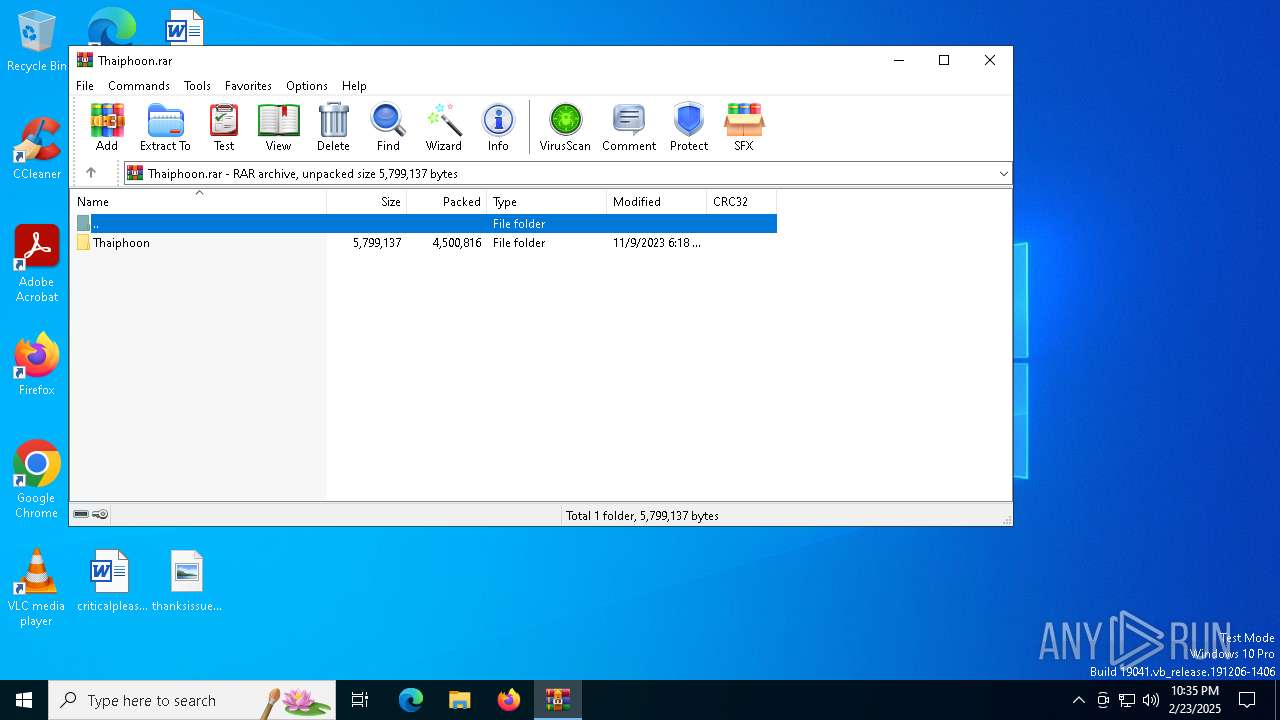
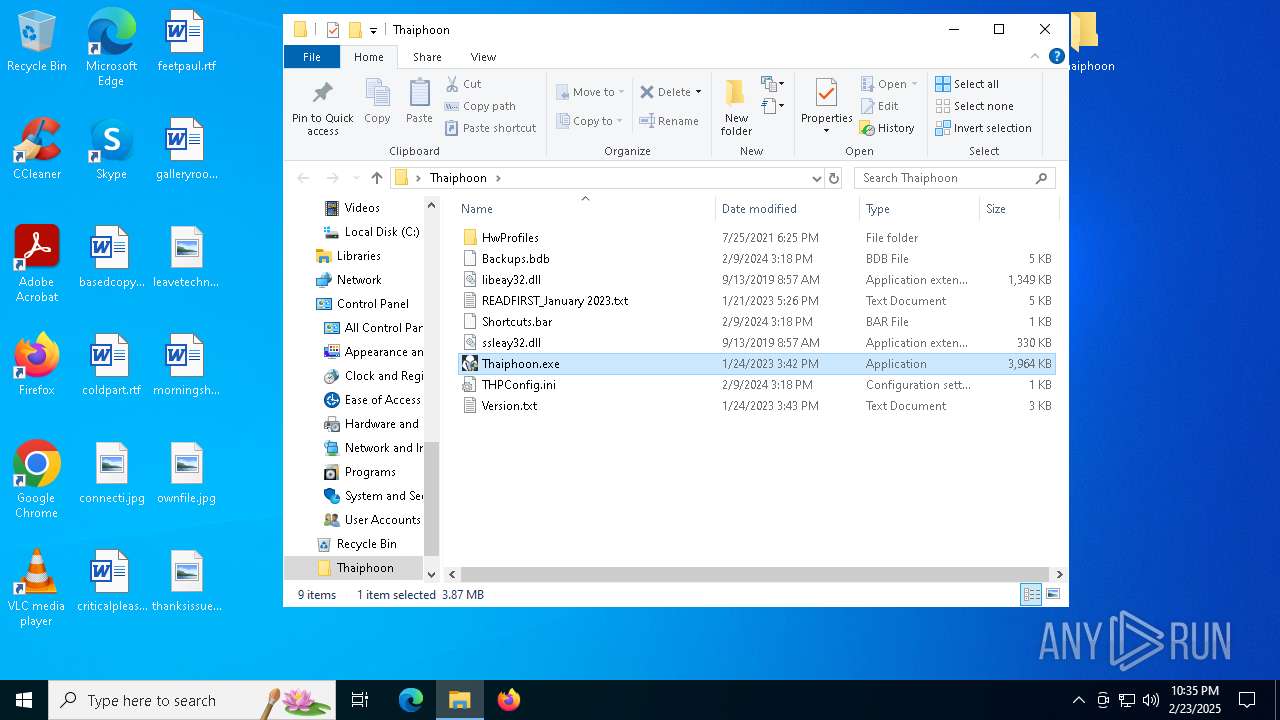
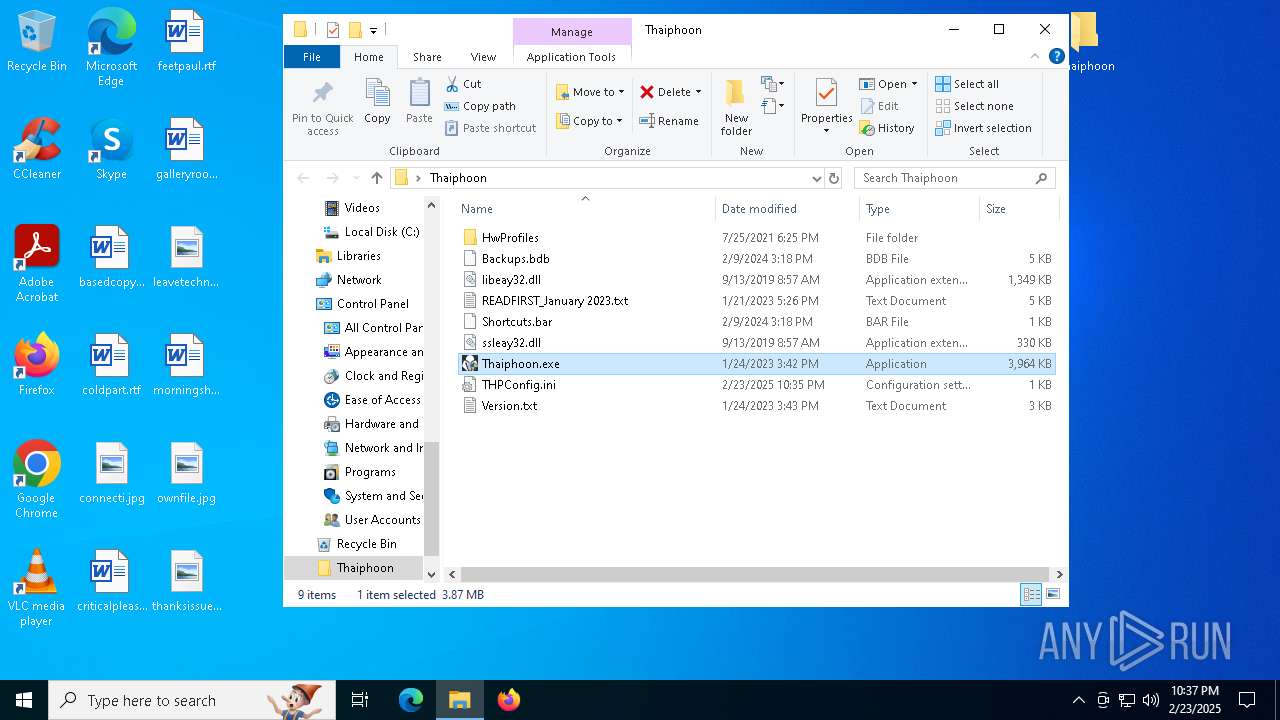
| File name: | Thaiphoon.rar |
| Full analysis: | https://app.any.run/tasks/88d2944e-234b-4875-a9b8-029fc1f197fc |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2025, 22:35:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 26B00DEFBADD08BE9164D23AC494B520 |
| SHA1: | 0FB37E284DABC36D2DAAEE4334ACF65BC05AF0D2 |
| SHA256: | CD3F3789B89A6DCBF8D05701C03DB67DA023A5AC68003DA523753D1C0A48E786 |
| SSDEEP: | 98304:3Nz9UrVbUV5HH4y+Ey7Nxm6cXAmo/p+D3aBnHHbPss6Tpmtz7pjG6hIsL+VT+y4y:GZFj2tlN |
MALICIOUS
No malicious indicators.SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Thaiphoon.exe (PID: 4308)
Creates files in the driver directory
- Thaiphoon.exe (PID: 4308)
Executable content was dropped or overwritten
- Thaiphoon.exe (PID: 4308)
Reads security settings of Internet Explorer
- Thaiphoon.exe (PID: 4308)
There is functionality for VM detection VirtualBox (YARA)
- Thaiphoon.exe (PID: 4308)
There is functionality for VM detection antiVM strings (YARA)
- Thaiphoon.exe (PID: 4308)
Drops a system driver (possible attempt to evade defenses)
- Thaiphoon.exe (PID: 4308)
INFO
Checks supported languages
- Thaiphoon.exe (PID: 4308)
- Thaiphoon.exe (PID: 2220)
- Thaiphoon.exe (PID: 3080)
- SystemSettings.exe (PID: 4320)
Manual execution by a user
- Thaiphoon.exe (PID: 4308)
- Thaiphoon.exe (PID: 5112)
- Thaiphoon.exe (PID: 2220)
- Thaiphoon.exe (PID: 628)
- Thaiphoon.exe (PID: 3080)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5320)
The sample compiled with english language support
- WinRAR.exe (PID: 5320)
- Thaiphoon.exe (PID: 4308)
Compiled with Borland Delphi (YARA)
- Thaiphoon.exe (PID: 4308)
Reads the computer name
- Thaiphoon.exe (PID: 2220)
- Thaiphoon.exe (PID: 3080)
- SystemSettings.exe (PID: 4320)
- Thaiphoon.exe (PID: 4308)
Reads Windows Product ID
- SystemSettings.exe (PID: 4320)
Reads CPU info
- SystemSettings.exe (PID: 4320)
Reads the software policy settings
- SystemSettings.exe (PID: 4320)
Reads the machine GUID from the registry
- SystemSettings.exe (PID: 4320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 237 |
| UncompressedSize: | 4160 |
| OperatingSystem: | Win32 |
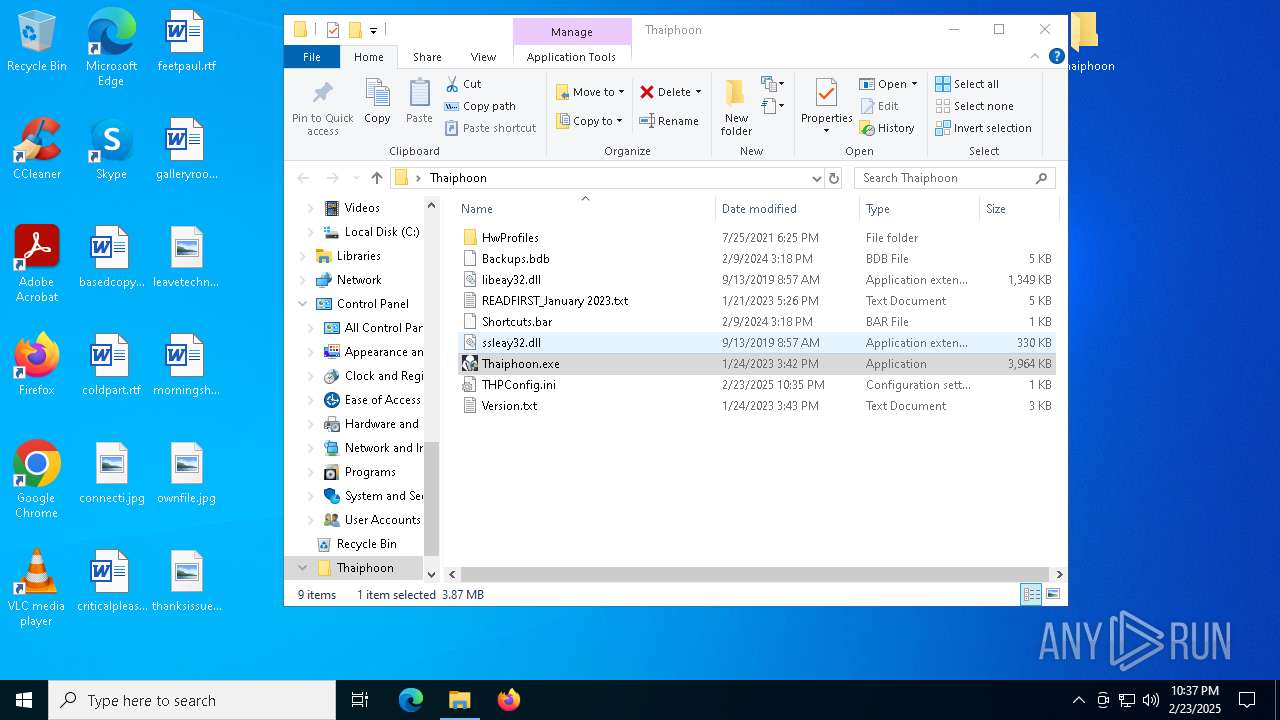
| ArchivedFileName: | Thaiphoon/Backups.bdb |
Total processes
141
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 628 | "C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe" | C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe | — | explorer.exe | |||||||||||
User: admin Company: Showshock Softnology LLC Integrity Level: MEDIUM Description: SPD EEPROM programming software Exit code: 3221226540 Modules
| |||||||||||||||
| 2220 | "C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe" | C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe | explorer.exe | ||||||||||||
User: admin Company: Showshock Softnology LLC Integrity Level: HIGH Description: SPD EEPROM programming software Exit code: 0 Modules
| |||||||||||||||
| 3080 | "C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe" | C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe | explorer.exe | ||||||||||||
User: admin Company: Showshock Softnology LLC Integrity Level: HIGH Description: SPD EEPROM programming software Exit code: 0 Modules
| |||||||||||||||
| 3420 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3920 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4308 | "C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe" | C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe | explorer.exe | ||||||||||||
User: admin Company: Showshock Softnology LLC Integrity Level: HIGH Description: SPD EEPROM programming software Modules
| |||||||||||||||
| 4320 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5112 | "C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe" | C:\Users\admin\Desktop\Thaiphoon\Thaiphoon.exe | — | explorer.exe | |||||||||||
User: admin Company: Showshock Softnology LLC Integrity Level: MEDIUM Description: SPD EEPROM programming software Exit code: 3221226540 Modules
| |||||||||||||||
| 5320 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Thaiphoon.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 398
Read events
4 377
Write events
21
Delete events
0
Modification events
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Thaiphoon.rar | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
5
Suspicious files
4
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\Backups.bdb | binary | |
MD5:96BB0395F7A82A161898B8A062825F5A | SHA256:77C9AAF00F17DA46C8C7328AC8B4EEA4A1FD71AE705D2F0936B95E3C36A08152 | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\HwProfiles\Gigabyte GA-H87N-WiFi [Rev.1.0-2.0].hwp | csv | |
MD5:C0F7EE256102AF41A6833EAC13C01AF5 | SHA256:FE128EBCB324C1A2891AE8C7BE38726DB96AD05580EDCB8A877BCB5A9358CC8E | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\HwProfiles\Gigabyte GA-AX370-Gaming K7 [Rev.1.0] (untested).hwp | text | |
MD5:8D7035762236CE0EACB3B92FCA9EA4D7 | SHA256:86DC87F83975C7D3409D19BF8504AA70A2AA1DCAE47FA4910994DA6A0156329B | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\HwProfiles\Gigabyte GA-AB350-Gaming 3 [Rev.1.01] (untested).hwp | csv | |
MD5:BF4B062B63FC9BB0E6E0BBF60E5AC557 | SHA256:F481D7E1F2C5B2F8BD4C29953AA964483D1CBDF9400D1ECE77CB028491F6C64A | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\HwProfiles\Gigabyte GA-E350N [Rev.3.0].hwp | csv | |
MD5:55E5D7C7D60D40D8B64DBF744B8070BE | SHA256:5EE0462DA7D38E3D07CF942DC042332304738D474D7E69AEFFF9F149A590871C | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\HwProfiles\Gigabyte Generic for AMD X399 Series.hwp | csv | |
MD5:67CC23A1D14811CB3348723493E4DFBA | SHA256:63FA40EB79051F24FBF4C71241BBEA574A468BD08A5F11825A846546CDBA89F1 | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\HwProfiles\Gigabyte GA-E2100N [Rev.1.01] (untested).hwp | csv | |
MD5:4534A306E93613C055C855AEF389F91B | SHA256:5CF61F1D83EBF5BD6B3A7E46D793B1C31B7EFEEA025BB5AA8DA09BE85A74F55C | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\HwProfiles\Gigabyte GA-X79-UD3 [Rev.1.03].hwp | csv | |
MD5:2BAD3303D3002FE8FEFED561A9C8467B | SHA256:661E70755B4093DBED4E6B2D9B055AE00BBCA37866F30C22EA6274FB4DAE3D5D | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\HwProfiles\Gigabyte GA-H61M-S1 [Rev.2.1].hwp | csv | |
MD5:14251DCB3EA808B11BD4D2D8EE309648 | SHA256:0ABA8B68E7BE1B6249A9DFED5AFF94D42DD810BE60F5A667AA59F663569A167C | |||
| 5320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5320.45965\Thaiphoon\HwProfiles\Gigabyte Generic for AMD X470 Series.hwp | csv | |
MD5:E79A3DEB6D9A34A1408B1B161C9550E2 | SHA256:FA9D1B3F727C4D4AD0942AEC1A60A50CF66B3AD328152AF6483AAF0BBA89085C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
50
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6100 | SystemSettings.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2220 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.33:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5200 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5200 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |