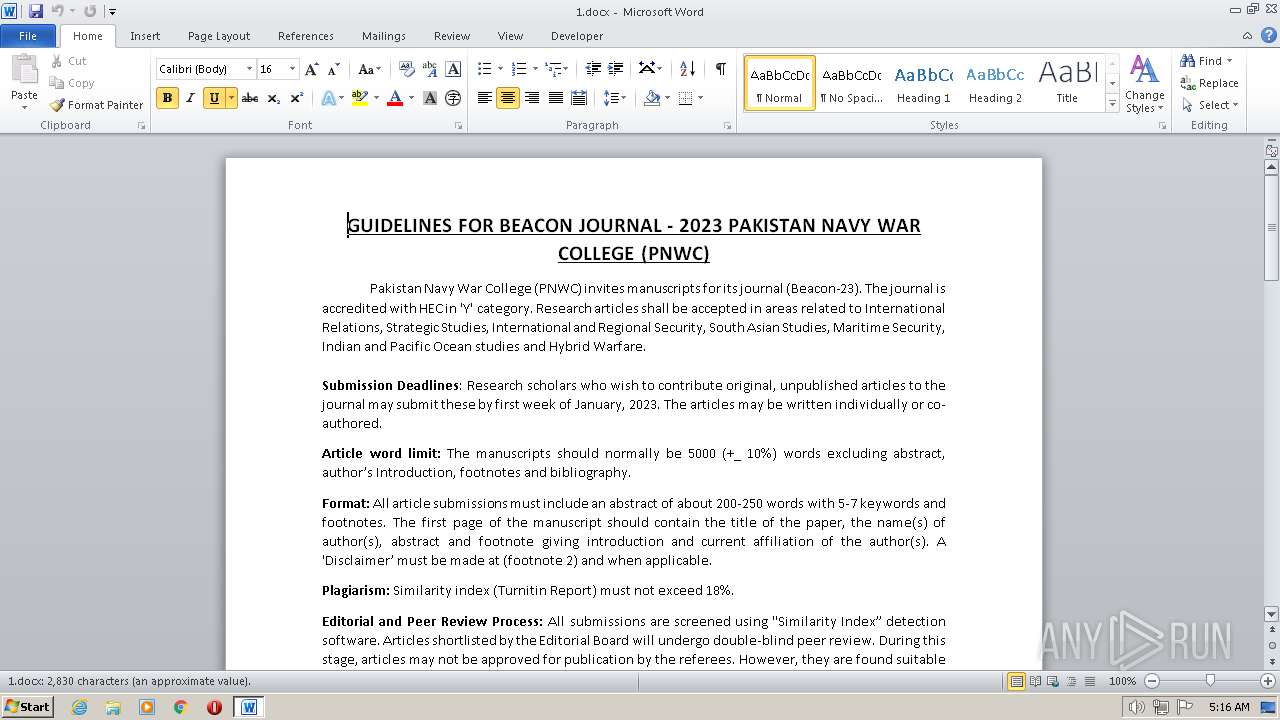
| File name: | 1.docx |
| Full analysis: | https://app.any.run/tasks/e2e17e55-f8a1-4d4f-8a86-2e168ff29159 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2022, 05:16:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 666B2B178CE52E30BE9E69DE93CC60A9 |
| SHA1: | FCC2D69A02F091593BC4F0B7D4F3CB5C90B4B011 |
| SHA256: | CD09BF437F46210521AD5C21891414F236E29AA6869906820C7C9DC2B565D8BE |
| SSDEEP: | 384:Txs3l0+5mYF8Bc2HtarGtYEerqy2SHgyOT4TO3wCB/g:Gv/yBcgtaQerqy2SHZOkTCXi |
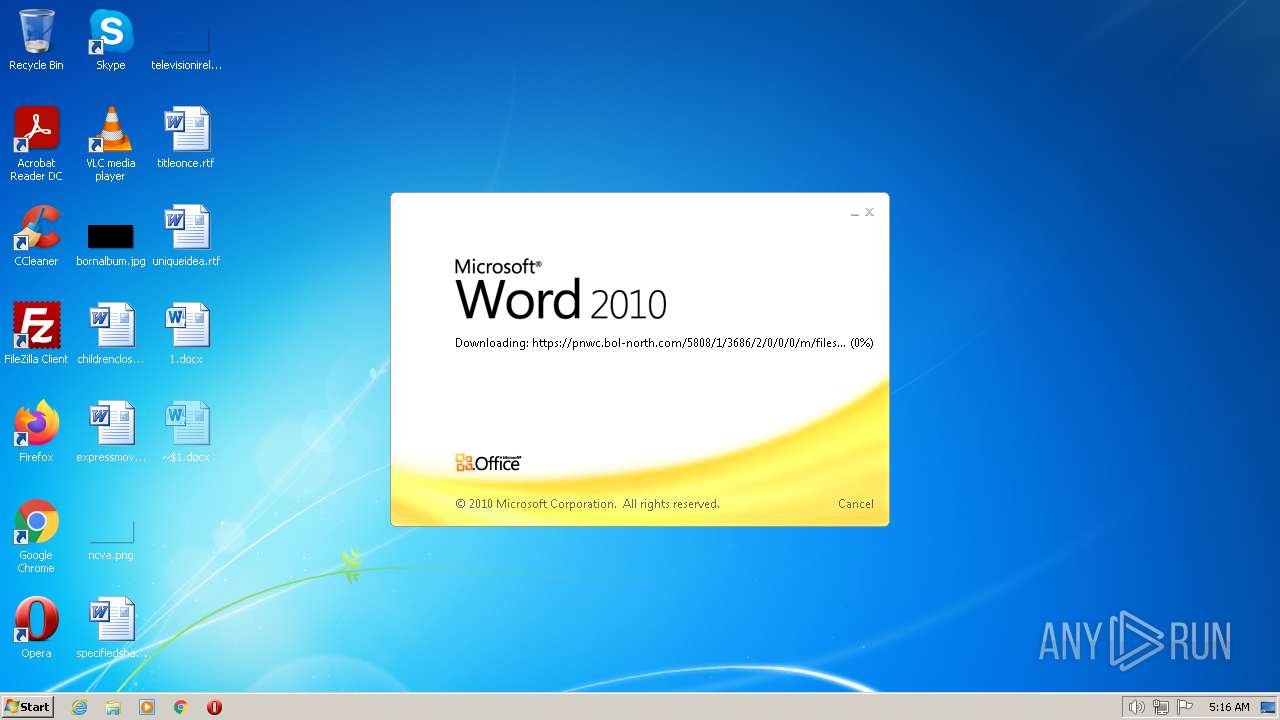
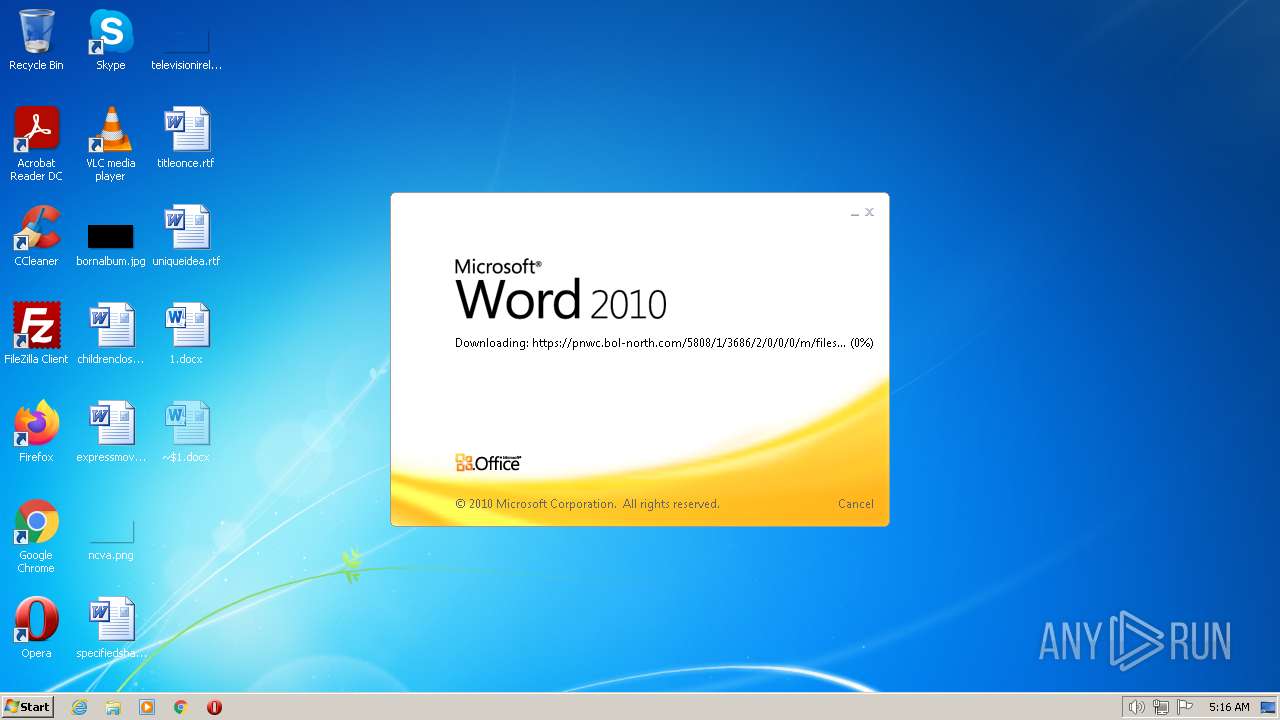
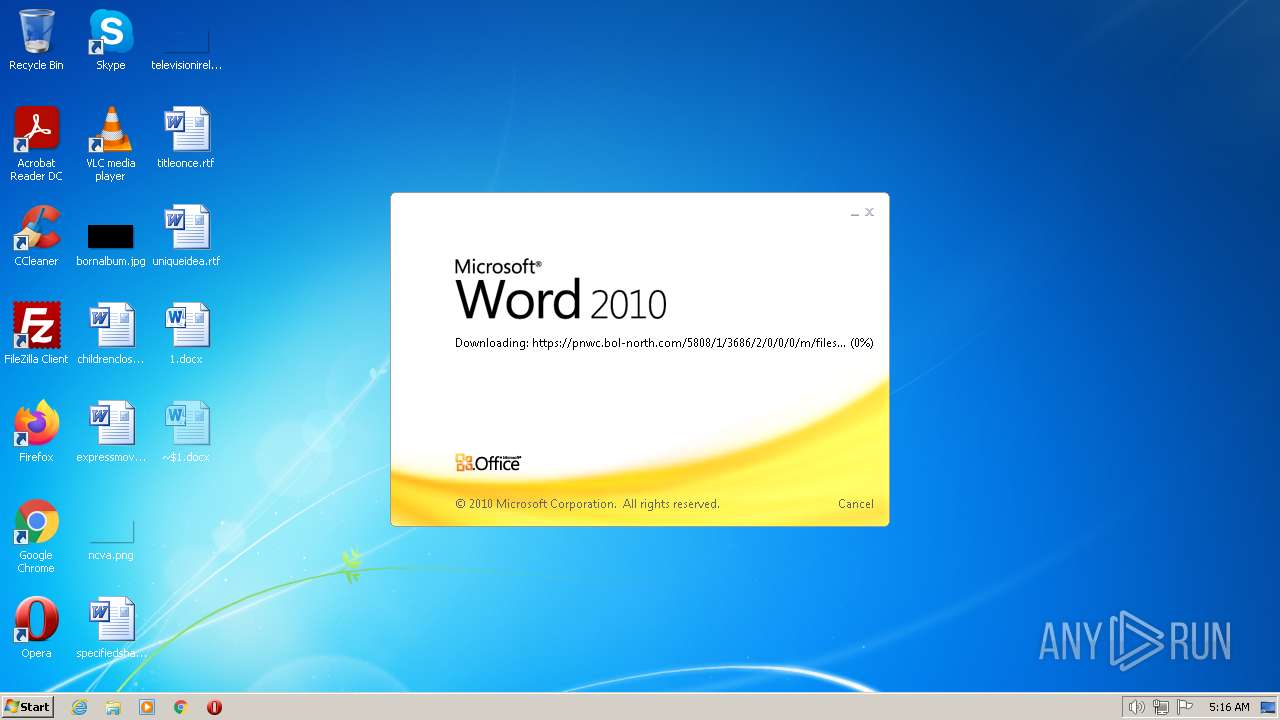
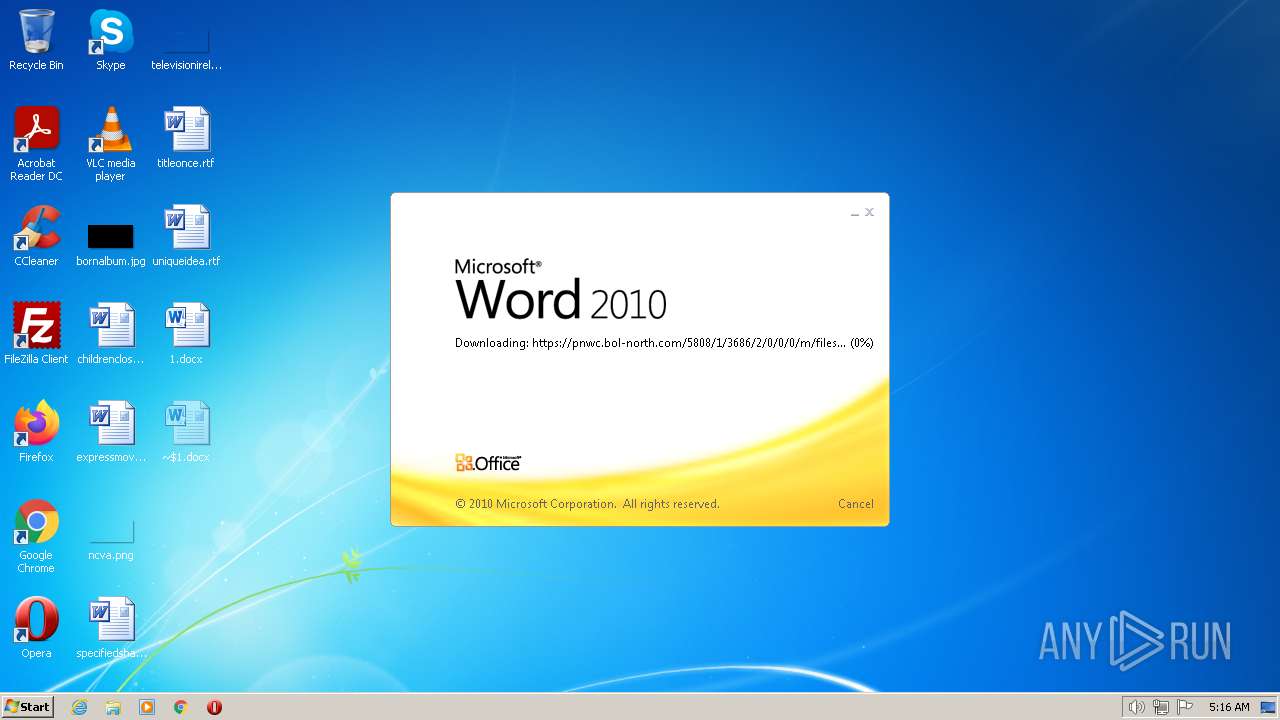
MALICIOUS
CVE-2022-30190 detected
- WINWORD.EXE (PID: 2276)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- WINWORD.EXE (PID: 2276)
INFO
Checks proxy server information
- WINWORD.EXE (PID: 2276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
Total processes
37
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2276 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\1.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
3 480
Read events
2 751
Write events
588
Delete events
141
Modification events
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | u?. |
Value: 753F2E00E4080000010000000000000000000000 | |||
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2276) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
8
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF775.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{65EB3D26-F59E-42F9-9738-A05FD102031C}.FSD | binary | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{271538B8-3EB4-453E-99AB-05ACE8104D52} | binary | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\Desktop\~$1.docx | pgc | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\9099C17C.emf | text | |
MD5:912FF26AC760112B12167F902F17ECFD | SHA256:1833637D2BB49186E0667AE0896ECC4D5B00B3383529F74EDB75CAD8748CD9B3 | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\1.docx.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{CCA6B314-0391-4AEF-83DE-857D2F6B32E5} | binary | |
MD5:— | SHA256:— | |||
| 2276 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
pnwc.bol-north.com |
| unknown |