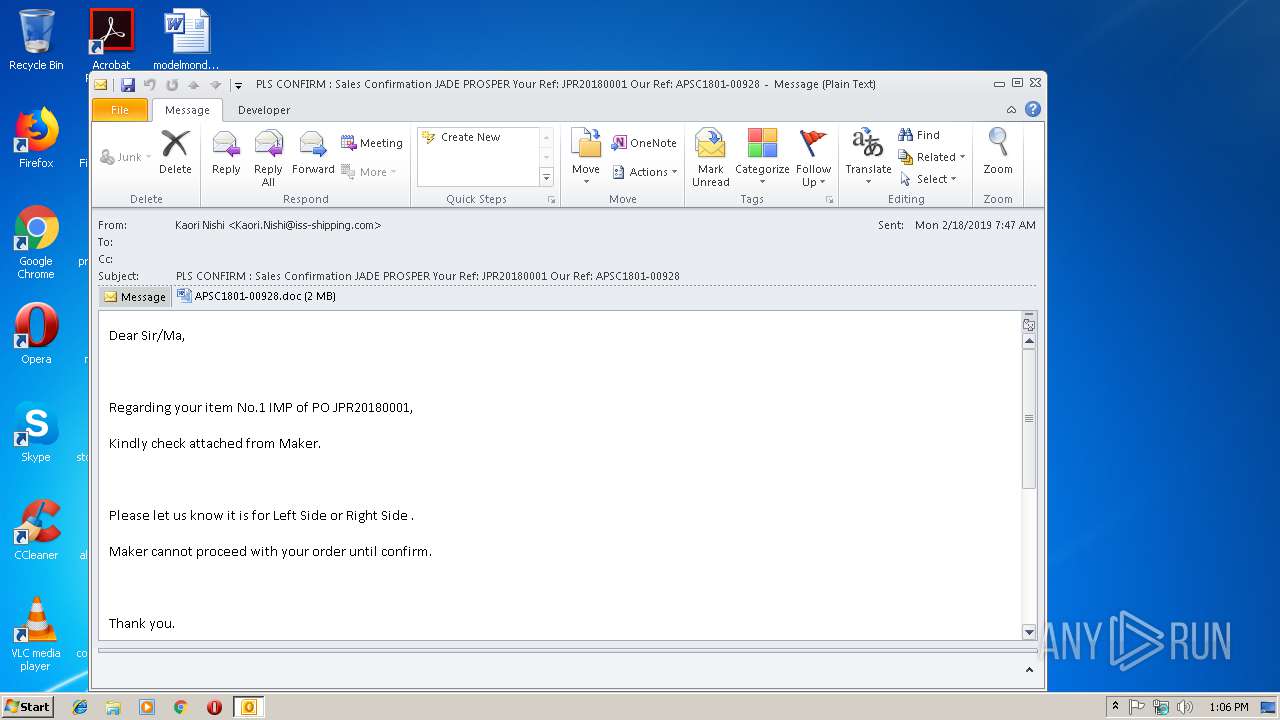
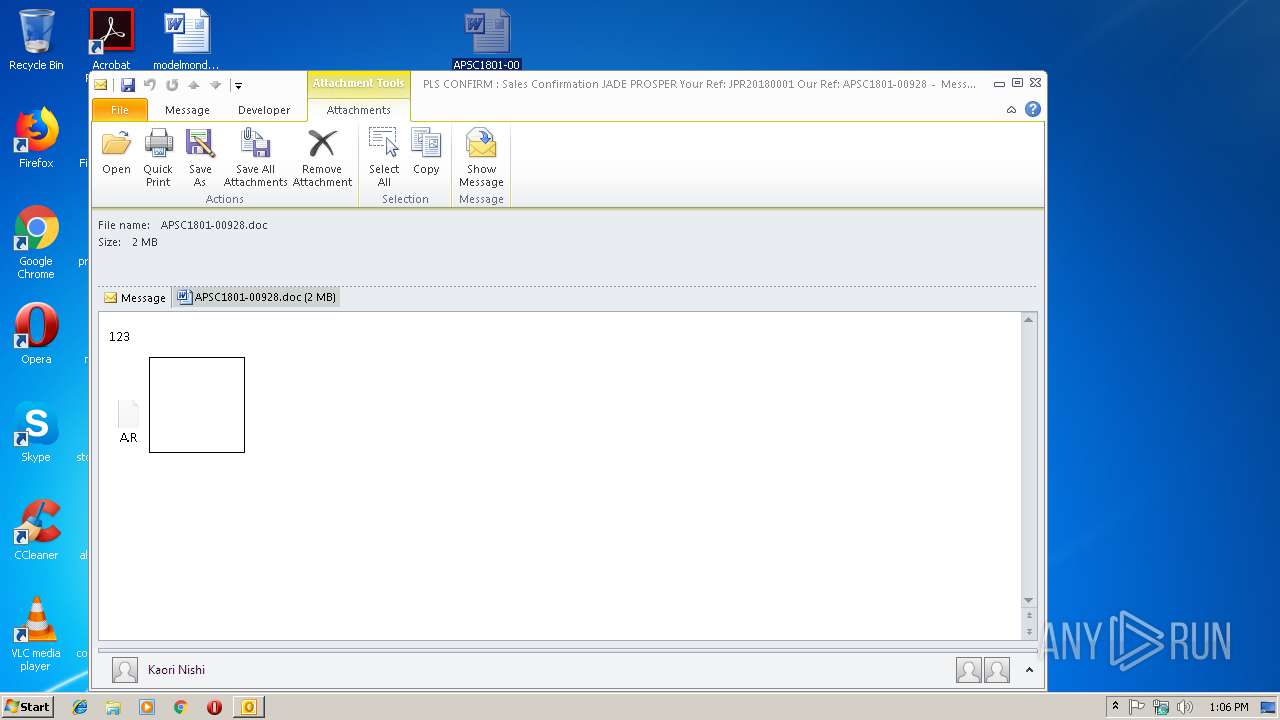
| File name: | ad.eml |
| Full analysis: | https://app.any.run/tasks/328cc88f-ee09-469c-aad4-05af466e7279 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2019, 13:05:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, UTF-8 Unicode text, with very long lines, with CRLF line terminators |
| MD5: | 13C8124A821487D5500F4B8E3A2B3E9D |
| SHA1: | DCDCEABD2576E7DF46A8D8F8D917C926AF3219A8 |
| SHA256: | CD4AC880AFA8BAA3D0DF88A2F276C5B5F100B9DF5B11B3D827B3D2E6EAF57E27 |
| SSDEEP: | 24576:u5NcJqgfRD2iiek6jXU2x384XfVRY54iy7EgYMZ0f:eXi7ieLQw3zVRYQEgYMZI |
MALICIOUS
Application was dropped or rewritten from another process
- A.R (PID: 2212)
- A.R (PID: 2268)
- EQNEDT32.EXE (PID: 3124)
- EQNEDT32.EXE (PID: 2608)
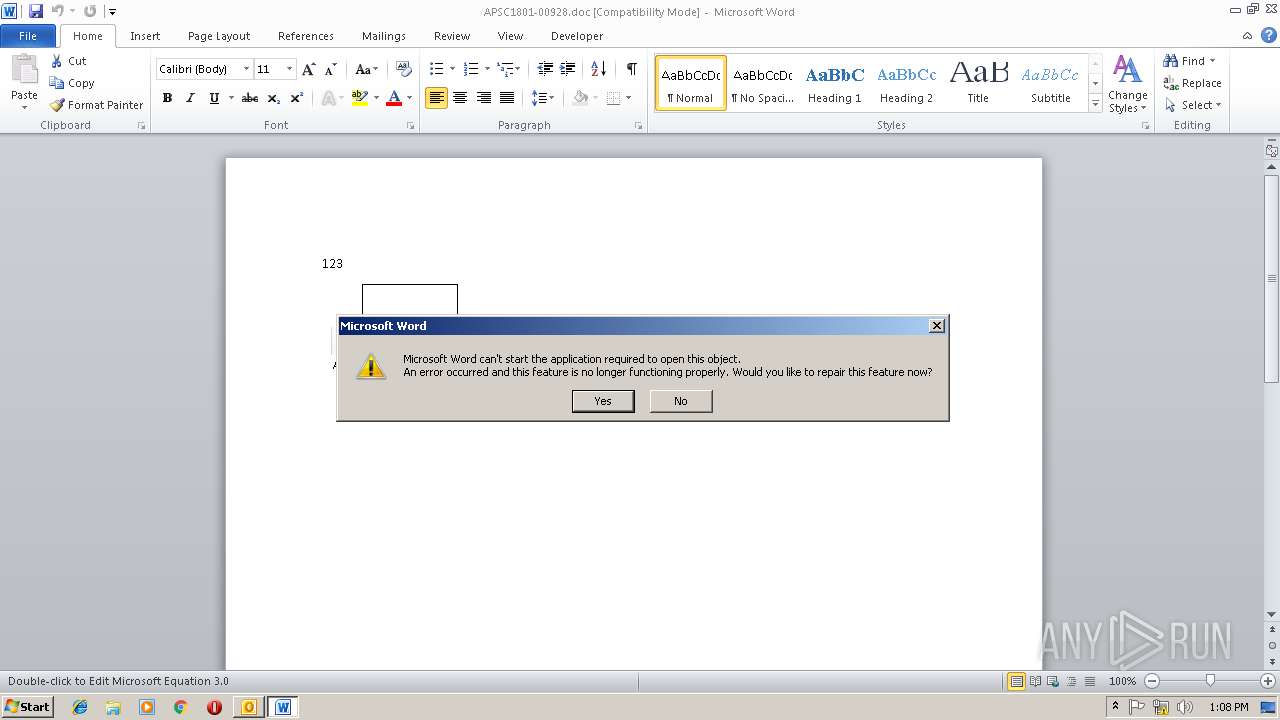
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3712)
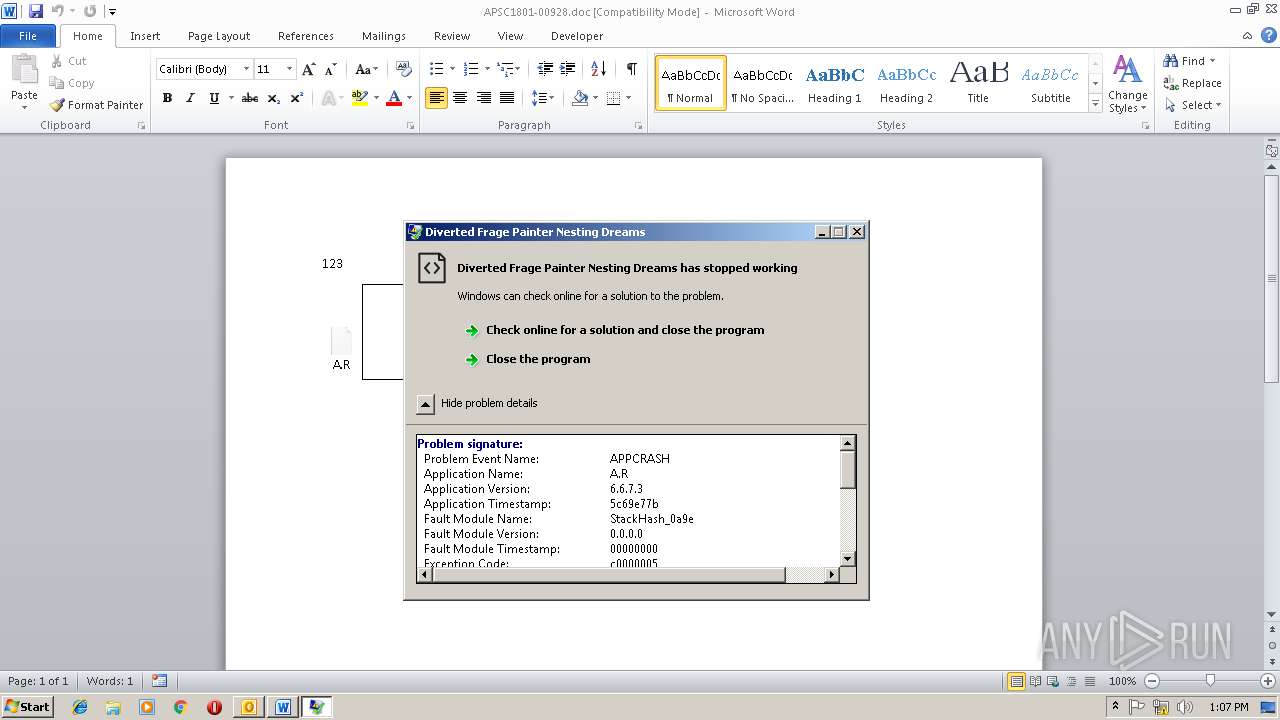
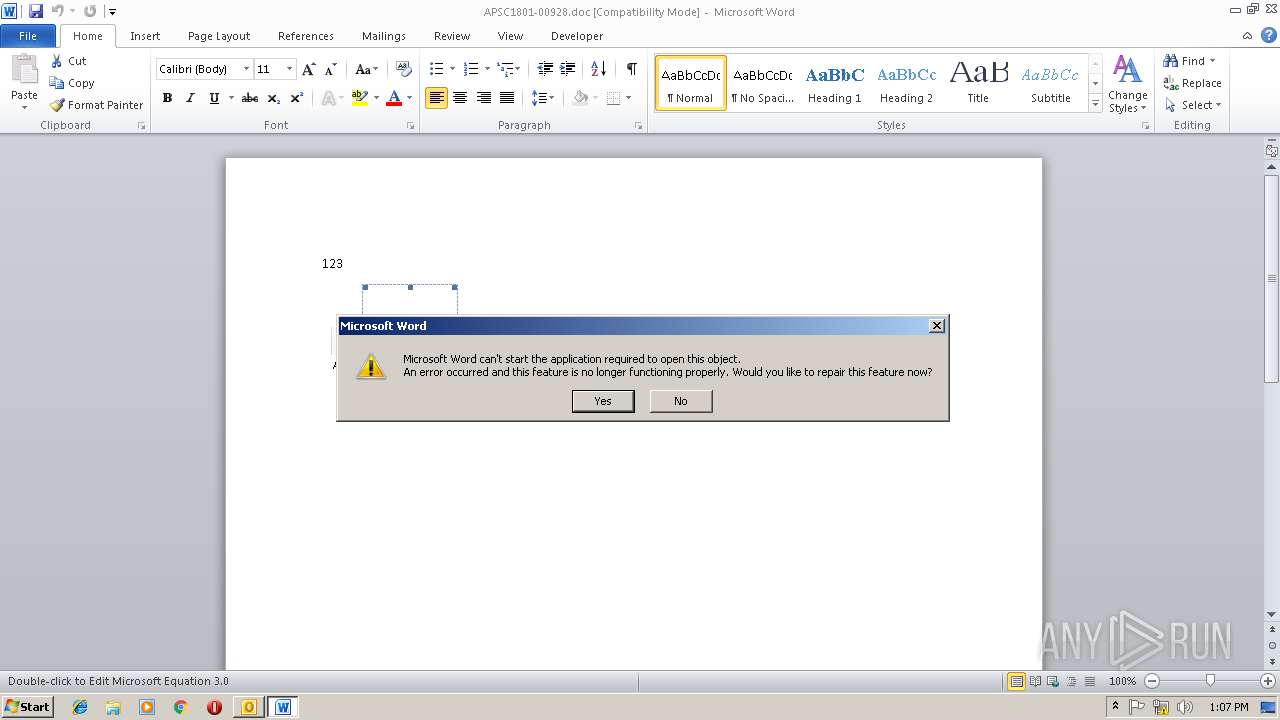
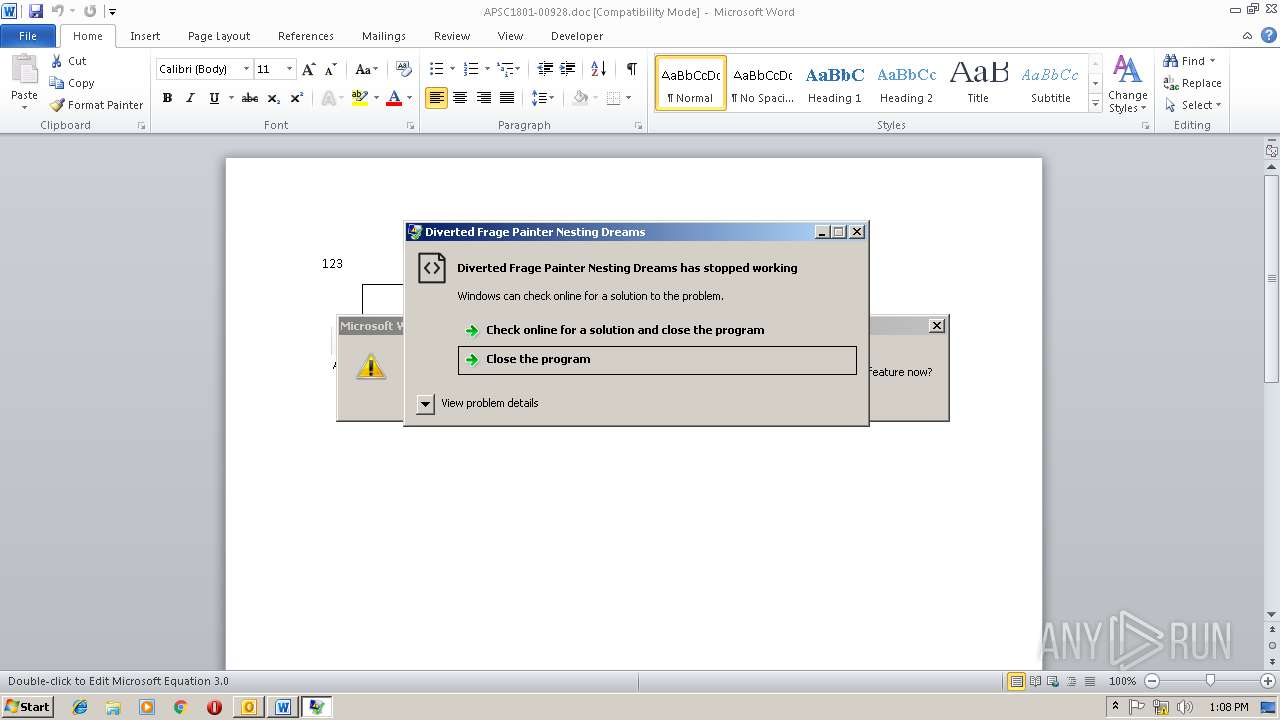
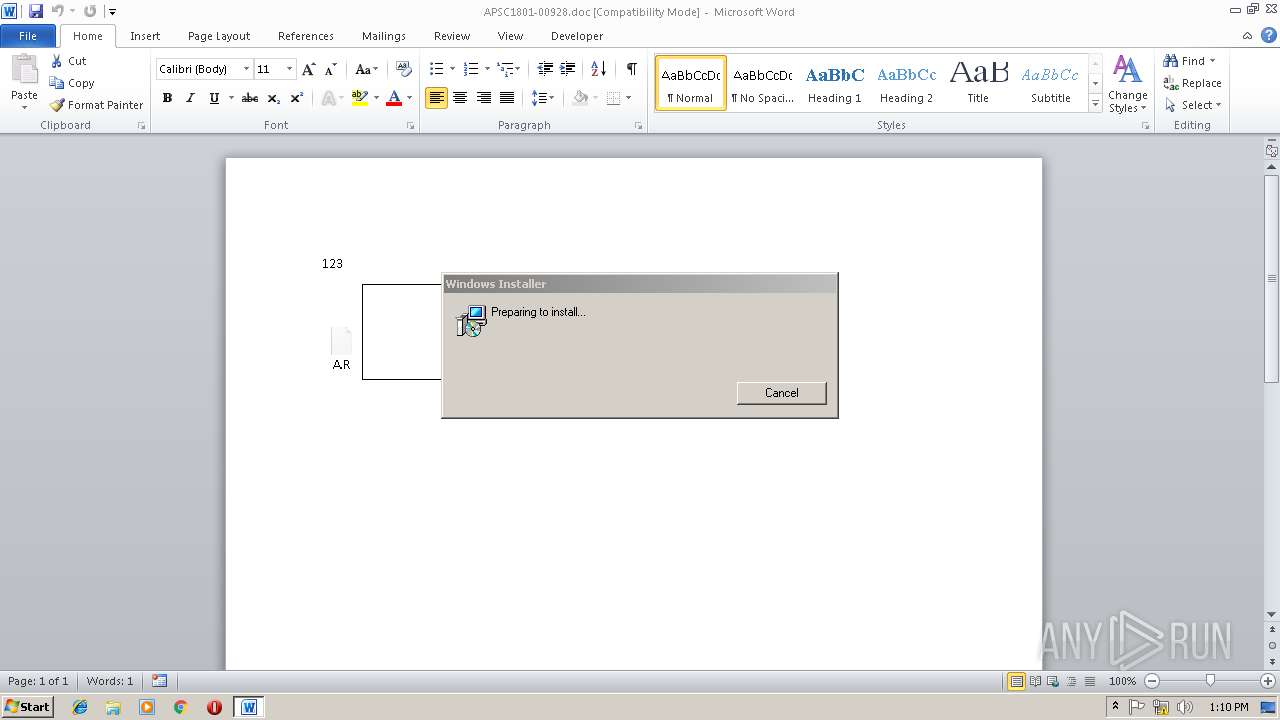
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3124)
- EQNEDT32.EXE (PID: 2608)
Loads dropped or rewritten executable
- Setup.exe (PID: 3904)
- WerFault.exe (PID: 3616)
- WerFault.exe (PID: 3296)
- EQNEDT32.EXE (PID: 2608)
- EQNEDT32.EXE (PID: 3124)
- OUTLOOK.EXE (PID: 2976)
- WINWORD.EXE (PID: 2328)
- WINWORD.EXE (PID: 3712)
- SearchProtocolHost.exe (PID: 3976)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2976)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2976)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 2976)
Starts CMD.EXE for commands execution
- EQNEDT32.EXE (PID: 3124)
- EQNEDT32.EXE (PID: 2608)
Starts application with an unusual extension
- CmD.exe (PID: 1816)
- CmD.exe (PID: 3200)
Executable content was dropped or overwritten
- Setup.exe (PID: 3904)
- MsiExec.exe (PID: 792)
- MsiExec.exe (PID: 3688)
- MsiExec.exe (PID: 2272)
- MsiExec.exe (PID: 4092)
- MsiExec.exe (PID: 3024)
- MsiExec.exe (PID: 2744)
- msiexec.exe (PID: 3104)
- MsiExec.exe (PID: 1300)
- MsiExec.exe (PID: 924)
- MsiExec.exe (PID: 2588)
- MsiExec.exe (PID: 3132)
Searches for installed software
- Setup.exe (PID: 3904)
Creates files in the Windows directory
- msiexec.exe (PID: 3104)
Creates COM task schedule object
- msiexec.exe (PID: 3104)
Removes files from Windows directory
- msiexec.exe (PID: 3104)
Modifies the open verb of a shell class
- msiexec.exe (PID: 3104)
INFO
Reads Microsoft Office registry keys
- SearchProtocolHost.exe (PID: 3976)
- WINWORD.EXE (PID: 2328)
- WINWORD.EXE (PID: 3712)
- OUTLOOK.EXE (PID: 2976)
- Setup.exe (PID: 3904)
- MsiExec.exe (PID: 3132)
Creates files in the user directory
- WINWORD.EXE (PID: 3712)
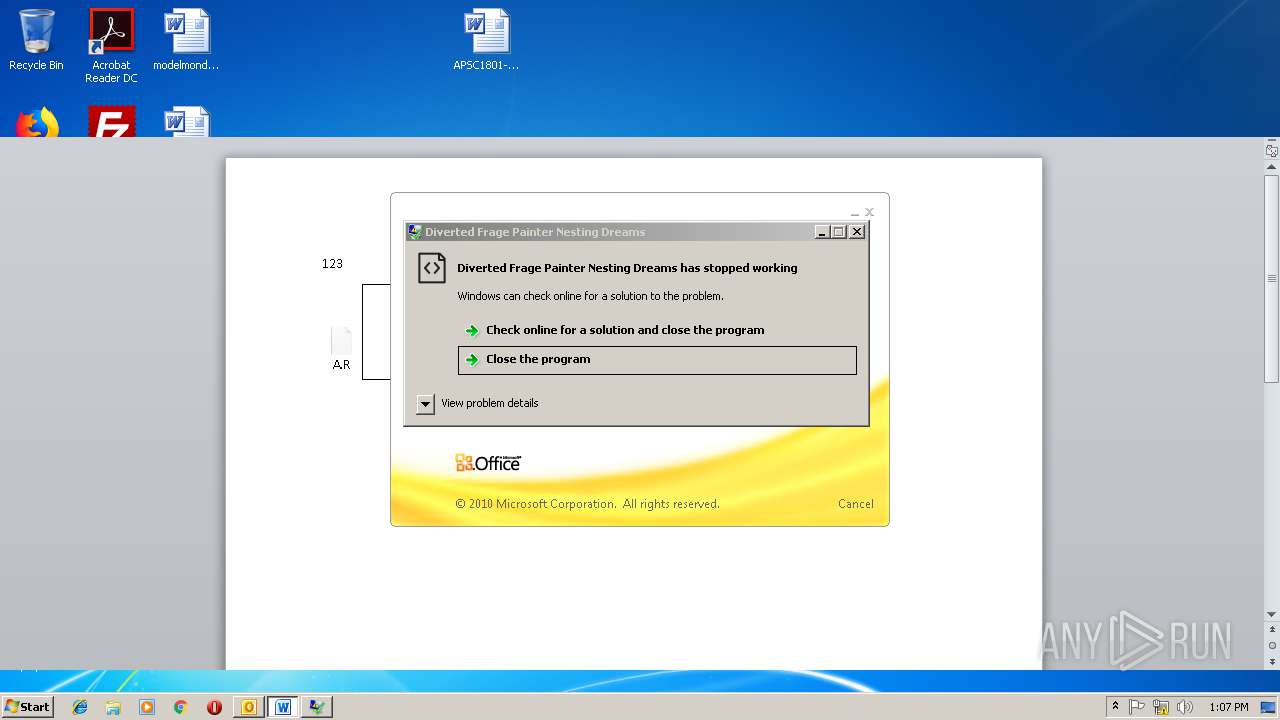
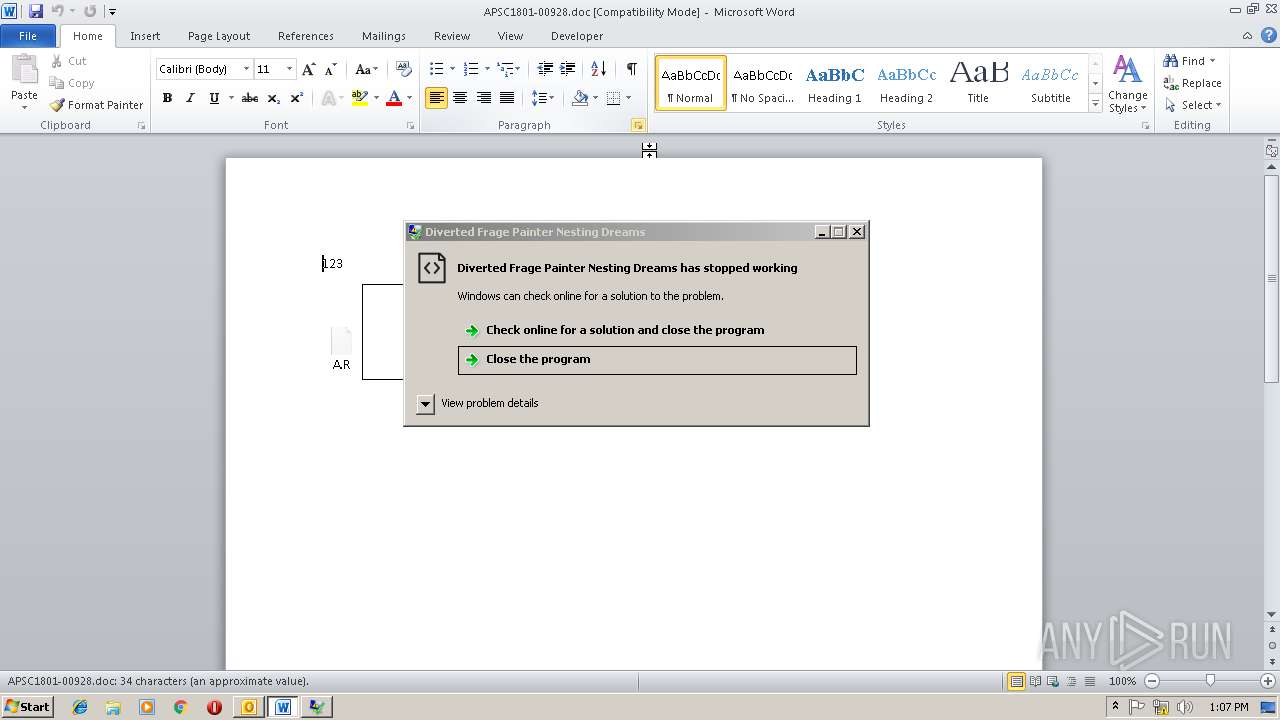
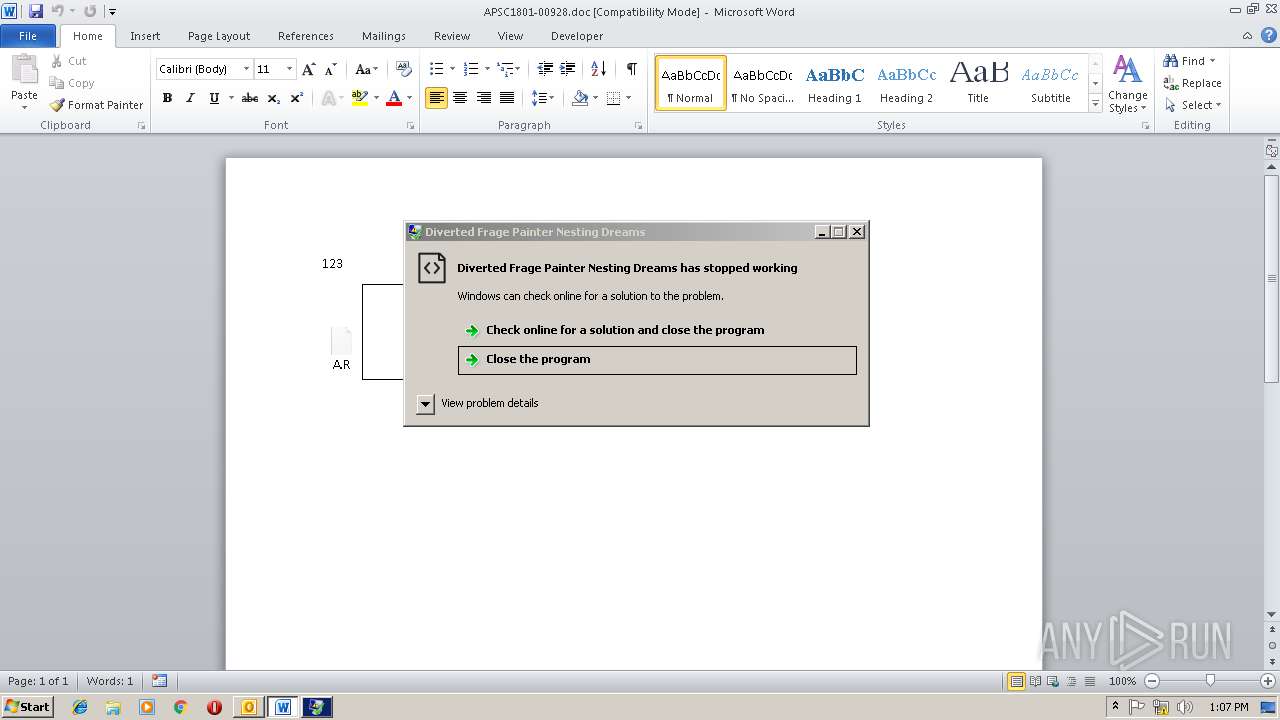
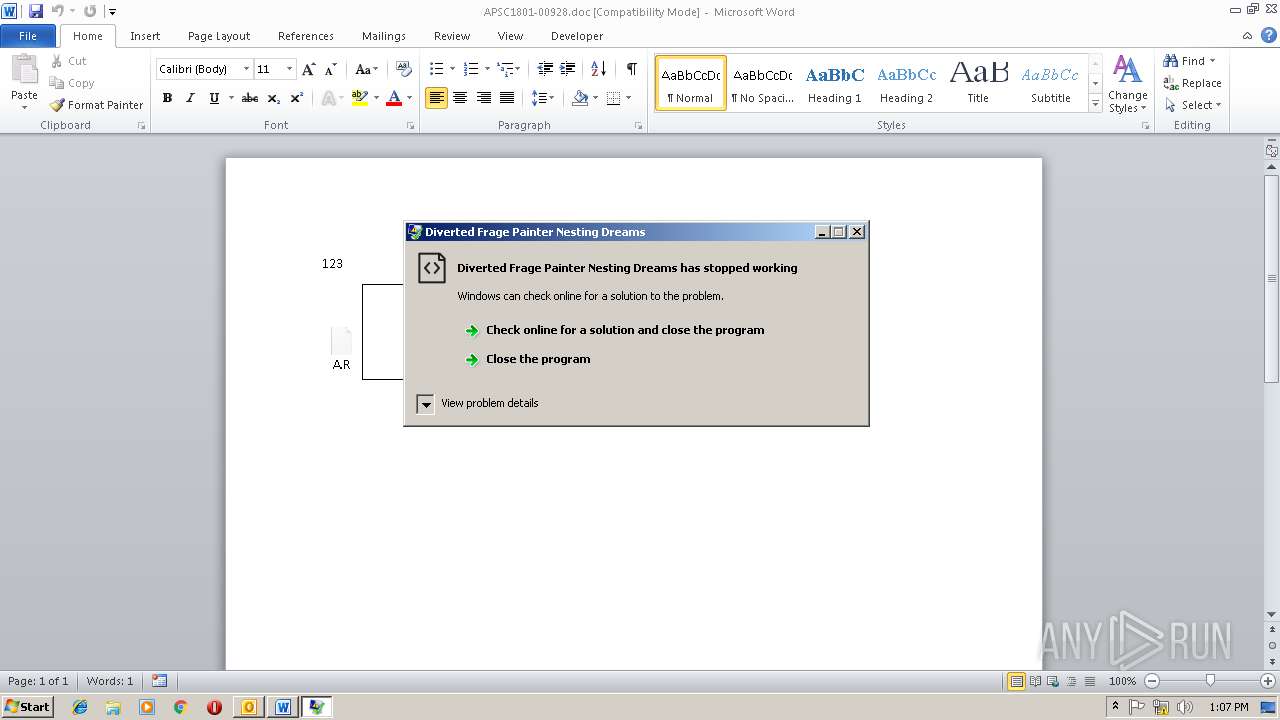
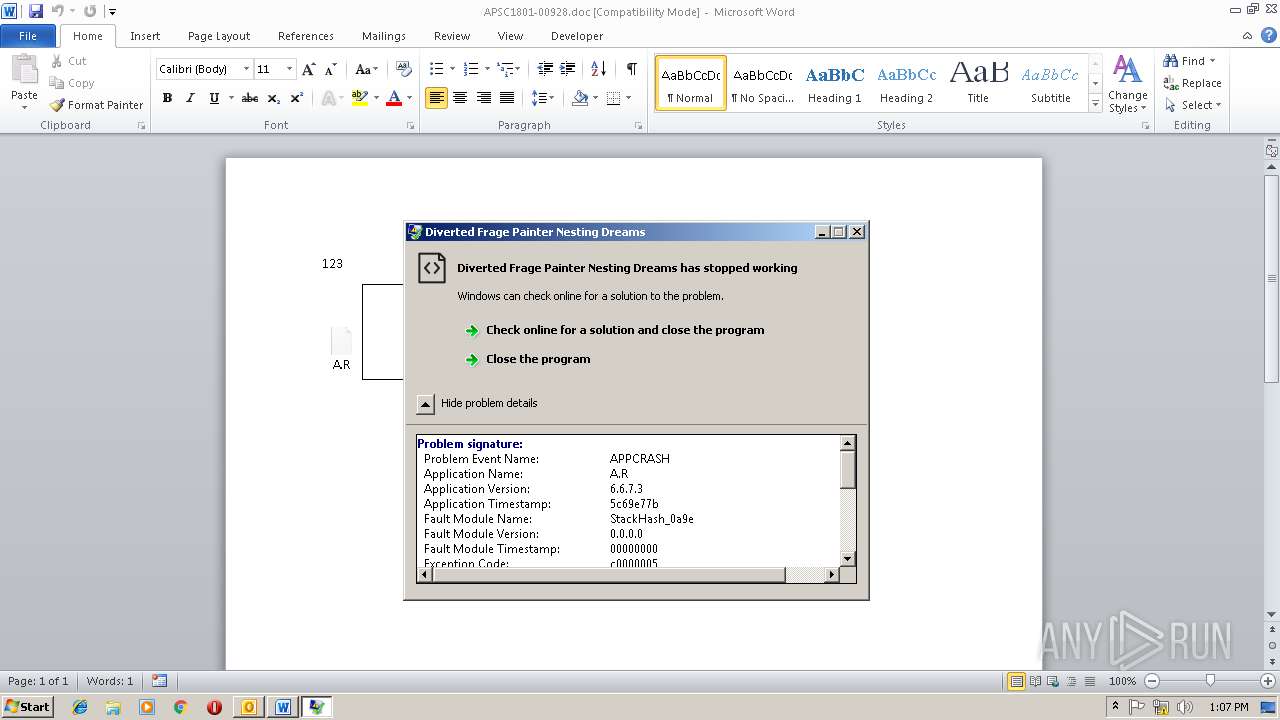
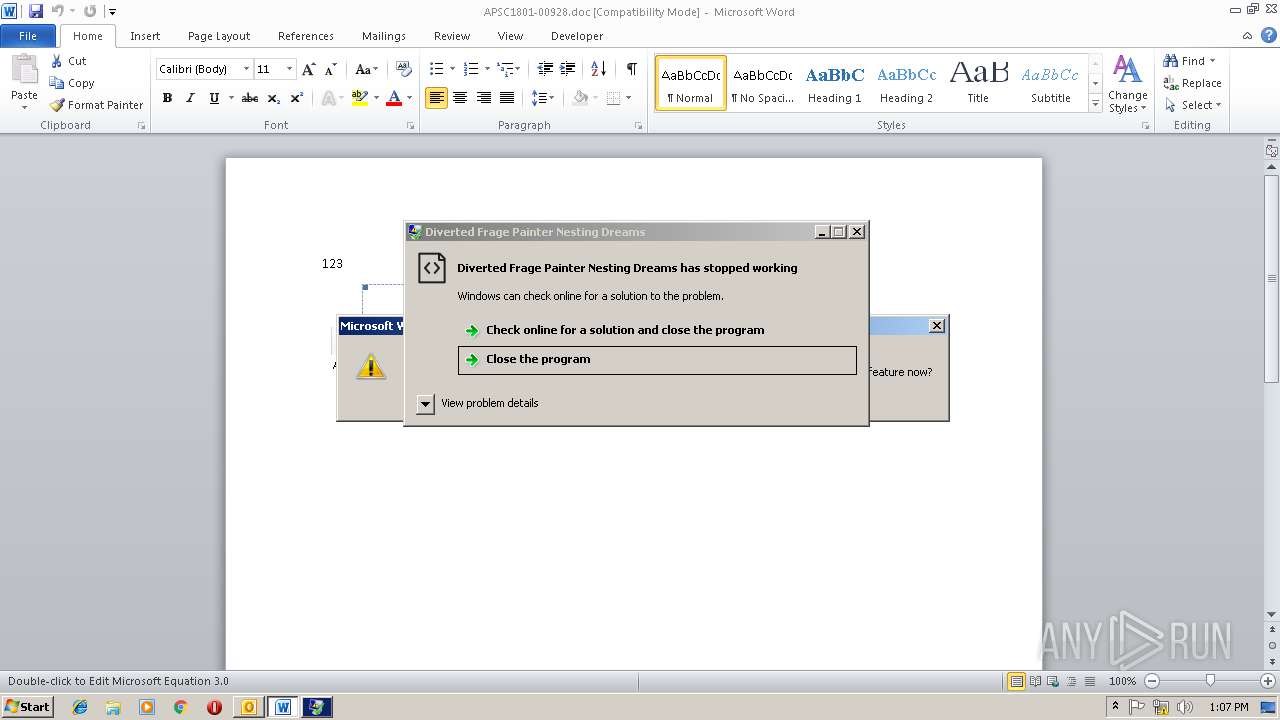
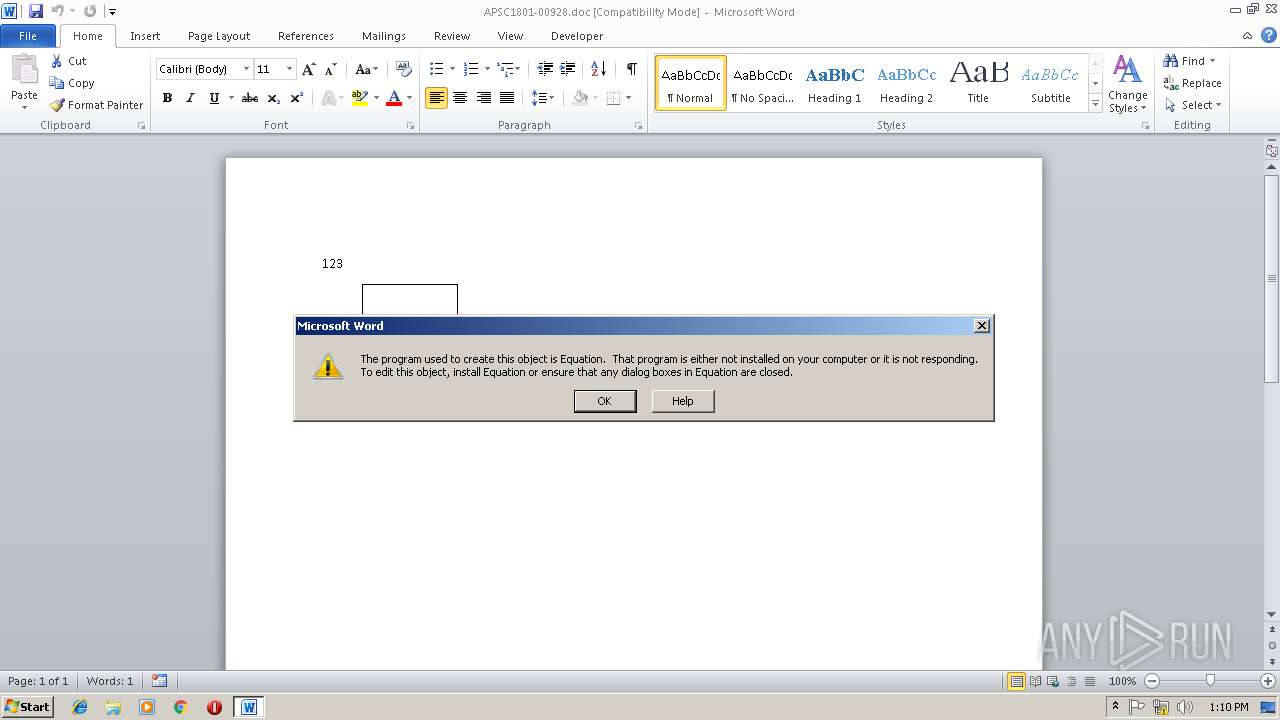
Application was crashed
- EQNEDT32.EXE (PID: 3124)
- A.R (PID: 2212)
- A.R (PID: 2268)
- EQNEDT32.EXE (PID: 2608)
Application launched itself
- msiexec.exe (PID: 3104)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2752)
- MsiExec.exe (PID: 792)
- msiexec.exe (PID: 3104)
- MsiExec.exe (PID: 3688)
- MsiExec.exe (PID: 4092)
- MsiExec.exe (PID: 2376)
- MsiExec.exe (PID: 2360)
- MsiExec.exe (PID: 2272)
- MsiExec.exe (PID: 3808)
- MsiExec.exe (PID: 3748)
- MsiExec.exe (PID: 1248)
- MsiExec.exe (PID: 2288)
- MsiExec.exe (PID: 2996)
- MsiExec.exe (PID: 3628)
- MsiExec.exe (PID: 2852)
- MsiExec.exe (PID: 3024)
- MsiExec.exe (PID: 1964)
- MsiExec.exe (PID: 2744)
- MsiExec.exe (PID: 3892)
- MsiExec.exe (PID: 1300)
- MsiExec.exe (PID: 2484)
- MsiExec.exe (PID: 924)
- MsiExec.exe (PID: 3440)
- MsiExec.exe (PID: 3768)
- MsiExec.exe (PID: 1380)
- MsiExec.exe (PID: 1316)
- MsiExec.exe (PID: 1244)
- MsiExec.exe (PID: 4024)
- MsiExec.exe (PID: 1940)
- MsiExec.exe (PID: 1756)
- MsiExec.exe (PID: 3168)
- MsiExec.exe (PID: 3032)
- MsiExec.exe (PID: 416)
- MsiExec.exe (PID: 4068)
- MsiExec.exe (PID: 2336)
- MsiExec.exe (PID: 3184)
- MsiExec.exe (PID: 2488)
- MsiExec.exe (PID: 2404)
- MsiExec.exe (PID: 3120)
- MsiExec.exe (PID: 2588)
- MsiExec.exe (PID: 1836)
- MsiExec.exe (PID: 4072)
- MsiExec.exe (PID: 2668)
- MsiExec.exe (PID: 2248)
- MsiExec.exe (PID: 280)
- MsiExec.exe (PID: 2548)
- MsiExec.exe (PID: 3132)
- MsiExec.exe (PID: 2352)
Creates files in the program directory
- MsiExec.exe (PID: 2752)
- MsiExec.exe (PID: 2360)
- MsiExec.exe (PID: 3808)
- MsiExec.exe (PID: 1248)
- MsiExec.exe (PID: 2852)
- msiexec.exe (PID: 3104)
- MsiExec.exe (PID: 1964)
- MsiExec.exe (PID: 3768)
- MsiExec.exe (PID: 3168)
- MsiExec.exe (PID: 1316)
- MsiExec.exe (PID: 2488)
- MsiExec.exe (PID: 1940)
- MsiExec.exe (PID: 3032)
- MsiExec.exe (PID: 1836)
- MsiExec.exe (PID: 4072)
- MsiExec.exe (PID: 2248)
- MsiExec.exe (PID: 4016)
- MsiExec.exe (PID: 3440)
- MsiExec.exe (PID: 2484)
Writes to a desktop.ini file (may be used to cloak folders)
- msiexec.exe (PID: 3104)
Creates a software uninstall entry
- msiexec.exe (PID: 3104)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 3104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
99
Monitored processes
62
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | C:\Windows\system32\MsiExec.exe -Embedding 5FD6584596A30A266B4F187A58CE763D | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 416 | C:\Windows\system32\MsiExec.exe -Embedding FE7D032BA4879276604A4D6B7C0C8A33 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 792 | C:\Windows\system32\MsiExec.exe -Embedding A00EB2206E81150E5EA75627B1248EF8 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | C:\Windows\system32\MsiExec.exe -Embedding 43C0AA17C85B57850BA356A746516876 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1244 | C:\Windows\system32\MsiExec.exe -Embedding A52FCBE15A87600AC4790267FCDA8158 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1248 | C:\Windows\system32\MsiExec.exe -Embedding 3EA8BFA424518163DC5605E11E858333 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1300 | C:\Windows\system32\MsiExec.exe -Embedding B4B6A8F1B8A42486C37B837E20C73AFD | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1316 | C:\Windows\system32\MsiExec.exe -Embedding D37B50C23B2DFE04F6A42BF8BD16E16F M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1380 | C:\Windows\system32\MsiExec.exe -Embedding E5EE95E91EAA0EC0C5153F9DD0DEA58D | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1756 | C:\Windows\system32\MsiExec.exe -Embedding 32807E563ECA58E7C88FE0D6CBDBEA20 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
27 866
Read events
14 764
Write events
10 706
Delete events
2 396
Modification events
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | r`% |
Value: 72602500A00B0000010000000000000000000000 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: A00B00000EF761B18AC7D40100000000 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219915360 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1313996821 | |||
Executable files
339
Suspicious files
44
Text files
86
Unknown types
138
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9CD2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp9ED7.tmp | — | |
MD5:— | SHA256:— | |||
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\ET6J3DI8\APSC1801-00928 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\OICE_C2AC63D4-D477-48FF-BE5C-E76146939964.0\C7137173.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3976 | SearchProtocolHost.exe | C:\Users\admin\Documents\Outlook Files\~honey@pot.com.pst.tmp | — | |
MD5:— | SHA256:— | |||
| 3976 | SearchProtocolHost.exe | C:\Users\admin\Documents\Outlook Files\~Outlook.pst.tmp | — | |
MD5:— | SHA256:— | |||
| 3712 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE792.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3976 | SearchProtocolHost.exe | C:\Users\admin\Documents\Outlook Files\honey@pot.com.pst | pst | |
MD5:— | SHA256:— | |||
| 3976 | SearchProtocolHost.exe | C:\Users\admin\Documents\Outlook Files\Outlook.pst | pst | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2976 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2976 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
msiexec.exe | Failed to release Service
|
msiexec.exe | Failed to release Service
|