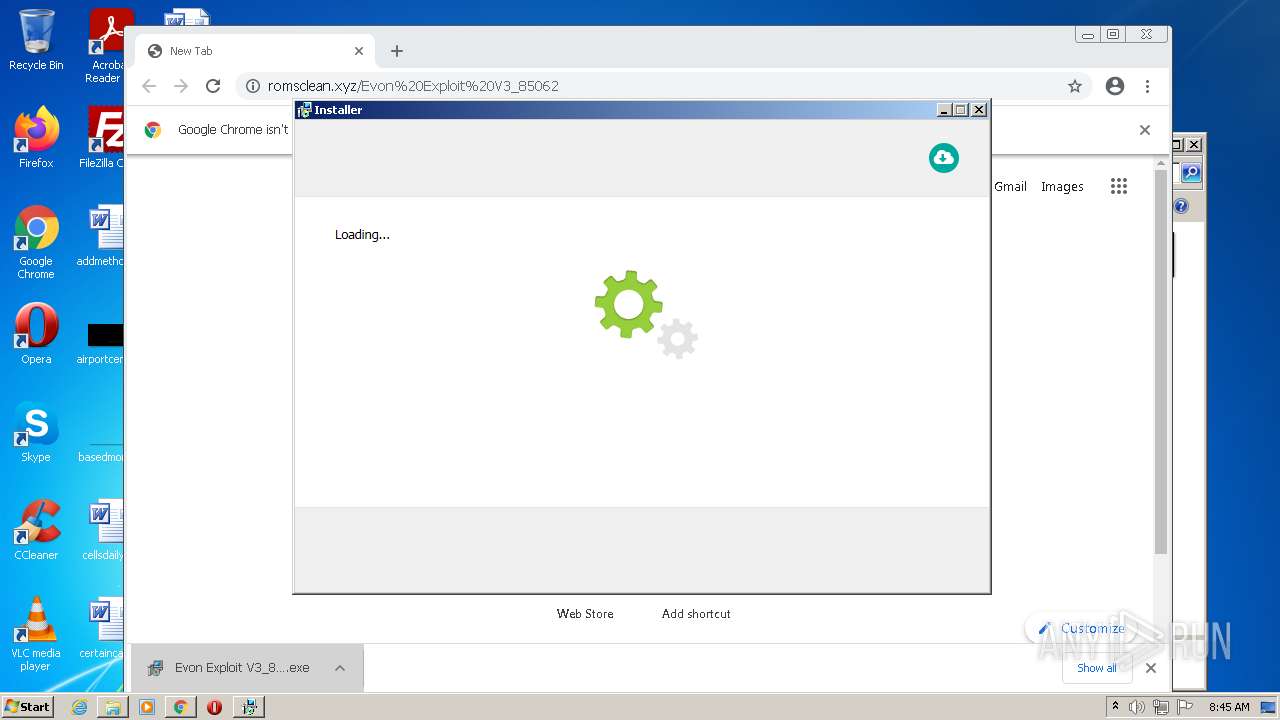
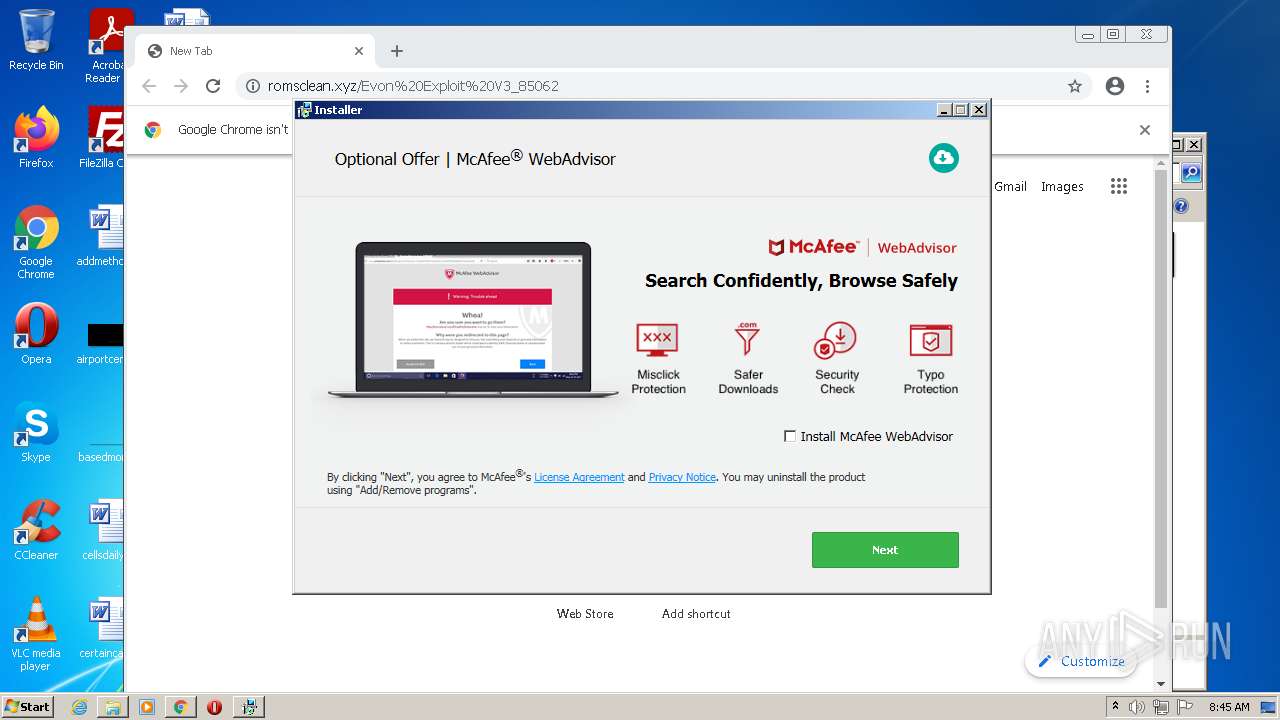
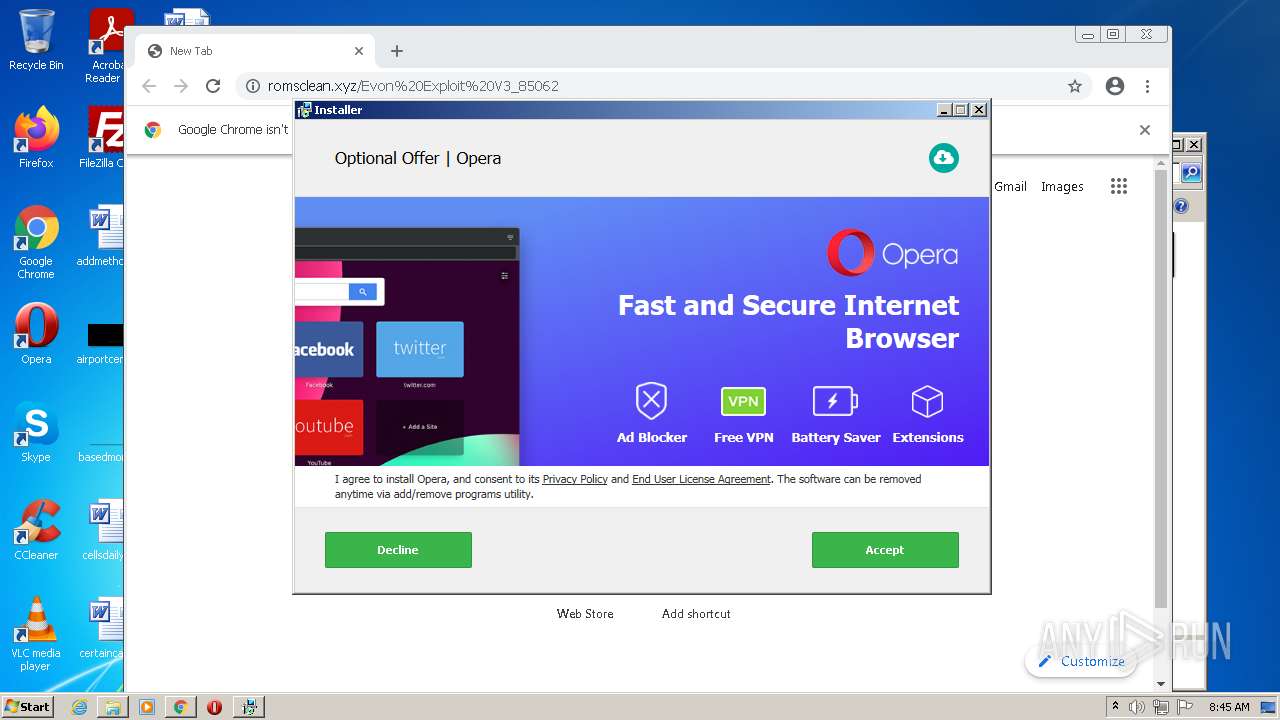
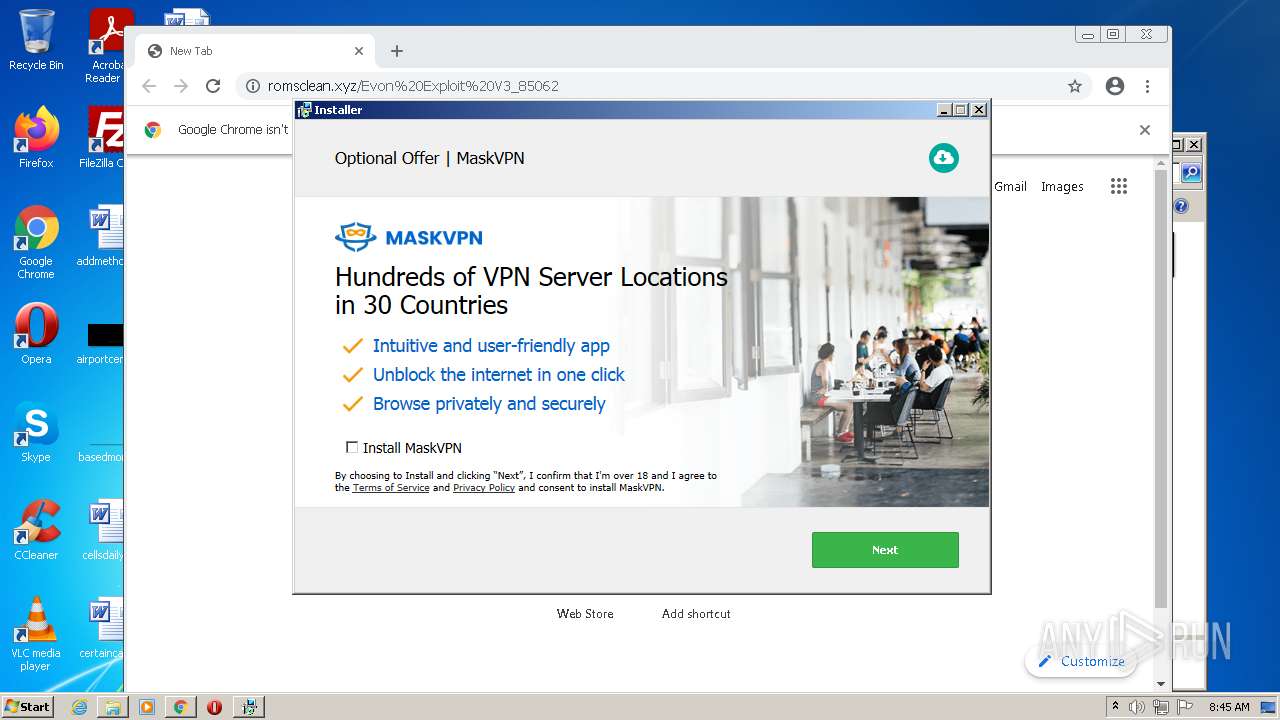
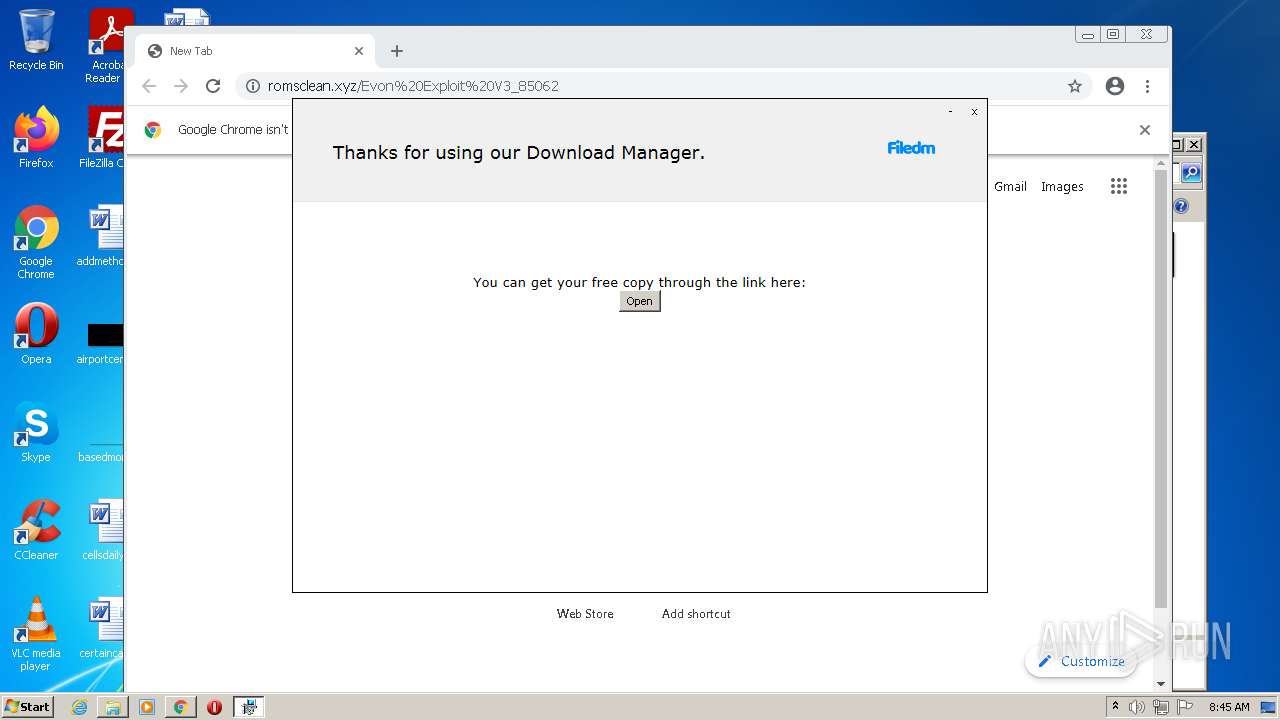
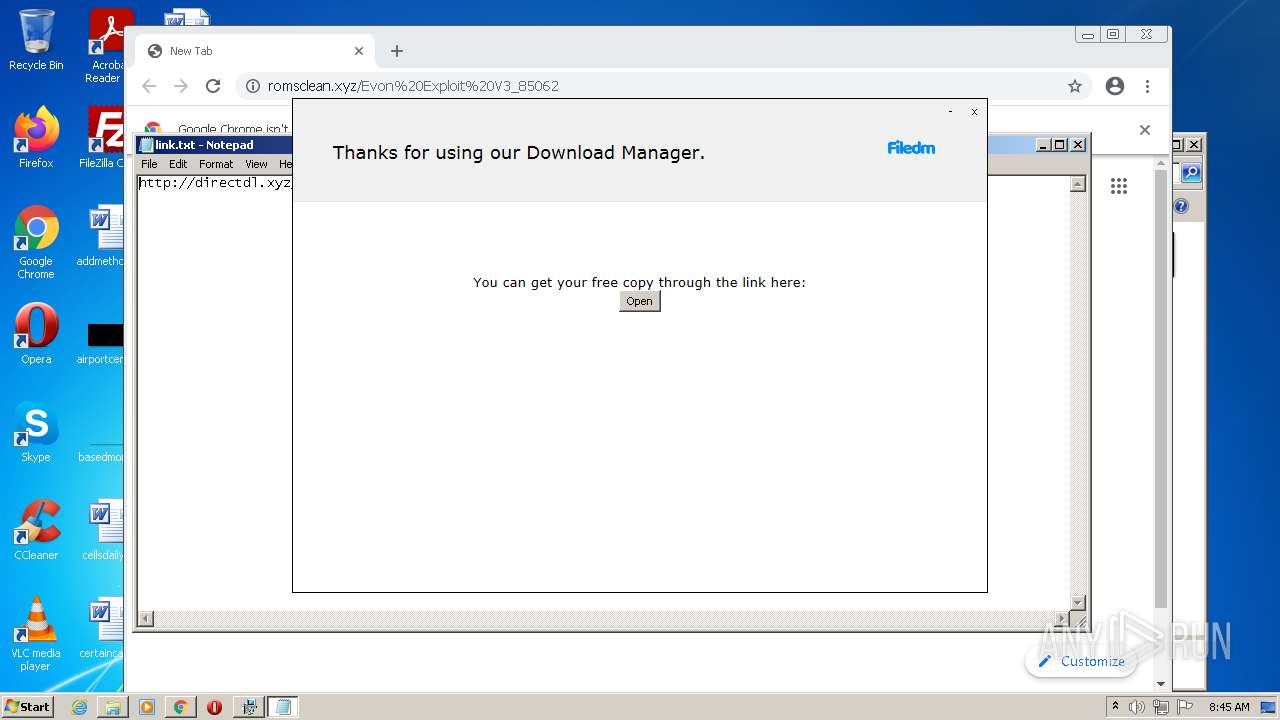
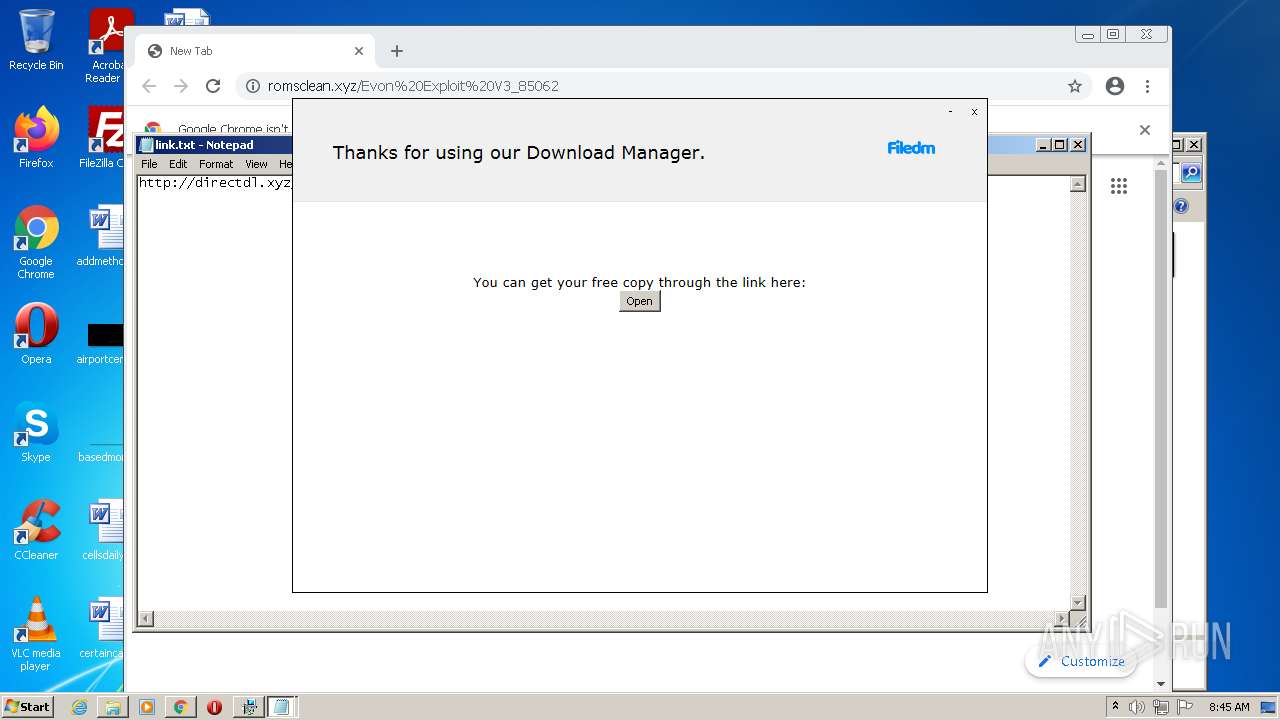
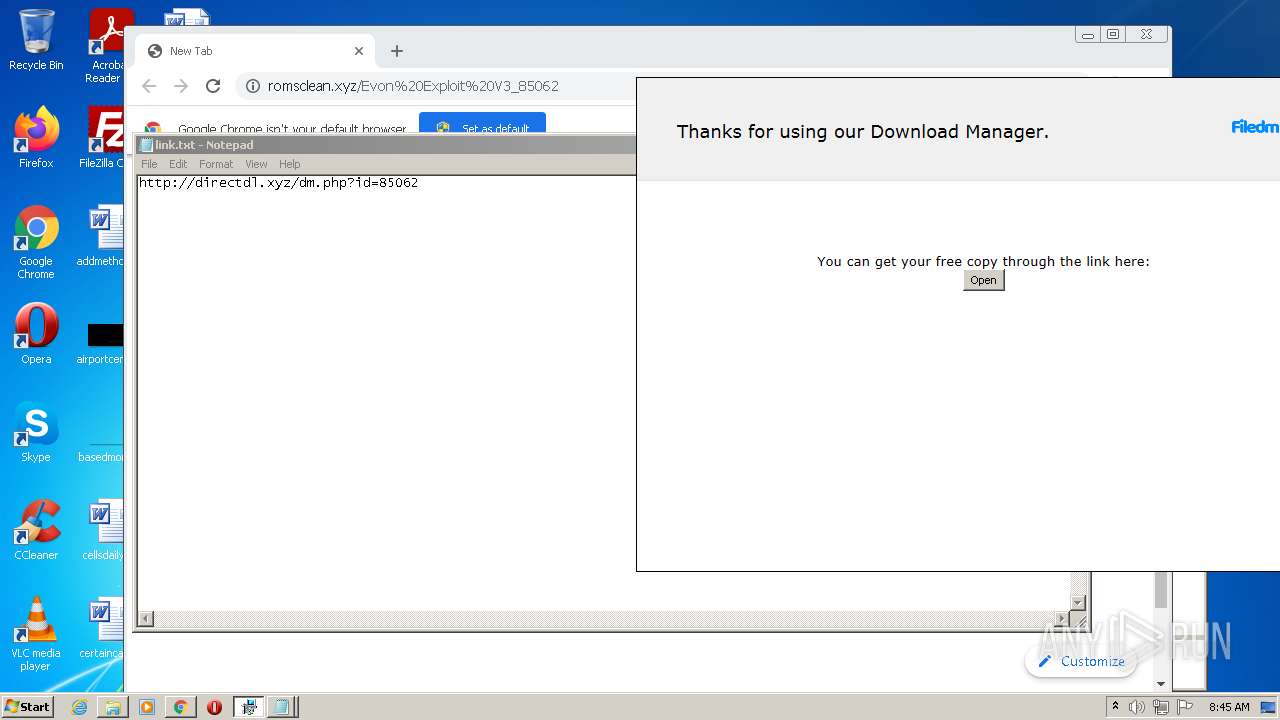
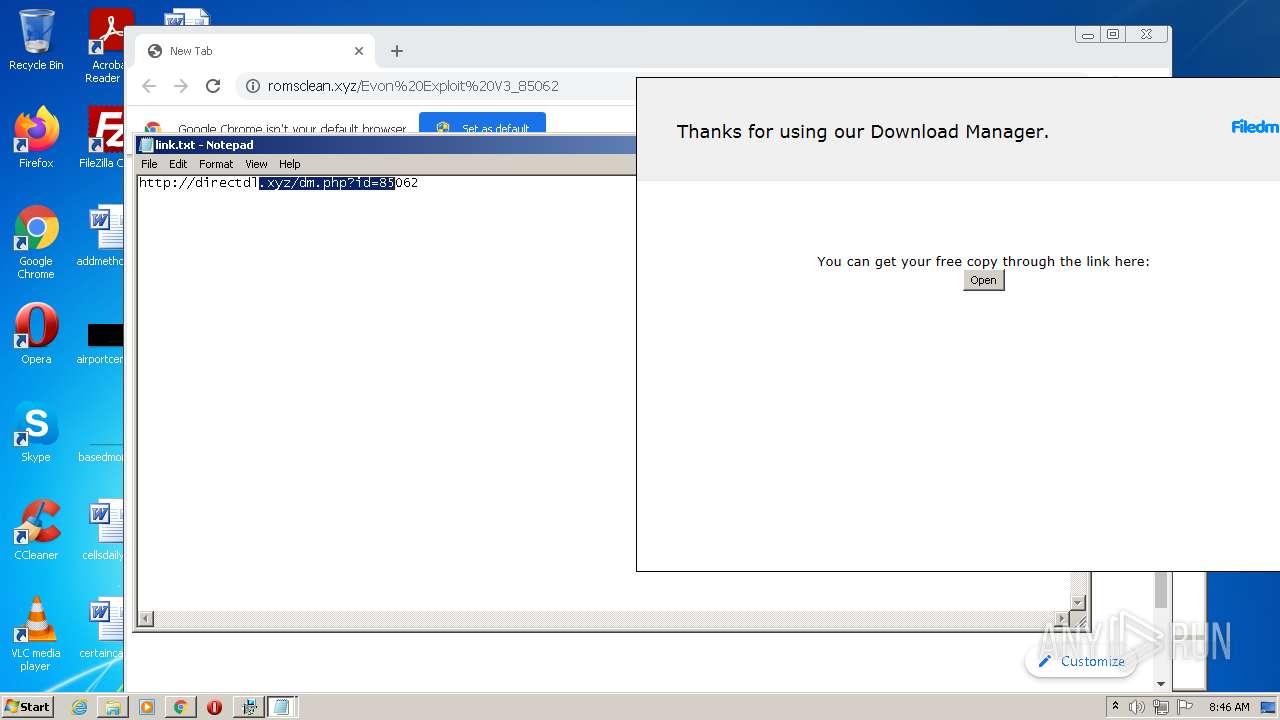
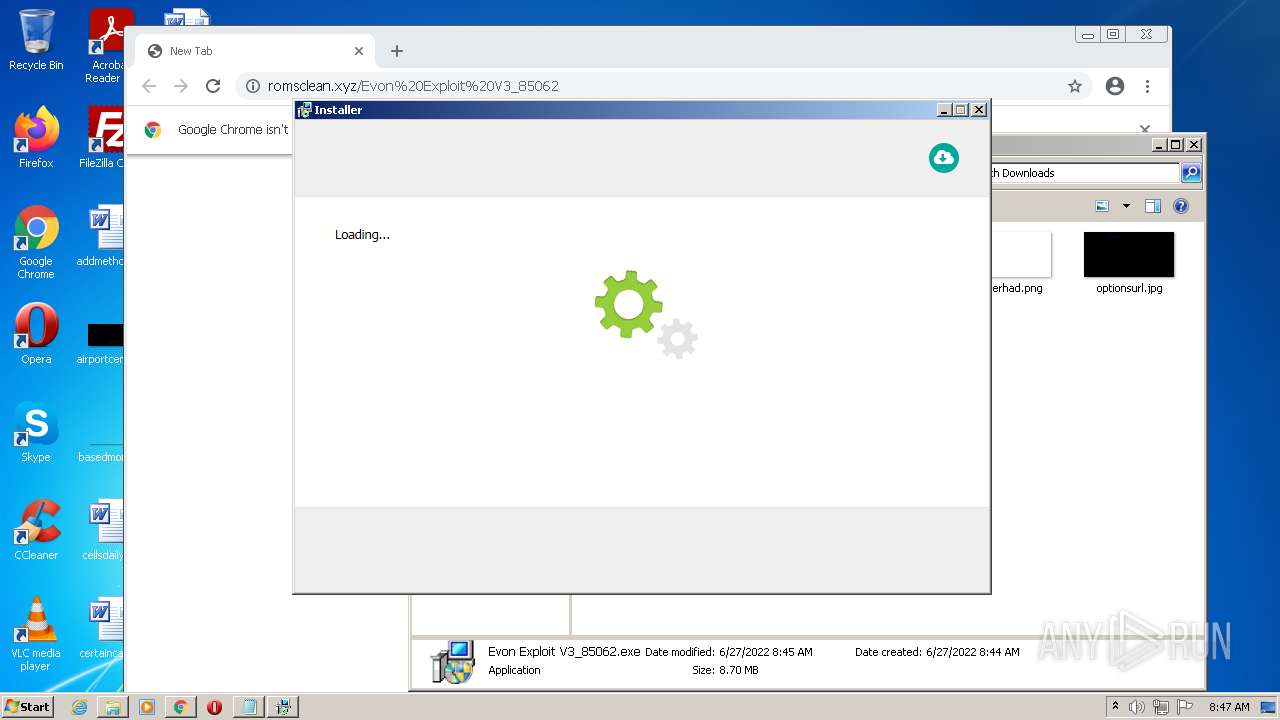
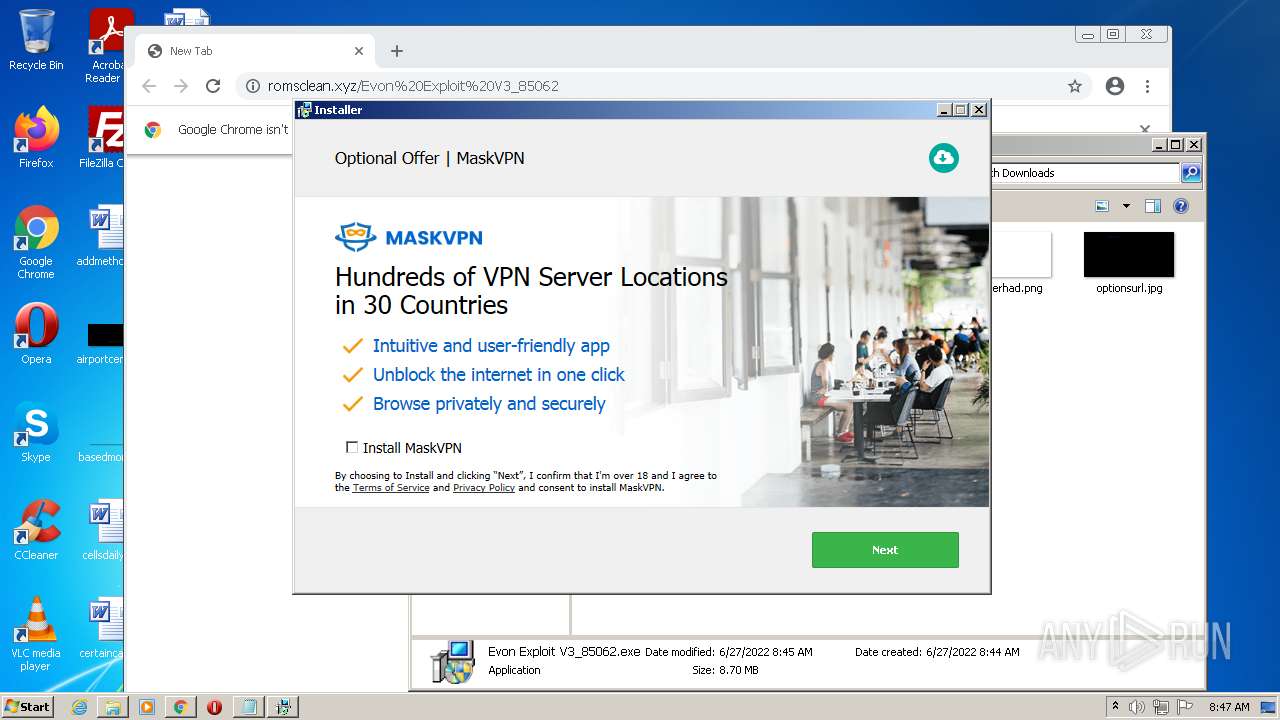
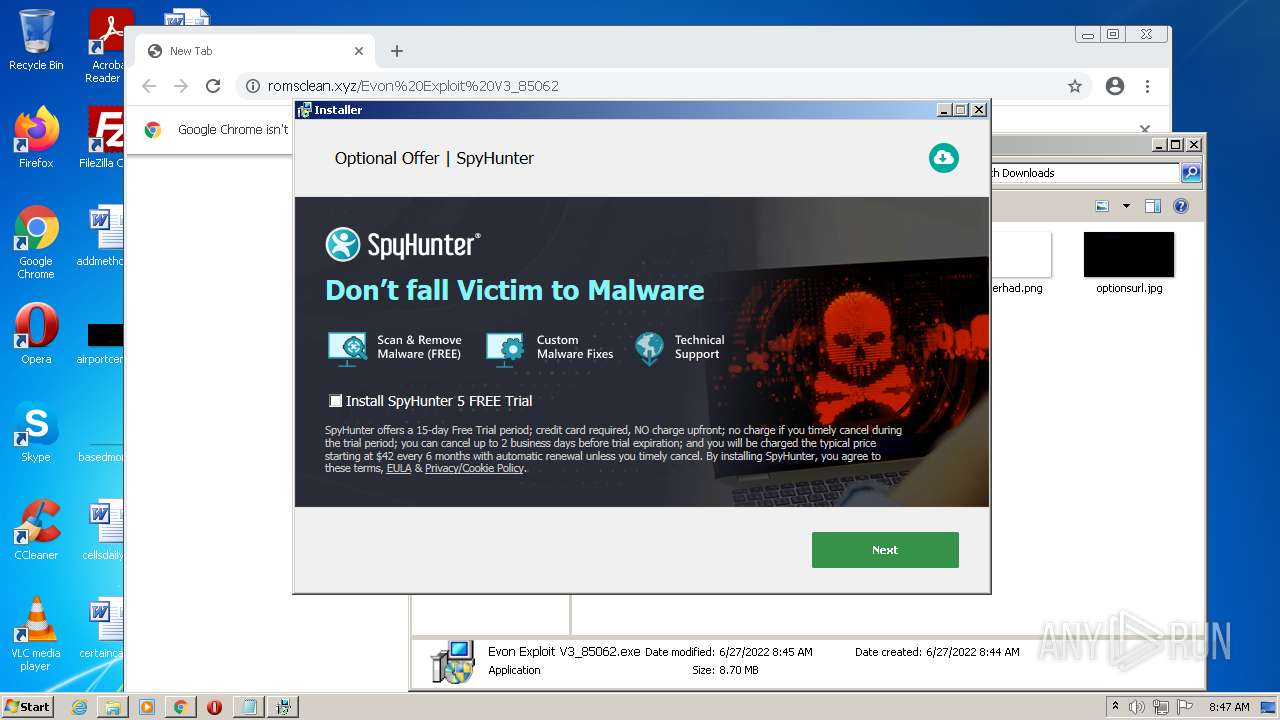
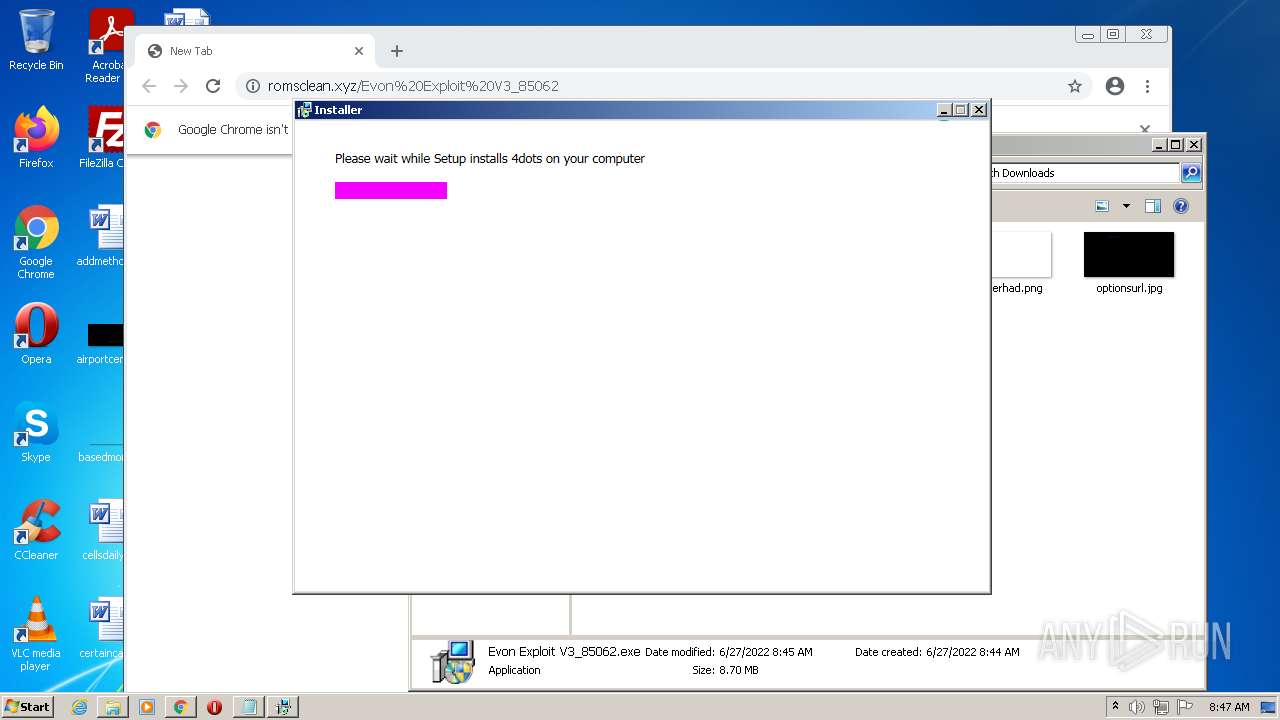
| download: | Evon%20Exploit%20V3_85062 |
| Full analysis: | https://app.any.run/tasks/3d67992e-e878-42cf-8d92-5440d86cfddb |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 07:43:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D95304D22479D196942A8E188113884C |
| SHA1: | F9F88C60A21B7348DD4732134862B80EB324BE60 |
| SHA256: | CC8884209D49144B756C86A3A65385307C06415776863EEEC0746438FF8D3E36 |
| SSDEEP: | 196608:yIIQxYuxFeQFrqNYaG59Fa9FVDNWXVkHo/EZb:rI0PFLrqNYv529PDNs2Ho/EZb |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 3836)
- chrome.exe (PID: 2452)
- Evon Exploit V3_85062.exe (PID: 3660)
- setup85062.exe (PID: 3404)
- GenericSetup.exe (PID: 3164)
- setup85062.exe (PID: 3636)
- setup85062.exe (PID: 2752)
- GenericSetup.exe (PID: 1640)
- setup85062.exe (PID: 3324)
- 4ebgru2l.jvk.exe (PID: 3996)
- 4ebgru2l.jvk.tmp (PID: 1832)
- DrvInst.exe (PID: 2768)
- tapinstall.exe (PID: 3648)
- chrome.exe (PID: 3208)
- DrvInst.exe (PID: 2028)
Changes settings of System certificates
- Evon Exploit V3_85062.exe (PID: 3660)
- GenericSetup.exe (PID: 3164)
- saBSI.exe (PID: 908)
- OfferInstaller.exe (PID: 1456)
- OfferInstaller.exe (PID: 1036)
- tapinstall.exe (PID: 3648)
- 4ebgru2l.jvk.tmp (PID: 1832)
Actions looks like stealing of personal data
- GenericSetup.exe (PID: 3164)
- OfferInstaller.exe (PID: 1456)
- GenericSetup.exe (PID: 1640)
- OfferInstaller.exe (PID: 1036)
Application was dropped or rewritten from another process
- setup85062.exe (PID: 3404)
- setup85062.exe (PID: 3636)
- GenericSetup.exe (PID: 3448)
- GenericSetup.exe (PID: 3164)
- OfferInstaller.exe (PID: 1456)
- setup85062.exe (PID: 2752)
- GenericSetup.exe (PID: 1640)
- setup85062.exe (PID: 3324)
- GenericSetup.exe (PID: 3908)
- OfferInstaller.exe (PID: 1036)
- tapinstall.exe (PID: 3924)
- tapinstall.exe (PID: 3648)
- mask_svc.exe (PID: 2696)
- mask_svc.exe (PID: 2564)
- mask_svc.exe (PID: 3988)
Loads dropped or rewritten executable
- GenericSetup.exe (PID: 3164)
- GenericSetup.exe (PID: 3448)
- OfferInstaller.exe (PID: 1456)
- GenericSetup.exe (PID: 1640)
- GenericSetup.exe (PID: 3908)
- OfferInstaller.exe (PID: 1036)
- mask_svc.exe (PID: 3988)
Changes the autorun value in the registry
- DrvInst.exe (PID: 2028)
SUSPICIOUS
Reads the computer name
- d37a3505-e28d-4e1f-a7e3-f434c23616f9.exe (PID: 268)
- Evon Exploit V3_85062.exe (PID: 3660)
- GenericSetup.exe (PID: 3164)
- GenericSetup.exe (PID: 3448)
- OfferInstaller.exe (PID: 1456)
- saBSI.exe (PID: 908)
- Evon Exploit V3_85062.exe (PID: 296)
- GenericSetup.exe (PID: 1640)
- OfferInstaller.exe (PID: 1036)
- GenericSetup.exe (PID: 3908)
- 4ebgru2l.jvk.tmp (PID: 1832)
- tapinstall.exe (PID: 3924)
- tapinstall.exe (PID: 3648)
- DrvInst.exe (PID: 2768)
- DrvInst.exe (PID: 2028)
- mask_svc.exe (PID: 2696)
- mask_svc.exe (PID: 2564)
- mask_svc.exe (PID: 3988)
Checks supported languages
- d37a3505-e28d-4e1f-a7e3-f434c23616f9.exe (PID: 268)
- Evon Exploit V3_85062.exe (PID: 3660)
- setup85062.exe (PID: 3404)
- GenericSetup.exe (PID: 3164)
- setup85062.exe (PID: 3636)
- GenericSetup.exe (PID: 3448)
- OfferInstaller.exe (PID: 1456)
- saBSI.exe (PID: 908)
- cmd.exe (PID: 3548)
- Evon Exploit V3_85062.exe (PID: 296)
- setup85062.exe (PID: 2752)
- GenericSetup.exe (PID: 1640)
- setup85062.exe (PID: 3324)
- OfferInstaller.exe (PID: 1036)
- cmd.exe (PID: 340)
- GenericSetup.exe (PID: 3908)
- 4ebgru2l.jvk.exe (PID: 3996)
- 4ebgru2l.jvk.tmp (PID: 1832)
- cmd.exe (PID: 1816)
- tapinstall.exe (PID: 3924)
- tapinstall.exe (PID: 3648)
- cmd.exe (PID: 2212)
- DrvInst.exe (PID: 2768)
- DrvInst.exe (PID: 2028)
- mask_svc.exe (PID: 2564)
- mask_svc.exe (PID: 2696)
- mask_svc.exe (PID: 3988)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3836)
Executable content was dropped or overwritten
- chrome.exe (PID: 3836)
- chrome.exe (PID: 2452)
- Evon Exploit V3_85062.exe (PID: 3660)
- setup85062.exe (PID: 3404)
- setup85062.exe (PID: 3636)
- GenericSetup.exe (PID: 3164)
- setup85062.exe (PID: 2752)
- GenericSetup.exe (PID: 1640)
- setup85062.exe (PID: 3324)
- 4ebgru2l.jvk.exe (PID: 3996)
- 4ebgru2l.jvk.tmp (PID: 1832)
- DrvInst.exe (PID: 2768)
- tapinstall.exe (PID: 3648)
- chrome.exe (PID: 3208)
- DrvInst.exe (PID: 2028)
Drops a file with a compile date too recent
- chrome.exe (PID: 3836)
- chrome.exe (PID: 2452)
- Evon Exploit V3_85062.exe (PID: 3660)
- setup85062.exe (PID: 3404)
- GenericSetup.exe (PID: 3164)
- setup85062.exe (PID: 3636)
- setup85062.exe (PID: 2752)
- GenericSetup.exe (PID: 1640)
- setup85062.exe (PID: 3324)
- 4ebgru2l.jvk.exe (PID: 3996)
- 4ebgru2l.jvk.tmp (PID: 1832)
- tapinstall.exe (PID: 3648)
- DrvInst.exe (PID: 2768)
- chrome.exe (PID: 3208)
- DrvInst.exe (PID: 2028)
Adds / modifies Windows certificates
- Evon Exploit V3_85062.exe (PID: 3660)
- GenericSetup.exe (PID: 3164)
- OfferInstaller.exe (PID: 1456)
- saBSI.exe (PID: 908)
- OfferInstaller.exe (PID: 1036)
Reads Environment values
- GenericSetup.exe (PID: 3164)
- OfferInstaller.exe (PID: 1456)
- GenericSetup.exe (PID: 1640)
- OfferInstaller.exe (PID: 1036)
- vssvc.exe (PID: 3240)
- DrvInst.exe (PID: 2028)
Reads Windows owner or organization settings
- GenericSetup.exe (PID: 3164)
- OfferInstaller.exe (PID: 1456)
- GenericSetup.exe (PID: 1640)
- OfferInstaller.exe (PID: 1036)
- 4ebgru2l.jvk.tmp (PID: 1832)
Reads the Windows organization settings
- GenericSetup.exe (PID: 3164)
- OfferInstaller.exe (PID: 1456)
- GenericSetup.exe (PID: 1640)
- OfferInstaller.exe (PID: 1036)
- 4ebgru2l.jvk.tmp (PID: 1832)
Creates files in the program directory
- saBSI.exe (PID: 908)
Starts CMD.EXE for commands execution
- OfferInstaller.exe (PID: 1456)
- OfferInstaller.exe (PID: 1036)
- 4ebgru2l.jvk.tmp (PID: 1832)
Creates a directory in Program Files
- 4ebgru2l.jvk.tmp (PID: 1832)
Creates files in the Windows directory
- DrvInst.exe (PID: 2768)
- DrvInst.exe (PID: 2028)
Creates files in the driver directory
- DrvInst.exe (PID: 2768)
- DrvInst.exe (PID: 2028)
Executed as Windows Service
- vssvc.exe (PID: 3240)
- mask_svc.exe (PID: 3988)
Executed via COM
- DrvInst.exe (PID: 2768)
- DrvInst.exe (PID: 2028)
Removes files from Windows directory
- DrvInst.exe (PID: 2768)
- DrvInst.exe (PID: 2028)
Searches for installed software
- GenericSetup.exe (PID: 3164)
- GenericSetup.exe (PID: 1640)
INFO
Checks supported languages
- explorer.exe (PID: 2656)
- chrome.exe (PID: 3836)
- chrome.exe (PID: 4060)
- chrome.exe (PID: 2452)
- chrome.exe (PID: 2312)
- chrome.exe (PID: 3096)
- chrome.exe (PID: 3100)
- chrome.exe (PID: 3276)
- chrome.exe (PID: 3520)
- chrome.exe (PID: 2724)
- chrome.exe (PID: 3168)
- chrome.exe (PID: 2848)
- chrome.exe (PID: 3428)
- chrome.exe (PID: 2292)
- chrome.exe (PID: 3356)
- chrome.exe (PID: 1224)
- chrome.exe (PID: 2208)
- chrome.exe (PID: 1256)
- chrome.exe (PID: 3920)
- chrome.exe (PID: 3164)
- chrome.exe (PID: 2724)
- chrome.exe (PID: 1760)
- chrome.exe (PID: 3908)
- chrome.exe (PID: 4076)
- chrome.exe (PID: 2836)
- chrome.exe (PID: 2868)
- chrome.exe (PID: 3792)
- chrome.exe (PID: 2620)
- chrome.exe (PID: 3096)
- chrome.exe (PID: 2168)
- chrome.exe (PID: 2664)
- chrome.exe (PID: 3628)
- NOTEPAD.EXE (PID: 3972)
- NOTEPAD.EXE (PID: 2392)
- chrome.exe (PID: 3872)
- chrome.exe (PID: 2528)
- chrome.exe (PID: 564)
- chrome.exe (PID: 2420)
- chrome.exe (PID: 824)
- NOTEPAD.EXE (PID: 2792)
- chrome.exe (PID: 3660)
- chrome.exe (PID: 3636)
- chrome.exe (PID: 3644)
- chrome.exe (PID: 3208)
- vssvc.exe (PID: 3240)
- chrome.exe (PID: 572)
- chrome.exe (PID: 3396)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 1000)
Reads the computer name
- explorer.exe (PID: 2656)
- chrome.exe (PID: 3836)
- chrome.exe (PID: 2312)
- chrome.exe (PID: 2452)
- chrome.exe (PID: 3428)
- chrome.exe (PID: 3920)
- chrome.exe (PID: 3164)
- chrome.exe (PID: 1760)
- chrome.exe (PID: 2868)
- chrome.exe (PID: 3792)
- vssvc.exe (PID: 3240)
Manual execution by user
- explorer.exe (PID: 2656)
- chrome.exe (PID: 3836)
- Evon Exploit V3_85062.exe (PID: 296)
- Evon Exploit V3_85062.exe (PID: 3068)
Reads the hosts file
- chrome.exe (PID: 3836)
- chrome.exe (PID: 2452)
Reads settings of System Certificates
- chrome.exe (PID: 2452)
- chrome.exe (PID: 3836)
- Evon Exploit V3_85062.exe (PID: 3660)
- GenericSetup.exe (PID: 3164)
- saBSI.exe (PID: 908)
- OfferInstaller.exe (PID: 1456)
- Evon Exploit V3_85062.exe (PID: 296)
- GenericSetup.exe (PID: 1640)
- OfferInstaller.exe (PID: 1036)
- tapinstall.exe (PID: 3648)
- 4ebgru2l.jvk.tmp (PID: 1832)
- DrvInst.exe (PID: 2768)
- DrvInst.exe (PID: 2028)
Application launched itself
- chrome.exe (PID: 3836)
Reads the date of Windows installation
- chrome.exe (PID: 1760)
Checks Windows Trust Settings
- chrome.exe (PID: 3836)
- Evon Exploit V3_85062.exe (PID: 3660)
- GenericSetup.exe (PID: 3164)
- OfferInstaller.exe (PID: 1456)
- saBSI.exe (PID: 908)
- Evon Exploit V3_85062.exe (PID: 296)
- GenericSetup.exe (PID: 1640)
- OfferInstaller.exe (PID: 1036)
- tapinstall.exe (PID: 3648)
- DrvInst.exe (PID: 2768)
- DrvInst.exe (PID: 2028)
Loads dropped or rewritten executable
- 4ebgru2l.jvk.tmp (PID: 1832)
Creates files in the program directory
- 4ebgru2l.jvk.tmp (PID: 1832)
Application was dropped or rewritten from another process
- 4ebgru2l.jvk.tmp (PID: 1832)
Creates a software uninstall entry
- 4ebgru2l.jvk.tmp (PID: 1832)
Searches for installed software
- DrvInst.exe (PID: 2768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x3822e3 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 4899840 |
| CodeSize: | 4248064 |
| LinkerVersion: | 14.22 |
| PEType: | PE32 |
| TimeStamp: | 2022:05:14 13:23:37+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 14-May-2022 11:23:37 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 14-May-2022 11:23:37 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0040D1FB | 0x0040D200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65052 |
.rdata | 0x0040F000 | 0x000F9CFA | 0x000F9E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.51035 |
.data | 0x00509000 | 0x0002A0EC | 0x00023E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.8239 |
.rsrc | 0x00534000 | 0x0033DA60 | 0x0033DC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.94858 |
.reloc | 0x00872000 | 0x0004A7B4 | 0x0004A800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.58622 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.04264 | 562 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 2.73071 | 67624 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 2.77417 | 16936 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.65334 | 9640 | UNKNOWN | Dutch - Netherlands | RT_ICON |
5 | 2.82974 | 4264 | UNKNOWN | Dutch - Netherlands | RT_ICON |
6 | 4.49114 | 1128 | UNKNOWN | Dutch - Netherlands | RT_ICON |
101 | 7.98701 | 3295384 | UNKNOWN | Dutch - Netherlands | RT_RCDATA |
103 | 2.75463 | 90 | UNKNOWN | Dutch - Netherlands | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IMM32.dll |
KERNEL32.dll |
OLEACC.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
Total processes
141
Monitored processes
79
Malicious processes
25
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Users\admin\AppData\Local\Temp\d37a3505-e28d-4e1f-a7e3-f434c23616f9.exe" | C:\Users\admin\AppData\Local\Temp\d37a3505-e28d-4e1f-a7e3-f434c23616f9.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 296 | "C:\Users\admin\Downloads\Evon Exploit V3_85062.exe" | C:\Users\admin\Downloads\Evon Exploit V3_85062.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 340 | "C:\Windows\system32\cmd.exe" /C ""C:\Users\admin\AppData\Local\Temp\4ebgru2l.jvk.exe" /silent /shortcut /startmenu /subid=663" | C:\Windows\system32\cmd.exe | — | OfferInstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1048,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3908 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4100 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 824 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1048,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=704 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 908 | "saBSI.exe" /affid 91213 PaidDistribution=true InstallID=e1ed5e94-2152-4580-b0e0-cf5c845b36e8 subID=ES | C:\Users\admin\AppData\Local\Temp\7zSC4DC3281\saBSI.exe | cmd.exe | ||||||||||||
User: admin Company: McAfee, LLC Integrity Level: HIGH Description: McAfee WebAdvisor(bootstrap installer) Exit code: 4294967295 Version: 4,1,1,663 Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=43 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4192 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1036 | "C:\Users\admin\AppData\Local\Temp\7zS0CA46183\OfferInstaller.exe" | C:\Users\admin\AppData\Local\Temp\7zS0CA46183\OfferInstaller.exe | GenericSetup.exe | ||||||||||||
User: admin Company: Adaware Integrity Level: HIGH Description: Software Installation Exit code: 0 Version: 6.9.0.5763 Modules
| |||||||||||||||
| 1224 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,17775649781548946282,4093554849767185399,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2456 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
96 542
Read events
95 514
Write events
968
Delete events
60
Modification events
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3836) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
124
Suspicious files
206
Text files
278
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-62B95FCA-EFC.pma | — | |
MD5:— | SHA256:— | |||
| 3836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\cf49713e-884b-4cc8-ab15-edac82ac5da5.tmp | text | |
MD5:— | SHA256:— | |||
| 2452 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\index | binary | |
MD5:— | SHA256:— | |||
| 3836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
| 3836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF10a8c5.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 3836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\042c9d00-fc12-423a-a769-6ddec255a91b.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 4060 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 3836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 3836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF10a8e4.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
90
DNS requests
46
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
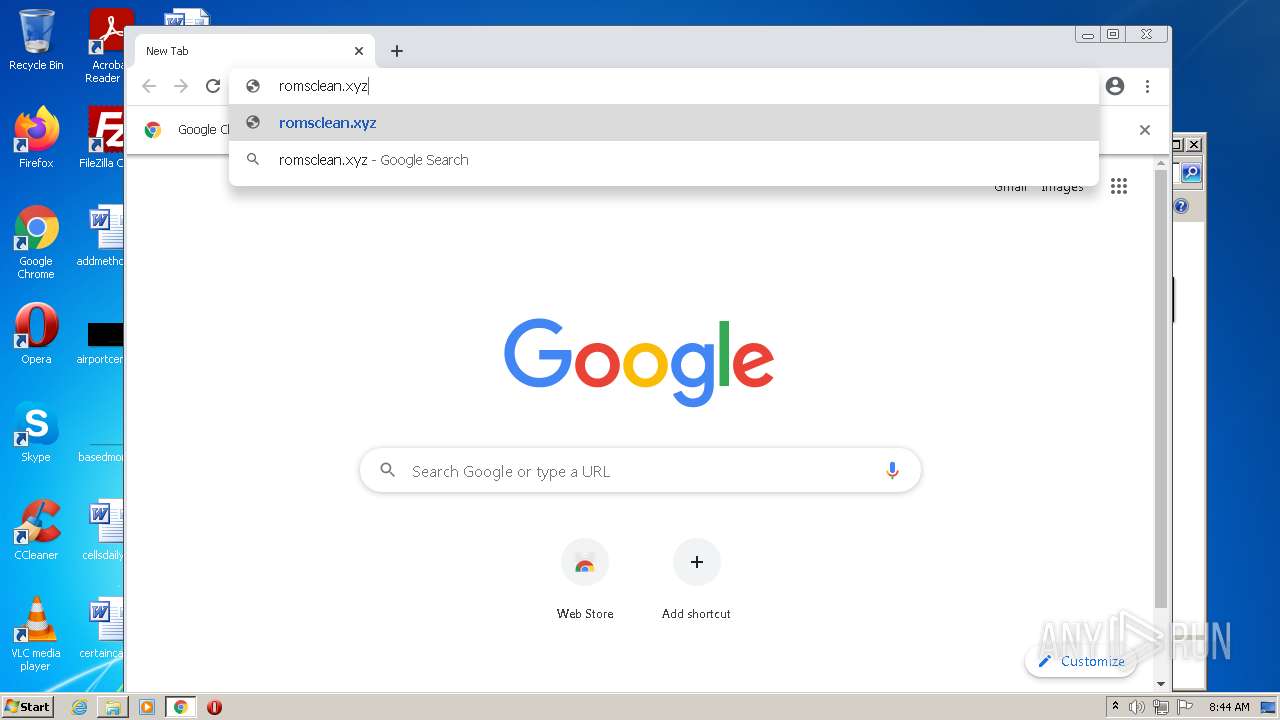
2452 | chrome.exe | GET | 301 | 172.67.154.128:80 | http://romsclean.xyz/Evon%20Exploit%20V3_85062 | US | — | — | suspicious |
3660 | Evon Exploit V3_85062.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | US | der | 724 b | whitelisted |
3660 | Evon Exploit V3_85062.exe | GET | 200 | 35.190.60.70:80 | http://dlsft.com/callback/info.php?id=85062 | US | text | 233 b | malicious |
3660 | Evon Exploit V3_85062.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3660 | Evon Exploit V3_85062.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3660 | Evon Exploit V3_85062.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/s/gts1d4/bN7zXbqFQrY/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEQDUIS4yX%2BvEeBDITghAx8GM | US | der | 472 b | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.70 Kb | whitelisted |
3660 | Evon Exploit V3_85062.exe | POST | 200 | 35.190.60.70:80 | http://dlsft.com/callback/geo/geo.php | US | text | 18 b | malicious |
3660 | Evon Exploit V3_85062.exe | POST | 200 | 35.190.60.70:80 | http://dlsft.com/callback/?channel=j3r8U&id=85062&action=started | US | compressed | 233 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2452 | chrome.exe | 142.250.184.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2452 | chrome.exe | 172.217.23.100:443 | www.google.com | Google Inc. | US | whitelisted |
2452 | chrome.exe | 142.250.185.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
2452 | chrome.exe | 172.217.23.97:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2452 | chrome.exe | 142.250.186.173:443 | accounts.google.com | Google Inc. | US | suspicious |
2452 | chrome.exe | 142.250.185.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2452 | chrome.exe | 142.251.36.142:443 | apis.google.com | Google Inc. | US | suspicious |
2452 | chrome.exe | 142.250.186.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2452 | chrome.exe | 142.250.186.174:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
2452 | chrome.exe | 172.217.16.195:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2452 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
— | — | Potentially Bad Traffic | ET DNS Query for .cc TLD |
908 | saBSI.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
908 | saBSI.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2452 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2452 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
12 ETPRO signatures available at the full report
Process | Message |
|---|---|
GenericSetup.exe | Error: File not found - genericsetup.wrappers.sciter:console.tis
|
GenericSetup.exe | at sciter:init-script.tis
|
GenericSetup.exe | |
GenericSetup.exe | |
GenericSetup.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
GenericSetup.exe | <div> element is not expected in <table>
|
GenericSetup.exe | <p> element is not expected in <table>
|
GenericSetup.exe | <div> element is not expected in <table>
|
GenericSetup.exe | <p> element is not expected in <table>
|
GenericSetup.exe | <div> element is not expected in <table>
|