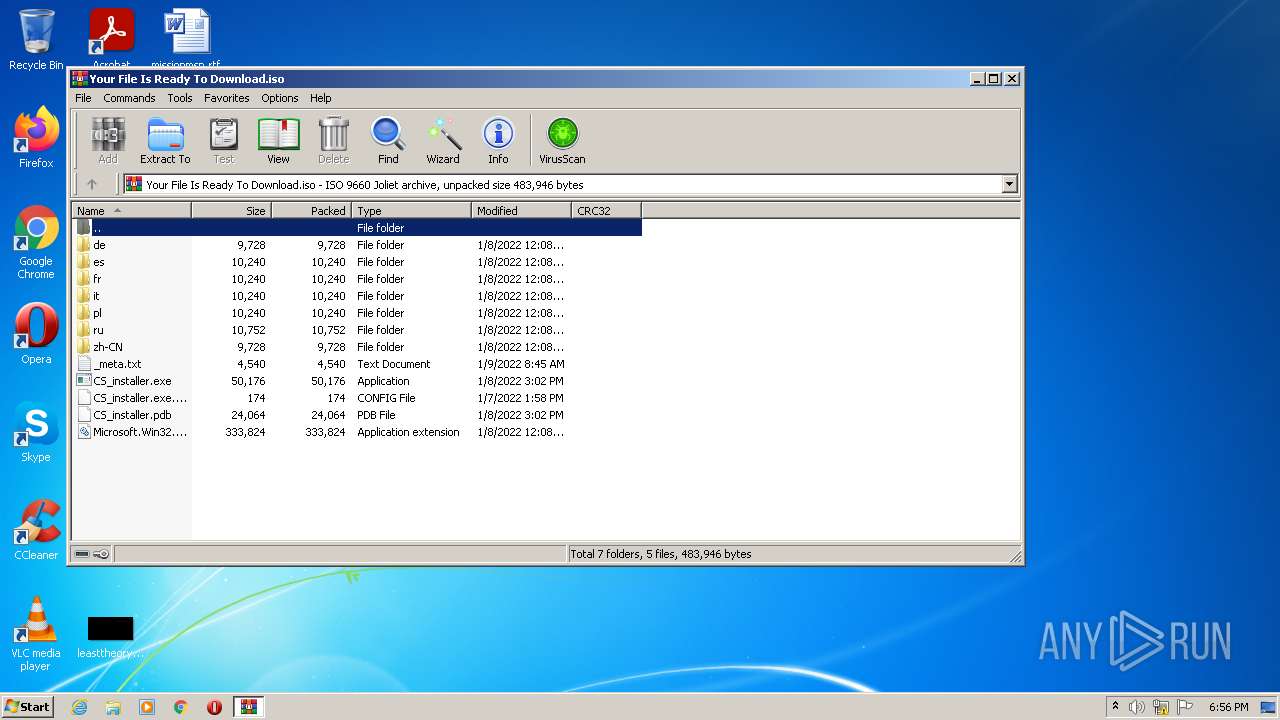
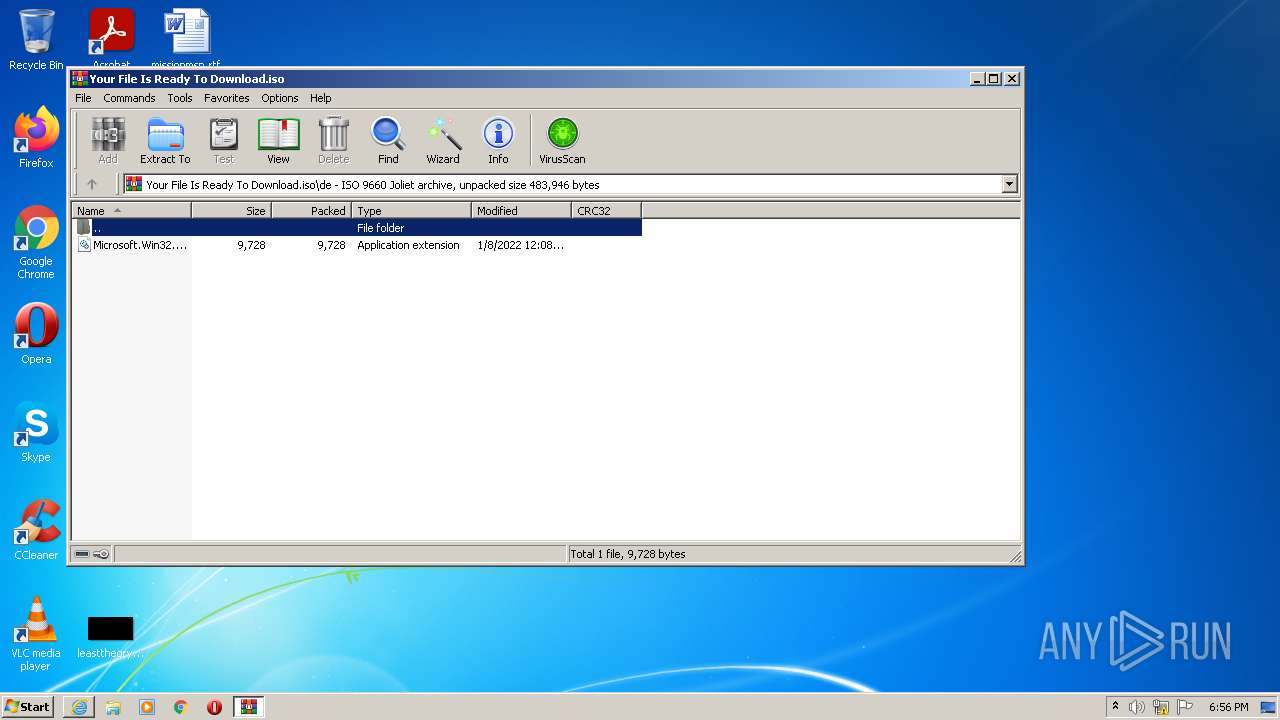
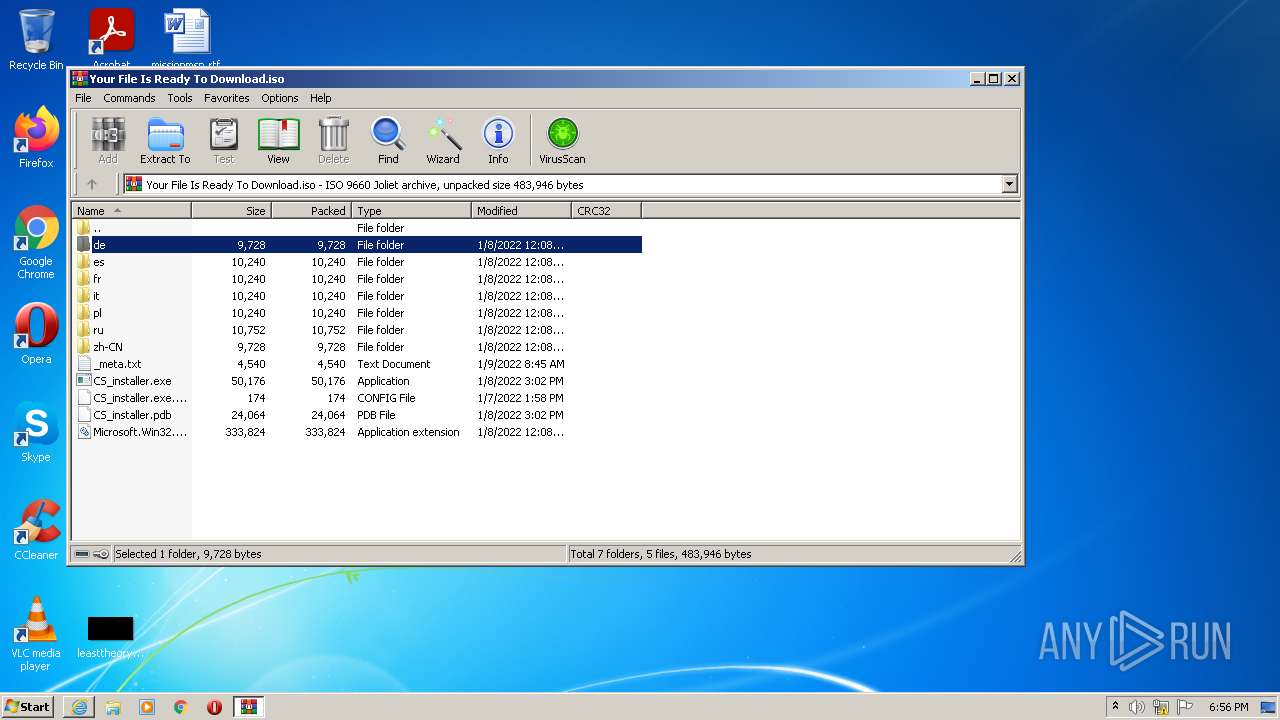
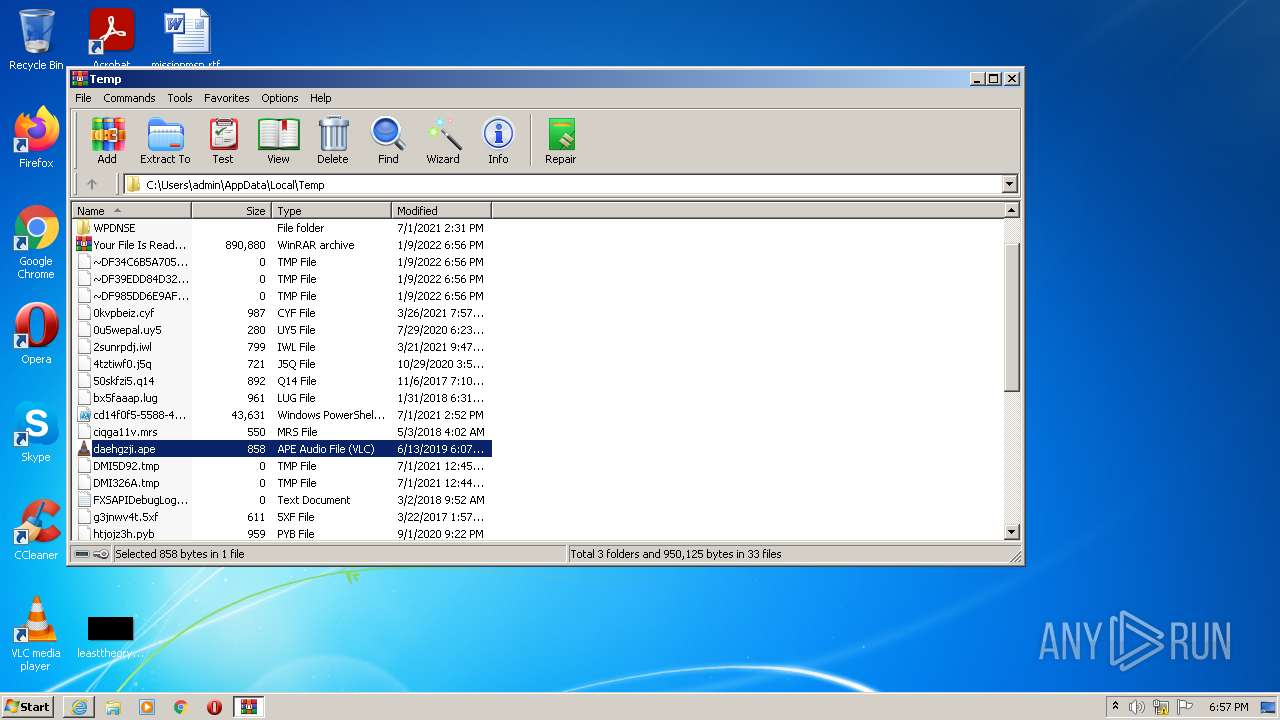
| File name: | Your File Is Ready To Download.iso |
| Full analysis: | https://app.any.run/tasks/769d9987-c909-4750-ac34-52a7e0f13067 |
| Verdict: | Malicious activity |
| Analysis date: | January 09, 2022, 18:56:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | ISO 9660 CD-ROM filesystem data 'CDROM' |
| MD5: | 845EFBE3B7B0163DD9D5C74F9BC32BF8 |
| SHA1: | 0D162EF4A9BDB2E378679B051D20DECBE0B651BE |
| SHA256: | CD999181DE69F01EC686F39CCF9A55131A695C55075D530A44F251A8F41DA7C8 |
| SSDEEP: | 6144:hduP1sSmlet/xMtsvR1KQfNXSIK26R7S:ut/wsvxfw3VR7S |
MALICIOUS
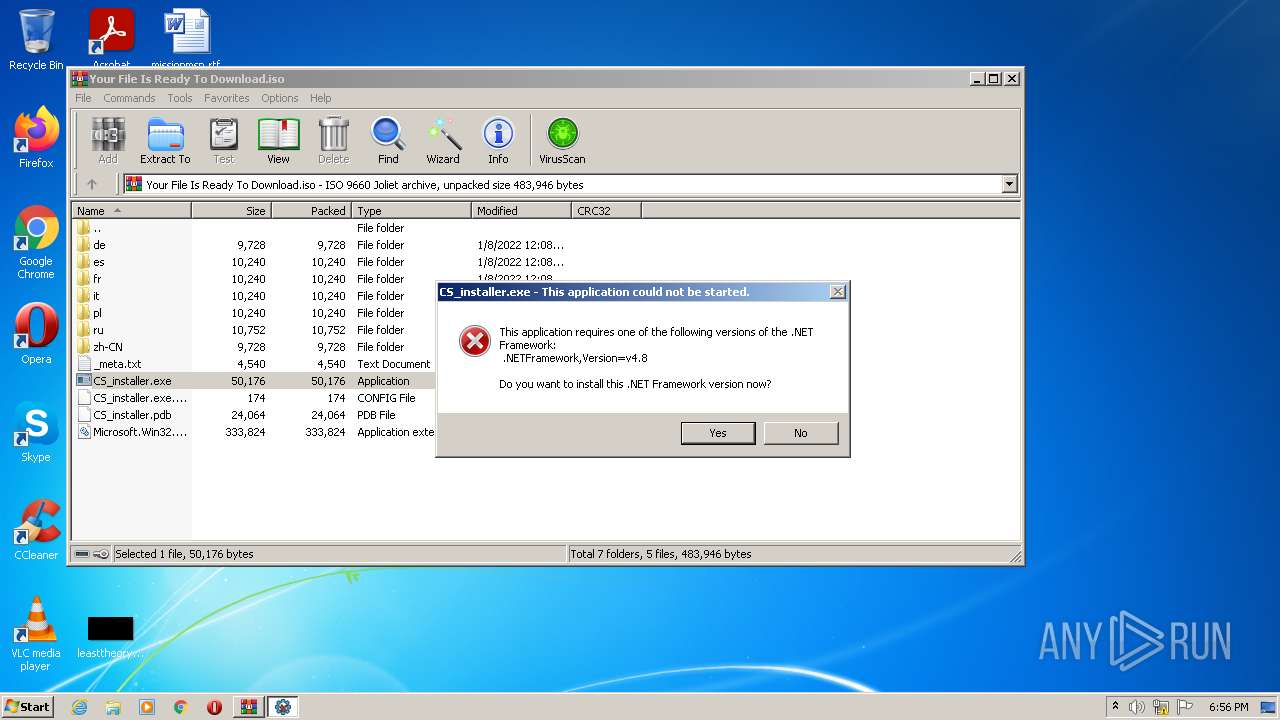
Application was dropped or rewritten from another process
- CS_installer.exe (PID: 2972)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3980)
- CS_installer.exe (PID: 2972)
- vlc.exe (PID: 1808)
Reads the computer name
- WinRAR.exe (PID: 3980)
- CS_installer.exe (PID: 2972)
- vlc.exe (PID: 1808)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3980)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3980)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3908)
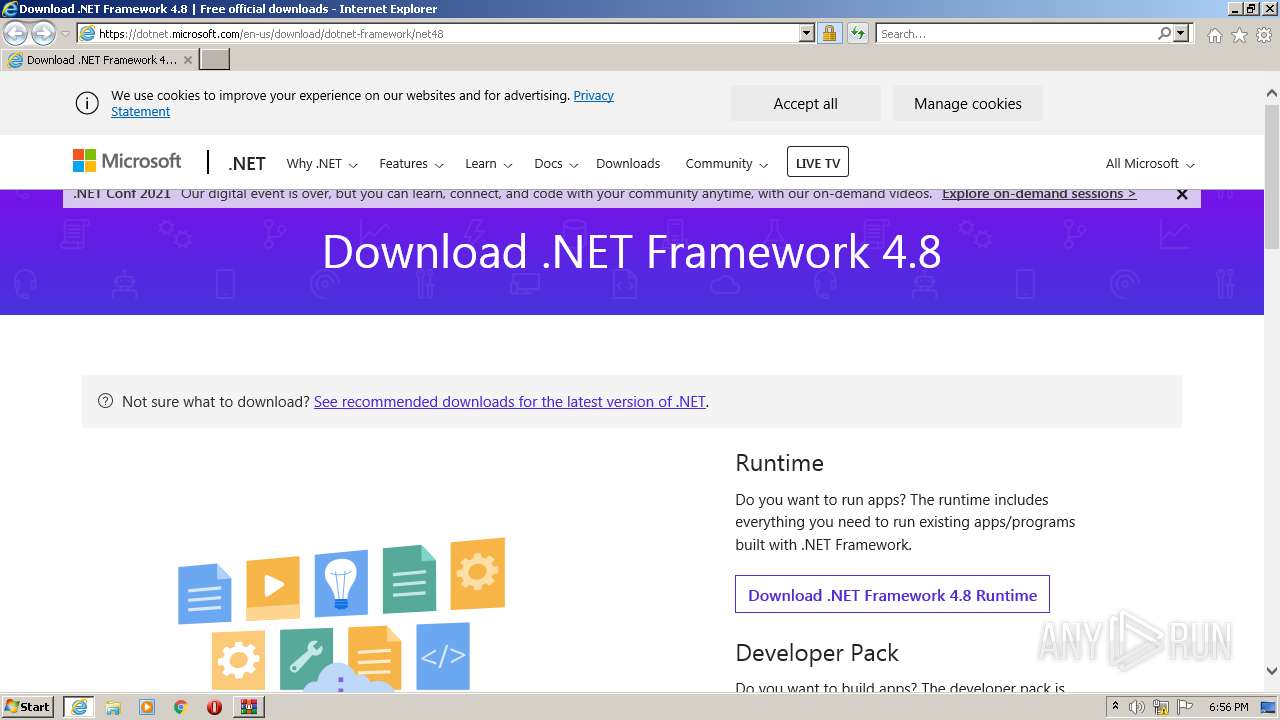
Starts Internet Explorer
- CS_installer.exe (PID: 2972)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3980)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3980)
Creates files in the user directory
- vlc.exe (PID: 1808)
INFO
Reads the computer name
- iexplore.exe (PID: 1876)
- iexplore.exe (PID: 3908)
Checks supported languages
- iexplore.exe (PID: 1876)
- iexplore.exe (PID: 3908)
- NOTEPAD.EXE (PID: 3088)
- rundll32.exe (PID: 120)
Application launched itself
- iexplore.exe (PID: 1876)
Changes internet zones settings
- iexplore.exe (PID: 1876)
Reads internet explorer settings
- iexplore.exe (PID: 3908)
Reads settings of System Certificates
- iexplore.exe (PID: 3908)
- iexplore.exe (PID: 1876)
Checks Windows Trust Settings
- iexplore.exe (PID: 3908)
- iexplore.exe (PID: 1876)
Creates files in the user directory
- iexplore.exe (PID: 3908)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1876)
Changes settings of System certificates
- iexplore.exe (PID: 1876)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 1876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .iso | | | ISO 9660 CD image (27.6) |
|---|---|---|
| .atn | | | Photoshop Action (27.1) |
| .gmc | | | Game Music Creator Music (6.1) |
EXIF
Composite
| VolumeSize: | 870 kB |
|---|
ISO
| VolumeEffectiveDate: | 2022:01:09 08:45:38.00+00:00 |
|---|---|
| VolumeModifyDate: | 2022:01:09 08:45:38.00+00:00 |
| VolumeCreateDate: | 2022:01:09 08:45:38.00+00:00 |
| Software: | MKISOFS ISO 9660/HFS FILESYSTEM BUILDER & CDRECORD CD-R/DVD CREATOR (C) 1993 E.YOUNGDALE (C) 1997 J.PEARSON/J.SCHILLING |
| RootDirectoryCreateDate: | 2022:01:09 08:45:38+00:00 |
| VolumeBlockSize: | 2048 |
| VolumeBlockCount: | 435 |
| VolumeName: | CDROM |
| System: | Win32 |
Total processes
42
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
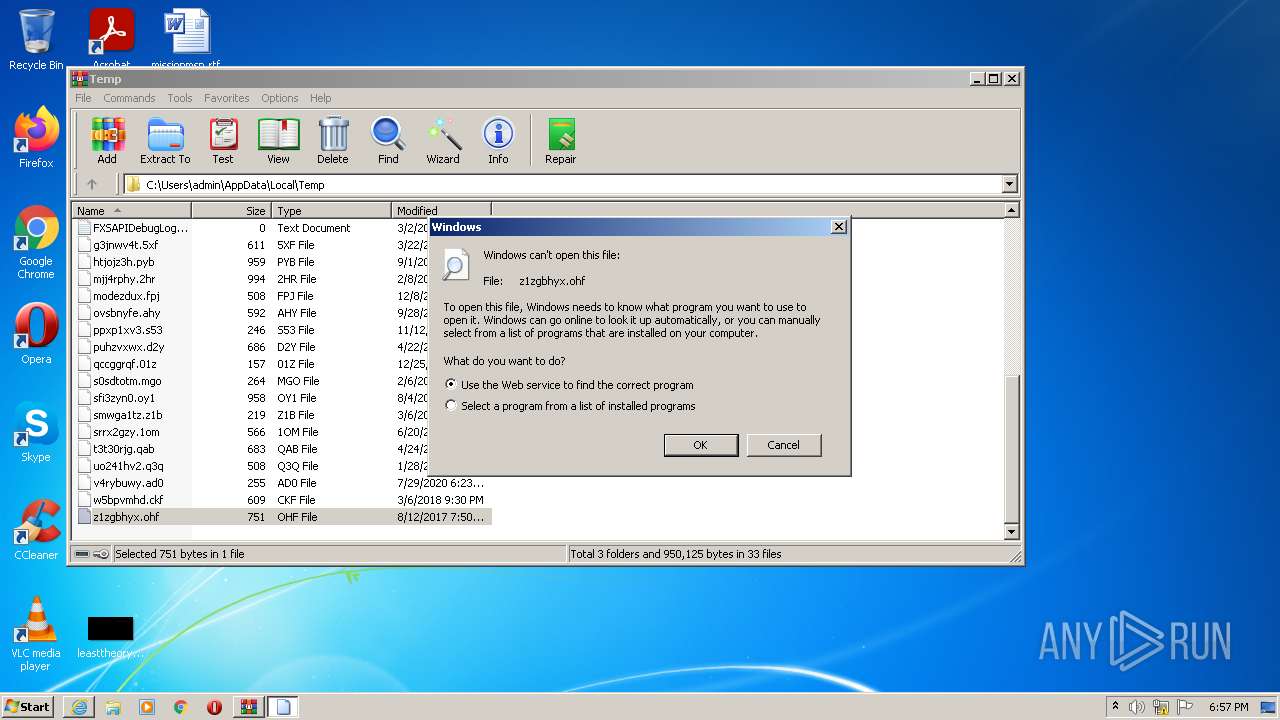
| 120 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\z1zgbhyx.ohf | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Local\Temp\daehgzji.ape" | C:\Program Files\VideoLAN\VLC\vlc.exe | WinRAR.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 3221225547 Version: 3.0.11 Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.8&processName=CS_installer.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | CS_installer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2972 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.24664\CS_installer.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.24664\CS_installer.exe | — | WinRAR.exe | |||||||||||
User: admin Company: CS_installer Integrity Level: MEDIUM Description: CS_installer Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3088 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\FXSAPIDebugLogFile.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3908 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1876 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3980 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Your File Is Ready To Download.iso" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
16 104
Read events
15 927
Write events
175
Delete events
2
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Your File Is Ready To Download.iso | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
9
Suspicious files
11
Text files
43
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.24664\es\Microsoft.Win32.TaskScheduler.resources.dll | executable | |
MD5:38E7487352DC57A70B8E378E15E79A40 | SHA256:9F378E15A31227466FA487F9C2D678955697ED3BF0EB994D0FCFC94E910AA107 | |||
| 3908 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.24664\zh-CN\Microsoft.Win32.TaskScheduler.resources.dll | executable | |
MD5:26446651D7A3D0FB73481824D9DD2CE9 | SHA256:01ACEC0D908EF5774977C92A1B9389267CBDC2E5BF149255287FEC6D810D8C87 | |||
| 3908 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_E503B048B745DFA14B81FCFC68D6DECE | der | |
MD5:— | SHA256:— | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.24664\it\Microsoft.Win32.TaskScheduler.resources.dll | executable | |
MD5:5AC67D6ACC14962CC87FC88F25F3390E | SHA256:59A800ED74A396F045C7768E676D152E94A572E6A4503457C398B6ECFFF33663 | |||
| 3908 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.24664\de\Microsoft.Win32.TaskScheduler.resources.dll | executable | |
MD5:C1119BCCC9DCA403B0DC03D02427FF68 | SHA256:A6B2810D931F5F624AF66A42B96433EC8DF5A4FDE3F5DF3ED273524DCC765E24 | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.24664\_meta.txt | text | |
MD5:8E0B8F170CCC7C38B01460B14610A214 | SHA256:97AB88FCB04EB4DFE1EA4EE4A5CED1A3A88933BD259D1D16234CA0958333C627 | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.24664\ru\Microsoft.Win32.TaskScheduler.resources.dll | executable | |
MD5:A265AF06F6E93BE2AC7E7209EF90DE99 | SHA256:665041CD5516C4ECCD31DA41F022671E297674FBD1801F27F6B5541770F5CED7 | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.24664\fr\Microsoft.Win32.TaskScheduler.resources.dll | executable | |
MD5:9377F8835789D8C352485D7CAEA18D84 | SHA256:DD512222844C61843529A95B86ED1A07581A0391C6FDCE58BE35D8D438D9844F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
37
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3908 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
3908 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
3908 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3908 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
1876 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3908 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
3908 | iexplore.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3eaf544d40887793 | US | compressed | 4.70 Kb | whitelisted |
3908 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3908 | iexplore.exe | 104.111.242.51:443 | go.microsoft.com | Akamai International B.V. | NL | unknown |
3908 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3908 | iexplore.exe | 13.107.246.45:443 | dotnet.microsoft.com | Microsoft Corporation | US | malicious |
— | — | 13.107.246.45:443 | dotnet.microsoft.com | Microsoft Corporation | US | malicious |
3908 | iexplore.exe | 2.18.233.62:443 | www.microsoft.com | Akamai International B.V. | — | whitelisted |
3908 | iexplore.exe | 152.199.21.175:443 | az416426.vo.msecnd.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1876 | iexplore.exe | 13.107.246.45:443 | dotnet.microsoft.com | Microsoft Corporation | US | malicious |
3908 | iexplore.exe | 13.69.106.211:443 | dc.services.visualstudio.com | Microsoft Corporation | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
statics-marketingsites-wcus-ms-com.akamaized.net |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
az416426.vo.msecnd.net |
| whitelisted |
wcpstatic.microsoft.com |
| whitelisted |
api.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: Copyright � 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=i686-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x86/contrib/i686-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: plug-ins loaded: 494 modules
|