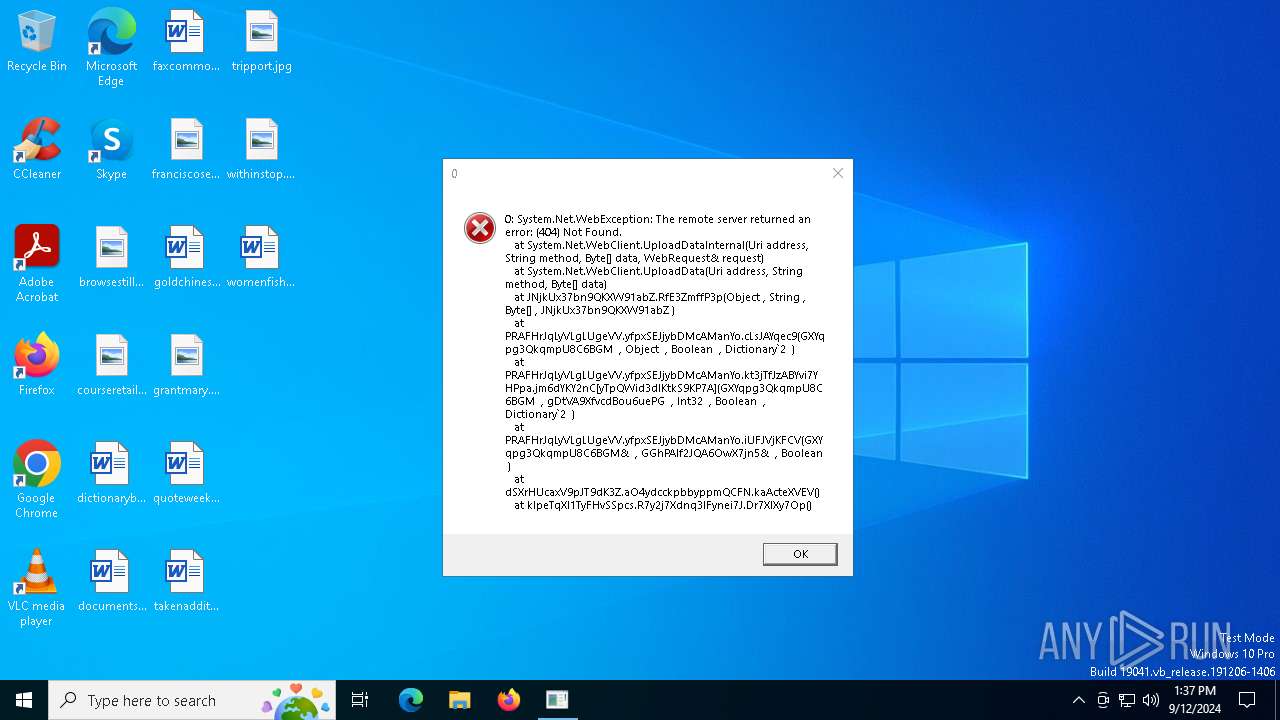
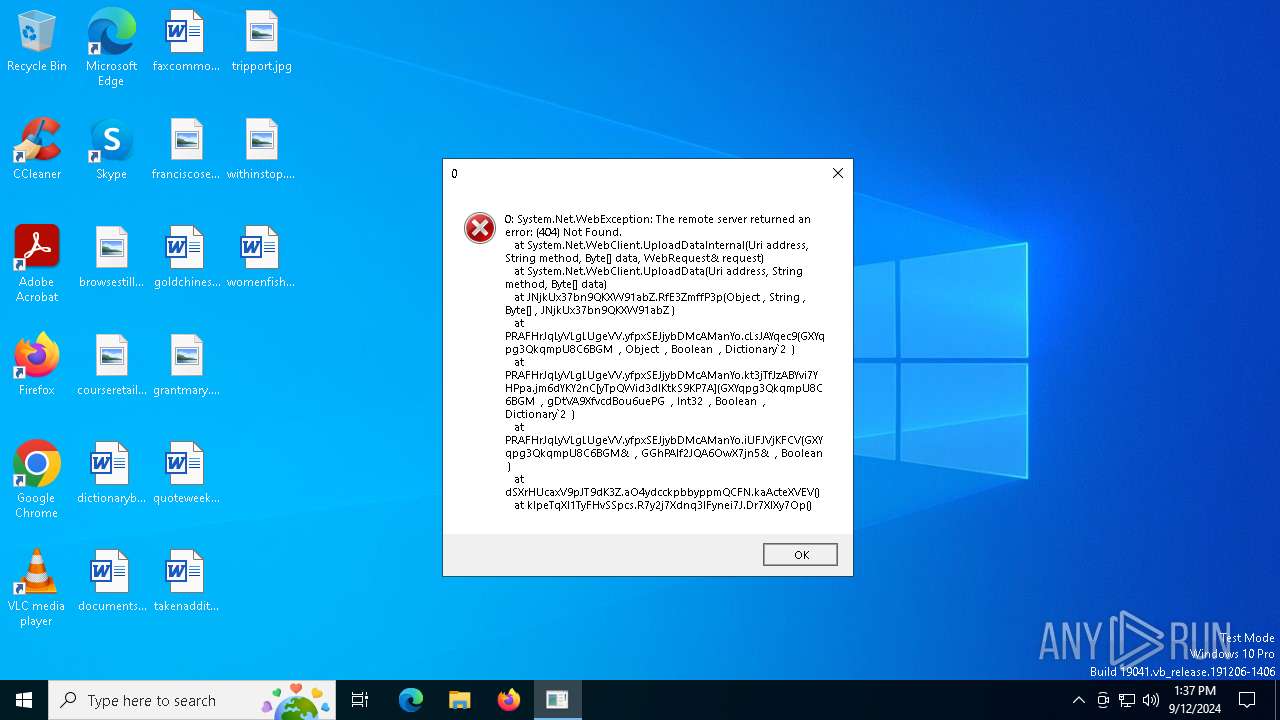
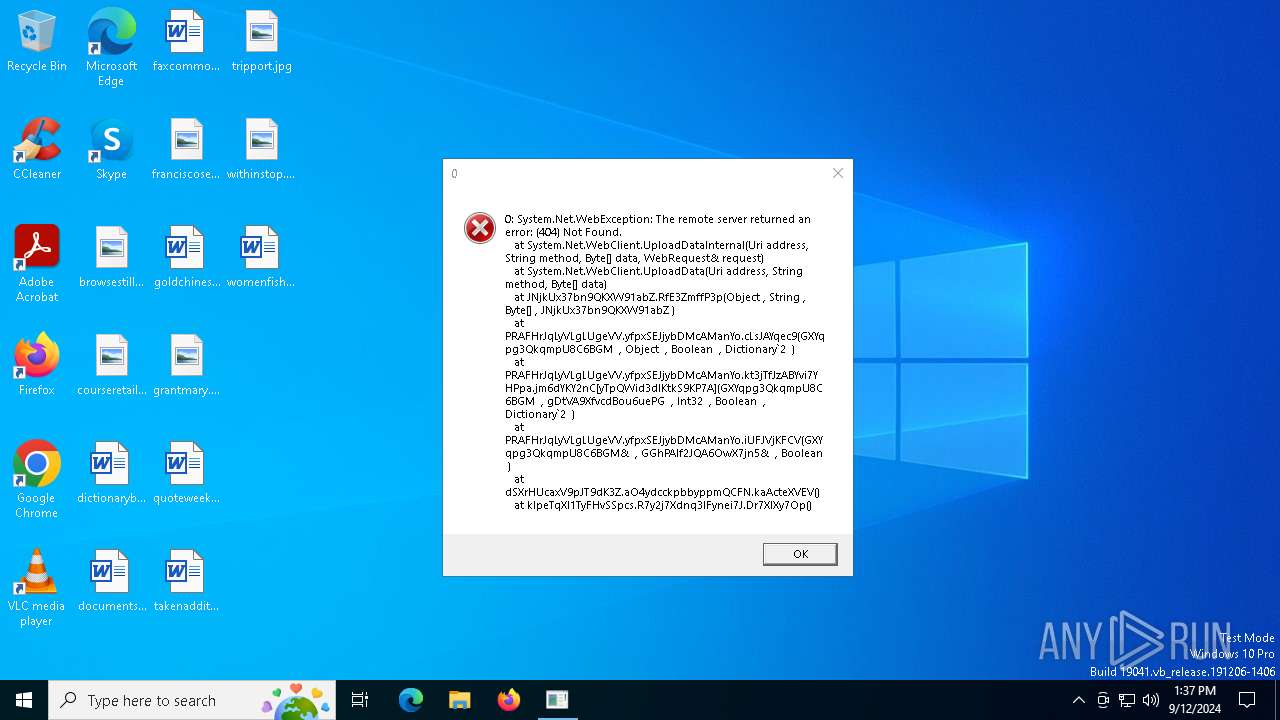
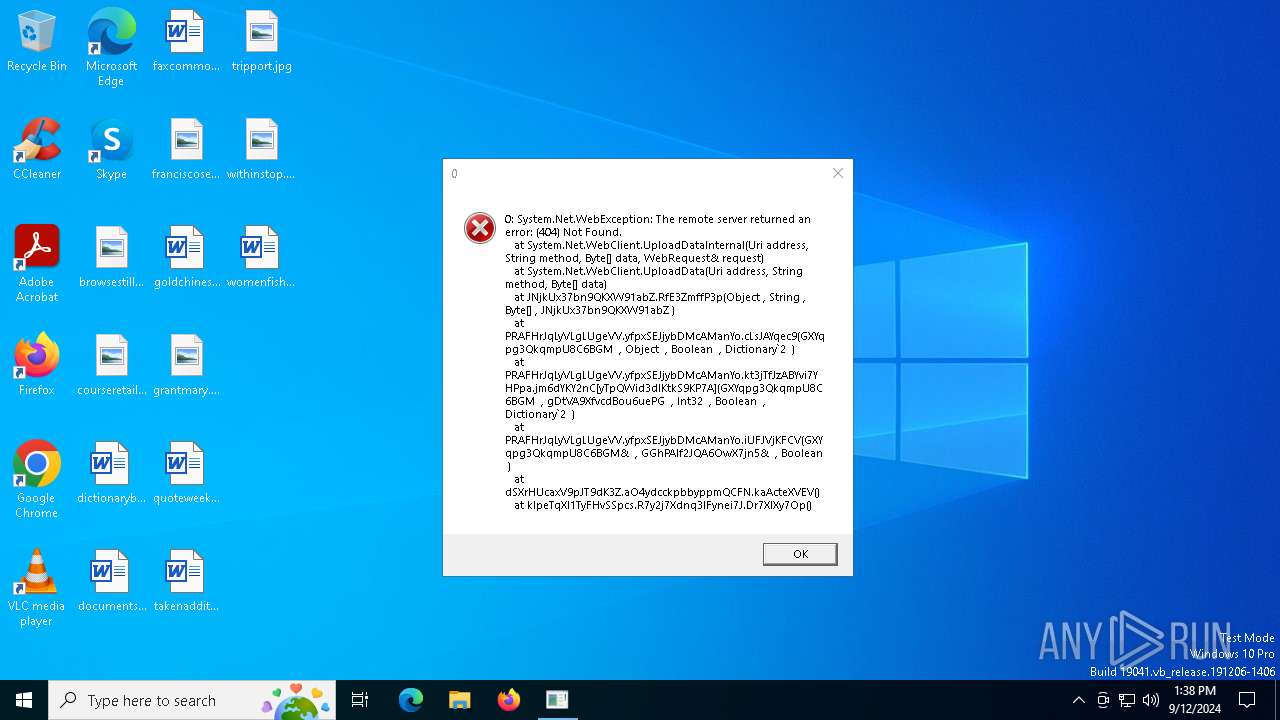
| File name: | MinecraftFpsMod.exe |
| Full analysis: | https://app.any.run/tasks/b3fc1edf-c062-4125-b76c-93a963f4711f |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | September 12, 2024, 13:36:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 73D7E637CD16F1F807930FA6442436DF |
| SHA1: | 26C13B2C29065485CE1858D85D9DC792C06ED052 |
| SHA256: | CD0F7FB1020A931C98C7C258241F06292CB9B7CAB8E9ACDB4010F4D56F076EF6 |
| SSDEEP: | 98304:ar7ayGJ6kHOScyi35C6FCsVe+u3HzdT3RV4nGPU1lnlakMbayrnk+WEMaI8aInoS:tJXHL |
MALICIOUS
Changes the autorun value in the registry
- MinecraftFpsMod.exe (PID: 5712)
- Bridgesurrogate.exe (PID: 2384)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 5544)
DcRAT is detected
- Bridgesurrogate.exe (PID: 2384)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
- dasHost.exe (PID: 6780)
Connects to the CnC server
- Synaptics.exe (PID: 7096)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
- dasHost.exe (PID: 6780)
DARKCRYSTAL has been detected (SURICATA)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
- dasHost.exe (PID: 6780)
DCRAT has been detected (YARA)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 6780)
SUSPICIOUS
Reads security settings of Internet Explorer
- Synaptics.exe (PID: 7096)
- MinecraftFpsMod.exe (PID: 5712)
- Bridgesurrogate.exe (PID: 2384)
- ._cache_MinecraftFpsMod.exe (PID: 4252)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
Executing commands from a ".bat" file
- wscript.exe (PID: 5544)
- Bridgesurrogate.exe (PID: 2384)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5544)
- Bridgesurrogate.exe (PID: 2384)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5544)
Executable content was dropped or overwritten
- Bridgesurrogate.exe (PID: 2384)
- csc.exe (PID: 6288)
- csc.exe (PID: 6192)
- dasHost.exe (PID: 6696)
- MinecraftFpsMod.exe (PID: 5712)
- ._cache_MinecraftFpsMod.exe (PID: 4252)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
- dasHost.exe (PID: 6780)
Executed via WMI
- schtasks.exe (PID: 4284)
- schtasks.exe (PID: 488)
- schtasks.exe (PID: 6808)
- schtasks.exe (PID: 7024)
- schtasks.exe (PID: 4060)
- schtasks.exe (PID: 6368)
- schtasks.exe (PID: 6544)
- schtasks.exe (PID: 1044)
- schtasks.exe (PID: 6980)
- schtasks.exe (PID: 5464)
- schtasks.exe (PID: 2460)
- schtasks.exe (PID: 6768)
- schtasks.exe (PID: 5044)
- schtasks.exe (PID: 4092)
- schtasks.exe (PID: 2724)
- schtasks.exe (PID: 1292)
- schtasks.exe (PID: 6480)
- schtasks.exe (PID: 4668)
Process drops legitimate windows executable
- Bridgesurrogate.exe (PID: 2384)
The process creates files with name similar to system file names
- Bridgesurrogate.exe (PID: 2384)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 1044)
- schtasks.exe (PID: 6980)
- schtasks.exe (PID: 2724)
Reads the date of Windows installation
- Bridgesurrogate.exe (PID: 2384)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
Starts application with an unusual extension
- cmd.exe (PID: 4540)
- cmd.exe (PID: 3160)
- cmd.exe (PID: 4252)
- cmd.exe (PID: 6260)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 4540)
- cmd.exe (PID: 4252)
- cmd.exe (PID: 6260)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 7096)
There is functionality for taking screenshot (YARA)
- Synaptics.exe (PID: 7096)
Contacting a server suspected of hosting an CnC
- Synaptics.exe (PID: 7096)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 7096)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3160)
Checks Windows Trust Settings
- Synaptics.exe (PID: 7096)
INFO
Checks supported languages
- MinecraftFpsMod.exe (PID: 5712)
- Bridgesurrogate.exe (PID: 2384)
- Synaptics.exe (PID: 7096)
- csc.exe (PID: 6192)
- csc.exe (PID: 6288)
- cvtres.exe (PID: 4824)
- cvtres.exe (PID: 5484)
- chcp.com (PID: 5264)
- dasHost.exe (PID: 6696)
- ._cache_MinecraftFpsMod.exe (PID: 4252)
- dasHost.exe (PID: 4680)
- chcp.com (PID: 3332)
- chcp.com (PID: 7000)
- dasHost.exe (PID: 4540)
- chcp.com (PID: 5980)
- dasHost.exe (PID: 6780)
Create files in a temporary directory
- MinecraftFpsMod.exe (PID: 5712)
- Bridgesurrogate.exe (PID: 2384)
- cvtres.exe (PID: 5484)
- cvtres.exe (PID: 4824)
- dasHost.exe (PID: 6696)
- Synaptics.exe (PID: 7096)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
Reads the computer name
- MinecraftFpsMod.exe (PID: 5712)
- ._cache_MinecraftFpsMod.exe (PID: 4252)
- Bridgesurrogate.exe (PID: 2384)
- Synaptics.exe (PID: 7096)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
- dasHost.exe (PID: 6780)
The process uses the downloaded file
- MinecraftFpsMod.exe (PID: 5712)
- wscript.exe (PID: 5544)
- Bridgesurrogate.exe (PID: 2384)
- ._cache_MinecraftFpsMod.exe (PID: 4252)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
Process checks computer location settings
- MinecraftFpsMod.exe (PID: 5712)
- ._cache_MinecraftFpsMod.exe (PID: 4252)
- Bridgesurrogate.exe (PID: 2384)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
Creates files in the program directory
- MinecraftFpsMod.exe (PID: 5712)
- csc.exe (PID: 6288)
- Synaptics.exe (PID: 7096)
Checks proxy server information
- Synaptics.exe (PID: 7096)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
- dasHost.exe (PID: 6780)
Reads the machine GUID from the registry
- Bridgesurrogate.exe (PID: 2384)
- csc.exe (PID: 6192)
- csc.exe (PID: 6288)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- Synaptics.exe (PID: 7096)
- dasHost.exe (PID: 4540)
- dasHost.exe (PID: 6780)
Reads Environment values
- Bridgesurrogate.exe (PID: 2384)
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
- dasHost.exe (PID: 6780)
Creates files or folders in the user directory
- csc.exe (PID: 6192)
- Synaptics.exe (PID: 7096)
Changes the display of characters in the console
- cmd.exe (PID: 4540)
- cmd.exe (PID: 3160)
- cmd.exe (PID: 4252)
- cmd.exe (PID: 6260)
Disables trace logs
- dasHost.exe (PID: 6696)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 4540)
- dasHost.exe (PID: 6780)
Reads the software policy settings
- Synaptics.exe (PID: 7096)
- slui.exe (PID: 1076)
.NET Reactor protector has been detected
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 6780)
Found Base64 encoded reference to WMI classes (YARA)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 6780)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- dasHost.exe (PID: 4680)
- dasHost.exe (PID: 6780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(4680) dasHost.exe
C2 (1)http://noburo.top/phpJavascriptSecurecpuupdateFlowerAsyncUniversaltrack
C2 (1)http://noburo.top/phpJavascriptSecurecpuupdateFlowerAsyncUniversaltrack
Options
Plugins (2)TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDALI7+mQAAAAAAAAAAOAAIiALAQgAAAgBAAAGAAAAAAAAricBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAArNABAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAKX/2QAAAAAAAAAAOAAIiALAQgAAEYBAAAGAAAAAAAA7mUBAAAgAAAAgAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAm0ACAAMAQIUA...
(PID) Process(6780) dasHost.exe
C2 (1)http://noburo.top/phpJavascriptSecurecpuupdateFlowerAsyncUniversaltrack
Options
Plugins (2)TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDALI7+mQAAAAAAAAAAOAAIiALAQgAAAgBAAAGAAAAAAAAricBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAArNABAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAKX/2QAAAAAAAAAAOAAIiALAQgAAEYBAAAGAAAAAAAA7mUBAAAgAAAAgAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAm0ACAAMAQIUA...
C2 (1)http://noburo.top/phpJavascriptSecurecpuupdateFlowerAsyncUniversaltrack
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (90.7) |
|---|---|---|
| .exe | | | InstallShield setup (5.8) |
| .exe | | | Win32 Executable Delphi generic (1.9) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 629760 |
| InitializedDataSize: | 6340096 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9ab80 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 1.0.0.0 |
| FileDescription: | 易语言程序 |
| ProductName: | 易语言程序 |
| ProductVersion: | 1.0.0.0 |
| LegalCopyright: | 作者版权所有 请尊重并使用正版 |
| Comments: | 本程序使用易语言编写(http://www.eyuyan.com) |
Total processes
179
Monitored processes
55
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | schtasks.exe /create /tn "dllhost" /sc ONLOGON /tr "'C:\MsAgentBrowserdhcp\dllhost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | schtasks.exe /create /tn "smss" /sc ONLOGON /tr "'C:\Users\Public\Libraries\smss.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | schtasks.exe /create /tn "BridgesurrogateB" /sc MINUTE /mo 9 /tr "'C:\MsAgentBrowserdhcp\Bridgesurrogate.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1776 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\System32\w32tm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2384 | "C:\MsAgentBrowserdhcp/Bridgesurrogate.exe" | C:\MsAgentBrowserdhcp\Bridgesurrogate.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.2.7.1277 Modules
| |||||||||||||||
| 2460 | schtasks.exe /create /tn "spoolsv" /sc ONLOGON /tr "'C:\MsAgentBrowserdhcp\spoolsv.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 571
Read events
12 540
Write events
31
Delete events
0
Modification events
| (PID) Process: | (5712) MinecraftFpsMod.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (5712) MinecraftFpsMod.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ????? |
Value: C:\ProgramData\Synaptics\Synaptics.exe | |||
| (PID) Process: | (5712) MinecraftFpsMod.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A7803901000010901EF8A46ECE11A7FF00AA003CA9F6AC000000 | |||
| (PID) Process: | (5712) MinecraftFpsMod.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 72EEE26600000000 | |||
| (PID) Process: | (4252) ._cache_MinecraftFpsMod.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (2384) Bridgesurrogate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\b0655bbd0c4c61bc2ceb54a836ca6af98732ab8c |
| Operation: | write | Name: | 6c301ebcb941da1736bd7aea0f488b660b21fbce |
Value: H4sIAAAAAAAEAIXOsQ7CMAwE0H/pjPgANtqlA0gsnTBD2lipJYMrX1r4/EZMLCjr3dPp7k13IrrinPiVW7c32OM8LURRdTbkI3+4OfxVA6xTKemPG0oLots6qkxEFxk9uHCJ8AQqg1jMFFtFxYC+fq51iYmxulsKmb/6sQP2lNZU8gAAAA== | |||
| (PID) Process: | (2384) Bridgesurrogate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | dllhost |
Value: "C:\MsAgentBrowserdhcp\dllhost.exe" | |||
| (PID) Process: | (2384) Bridgesurrogate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UsoClient |
Value: "C:\MsAgentBrowserdhcp\UsoClient.exe" | |||
| (PID) Process: | (2384) Bridgesurrogate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | smss |
Value: "C:\Users\Public\Libraries\smss.exe" | |||
| (PID) Process: | (2384) Bridgesurrogate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | spoolsv |
Value: "C:\MsAgentBrowserdhcp\spoolsv.exe" | |||
Executable files
34
Suspicious files
8
Text files
22
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5712 | MinecraftFpsMod.exe | C:\ProgramData\Synaptics\RCXBBC6.tmp | executable | |
MD5:72582E1152710DD8FD17C22FC6117094 | SHA256:7FC7A9EF9FFFF42C18143F3C8F02BB3C7980708E08439B1ED5269B1125BDD8A0 | |||
| 5712 | MinecraftFpsMod.exe | C:\ProgramData\Synaptics\Synaptics.exe | executable | |
MD5:73D7E637CD16F1F807930FA6442436DF | SHA256:CD0F7FB1020A931C98C7C258241F06292CB9B7CAB8E9ACDB4010F4D56F076EF6 | |||
| 4252 | ._cache_MinecraftFpsMod.exe | C:\MsAgentBrowserdhcp\Bridgesurrogate.exe | executable | |
MD5:D5EB73597ED0A278E1A993EE15C5CDB1 | SHA256:B6B9517B7429AFEA6D33AE62A1CFF9CE8290B160F9F5544B1D9DD3AB0F620404 | |||
| 2384 | Bridgesurrogate.exe | C:\MsAgentBrowserdhcp\f3b6ecef712a24 | text | |
MD5:F9DE964396C8CDB193C00B5048FC64D8 | SHA256:B93CC6E2D1F460DDEF15D0C3E9FB72901F423CFF76F4B3C7645BA8A56E958779 | |||
| 5712 | MinecraftFpsMod.exe | C:\Users\admin\AppData\Local\Temp\._cache_MinecraftFpsMod.exe | executable | |
MD5:885383199B4458661A083D690ADEC52F | SHA256:7E1FBCC206AED09FF42684B9DCDAC876E2A1F7C068463430B1BFB21564AF1252 | |||
| 2384 | Bridgesurrogate.exe | C:\Users\admin\Desktop\MRjXOstH.log | executable | |
MD5:F4B38D0F95B7E844DD288B441EBC9AAF | SHA256:AAB95596475CA74CEDE5BA50F642D92FA029F6F74F6FAEAE82A9A07285A5FB97 | |||
| 2384 | Bridgesurrogate.exe | C:\Users\admin\Desktop\FsmIeiTa.log | executable | |
MD5:0B2AFABFAF0DD55AD21AC76FBF03B8A0 | SHA256:DD4560987BD87EF3E6E8FAE220BA22AA08812E9743352523C846553BD99E4254 | |||
| 4252 | ._cache_MinecraftFpsMod.exe | C:\MsAgentBrowserdhcp\RJohyDXhI3BukXB8LZtFph4xzxsRiCFy2OHMYmU5wvokqlpzCh.vbe | vbe | |
MD5:E6AA5A9A61E5A14929496CC623751FCB | SHA256:4518EAB1E079194970BEE0B64F0DC5151E2208A48A94672E9A98FBE046E6A7D9 | |||
| 2384 | Bridgesurrogate.exe | C:\Users\admin\Desktop\PbFYOLZH.log | executable | |
MD5:E9CE850DB4350471A62CC24ACB83E859 | SHA256:7C95D3B38114E7E4126CB63AADAF80085ED5461AB0868D2365DD6A18C946EA3A | |||
| 2384 | Bridgesurrogate.exe | C:\MsAgentBrowserdhcp\f21121a7321372 | text | |
MD5:39FB2F2FC5570FC62473BD7249E8C703 | SHA256:97D756031180BEFC035EB8B3B6E3396DCF6D5613131675E828F08F00CFFBB335 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
40
DNS requests
24
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1356 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7096 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
2024 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6696 | dasHost.exe | POST | 404 | 80.211.144.156:80 | http://noburo.top/phpJavascriptSecurecpuupdateFlowerAsyncUniversaltrack.php | unknown | — | — | unknown |
2476 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2476 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4680 | dasHost.exe | POST | 404 | 80.211.144.156:80 | http://noburo.top/phpJavascriptSecurecpuupdateFlowerAsyncUniversaltrack.php | unknown | — | — | unknown |
7096 | Synaptics.exe | GET | 200 | 172.217.16.131:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEEY%2BBbWicZDJCutGRyts3so%3D | unknown | — | — | whitelisted |
7096 | Synaptics.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
7096 | Synaptics.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1356 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1084 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1356 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7096 | Synaptics.exe | 69.42.215.252:80 | freedns.afraid.org | AWKNET | US | whitelisted |
1356 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2256 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2256 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
xred.mooo.com |
| whitelisted |
freedns.afraid.org |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
noburo.top |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
2256 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
6696 | dasHost.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
6696 | dasHost.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
6696 | dasHost.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
4680 | dasHost.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
4680 | dasHost.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
4540 | dasHost.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
4540 | dasHost.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
4540 | dasHost.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
3 ETPRO signatures available at the full report