| File name: | ChimeraInstaller.exe |
| Full analysis: | https://app.any.run/tasks/ced91c0c-2857-458b-9dc2-b4dc8889284e |
| Verdict: | Malicious activity |
| Analysis date: | December 11, 2023, 15:50:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 34CCA09CCC351EE6E292AC9F6674BC9E |
| SHA1: | BC3C97EF7325D0F5A9C0972C2319429D4C11F543 |
| SHA256: | CCC8EA653C0F5EF241D4F47AD757918C98F530B2072E234180E4A30A0D85A065 |
| SSDEEP: | 196608:bnoBjn6NrW719ck+i+fy9ikn7ZxUekUf5Jw9UmSbz/5/U9+4kfZ:Et6NK7Oy9iHJC5J/bz/5/M+4kZ |
MALICIOUS
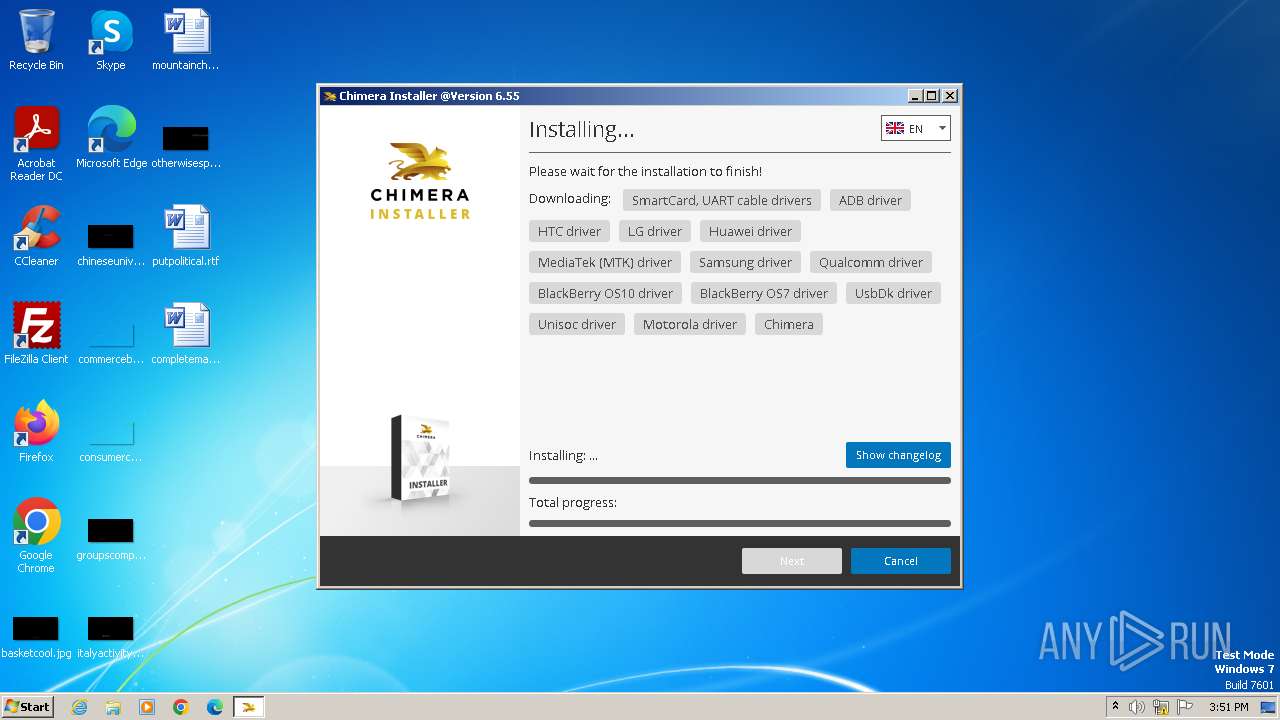
Drops the executable file immediately after the start
- ChimeraInstaller.exe (PID: 1840)
- 1228d68c662bc087f761f82eb76af633e7c02686.exe (PID: 240)
- irsetup.exe (PID: 1276)
- drvinst.exe (PID: 3296)
- dpinst.exe (PID: 3116)
- drvinst.exe (PID: 1004)
- dpinst.exe (PID: 4080)
- dpinst.exe (PID: 2548)
- a6013bbd273450b4838da21a135973eb8f41b332.exe (PID: 1064)
- irsetup.exe (PID: 3516)
- drvinst.exe (PID: 3972)
Creates a writable file in the system directory
- drvinst.exe (PID: 1004)
- drvinst.exe (PID: 3156)
- drvinst.exe (PID: 3972)
- drvinst.exe (PID: 3296)
SUSPICIOUS
Reads the Internet Settings
- 1228d68c662bc087f761f82eb76af633e7c02686.exe (PID: 240)
- irsetup.exe (PID: 1276)
- a6013bbd273450b4838da21a135973eb8f41b332.exe (PID: 1064)
Process drops legitimate windows executable
- irsetup.exe (PID: 1276)
- dpinst.exe (PID: 2548)
- drvinst.exe (PID: 3296)
- dpinst.exe (PID: 3116)
- drvinst.exe (PID: 1004)
- dpinst.exe (PID: 4080)
- irsetup.exe (PID: 3516)
- drvinst.exe (PID: 3972)
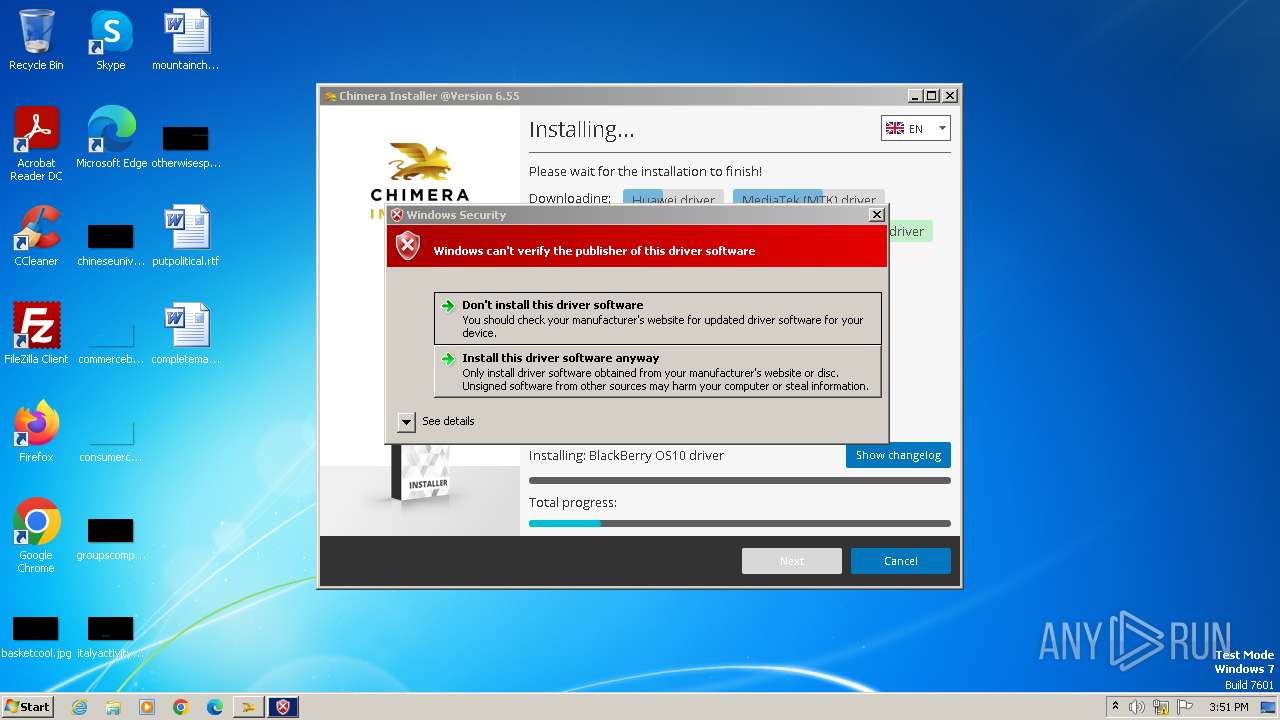
Drops a system driver (possible attempt to evade defenses)
- irsetup.exe (PID: 1276)
- dpinst.exe (PID: 2548)
- drvinst.exe (PID: 3296)
- dpinst.exe (PID: 3116)
- drvinst.exe (PID: 1004)
- dpinst.exe (PID: 4080)
- irsetup.exe (PID: 3516)
- drvinst.exe (PID: 3972)
Reads the Windows owner or organization settings
- irsetup.exe (PID: 1276)
- irsetup.exe (PID: 3516)
Creates files in the driver directory
- drvinst.exe (PID: 3296)
- drvinst.exe (PID: 1004)
- drvinst.exe (PID: 3156)
- drvinst.exe (PID: 3972)
Checks Windows Trust Settings
- drvinst.exe (PID: 3296)
- drvinst.exe (PID: 1004)
- drvinst.exe (PID: 3156)
- drvinst.exe (PID: 3972)
Executes as Windows Service
- VSSVC.exe (PID: 3928)
Searches for installed software
- irsetup.exe (PID: 3516)
- dllhost.exe (PID: 3596)
INFO
Reads the computer name
- ChimeraInstaller.exe (PID: 1840)
- 1228d68c662bc087f761f82eb76af633e7c02686.exe (PID: 240)
- irsetup.exe (PID: 1276)
- dpinst.exe (PID: 2548)
- drvinst.exe (PID: 3296)
- dpinst.exe (PID: 3116)
- drvinst.exe (PID: 1004)
- dpinst.exe (PID: 4080)
- drvinst.exe (PID: 3156)
- drvinst.exe (PID: 3972)
- a6013bbd273450b4838da21a135973eb8f41b332.exe (PID: 1064)
- irsetup.exe (PID: 3516)
Checks supported languages
- ChimeraInstaller.exe (PID: 1840)
- 1228d68c662bc087f761f82eb76af633e7c02686.exe (PID: 240)
- irsetup.exe (PID: 1276)
- dpinst.exe (PID: 2548)
- drvinst.exe (PID: 3296)
- dpinst.exe (PID: 3116)
- drvinst.exe (PID: 1004)
- dpinst.exe (PID: 4080)
- drvinst.exe (PID: 3156)
- drvinst.exe (PID: 3972)
- a6013bbd273450b4838da21a135973eb8f41b332.exe (PID: 1064)
- irsetup.exe (PID: 3516)
Creates files or folders in the user directory
- ChimeraInstaller.exe (PID: 1840)
Reads the machine GUID from the registry
- ChimeraInstaller.exe (PID: 1840)
- dpinst.exe (PID: 2548)
- drvinst.exe (PID: 3296)
- dpinst.exe (PID: 3116)
- drvinst.exe (PID: 1004)
- dpinst.exe (PID: 4080)
- drvinst.exe (PID: 3156)
- drvinst.exe (PID: 3972)
- irsetup.exe (PID: 3516)
Creates files in the program directory
- ChimeraInstaller.exe (PID: 1840)
Create files in a temporary directory
- ChimeraInstaller.exe (PID: 1840)
- 1228d68c662bc087f761f82eb76af633e7c02686.exe (PID: 240)
- irsetup.exe (PID: 1276)
- dpinst.exe (PID: 2548)
- dpinst.exe (PID: 3116)
- dpinst.exe (PID: 4080)
- a6013bbd273450b4838da21a135973eb8f41b332.exe (PID: 1064)
- irsetup.exe (PID: 3516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:03:26 15:01:01+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 7864320 |
| InitializedDataSize: | 86016 |
| UninitializedDataSize: | 20398080 |
| EntryPoint: | 0x1af3be0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.55.1457.0 |
| ProductVersionNumber: | 6.55.1457.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Euroserver Sro. |
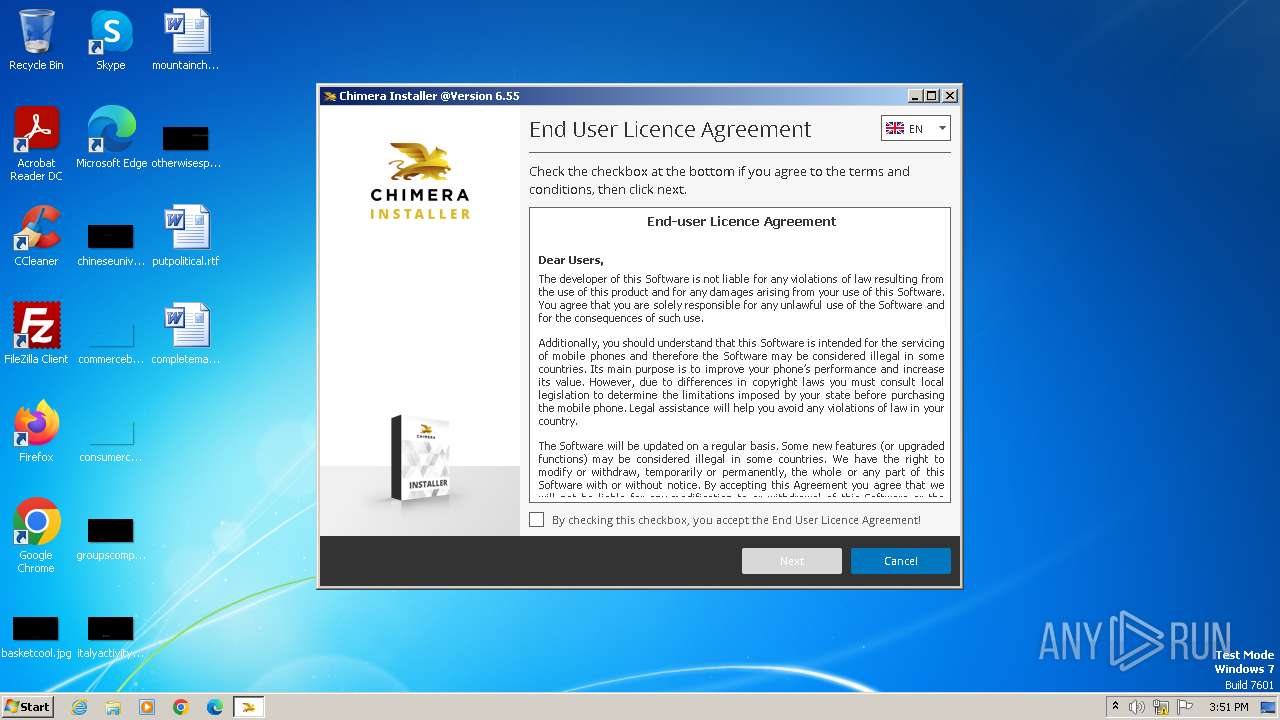
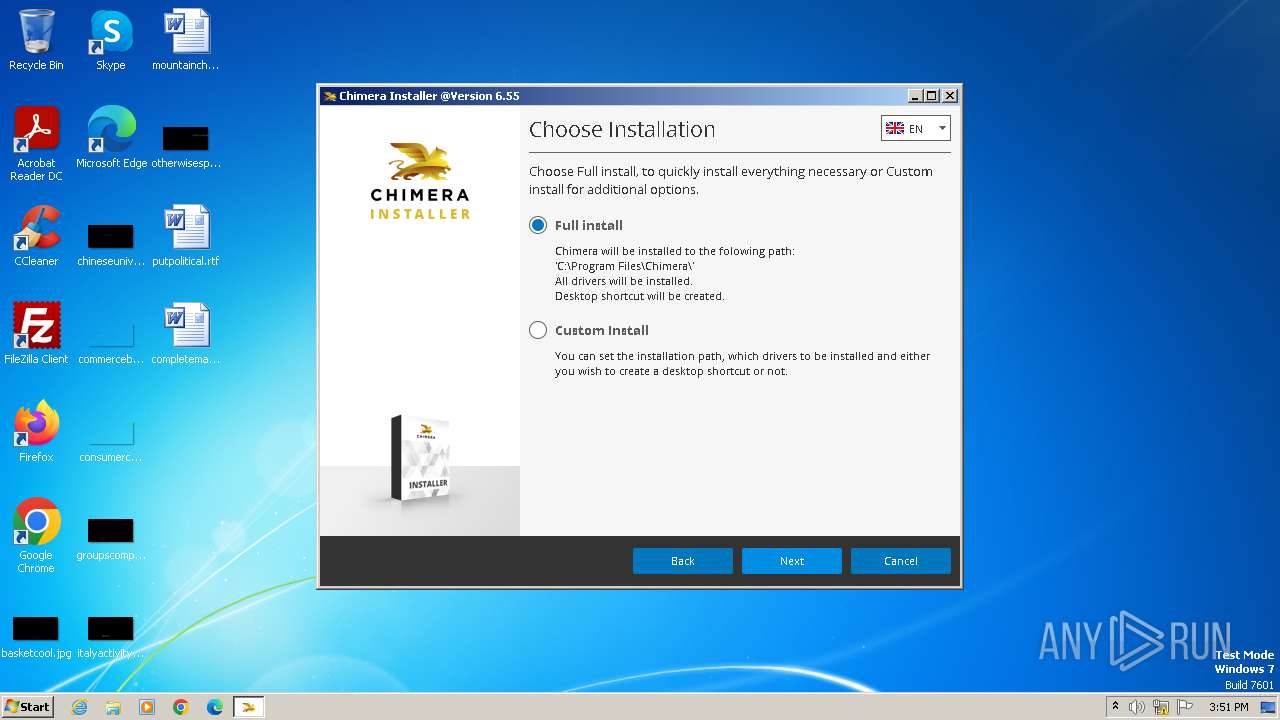
| FileDescription: | Chimera mobile tool installer |
| InternalName: | chimeraInstaller |
| LegalCopyright: | Copyright (C) 2016 Euroserver Sro. |
| OriginalFileName: | ChimeraInstaller.exe |
| ProductName: | Chimera Installer |
| FileVersion: | 6, 55, 1457, 0 |
Total processes
82
Monitored processes
43
Malicious processes
13
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\Chimera\Drivers\1228d68c662bc087f761f82eb76af633e7c02686.exe" | C:\Program Files\Chimera\Drivers\1228d68c662bc087f761f82eb76af633e7c02686.exe | — | ChimeraInstaller.exe | |||||||||||
User: admin Company: Euro-Server s.r.o. Integrity Level: HIGH Description: ChimeraTool OS10 driver installer Exit code: 0 Version: 1.2.2.5 Modules
| |||||||||||||||
| 296 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe" /SW /D /U "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\ssuddmgr.inf" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 | |||||||||||||||
| 564 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe" /SW /D /U "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\ssudserd.inf" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 | |||||||||||||||
| 732 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe" /SW /D /U "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\ssudmdm.inf" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 | |||||||||||||||
| 880 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 10 Global\{0c27bbcb-2bf0-557a-adbd-f864bcf2f36f} Global\{674b4db0-9f3a-24b5-bcf2-f36f526f076d} C:\Windows\System32\DriverStore\Temp\{529e9eef-6e75-5f3c-5f32-40650baf2769}\rimserial.inf C:\Windows\System32\DriverStore\Temp\{529e9eef-6e75-5f3c-5f32-40650baf2769}\RimSerial.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1004 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{05bdc259-be9e-7de3-fff7-77586bfe8715}\blackberryncm.inf" "0" "65572e653" "000004C0" "WinSta0\Default" "000004AC" "208" "c:\users\admin\appdata\local\temp\_ir_sf_temp_0\ncm_driver" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe" /SW /D /U "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\ssudeadb.inf" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 2147483648 Version: 2.1 | |||||||||||||||
| 1064 | "C:\Program Files\Chimera\Drivers\a6013bbd273450b4838da21a135973eb8f41b332.exe" | C:\Program Files\Chimera\Drivers\a6013bbd273450b4838da21a135973eb8f41b332.exe | — | ChimeraInstaller.exe | |||||||||||
User: admin Company: Euro-Server s.r.o. Integrity Level: HIGH Description: ChimeraTool Samsung driver installer Exit code: 0 Version: 1.2.2.5 Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe" /SW /F /SA /SE /LM | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 0 Version: 2.1 | |||||||||||||||
| 1276 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe" __IRAOFF:1810690 "__IRAFN:C:\Program Files\Chimera\Drivers\1228d68c662bc087f761f82eb76af633e7c02686.exe" "__IRCT:2" "__IRTSS:0" "__IRSID:S-1-5-21-1302019708-1500728564-335382590-1000" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | — | 1228d68c662bc087f761f82eb76af633e7c02686.exe | |||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: HIGH Description: Setup Application Exit code: 0 Version: 9.5.0.0 Modules
| |||||||||||||||
Total events
16 260
Read events
16 131
Write events
129
Delete events
0
Modification events
| (PID) Process: | (1840) ChimeraInstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (240) 1228d68c662bc087f761f82eb76af633e7c02686.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (240) 1228d68c662bc087f761f82eb76af633e7c02686.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (240) 1228d68c662bc087f761f82eb76af633e7c02686.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (240) 1228d68c662bc087f761f82eb76af633e7c02686.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1276) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1276) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1276) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1276) irsetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2548) dpinst.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
106
Suspicious files
251
Text files
4
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\9764a0cf7398d05f1f046dc0c358adf765f28657.jsc | binary | |
MD5:96678B8BD1C4DDF39AD6F67980621EAB | SHA256:441C9DA67C9316D0F850C1AE534AA9BE152B9AFCE3BB9FC8180BDD84B55904C9 | |||
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\116d9014284e9a310aa20bd041d1b09d87828908.qmlc | binary | |
MD5:DD3DAEA8464D0970AA2ED70DE8535F24 | SHA256:5384131CC87492425AFF85DF3CE99F450FA5C44A14FD46B383F2F0ED504FC748 | |||
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\170ac466fb099e5966c88f98dc00006766876aac.qmlc | binary | |
MD5:1512791F9E73EC2B4B10400473D52744 | SHA256:77B012A49A6B1AC2AC8931AA97B59CA6E227B63B85268F4B60A259CE10C659B2 | |||
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\619572f4c59c16656b0e91e66eead08b0e301f06.jsc.Hp1840 | binary | |
MD5:850B4391D84AC1E95C44A45E9F458A03 | SHA256:A4530E9DEE2CB7DFA4FA22321624FC798BD7F377020232F38E3CE3A6F6E01B1F | |||
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\9779a7429fce2510e47ce1a9b32b01bfc446a599.jsc | binary | |
MD5:D54FF5C7548719A6A6C27887E2C9AC0D | SHA256:BB5BD68D79D63AA896E63492DCED9DDA6BEC6E3FFA20CC6CF0494654AFB2F4B7 | |||
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\9764a0cf7398d05f1f046dc0c358adf765f28657.jsc.Ya1840 | binary | |
MD5:96678B8BD1C4DDF39AD6F67980621EAB | SHA256:441C9DA67C9316D0F850C1AE534AA9BE152B9AFCE3BB9FC8180BDD84B55904C9 | |||
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\9779a7429fce2510e47ce1a9b32b01bfc446a599.jsc.em1840 | binary | |
MD5:D54FF5C7548719A6A6C27887E2C9AC0D | SHA256:BB5BD68D79D63AA896E63492DCED9DDA6BEC6E3FFA20CC6CF0494654AFB2F4B7 | |||
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\e4ef80837691d5be54fee0047ddf51951a963467.jsc | binary | |
MD5:E3F5DDF4C0D9BC5BC5F52D31C6D3B3E7 | SHA256:B80567D9C44534F1C8D469EF7DA280B2B61B6A281729423280FB237F48B6C1DA | |||
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\7225451fcacc3b7ad282a5fc4489dd7ad6f3e571.qmlc.if1840 | binary | |
MD5:8C7C4F11825DC74099EC614AA9666C27 | SHA256:1D0183116A722A574E18FB84E31DDA1A488AD4A6E16B2599AFF3B4AC24B6F745 | |||
| 1840 | ChimeraInstaller.exe | C:\Users\admin\AppData\Local\ChimeraInstaller\cache\qmlcache\60275f5f6e33c334fc27395521c9281b31d7c5ab.qmlc.cr1840 | binary | |
MD5:23E104189383168335A59B1B7977B86B | SHA256:02850E7D904B9610E78F3B13349868DA27CECDAFB338A632702DE517DCDD4155 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
27
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1840 | ChimeraInstaller.exe | 104.20.78.245:443 | chimeratool.com | CLOUDFLARENET | — | shared |
1840 | ChimeraInstaller.exe | 104.18.14.248:443 | data.chimeratool.com | CLOUDFLARENET | — | unknown |
1840 | ChimeraInstaller.exe | 104.18.15.248:443 | data.chimeratool.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
chimeratool.com |
| whitelisted |
data.chimeratool.com |
| unknown |
Threats
Process | Message |
|---|---|
ChimeraInstaller.exe | Failed to load libEGL (The specified module could not be found.)
|
ChimeraInstaller.exe | QWindowsEGLStaticContext::doTest: Failed to load and resolve libEGL functions
|