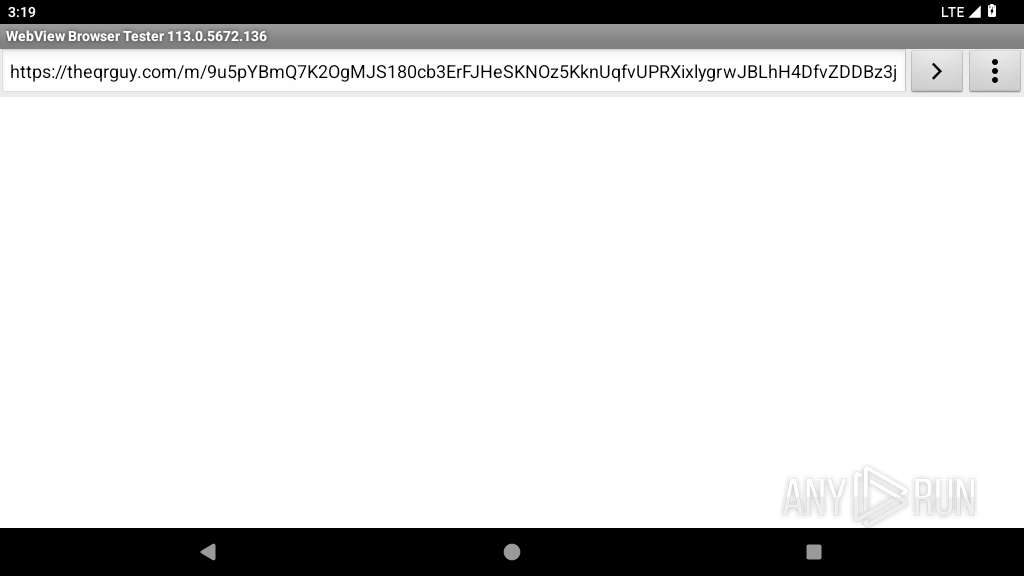
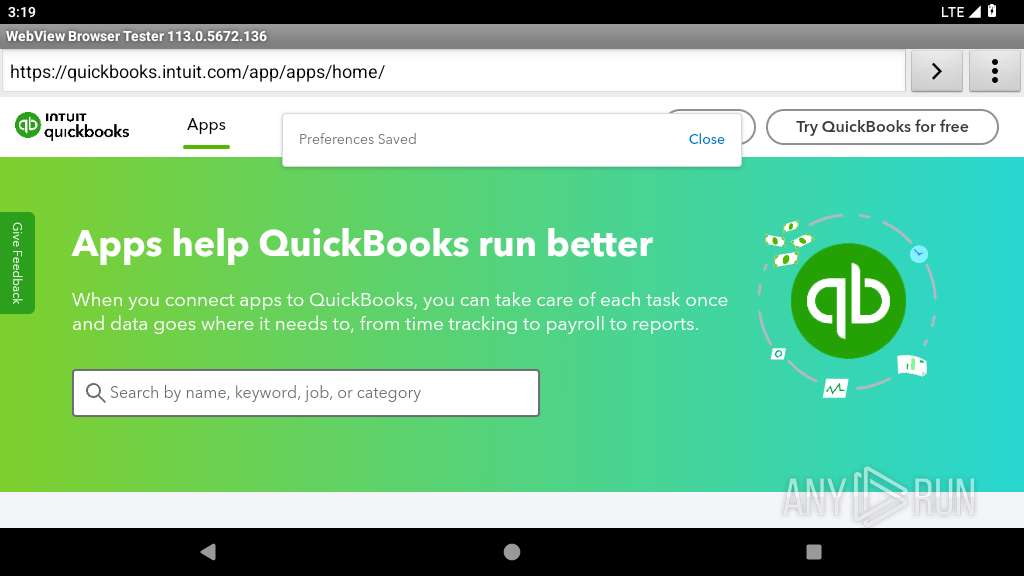
| URL: | https://theqrguy.com/m/9u5pYBmQ7K2OgMJS180cb3ErFJHeSKNOz5KknUqfvUPRXixlygrwJBLhH4DfvZDDBz3jKghxor0T3civBRUeHIkjNNbz4oBxSObscELR4MmFcPE37705tBIar3MugcHoWnw8pOM1nNoI72bK5Ac7gm |
| Full analysis: | https://app.any.run/tasks/cc62ab56-6c72-42a2-894a-05992eb00971 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 15:19:28 |
| OS: | Android 14 |
| Tags: | |
| Indicators: | |
| MD5: | 33E88E9F55E8386FD7F69F1FAF42F53B |
| SHA1: | D22F46E385FD9C7A65B9D89B26D5F7D23372071C |
| SHA256: | CE4057E90174DAF750B8B28C59385A57E6C10DAFBD5E7F91068B3C01016DAEE6 |
| SSDEEP: | 3:N8FAUXC88d6r5VGHDGPjdSCytjzhZ+j3vTrZKd2HZ+I/WysEGQGDS6oY+HO:2/5rYDWGI3vn0C3TslO6R+HO |
MALICIOUS
PHISHING has been detected (SURICATA)
- netd (PID: 345)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
126
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 345 | /system/bin/netd | /system/bin/netd | init | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2231 | org.chromium.webview_shell | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2259 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2261 | webview_zygote | /system/bin/app_process32 | — | app_process32 |
User: webview_zygote Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2308 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
63
DNS requests
31
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 216.58.212.163:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
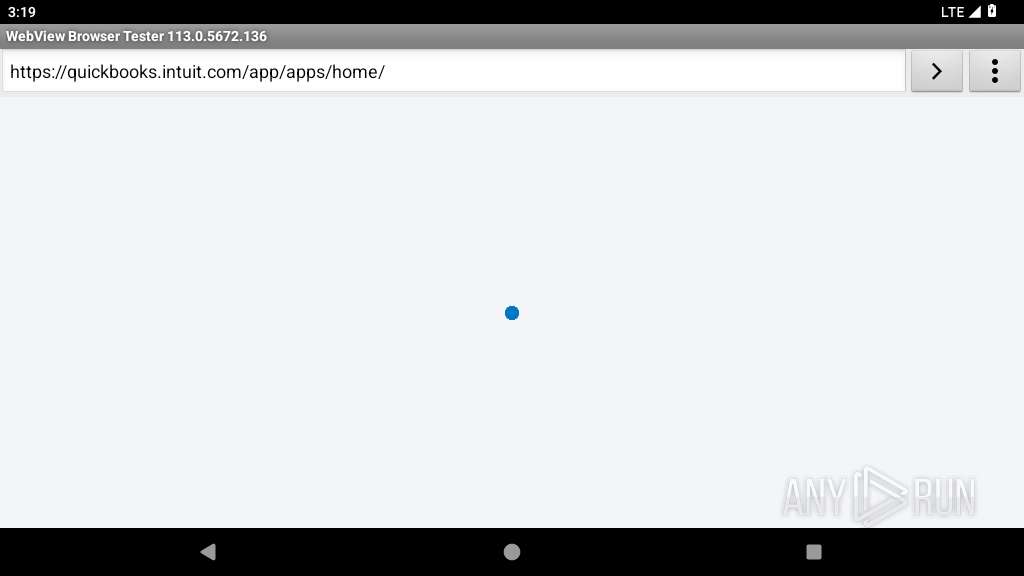
2231 | app_process64 | GET | 301 | 18.222.74.69:80 | http://wolf.pavo-consulting-llc.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
449 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.4:123 | time.android.com | — | — | whitelisted |
— | — | 216.58.212.163:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.68:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.251.31.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
2308 | app_process32 | 142.250.181.227:443 | update.googleapis.com | GOOGLE | US | whitelisted |
2259 | app_process32 | 142.250.185.195:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2308 | app_process32 | 172.217.16.206:443 | dl.google.com | GOOGLE | US | whitelisted |
2231 | app_process64 | 162.215.254.72:443 | theqrguy.com | UNIFIEDLAYER-AS-1 | US | unknown |
575 | app_process64 | 216.239.35.0:123 | time.android.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
dl.google.com |
| whitelisted |
theqrguy.com |
| unknown |
wolf.pavo-consulting-llc.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
345 | netd | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (theqrguy .com) |
2231 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2231 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |