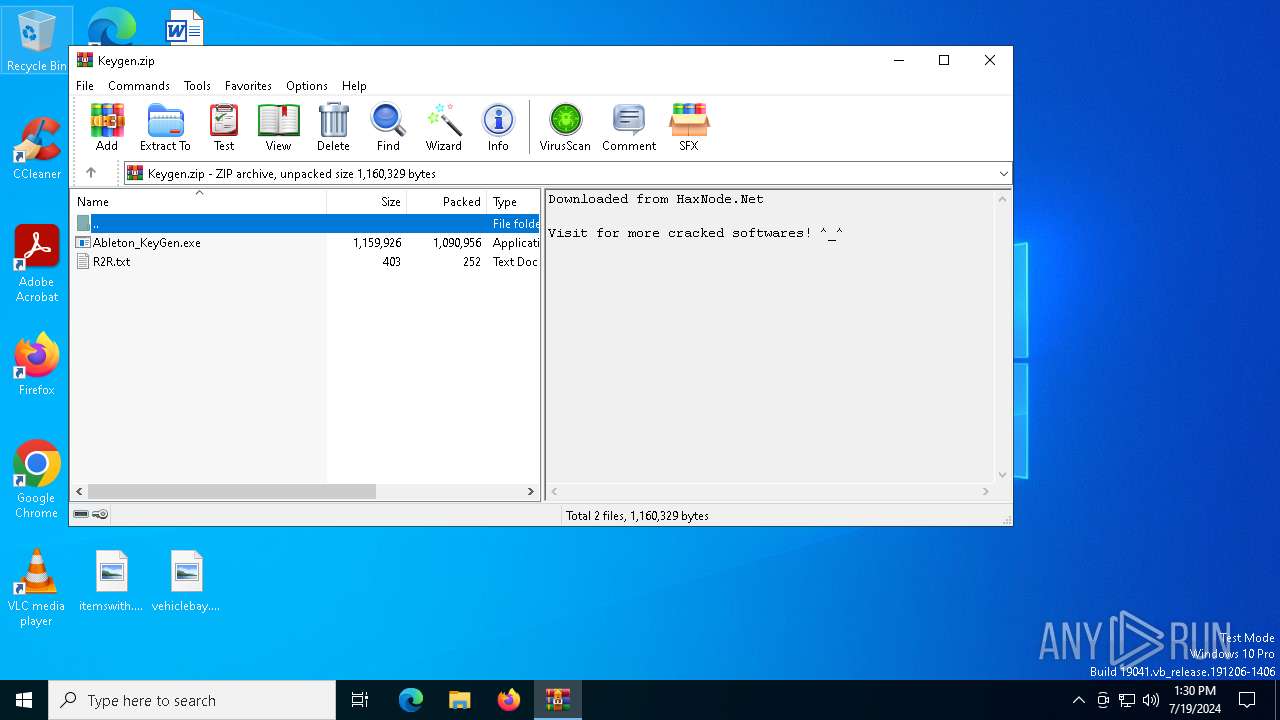
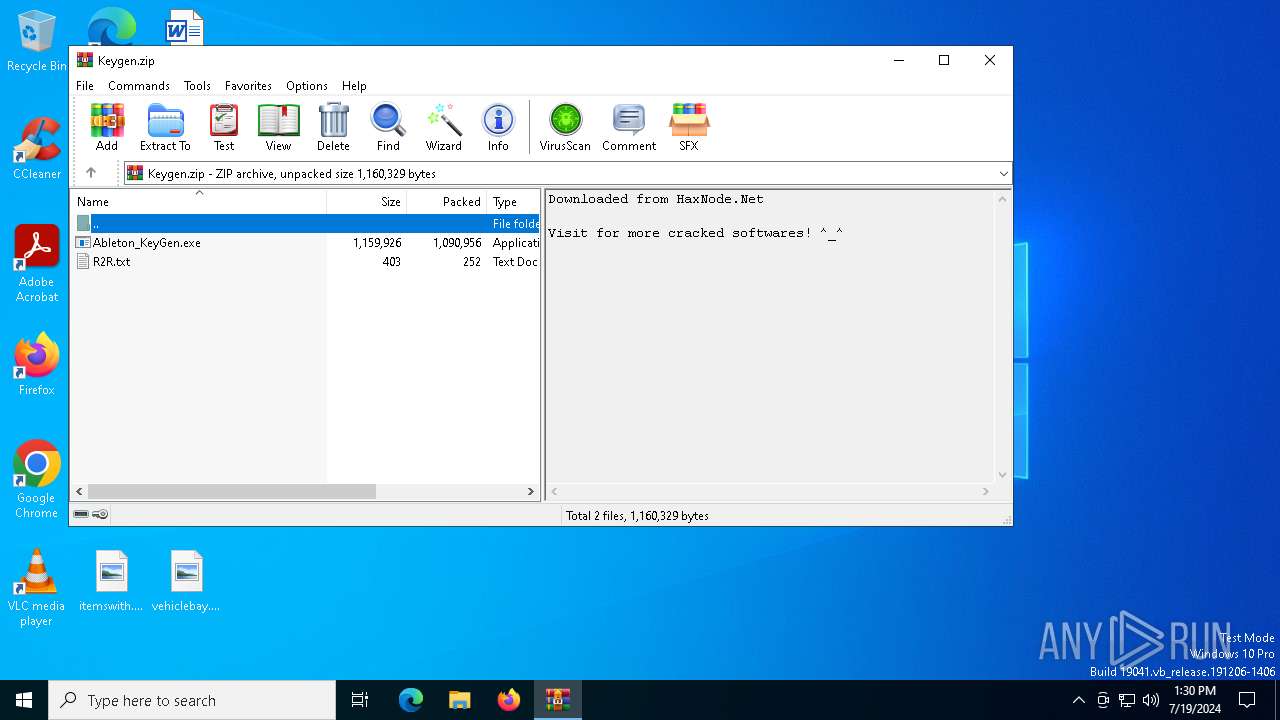
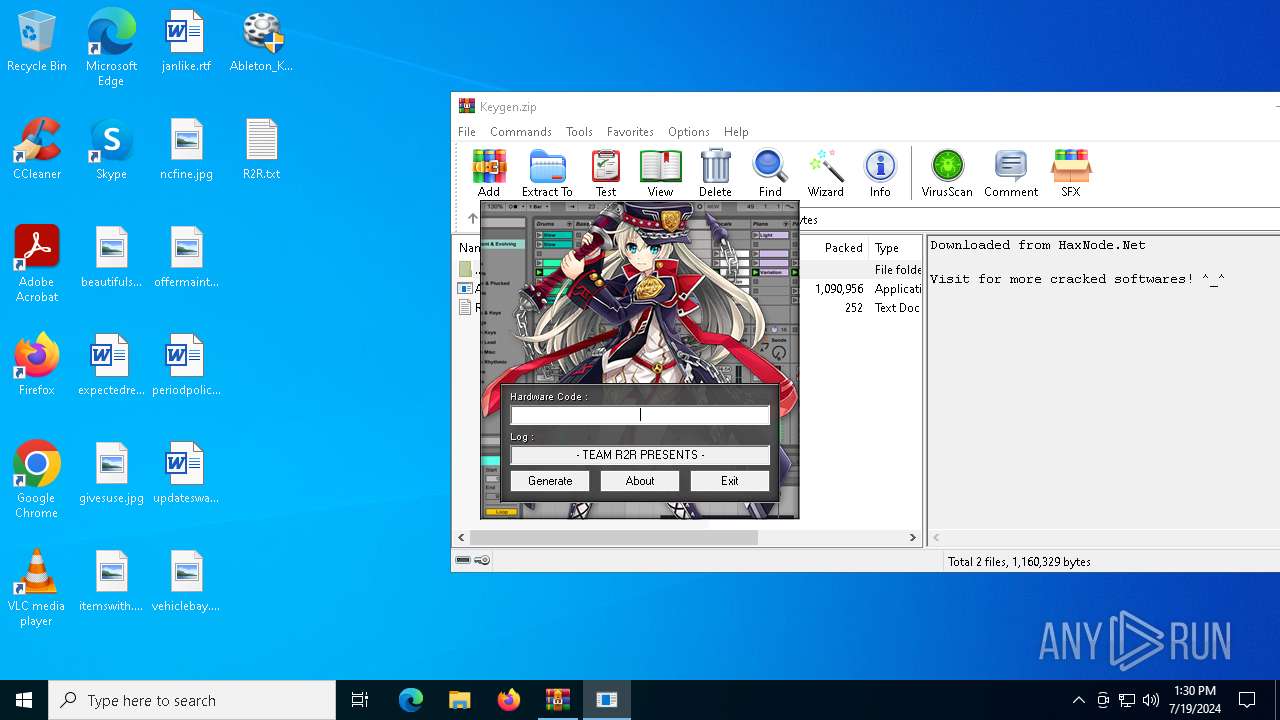
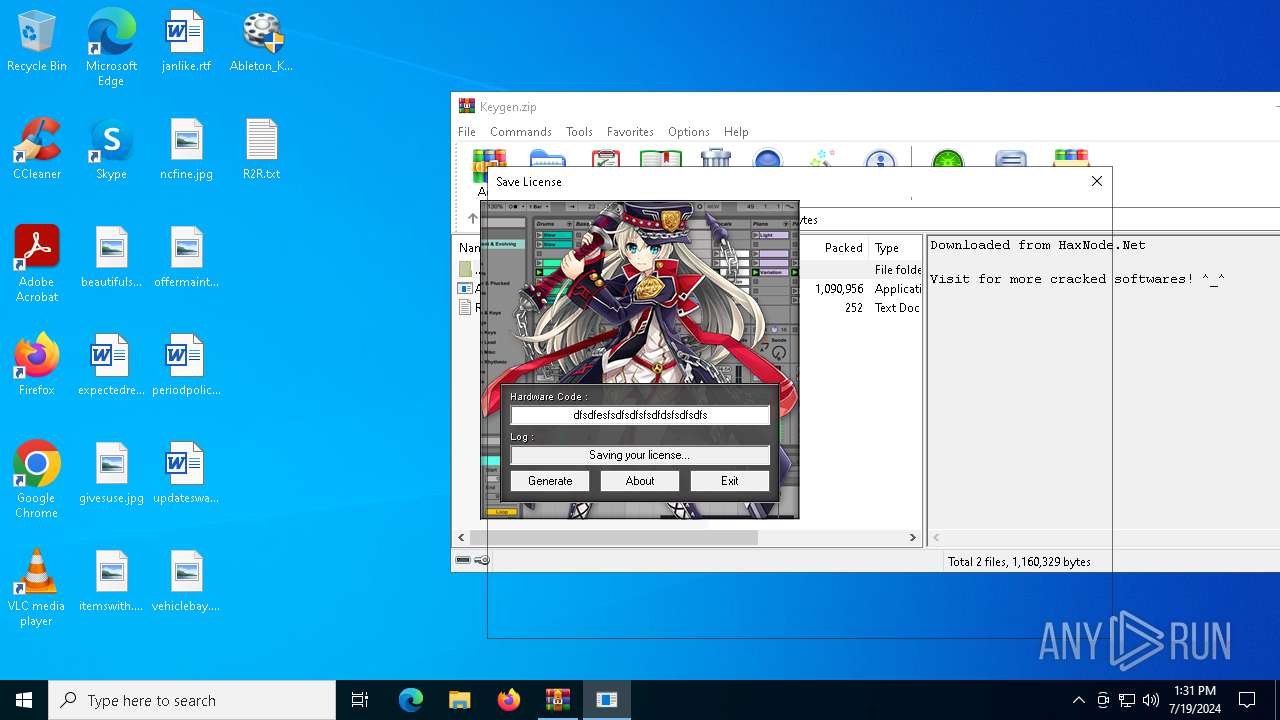
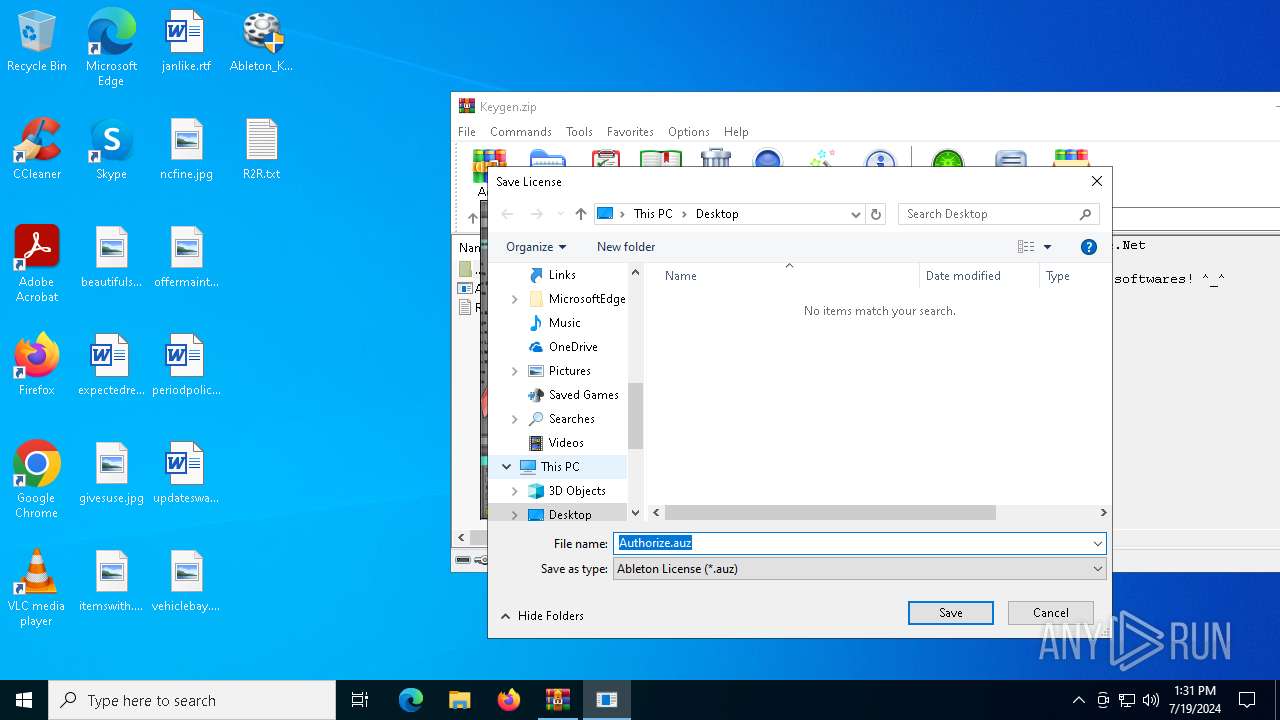
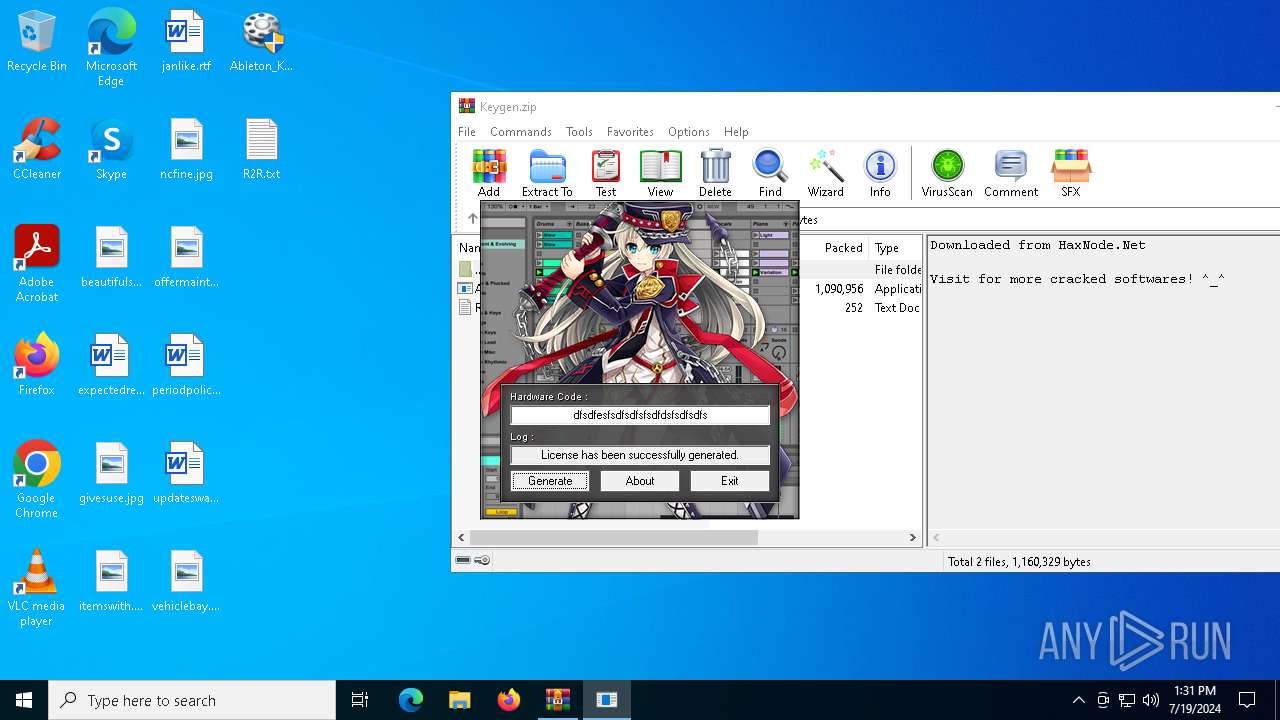
| File name: | Keygen.zip |
| Full analysis: | https://app.any.run/tasks/5f37f154-8082-4be8-b272-01a62e33c34d |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 13:30:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 17E1DD74CF22EFEE1820F138AE2C61BE |
| SHA1: | 76EF6E824C437A9A01AB7A144277166E2B9C6175 |
| SHA256: | CDBA2E7F5C66B5B7B90E8DF72C74A7F1CEE4084055E9D6F9FDF16A7C3B19D70A |
| SSDEEP: | 49152:dyOIwxLW0fx8Iq1Oh+TApHh9Dy1WXozq02F/sS/KCUxsglxVxPWh7uWdlYQk8vn9:dyBwxLWGx8R1k+UB9DywXoJOBKCUxsIu |
MALICIOUS
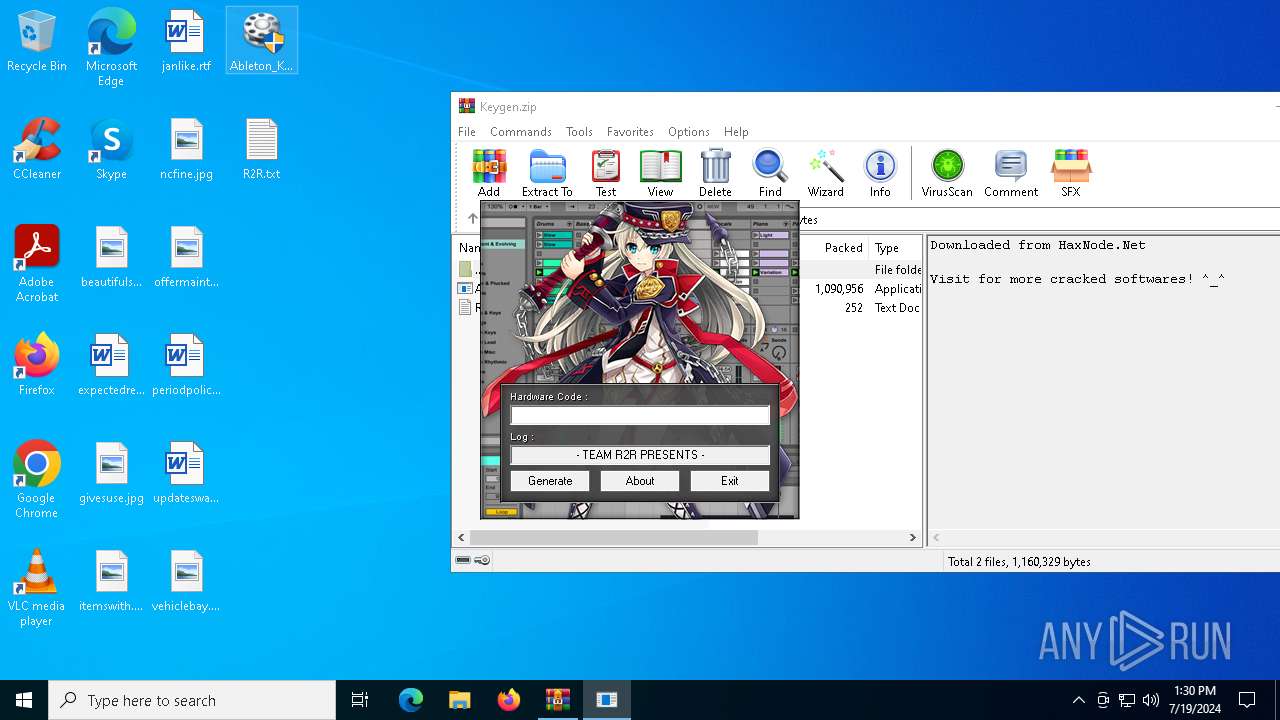
Drops the executable file immediately after the start
- Ableton_KeyGen.exe (PID: 7520)
- WinRAR.exe (PID: 7120)
SUSPICIOUS
Reads security settings of Internet Explorer
- keygen.exe (PID: 6840)
Executable content was dropped or overwritten
- Ableton_KeyGen.exe (PID: 7520)
INFO
Checks supported languages
- Ableton_KeyGen.exe (PID: 7520)
- keygen.exe (PID: 6840)
Create files in a temporary directory
- keygen.exe (PID: 6840)
- Ableton_KeyGen.exe (PID: 7520)
Manual execution by a user
- Ableton_KeyGen.exe (PID: 5936)
- Ableton_KeyGen.exe (PID: 7520)
Reads the machine GUID from the registry
- keygen.exe (PID: 6840)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7120)
Reads the computer name
- keygen.exe (PID: 6840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:02:25 07:29:48 |
| ZipCRC: | 0x89c07c47 |
| ZipCompressedSize: | 1090956 |
| ZipUncompressedSize: | 1159926 |
| ZipFileName: | Ableton_KeyGen.exe |
Total processes
140
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4316 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5936 | "C:\Users\admin\Desktop\Ableton_KeyGen.exe" | C:\Users\admin\Desktop\Ableton_KeyGen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6840 | C:\Users\admin\AppData\Local\Temp\keygen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | — | Ableton_KeyGen.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 7120 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Keygen.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7520 | "C:\Users\admin\Desktop\Ableton_KeyGen.exe" | C:\Users\admin\Desktop\Ableton_KeyGen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
12 242
Read events
12 174
Write events
63
Delete events
5
Modification events
| (PID) Process: | (7120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Keygen.zip | |||
| (PID) Process: | (7120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (6840) keygen.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | delete value | Name: | MRUList |
Value: | |||
Executable files
4
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7120 | WinRAR.exe | C:\Users\admin\Desktop\R2R.txt | text | |
MD5:BA12684AEFC4F41FC99AA80B3C29AA49 | SHA256:D0156CAD8D8FB0B656991E8AD409000056417C891FF71F54E34C8E110DEBC4C8 | |||
| 7520 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\bgm.xm | binary | |
MD5:EAC249A6CBD92E5A744F1921261B4134 | SHA256:9AE311E672F224A27350DD37CCE871187377531741DF048082B9CB680CD12882 | |||
| 7120 | WinRAR.exe | C:\Users\admin\Desktop\Ableton_KeyGen.exe | executable | |
MD5:5137F6C1B6FEC54E3C4FCE6261905DD6 | SHA256:72C96F7E2F4823BB9F28944C96AA1B737BE20EDD52CA97B699085D3498E4AB74 | |||
| 6840 | keygen.exe | C:\Users\admin\Desktop\Authorize.auz | csv | |
MD5:09EB714ECBFFA693CAAAB42B38AEDCB3 | SHA256:449BC76256D03889E9415962631CF137FC786C8118766ABF945FB36684810DCE | |||
| 6840 | keygen.exe | C:\Users\admin\AppData\Local\Temp\~DF10EFFCC93B736DAF.TMP | binary | |
MD5:08BC96774FBD93252C2C9D4EAE89EB12 | SHA256:40E579971A95F02D6D23A9EACBBACA26E816BD411FD77488AD7766C02AE818F1 | |||
| 7520 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\BASSMOD.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
| 7520 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\R2RLIVE.dll | executable | |
MD5:4CE264468BE29F6504EB745D11AA1D5C | SHA256:33339FD831B14D39514593CF7494BA1985DF6E32DBEF166B70D94EBAAD78CD3B | |||
| 7520 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | executable | |
MD5:88FB2EFAEF130C7256BF703580A414A7 | SHA256:2EF24CB81741BCDCCE8FDAE0812ECB86A334B0A98160B4C068D2B59913C3896D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
34
DNS requests
12
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4716 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2760 | svchost.exe | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | unknown |
7856 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3352 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |