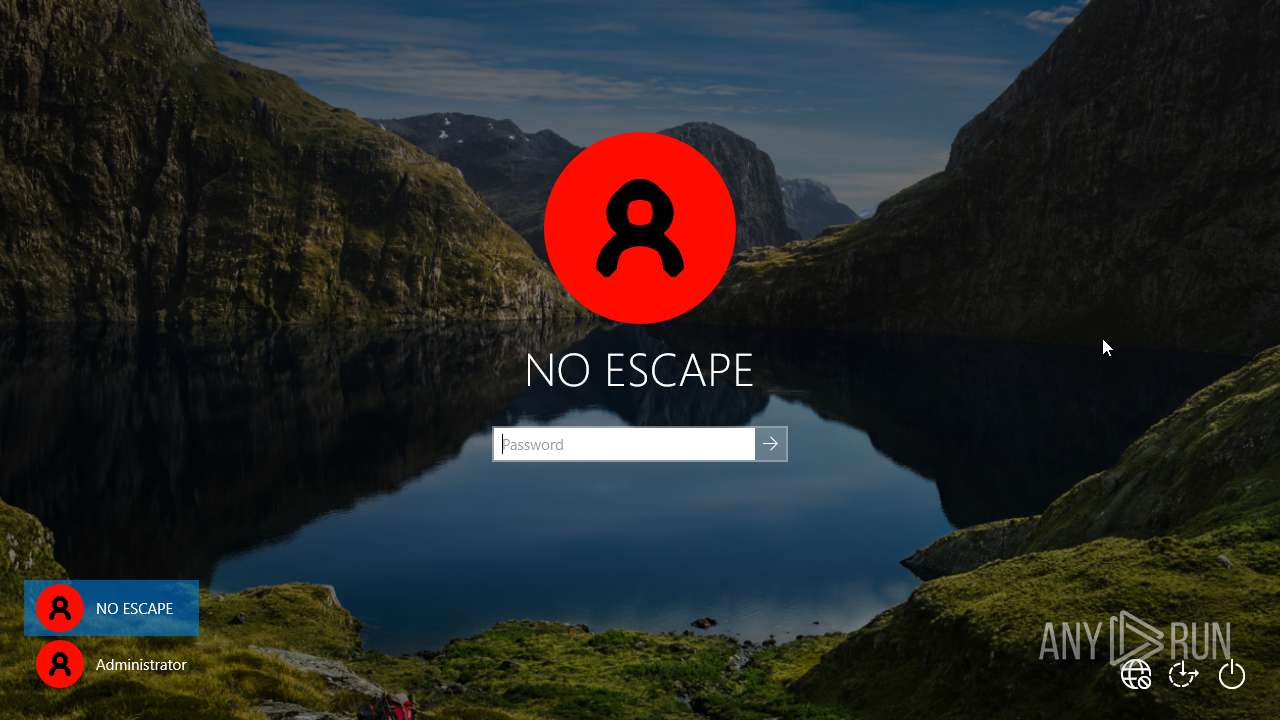
| File name: | NoEscape.exe |
| Full analysis: | https://app.any.run/tasks/18f8033a-751b-4b6d-a888-c0e89f9930ed |
| Verdict: | Malicious activity |
| Analysis date: | August 02, 2024, 16:33:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CDBB54A3EC888C3EAC84DEAA408F7B8A |
| SHA1: | 4478842748DB03E2E3879AC6A3854A82E30C845D |
| SHA256: | CCCC326ADF56026FA3E5EFBA505A6F51C091D7362B8CD68B322D301300AA6615 |
| SSDEEP: | 49152:SigiRtuTAxKnclWLopyfk9ejwB63M1GbY5ivUNOzgRpRAZ0CWIUGlcja+gXllDQc:cdwDWuj0QNkZ |
MALICIOUS
Drops the executable file immediately after the start
- NoEscape.exe (PID: 6388)
UAC/LUA settings modification
- NoEscape.exe (PID: 6388)
Changes the login/logoff helper path in the registry
- NoEscape.exe (PID: 6388)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 6948)
- net.exe (PID: 7164)
SUSPICIOUS
Executable content was dropped or overwritten
- NoEscape.exe (PID: 6388)
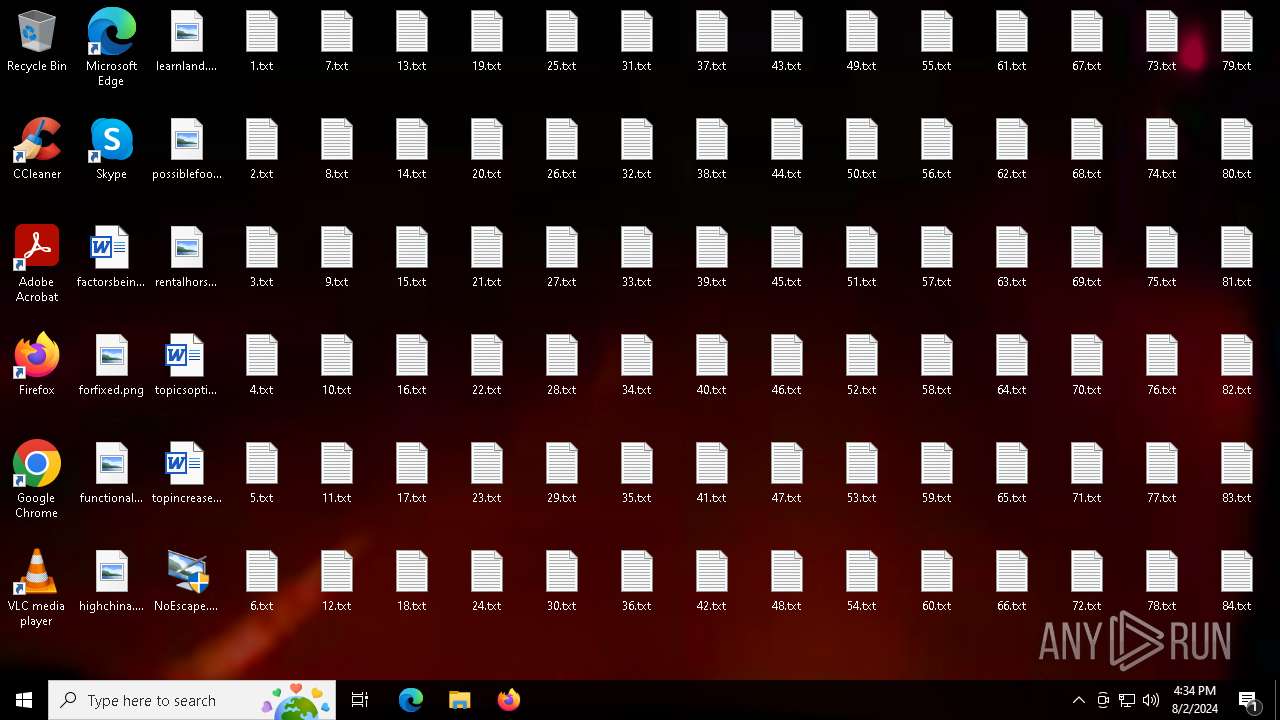
Creates file in the systems drive root
- NoEscape.exe (PID: 6388)
- cmd.exe (PID: 6948)
- attrib.exe (PID: 7100)
- attrib.exe (PID: 7132)
- xcopy.exe (PID: 4276)
- xcopy.exe (PID: 4404)
Reads security settings of Internet Explorer
- NoEscape.exe (PID: 6388)
- ShellExperienceHost.exe (PID: 7052)
Reads the date of Windows installation
- NoEscape.exe (PID: 6388)
Starts CMD.EXE for commands execution
- NoEscape.exe (PID: 6388)
Executing commands from a ".bat" file
- NoEscape.exe (PID: 6388)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6948)
Uses WMIC.EXE to obtain user accounts information
- cmd.exe (PID: 6948)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 6948)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6948)
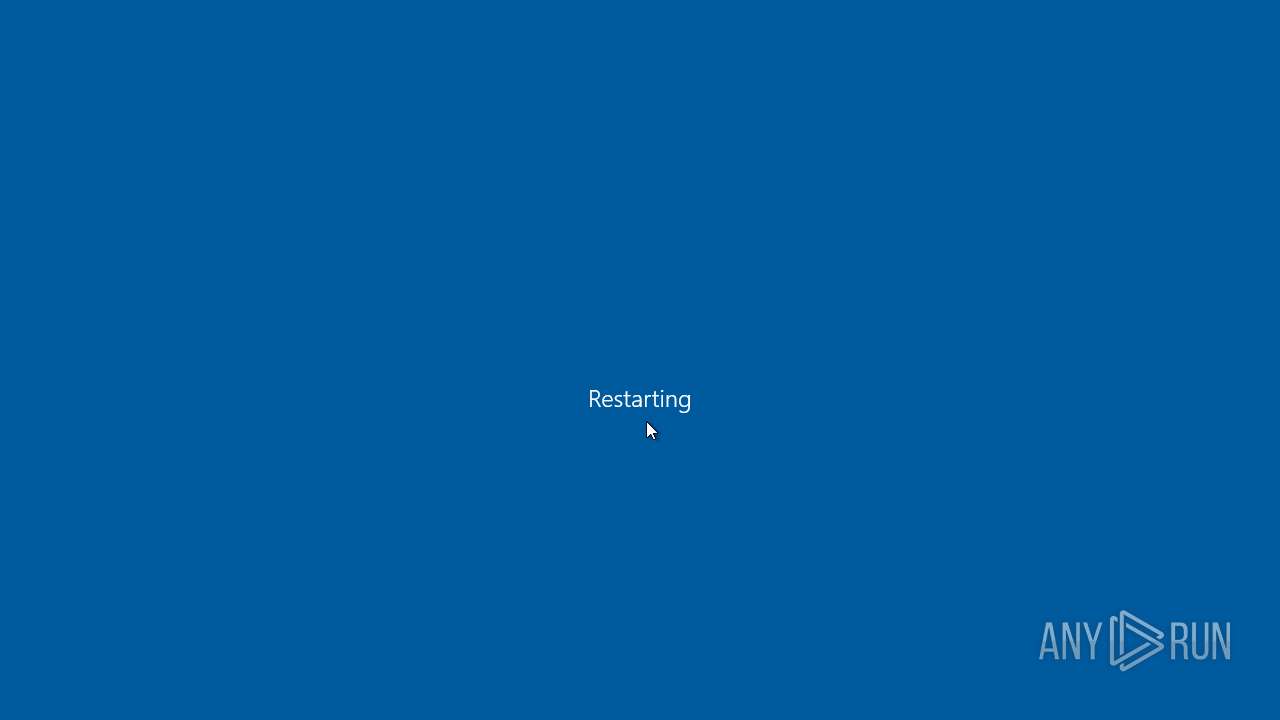
The system shut down or reboot
- cmd.exe (PID: 6948)
INFO
Checks supported languages
- NoEscape.exe (PID: 6388)
- ShellExperienceHost.exe (PID: 7052)
Reads the computer name
- NoEscape.exe (PID: 6388)
- ShellExperienceHost.exe (PID: 7052)
Process checks computer location settings
- NoEscape.exe (PID: 6388)
Reads the time zone
- net1.exe (PID: 6208)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6268)
Creates files in the program directory
- xcopy.exe (PID: 4276)
- xcopy.exe (PID: 4404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:01:28 12:19:44+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.34 |
| CodeSize: | 19456 |
| InitializedDataSize: | 1044480 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4f1c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
138
Monitored processes
16
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2628 | regedit -s C:\Windows\System32\hello.reg | C:\Windows\SysWOW64\regedit.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3076 | shutdown /t 0 /r | C:\Windows\SysWOW64\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4276 | xcopy *.png "C:\ProgramData\Microsoft\User Account Pictures\" | C:\Windows\SysWOW64\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4404 | xcopy *.bmp "C:\ProgramData\Microsoft\User Account Pictures\" | C:\Windows\SysWOW64\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5900 | takeown /f "C:\ProgramData\Microsoft\User Account Pictures" /r /d y | C:\Windows\SysWOW64\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6016 | regedit /s C:\Windows\System32\hello.reg | C:\Windows\SysWOW64\regedit.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6208 | C:\WINDOWS\system32\net1 user admin death | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6268 | wmic useraccount where name='admin' rename 'NO ESCAPE' | C:\Windows\SysWOW64\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6328 | "C:\Users\admin\Desktop\NoEscape.exe" | C:\Users\admin\Desktop\NoEscape.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6388 | "C:\Users\admin\Desktop\NoEscape.exe" | C:\Users\admin\Desktop\NoEscape.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
Total events
3 711
Read events
3 696
Write events
15
Delete events
0
Modification events
| (PID) Process: | (6388) NoEscape.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Userinit |
Value: C:\Windows\system32\userinit.exe,C:\Windows\System32\winnt32.exe | |||
| (PID) Process: | (6388) NoEscape.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (6388) NoEscape.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop |
| Operation: | write | Name: | NoChangingWallPaper |
Value: 1 | |||
| (PID) Process: | (6388) NoEscape.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | AutoColorization |
Value: 1 | |||
| (PID) Process: | (6388) NoEscape.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | UseDefaultTile |
Value: 1 | |||
| (PID) Process: | (6388) NoEscape.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6388) NoEscape.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6388) NoEscape.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6388) NoEscape.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7052) ShellExperienceHost.exe | Key: | \REGISTRY\A\{16919395-f2c1-553b-e212-801501e54823}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000C34517CDF9E4DA01 | |||
Executable files
1
Suspicious files
0
Text files
164
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6388 | NoEscape.exe | C:\user.png | image | |
MD5:96F17C361A25164E71716D5BB56CB3D8 | SHA256:1025314EF977B5D07041B8B73E4ADBEA779E5E06096C3C66BD1F06FBBBA7FD1C | |||
| 6388 | NoEscape.exe | C:\Users\Public\Desktop\2.txt | text | |
MD5:C0D310F6A15D755A8FB4F3F4F6183D58 | SHA256:B0E0514242246A453EAE64811BDB6DD50C69E056D0E9C1B9C674168BEFC51048 | |||
| 6388 | NoEscape.exe | C:\user-48.png | image | |
MD5:C7572C5706CA8D652D6B87787AE7F5B2 | SHA256:37C63EE5D26FB77F8E697FAEC3891673E40C449BF8411CFF806D852AE7506ADA | |||
| 6388 | NoEscape.exe | C:\user-40.png | image | |
MD5:D8E22EF10BD7AB65F56220D2845D6A94 | SHA256:B115A4548AD8E9C7CADB707A0FF79FCD55D9D900EEFA7A922CA50C85C4D3CA1D | |||
| 6388 | NoEscape.exe | C:\Windows\SysWOW64\winnt32.exe | executable | |
MD5:CDBB54A3EC888C3EAC84DEAA408F7B8A | SHA256:CCCC326ADF56026FA3E5EFBA505A6F51C091D7362B8CD68B322D301300AA6615 | |||
| 6388 | NoEscape.exe | C:\user.bmp | image | |
MD5:2AB3698B005B421349512142ED6B965E | SHA256:150E95DA6C1E09511241130DA0E376878F5E24E21C2A9DFE7FBCC1022660E29F | |||
| 6388 | NoEscape.exe | C:\Users\Public\Desktop\3.txt | text | |
MD5:C0D310F6A15D755A8FB4F3F4F6183D58 | SHA256:B0E0514242246A453EAE64811BDB6DD50C69E056D0E9C1B9C674168BEFC51048 | |||
| 6388 | NoEscape.exe | C:\user-32.png | image | |
MD5:5D572D54E293ACD90D5B8AD6036333DA | SHA256:4810DC6C101937DDE12D4581DE81E608EA144761D1307779DC6A256872330EDE | |||
| 6388 | NoEscape.exe | C:\hello.png | image | |
MD5:9E655CFD3D501F1ED01D6A2E0DB0E744 | SHA256:CF7B5334E06A13501821834CD1AEDB7C3306A543F7D8EC03D1F20BFAF9BED613 | |||
| 6388 | NoEscape.exe | C:\user-192.png | image | |
MD5:6BF949C62C5E9D07593BA5B604E36773 | SHA256:E54EA8405024F1FA72E470417059BDD186B0A3836F7D5E1C2C95C6003383912F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 52.168.117.169:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | GET | 200 | 52.109.76.240:443 | https://officeclient.microsoft.com/config16/?syslcid=1033&build=16.0.16026&crev=3 | unknown | xml | 171 Kb | unknown |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/officeclicktorun/16.0.16026.20140/Production/CC?&Clientid=%7b48BA7FDF-353C-4FE5-8D8F-9E31911A3891%7d&Application=officeclicktorun&Platform=win32&Version=16.0.16026.20140&MsoVersion=16.0.16026.20140&ProcessName=officeclicktorun.exe&Audience=Production&Build=ship&Architecture=x64&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bC83AE41D-F2D0-4B3E-BA34-A3F7F04FA747%7d&LabMachine=false | unknown | text | 334 Kb | unknown |
— | — | POST | 200 | 20.42.65.94:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4708 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4232 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4708 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
Threats
Process | Message |
|---|---|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|