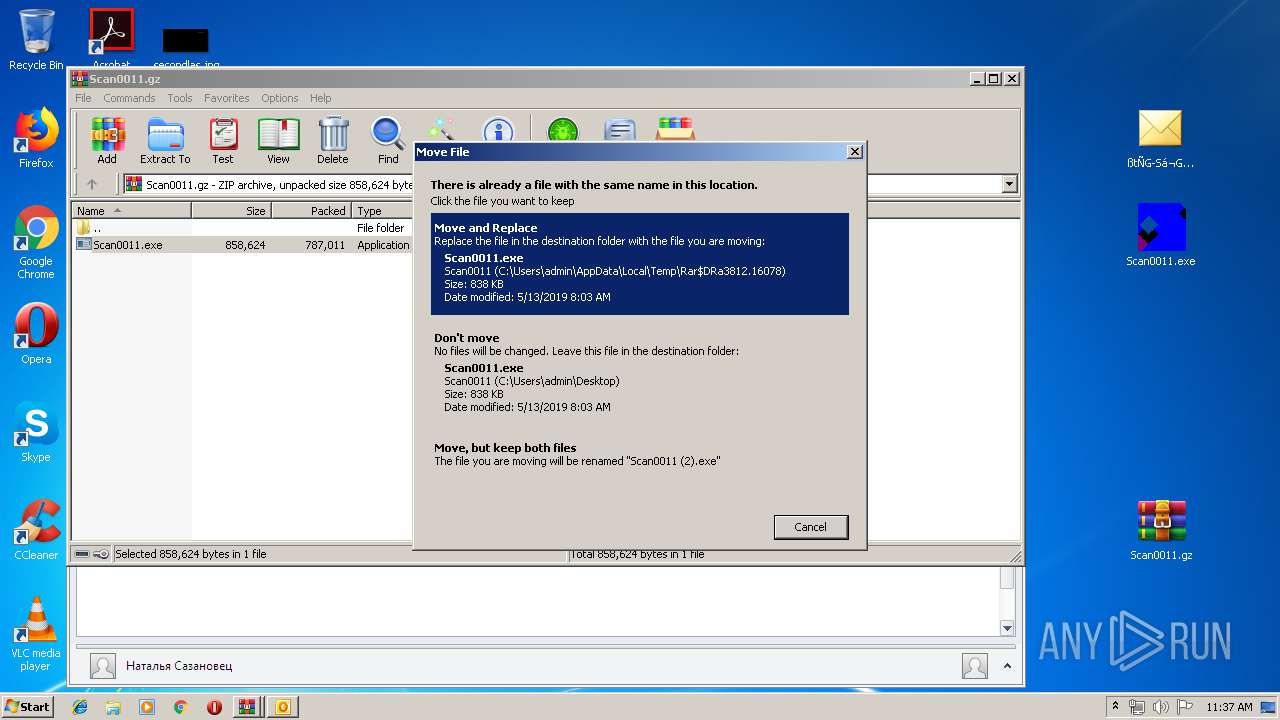
| 3812 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Scan0011.gz" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
2 455
Read events
1 982
Write events
454
Delete events
19
Modification events
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\счет-фактура.zip | |||
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {0006F045-0000-0000-C000-000000000046} {000214FA-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000004C7ACAF1090BD501 | |||
| (PID) Process: | (3324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {0006F045-0000-0000-C000-000000000046} {000214EB-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000005AA1D1F1090BD501 | |||
Executable files
1
Suspicious files
1
Text files
25
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3324.9511\ßtÑG-Sá¬Gpaá.msg | — | |
MD5:— | SHA256:— | |||
| 3548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE4AB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3208 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3208.12114\Scan0011.exe | — | |
MD5:— | SHA256:— | |||
| 3548 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3812.16078\Scan0011.exe | executable | |
MD5:— | SHA256:— | |||
| 3548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_7FE98631FF5A7C4FB002641B85801062.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 3548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 3548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_D10C0FFD9AE91543865AA695ABFAC904.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 3548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 3548 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TCPrefs_2_224F762F9B10DE4A98EEA6E5403F1B66.dat | xml | |
MD5:F194B1FA12F9B6F46A47391FAE8BEEC2 | SHA256:FCD8D7E030BE6EA7588E5C6CB568E3F1BDFC263942074B693942A27DF9521A74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3548 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3444 | RegSvcs.exe | 164.138.222.99:587 | mail.trade345.com | SuperHosting.BG Ltd. | BG | suspicious |
3548 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2524 | RegSvcs.exe | 164.138.222.99:587 | mail.trade345.com | SuperHosting.BG Ltd. | BG | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
mail.trade345.com |
| suspicious |