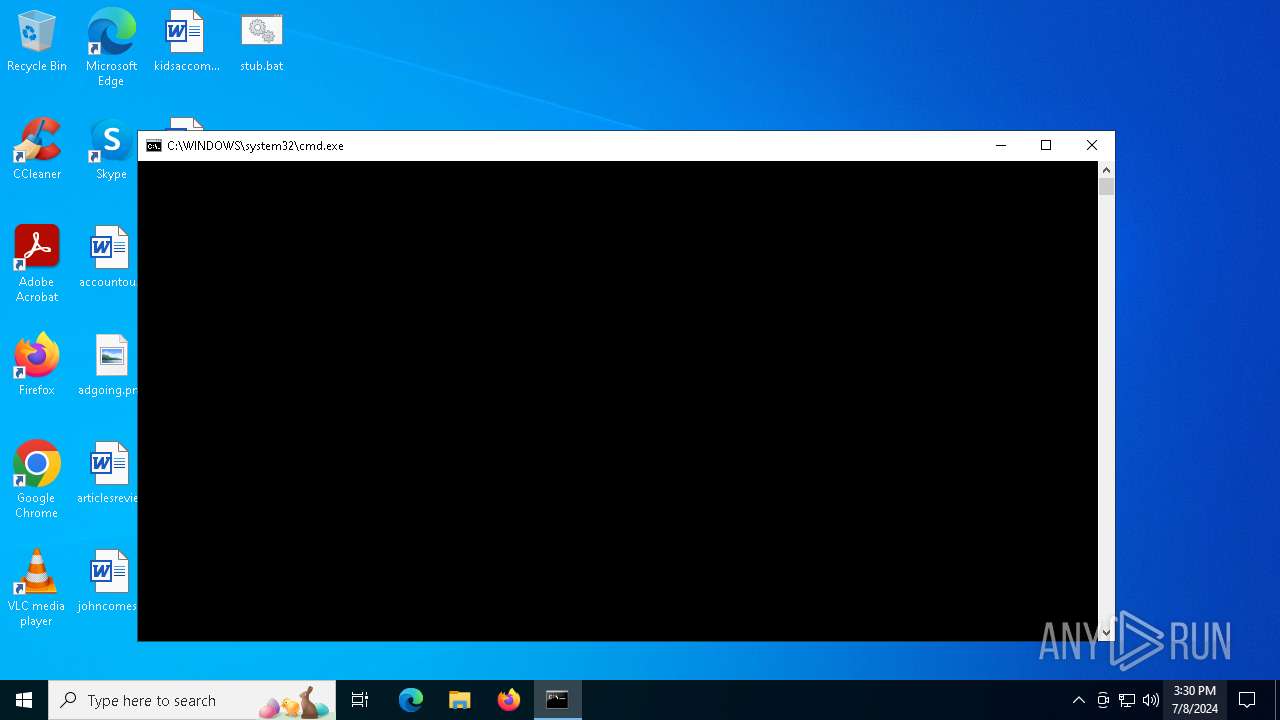
| File name: | stub.bat |
| Full analysis: | https://app.any.run/tasks/ce03744d-bb4b-492d-8c4b-bee1913af4ed |
| Verdict: | Malicious activity |
| Analysis date: | July 08, 2024, 15:30:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (65040), with CRLF line terminators |
| MD5: | C27B8C9F05C86817D8D287F0D0BD8698 |
| SHA1: | 239748A1871A85C7DF6733BC24D9497A331ACA87 |
| SHA256: | CD6C05138680001D640A47ED988487797A4B77E95BFF6C4F57AE57D294AA53E1 |
| SSDEEP: | 49152:/mThC67EFbMUKiKknefnfIlTYhjwHs0j+VqdyvZWs6sT/Pj5wSe/XDX/DlbfZ5+m:n |
MALICIOUS
Drops the executable file immediately after the start
- powershell.exe (PID: 4800)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 4800)
- $ktm-powershell.exe (PID: 5484)
Application was injected by another process
- svchost.exe (PID: 1060)
- svchost.exe (PID: 1172)
- svchost.exe (PID: 1180)
- svchost.exe (PID: 1252)
- svchost.exe (PID: 1360)
- svchost.exe (PID: 1312)
- lsass.exe (PID: 768)
- svchost.exe (PID: 320)
- dwm.exe (PID: 852)
- svchost.exe (PID: 1040)
- svchost.exe (PID: 1100)
- winlogon.exe (PID: 684)
- svchost.exe (PID: 1400)
- svchost.exe (PID: 1464)
- svchost.exe (PID: 1620)
- svchost.exe (PID: 1532)
- svchost.exe (PID: 1600)
- svchost.exe (PID: 1608)
- svchost.exe (PID: 1744)
- svchost.exe (PID: 1752)
- svchost.exe (PID: 1836)
- svchost.exe (PID: 1892)
- svchost.exe (PID: 1984)
- svchost.exe (PID: 2280)
- svchost.exe (PID: 2376)
- svchost.exe (PID: 2348)
- svchost.exe (PID: 2424)
- svchost.exe (PID: 2592)
- spoolsv.exe (PID: 2544)
- svchost.exe (PID: 2948)
- svchost.exe (PID: 2696)
- svchost.exe (PID: 3000)
- svchost.exe (PID: 2732)
- svchost.exe (PID: 2956)
- svchost.exe (PID: 3032)
- OfficeClickToRun.exe (PID: 3040)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 2816)
- svchost.exe (PID: 1900)
- svchost.exe (PID: 2092)
- svchost.exe (PID: 2168)
- svchost.exe (PID: 2384)
- svchost.exe (PID: 2760)
- svchost.exe (PID: 3196)
- svchost.exe (PID: 3240)
- svchost.exe (PID: 2900)
- svchost.exe (PID: 3368)
- svchost.exe (PID: 3608)
- svchost.exe (PID: 3884)
- svchost.exe (PID: 3732)
- dasHost.exe (PID: 3948)
- svchost.exe (PID: 1488)
- svchost.exe (PID: 4184)
- svchost.exe (PID: 4032)
- svchost.exe (PID: 4344)
- svchost.exe (PID: 4548)
- svchost.exe (PID: 4228)
- explorer.exe (PID: 4612)
- ctfmon.exe (PID: 4404)
- RuntimeBroker.exe (PID: 5088)
- svchost.exe (PID: 4824)
- dllhost.exe (PID: 5352)
- RuntimeBroker.exe (PID: 5256)
- RuntimeBroker.exe (PID: 5796)
- dllhost.exe (PID: 6084)
- svchost.exe (PID: 1132)
- dllhost.exe (PID: 6096)
- MoUsoCoreWorker.exe (PID: 3164)
- svchost.exe (PID: 3092)
- MusNotification.exe (PID: 5524)
- UsoClient.exe (PID: 2176)
- svchost.exe (PID: 2536)
- svchost.exe (PID: 4804)
- audiodg.exe (PID: 1096)
- svchost.exe (PID: 3644)
- svchost.exe (PID: 5588)
- svchost.exe (PID: 3028)
- uhssvc.exe (PID: 2656)
- svchost.exe (PID: 1196)
- UserOOBEBroker.exe (PID: 844)
- ApplicationFrameHost.exe (PID: 1028)
- svchost.exe (PID: 6004)
- UsoClient.exe (PID: 652)
- MusNotificationUx.exe (PID: 4172)
- WmiPrvSE.exe (PID: 3908)
- UsoClient.exe (PID: 2032)
- sihost.exe (PID: 4156)
- svchost.exe (PID: 4384)
Runs injected code in another process
- $ktm-powershell.exe (PID: 5484)
Starts PowerShell from an unusual location
- conhost.exe (PID: 5504)
- $ktm-powershell.exe (PID: 5484)
Known privilege escalation attack
- dllhost.exe (PID: 2100)
SUSPICIOUS
Starts CMD.EXE for commands execution
- explorer.exe (PID: 4612)
The process executes Powershell scripts
- cmd.exe (PID: 1280)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 1280)
Executing commands from a ".bat" file
- explorer.exe (PID: 4612)
Executable content was dropped or overwritten
- powershell.exe (PID: 4800)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1280)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 1280)
The process creates files with name similar to system file names
- powershell.exe (PID: 4800)
Process drops legitimate windows executable
- powershell.exe (PID: 4800)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4800)
- $ktm-powershell.exe (PID: 5484)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 4800)
Checks Windows Trust Settings
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
- OfficeClickToRun.exe (PID: 3040)
Reads security settings of Internet Explorer
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
Application launched itself
- $ktm-powershell.exe (PID: 5484)
Reads the date of Windows installation
- $ktm-powershell.exe (PID: 5484)
Possibly patching Antimalware Scan Interface function (YARA)
- conhost.exe (PID: 5504)
- dllhost.exe (PID: 2100)
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
- conhost.exe (PID: 1068)
- WmiPrvSE.exe (PID: 3908)
Checks for external IP
- $ktm-powershell.exe (PID: 5484)
- svchost.exe (PID: 2168)
Potential Corporate Privacy Violation
- $ktm-powershell.exe (PID: 5484)
Connects to unusual port
- $ktm-powershell.exe (PID: 5484)
INFO
Gets data length (POWERSHELL)
- powershell.exe (PID: 4800)
- $ktm-powershell.exe (PID: 5484)
Reads the software policy settings
- lsass.exe (PID: 768)
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
- OfficeClickToRun.exe (PID: 3040)
Disables trace logs
- cmstp.exe (PID: 5344)
- $ktm-powershell.exe (PID: 5484)
Checks transactions between databases Windows and Oracle
- cmstp.exe (PID: 5344)
Checks supported languages
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
Process checks Powershell version
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
Reads the machine GUID from the registry
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
- OfficeClickToRun.exe (PID: 3040)
Reads the computer name
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
Create files in a temporary directory
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 3040)
Creates a writable file in the system directory
- svchost.exe (PID: 1312)
Reads Environment values
- $ktm-powershell.exe (PID: 5484)
- $ktm-powershell.exe (PID: 1192)
Process checks computer location settings
- $ktm-powershell.exe (PID: 5484)
Checks proxy server information
- $ktm-powershell.exe (PID: 5484)
Reads the time zone
- MusNotificationUx.exe (PID: 4172)
Reads Windows Product ID
- WmiPrvSE.exe (PID: 3908)
Creates files in the program directory
- MoUsoCoreWorker.exe (PID: 3164)
- MusNotificationUx.exe (PID: 4172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
130
Monitored processes
97
Malicious processes
9
Suspicious processes
85
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 652 | "C:\WINDOWS\system32\usoclient.exe" StartScan | C:\Windows\System32\UsoClient.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: UsoClient Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 844 | C:\Windows\System32\oobe\UserOOBEBroker.exe -Embedding | C:\Windows\System32\oobe\UserOOBEBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: User OOBE Broker Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 852 | "dwm.exe" | C:\Windows\System32\dwm.exe | winlogon.exe | ||||||||||||
User: DWM-1 Company: Microsoft Corporation Integrity Level: SYSTEM Description: Desktop Window Manager Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | C:\WINDOWS\system32\ApplicationFrameHost.exe -Embedding | C:\Windows\System32\ApplicationFrameHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Application Frame Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s gpsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1060 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s DsmSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | $ktm-powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
48 763
Read events
48 178
Write events
335
Delete events
250
Modification events
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000004026E |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456249F86704CD0354CAF53943DFF6B26B6 | |||
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010013000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000015000000000000006100630063006F0075006E0074006F00750074007000750074002E007200740066003E002000200000000F000000000000006100640067006F0069006E0067002E0070006E0067003E002000200000001600000000000000610072007400690063006C00650073007200650076006900650077002E007200740066003E0020002000000011000000000000006A006F0068006E0063006F006D00650073002E007200740066003E0020002000000019000000000000006B006900640073006100630063006F006D006D006F0064006100740069006F006E002E007200740066003E0020002000000010000000000000006D006100700073006E0061006D0065002E007200740066003E002000200000000E000000000000006D00610072006B00640063002E007200740066003E00200020000000140000000000000070006F006B0065007200770065006400640069006E0067002E0070006E0067003E002000200000001800000000000000730063006F00740074007200650063006F006D006D0065006E006400650064002E0070006E0067003E002000200000001600000000000000730074006F00720065006D00610072006B006500740069006E0067002E007200740066003E002000200000000C0000000000000073007400750062002E006200610074003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001300000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A0401100000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000004040000000001200 | |||
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 1B068C6600000000 | |||
| (PID) Process: | (4404) ctfmon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Input\TypingInsights |
| Operation: | write | Name: | Insights |
Value: 02000000071DE8C131CC8360A3D6D9C1330A686B165ABA2E235F5A5C | |||
| (PID) Process: | (1312) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{F93AD50A-2FB2-4A34-88EF-786903C710ED} |
| Operation: | write | Name: | DynamicInfo |
Value: 03000000C09775A51C59DA010A9C25C34BD1DA010000000005400080451B57C94BD1DA01 | |||
| (PID) Process: | (768) lsass.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits |
| Operation: | write | Name: | SecureTimeHigh |
Value: 5E3432F6CE6FDA01 | |||
| (PID) Process: | (768) lsass.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits |
| Operation: | write | Name: | SecureTimeEstimated |
Value: 5ECC6D94C66FDA01 | |||
| (PID) Process: | (768) lsass.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits |
| Operation: | write | Name: | SecureTimeLow |
Value: 5E64A932BE6FDA01 | |||
| (PID) Process: | (768) lsass.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\W32Time\SecureTimeLimits\RunTime |
| Operation: | write | Name: | SecureTimeTickCount |
Value: 34FD1C0000000000 | |||
Executable files
1
Suspicious files
62
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4800 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wzxzuchn.i2v.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4612 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 5484 | $ktm-powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_aeldhbvy.olq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1608 | svchost.exe | C:\Windows\Prefetch\MOUSOCOREWORKER.EXE-681A8FEE.pf | binary | |
MD5:0DD026228B862A173BCD00838B4CC816 | SHA256:36A81332438CDD88162F9669AABEE9D4F0D1EA163050C9CBEA62A50A03EF26BE | |||
| 4800 | powershell.exe | C:\Users\admin\AppData\Local\$ktm-powershell.exe | executable | |
MD5:2E5A8590CF6848968FC23DE3FA1E25F1 | SHA256:9785001B0DCF755EDDB8AF294A373C0B87B2498660F724E76C4D53F9C217C7A3 | |||
| 1608 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-0C2D202C.pf | binary | |
MD5:FBD627B3D2908B6D20B57F431634534D | SHA256:5B8C0B164021528882C91184FDEDE7402B341B9B86B9A30A461F7FBA9CAEC268 | |||
| 1608 | svchost.exe | C:\Windows\Prefetch\CONSENT.EXE-531BD9EA.pf | binary | |
MD5:825052F0CE5A243A53D8E80BE31DBDC9 | SHA256:937258123135CDAEA25830E9A9395E47C5554395A9351D95EFC453074808740F | |||
| 4800 | powershell.exe | C:\Users\admin\AppData\Local\Temp\$ktm-uac.ini | ini | |
MD5:4DB235719A2913AED13A679176245CC7 | SHA256:F2FFBBC3BF6C369A0BAEBFD6A7066808C653999D725E64E80C7279158A7CC9FD | |||
| 3164 | MoUsoCoreWorker.exe | C:\WINDOWS\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:CBA2426F2AAFE31899569ACE05E89796 | SHA256:A465FEBE8A024E3CDB548A3731B2EA60C7B2919E941A24B9A42890B2B039B85A | |||
| 3164 | MoUsoCoreWorker.exe | C:\WINDOWS\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:F78C276898B23FB83E294B8955073274 | SHA256:3A920D5962BC574FD1FCC28DD439C57CEC666633BF537333C894DBCFA396A680 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
36
DNS requests
6
Threats
54
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3164 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3164 | MoUsoCoreWorker.exe | GET | 200 | 95.101.54.128:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 104.26.13.205:443 | https://api.ipify.org/ | unknown | — | — | unknown |
— | — | GET | 200 | 172.67.74.152:443 | https://api.ipify.org/ | unknown | — | — | unknown |
— | — | GET | 200 | 172.67.74.152:443 | https://api.ipify.org/ | unknown | — | — | unknown |
— | — | GET | 200 | 104.26.13.205:443 | https://api.ipify.org/ | unknown | — | — | unknown |
— | — | GET | 200 | 104.26.12.205:443 | https://api.ipify.org/ | unknown | text | 11 b | unknown |
— | — | GET | 200 | 104.26.12.205:443 | https://api.ipify.org/ | unknown | text | 11 b | unknown |
— | — | GET | 200 | 104.26.13.205:443 | https://api.ipify.org/ | unknown | text | 11 b | unknown |
— | — | GET | 200 | 172.67.74.152:443 | https://api.ipify.org/ | unknown | text | 11 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2272 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3164 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2272 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3164 | MoUsoCoreWorker.exe | 95.101.54.128:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
3164 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5484 | $ktm-powershell.exe | 147.189.168.82:6001 | — | combahton GmbH | DE | unknown |
5484 | $ktm-powershell.exe | 172.67.74.152:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
3164 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.ipify.org |
| shared |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5484 | $ktm-powershell.exe | Potential Corporate Privacy Violation | ET POLICY Possible IP Check api.ipify.org |
2168 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
5484 | $ktm-powershell.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |