| File name: | Sniffthem.exe |
| Full analysis: | https://app.any.run/tasks/013272a2-e4d3-4a67-9be7-dcd66f20d911 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | September 11, 2024, 00:43:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | E99986A942B4CF4DB99CED3206FF1354 |
| SHA1: | 0337568B859DE281C959C294EA71705E70788D4F |
| SHA256: | CDC7077FACB5FCA34AD8250AC87CCC8E4A8CE6319F9591A6BD1310E48B5397E3 |
| SSDEEP: | 6144:ahmprCOckOCExek/tPJxVbKx4QRPSIaMKKeB2TC5HRcHU1eXDHJ:mkXEsk/thxVbKxrRP4MKKY5xcH7XDJ |
MALICIOUS
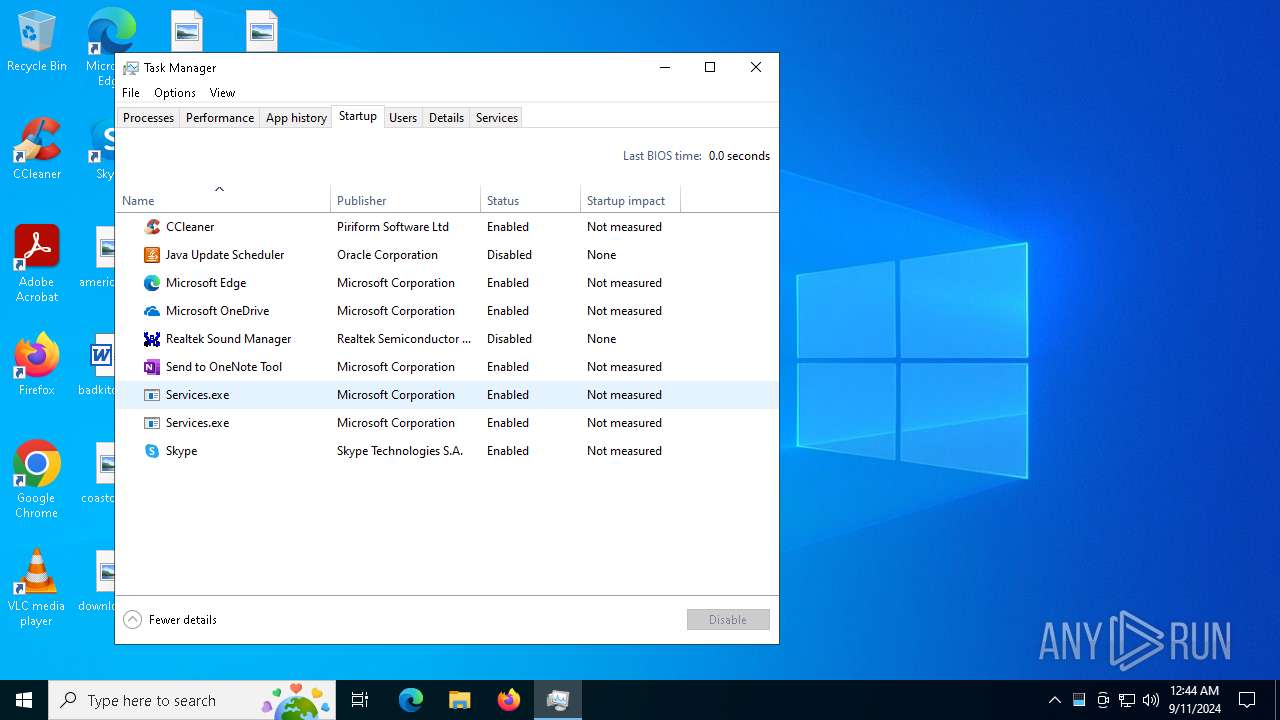
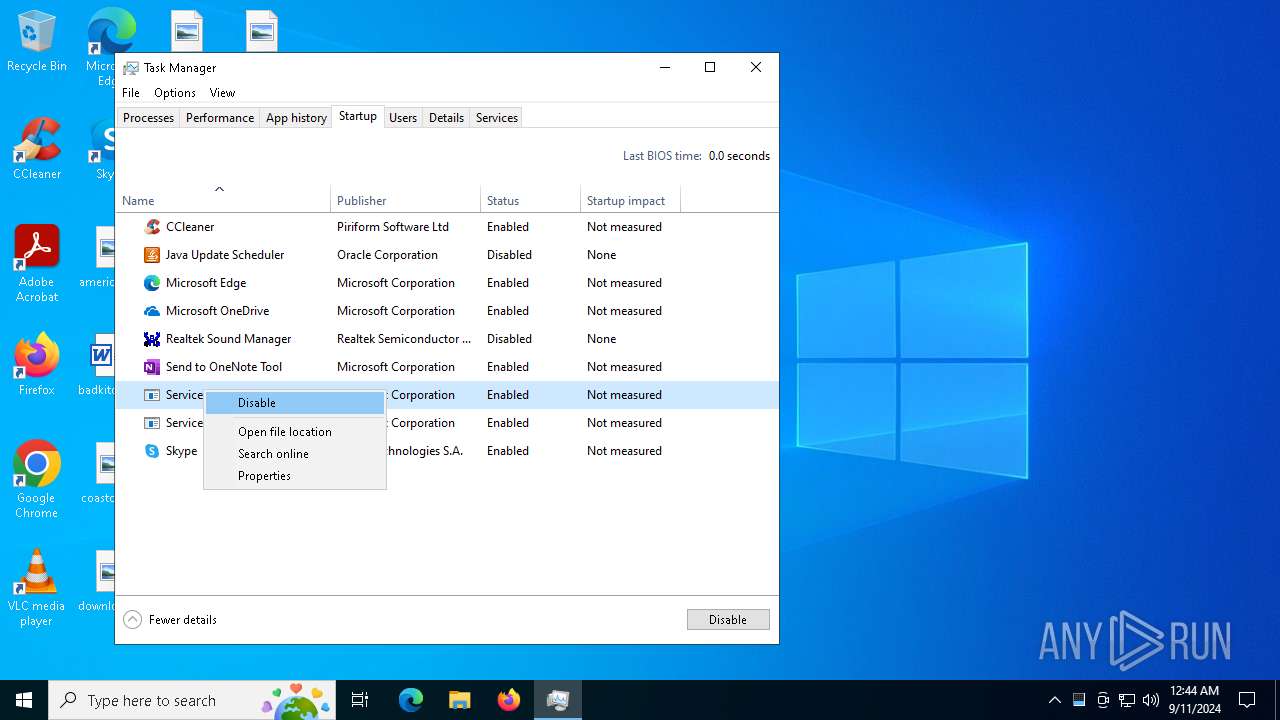
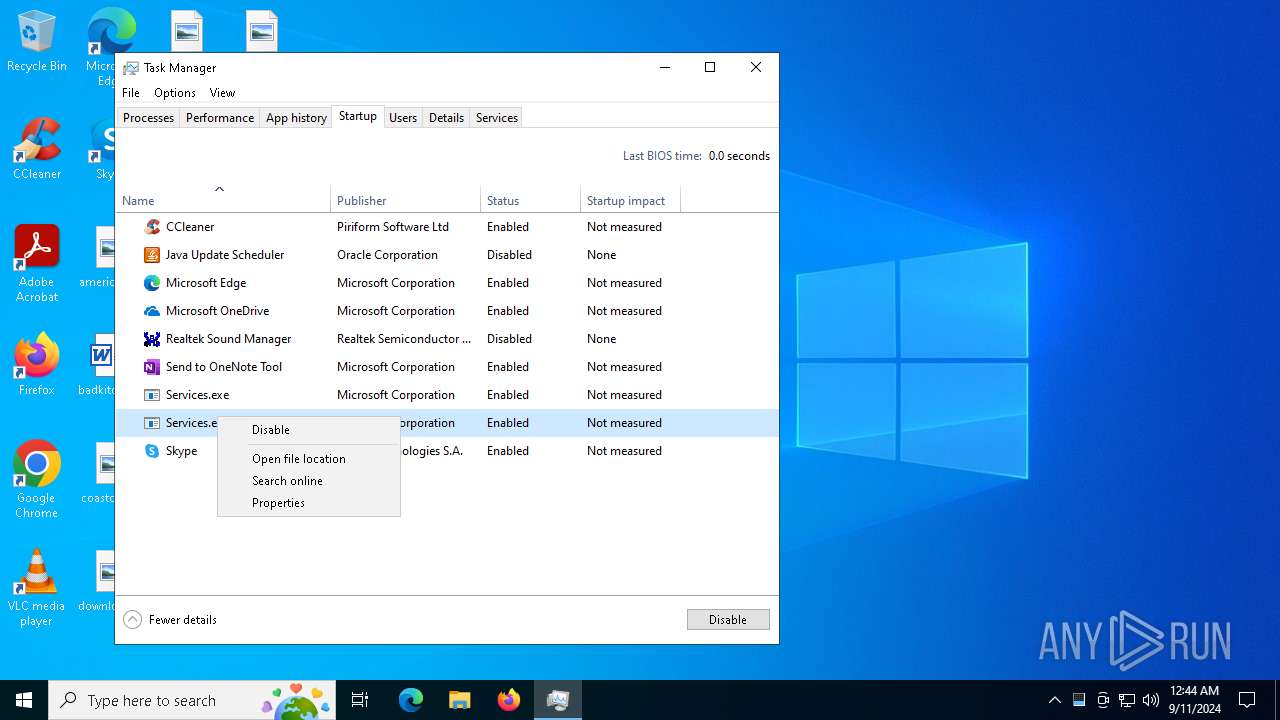
Changes the autorun value in the registry
- Sniffthem.exe (PID: 6176)
Create files in the Startup directory
- Sniffthem.exe (PID: 6176)
Application was injected by another process
- explorer.exe (PID: 4552)
SNIFFTHEM has been detected (SURICATA)
- svchost.exe (PID: 5388)
- explorer.exe (PID: 4552)
Runs injected code in another process
- svchost.exe (PID: 5388)
DIAMOTRIX has been detected (SURICATA)
- firefox.exe (PID: 6884)
- explorer.exe (PID: 4552)
- firefox.exe (PID: 7068)
- firefox.exe (PID: 964)
- firefox.exe (PID: 1020)
- firefox.exe (PID: 2640)
- firefox.exe (PID: 1164)
- firefox.exe (PID: 7016)
The DLL Hijacking
- WerFault.exe (PID: 1496)
- WerFault.exe (PID: 7072)
SUSPICIOUS
Starts a Microsoft application from unusual location
- Sniffthem.exe (PID: 6176)
Process drops legitimate windows executable
- Sniffthem.exe (PID: 6176)
Potential Corporate Privacy Violation
- svchost.exe (PID: 5388)
- explorer.exe (PID: 4552)
Executable content was dropped or overwritten
- Sniffthem.exe (PID: 6176)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 4552)
- firefox.exe (PID: 6884)
- firefox.exe (PID: 7068)
- firefox.exe (PID: 1020)
- firefox.exe (PID: 964)
- firefox.exe (PID: 2640)
- firefox.exe (PID: 1164)
- firefox.exe (PID: 7016)
Executes application which crashes
- firefox.exe (PID: 3144)
- firefox.exe (PID: 6016)
Loads DLL from Mozilla Firefox
- WerFault.exe (PID: 1496)
- WerFault.exe (PID: 7072)
INFO
Reads security settings of Internet Explorer
- svchost.exe (PID: 5388)
- explorer.exe (PID: 4552)
- Taskmgr.exe (PID: 7648)
Checks supported languages
- Sniffthem.exe (PID: 6176)
Checks proxy server information
- explorer.exe (PID: 4552)
- svchost.exe (PID: 5388)
- WerFault.exe (PID: 7072)
- WerFault.exe (PID: 1496)
Reads the computer name
- Sniffthem.exe (PID: 6176)
Creates files or folders in the user directory
- Sniffthem.exe (PID: 6176)
- explorer.exe (PID: 4552)
- WerFault.exe (PID: 1496)
- WerFault.exe (PID: 7072)
The process uses the downloaded file
- explorer.exe (PID: 4552)
Reads the software policy settings
- WerFault.exe (PID: 1496)
- WerFault.exe (PID: 7072)
Application launched itself
- firefox.exe (PID: 6696)
- firefox.exe (PID: 7068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:09:10 22:37:31+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 11 |
| CodeSize: | 135168 |
| InitializedDataSize: | 169472 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xeee0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.0.1 |
| ProductVersionNumber: | 1.2.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Unknown (1401) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Services.exe |
| FileVersion: | 1.2.0.1 |
| InternalName: | Services.exe |
| LegalCopyright: | Copyright (C) 2024 |
| OriginalFileName: | Services.exe |
| ProductName: | Services.exe |
| ProductVersion: | 1.2.0.1 |
Total processes
161
Monitored processes
20
Malicious processes
13
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2928 -childID 1 -isForBrowser -prefsHandle 2924 -prefMapHandle 2920 -prefsLen 30996 -prefMapSize 245487 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {76c638cf-90a0-40f2-8960-90319b560688} 7068 "\\.\pipe\gecko-crash-server-pipe.7068" 12fef560690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4564 -childID 2 -isForBrowser -prefsHandle 4560 -prefMapHandle 4556 -prefsLen 36351 -prefMapSize 245487 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {014de8a4-4aa6-497d-8bdd-bd65e421362e} 7068 "\\.\pipe\gecko-crash-server-pipe.7068" 12ff0d39a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1164 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5756 -childID 4 -isForBrowser -prefsHandle 5748 -prefMapHandle 5744 -prefsLen 31247 -prefMapSize 245487 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {55b662d9-715d-44c1-ac30-fb23ba2878e5} 7068 "\\.\pipe\gecko-crash-server-pipe.7068" 12ff4796a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1496 | C:\WINDOWS\system32\WerFault.exe -u -p 6016 -s 824 | C:\Windows\System32\WerFault.exe | firefox.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2640 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5740 -childID 3 -isForBrowser -prefsHandle 5728 -prefMapHandle 5724 -prefsLen 31247 -prefMapSize 245487 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9d119582-cc87-4cd7-be9d-f3d3a8cd03ec} 7068 "\\.\pipe\gecko-crash-server-pipe.7068" 12ff4796850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 3144 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5264 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 5256 -prefMapHandle 5212 -prefsLen 34801 -prefMapSize 245487 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {98c2a721-6dee-41f5-ab14-a8a2048c42c4} 7068 "\\.\pipe\gecko-crash-server-pipe.7068" 12ff1c7ad10 utility | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 3221225477 Version: 123.0 Modules
| |||||||||||||||
| 4552 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1073807364 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5388 | C:\WINDOWS\system32\svchost.exe | C:\Windows\System32\svchost.exe | Sniffthem.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 1073807364 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6016 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2292 -parentBuildID 20240213221259 -prefsHandle 2284 -prefMapHandle 2272 -prefsLen 30580 -prefMapSize 245487 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {862110ef-6f35-4714-8573-036a9895663f} 7068 "\\.\pipe\gecko-crash-server-pipe.7068" 12fdd180910 socket | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 3221225477 Version: 123.0 Modules
| |||||||||||||||
| 6176 | "C:\Users\admin\AppData\Local\Temp\Sniffthem.exe" | C:\Users\admin\AppData\Local\Temp\Sniffthem.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services.exe Exit code: 0 Version: 1.2.0.1 Modules
| |||||||||||||||
Total events
35 650
Read events
35 576
Write events
64
Delete events
10
Modification events
| (PID) Process: | (6176) Sniffthem.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Services |
Value: C:\Users\admin\AppData\Roaming\{2F33566DA0B91573532102}\{2F33566DA0B91573532102}.exe | |||
| (PID) Process: | (5388) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5388) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\StartupFolder |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | InstalledWin32AppsRevision |
Value: {B1147704-1042-4E16-848C-FA76423A9A69} | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: ADE7E06600000000 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | write | Name: | Classes |
Value: .accdb | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | write | Name: | ~reserved~ |
Value: 0800000000000600 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | Mode |
Value: 1 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | LogicalViewMode |
Value: 3 | |||
Executable files
1
Suspicious files
165
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6176 | Sniffthem.exe | C:\Users\admin\AppData\Local\Temp\TH9D13.tmp | binary | |
MD5:6022D8188BC7BD49A76F2DBA61EBADD8 | SHA256:5231D360C8364DF92828FEAA89A66990F682FECB645A32B029A4F5F7188D328D | |||
| 6176 | Sniffthem.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\MicrosoftEdgeUpdate.lnk | binary | |
MD5:BEAAC1FBAA729489B4F1DAEC1F070E5A | SHA256:CE9FC83505E8A121A0973174B9AAD769CA7286373F433CD06A760EF74B946928 | |||
| 7068 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7068 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db | binary | |
MD5:F6BF25A88C130CE18DF5117B06E0720E | SHA256:6B5DF5CB168AE96406FF48E102C0952959210228EFAB9ACE35599692EBE743D1 | |||
| 7068 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7068 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7068 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7068 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7068 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:A9FC73DB5C216AA16599D649960AEF3C | SHA256:4F3AC02304D08FE24FEF4DF418B5305310A1A667EF84FA7928B1E192EAB95C56 | |||
| 7068 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
141
DNS requests
124
Threats
57
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4552 | explorer.exe | POST | 200 | 176.111.174.140:80 | http://176.111.174.140/api.php?{2F33566DA0B91573532102} | unknown | — | — | unknown |
7068 | firefox.exe | POST | 200 | 2.16.202.121:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6224 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7068 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7068 | firefox.exe | POST | 200 | 2.16.202.121:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
7068 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/s/wr3/XjA | unknown | — | — | unknown |
7068 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7068 | firefox.exe | POST | 200 | 2.16.202.121:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
7068 | firefox.exe | POST | 200 | 2.16.202.121:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
7068 | firefox.exe | POST | 200 | 2.16.202.121:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6404 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6224 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5388 | svchost.exe | 176.111.174.140:80 | — | Chang Way Technologies Co. Limited | RU | malicious |
4552 | explorer.exe | 176.111.174.140:80 | — | Chang Way Technologies Co. Limited | RU | malicious |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1744 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1744 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5388 | svchost.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
5388 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
5388 | svchost.exe | A Network Trojan was detected | LOADER [ANY.RUN] Sniffthem/Tnaket downloads via HTTP GET request (UA) |
5388 | svchost.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
4552 | explorer.exe | A Network Trojan was detected | LOADER [ANY.RUN] Sniffthem/Tnaket downloads via HTTP GET request (UA) |
4552 | explorer.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
4552 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
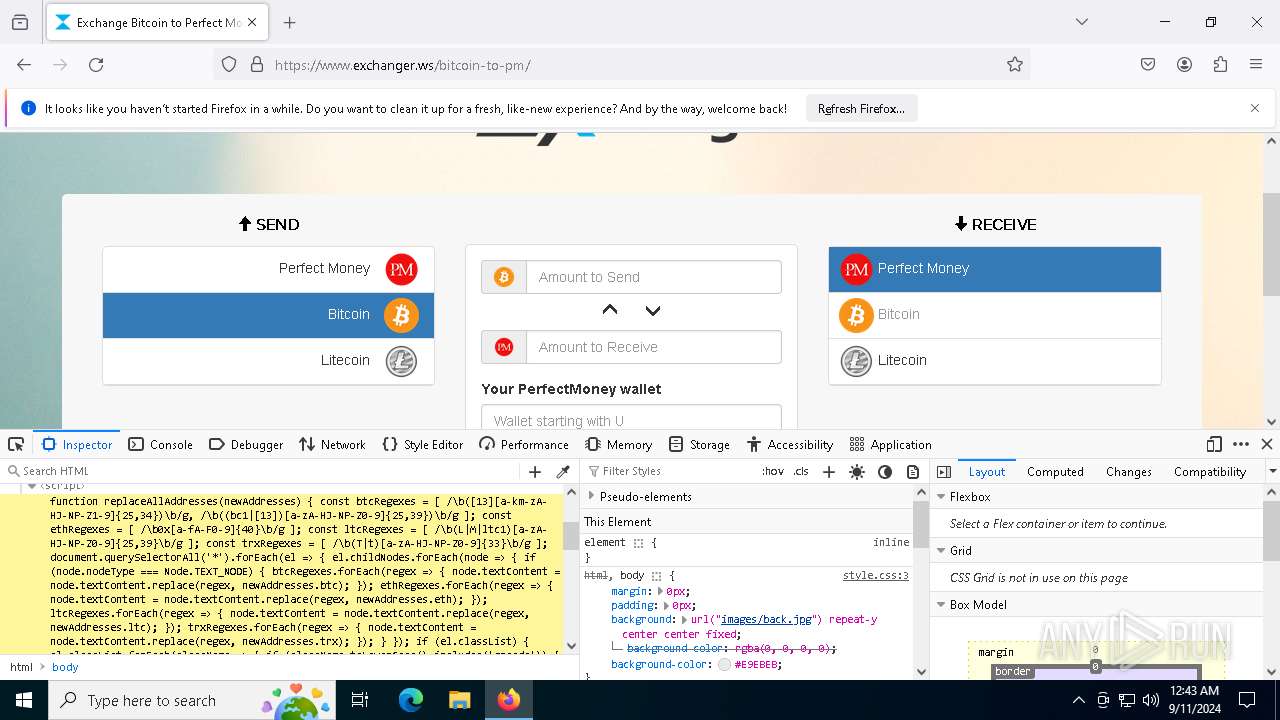
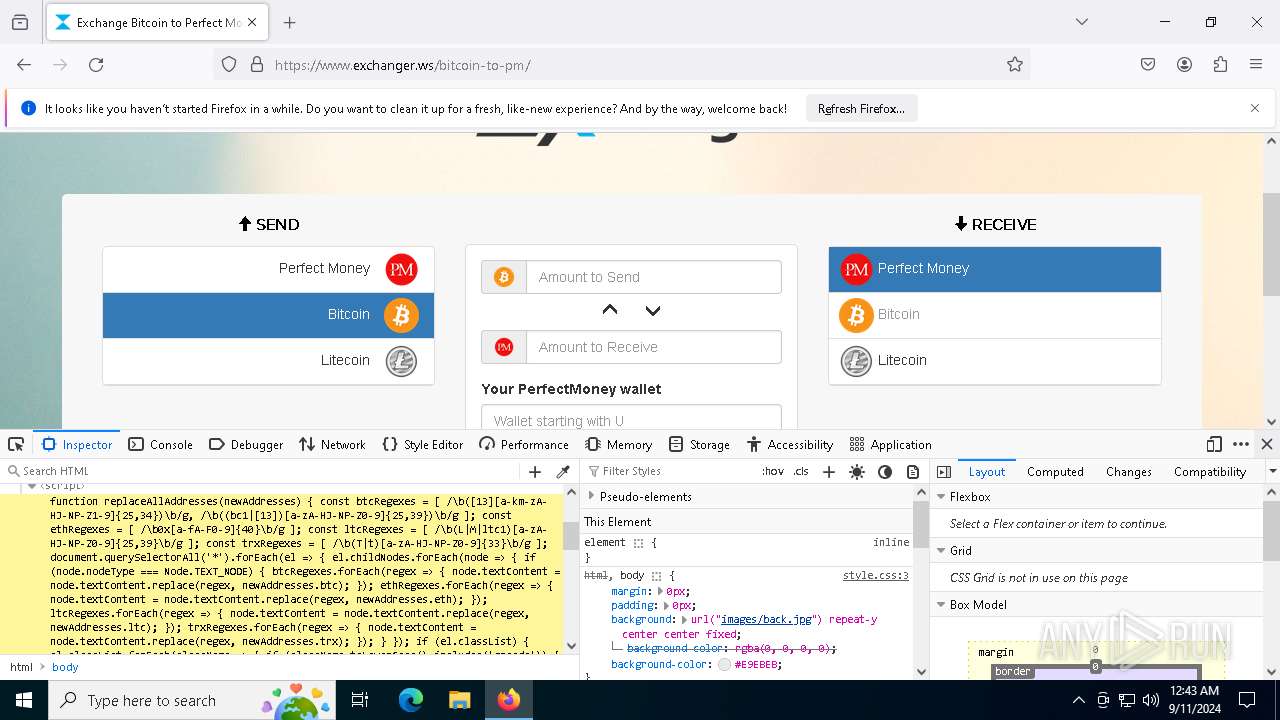
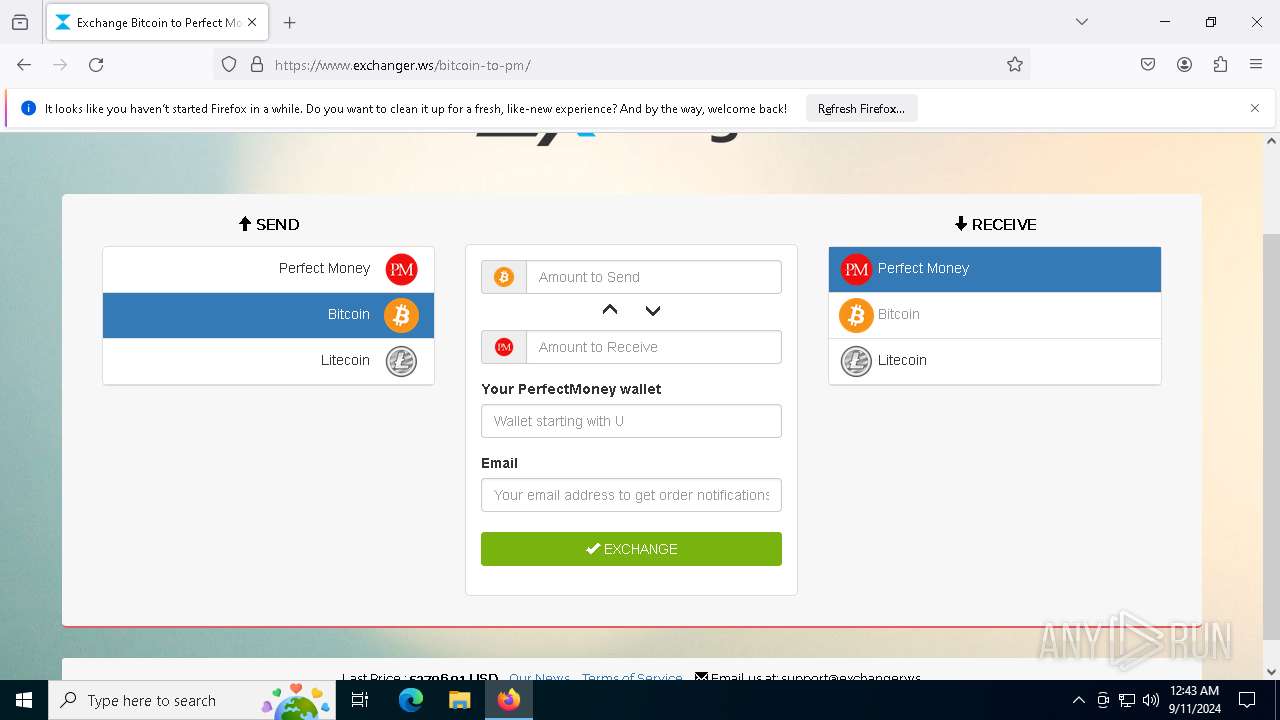
4552 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Diamotrix Clipper Wallet Request (User-Agent) |
4552 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Diamotrix Clipper Wallet Request URI Observed (POST) |
4552 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Diamotrix Clipper Wallet Request (User-Agent) |