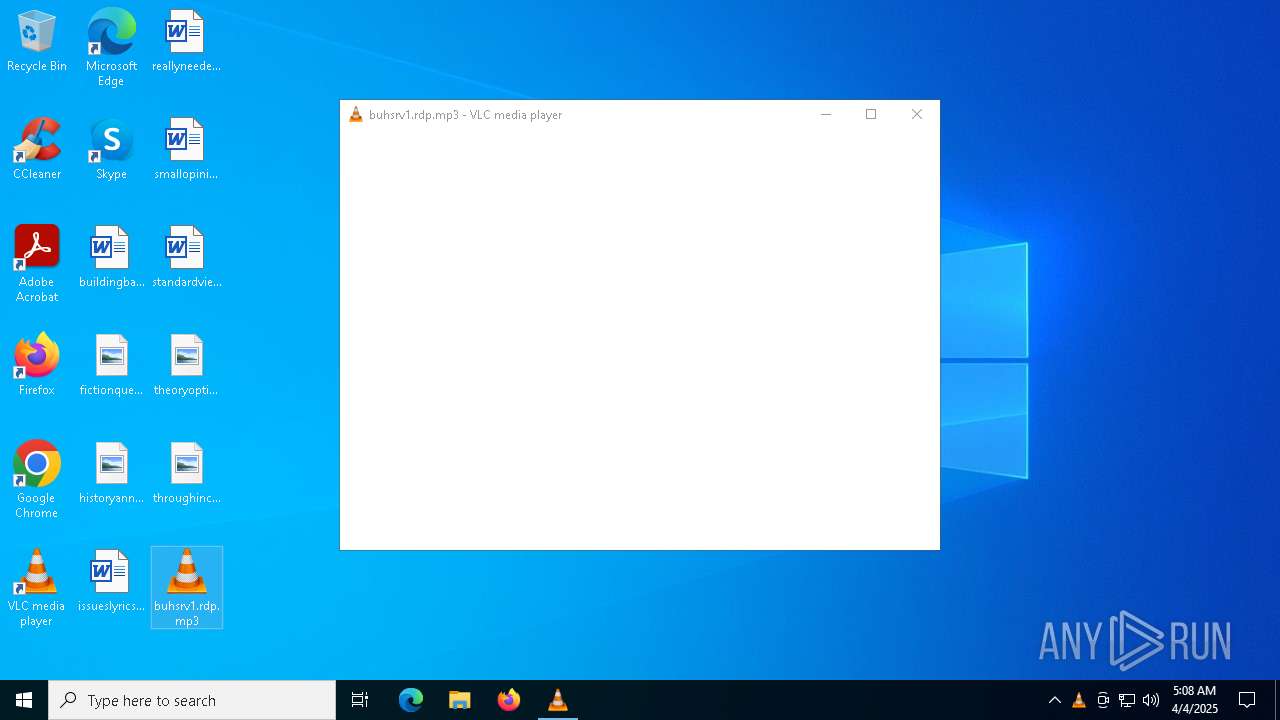
| File name: | buhsrv1.rdp |
| Full analysis: | https://app.any.run/tasks/41b3ffed-2d31-4a8f-9a7a-c77172b8b53b |
| Verdict: | Malicious activity |
| Analysis date: | April 04, 2025, 05:08:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-16, little-endian text, with very long lines (5074), with CRLF line terminators |
| MD5: | 95E6FD77AD7A0BFC8C3D1F3D2FD8A283 |
| SHA1: | 2418177DC2D64A85C99C93FAF9DF3D819E8DF153 |
| SHA256: | CCA25DB9EF9D7108AAD35BE9E394B268A561A78DD9B789E658000CDCAB271B4F |
| SSDEEP: | 192:Z0FMWRw31vLguo4rWl873jCIHFE1tGLl6nsCtF7F08oFC3ZAWLZ+65YxhHV:zWR4Uuo43mIlE3UcztpNoI3ZA2Wl |
MALICIOUS
Create files in the Startup directory
- mstsc.exe (PID: 6272)
Attempt to connect to SMB server
- System (PID: 4)
SMBSCAN has been detected (SURICATA)
- System (PID: 4)
SUSPICIOUS
Smart Card resource manager service initialization
- mstsc.exe (PID: 6272)
SMB connection has been detected (probably for file transfer)
- explorer.exe (PID: 5492)
Uses pipe srvsvc via SMB (transferring data)
- explorer.exe (PID: 5492)
Executable content was dropped or overwritten
- mstsc.exe (PID: 6272)
Potential Corporate Privacy Violation
- mstsc.exe (PID: 6272)
- System (PID: 4)
Reads the history of recent RDP connections
- mstsc.exe (PID: 6272)
INFO
Creates files or folders in the user directory
- mstsc.exe (PID: 6272)
- explorer.exe (PID: 5492)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- mstsc.exe (PID: 6272)
Reads the software policy settings
- mstsc.exe (PID: 6272)
Checks proxy server information
- explorer.exe (PID: 5492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rdp | | | Remote Desktop Connection Settings (Unicode) (99.1) |
|---|---|---|
| .txt | | | Text - UTF-16 (LE) encoded (0.5) |
| .mp3 | | | MP3 audio (0.2) |
Total processes
130
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4 | System | [System Process] | |||||||||||||
User: SYSTEM Integrity Level: SYSTEM | |||||||||||||||
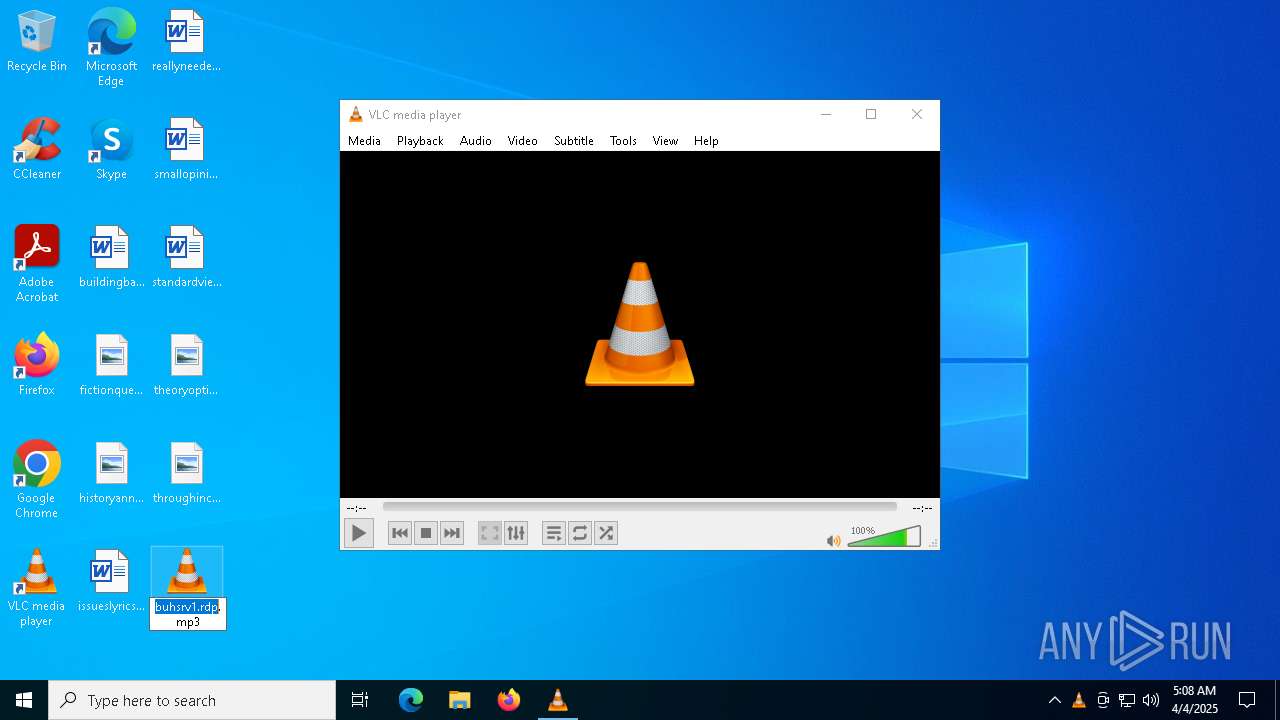
| 3300 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file C:\Users\admin\Desktop\buhsrv1.rdp.mp3 | C:\Program Files\VideoLAN\VLC\vlc.exe | — | explorer.exe | |||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 4812 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 5492 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
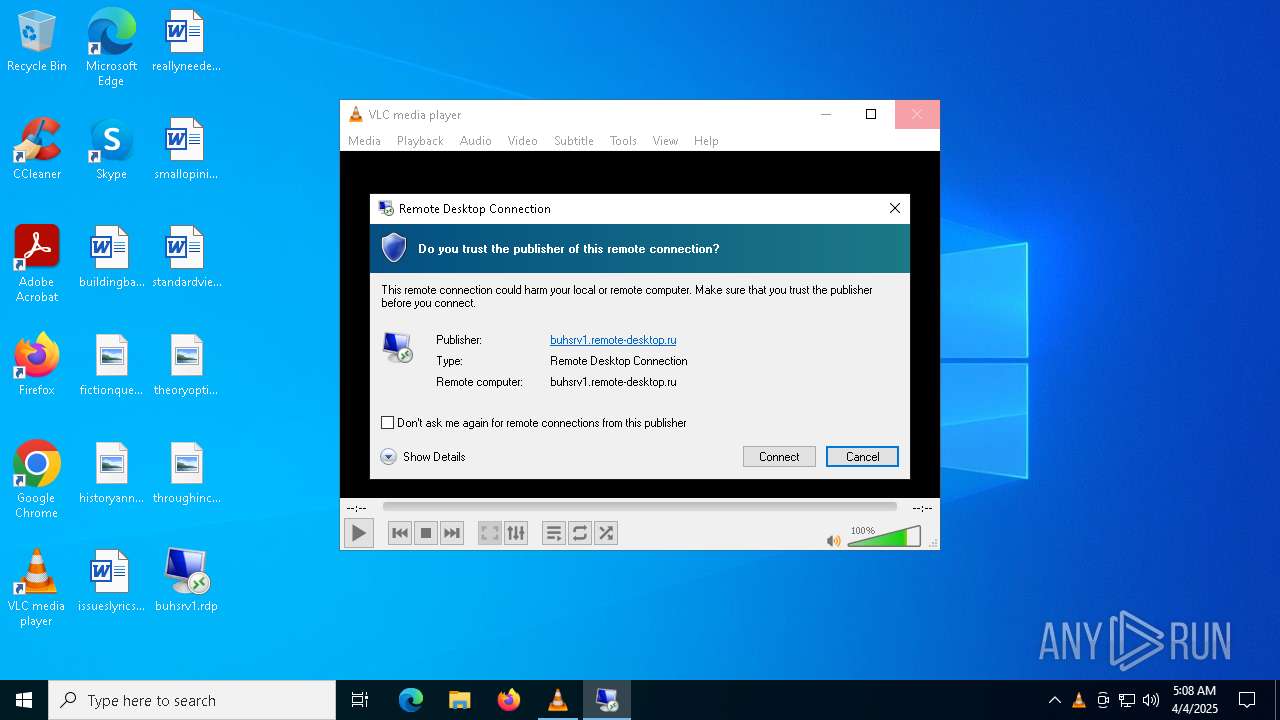
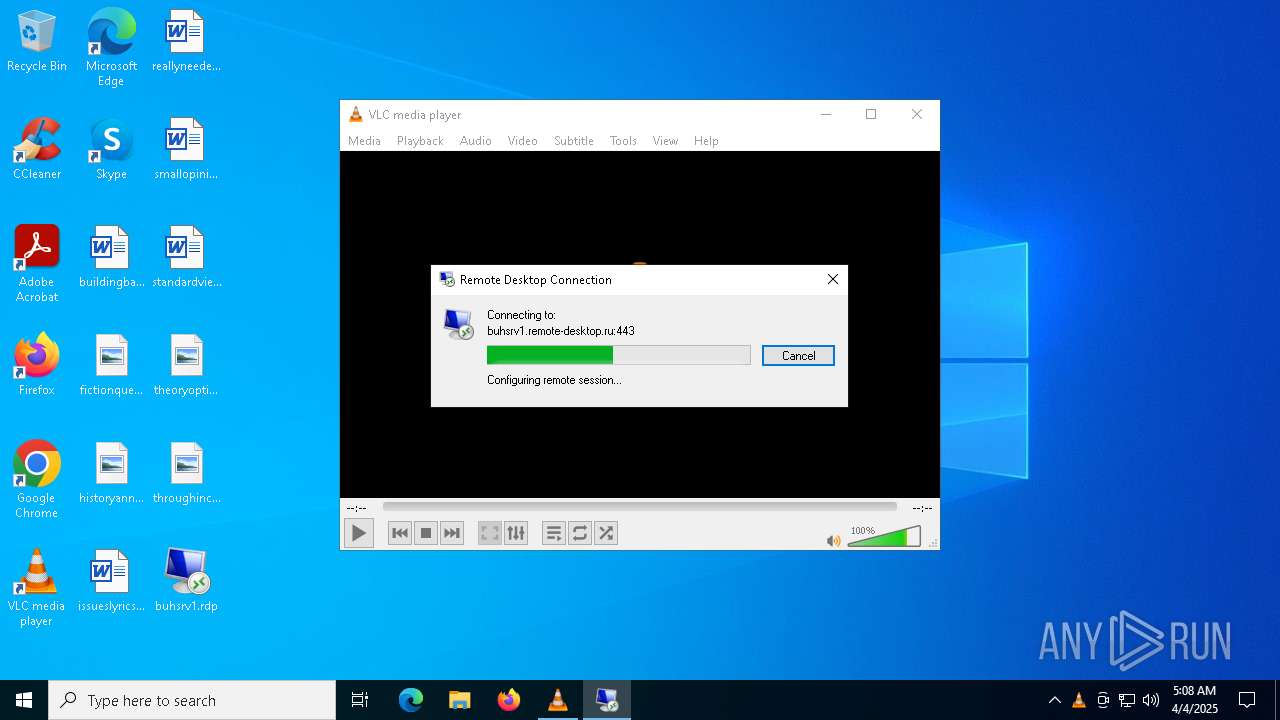
| 6272 | "mstsc.exe" "C:\Users\admin\Desktop\buhsrv1.rdp" | C:\Windows\System32\mstsc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Connection Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 132
Read events
8 074
Write events
35
Delete events
23
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010012000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000013000000000000006200750069006C00640069006E0067006200610064002E007200740066003E002000200000001800000000000000660069006300740069006F006E007100750065007300740069006F006E0073002E006A00700067003E002000200000001C0000000000000068006900730074006F007200790061006E006E006F0075006E00630065006D0065006E00740073002E006A00700067003E0020002000000014000000000000006900730073007500650073006C00790072006900630073002E007200740066003E0020002000000014000000000000007200650061006C006C0079006E00650065006400650064002E007200740066003E00200020000000140000000000000073006D0061006C006C006F00700069006E0069006F006E002E007200740066003E0020002000000014000000000000007300740061006E00640061007200640076006900650077002E007200740066003E0020002000000016000000000000007400680065006F00720079006F007000740069006F006E0061006C002E0070006E0067003E0020002000000015000000000000007400680072006F0075006700680069006E0063006500730074002E0070006E0067003E00200020000000130000000000000062007500680073007200760031002E007200640070002E006D00700033003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001200000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000000400000A0401100 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 3569EF6700000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000004400000044000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {C120DE80-FDE4-49F5-A713-E902EF062B8A} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 0100000000000000634F588E1FA5DB01 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000502D2 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:000000000009014C |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:000000000009014C |
| Operation: | delete key | Name: | (default) |
Value: | |||
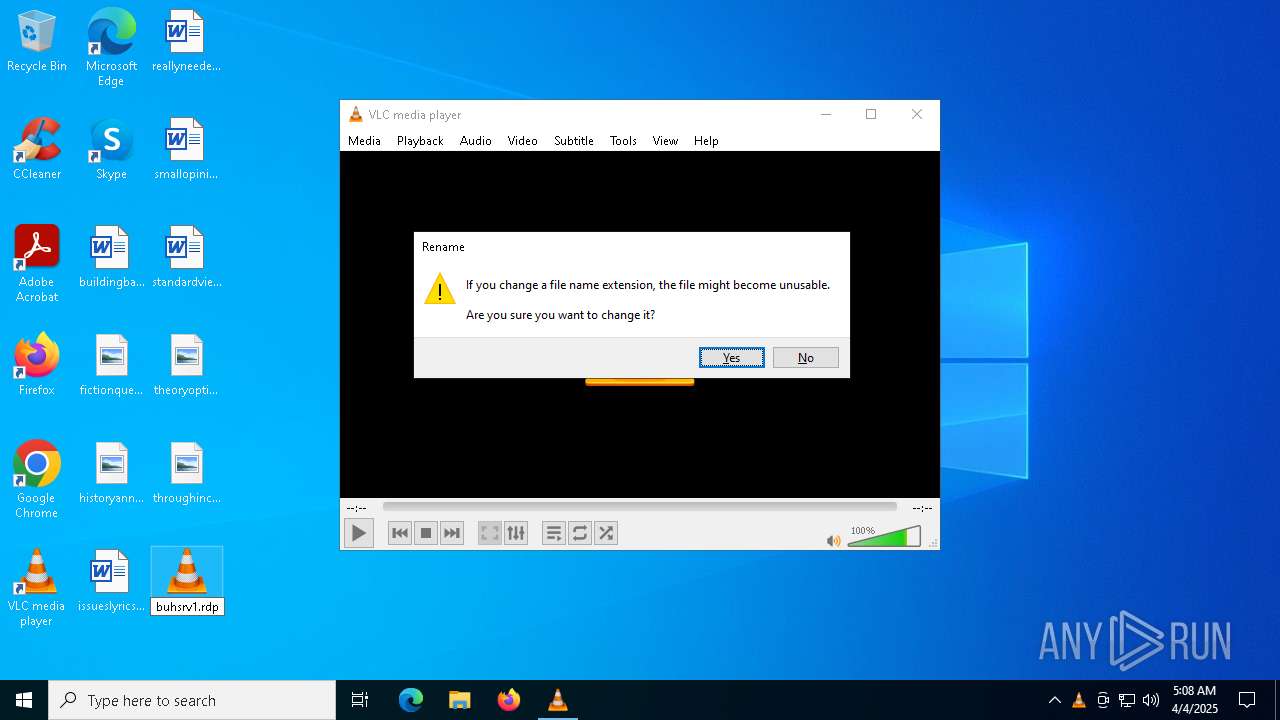
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rdp\OpenWithProgids |
| Operation: | write | Name: | RDP.File |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rdp\OpenWithList |
| Operation: | write | Name: | a |
Value: mstsc.exe | |||
Executable files
5
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3300 | vlc.exe | — | ||
MD5:— | SHA256:— | |||
| 5492 | explorer.exe | C:\Users\admin\Desktop\buhsrv1.rdp | text | |
MD5:95E6FD77AD7A0BFC8C3D1F3D2FD8A283 | SHA256:CCA25DB9EF9D7108AAD35BE9E394B268A561A78DD9B789E658000CDCAB271B4F | |||
| 3300 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | text | |
MD5:E32BAB2C0A1D850ED3BC5401F749CFE7 | SHA256:A59406D335C05D703F60510AFFFB251470109AA28D161734C781827CDE220839 | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 3300 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.lock | text | |
MD5:7AC78C485C3BBE73ECF0C5494EA7F373 | SHA256:82B43E65B2FDEB4D4AF6421AB871585DD2A3B163FF5C45AC46A03520D094C229 | |||
| 3300 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\ml.xspf | xml | |
MD5:781602441469750C3219C8C38B515ED4 | SHA256:81970DBE581373D14FBD451AC4B3F96E5F69B79645F1EE1CA715CFF3AF0BF20D | |||
| 3300 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.Hp3300 | text | |
MD5:E32BAB2C0A1D850ED3BC5401F749CFE7 | SHA256:A59406D335C05D703F60510AFFFB251470109AA28D161734C781827CDE220839 | |||
| 3300 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.gq3300 | text | |
MD5:FDF960177BAE8D6D100AEF43865ECECB | SHA256:91B1E2C6168C135ADF6BE83696933C4DCC3DFF349E7F0B3A32420AA23E5FB5B7 | |||
| 6272 | mstsc.exe | C:\Users\admin\AppData\Local\Microsoft\Terminal Server Client\Cache\bcache22.bmc | binary | |
MD5:1768DE2127E43ED85AD0A39054107F67 | SHA256:8464F35403F7C0EDAB324AAFBB0A17861160146B18561F1AA0689295C3598ECE | |||
| 6272 | mstsc.exe | C:\Users\admin\Desktop\StickyWerewolf.lnk | binary | |
MD5:07AA139DBCDC9D31315D5F0EB9AB3FB6 | SHA256:7D32B760EAD0224FCFA9D1B6CA5AD204CCFA43C4EB4BC22546A67AD399E22F4E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
44
DNS requests
15
Threats
76
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4464 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4464 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 20.10.31.115:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
buhsrv1.remote-desktop.ru |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6272 | mstsc.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 29 |
6272 | mstsc.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] RDP protocol for remote access (TPKT Header) |
6272 | mstsc.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] RDP protocol for remote access (TPKT Header) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible NTLM Hash leak over SMB (NTLMSSP_AUTH) |