| File name: | 11 FBI Tools.rar |
| Full analysis: | https://app.any.run/tasks/05c2563f-a98a-452e-9149-06e17dc91df2 |
| Verdict: | Malicious activity |
| Analysis date: | July 28, 2020, 23:21:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 9001B4A355E92C251788856E195B1354 |
| SHA1: | 6CD5D32B9B835F681AE1B2CD48DCB1C9454CBD37 |
| SHA256: | CCB375E84FC672486EA55AAADF7A33988C57845CE9AC23443D9E3F01D6C5CBA3 |
| SSDEEP: | 196608:80mEn7Z5RyAe2t1aLzXxVpKMCmaIPMgUsrxrg:8FwZ5rf1qLcZ3SZg |
MALICIOUS
Application was dropped or rewritten from another process
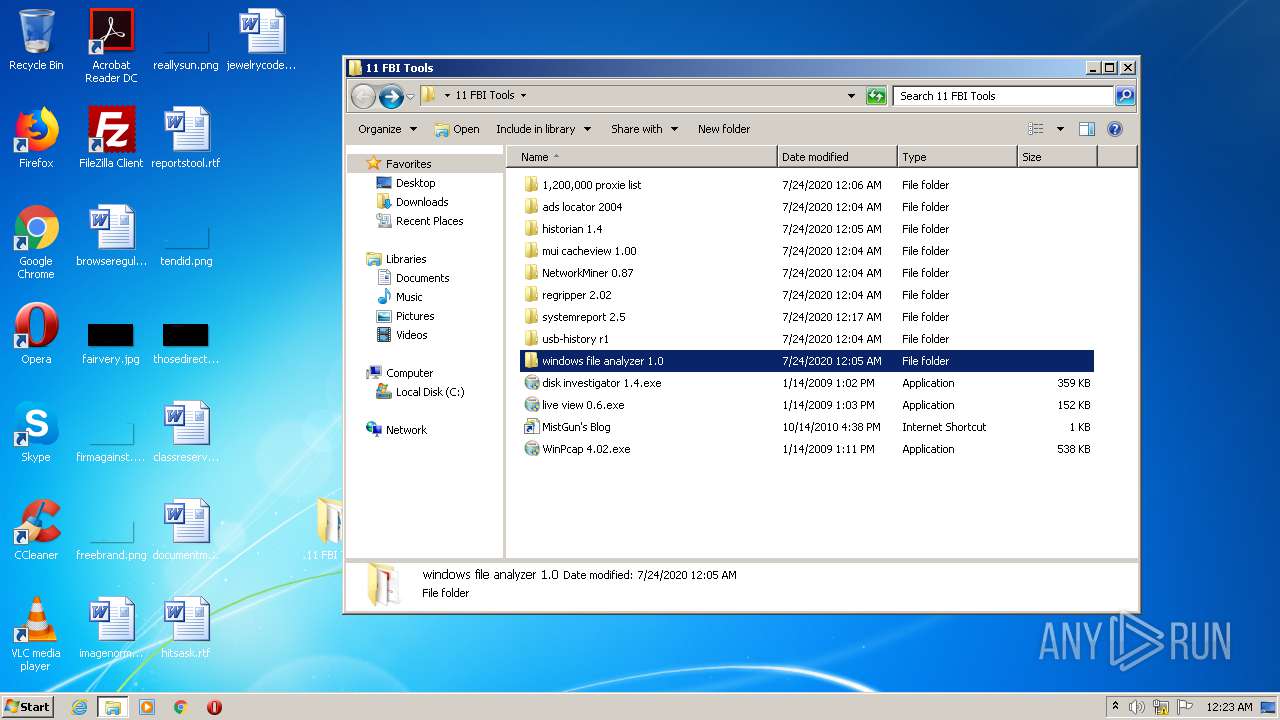
- adsdir.exe (PID: 2508)
- ADSLocator.exe (PID: 2252)
- Historian.exe (PID: 1112)
- MUICacheView.exe (PID: 2044)
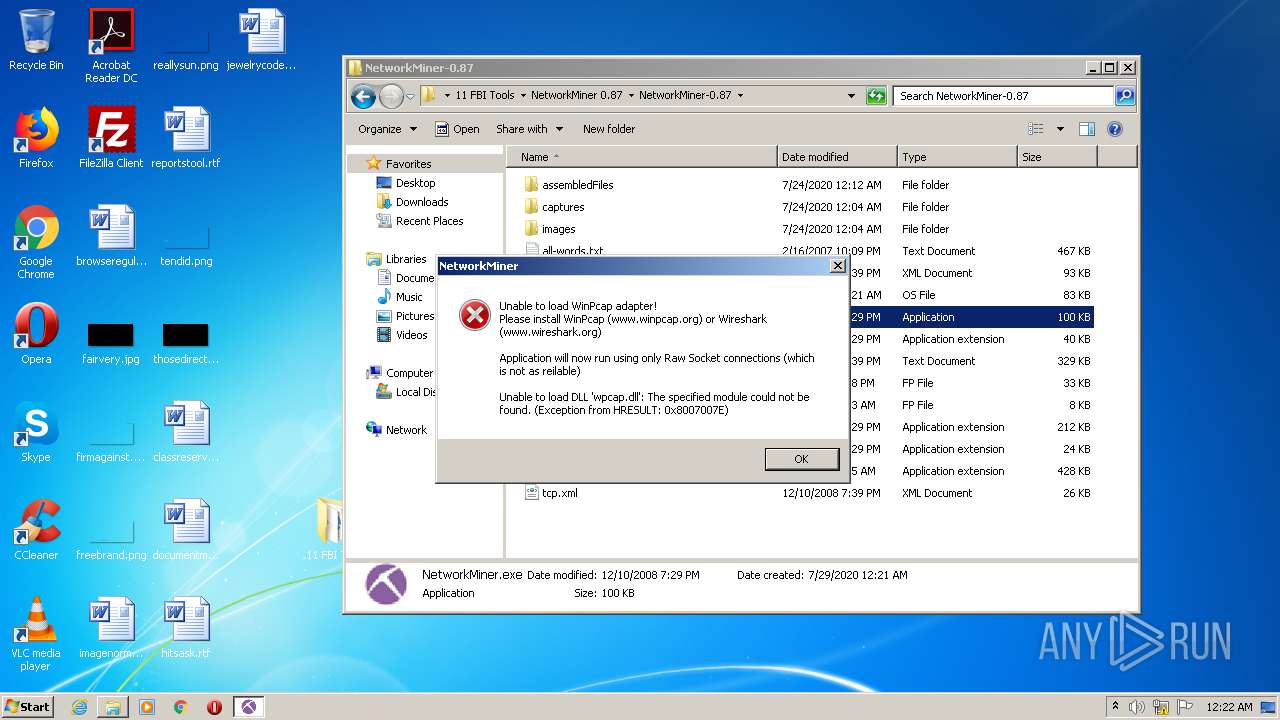
- NetworkMiner.exe (PID: 3660)
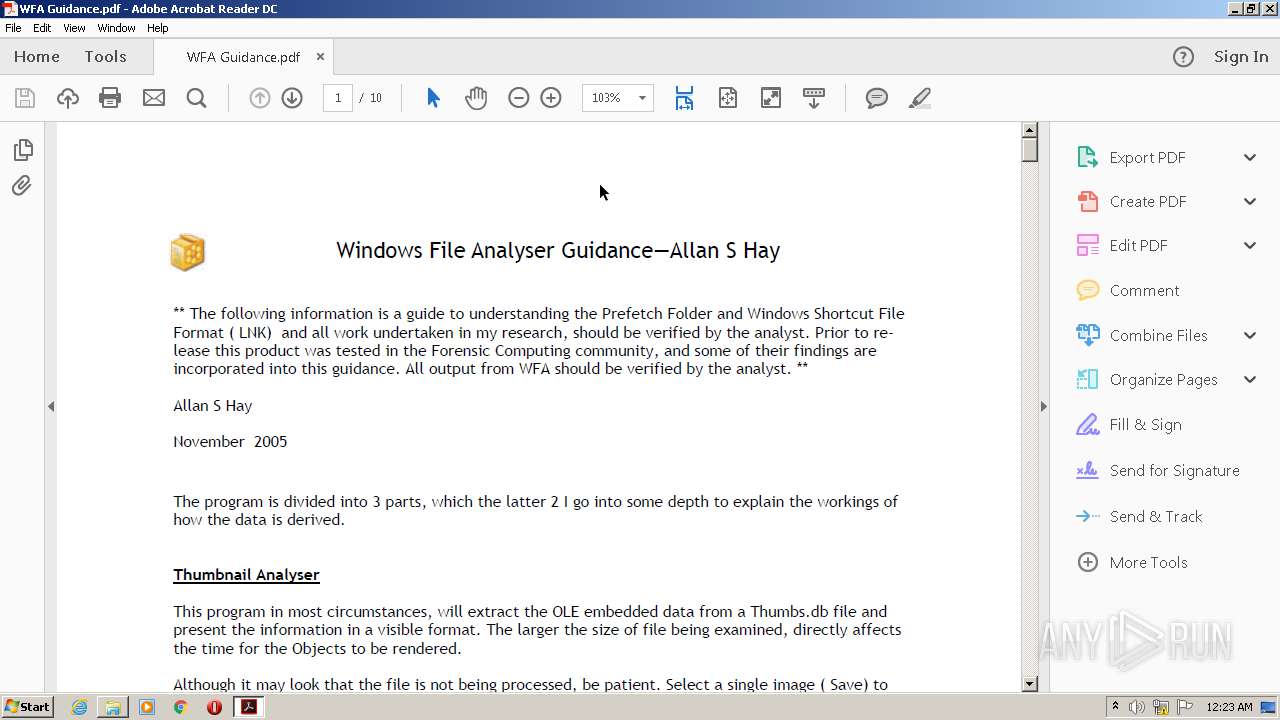
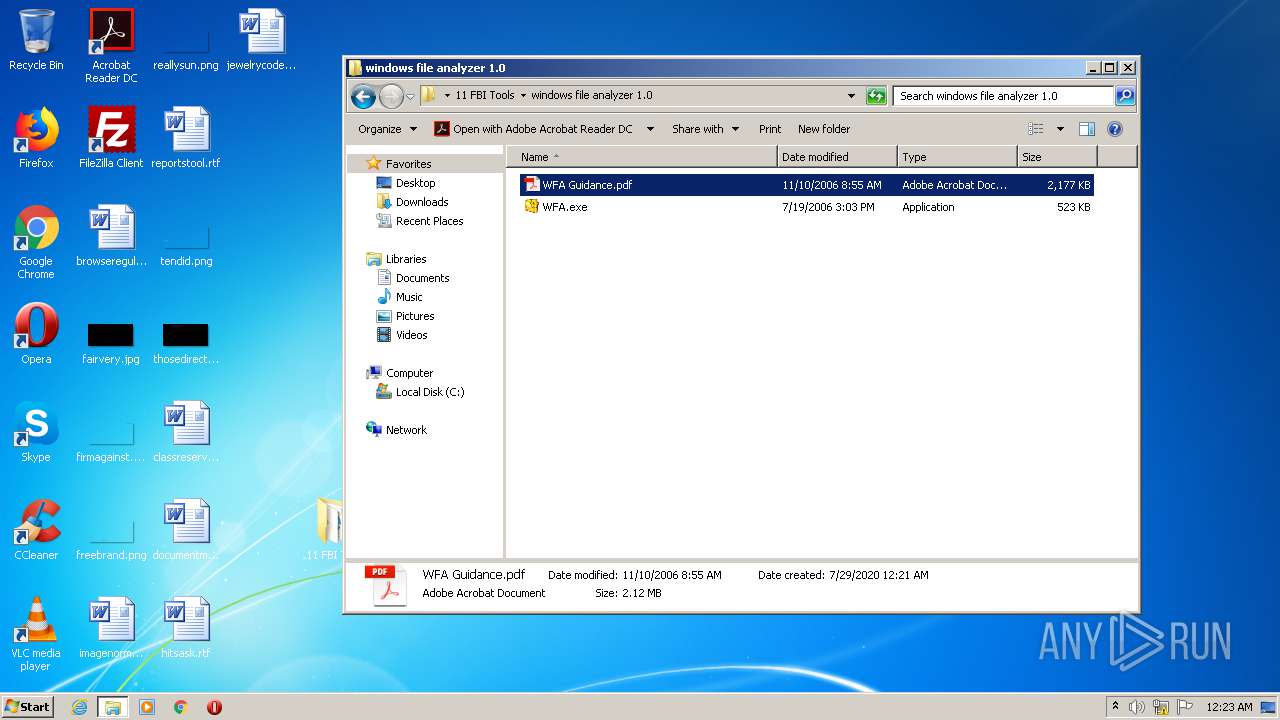
- WFA.exe (PID: 3652)
- OSWin.exe (PID: 4000)
- AutoRun.exe (PID: 2824)
- usbHistory.exe (PID: 2912)
- BIOS.exe (PID: 2912)
- CPU.exe (PID: 1072)
- rip.exe (PID: 3212)
Loads dropped or rewritten executable
- Historian.exe (PID: 1112)
- NetworkMiner.exe (PID: 3660)
- SearchProtocolHost.exe (PID: 3568)
- rip.exe (PID: 3212)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2416)
Creates executable files which already exist in Windows
- WinRAR.exe (PID: 2416)
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 3844)
INFO
Manual execution by user
- ADSLocator.exe (PID: 2252)
- Historian.exe (PID: 1112)
- adsdir.exe (PID: 2508)
- taskmgr.exe (PID: 3248)
- MUICacheView.exe (PID: 2044)
- NetworkMiner.exe (PID: 3660)
- WFA.exe (PID: 3652)
- AcroRd32.exe (PID: 3844)
- usbHistory.exe (PID: 2912)
- BIOS.exe (PID: 2912)
- CPU.exe (PID: 1072)
- AutoRun.exe (PID: 2824)
- OSWin.exe (PID: 4000)
- cmd.exe (PID: 2492)
Application launched itself
- AcroRd32.exe (PID: 3844)
- RdrCEF.exe (PID: 3096)
Reads the hosts file
- RdrCEF.exe (PID: 3096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
71
Monitored processes
21
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 648 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\Desktop\11 FBI Tools\windows file analyzer 1.0\WFA Guidance.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\Desktop\11 FBI Tools\systemreport 2.5\CPU.exe" | C:\Users\admin\Desktop\11 FBI Tools\systemreport 2.5\CPU.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1112 | "C:\Users\admin\Desktop\11 FBI Tools\historian 1.4\Historian.exe" | C:\Users\admin\Desktop\11 FBI Tools\historian 1.4\Historian.exe | — | explorer.exe | |||||||||||
User: admin Company: Werner Rumpeltesz Integrity Level: MEDIUM Description: Historian Exit code: 0 Version: 1.4.1.0 Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\Desktop\11 FBI Tools\mui cacheview 1.00\MUICacheView.exe" | C:\Users\admin\Desktop\11 FBI Tools\mui cacheview 1.00\MUICacheView.exe | — | explorer.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: MUICacheView Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2252 | "C:\Users\admin\Desktop\11 FBI Tools\ads locator 2004\ADSLocator.exe" | C:\Users\admin\Desktop\11 FBI Tools\ads locator 2004\ADSLocator.exe | explorer.exe | ||||||||||||
User: admin Company: Safer Networking Limited Integrity Level: MEDIUM Description: ADS alternate streams locator Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\11 FBI Tools.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
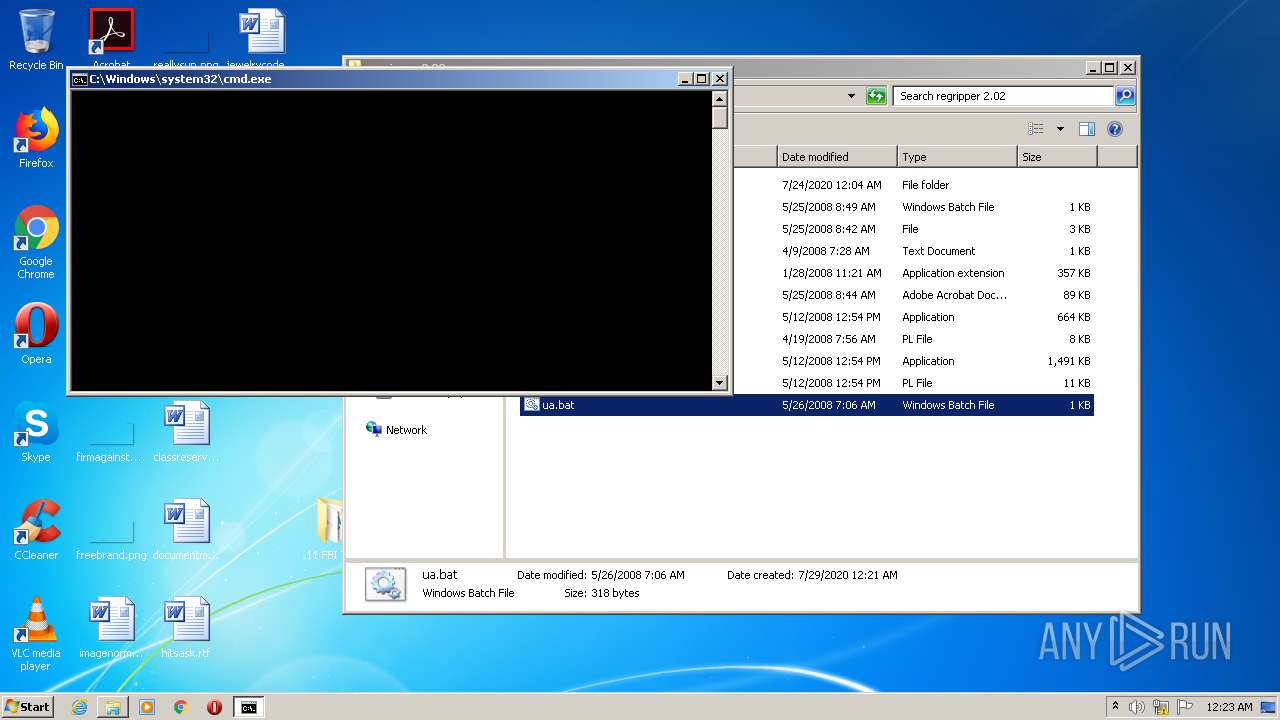
| 2492 | cmd /c ""C:\Users\admin\Desktop\11 FBI Tools\regripper 2.02\ua.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\Desktop\11 FBI Tools\ads locator 2004\adsdir.exe" | C:\Users\admin\Desktop\11 FBI Tools\ads locator 2004\adsdir.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2824 | "C:\Users\admin\Desktop\11 FBI Tools\systemreport 2.5\AutoRun.exe" | C:\Users\admin\Desktop\11 FBI Tools\systemreport 2.5\AutoRun.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2912 | "C:\Users\admin\Desktop\11 FBI Tools\usb-history r1\usbHistory.exe" | C:\Users\admin\Desktop\11 FBI Tools\usb-history r1\usbHistory.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 569
Read events
1 391
Write events
178
Delete events
0
Modification events
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\11 FBI Tools.rar | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-10046 |
Value: Internet Shortcut | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
41
Suspicious files
5
Text files
240
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\1,200,000 proxie list\1,200,000 Proxies.txt | — | |
MD5:— | SHA256:— | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\historian 1.4\Language\English_Templates\CSV table (semicolon)\GCCookie.format | text | |
MD5:169703C32372E952C9D75808D6AC7928 | SHA256:F34233455E371B2804680C03A336DE30047F11D02EAC1ED07473140F8504FACC | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\historian 1.4\Language\English_Templates\CSV table (semicolon)\MozDown.format | text | |
MD5:D4EC56AC8F8B8151F2CC854610FDF856 | SHA256:27F581BA10521873F477D31636D39E612AE1737CDED1D25B0A5915B28B246637 | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\historian 1.4\Historian.exe | executable | |
MD5:D8514EA411FC7F4CFBF5B7ECDA1F4B8F | SHA256:B50A3E9B293A31044277E75E409FE632A352D14FFB00125B912002D148A411EA | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\historian 1.4\Historian.ini | text | |
MD5:D4C5C4298A44936244ECA6A1F4F294A7 | SHA256:3D0F577EB6495908911AFBFB90355A7EA154C7D047FEF4DBFC5C68ABB02E16F6 | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\historian 1.4\Language\English_Templates\CSV table (semicolon)\MozCookie.format | text | |
MD5:BE0A0537226164B57AA0C6B3079F8CBD | SHA256:7E4080D5B5A239B4D95E2688260112AD6B989DE42FC1E378BBAC2A5B0B7DF01E | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\historian 1.4\Language\English_Templates\CSV table (semicolon)\MozFF3Cookie.format | text | |
MD5:4DB6905CB1679F9F55B93E6F1CF3F398 | SHA256:11F8FF65A5C591A7693B5ACA2EA7390CC318519CA7186E2F94A064D07CB6CF1F | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\historian 1.4\Language\English_Templates\CSV table (semicolon)\MozFF3Fav.format | text | |
MD5:38677377F37C6A9922DC5CCD517A4133 | SHA256:D54C40F2D13064B8A75E3E20FC3DC46CD04EDDB01F77234656A2507783CC6415 | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\historian 1.4\Language\English_Templates\CSV table (semicolon)\IECookie.format | text | |
MD5:ED4C2A306D16DC116D9BA092DDE43452 | SHA256:1429E7F48E95BA0E783F67D693109AEE338E925BE3DC26B34116D76D58E95088 | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2416.32922\11 FBI Tools\historian 1.4\Language\English_Templates\CSV table (semicolon)\GCHist.format | text | |
MD5:F55F3ECB74ABD63B1DC0765570FEA59A | SHA256:E7365132C8B7CADCA471028F446803FDB39D49D596054D518FEBC2EC79BBFF22 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
ADSLocator.exe | Initialization: pkMisc |