| File name: | 1 (173) |
| Full analysis: | https://app.any.run/tasks/5faf3454-416a-4c6c-b5c1-931cd0dcad03 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 16:51:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 3F369F627C7E25F598B1B17D8905B2A0 |
| SHA1: | 83E4B63876E4DA8141B921BC3E1D59D3595E77D8 |
| SHA256: | CDA9367C37B4CB0745D09BC05E525DAEA618DC341BE33D1D6ABEE7189B3D791D |
| SSDEEP: | 49152:oIc0euibtmmpn+S8PSuOuPxRfWXNqtRXfK5JIUNY/a72EbLckqe6:oRJ7gs+S8auOuPxRWXNcvAJhNY/02Eb1 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- 1 (173).exe (PID: 7348)
- 1 (173).exe (PID: 7464)
Reads Microsoft Outlook installation path
- 1 (173).exe (PID: 7464)
Reads Internet Explorer settings
- 1 (173).exe (PID: 7464)
Application launched itself
- 1 (173).exe (PID: 7348)
- download.exe (PID: 2504)
Executable content was dropped or overwritten
- 1 (173).exe (PID: 7464)
- download.exe (PID: 2504)
Process drops python dynamic module
- download.exe (PID: 2504)
Process drops legitimate windows executable
- download.exe (PID: 2504)
The process drops C-runtime libraries
- download.exe (PID: 2504)
Loads Python modules
- download.exe (PID: 7000)
Starts CMD.EXE for commands execution
- download.exe (PID: 7000)
INFO
Reads the computer name
- 1 (173).exe (PID: 7348)
- 1 (173).exe (PID: 7464)
Checks supported languages
- 1 (173).exe (PID: 7348)
- 1 (173).exe (PID: 7464)
- download.exe (PID: 7000)
Process checks computer location settings
- 1 (173).exe (PID: 7348)
Checks proxy server information
- 1 (173).exe (PID: 7464)
Reads the machine GUID from the registry
- 1 (173).exe (PID: 7464)
Reads the software policy settings
- 1 (173).exe (PID: 7464)
Create files in a temporary directory
- 1 (173).exe (PID: 7464)
- download.exe (PID: 2504)
- 1 (173).exe (PID: 7348)
The sample compiled with english language support
- download.exe (PID: 2504)
- 1 (173).exe (PID: 7464)
Checks operating system version
- download.exe (PID: 7000)
Creates files or folders in the user directory
- 1 (173).exe (PID: 7464)
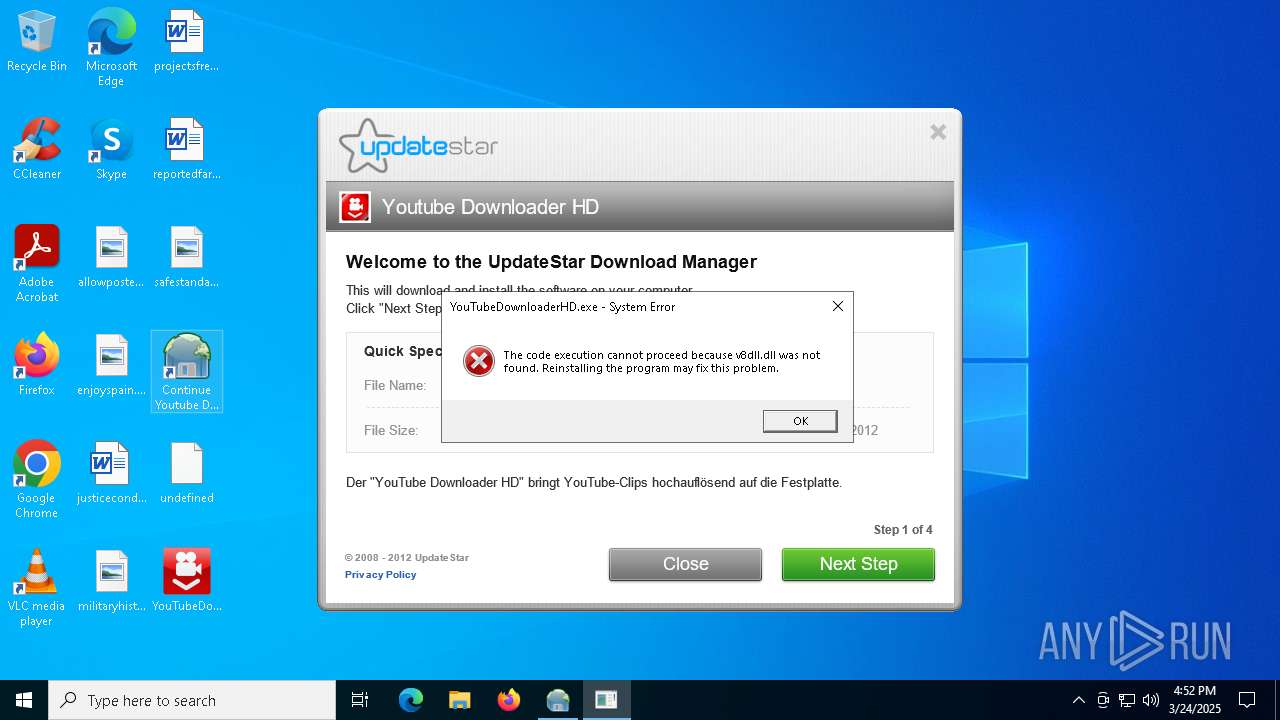
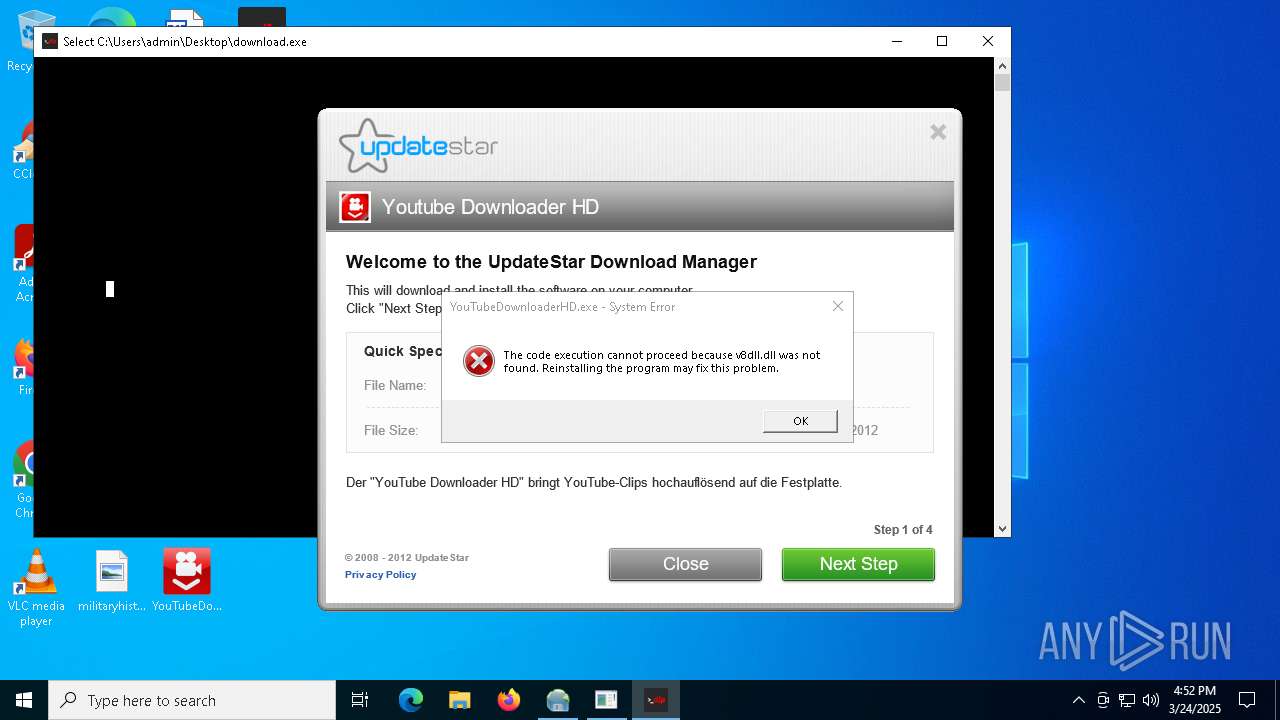
Manual execution by a user
- YouTubeDownloaderHD.exe (PID: 672)
- download.exe (PID: 2504)
- notepad.exe (PID: 8148)
- notepad.exe (PID: 8032)
PyInstaller has been detected (YARA)
- download.exe (PID: 2504)
Reads security settings of Internet Explorer
- notepad.exe (PID: 8032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (37.4) |
|---|---|---|
| .scr | | | Windows screen saver (34.5) |
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 898560 |
| InitializedDataSize: | 306688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd83a0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
154
Monitored processes
14
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | download.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
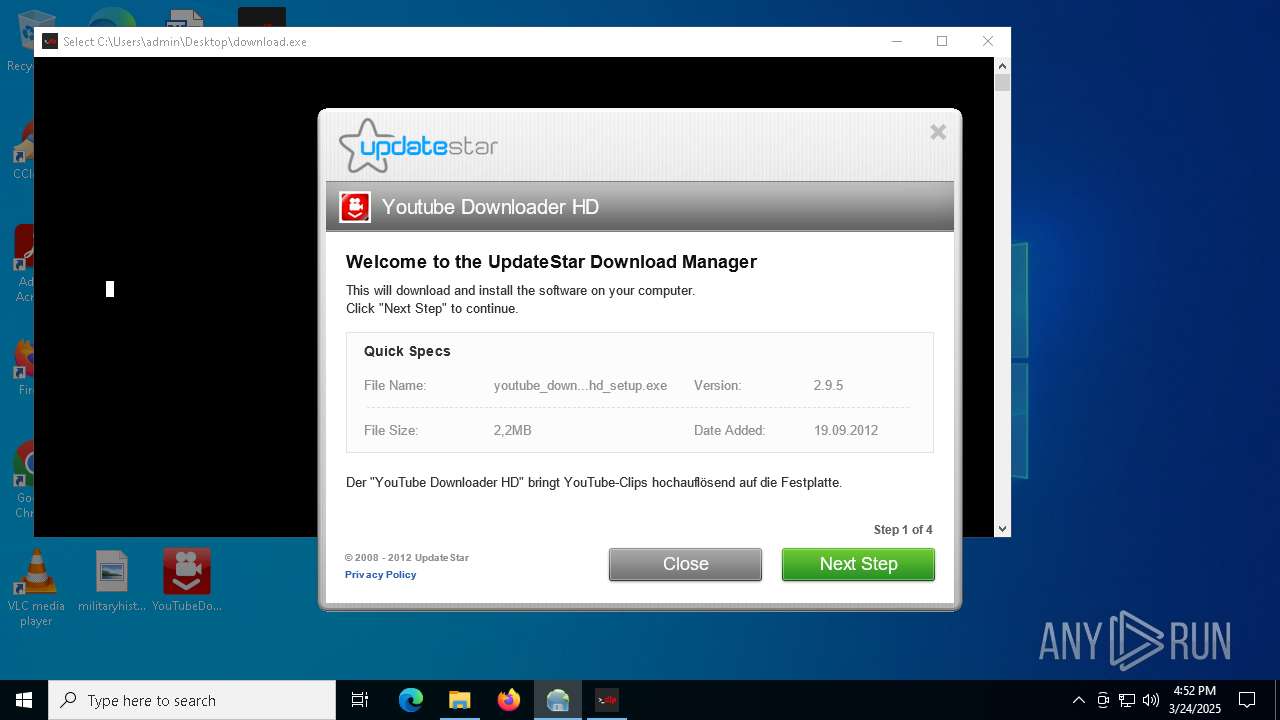
| 672 | "C:\Users\admin\Desktop\YouTubeDownloaderHD.exe" | C:\Users\admin\Desktop\YouTubeDownloaderHD.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Version: 5.9.6.0 Modules
| |||||||||||||||
| 780 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | download.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2504 | "C:\Users\admin\Desktop\download.exe" | C:\Users\admin\Desktop\download.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4428 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | download.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | download.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7000 | "C:\Users\admin\Desktop\download.exe" | C:\Users\admin\Desktop\download.exe | — | download.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7348 | "C:\Users\admin\AppData\Local\Temp\1 (173).exe" | C:\Users\admin\AppData\Local\Temp\1 (173).exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7464 | "C:\Users\admin\AppData\Local\Temp\1 (173).exe" /RSF | C:\Users\admin\AppData\Local\Temp\1 (173).exe | 1 (173).exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 7660 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 547
Read events
2 544
Write events
3
Delete events
0
Modification events
| (PID) Process: | (7464) 1 (173).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7464) 1 (173).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7464) 1 (173).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
117
Suspicious files
13
Text files
76
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\css\main.css | text | |
MD5:FB45D7F6FB4D518A0ECC05CF7CE5363C | SHA256:4A01A4D6E711E873A065510A407CB6D37535D8BECABBCFE9F05FE3DEC13E5B9E | |||
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\images\Close_Hover.png | image | |
MD5:F5BDB3CABDC15580D97FA94AA3397C08 | SHA256:B28DB98F2A6B06B6783B8FCA6AABDCB89234D5BD4306FA71711988DBA1FC71EA | |||
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\css\sdk-ui\checkbox.css | text | |
MD5:64773C6B0E3413C81AEBC46CCE8C9318 | SHA256:B09504C1BF0486D3EC46500592B178A3A6C39284672AF8815C3687CC3D29560D | |||
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\css\sdk-ui\browse.css | text | |
MD5:6009D6E864F60AEA980A9DF94C1F7E1C | SHA256:5EF48A8C8C3771B4F233314D50DD3B5AFDCD99DD4B74A9745C8FE7B22207056D | |||
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\css\sdk-ui\button.css | text | |
MD5:37E1FF96E084EC201F0D95FEEF4D5E94 | SHA256:8E806F5B94FC294E918503C8053EF1284E4F4B1E02C7DA4F4635E33EC33E0534 | |||
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\css\ie6_main.css | text | |
MD5:72654AC770EF4C7322124F8241C08D75 | SHA256:2933D672D70E4D5E5F06AF819BC97E4C594E1E0BF3351EB2929A3CD3DD387572 | |||
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\css\sdk-ui\images\button-bg.png | image | |
MD5:98B1DE48DFA64DC2AA1E52FACFBEE3B0 | SHA256:2693930C474FE640E2FE8D6EF98ABE2ECD303D2392C3D8B2E006E8942BA8F534 | |||
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\images\Color_Button.png | image | |
MD5:CCFBCBB51598A1946B19FF56C4AE9BD1 | SHA256:7EC494B43D8C70C338929FD88AF752E117BB924A4284B93567E7B8C9CB79BE9F | |||
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\css\sdk-ui\images\progress-bg-corner.png | image | |
MD5:608F1F20CD6CA9936EAA7E8C14F366BE | SHA256:86B6E6826BCDE2955D64D4600A4E01693522C1FDDF156CE31C4BA45B3653A7BD | |||
| 7348 | 1 (173).exe | C:\Users\admin\AppData\Local\Temp\ish1094359\css\sdk-ui\images\progress-bg.png | image | |
MD5:E9F12F92A9EEB8EBE911080721446687 | SHA256:C1CF449536BC2778E27348E45F0F53D04C284109199FB7A9AF7A61016B91F8BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
26
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7464 | 1 (173).exe | GET | 301 | 67.217.61.118:80 | http://static.updatestar.net/img/icons/1506230.32.png | unknown | — | — | unknown |
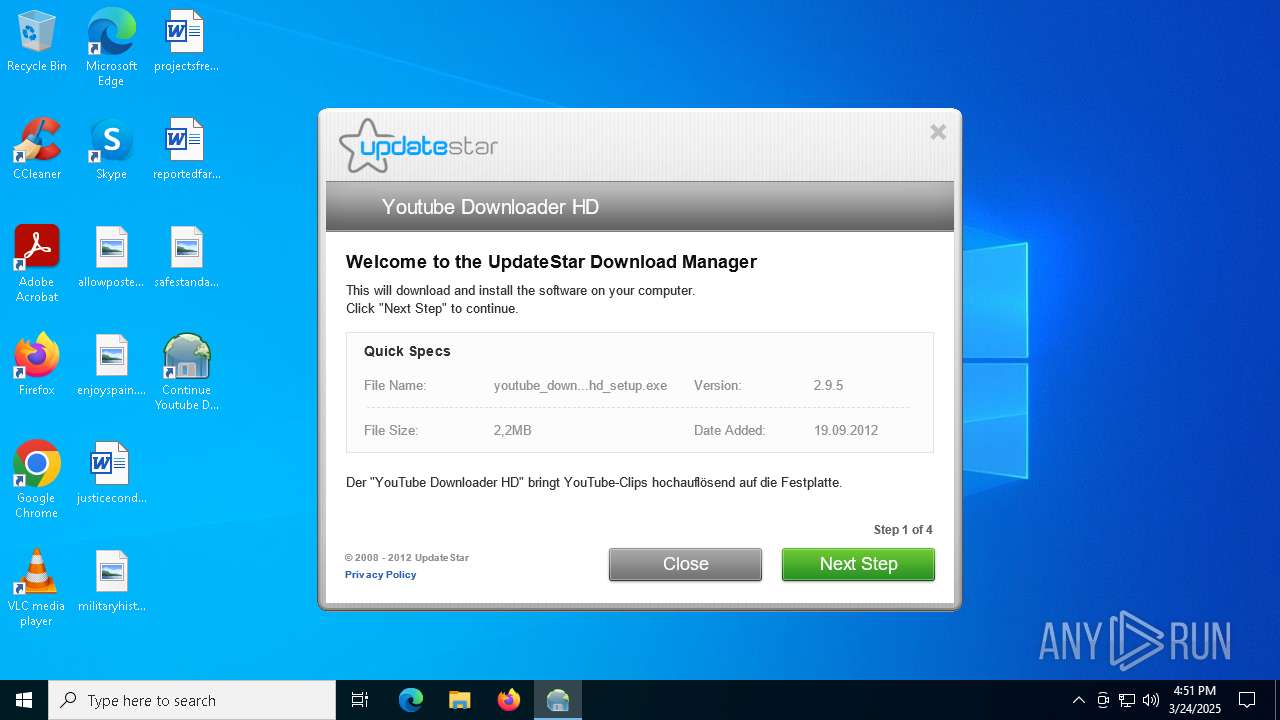
7464 | 1 (173).exe | GET | 301 | 138.201.226.176:80 | http://www.youtubedownloaderhd.com/files/youtube_downloader_hd_setup.exe | unknown | — | — | whitelisted |
7464 | 1 (173).exe | GET | 200 | 138.201.226.176:80 | http://www.youtubedownloaderhd.com/files/youtube_downloader_hd.zip | unknown | — | — | whitelisted |
7464 | 1 (173).exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEQCtjS32RoGg02RH6qlPonPB | unknown | — | — | whitelisted |
7464 | 1 (173).exe | GET | 200 | 18.244.18.92:80 | http://crls.ssl.com/SSL.com-TLS-T-ECC-R2.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7840 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1228 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1228 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7464 | 1 (173).exe | 67.217.61.118:80 | static.updatestar.net | IS-AS-1 | US | suspicious |
7464 | 1 (173).exe | 138.201.226.176:80 | www.youtubedownloaderhd.com | Hetzner Online GmbH | DE | whitelisted |
7464 | 1 (173).exe | 172.67.71.196:443 | static.updatestar.com | CLOUDFLARENET | US | suspicious |
7464 | 1 (173).exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
7464 | 1 (173).exe | 18.244.18.92:80 | crls.ssl.com | — | US | whitelisted |
2564 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
os.updatestarcdn.com |
| malicious |
www.youtubedownloaderhd.com |
| whitelisted |
static.updatestar.net |
| unknown |
static.updatestar.com |
| unknown |
ocsp.comodoca.com |
| whitelisted |
crls.ssl.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |