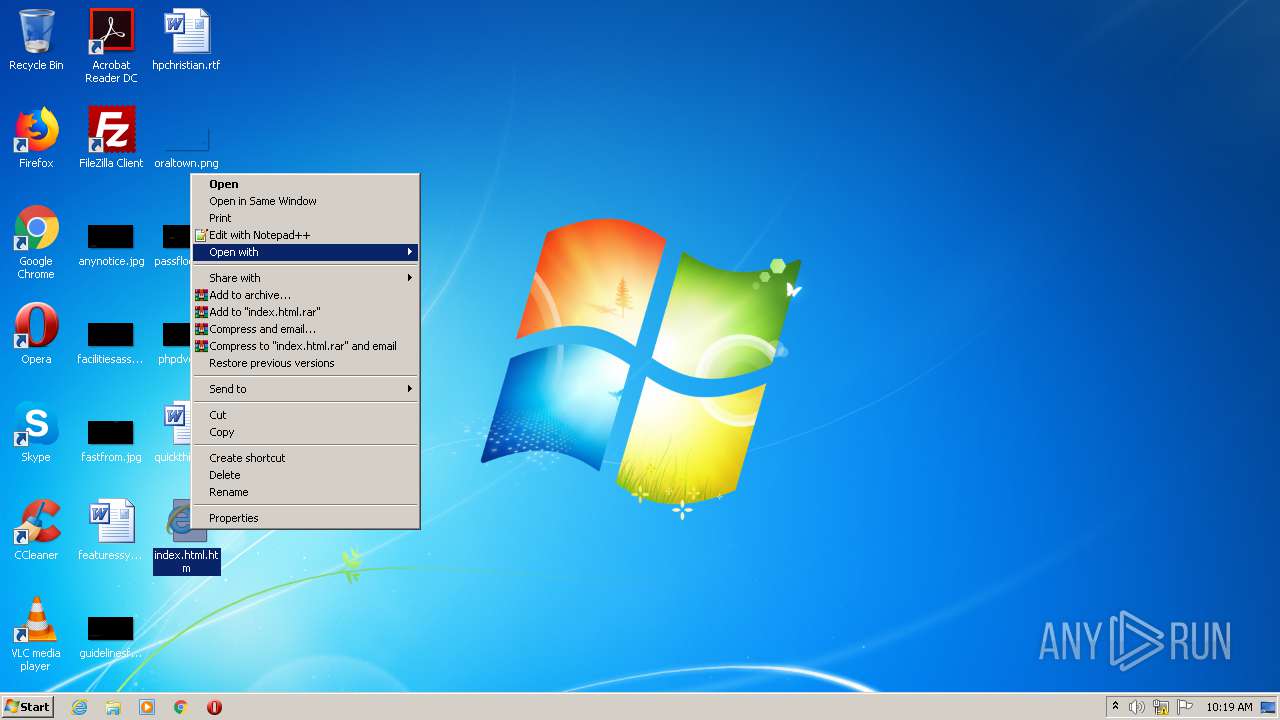
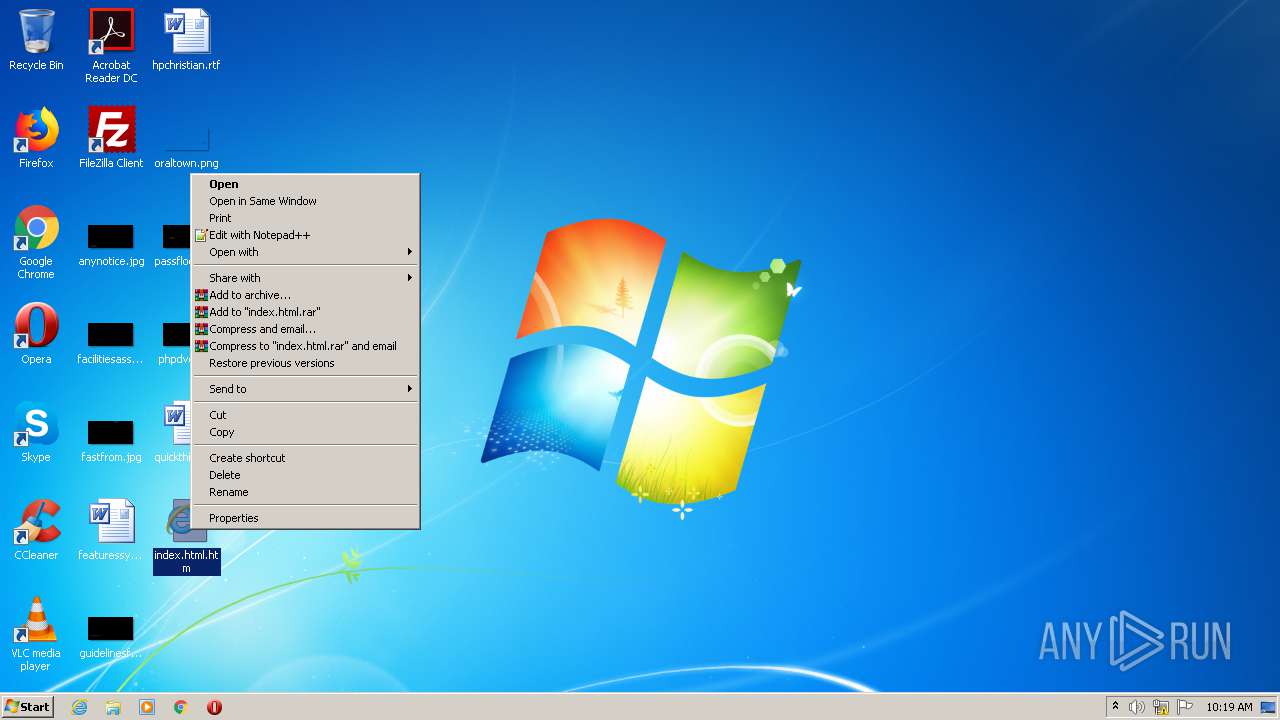
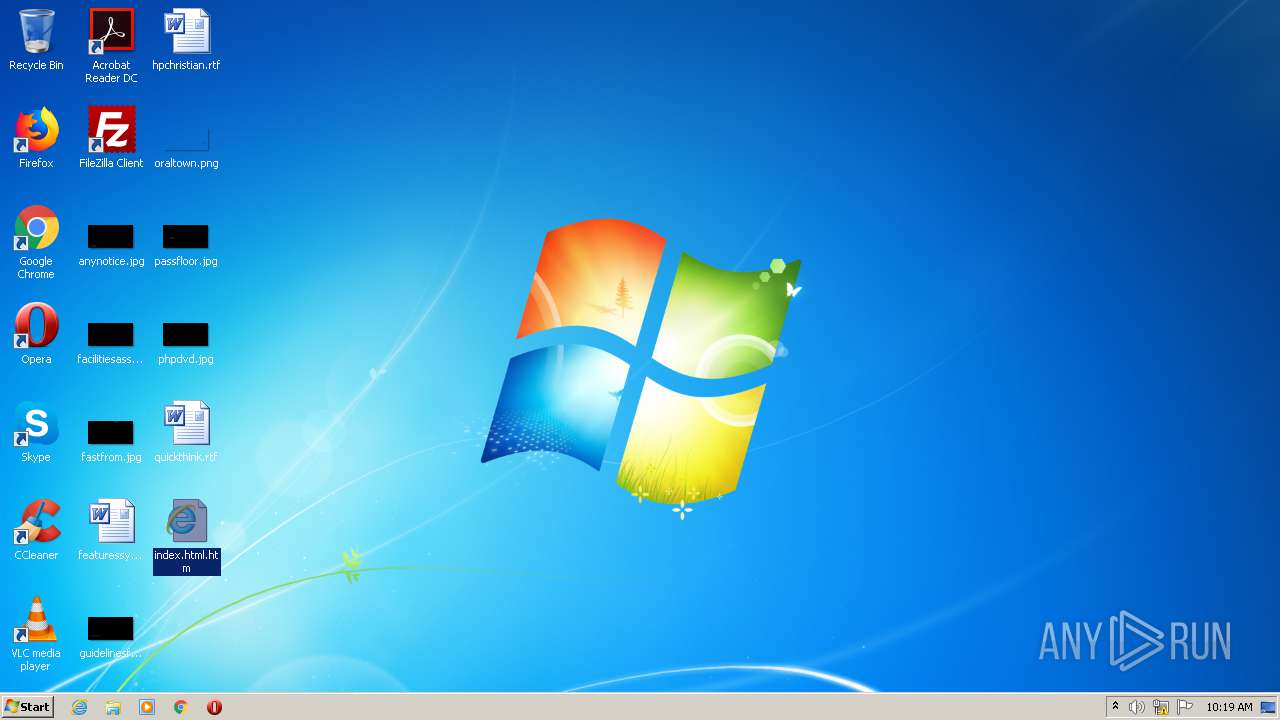
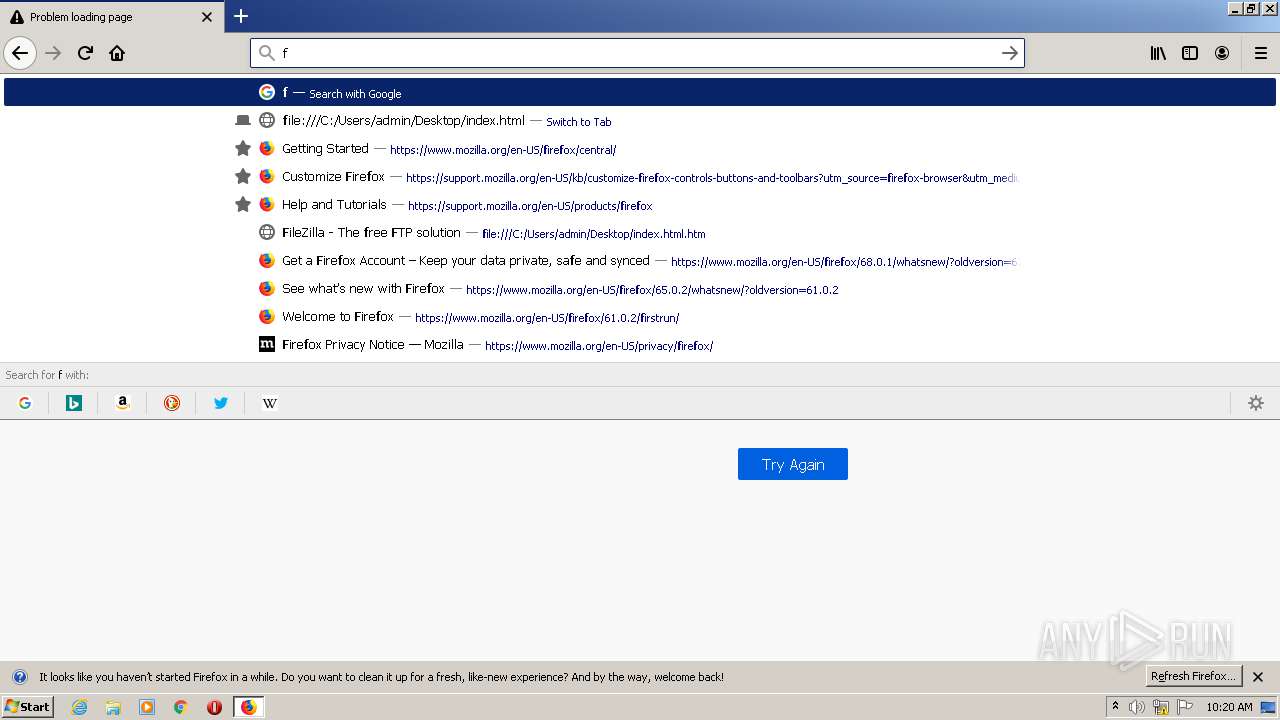
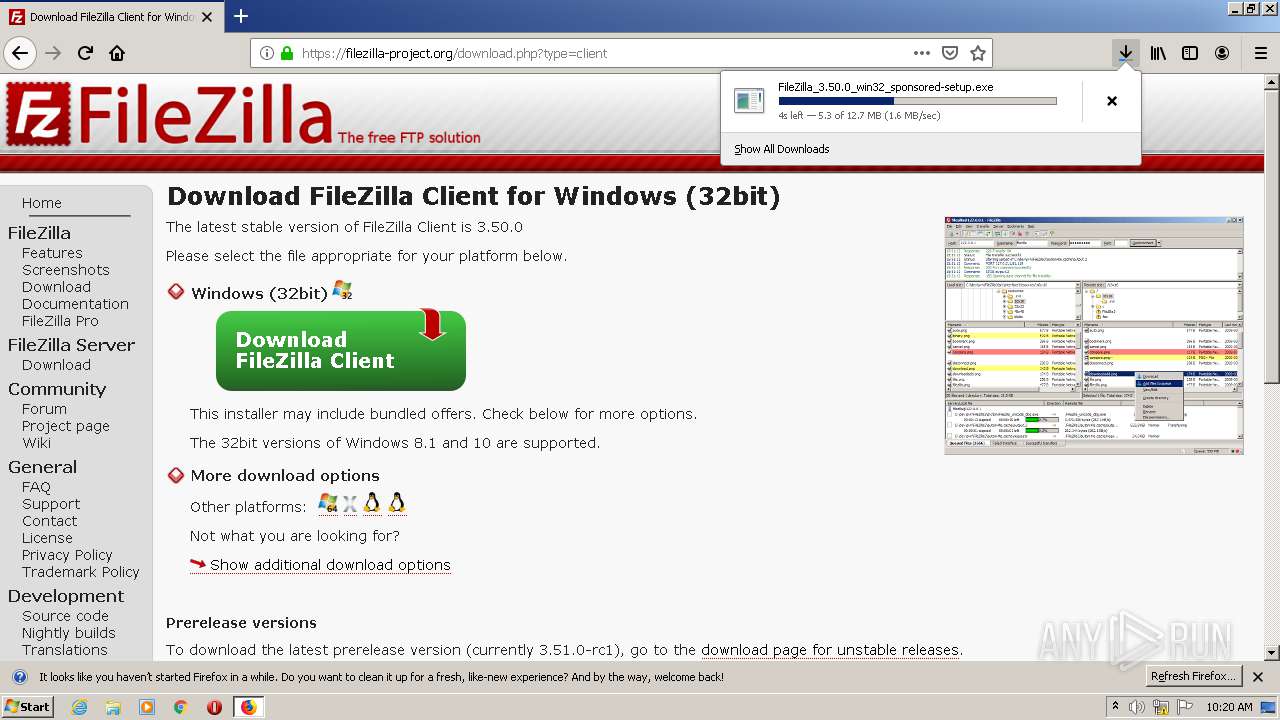
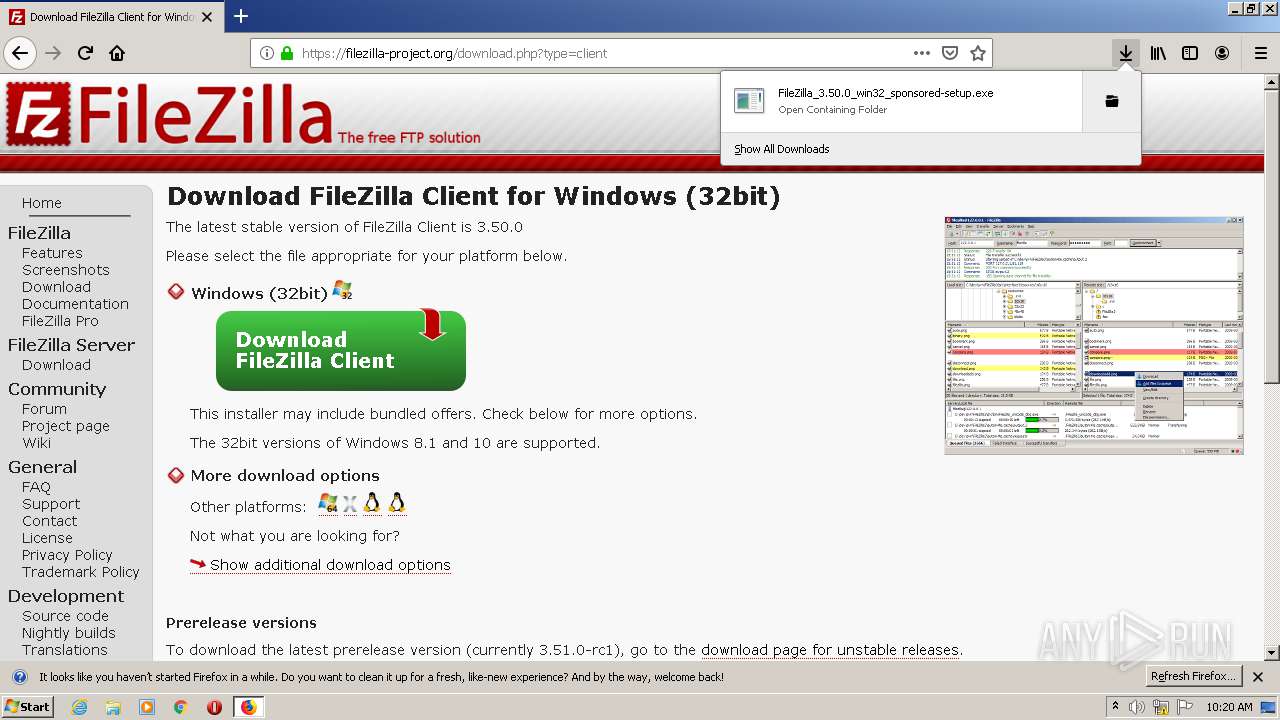
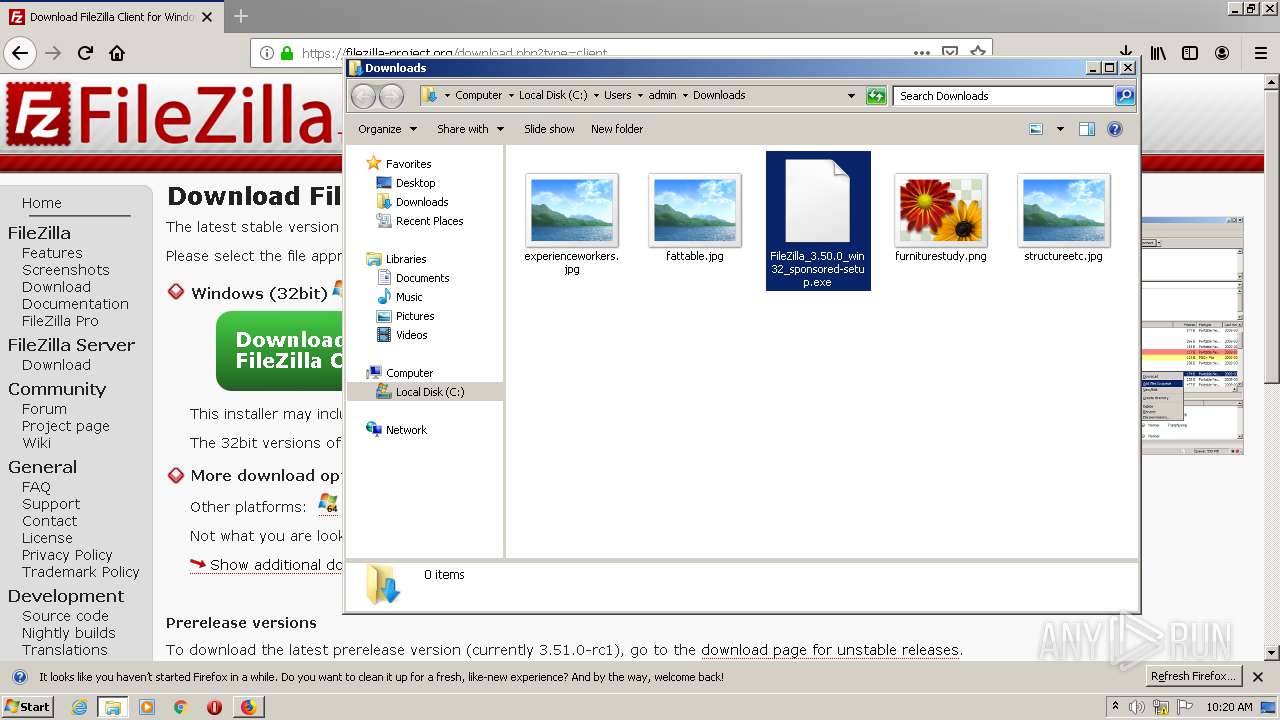
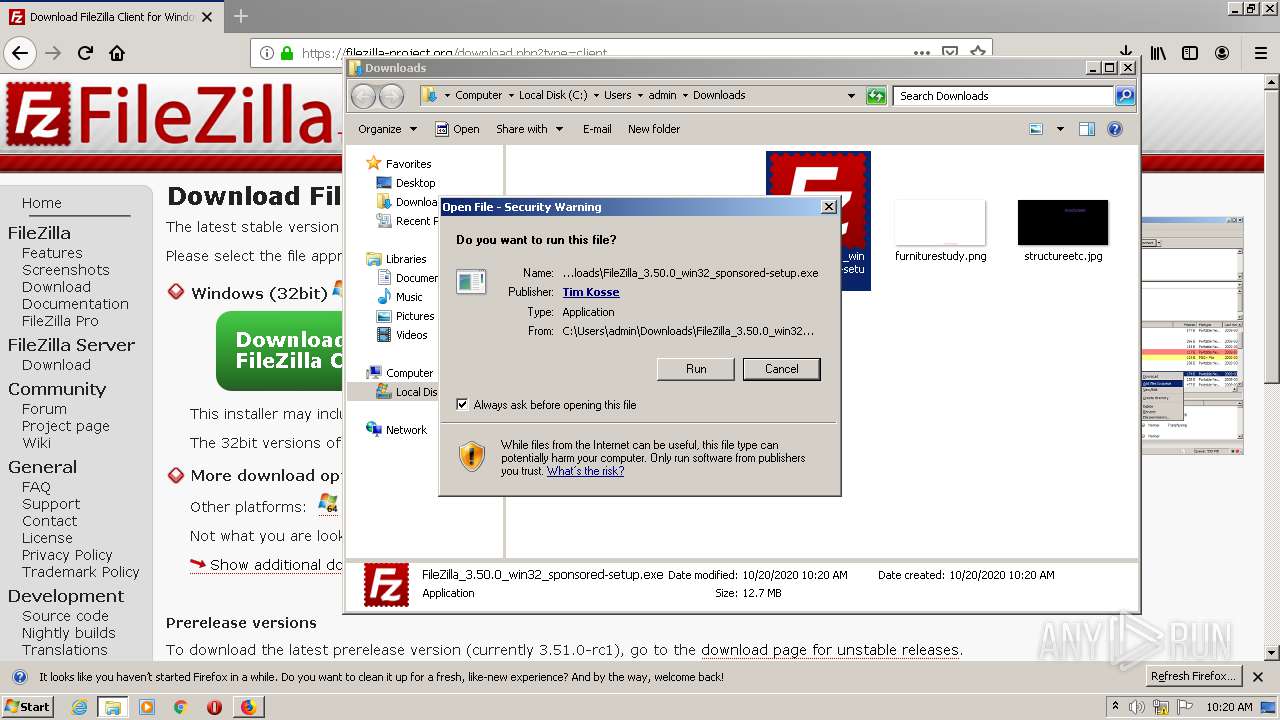
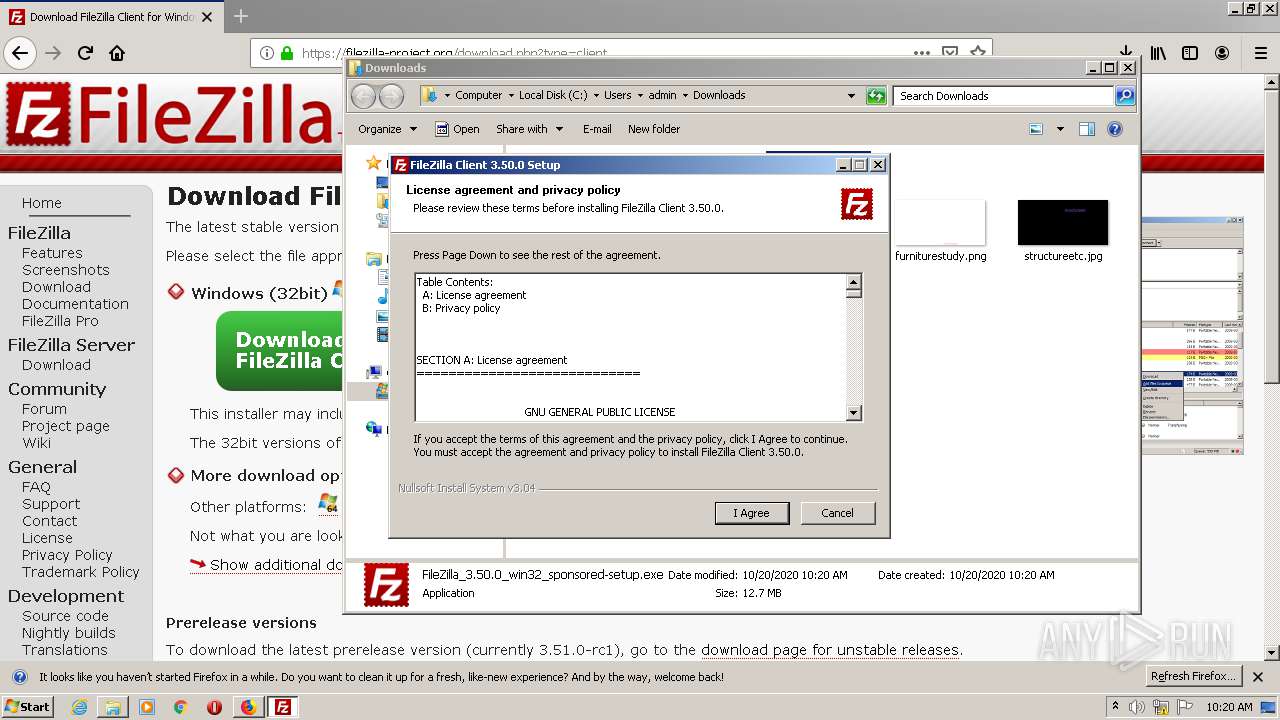
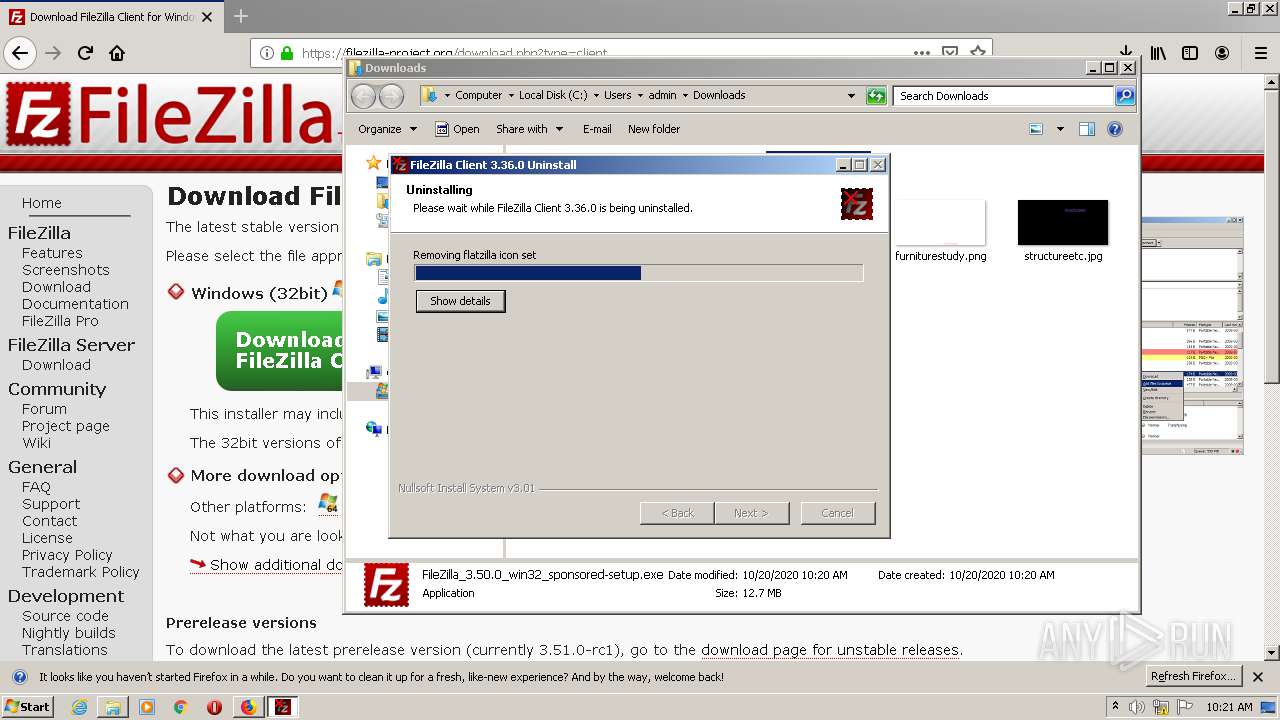
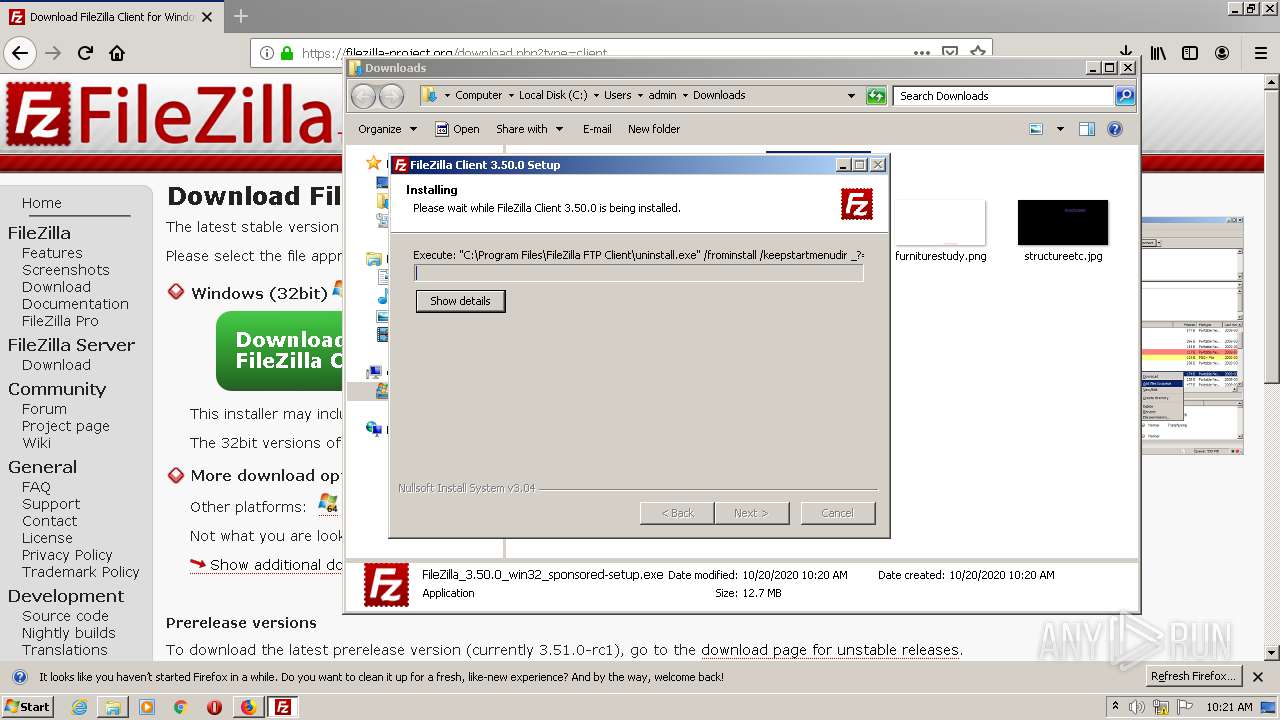
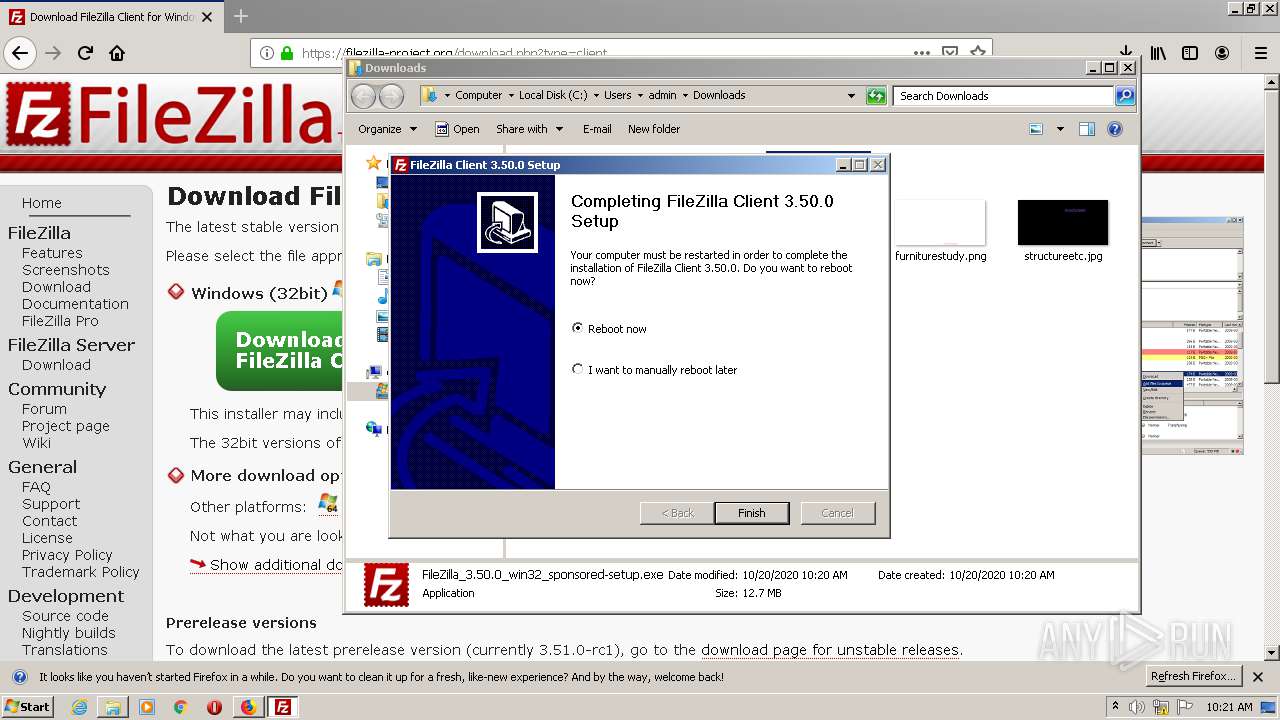
| download: | index.html |
| Full analysis: | https://app.any.run/tasks/739a7155-9831-407a-bc01-c3454ffba8f3 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 09:19:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | F0CC7078E97C4284B705D149018EB491 |
| SHA1: | 4866BB903E792CEF2E974D99B5E489DF6A5CAEB7 |
| SHA256: | CDE72BA3C4783E30C3072C70A3B6F77B773B423A24841AAA4FFCEBE6129D47A7 |
| SSDEEP: | 192:zT/4gdv/eUUFzHbIm5B0aS4VlS0UFJc6VhEDuu5:zb42/apHbLBNS4V40U46y |
MALICIOUS
Runs injected code in another process
- iexplore.exe (PID: 1860)
Application was injected by another process
- dllhost.exe (PID: 1732)
Application was dropped or rewritten from another process
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 2920)
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Loads dropped or rewritten executable
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 2920)
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
- uninstall.exe (PID: 1864)
Changes the autorun value in the registry
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Changes settings of System certificates
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Actions looks like stealing of personal data
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
SUSPICIOUS
Starts Internet Explorer
- explorer.exe (PID: 392)
Creates files in the user directory
- explorer.exe (PID: 392)
Executable content was dropped or overwritten
- firefox.exe (PID: 2176)
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 2920)
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
- uninstall.exe (PID: 1864)
Application launched itself
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 2920)
Reads Internet Cache Settings
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Reads internet explorer settings
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Creates files in the program directory
- uninstall.exe (PID: 1864)
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Creates a software uninstall entry
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Adds / modifies Windows certificates
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Reads Environment values
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
INFO
Changes internet zones settings
- iexplore.exe (PID: 1860)
Reads Internet Cache Settings
- iexplore.exe (PID: 2132)
- firefox.exe (PID: 2176)
- iexplore.exe (PID: 1860)
Application launched itself
- firefox.exe (PID: 2064)
- iexplore.exe (PID: 1860)
- iexplore.exe (PID: 1732)
- firefox.exe (PID: 2176)
Reads CPU info
- firefox.exe (PID: 2176)
Manual execution by user
- firefox.exe (PID: 2064)
Reads settings of System Certificates
- iexplore.exe (PID: 1860)
- explorer.exe (PID: 392)
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Reads internet explorer settings
- iexplore.exe (PID: 1732)
Creates files in the program directory
- firefox.exe (PID: 2176)
Changes settings of System certificates
- iexplore.exe (PID: 1860)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1860)
Creates files in the user directory
- firefox.exe (PID: 2176)
Dropped object may contain Bitcoin addresses
- FileZilla_3.50.0_win32_sponsored-setup.exe (PID: 1748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| ContentType: | text/html; charset=utf-8 |
|---|---|
| Keywords: | FileZilla, ftp, sftp, client, server, open source |
| viewport: | width=device-width, initial-scale=0.7 |
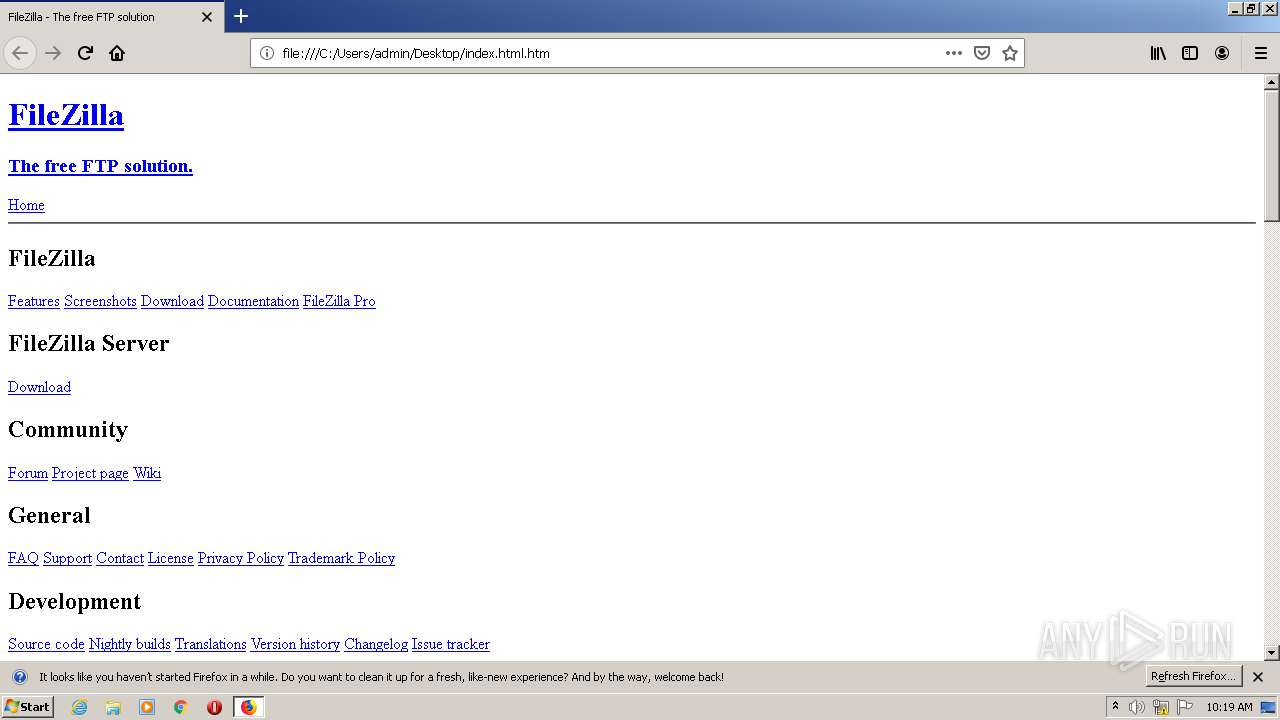
| Title: | FileZilla - The free FTP solution |
| Description: | FileZilla - The free FTP solution for both client and server. Filezilla is open source software distributed free of charge. |
Total processes
60
Monitored processes
16
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1860 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1732 | dllhost.exe | svchost.exe | |||||||||||||
Integrity Level: UNKNOWN Exit code: 0 Modules
| |||||||||||||||
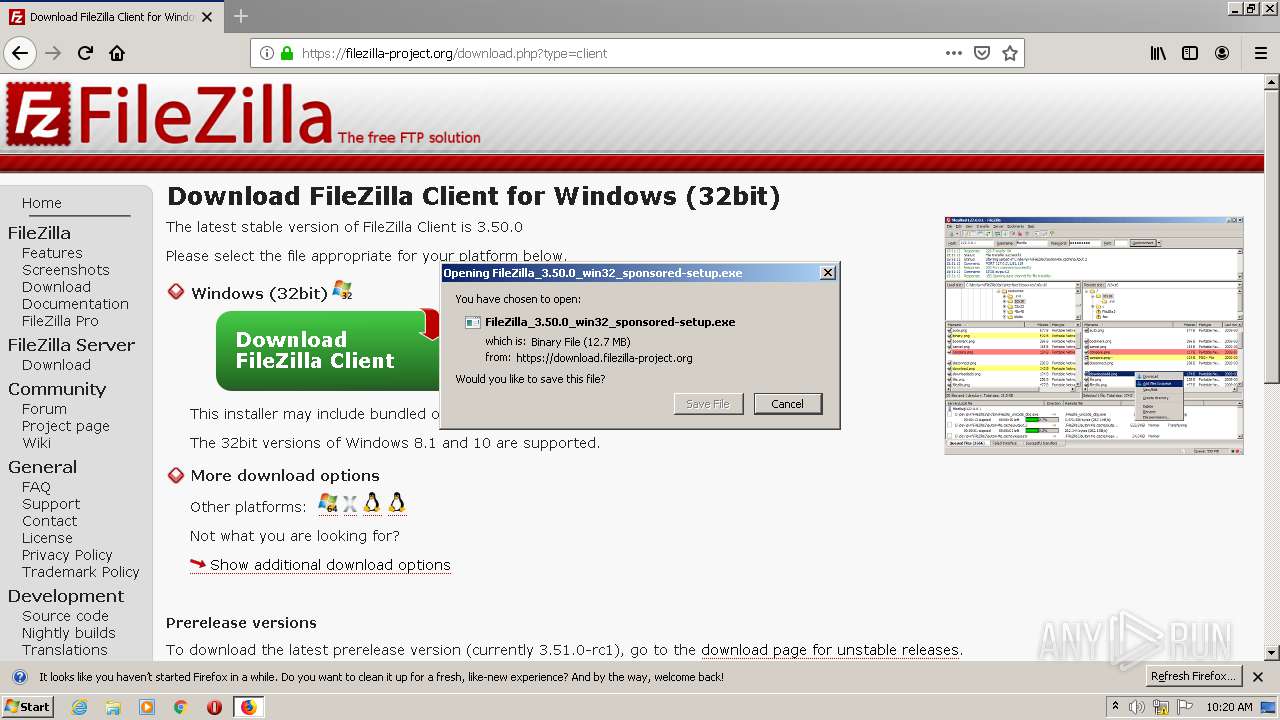
| 1748 | "C:\Users\admin\Downloads\FileZilla_3.50.0_win32_sponsored-setup.exe" /UAC:1801A6 /NCRC | C:\Users\admin\Downloads\FileZilla_3.50.0_win32_sponsored-setup.exe | FileZilla_3.50.0_win32_sponsored-setup.exe | ||||||||||||
User: admin Company: Tim Kosse Integrity Level: HIGH Description: FileZilla FTP Client Exit code: 0 Version: 3.50.0 Modules
| |||||||||||||||
| 1860 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\Desktop\index.html.htm | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1864 | "C:\Program Files\FileZilla FTP Client\uninstall.exe" /frominstall /keepstartmenudir _?=C:\Program Files\FileZilla FTP Client | C:\Program Files\FileZilla FTP Client\uninstall.exe | FileZilla_3.50.0_win32_sponsored-setup.exe | ||||||||||||
User: admin Company: Tim Kosse Integrity Level: HIGH Description: FileZilla FTP Client Exit code: 0 Version: 3.36.0 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Mozilla Firefox\firefox.exe" -osint -url "C:\Users\admin\Desktop\index.html.htm" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1860 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Mozilla Firefox\firefox.exe" -osint -url C:\Users\admin\Desktop\index.html.htm | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2176.27.666598009\372816456" -childID 4 -isForBrowser -prefsHandle 3848 -prefMapHandle 3852 -prefsLen 7733 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2176 "\\.\pipe\gecko-crash-server-pipe.2176" 3864 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
Total events
5 783
Read events
5 479
Write events
284
Delete events
20
Modification events
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 761345440 | |||
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30844610 | |||
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
35
Suspicious files
234
Text files
824
Unknown types
99
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1860 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1860 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF8687A603BA029104.TMP | — | |
MD5:— | SHA256:— | |||
| 1860 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF722C89647DC44A1B.TMP | — | |
MD5:— | SHA256:— | |||
| 1860 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFFB2D170391191F55.TMP | — | |
MD5:— | SHA256:— | |||
| 1860 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE272BF059127E5B9.TMP | — | |
MD5:— | SHA256:— | |||
| 2176 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 2176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 2176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 2176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
69
DNS requests
136
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1860 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1860 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2176 | firefox.exe | POST | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
2176 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2176 | firefox.exe | POST | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core | US | der | 471 b | whitelisted |
2176 | firefox.exe | POST | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
2176 | firefox.exe | POST | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
2176 | firefox.exe | POST | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
1860 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2176 | firefox.exe | POST | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1860 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2176 | firefox.exe | 49.12.121.47:443 | forum.filezilla-project.org | — | IN | suspicious |
2176 | firefox.exe | 99.86.7.78:443 | snippets.cdn.mozilla.net | AT&T Services, Inc. | US | unknown |
2176 | firefox.exe | 216.58.206.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
1860 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2176 | firefox.exe | 172.217.21.238:443 | apis.google.com | Google Inc. | US | whitelisted |
2176 | firefox.exe | 172.217.21.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2176 | firefox.exe | 54.148.7.60:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
2176 | firefox.exe | 99.86.7.38:443 | tracking-protection.cdn.mozilla.net | AT&T Services, Inc. | US | malicious |
2176 | firefox.exe | 172.217.18.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
forum.filezilla-project.org |
| suspicious |
wiki.filezilla-project.org |
| suspicious |
sourceforge.net |
| whitelisted |
trac.filezilla-project.org |
| suspicious |
lib.filezilla-project.org |
| suspicious |
octochess.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |