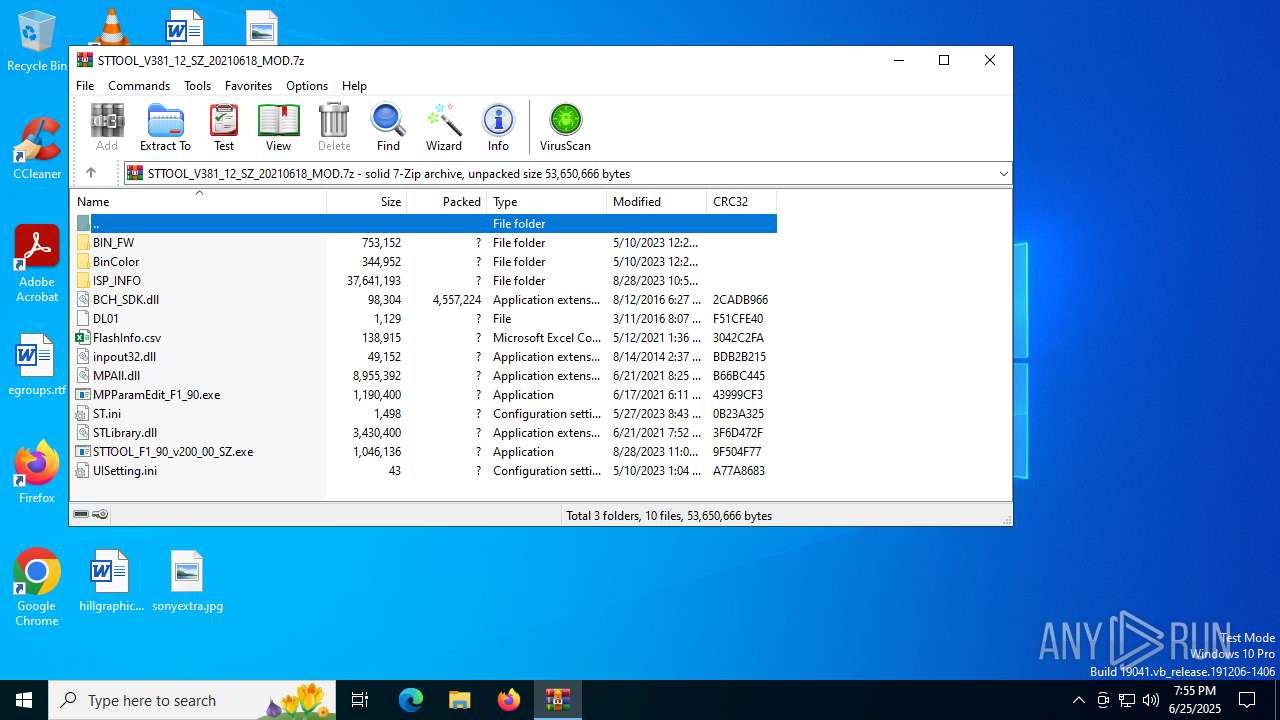
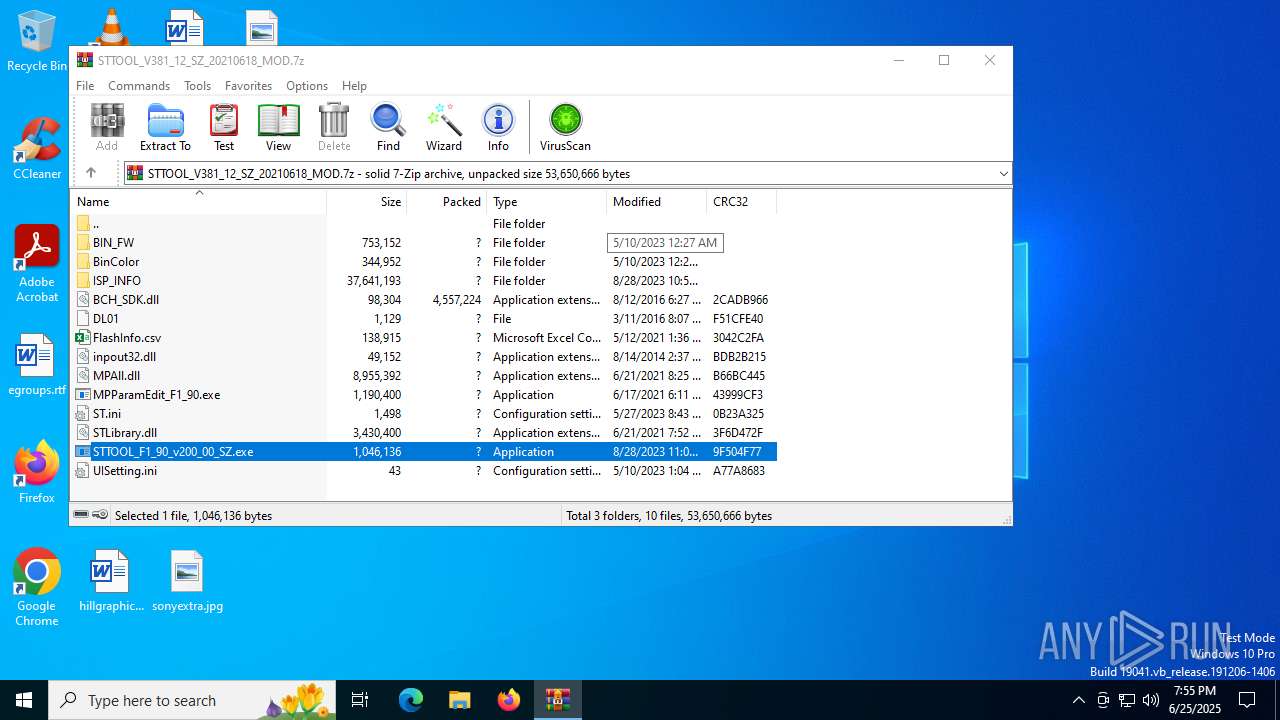
| File name: | STTOOL_V381_12_SZ_20210618_MOD.7z |
| Full analysis: | https://app.any.run/tasks/9b9fb7e0-16a1-4969-9e7e-cfe230733509 |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2025, 19:55:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 5F93E734F975D869ADE2F470A595095F |
| SHA1: | ACA72BEE164877719F354B71A97DFF190FC32363 |
| SHA256: | CE1597A6BEF8C4282A769AF1F7848221B109192C582BD1FA36A3A656218B9EC1 |
| SSDEEP: | 98304:Lu3QcDPDjpItMVWbi2EKhmdIpndk2/+VThwUiZIccjVs4nu/3nTBue6r29ShbggD:1JM52xPx4pb |
MALICIOUS
Executing a file with an untrusted certificate
- STTOOL_F1_90_v200_00_SZ.exe (PID: 6412)
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
- STTOOL_F1_90_v200_00_SZ.exe (PID: 4828)
SUSPICIOUS
Creates files in the driver directory
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
Executable content was dropped or overwritten
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
Creates or modifies Windows services
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
There is functionality for taking screenshot (YARA)
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
- MPParamEdit_F1_90.exe (PID: 5808)
Reads security settings of Internet Explorer
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
- WinRAR.exe (PID: 7096)
Application launched itself
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
Drops a system driver (possible attempt to evade defenses)
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 7096)
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
The sample compiled with chinese language support
- WinRAR.exe (PID: 7096)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7096)
Reads the computer name
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
- MPParamEdit_F1_90.exe (PID: 5808)
- STTOOL_F1_90_v200_00_SZ.exe (PID: 4828)
Checks supported languages
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
- MPParamEdit_F1_90.exe (PID: 5808)
- STTOOL_F1_90_v200_00_SZ.exe (PID: 4828)
Process checks computer location settings
- STTOOL_F1_90_v200_00_SZ.exe (PID: 1984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2023:05:10 00:27:52+00:00 |
| ArchivedFileName: | BinColor |
Total processes
142
Monitored processes
6
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1984 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\STTOOL_F1_90_v200_00_SZ.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\STTOOL_F1_90_v200_00_SZ.exe | WinRAR.exe | ||||||||||||
User: admin Company: Best Company Integrity Level: HIGH Description: Build by VC Exit code: 2 Version: 2.0.1.6 Modules
| |||||||||||||||
| 4828 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\STTOOL_F1_90_v200_00_SZ.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\STTOOL_F1_90_v200_00_SZ.exe | STTOOL_F1_90_v200_00_SZ.exe | ||||||||||||
User: admin Company: Best Company Integrity Level: HIGH Description: Build by VC Version: 2.0.1.6 Modules
| |||||||||||||||
| 5284 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5808 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\MPParamEdit_F1_90.exe" 144 .\ST.ini DL01 1 | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\MPParamEdit_F1_90.exe | STTOOL_F1_90_v200_00_SZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Version: 3, 10, 11, 0 Modules
| |||||||||||||||
| 6412 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\STTOOL_F1_90_v200_00_SZ.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\STTOOL_F1_90_v200_00_SZ.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Best Company Integrity Level: MEDIUM Description: Build by VC Exit code: 3221226540 Version: 2.0.1.6 Modules
| |||||||||||||||
| 7096 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\STTOOL_V381_12_SZ_20210618_MOD.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 658
Read events
2 634
Write events
24
Delete events
0
Modification events
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\STTOOL_V381_12_SZ_20210618_MOD.7z | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1984) STTOOL_F1_90_v200_00_SZ.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\usbflags |
| Operation: | write | Name: | IgnoreHWSerNum13fe3400 |
Value: 01 | |||
| (PID) Process: | (1984) STTOOL_F1_90_v200_00_SZ.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\usbflags |
| Operation: | write | Name: | IgnoreHWSerNum13fe3100 |
Value: 01 | |||
Executable files
13
Suspicious files
80
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\BinColor\192GB_BinColor.ini | text | |
MD5:BB043F1E4F89CFEAD001D5C724168EA9 | SHA256:FE5C8738112D344E490FFC5121BF9DC66B397F3155CBC3DEF397A6F6C1C81EB2 | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\BinColor\16GB_BinColor.ini | text | |
MD5:F5E147145DD0854DEE974E6EFA667BD5 | SHA256:603C592F1742F526EA57A3CDB047D03071691BF35885FF150D3EFEDCBFB9F131 | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\BinColor\96GB_BinColor.ini | text | |
MD5:1F5BC8F9211CF4671ED3091600CB315D | SHA256:3BCE675BCF8F7B0DC76867F37B7E2CD2F6177F105B8D2948D009D73992D68D46 | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\BinColor\512GB_BinColor.ini | text | |
MD5:F938C3DD7FA9A68F9D965CE618D675E1 | SHA256:FDD6A4E266C2C3E09035597B4C8DCC6BD65B9B2267BE7CA01511A5250837F98D | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\BinColor\144GB_BinColor.ini | text | |
MD5:7E73C8B574AA9A06894D9F2005311ACC | SHA256:80B01D72E3790B00F6C55D12BE6A01AEA4A81CE1B029E75C0ED2CEB4C04464E1 | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\BinColor\128GB_BinColor.ini | text | |
MD5:8A787DA88C798D6AA35B30B8838D5D66 | SHA256:8E7B928649473921A640EF84718D5E095E2CF42BEC1208C661EFCF41411E188A | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\FlashInfo.csv | csv | |
MD5:5F8FE8A96F7BACC906686DEC530C7764 | SHA256:006D1FF98442F25BEE4DBC73FB5CE3010503429C9DD9FB6E5A263B7F4D7AF47A | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\BIN_FW\b2307_bank.bin | binary | |
MD5:CF09242A48B6DEFED45B62F8B5731CDF | SHA256:AD460E6E5D9A30E5CAEFC8B8179DB0FA94D8E2CDF88FEC5027AC87282AE65E25 | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\BIN_FW\b2309_bank.bin | binary | |
MD5:A2036D1F5B3581A1A8D736541FD9DCED | SHA256:C46C9ED187019ED9D080FB871D3F4DF575E05A2B1F4993A88E3BEF0579A6F35B | |||
| 7096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\BIN_FW\b2267_bank.bin | binary | |
MD5:8B2C688BF9F93AF0B0B039F91BDC912D | SHA256:5B6D217234D869597A037115FC3F179E985E437A99551EBC38CA94964AD08CEA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2288 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3608 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3608 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5576 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2288 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2288 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
STTOOL_F1_90_v200_00_SZ.exe | Init criticalSection |
STTOOL_F1_90_v200_00_SZ.exe | MyFlashInfo : filename |
STTOOL_F1_90_v200_00_SZ.exe | flashInfo.csv |
STTOOL_F1_90_v200_00_SZ.exe | PortSetting |
STTOOL_F1_90_v200_00_SZ.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7096.12141\STTOOL_F1_90_v200_00_SZ.exe |
STTOOL_F1_90_v200_00_SZ.exe | ****CMPProgramDlg::GetVarFromIni
|
STTOOL_F1_90_v200_00_SZ.exe | W7 GetMACaddress start |
STTOOL_F1_90_v200_00_SZ.exe | blEraseKeepEarly = 0 |
STTOOL_F1_90_v200_00_SZ.exe | blEraseKeepEarly = 0 |
STTOOL_F1_90_v200_00_SZ.exe | IgnoreHWSerNum13fe3100 |