| File name: | 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer |
| Full analysis: | https://app.any.run/tasks/6007c850-e2b0-46dc-bf84-40b6302f8bea |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2025, 04:40:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 8D295B9BCD55FE2AEC91CB6CA5AD99E5 |
| SHA1: | 83603A22E7B986BBDE30E6EF61A627F30CCEE7C1 |
| SHA256: | CD03958AC79BDDA675AFA2B37CE895D6E28CAAAA04EFBCF68341B71BC0E3D72A |
| SSDEEP: | 98304:byi3/tuCJcoKogj0YjbdDXayrZrRQQk1XB2EX5RfW6atOc4utMRF73J4sHRDJw+8:vgBQFxg |
MALICIOUS
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 5608)
- NSudoLG.exe (PID: 7864)
Changes Windows Defender settings
- NSudoLG.exe (PID: 7864)
Starts SC.EXE for service management
- cmd.exe (PID: 5608)
SUSPICIOUS
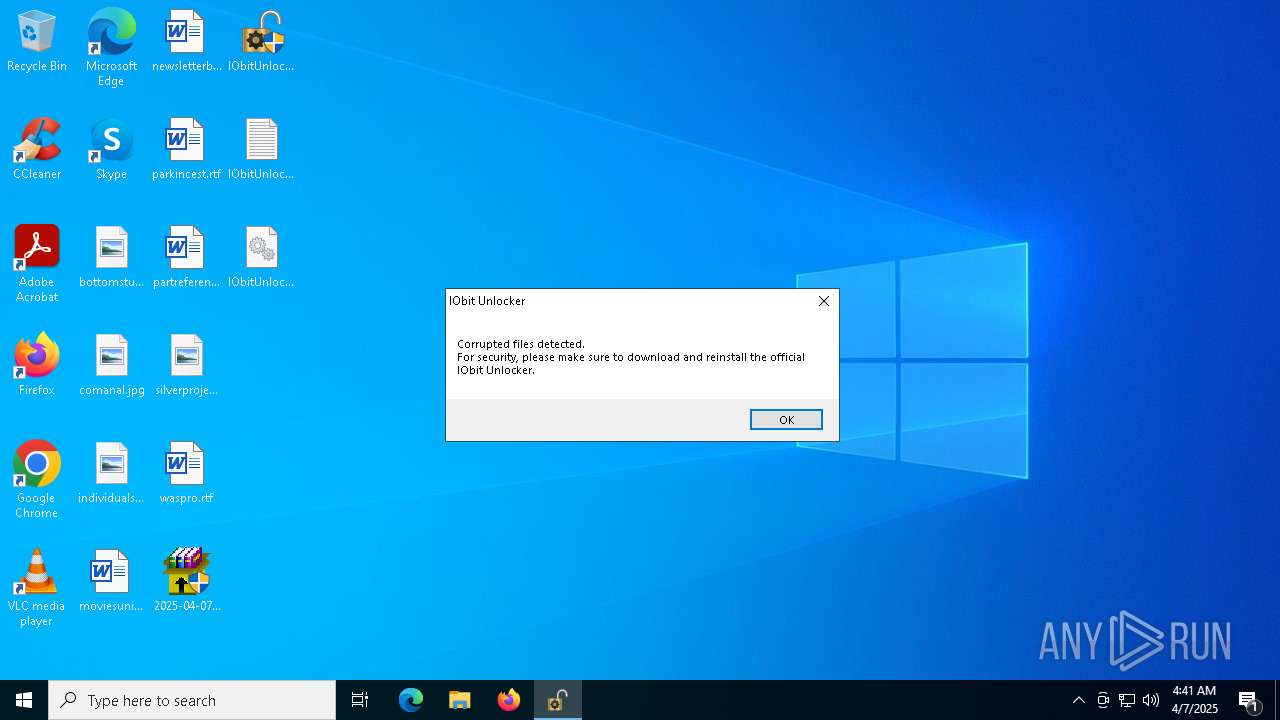
The process creates files with name similar to system file names
- 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe (PID: 7808)
Executable content was dropped or overwritten
- 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe (PID: 7808)
- 7z.exe (PID: 8036)
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 5640)
- Unlocker.exe (PID: 6640)
- cmd.exe (PID: 5608)
Drops 7-zip archiver for unpacking
- 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe (PID: 7808)
Reads security settings of Internet Explorer
- 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe (PID: 7808)
- 25.exe (PID: 7868)
- 25.exe (PID: 8048)
- 25.exe (PID: 1760)
- 25.exe (PID: 6988)
- Unlocker.exe (PID: 8024)
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 5640)
- Unlocker.exe (PID: 6640)
- Unlocker.exe (PID: 4896)
- ShellExperienceHost.exe (PID: 5964)
Executing commands from a ".bat" file
- 25.exe (PID: 7868)
- 25.exe (PID: 8048)
- 25.exe (PID: 1760)
- 25.exe (PID: 6988)
Starts CMD.EXE for commands execution
- 25.exe (PID: 7868)
- cmd.exe (PID: 7920)
- 25.exe (PID: 8048)
- 25.exe (PID: 1760)
- 25.exe (PID: 6988)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 5552)
- Unlocker.exe (PID: 8024)
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 5640)
- Unlocker.exe (PID: 6640)
- Unlocker.exe (PID: 4896)
The executable file from the user directory is run by the CMD process
- 25.exe (PID: 8048)
- 25.exe (PID: 6988)
Application launched itself
- cmd.exe (PID: 7920)
- cmd.exe (PID: 5552)
- cmd.exe (PID: 5608)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8096)
- cmd.exe (PID: 5608)
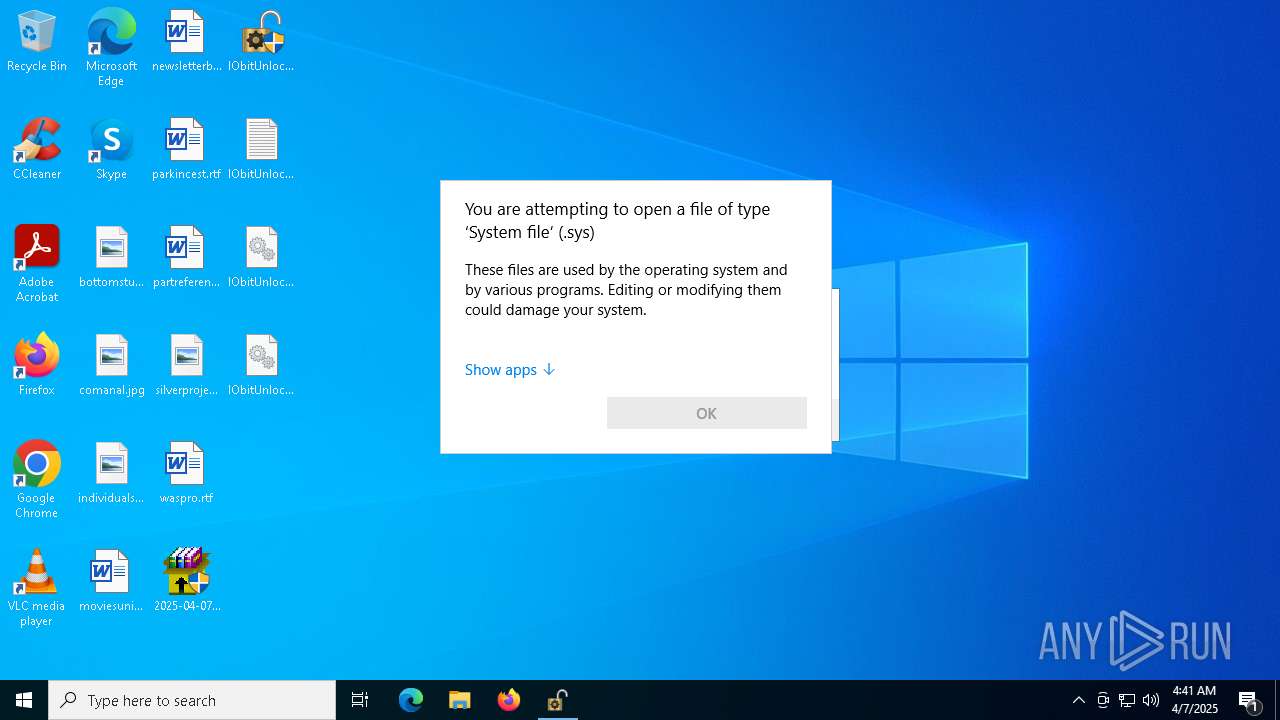
Starts application with an unusual extension
- cmd.exe (PID: 8096)
- cmd.exe (PID: 5608)
Get information on the list of running processes
- cmd.exe (PID: 7020)
- cmd.exe (PID: 5608)
Script adds exclusion path to Windows Defender
- NSudoLG.exe (PID: 7864)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 7936)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5608)
Starts POWERSHELL.EXE for commands execution
- NSudoLG.exe (PID: 7864)
Starts SC.EXE for service management
- cmd.exe (PID: 6456)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 6964)
- cmd.exe (PID: 7236)
- cmd.exe (PID: 7932)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 8084)
- cmd.exe (PID: 1912)
- cmd.exe (PID: 7584)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 1324)
Windows service management via SC.EXE
- sc.exe (PID: 5552)
- sc.exe (PID: 1676)
- sc.exe (PID: 7192)
- sc.exe (PID: 7592)
- sc.exe (PID: 5008)
- sc.exe (PID: 5164)
- sc.exe (PID: 8016)
- sc.exe (PID: 8136)
- sc.exe (PID: 5360)
- sc.exe (PID: 4400)
- sc.exe (PID: 6800)
- sc.exe (PID: 7644)
- sc.exe (PID: 7684)
- sc.exe (PID: 8168)
- sc.exe (PID: 8152)
- sc.exe (PID: 744)
- sc.exe (PID: 6876)
- sc.exe (PID: 7304)
- sc.exe (PID: 7992)
- sc.exe (PID: 8072)
- sc.exe (PID: 7936)
- sc.exe (PID: 8004)
- sc.exe (PID: 1276)
- sc.exe (PID: 7876)
- sc.exe (PID: 6540)
- sc.exe (PID: 5056)
- sc.exe (PID: 4620)
- sc.exe (PID: 680)
- sc.exe (PID: 660)
- sc.exe (PID: 5008)
- sc.exe (PID: 7180)
- sc.exe (PID: 7592)
- sc.exe (PID: 5868)
- sc.exe (PID: 8028)
- sc.exe (PID: 5428)
- sc.exe (PID: 4724)
- sc.exe (PID: 5800)
- sc.exe (PID: 5328)
- sc.exe (PID: 920)
- sc.exe (PID: 7560)
- sc.exe (PID: 7724)
- sc.exe (PID: 7784)
- sc.exe (PID: 4068)
- sc.exe (PID: 3900)
- sc.exe (PID: 7244)
- sc.exe (PID: 7516)
- sc.exe (PID: 7352)
- sc.exe (PID: 5800)
- sc.exe (PID: 5212)
Reads the date of Windows installation
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 8024)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 5640)
- Unlocker.exe (PID: 6640)
- Unlocker.exe (PID: 4896)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6132)
- cmd.exe (PID: 6344)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 6036)
- cmd.exe (PID: 7316)
- cmd.exe (PID: 6040)
- cmd.exe (PID: 3768)
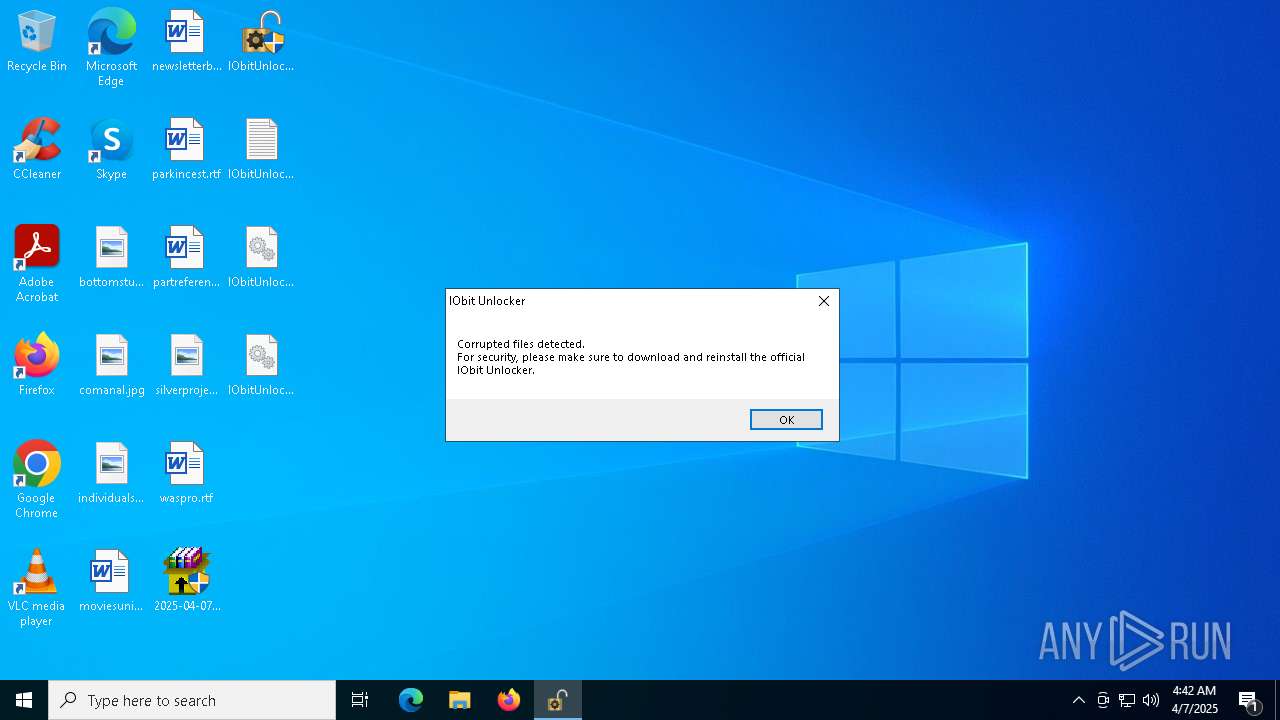
Drops a system driver (possible attempt to evade defenses)
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 5640)
- Unlocker.exe (PID: 6640)
Creates or modifies Windows services
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 6640)
- Unlocker.exe (PID: 5640)
Stops a currently running service
- sc.exe (PID: 7676)
- sc.exe (PID: 4068)
- sc.exe (PID: 8036)
- sc.exe (PID: 5956)
- sc.exe (PID: 2800)
- sc.exe (PID: 5968)
- sc.exe (PID: 8160)
- sc.exe (PID: 2552)
- sc.exe (PID: 8100)
- sc.exe (PID: 7960)
- sc.exe (PID: 6028)
- sc.exe (PID: 780)
- sc.exe (PID: 5408)
- sc.exe (PID: 5956)
- sc.exe (PID: 8036)
- sc.exe (PID: 5212)
- sc.exe (PID: 7652)
- sc.exe (PID: 7684)
- sc.exe (PID: 7804)
- sc.exe (PID: 7636)
- sc.exe (PID: 6108)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5608)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 7892)
- schtasks.exe (PID: 7964)
- schtasks.exe (PID: 7904)
- schtasks.exe (PID: 7864)
- schtasks.exe (PID: 7944)
INFO
The sample compiled with english language support
- 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe (PID: 7808)
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 6640)
- Unlocker.exe (PID: 5640)
- cmd.exe (PID: 5608)
Reads the computer name
- 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe (PID: 7808)
- 25.exe (PID: 7868)
- 25.exe (PID: 8048)
- NSudoLG.exe (PID: 7228)
- 25.exe (PID: 1760)
- 25.exe (PID: 6988)
- NSudoLG.exe (PID: 7864)
- 7z.exe (PID: 8036)
- Unlocker.exe (PID: 8024)
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 5640)
- Unlocker.exe (PID: 6640)
- Unlocker.exe (PID: 4896)
- ShellExperienceHost.exe (PID: 5964)
- IObitUnlocker.exe (PID: 5508)
Process checks computer location settings
- 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe (PID: 7808)
- 25.exe (PID: 7868)
- 25.exe (PID: 8048)
Create files in a temporary directory
- 25.exe (PID: 7868)
- 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe (PID: 7808)
- 7z.exe (PID: 8036)
- 25.exe (PID: 8048)
Checks supported languages
- 25.exe (PID: 7868)
- 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe (PID: 7808)
- 25.exe (PID: 8048)
- chcp.com (PID: 8156)
- 25.exe (PID: 1760)
- NSudoLG.exe (PID: 7228)
- 25.exe (PID: 6988)
- chcp.com (PID: 5204)
- mode.com (PID: 7052)
- NSudoLG.exe (PID: 7864)
- 7z.exe (PID: 8036)
- Unlocker.exe (PID: 8024)
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 5640)
- Unlocker.exe (PID: 6640)
- ShellExperienceHost.exe (PID: 5964)
- Unlocker.exe (PID: 4896)
- IObitUnlocker.exe (PID: 5508)
Changes the display of characters in the console
- cmd.exe (PID: 8096)
- cmd.exe (PID: 5608)
Starts MODE.COM to configure console settings
- mode.com (PID: 7052)
Checks operating system version
- cmd.exe (PID: 5608)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7936)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7936)
Reads the machine GUID from the registry
- Unlocker.exe (PID: 8024)
- Unlocker.exe (PID: 7816)
- Unlocker.exe (PID: 7840)
- Unlocker.exe (PID: 8172)
- Unlocker.exe (PID: 5640)
- Unlocker.exe (PID: 6640)
- Unlocker.exe (PID: 4896)
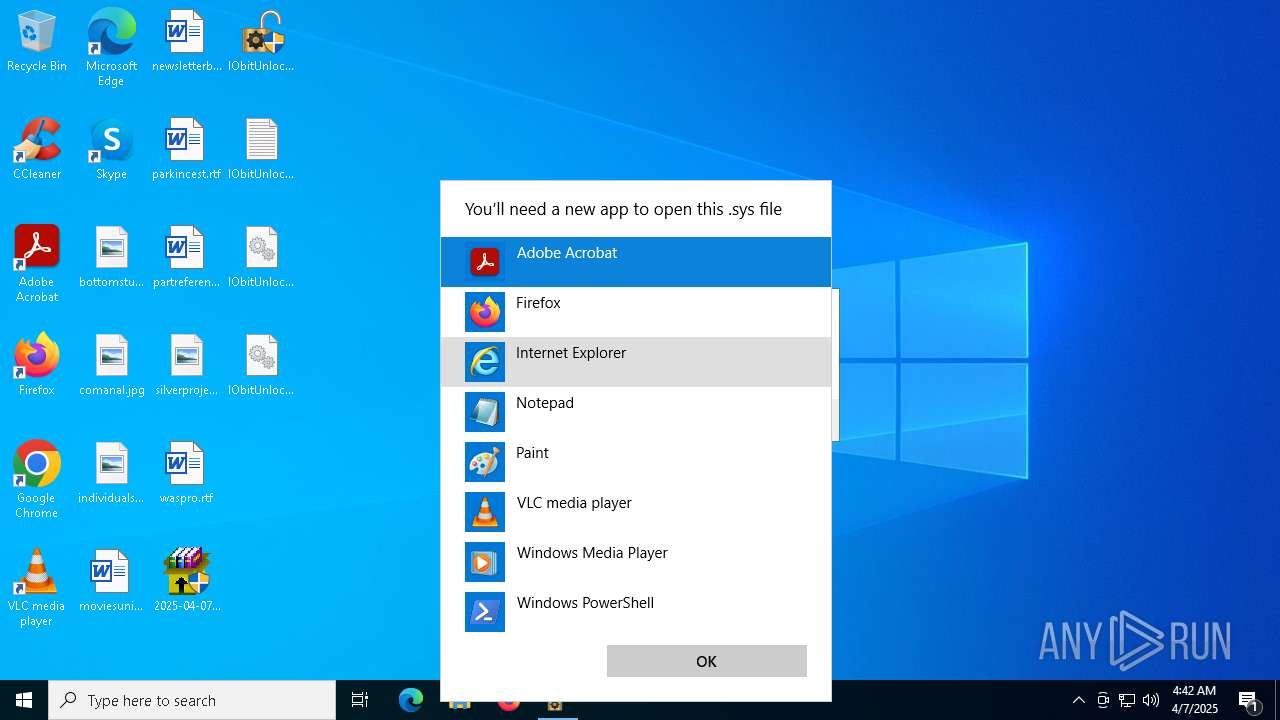
Manual execution by a user
- IObitUnlocker.exe (PID: 5508)
- OpenWith.exe (PID: 8168)
- IObitUnlocker.exe (PID: 7712)
Creates files in the program directory
- IObitUnlocker.exe (PID: 5508)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 8168)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 8168)
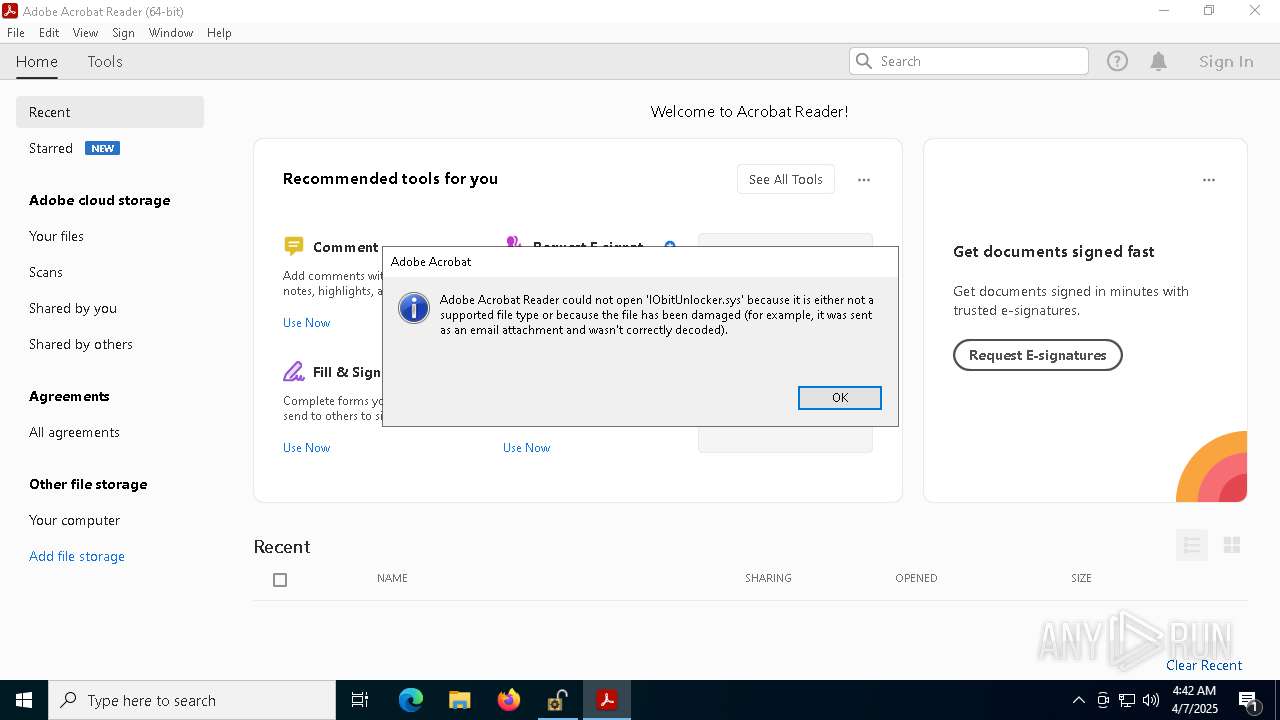
Application launched itself
- Acrobat.exe (PID: 7916)
- AcroCEF.exe (PID: 2228)
Checks proxy server information
- slui.exe (PID: 5400)
Reads the software policy settings
- slui.exe (PID: 5400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:03:03 13:15:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.3 |
| CodeSize: | 203776 |
| InitializedDataSize: | 77312 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f530 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
372
Monitored processes
243
Malicious processes
14
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | taskkill /f /pid "4896" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | reg query "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v "EnableLUA" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | sc delete "webthreatdefusersvc" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | sc config "webthreatdefusersvc" start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1520 --field-trial-handle=1572,i,1773485491306749916,13364572437870331097,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 744 | sc delete "WinDefend" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | sc stop "webthreatdefsvc" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | timeout /t 2 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | sc config "SgrmAgent" start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 217
Read events
32 956
Write events
123
Delete events
138
Modification events
| (PID) Process: | (6476) reg.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize |
| Operation: | write | Name: | AppsUseLightTheme |
Value: 0 | |||
| (PID) Process: | (5800) reg.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize |
| Operation: | write | Name: | AppsUseLightTheme |
Value: 0 | |||
| (PID) Process: | (8024) Unlocker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\DK |
| Operation: | write | Name: | CurrentDiskSize |
Value: 228901273600 | |||
| (PID) Process: | (7816) Unlocker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\IObitUnlocker |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (7816) Unlocker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\IObitUnlocker |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (7816) Unlocker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\IObitUnlocker |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (7816) Unlocker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\IObitUnlocker |
| Operation: | write | Name: | ImagePath |
Value: C:\WINDOWS\TEMP\IObitUnlocker\IObitUnlocker.sys | |||
| (PID) Process: | (7840) Unlocker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\IObitUnlocker |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (7840) Unlocker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\IObitUnlocker |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (7840) Unlocker.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\IObitUnlocker |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
Executable files
25
Suspicious files
113
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7808 | 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\25.exe | executable | |
MD5:87FA6883F60EAD8AB996B42314060FF7 | SHA256:A2CCB2AD0C77FCF5F418B7A9BE2B88A657CD22019DBED44C125DA3CBF659E8E4 | |||
| 7808 | 2025-04-07_8d295b9bcd55fe2aec91cb6ca5ad99e5_black-basta_cova_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\Work\DKTolz.zip | compressed | |
MD5:B4163C2AF1EBA60ECDD85C4DCBA6BEEE | SHA256:8EA3DEBBC3EEE93B37B27188477BB573EAF0868BC33ECAF27DABC5D6DF39F3B1 | |||
| 7936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_y5ezsyk4.5yc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7936 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:FD1420CD8AE2AA8222F0C958165E709D | SHA256:CA1CCB21DAA7FA2F9A40234899477AF380C0DBFC840ECF4C4108DA0430691054 | |||
| 7816 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker.zip | compressed | |
MD5:6833604A8B0F0BD4E65F14D5DEDB13FD | SHA256:F81163FE8E7C95157797F4D955BB6E9FCBB4C0E16A0798D459974E3320DAB942 | |||
| 7840 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker\IObitUnlocker.dll | executable | |
MD5:2C6233C8DBC560027EE1427F5413E4B1 | SHA256:37D2A1626DC205D60F0BEC8746AB256569267E4EF2F8F84DFF4D9D792AA3AF30 | |||
| 7816 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker\IObitUnlocker.exe | executable | |
MD5:2541290195FFE29716EBBC7AAC76D82F | SHA256:EAA9DC1C9DC8620549FEE54D81399488292349D2C8767B58B7D0396564FB43E7 | |||
| 7840 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker.zip | compressed | |
MD5:6833604A8B0F0BD4E65F14D5DEDB13FD | SHA256:F81163FE8E7C95157797F4D955BB6E9FCBB4C0E16A0798D459974E3320DAB942 | |||
| 7936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5z3hny5h.ji5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7816 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker\IObitUnlocker.dll | executable | |
MD5:2C6233C8DBC560027EE1427F5413E4B1 | SHA256:37D2A1626DC205D60F0BEC8746AB256569267E4EF2F8F84DFF4D9D792AA3AF30 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | OPTIONS | 204 | 34.237.241.83:443 | https://p13n.adobe.io/psdk/v2/content?surfaceId=ACROBAT_READER_MASTER_SURFACEID&surfaceId=DC_READER_LAUNCH_CARD&surfaceId=DC_Reader_RHP_Banner&surfaceId=DC_Reader_RHP_Retention&surfaceId=Edit_InApp_Aug2020&surfaceId=DC_FirstMile_Right_Sec_Surface&surfaceId=DC_Reader_Upsell_Cards&surfaceId=DC_FirstMile_Home_View_Surface&surfaceId=DC_Reader_RHP_Intent_Banner&surfaceId=DC_Reader_Disc_LHP_Banner&surfaceId=DC_Reader_Edit_LHP_Banner&surfaceId=DC_Reader_Convert_LHP_Banner&surfaceId=DC_Reader_Sign_LHP_Banner&surfaceId=DC_Reader_More_LHP_Banner&surfaceId=DC_Reader_Disc_LHP_Retention&adcProductLanguage=en-us&adcVersion=23.1.20093&adcProductType=SingleClientMini&adcOSType=WIN&adcCountryCode=TH&adcXAPIClientID=api_reader_desktop_win_23.1.20093&encodingScheme=BASE_64 | unknown | — | — | unknown |
4108 | RUXIMICS.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 23.213.164.167:443 | https://geo2.adobe.com/ | unknown | text | 50 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 18.213.11.84:443 | https://p13n.adobe.io/psdk/v2/content?surfaceId=ACROBAT_READER_MASTER_SURFACEID&surfaceId=DC_READER_LAUNCH_CARD&surfaceId=DC_Reader_RHP_Banner&surfaceId=DC_Reader_RHP_Retention&surfaceId=Edit_InApp_Aug2020&surfaceId=DC_FirstMile_Right_Sec_Surface&surfaceId=DC_Reader_Upsell_Cards&surfaceId=DC_FirstMile_Home_View_Surface&surfaceId=DC_Reader_RHP_Intent_Banner&surfaceId=DC_Reader_Disc_LHP_Banner&surfaceId=DC_Reader_Edit_LHP_Banner&surfaceId=DC_Reader_Convert_LHP_Banner&surfaceId=DC_Reader_Sign_LHP_Banner&surfaceId=DC_Reader_More_LHP_Banner&surfaceId=DC_Reader_Disc_LHP_Retention&adcProductLanguage=en-us&adcVersion=23.1.20093&adcProductType=SingleClientMini&adcOSType=WIN&adcCountryCode=TH&adcXAPIClientID=api_reader_desktop_win_23.1.20093&encodingScheme=BASE_64 | unknown | binary | 187 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4108 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4108 | RUXIMICS.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7404 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4008 | AcroCEF.exe | 23.213.164.167:443 | geo2.adobe.com | AKAMAI-AS | DE | whitelisted |
4008 | AcroCEF.exe | 34.237.241.83:443 | p13n.adobe.io | AMAZON-AES | US | whitelisted |
5400 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |