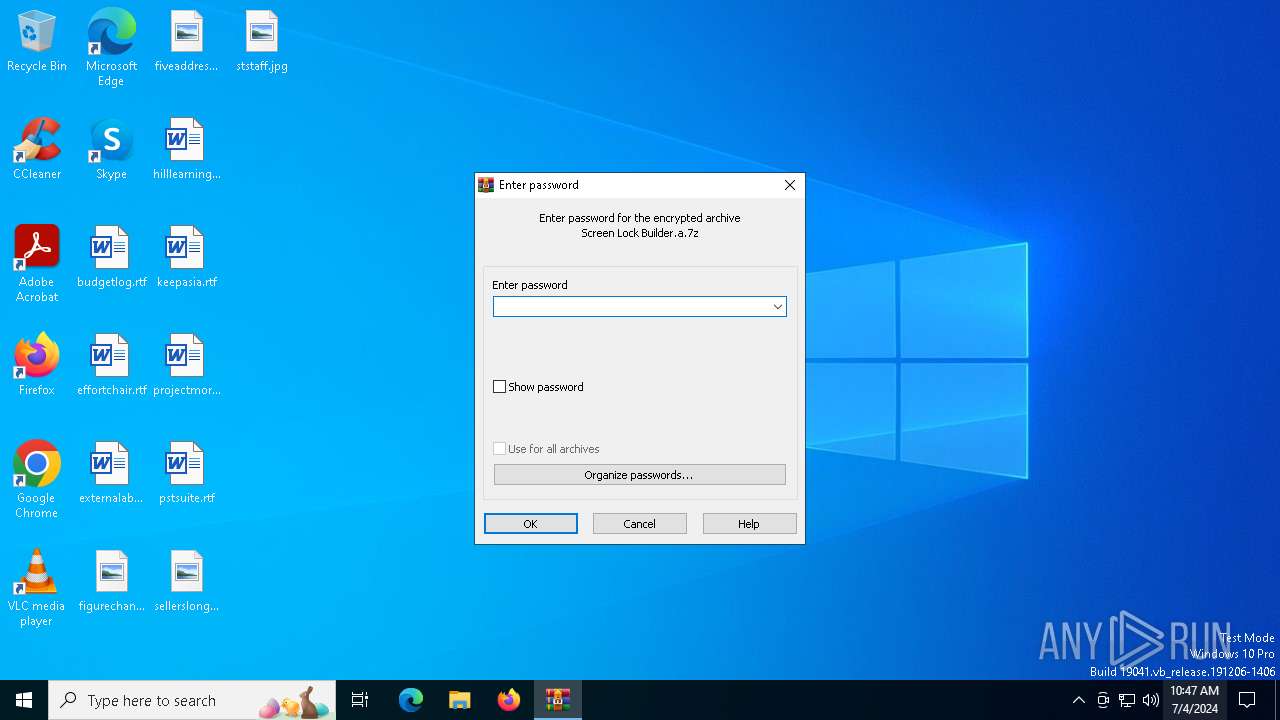
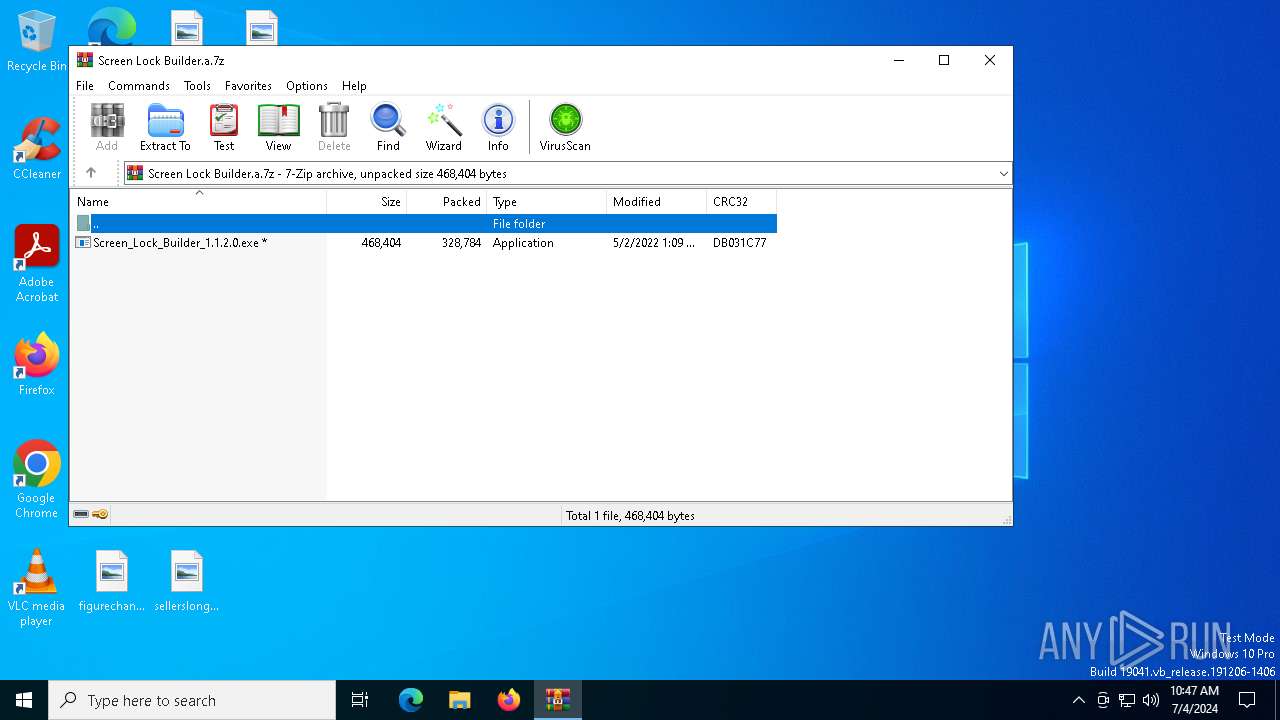
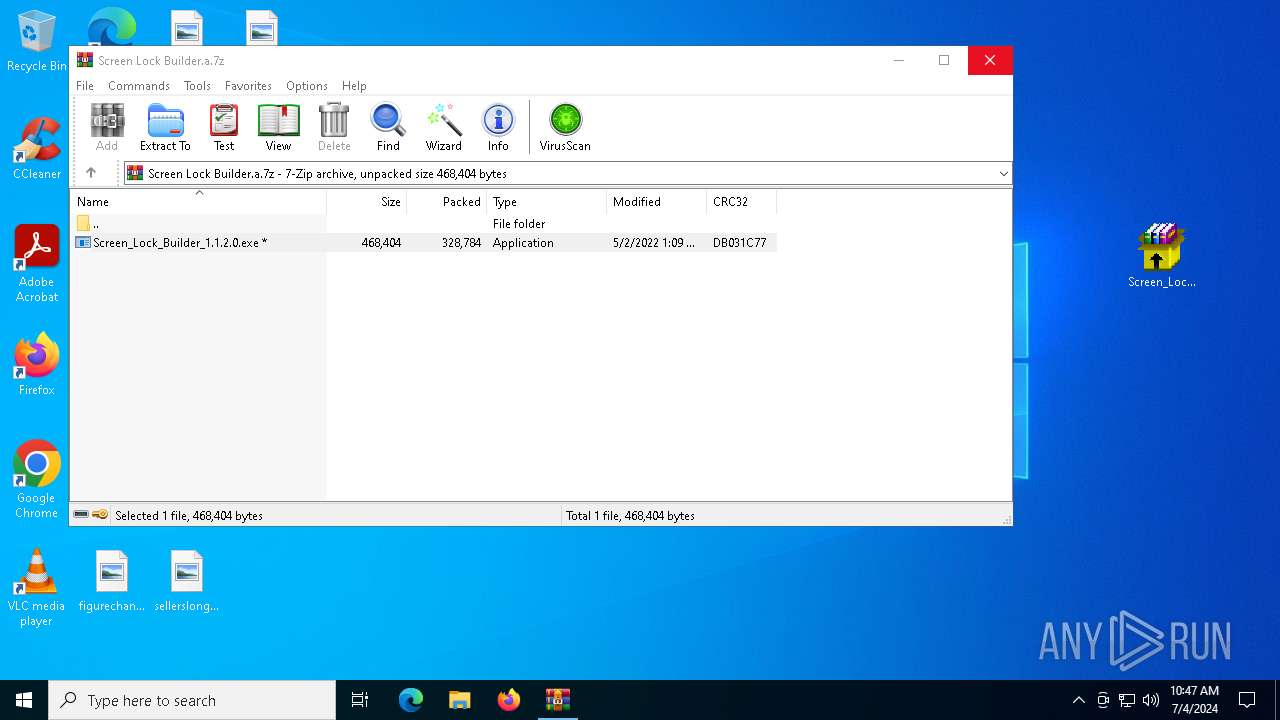
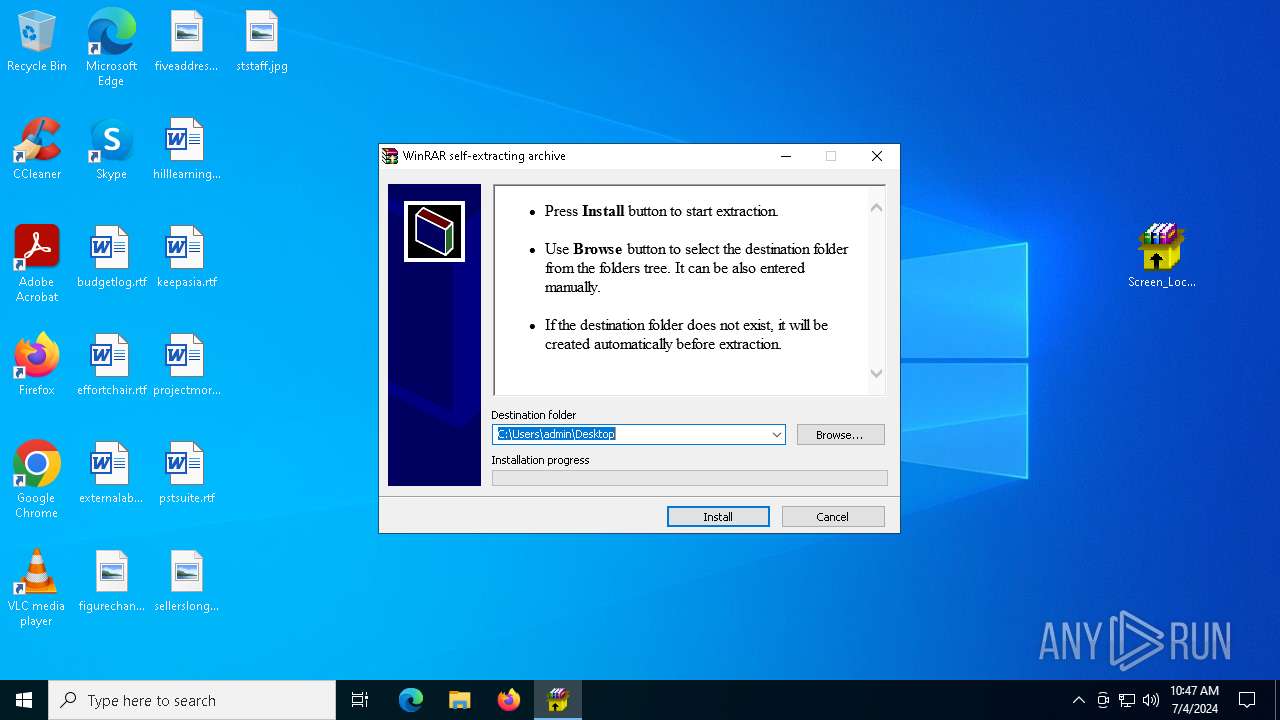
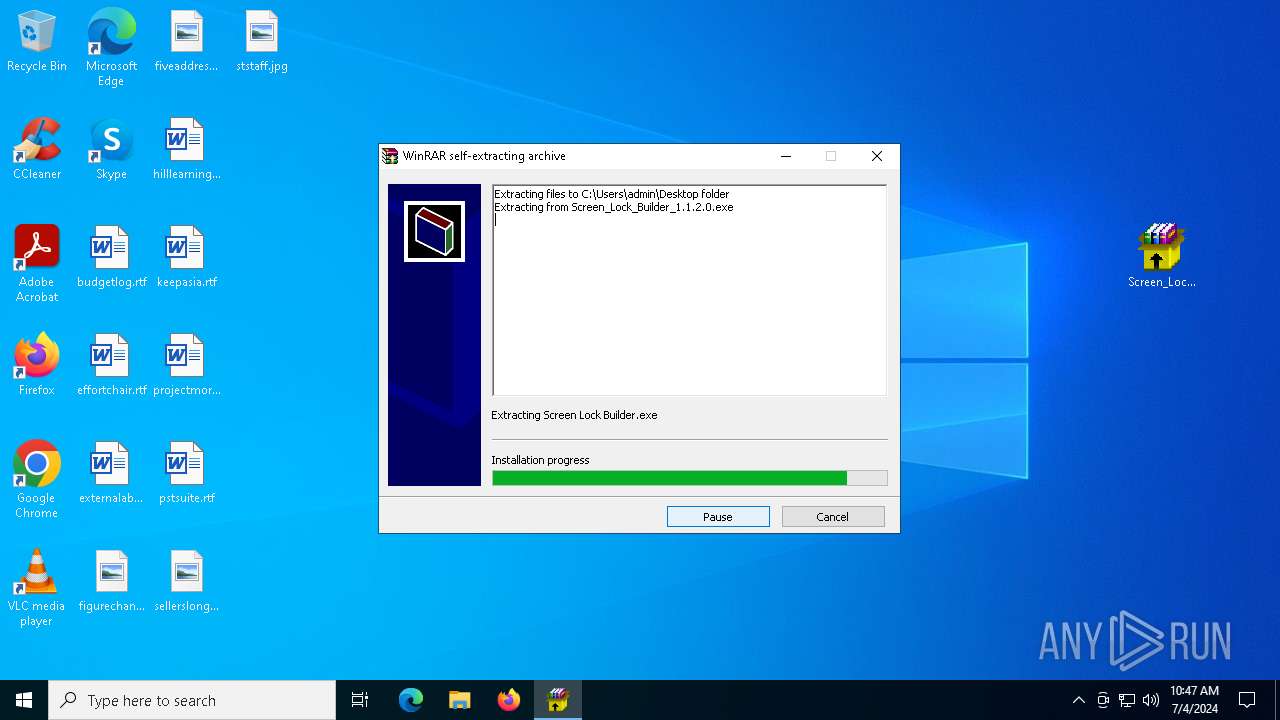
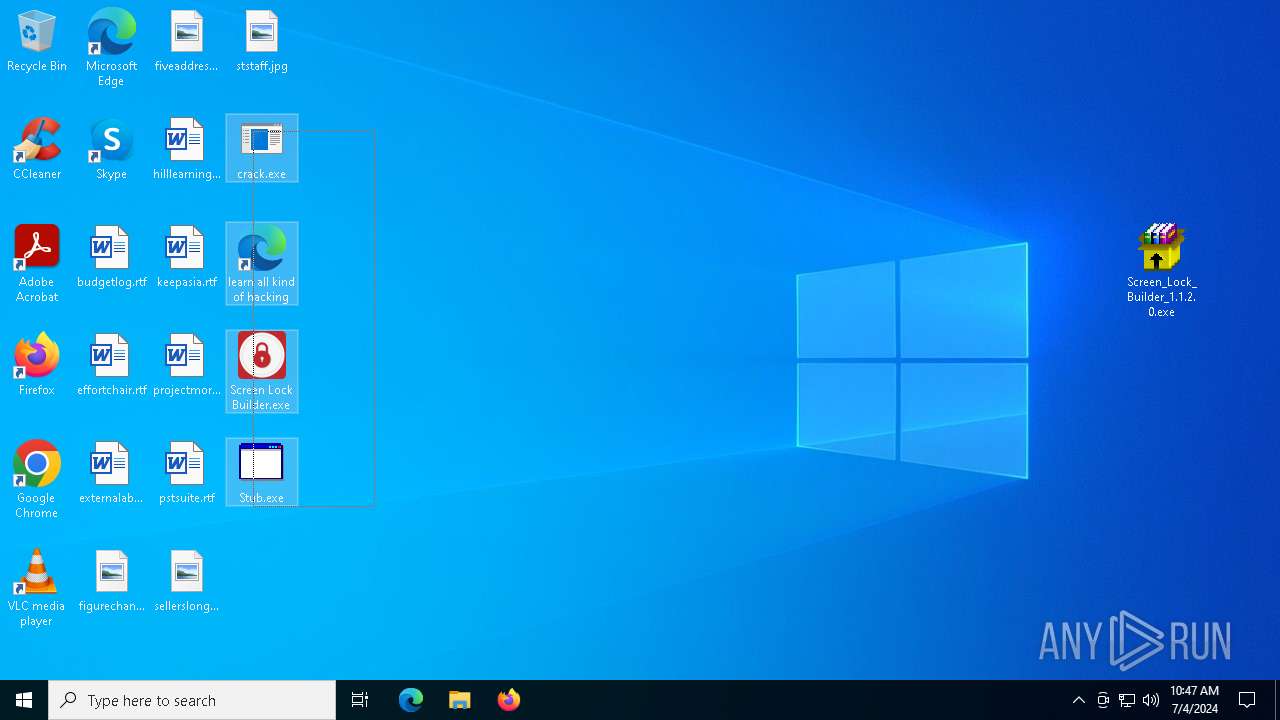
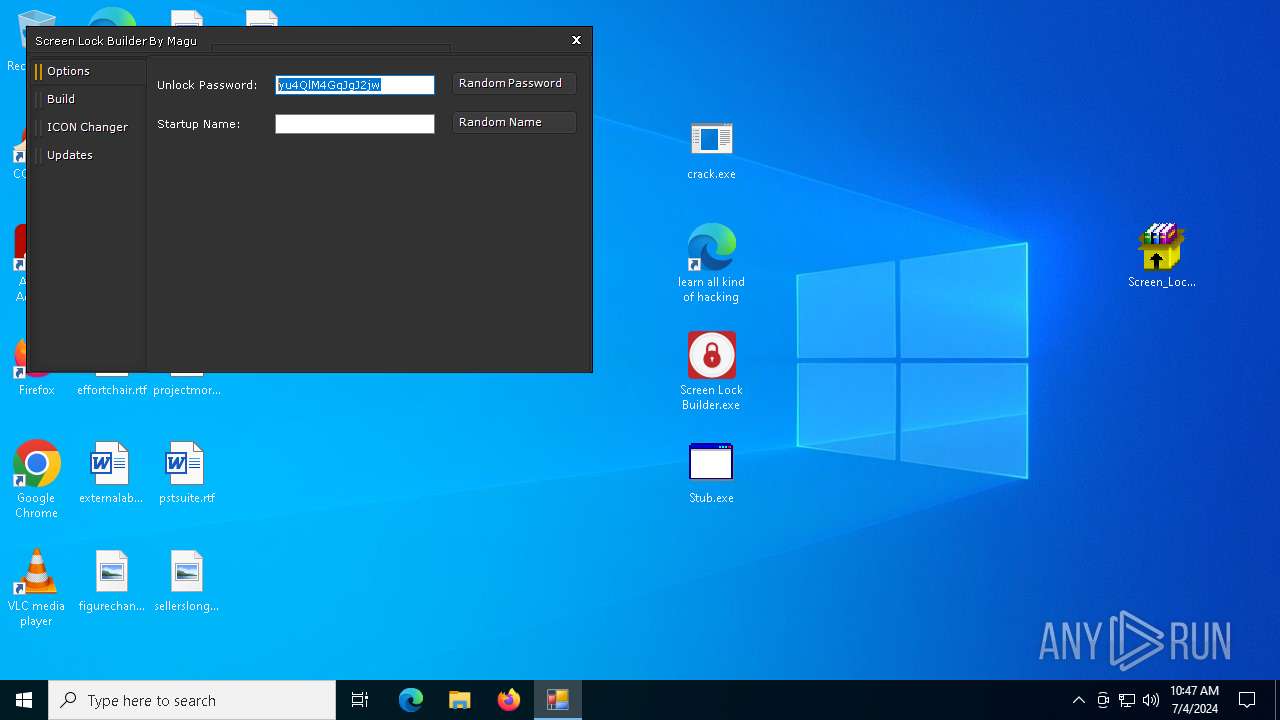
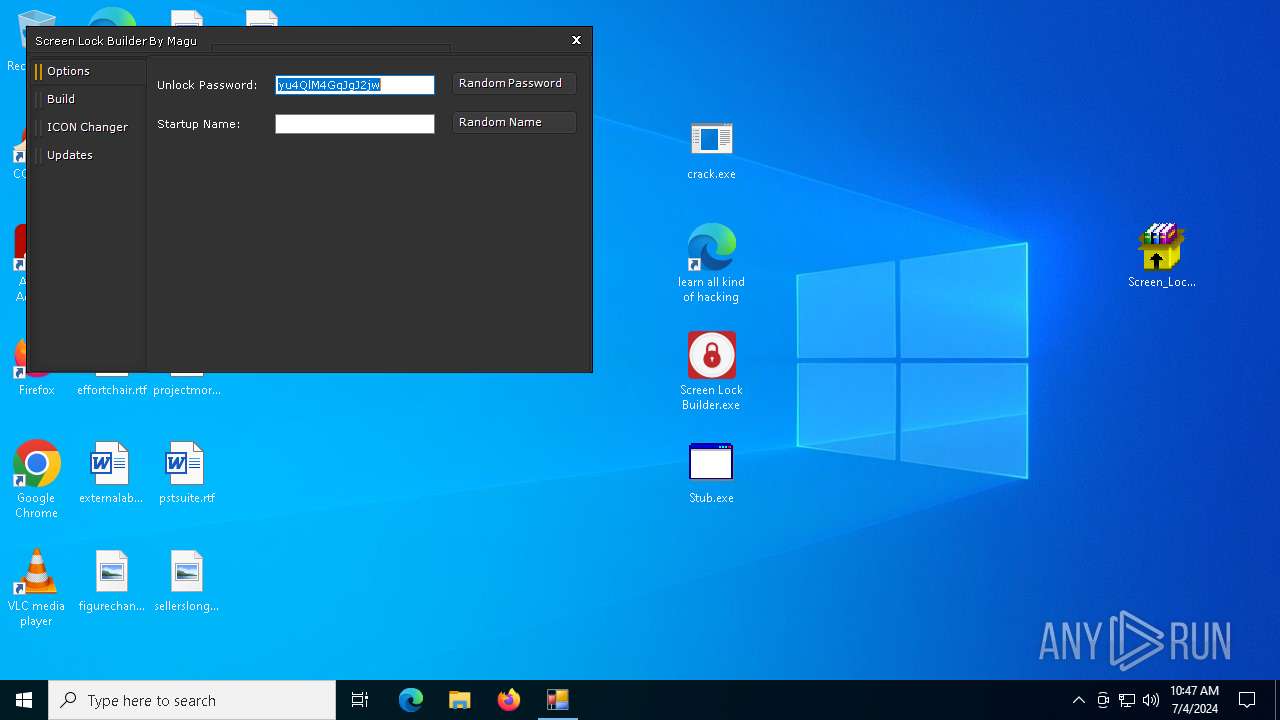
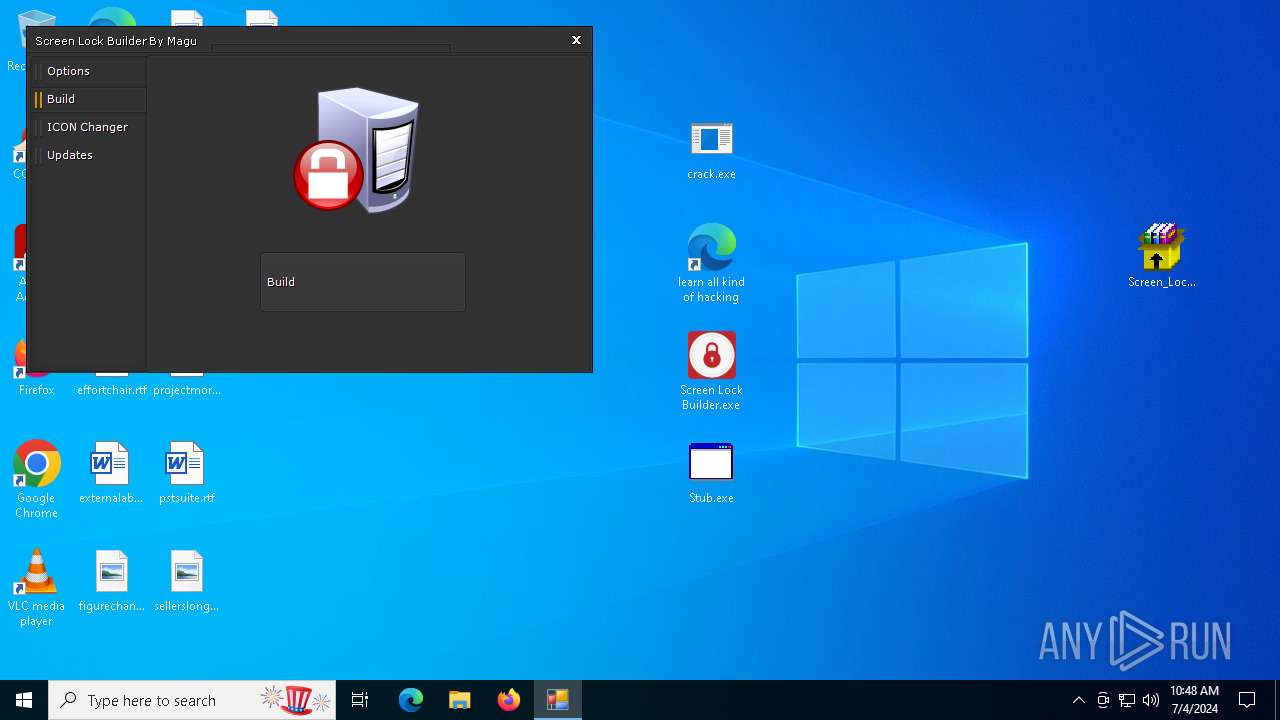
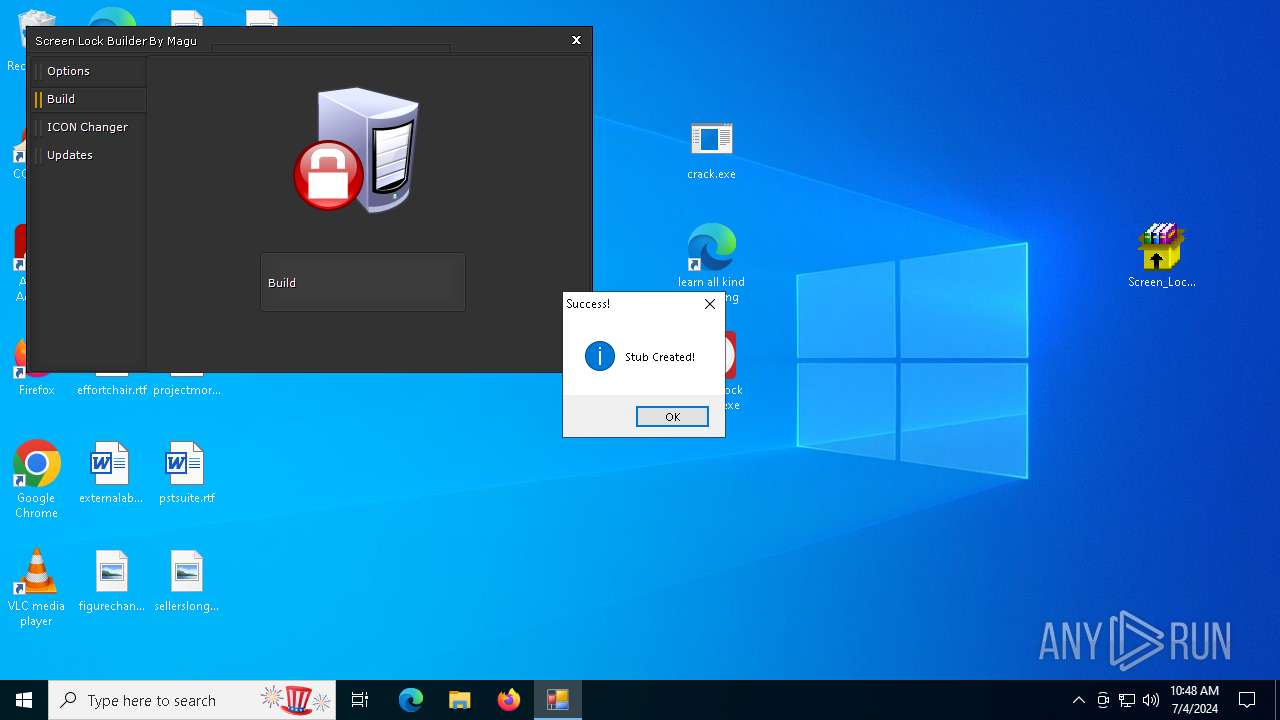
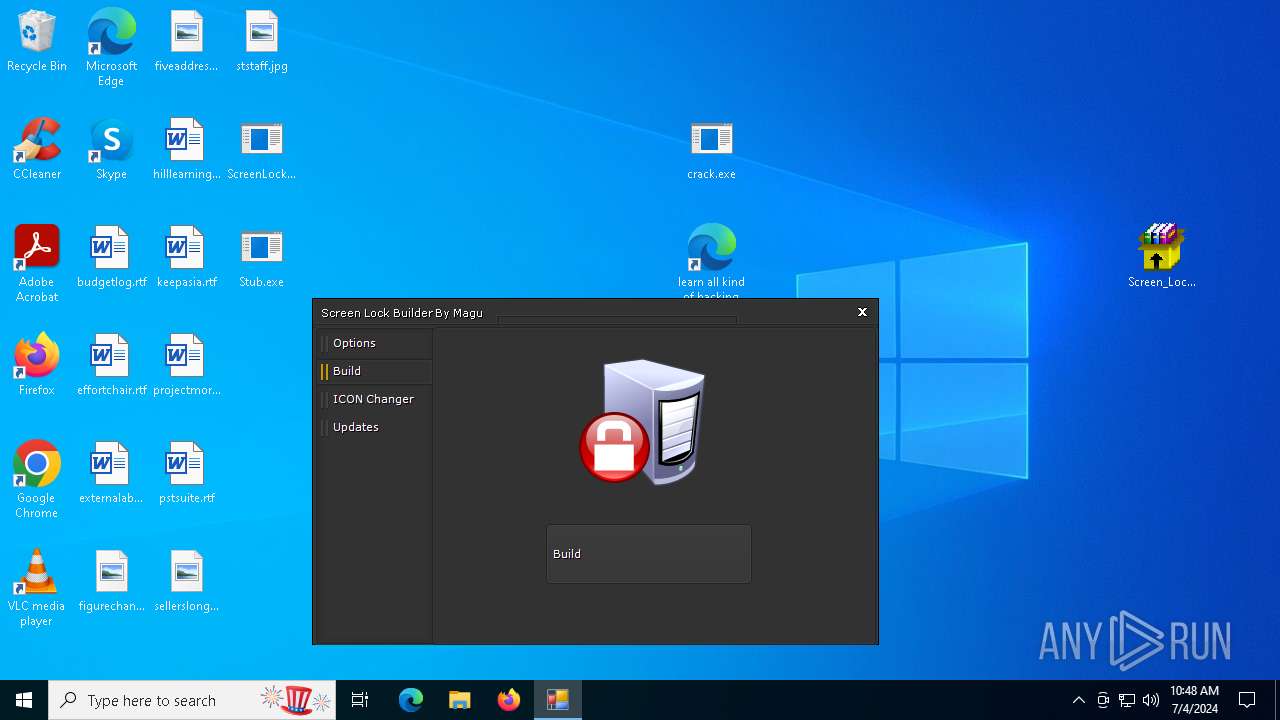
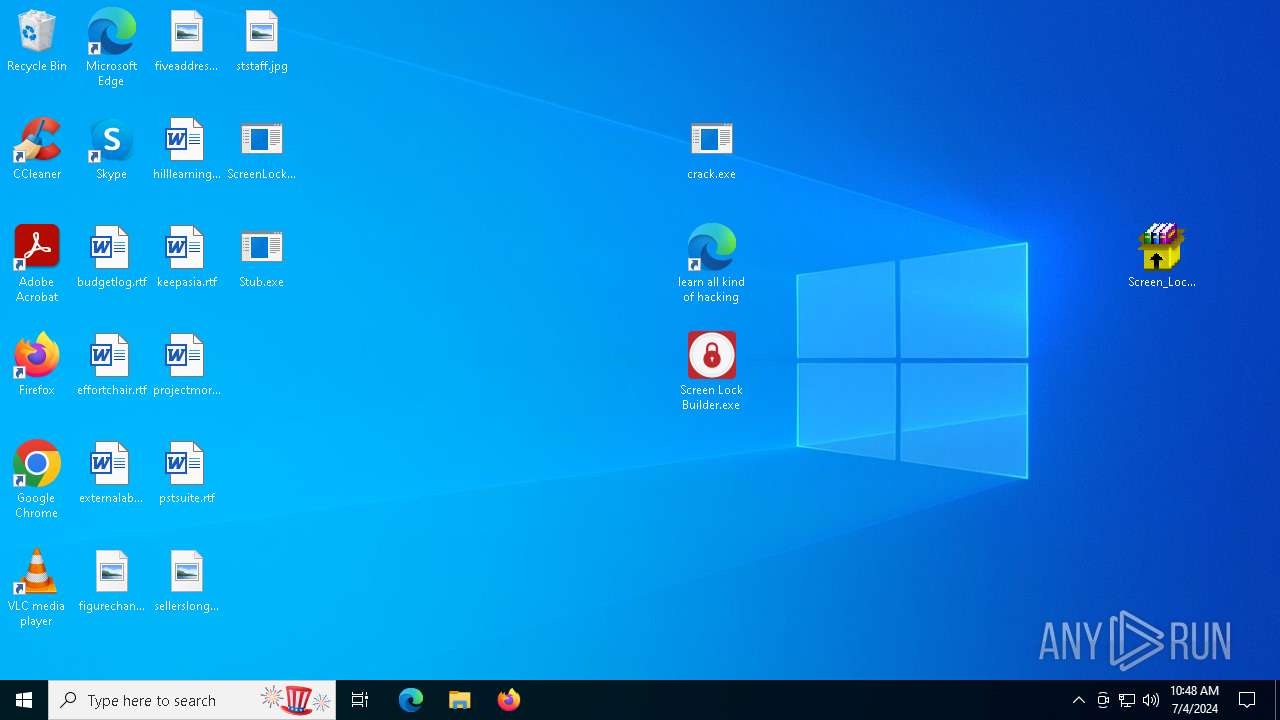
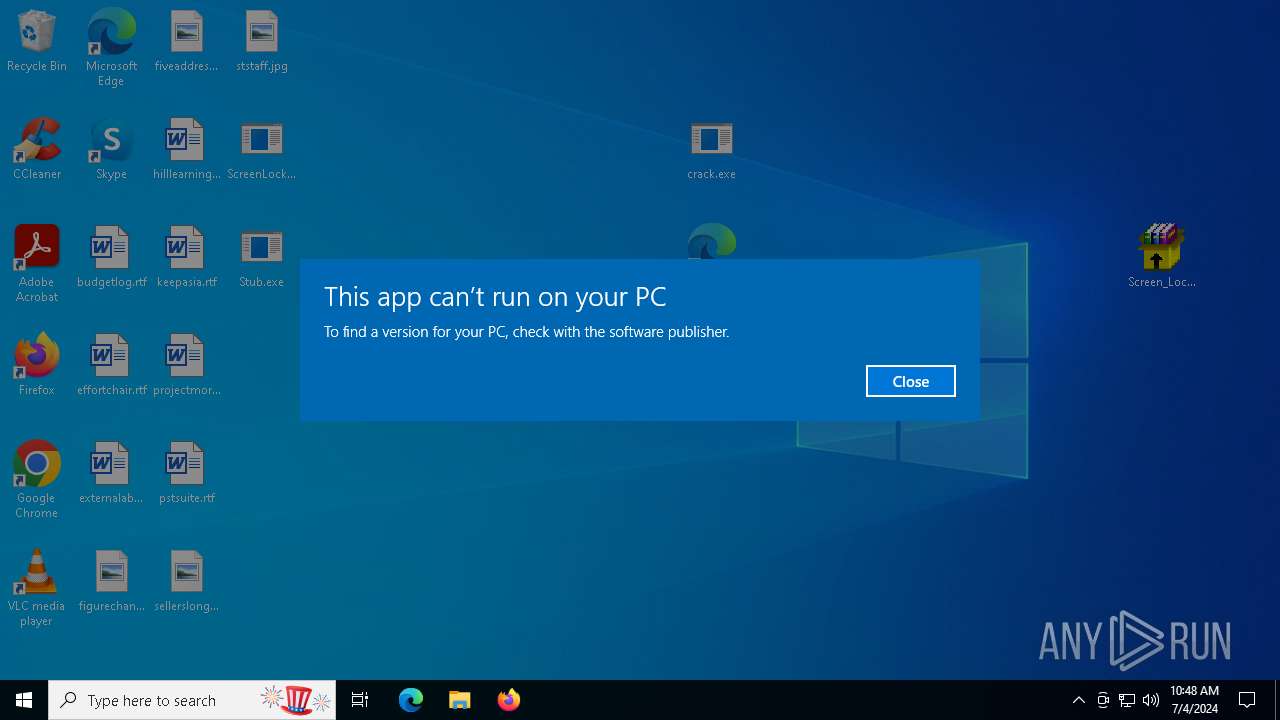
| File name: | Screen Lock Builder.a.7z |
| Full analysis: | https://app.any.run/tasks/2fde3531-965a-4324-9721-e752030737eb |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2024, 10:47:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | AC1BF901C4D70EB454B253C76D801583 |
| SHA1: | 54E3684DFFEB2563D04D577F5B8C83D9067CF714 |
| SHA256: | CE05F4516D8552F4C893CF59D7F171DBBAA9A6AC0C303F5E0A92000A72B0DFDB |
| SSDEEP: | 6144:STaRnUJxm8P3ZYaSdRFPtPxHjAsgnRBrwgcxG7aUDDPe/abKfgs:gSYb5SdRF3yRBD8gaKLe/iKfF |
MALICIOUS
Drops the executable file immediately after the start
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
- crack.exe (PID: 6856)
- Screen Lock Builder.exe (PID: 5504)
Create files in the Startup directory
- crack.exe (PID: 6856)
Changes the autorun value in the registry
- crack.exe (PID: 6856)
SUSPICIOUS
Executable content was dropped or overwritten
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
- crack.exe (PID: 6856)
- Screen Lock Builder.exe (PID: 5504)
Reads Internet Explorer settings
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
Reads Microsoft Outlook installation path
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
Reads the date of Windows installation
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
Reads security settings of Internet Explorer
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
- crack.exe (PID: 6856)
INFO
Manual execution by a user
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
- Screen Lock Builder.exe (PID: 5504)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6236)
Reads the computer name
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
- crack.exe (PID: 6856)
- Screen Lock Builder.exe (PID: 5504)
Process checks Internet Explorer phishing filters
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6236)
Process checks computer location settings
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
Checks supported languages
- crack.exe (PID: 6856)
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
- Screen Lock Builder.exe (PID: 5504)
Reads the machine GUID from the registry
- crack.exe (PID: 6856)
- Screen Lock Builder.exe (PID: 5504)
Checks proxy server information
- Screen_Lock_Builder_1.1.2.0.exe (PID: 5652)
Create files in a temporary directory
- crack.exe (PID: 6856)
Creates files or folders in the user directory
- crack.exe (PID: 6856)
Reads the software policy settings
- slui.exe (PID: 5224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
147
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2132 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5224 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
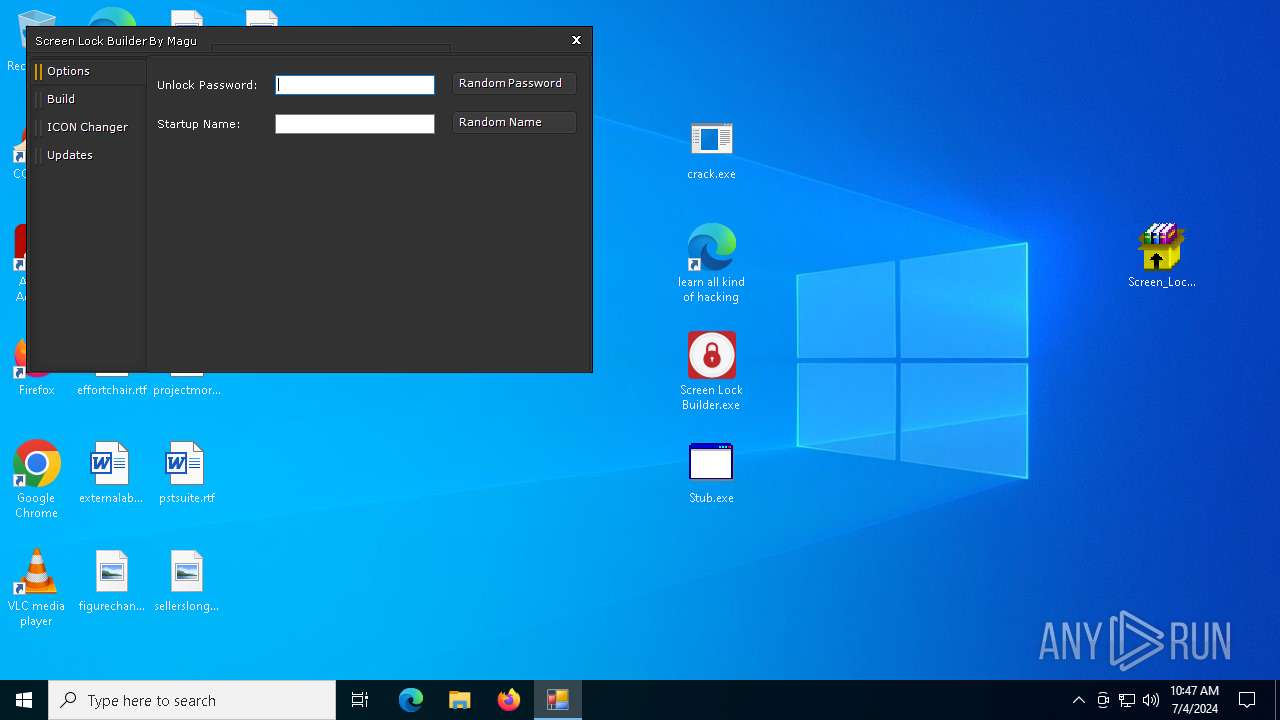
| 5504 | "C:\Users\admin\Desktop\Screen Lock Builder.exe" | C:\Users\admin\Desktop\Screen Lock Builder.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Screen Lock Builder Version: 1.1.2.0 Modules
| |||||||||||||||
| 5652 | "C:\Users\admin\Desktop\Screen_Lock_Builder_1.1.2.0.exe" | C:\Users\admin\Desktop\Screen_Lock_Builder_1.1.2.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5872 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6236 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Screen Lock Builder.a.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6856 | "C:\Users\admin\Desktop\crack.exe" | C:\Users\admin\Desktop\crack.exe | Screen_Lock_Builder_1.1.2.0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Get Cliboard Address Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
8 655
Read events
8 612
Write events
41
Delete events
2
Modification events
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Screen Lock Builder.a.7z | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
7
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5652 | Screen_Lock_Builder_1.1.2.0.exe | C:\Users\admin\Desktop\Screen Lock Builder.exe | executable | |
MD5:37903E2E1A0332E3EACD2311DD71EC86 | SHA256:D49C0F2E95E8F08120E0980D36AFC5A1600EF6A57DA7E6892384F9DF84E51D9E | |||
| 6236 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6236.35719\Screen_Lock_Builder_1.1.2.0.exe | executable | |
MD5:29981C395D8CF10E0CDA07567B54BCCF | SHA256:D849E7CBB8AC126283730F81603FAD20978BF47D9FABE4B6B02496775178B93C | |||
| 6856 | crack.exe | C:\Users\admin\AppData\Local\Temp\crack.exe | executable | |
MD5:B5086EEBE0A0A878807A677AEB4FC4F6 | SHA256:69029912F948D6BD6C3084CA34885CDEEF97190865F6838C9A928FAD56B3F958 | |||
| 5652 | Screen_Lock_Builder_1.1.2.0.exe | C:\Users\admin\Desktop\crack.exe | executable | |
MD5:B5086EEBE0A0A878807A677AEB4FC4F6 | SHA256:69029912F948D6BD6C3084CA34885CDEEF97190865F6838C9A928FAD56B3F958 | |||
| 5652 | Screen_Lock_Builder_1.1.2.0.exe | C:\Users\admin\Desktop\Stub.exe | executable | |
MD5:32E653A443AE530E664C0FDA0E5D0C28 | SHA256:1FBE18A012CFF3E4AEFB3A0238276A6A12CB6A8FBF8EA8BD4F4D9B95A220941B | |||
| 5652 | Screen_Lock_Builder_1.1.2.0.exe | C:\Users\admin\Desktop\learn all kind of hacking.url | binary | |
MD5:7ADE4A739CBD8F44D0EF52A2F1BC6E7B | SHA256:CC7649ED53C65E4851ACE414529564FE16801BB2BED4CB15588BFD6B4AC13616 | |||
| 6856 | crack.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\WindowsUpdater.lnk | lnk | |
MD5:EBEAFB6B543D005B9EBE42F134740D3C | SHA256:8EB6C3F3CA91B9CAEC5EA6452485EFD1C9B3321AAF8245886993DFDEFE6130C1 | |||
| 6856 | crack.exe | C:\Users\admin\AppData\Local\GetCliboardAddress\crack.exe_Url_vwz1sbgrmhsrf1oi3kv2hzvndbs0ehl3\1.0.0.0\tn5j1hr1.newcfg | xml | |
MD5:926E6E2285AF0AE654393254F4B49957 | SHA256:254F6BE1B7C21088F96736907B4990F6FBF2B4EED960B3B6815F8CB3B6535A47 | |||
| 6856 | crack.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\crack.exe | executable | |
MD5:B5086EEBE0A0A878807A677AEB4FC4F6 | SHA256:69029912F948D6BD6C3084CA34885CDEEF97190865F6838C9A928FAD56B3F958 | |||
| 6856 | crack.exe | C:\Users\admin\AppData\Local\GetCliboardAddress\crack.exe_Url_vwz1sbgrmhsrf1oi3kv2hzvndbs0ehl3\1.0.0.0\user.config | xml | |
MD5:926E6E2285AF0AE654393254F4B49957 | SHA256:254F6BE1B7C21088F96736907B4990F6FBF2B4EED960B3B6815F8CB3B6535A47 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
68
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3992 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1968 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1968 | MoUsoCoreWorker.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6464 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6548 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
5184 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
5184 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
528 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2140 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1968 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3992 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3992 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1060 | svchost.exe | 2.18.97.227:443 | go.microsoft.com | Akamai International B.V. | FR | unknown |
3040 | OfficeClickToRun.exe | 52.111.236.23:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |