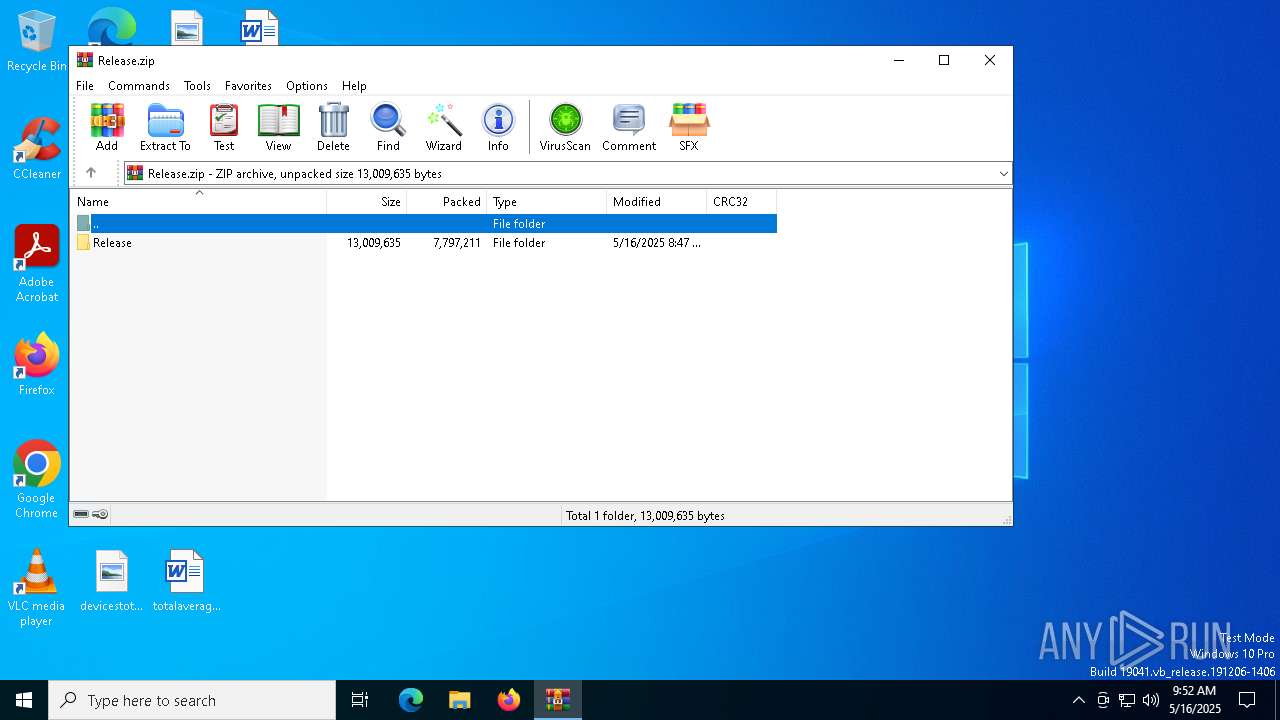
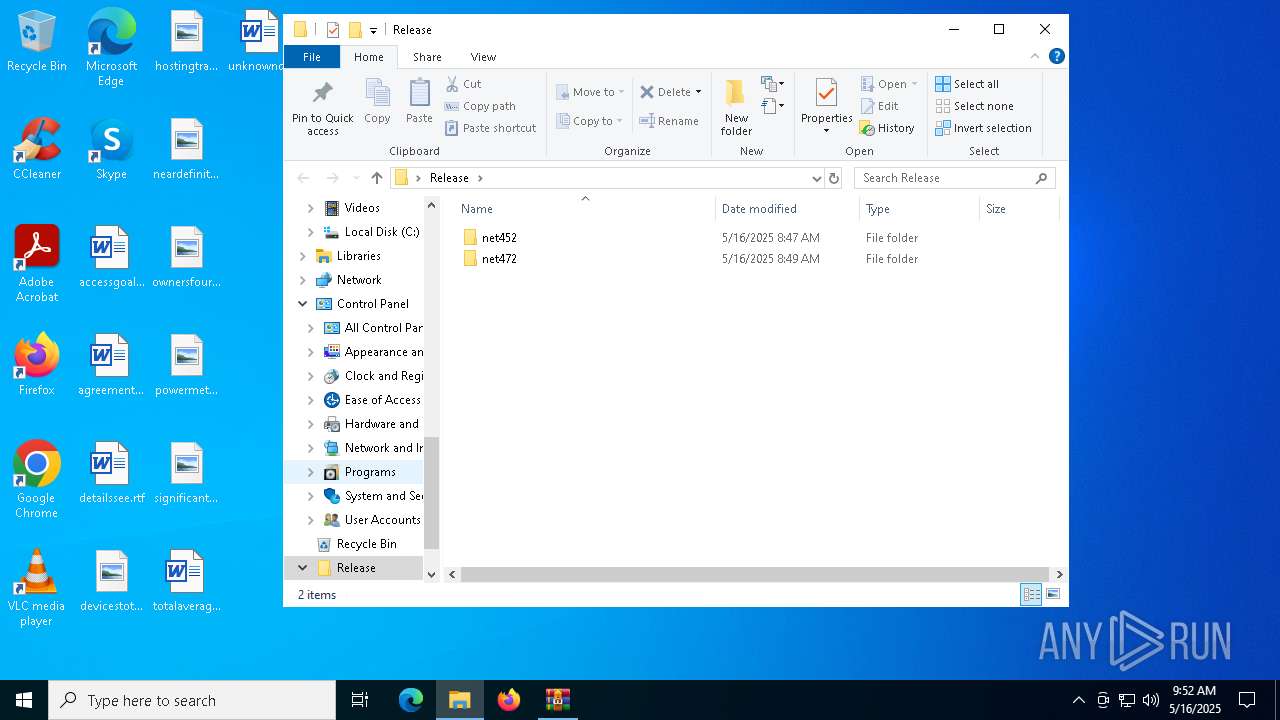
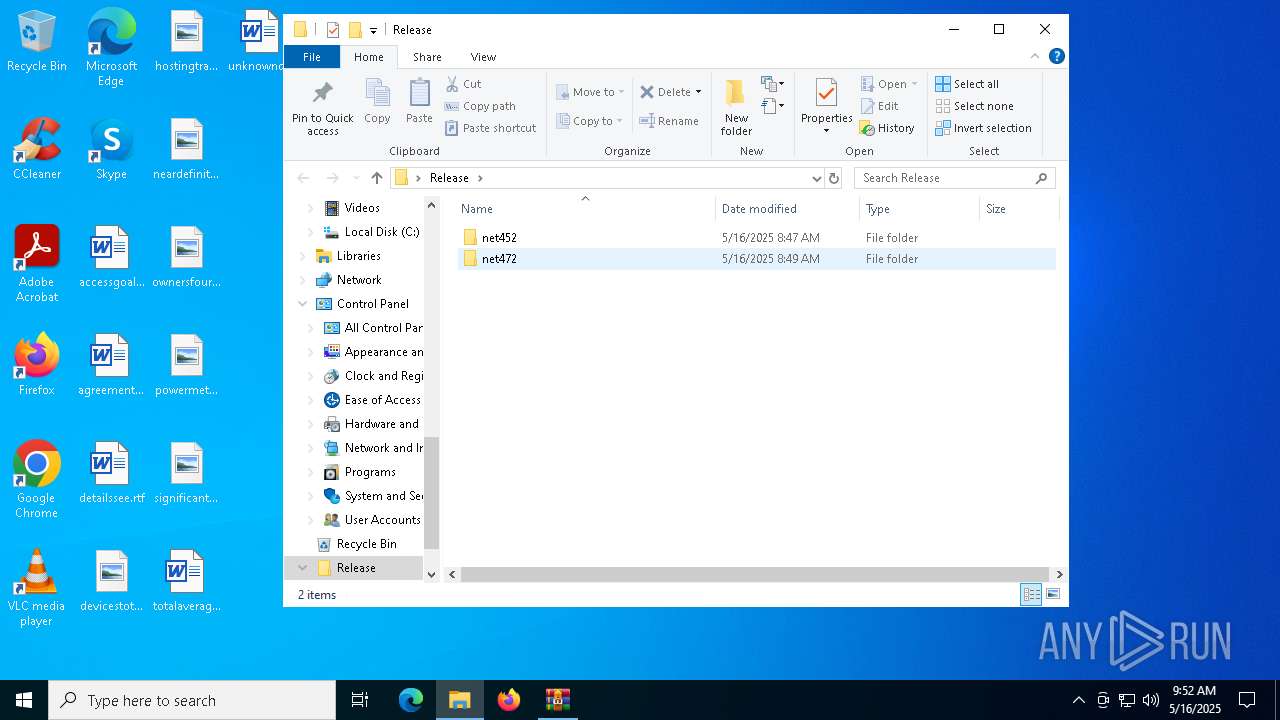
| File name: | Release.zip |
| Full analysis: | https://app.any.run/tasks/f106abe6-2095-4799-b805-0fbd05e2b5ae |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 09:52:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 281EF50C5F2085782239D90114BAB3E0 |
| SHA1: | 6EB53BAF86E8CE6928430A76E2C617D7FB43EC91 |
| SHA256: | CCCE27D92D4593FE0BEB0239C0BE22589321ED5FD38493E450ED4299BB55857F |
| SSDEEP: | 98304:XFsW9HlcPV1RStkJUz891wLFEUxrB/XyeXEoGq9VxcOwtw0L9OyEPFjanbdk9A61:rSV1wQyRXKsJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates file in the systems drive root
- explorer.exe (PID: 3676)
Reads security settings of Internet Explorer
- Pulsar.exe (PID: 8116)
Process drops legitimate windows executable
- WinRAR.exe (PID: 7396)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 7396)
Reads the date of Windows installation
- Pulsar.exe (PID: 8116)
INFO
Manual execution by a user
- Pulsar.exe (PID: 8116)
Reads security settings of Internet Explorer
- explorer.exe (PID: 3676)
Creates files or folders in the user directory
- Pulsar.exe (PID: 8116)
Creates files in the program directory
- Pulsar.exe (PID: 8116)
Process checks computer location settings
- Pulsar.exe (PID: 8116)
Reads the machine GUID from the registry
- Pulsar.exe (PID: 8116)
Reads Environment values
- Pulsar.exe (PID: 8116)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7396)
Reads the computer name
- Pulsar.exe (PID: 8116)
Reads product name
- Pulsar.exe (PID: 8116)
Checks supported languages
- Pulsar.exe (PID: 8116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:16 09:47:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Release/ |
Total processes
136
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3676 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7220 | "C:\Windows\explorer.exe" /select, "C:\Users\admin\Desktop\Release\net472\Pulsar.p12" | C:\Windows\explorer.exe | — | Pulsar.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
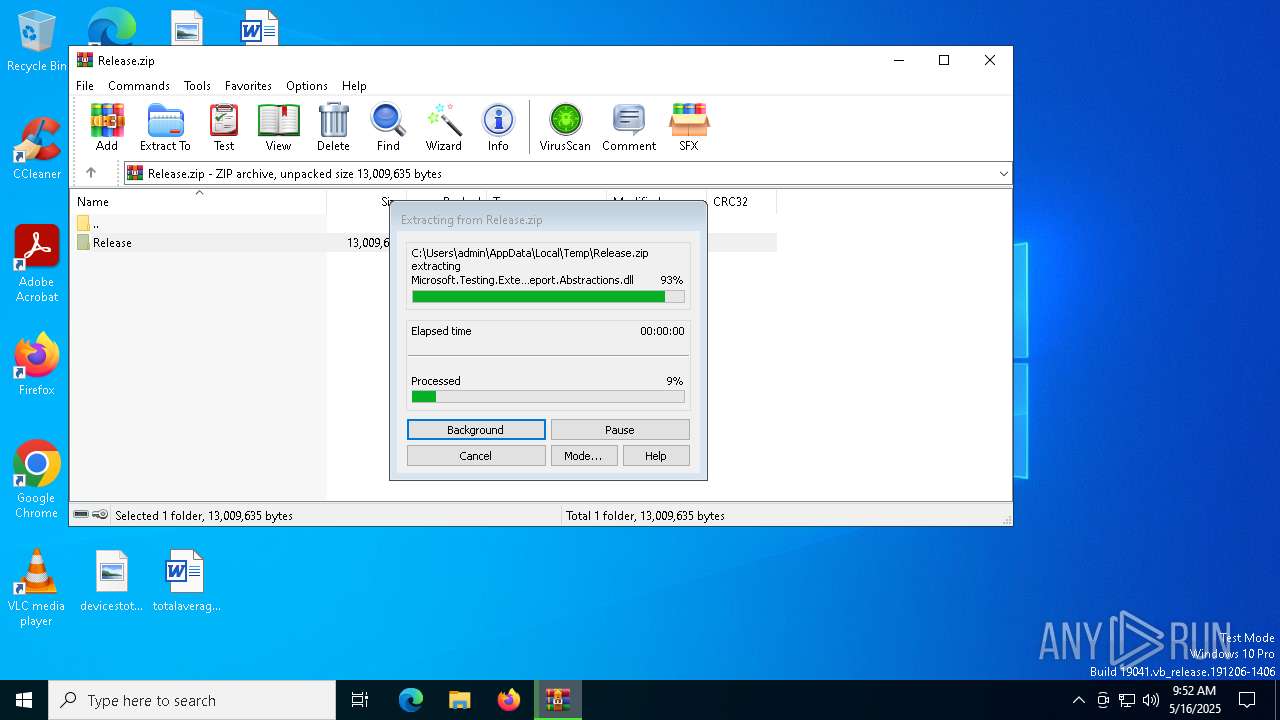
| 7396 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Release.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7552 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7584 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7976 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
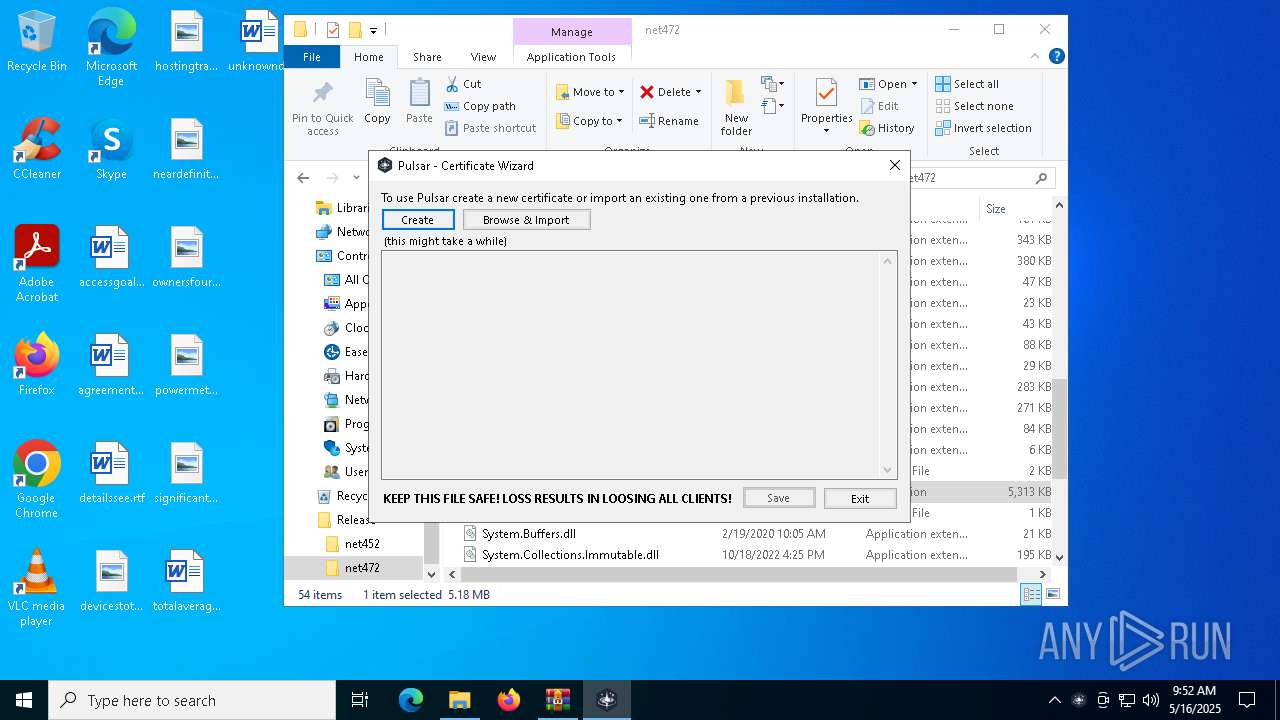
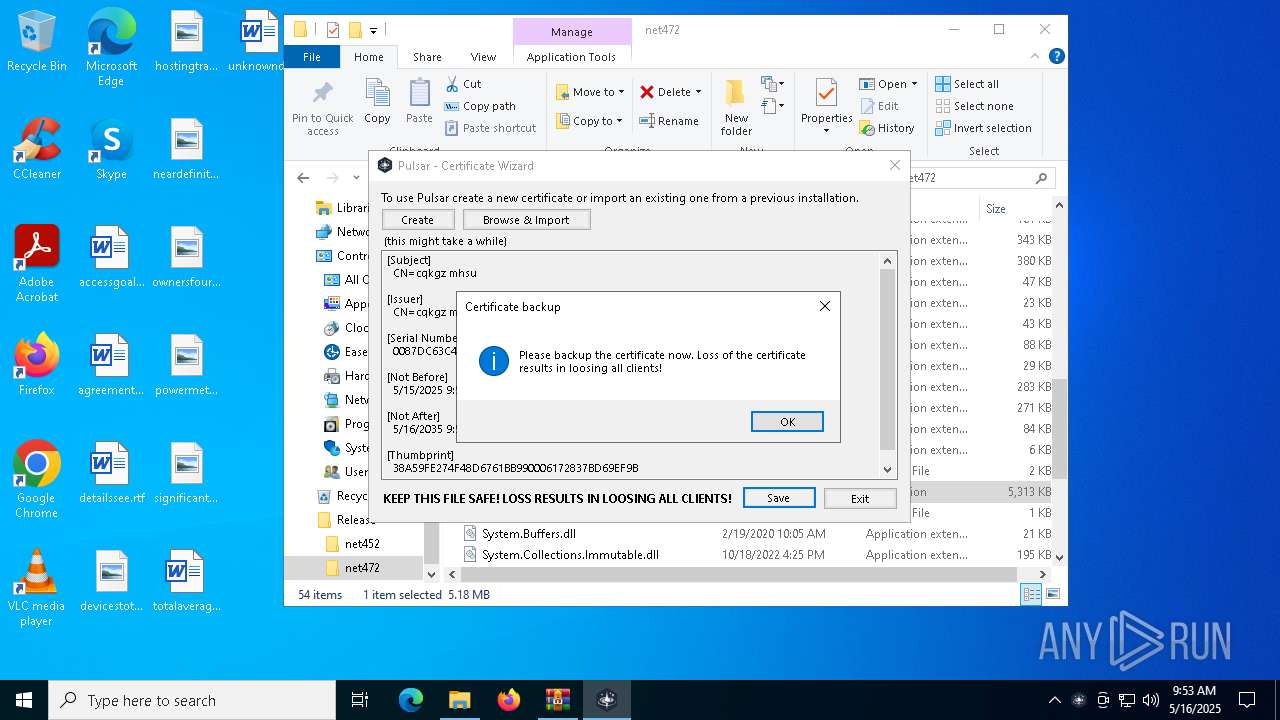
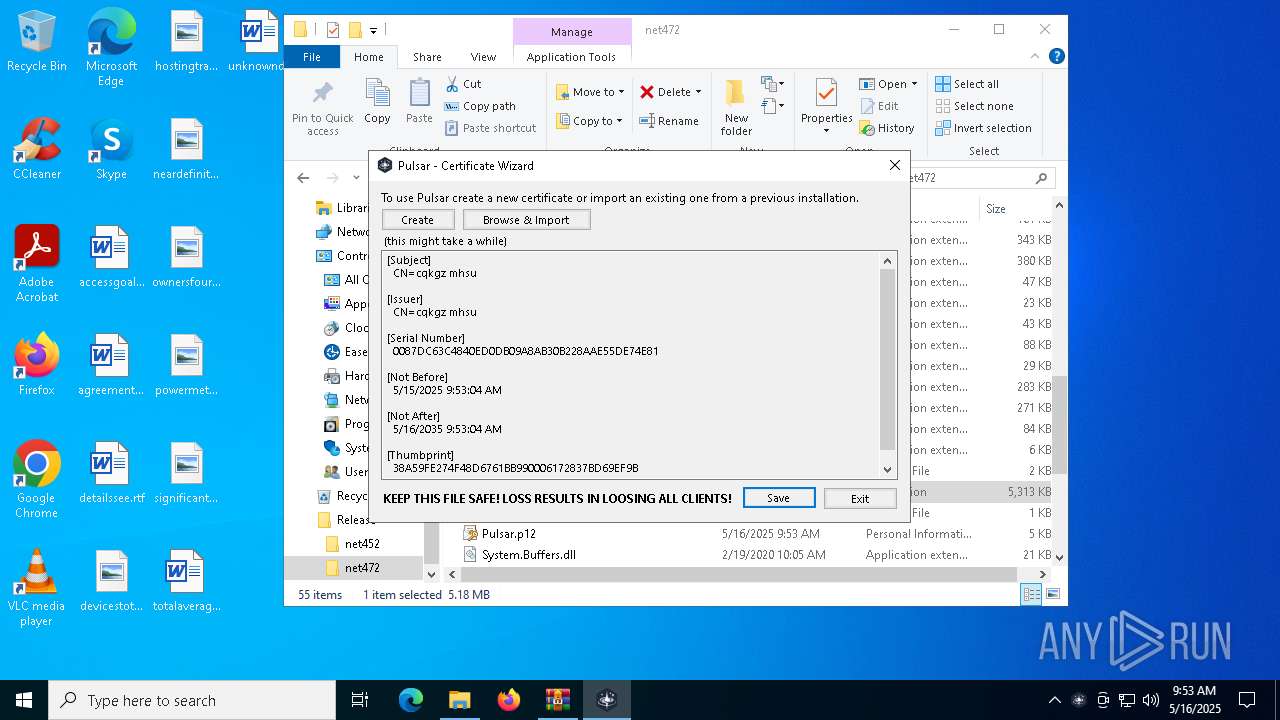
| 8116 | "C:\Users\admin\Desktop\Release\net472\Pulsar.exe" | C:\Users\admin\Desktop\Release\net472\Pulsar.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Pulsar Server Exit code: 0 Version: 1.6.0 Modules
| |||||||||||||||
Total events
10 179
Read events
10 140
Write events
36
Delete events
3
Modification events
| (PID) Process: | (7396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Release.zip | |||
| (PID) Process: | (7396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7396) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3676) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | MinimizedStateTabletModeOff |
Value: 0 | |||
| (PID) Process: | (3676) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | QatItems |
Value: 3C7369713A637573746F6D554920786D6C6E733A7369713D22687474703A2F2F736368656D61732E6D6963726F736F66742E636F6D2F77696E646F77732F323030392F726962626F6E2F716174223E3C7369713A726962626F6E206D696E696D697A65643D2266616C7365223E3C7369713A71617420706F736974696F6E3D2230223E3C7369713A736861726564436F6E74726F6C733E3C7369713A636F6E74726F6C206964513D227369713A3136313238222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3136313239222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333532222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333834222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333336222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333537222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C2F7369713A736861726564436F6E74726F6C733E3C2F7369713A7161743E3C2F7369713A726962626F6E3E3C2F7369713A637573746F6D55493E | |||
Executable files
129
Suspicious files
3
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\cs\Microsoft.Testing.Extensions.VSTestBridge.resources.dll | executable | |
MD5:88DDF36119B1278D60BED2F81F1F35D4 | SHA256:22BD5E7A2E719EFF9F57D5EE9957A2D92FA78BB631A2F95101219CC2FB84F52A | |||
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\cs\Microsoft.Testing.Extensions.Telemetry.resources.dll | executable | |
MD5:839950F946113B5FC375DD3DA71B16BC | SHA256:46DD55883BADEDAF61A6B47DDF6778DABCE0B03F25C14AE235133B2C06C03095 | |||
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\cs\Microsoft.Testing.Extensions.MSBuild.resources.dll | executable | |
MD5:8615942CA00F0D60A1CB66986370A4E3 | SHA256:50AE5EA6A47C707230CD28A75F8C70DAB459112BD45CB51B58BF58492115B89B | |||
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\cs\Microsoft.VisualStudio.TestPlatform.TestFramework.resources.dll | executable | |
MD5:31312A8C4087DEDC46CF209903230F70 | SHA256:EB9CE6BC555187D4AEDC5C700EC4FC62F90C7F67493AF8B56A8C9BC34F0A41F6 | |||
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\cs\Microsoft.TestPlatform.CoreUtilities.resources.dll | executable | |
MD5:693EC085DD366C21DE93F8306983E61D | SHA256:503F10BDC72BD3CA08B8B6A752605A91473B73BEA2ACD22602B88A0D41F1AEF7 | |||
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\cs\Microsoft.VisualStudio.TestPlatform.ObjectModel.resources.dll | executable | |
MD5:D121F6CECC4CA91653359CEC173B6BF7 | SHA256:C7D068FE4DA899069605B3B1F9DAA3F63D6C16C67F5C01698E2193CACEE48F59 | |||
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\cs\Microsoft.Testing.Platform.resources.dll | executable | |
MD5:D3EA6F9C5A84FB1A464D401D989C9338 | SHA256:567645C51EF8D36C725563515E4B54A0C4003EB9281D5B7BDC39FDE15FBB4DB6 | |||
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\de\Microsoft.TestPlatform.CoreUtilities.resources.dll | executable | |
MD5:34C967C01370C1E4BF1ADFCAB9B86A50 | SHA256:BD20DFFDFE3266E0FD4935A0E8EC581DEE18C448BC54475F79F6D4AFB2EAB03C | |||
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\de\Microsoft.VisualStudio.TestPlatform.ObjectModel.resources.dll | executable | |
MD5:E3B6DCBA6FB2FC2D98D7245D7C403D42 | SHA256:05E9280DFF0F134353E58E84080ED935C8205B78B00D6BE9393D31CAAA294C57 | |||
| 7396 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7396.46710\Release\net472\de\Microsoft.Testing.Platform.resources.dll | executable | |
MD5:2443E724805DCEF0D9285BA97CF68655 | SHA256:70BF90191BF466A2C9AD272F7C23942AD880E898D95B37D5AECB4D14D9C0A44E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7316 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7316 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7316 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |