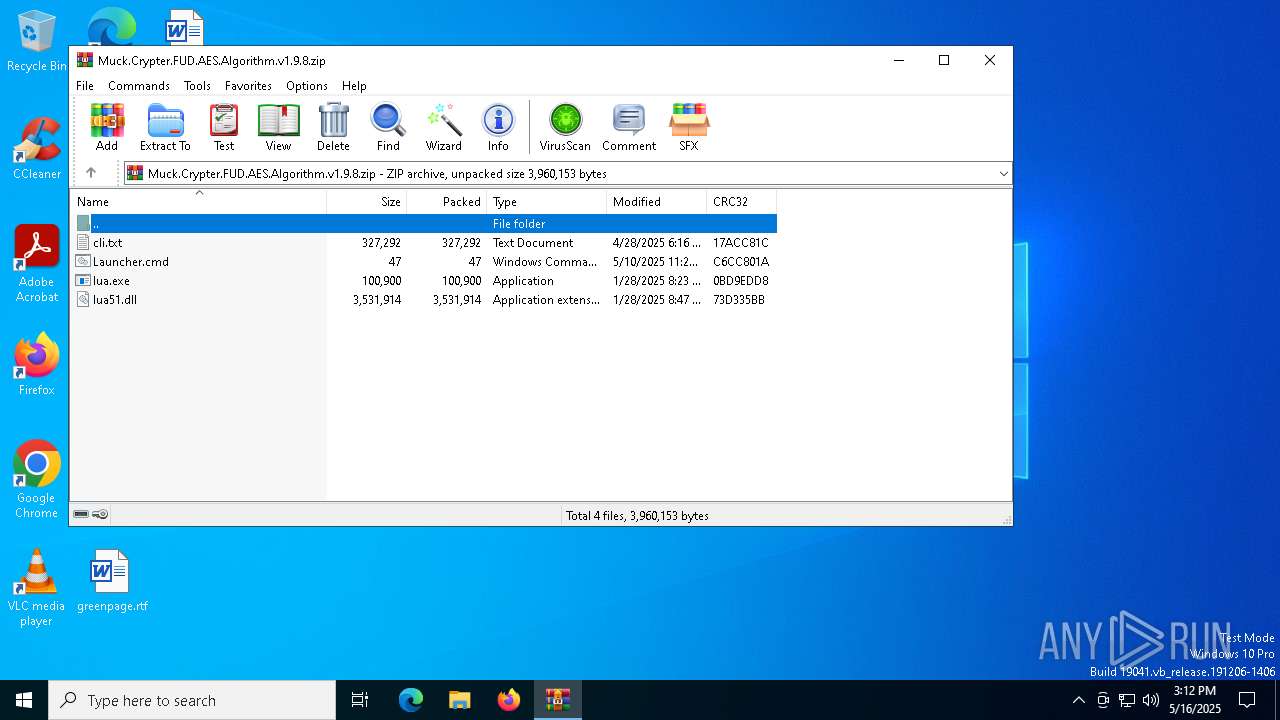
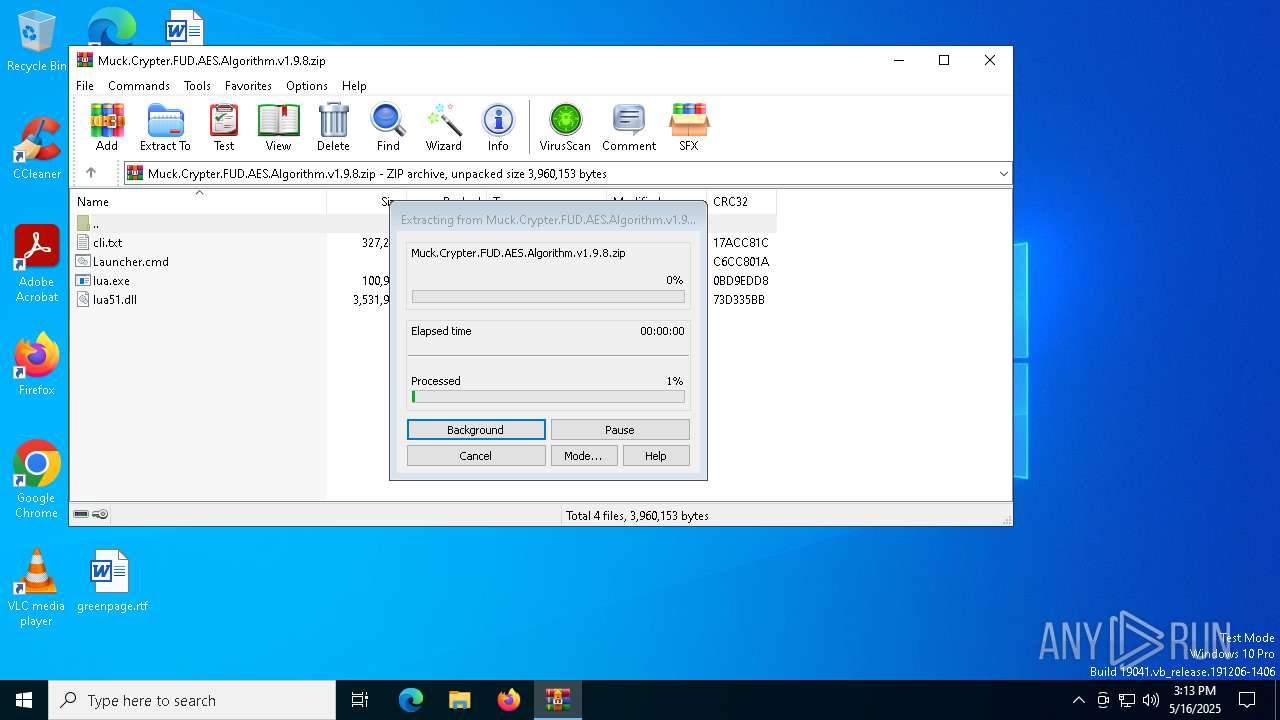
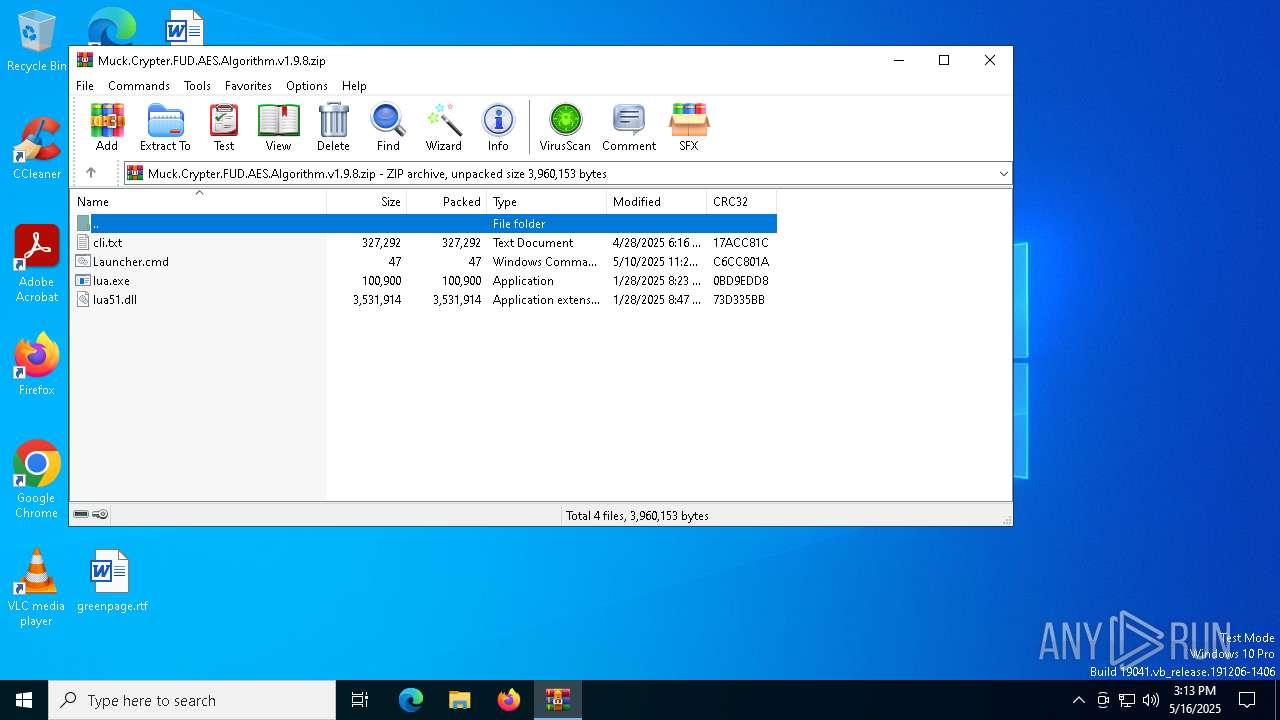
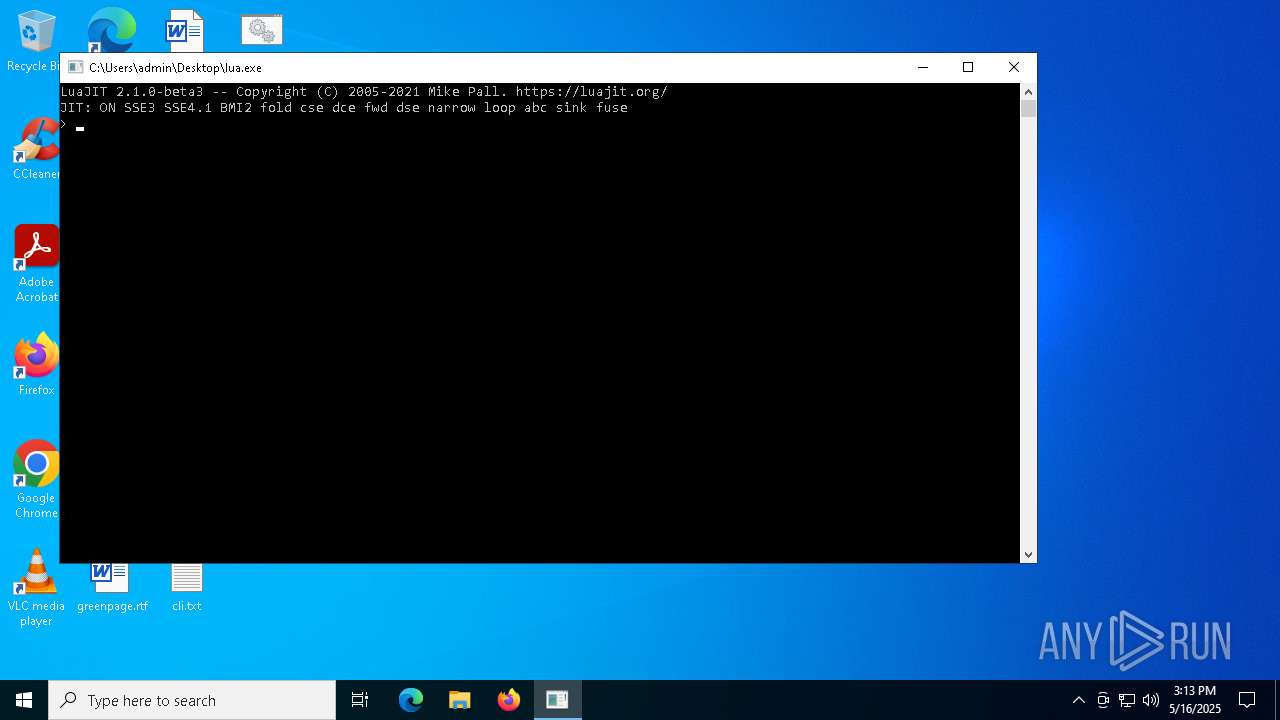
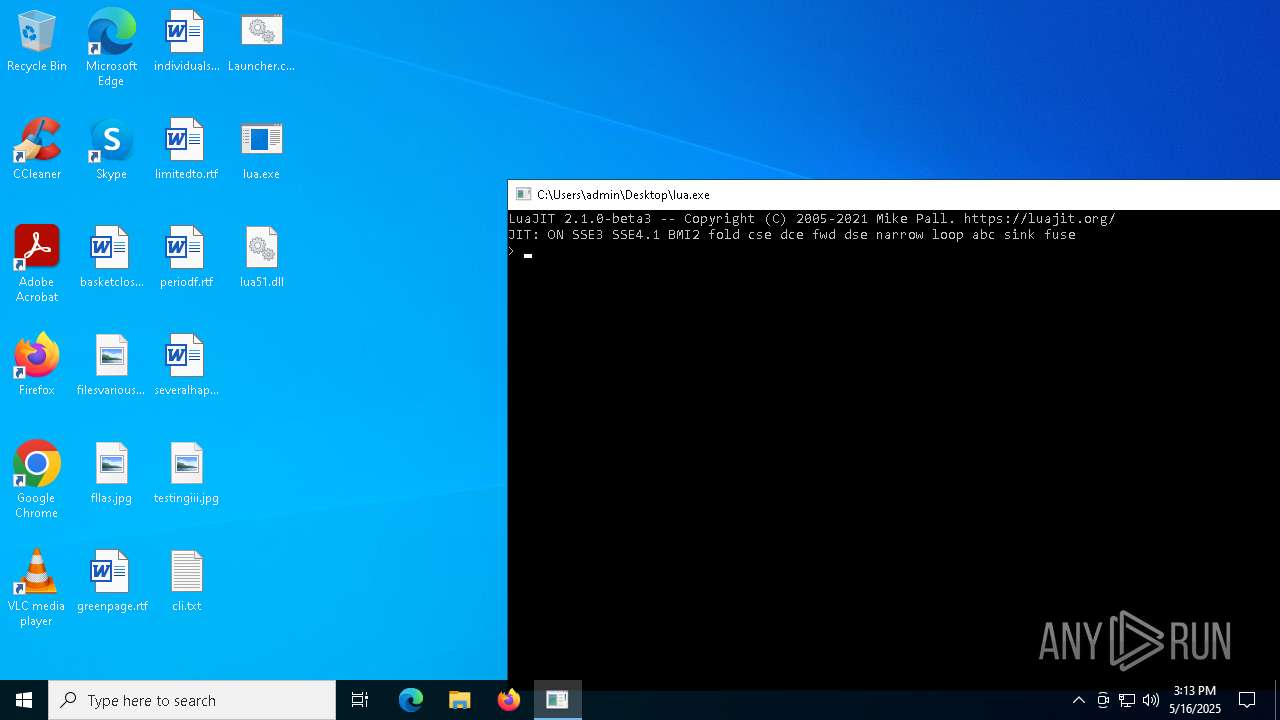
| File name: | Muck.Crypter.FUD.AES.Algorithm.v1.9.8.zip |
| Full analysis: | https://app.any.run/tasks/4eda8aea-5a58-47a2-af39-7cd33f57b399 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 15:12:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | B9652F1A78D0A5A90ED0D9DFF7973306 |
| SHA1: | 5CDAA30A537C68DC455A252BDEAC34742448F152 |
| SHA256: | CD82B091BA5B297D1E1AC245DC91C740166396F19D62DF1569D2AE33A52CABA4 |
| SSDEEP: | 98304:qmgF7Ngb7nVKrHlqTqPzoixfg+hGs6jGQe11Fgu:+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- lua.exe (PID: 5384)
Checks for external IP
- lua.exe (PID: 5384)
- svchost.exe (PID: 2196)
Connects to the server without a host name
- lua.exe (PID: 5384)
INFO
Manual execution by a user
- lua.exe (PID: 4776)
- cmd.exe (PID: 5324)
- cmd.exe (PID: 2040)
- lua.exe (PID: 5772)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4244)
Checks supported languages
- lua.exe (PID: 4776)
- lua.exe (PID: 5384)
- lua.exe (PID: 1676)
- lua.exe (PID: 5772)
Reads the computer name
- lua.exe (PID: 5384)
Reads the machine GUID from the registry
- lua.exe (PID: 5384)
Checks proxy server information
- lua.exe (PID: 5384)
Creates files or folders in the user directory
- lua.exe (PID: 5384)
Reads the software policy settings
- lua.exe (PID: 5384)
- slui.exe (PID: 5244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:28 11:16:44 |
| ZipCRC: | 0x17acc81c |
| ZipCompressedSize: | 327292 |
| ZipUncompressedSize: | 327292 |
| ZipFileName: | cli.txt |
Total processes
142
Monitored processes
16
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | lua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | lua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | lua.exe cli.txt | C:\Users\admin\Desktop\lua.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2040 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Launcher.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Muck.Crypter.FUD.AES.Algorithm.v1.9.8.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4776 | "C:\Users\admin\Desktop\lua.exe" | C:\Users\admin\Desktop\lua.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225547 Modules
| |||||||||||||||
Total events
3 710
Read events
3 673
Write events
24
Delete events
13
Modification events
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Muck.Crypter.FUD.AES.Algorithm.v1.9.8.zip | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
2
Suspicious files
9
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4244 | WinRAR.exe | C:\Users\admin\Desktop\lua51.dll | executable | |
MD5:4EBD617A3AD9A9619172BD14A902A400 | SHA256:C7A657AF5455812FB215A8888B7E3FD8FA1BA27672A3ED9021EB6004EFF271AC | |||
| 5384 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:C22301B5245B697AA0D960E7D3A2D560 | SHA256:8E63BB9D833DDFF90DB225799A6B20821540B2A10AB3764EE07767259765DA0E | |||
| 4244 | WinRAR.exe | C:\Users\admin\Desktop\Launcher.cmd | text | |
MD5:BEC5BD9518AF1159D2B892231D953395 | SHA256:076727FB465DB03C8F3538E2EECFE7C648336A3A8C40E97519F35F893226453F | |||
| 5384 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:A5333BBDA908BBA68EEA5E22858D7125 | SHA256:C4FAA7D92DCA4BAE1DE85754073D559F0E3113CDB43BF3EAC23220D5841E34C9 | |||
| 5384 | lua.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\json[1].json | binary | |
MD5:311A19D0C829734CF62B6A1FE9EE9045 | SHA256:332DA67A4601B0F0EE163009F1BE40EDA492A27340B6DB0CD8D5FD12AFD2693B | |||
| 4244 | WinRAR.exe | C:\Users\admin\Desktop\cli.txt | text | |
MD5:BD48378E8370372F1C59E404BCB5C840 | SHA256:5FF619A187668B9FBF6426A4F3804F52900C7E0B2A9F3E8E140DEB00FB9F1829 | |||
| 4244 | WinRAR.exe | C:\Users\admin\Desktop\lua.exe | executable | |
MD5:00F60EE3FF2DEE681B5D7D442009B2C2 | SHA256:5343326FB0B4F79C32276F08FFCC36BD88CDE23AA19962BD1E8D8B80F5D33953 | |||
| 5384 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:61302199C5911A5B1F51DCA317395A31 | SHA256:C16A23678889F905713DFC7248D0C88117F2A0DD9A187AE7A01E16BF6F9A6621 | |||
| 5384 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:2123D0242379DAD9A20B81417813A5AA | SHA256:3E2B1820B7D1866259C59826E2B155EB4510D8C5EDBC2BC648F52FBFEB552B1A | |||
| 5384 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\45266914391285466AEA1EA8BECBA90A_AFA50D4C705D6DE2B3101866B18F3B18 | binary | |
MD5:3CBA88223833818170316878C1CF9BD5 | SHA256:37E484D565E0BA815C5481A349F13D843D557BC5F802DDC50446470AA3C93C0A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
24
DNS requests
18
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4180 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.73:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4180 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5384 | lua.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | whitelisted |
5384 | lua.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
5384 | lua.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5384 | lua.exe | GET | 200 | 142.250.184.195:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
5384 | lua.exe | GET | 200 | 216.58.212.131:80 | http://o.pki.goog/s/wr1/syE/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQwHTUyHgfAxFi3r4z8dPC7p%2BvIYAQUZmlJ1N4qnJEDz4kOJLgOMANuiC4CEQCzIZwUD2fxGg1YekhLZbuP | unknown | — | — | whitelisted |
5384 | lua.exe | POST | 200 | 91.196.32.114:80 | http://91.196.32.114/api/YTAsODYsODIsOWQsYTEsODgsOTAsOTUsNjUsN2Qs | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.164.73:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4180 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4180 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4180 | SIHClient.exe | 52.165.164.15:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
ip-api.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
polygon-rpc.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
5384 | lua.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |