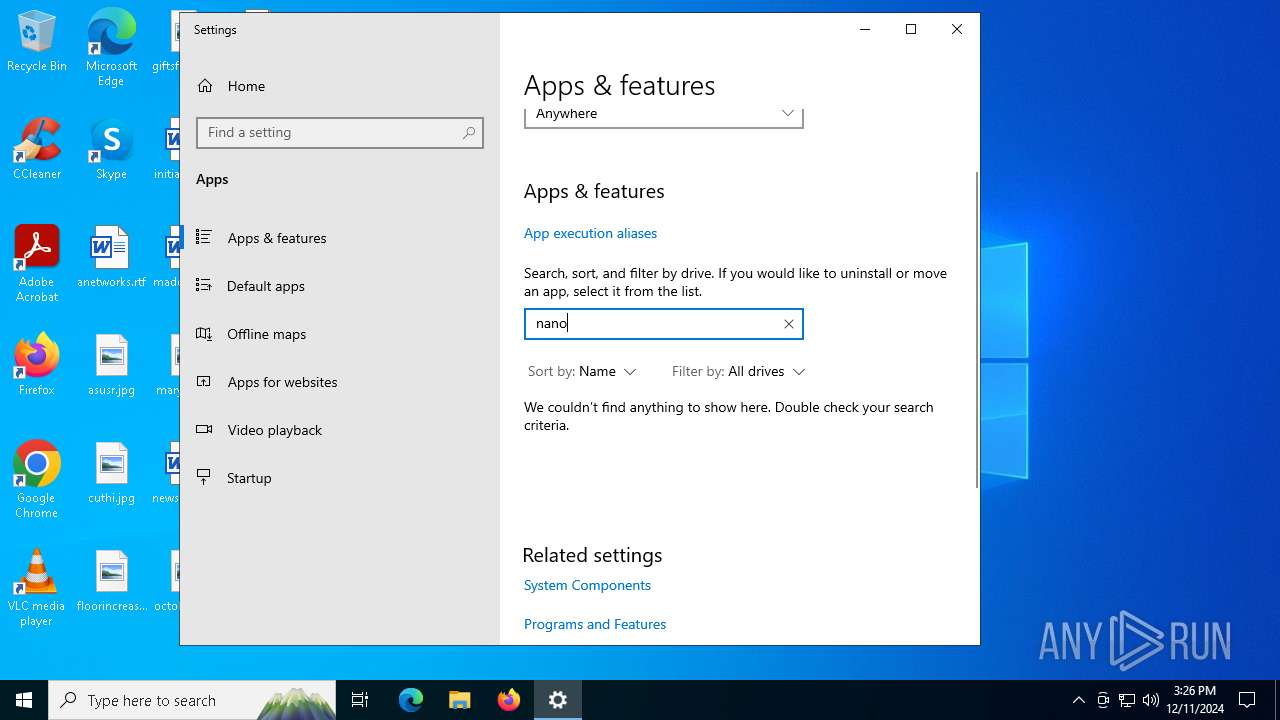
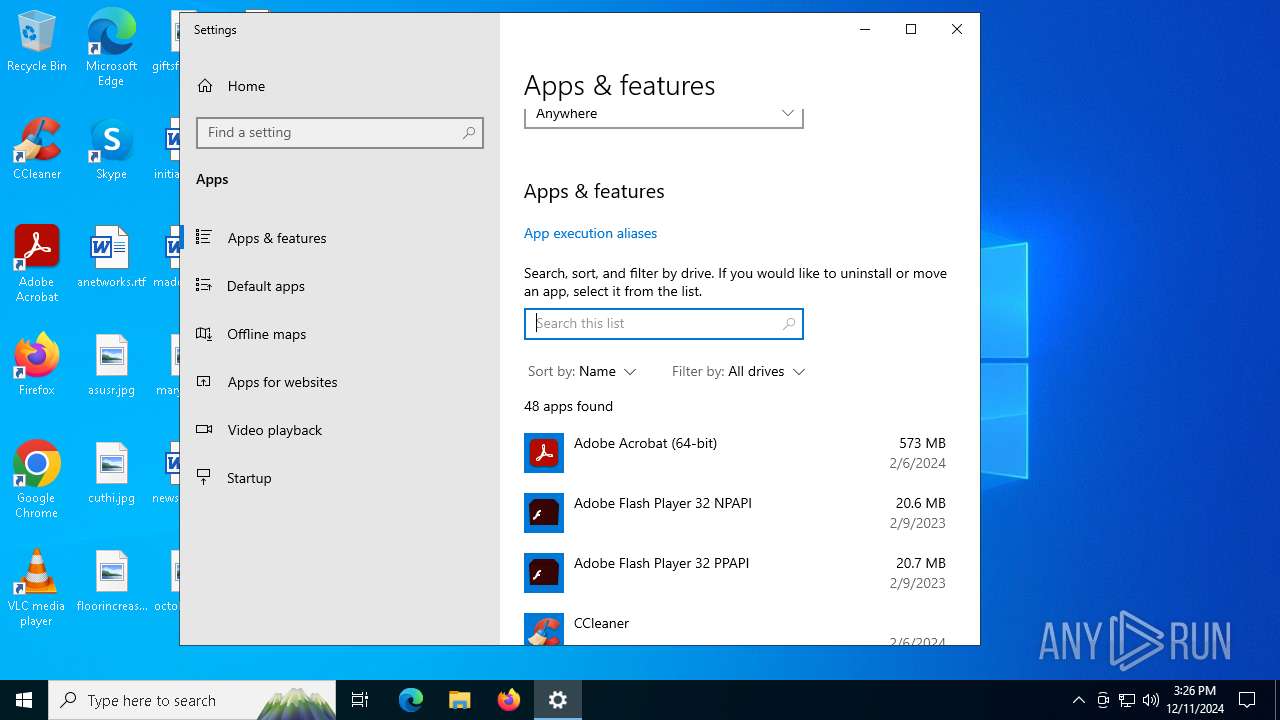
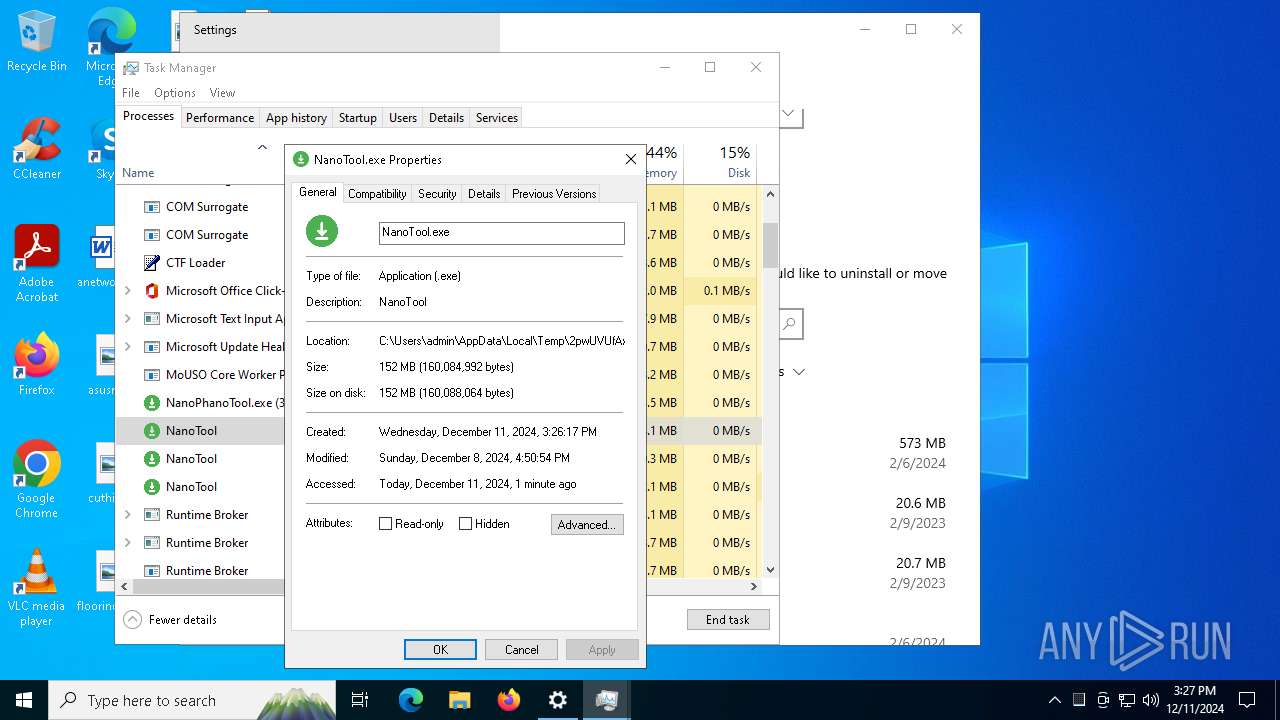
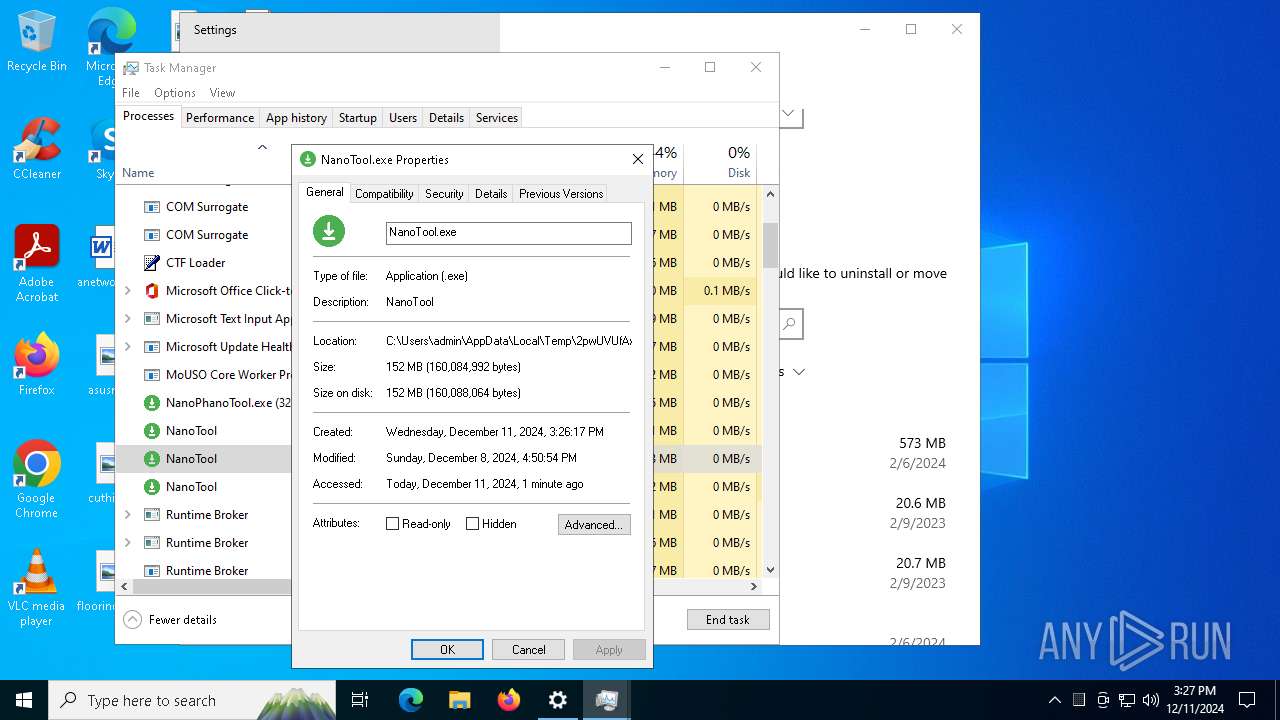
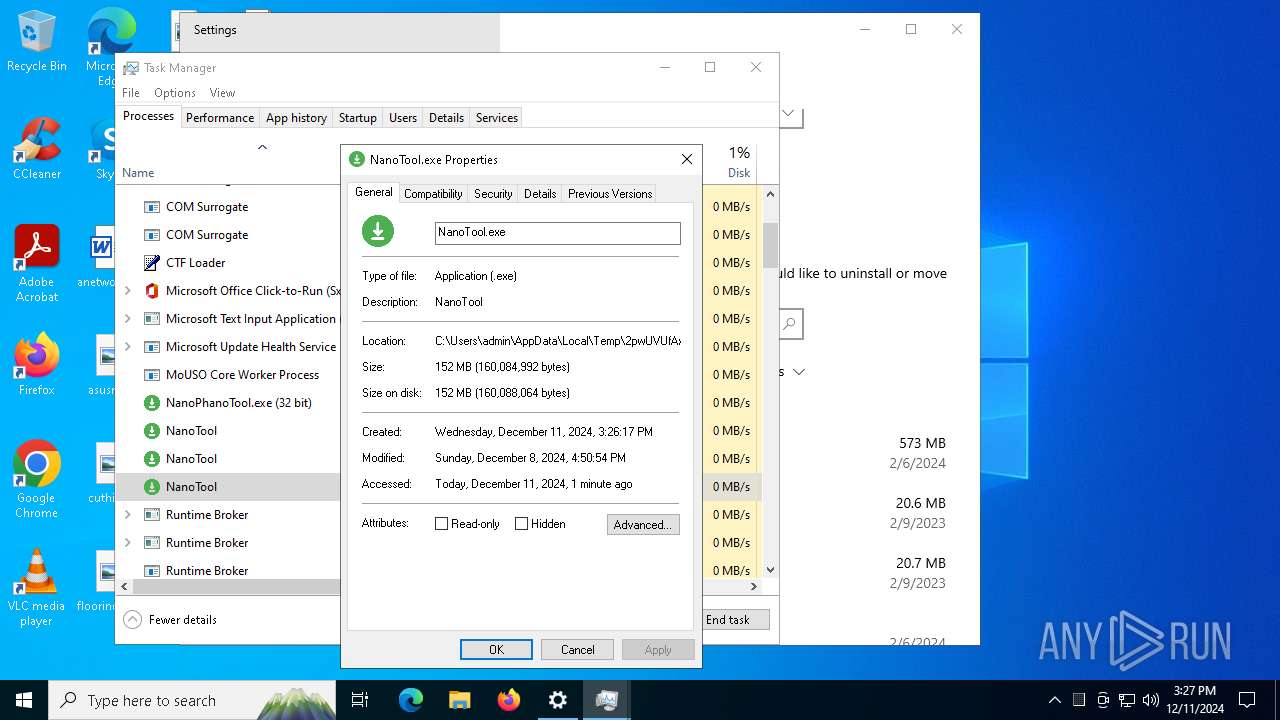
| File name: | NanoPhanoTool.exe |
| Full analysis: | https://app.any.run/tasks/4d727cc3-dd1f-415f-b7d0-fd4c3291e7aa |
| Verdict: | Malicious activity |
| Analysis date: | December 11, 2024, 15:25:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 6AE17B0BDDDA685EAA622CEF4BA2E805 |
| SHA1: | 8139F07B57A1D71B60D32CBA52167AA824AFAD2A |
| SHA256: | CD207B81505F13D46D94B08FB5130DDAE52BD1748856E6B474688E590933A718 |
| SSDEEP: | 393216:SgqoMmxIWo7SbYwWzv0Nv26ypNqLCvssOFCTiQi0PKwdtN2Zg2fA29/Oj58j:SgqoMmxZbJzo0C1I2iRwvNgg2fA29mjE |
MALICIOUS
Changes powershell execution policy (Unrestricted)
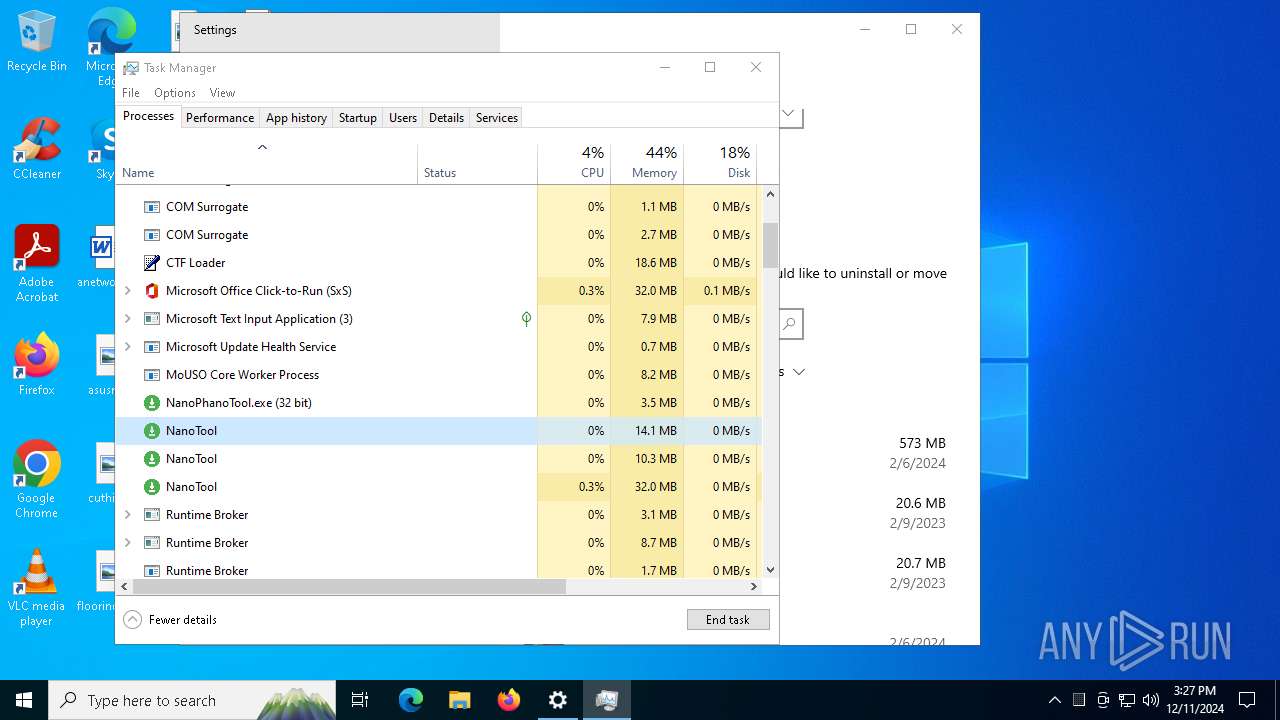
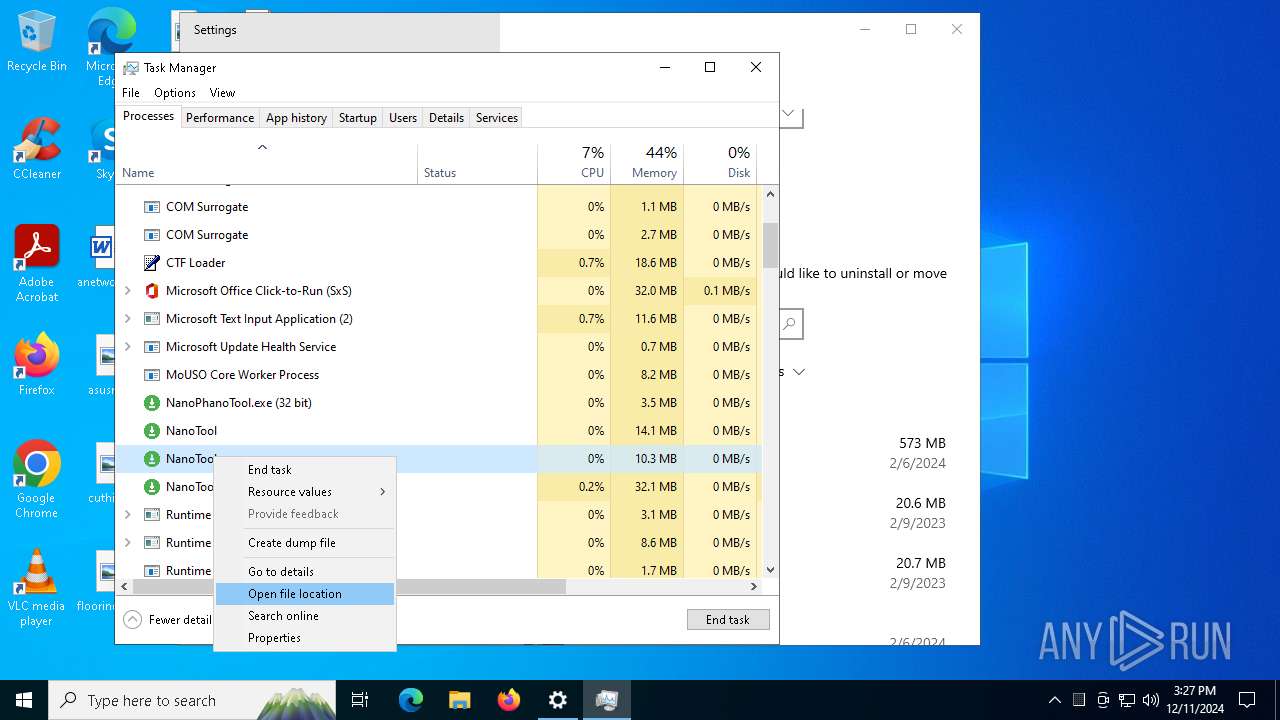
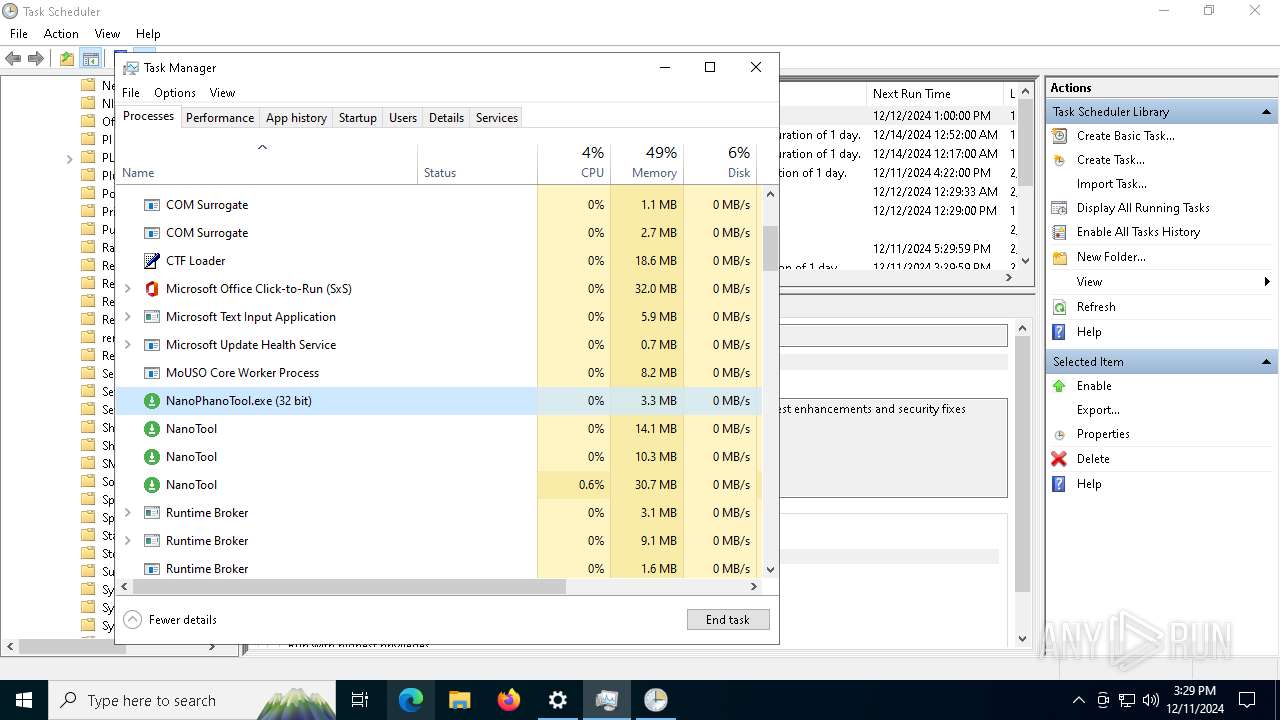
- NanoTool.exe (PID: 6852)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- NanoPhanoTool.exe (PID: 6648)
Reads security settings of Internet Explorer
- NanoPhanoTool.exe (PID: 6648)
Process drops legitimate windows executable
- NanoPhanoTool.exe (PID: 6648)
Executable content was dropped or overwritten
- NanoPhanoTool.exe (PID: 6648)
Starts application with an unusual extension
- cmd.exe (PID: 6932)
Drops 7-zip archiver for unpacking
- NanoPhanoTool.exe (PID: 6648)
Starts CMD.EXE for commands execution
- NanoTool.exe (PID: 6852)
Application launched itself
- NanoTool.exe (PID: 6852)
Starts POWERSHELL.EXE for commands execution
- NanoTool.exe (PID: 6852)
The process bypasses the loading of PowerShell profile settings
- NanoTool.exe (PID: 6852)
The process hides Powershell's copyright startup banner
- NanoTool.exe (PID: 6852)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7824)
INFO
The sample compiled with english language support
- NanoPhanoTool.exe (PID: 6648)
Reads product name
- NanoTool.exe (PID: 6852)
Checks supported languages
- NanoTool.exe (PID: 6852)
- NanoPhanoTool.exe (PID: 6648)
- chcp.com (PID: 6988)
- NanoTool.exe (PID: 7108)
- NanoTool.exe (PID: 3288)
- NanoTool.exe (PID: 8400)
- NanoTool.exe (PID: 7344)
Reads the computer name
- NanoPhanoTool.exe (PID: 6648)
- NanoTool.exe (PID: 6852)
- NanoTool.exe (PID: 7108)
- NanoTool.exe (PID: 3288)
- NanoTool.exe (PID: 7488)
- NanoTool.exe (PID: 6800)
Reads Environment values
- NanoTool.exe (PID: 6852)
Changes the display of characters in the console
- cmd.exe (PID: 6932)
Reads the machine GUID from the registry
- NanoTool.exe (PID: 6852)
Checks proxy server information
- NanoTool.exe (PID: 6852)
Create files in a temporary directory
- NanoPhanoTool.exe (PID: 6648)
Node.js compiler has been detected
- NanoTool.exe (PID: 7108)
- NanoTool.exe (PID: 6852)
- NanoTool.exe (PID: 3288)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6744)
- mmc.exe (PID: 1216)
Manual execution by a user
- Taskmgr.exe (PID: 5192)
- Taskmgr.exe (PID: 6744)
- msedge.exe (PID: 6184)
- mmc.exe (PID: 4724)
- mmc.exe (PID: 1216)
Sends debugging messages
- mmc.exe (PID: 1216)
Application launched itself
- msedge.exe (PID: 6184)
- msedge.exe (PID: 5872)
The process uses the downloaded file
- Taskmgr.exe (PID: 6744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.9.6.0 |
| ProductVersionNumber: | 6.9.6.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | - |
| FileVersion: | 7.1.0 |
| LegalCopyright: | Copyright © 2024 NanoTool |
| LegalTrademarks: | Nano Pnato Tools (C) |
| ProductName: | NanoTool |
| ProductVersion: | 6.9.6 |
Total processes
256
Monitored processes
128
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4724 --field-trial-handle=2272,i,2036238937888113685,4295111176528505544,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1152 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4312 --field-trial-handle=2296,i,13491400277050692380,2177388995329882570,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1216 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4088 --field-trial-handle=2296,i,13491400277050692380,2177388995329882570,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1344 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2628 --field-trial-handle=2272,i,2036238937888113685,4295111176528505544,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1916 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3496 --field-trial-handle=2272,i,2036238937888113685,4295111176528505544,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2152 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5068 --field-trial-handle=2296,i,13491400277050692380,2177388995329882570,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2160 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7484 --field-trial-handle=2272,i,2036238937888113685,4295111176528505544,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
53 423
Read events
53 351
Write events
71
Delete events
1
Modification events
| (PID) Process: | (6744) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (6744) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AA6C15F77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AA6C15F77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AA6C15F77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AA6C15F77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000AB6C15F77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028AB6C15F77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050AB6C15F77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AA6C15F77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070AB6C15F77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088AB6C15F77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8AB6C15F77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8AB6C15F77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0AB6C15F77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010AC6C15F77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AA6C15F77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AA6C15F77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040AC6C15F77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068AC6C15F77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090AC6C15F77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8AC6C15F77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8AC6C15F77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8AC6C15F77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028AB6C15F77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AA6C15F77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020AD6C15F77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040AD6C15F77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068AD6C15F77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050AB6C15F77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AA6C15F77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070AB6C15F77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088AB6C15F77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8AB6C15F77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8AB6C15F77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AA6C15F77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AE6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AE6C15F77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AE6C15F77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AE6C15F77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (1216) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | HelpTopic |
Value: C:\WINDOWS\Help\taskscheduler.chm | |||
| (PID) Process: | (1216) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | LinkedHelpTopics |
Value: C:\WINDOWS\Help\taskscheduler.chm | |||
| (PID) Process: | (6744) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | write | Name: | CCleaner Smart Cleaning |
Value: 03000000388271EEFD58DA01 | |||
| (PID) Process: | (6744) Taskmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run32 |
| Operation: | write | Name: | SunJavaUpdateSched |
Value: 030000006B0EA3ECFD58DA01 | |||
| (PID) Process: | (6744) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: 030000002B498EF9C8B7D801 | |||
| (PID) Process: | (6744) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | write | Name: | OneDrive |
Value: 03000000A31484EEAAD7D301 | |||
| (PID) Process: | (6744) Taskmgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run |
| Operation: | write | Name: | SoundMan |
Value: 030000009F7A12EAC6B7D801 | |||
| (PID) Process: | (6744) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\StartupFolder |
| Operation: | write | Name: | Send to OneNote.lnk |
Value: 030000004443A9558E3CD901 | |||
Executable files
45
Suspicious files
937
Text files
206
Unknown types
44
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\app-64.7z | — | |
MD5:— | SHA256:— | |||
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\nsis7z.dll | executable | |
MD5:80E44CE4895304C6A3A831310FBF8CD0 | SHA256:B393F05E8FF919EF071181050E1873C9A776E1A0AE8329AEFFF7007D0CADF592 | |||
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\7z-out\locales\cs.pak | pgc | |
MD5:04A680847C4A66AD9F0A88FB9FB1FC7B | SHA256:1CC44C5FBE1C0525DF37C5B6267A677F79C9671F86EDA75B6FC13ABF5D5356EB | |||
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\7z-out\locales\el.pak | pgc | |
MD5:9528D21E8A3F5BAD7CA273999012EBE8 | SHA256:E79C1E7A47250D88581E8E3BAF78DCAF31FE660B74A1E015BE0F4BAFDFD63E12 | |||
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\7z-out\locales\bn.pak | pgc | |
MD5:5CDD07FA357C846771058C2DB67EB13B | SHA256:01C830B0007B8CE6ACA46E26D812947C3DF818927B826F7D8C5FFD0008A32384 | |||
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\7z-out\locales\de.pak | pgc | |
MD5:8E6654B89ED4C1DC02E1E2D06764805A | SHA256:61CBCE9A31858DDF70CC9B0C05FB09CE7032BFB8368A77533521722465C57475 | |||
| 6648 | NanoPhanoTool.exe | C:\Users\admin\AppData\Local\Temp\nsl9908.tmp\7z-out\locales\en-GB.pak | mmw | |
MD5:D59E613E8F17BDAFD00E0E31E1520D1F | SHA256:90E585F101CF0BB77091A9A9A28812694CEE708421CE4908302BBD1BC24AC6FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
118
DNS requests
31
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 304 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2396 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2396 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6748 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6748 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6300 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2396 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.209.183:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2396 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.6:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
1344 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1344 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|