| File name: | Setup.exe |
| Full analysis: | https://app.any.run/tasks/7ca63de8-068a-465c-b284-b2c042d9fa33 |
| Verdict: | No threats detected |
| Analysis date: | August 07, 2025, 10:00:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | BCDA19971143D986D00614AA63B9BF0E |
| SHA1: | 2873AD181DF47E470377A7AF56F3B492CED911D1 |
| SHA256: | CDFA0E7C30AE1B0AF474CF9E5026E8E606C78DC47A8C3280E87E9E3308AC7389 |
| SSDEEP: | 98304:q+cD4dnbPJ0a0ad3ZTvW6IMtCaQgnms0f9LKY6k5LlKcMhjeMcoKI22LnXK65DlC:tq |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Setup.exe (PID: 2716)
- Setup.tmp (PID: 892)
- Setup.exe (PID: 5808)
Reads security settings of Internet Explorer
- Setup.tmp (PID: 3908)
Reads the Windows owner or organization settings
- Setup.tmp (PID: 892)
Drops 7-zip archiver for unpacking
- Setup.tmp (PID: 892)
INFO
Checks supported languages
- Setup.exe (PID: 2716)
- Setup.exe (PID: 5808)
- 7z.exe (PID: 1808)
- 7z.exe (PID: 6876)
- 7z.exe (PID: 1864)
- 7z.exe (PID: 6860)
- Setup.tmp (PID: 3908)
- Setup.tmp (PID: 892)
Create files in a temporary directory
- Setup.exe (PID: 2716)
- Setup.exe (PID: 5808)
- Setup.tmp (PID: 892)
Reads the computer name
- Setup.tmp (PID: 3908)
- 7z.exe (PID: 1808)
- 7z.exe (PID: 6876)
- 7z.exe (PID: 1864)
- 7z.exe (PID: 6860)
- Setup.tmp (PID: 892)
The sample compiled with english language support
- Setup.tmp (PID: 892)
Creates files in the program directory
- Setup.tmp (PID: 892)
Process checks computer location settings
- Setup.tmp (PID: 3908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 173568 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
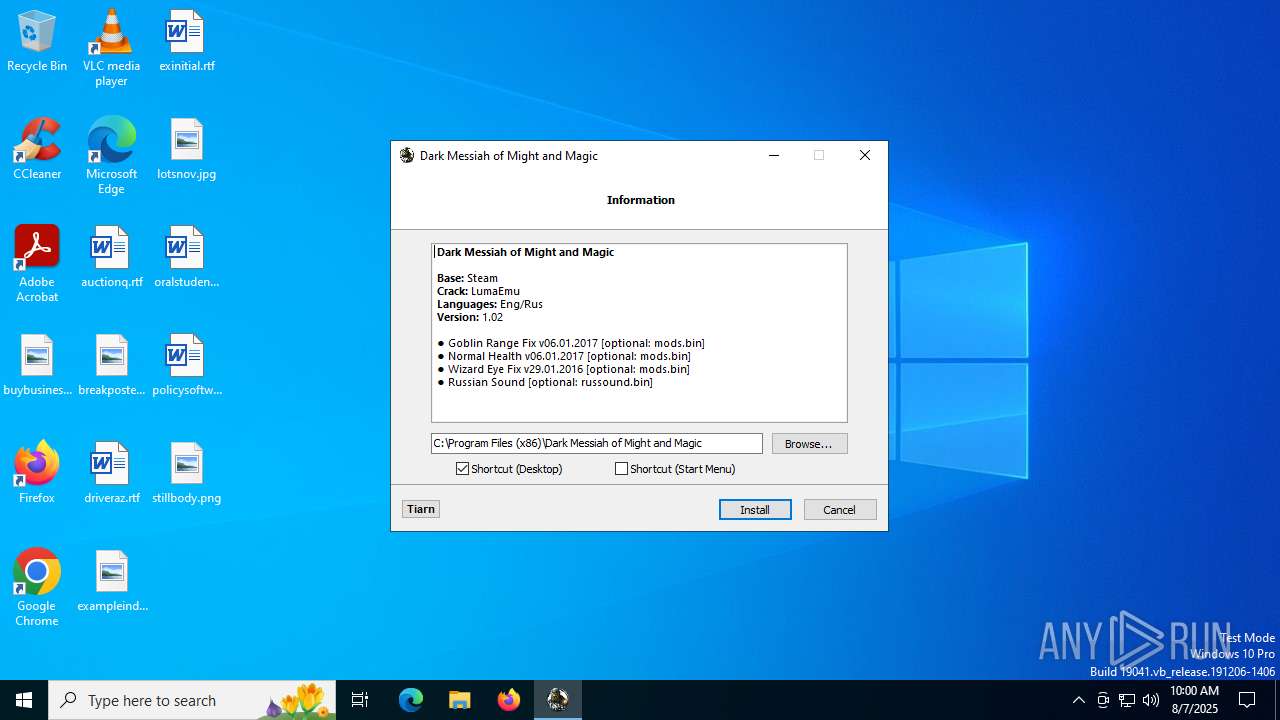
| FileDescription: | Dark Messiah of Might and Magic Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Dark Messiah of Might and Magic |
| ProductVersion: | 1.02 |
Total processes
149
Monitored processes
13
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 892 | "C:\Users\admin\AppData\Local\Temp\is-OSFPF.tmp\Setup.tmp" /SL5="$B02EA,1672120,916480,C:\Users\admin\AppData\Local\Temp\Setup.exe" /SPAWNWND=$70324 /NOTIFYWND=$702BE | C:\Users\admin\AppData\Local\Temp\is-OSFPF.tmp\Setup.tmp | Setup.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1808 | "C:\Program Files (x86)\Dark Messiah of Might and Magic\7z.exe" x "C:\Users\admin\AppData\Local\Temp\data1.bin" -y -pHr355BpPQc3J | C:\Program Files (x86)\Dark Messiah of Might and Magic\7z.exe | — | Setup.tmp | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Console Exit code: 2 Version: 23.01 Modules
| |||||||||||||||
| 1864 | "C:\Program Files (x86)\Dark Messiah of Might and Magic\7z.exe" x "C:\Users\admin\AppData\Local\Temp\mods.bin" -y -pHr355BpPQc3J | C:\Program Files (x86)\Dark Messiah of Might and Magic\7z.exe | — | Setup.tmp | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Console Exit code: 2 Version: 23.01 Modules
| |||||||||||||||
| 2716 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" /SPAWNWND=$70324 /NOTIFYWND=$702BE | C:\Users\admin\AppData\Local\Temp\Setup.exe | Setup.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Dark Messiah of Might and Magic Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3908 | "C:\Users\admin\AppData\Local\Temp\is-T50JL.tmp\Setup.tmp" /SL5="$702BE,1672120,916480,C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-T50JL.tmp\Setup.tmp | — | Setup.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3964 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4168 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5808 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Dark Messiah of Might and Magic Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 6356 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
789
Read events
787
Write events
1
Delete events
1
Modification events
| (PID) Process: | (892) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\UbiSoft\Dark Messiah of Might and Magic |
| Operation: | write | Name: | mm_gamma_already_set |
Value: 1 | |||
| (PID) Process: | (892) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Keyboard Layouts\0000040c |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
7
Suspicious files
0
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 892 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-S8GHP.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 892 | Setup.tmp | C:\Program Files (x86)\Dark Messiah of Might and Magic\is-MQ1RI.tmp | executable | |
MD5:4E35A902CA8ED1C3D4551B1A470C4655 | SHA256:77222E81CB7004E8C3E077AADA02B555A3D38FB05B50C64AFD36CA230A8FD5B9 | |||
| 892 | Setup.tmp | C:\Program Files (x86)\Dark Messiah of Might and Magic\7z.exe | executable | |
MD5:9A1DD1D96481D61934DCC2D568971D06 | SHA256:8CEBB25E240DB3B6986FCAED6BC0B900FA09DAD763A56FB71273529266C5C525 | |||
| 892 | Setup.tmp | C:\Program Files (x86)\Dark Messiah of Might and Magic\7z.dll | executable | |
MD5:4E35A902CA8ED1C3D4551B1A470C4655 | SHA256:77222E81CB7004E8C3E077AADA02B555A3D38FB05B50C64AFD36CA230A8FD5B9 | |||
| 892 | Setup.tmp | C:\Program Files (x86)\Dark Messiah of Might and Magic\is-0AGVP.tmp | executable | |
MD5:9A1DD1D96481D61934DCC2D568971D06 | SHA256:8CEBB25E240DB3B6986FCAED6BC0B900FA09DAD763A56FB71273529266C5C525 | |||
| 5808 | Setup.exe | C:\Users\admin\AppData\Local\Temp\is-T50JL.tmp\Setup.tmp | executable | |
MD5:54563EF52C049F57D196FC8FB7E6F74B | SHA256:A73CF57EAD0CC746B34DDFA63393D8E4E4E784D1B7402738D9EE09A0C08BEAD2 | |||
| 2716 | Setup.exe | C:\Users\admin\AppData\Local\Temp\is-OSFPF.tmp\Setup.tmp | executable | |
MD5:54563EF52C049F57D196FC8FB7E6F74B | SHA256:A73CF57EAD0CC746B34DDFA63393D8E4E4E784D1B7402738D9EE09A0C08BEAD2 | |||
| 892 | Setup.tmp | C:\Users\admin\Desktop\Dark Messiah of Might and Magic.lnk | lnk | |
MD5:519095FF727A27A01F4E5B98BA1BABC3 | SHA256:0D81CF08B9C04DC5273C09F3C1D0C21D19CDFD36CF2066AC86D0D2EB310E1439 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2460 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.11:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6980 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6980 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2596 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2460 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2460 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.216.77.11:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |