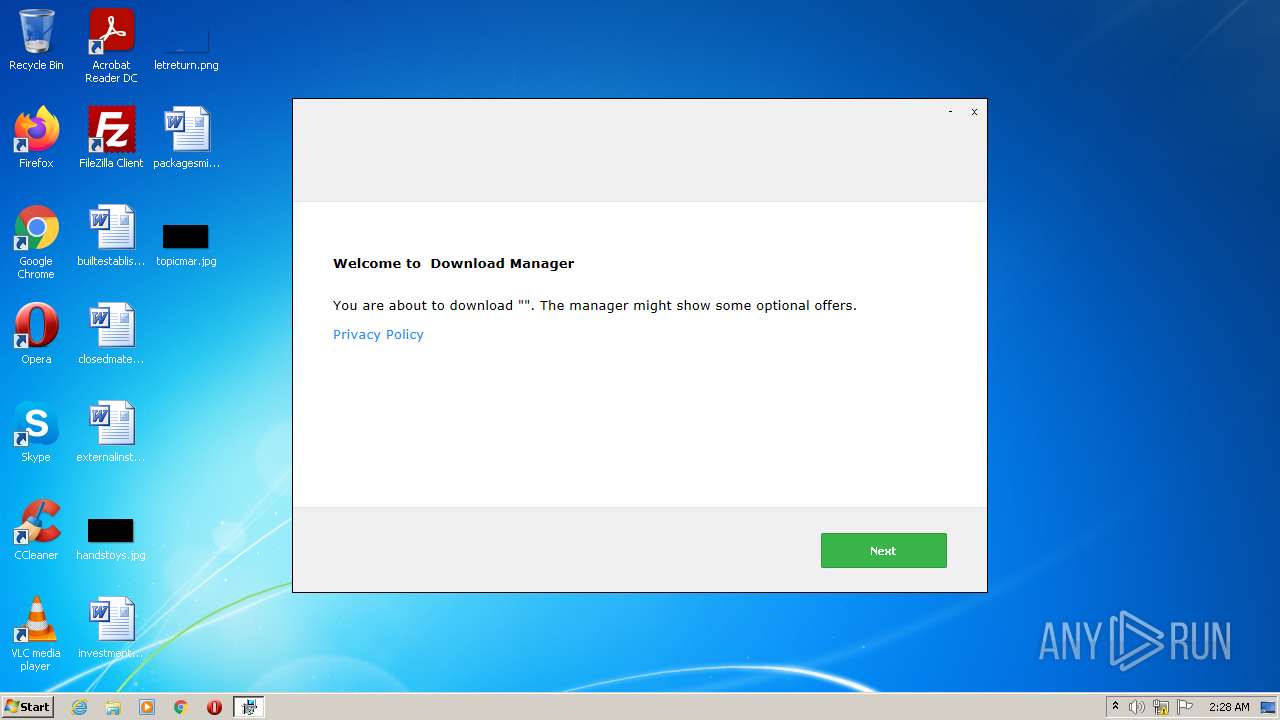
| File name: | EasyXploits_API_81905.exe |
| Full analysis: | https://app.any.run/tasks/337e0260-c82b-47d8-bbd8-f52fa9cce655 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 01:28:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D95304D22479D196942A8E188113884C |
| SHA1: | F9F88C60A21B7348DD4732134862B80EB324BE60 |
| SHA256: | CC8884209D49144B756C86A3A65385307C06415776863EEEC0746438FF8D3E36 |
| SSDEEP: | 196608:yIIQxYuxFeQFrqNYaG59Fa9FVDNWXVkHo/EZb:rI0PFLrqNYv529PDNs2Ho/EZb |
MALICIOUS
Drops executable file immediately after starts
- EasyXploits_API_81905.exe (PID: 4024)
- setup81905.exe (PID: 2524)
- GenericSetup.exe (PID: 3024)
- setup81905.exe (PID: 2396)
Loads dropped or rewritten executable
- GenericSetup.exe (PID: 3024)
- GenericSetup.exe (PID: 1080)
Application was dropped or rewritten from another process
- setup81905.exe (PID: 2524)
- GenericSetup.exe (PID: 3024)
- setup81905.exe (PID: 2396)
- GenericSetup.exe (PID: 1080)
Changes settings of System certificates
- GenericSetup.exe (PID: 3024)
Actions looks like stealing of personal data
- GenericSetup.exe (PID: 3024)
SUSPICIOUS
Checks supported languages
- EasyXploits_API_81905.exe (PID: 4024)
- setup81905.exe (PID: 2524)
- GenericSetup.exe (PID: 3024)
- setup81905.exe (PID: 2396)
- GenericSetup.exe (PID: 1080)
Reads the computer name
- EasyXploits_API_81905.exe (PID: 4024)
- GenericSetup.exe (PID: 3024)
- GenericSetup.exe (PID: 1080)
Executable content was dropped or overwritten
- EasyXploits_API_81905.exe (PID: 4024)
- setup81905.exe (PID: 2524)
- GenericSetup.exe (PID: 3024)
- setup81905.exe (PID: 2396)
Drops a file with a compile date too recent
- setup81905.exe (PID: 2524)
- EasyXploits_API_81905.exe (PID: 4024)
- GenericSetup.exe (PID: 3024)
- setup81905.exe (PID: 2396)
Reads Environment values
- GenericSetup.exe (PID: 3024)
Reads the Windows organization settings
- GenericSetup.exe (PID: 3024)
Reads Windows owner or organization settings
- GenericSetup.exe (PID: 3024)
Adds / modifies Windows certificates
- GenericSetup.exe (PID: 3024)
Searches for installed software
- GenericSetup.exe (PID: 3024)
INFO
Checks Windows Trust Settings
- GenericSetup.exe (PID: 3024)
Reads settings of System Certificates
- GenericSetup.exe (PID: 3024)
Checks supported languages
- NOTEPAD.EXE (PID: 1052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2022-May-14 11:23:37 |
| Detected languages: |
|
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 296 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 5 |
| TimeDateStamp: | 2022-May-14 11:23:37 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 4248059 | 4248064 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65052 |
.rdata | 4255744 | 1023226 | 1023488 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.51035 |
.data | 5279744 | 172268 | 146944 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.8239 |
.rsrc | 5455872 | 3398240 | 3398656 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.94858 |
.reloc | 8855552 | 305076 | 305152 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.58622 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 7.03313 | 2051 | UNKNOWN | Dutch - Netherlands | RT_ICON |
2 | 2.73071 | 67624 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 2.77417 | 16936 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.65334 | 9640 | UNKNOWN | Dutch - Netherlands | RT_ICON |
5 | 2.82974 | 4264 | UNKNOWN | Dutch - Netherlands | RT_ICON |
6 | 4.49114 | 1128 | UNKNOWN | Dutch - Netherlands | RT_ICON |
101 | 7.98701 | 3295384 | UNKNOWN | Dutch - Netherlands | RT_RCDATA |
103 | 2.75463 | 90 | UNKNOWN | Dutch - Netherlands | RT_GROUP_ICON |
1 (#2) | 5.04264 | 562 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IMM32.dll |
KERNEL32.dll |
OLEACC.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
Total processes
44
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\link.txt | C:\Windows\system32\NOTEPAD.EXE | — | EasyXploits_API_81905.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1080 | .\GenericSetup.exe hready | C:\Users\admin\AppData\Local\Temp\7zSC59BD2A3\GenericSetup.exe | — | setup81905.exe | |||||||||||
User: admin Integrity Level: HIGH Description: DT001 Exit code: 0 Version: 2.0.2.5763 Modules
| |||||||||||||||
| 2396 | C:\Users\admin\AppData\Local\setup81905.exe hready | C:\Users\admin\AppData\Local\setup81905.exe | EasyXploits_API_81905.exe | ||||||||||||
User: admin Company: DT001 Integrity Level: HIGH Description: Software Installation Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2524 | C:\Users\admin\AppData\Local\setup81905.exe hhwnd=196904 hreturntoinstaller hextras=id:-- | C:\Users\admin\AppData\Local\setup81905.exe | EasyXploits_API_81905.exe | ||||||||||||
User: admin Company: DT001 Integrity Level: HIGH Description: Software Installation Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3024 | .\GenericSetup.exe hhwnd=196904 hreturntoinstaller hextras=id:-- | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\GenericSetup.exe | setup81905.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: DT001 Exit code: 0 Version: 2.0.2.5763 Modules
| |||||||||||||||
| 3376 | "C:\Windows\EasyXploits_API_81905.exe" | C:\Windows\EasyXploits_API_81905.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4024 | "C:\Windows\EasyXploits_API_81905.exe" | C:\Windows\EasyXploits_API_81905.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
7 250
Read events
7 178
Write events
72
Delete events
0
Modification events
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4024) EasyXploits_API_81905.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{362E934C-743B-4588-8259-D2482DB771A8} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
Executable files
34
Suspicious files
1
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4024 | EasyXploits_API_81905.exe | C:\Users\admin\AppData\Local\setup81905.exe | executable | |
MD5:369ACF60D8B5ED6168C74955EE04654F | SHA256:3FF8EC8F9F27A27F414A90BFED5B7F5A3C118B33CF0F80AEB7026E0A53E26632 | |||
| 2524 | setup81905.exe | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\MyDownloader.Extension.dll | executable | |
MD5:28F1996059E79DF241388BD9F89CF0B1 | SHA256:C3F8A46E81F16BBFC75DE44DC95F0D145213C8AF0006BB097950AC4D1562F5CE | |||
| 2524 | setup81905.exe | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\OfferInstaller.exe.config | xml | |
MD5:67ED4EDC1D47444B046AD77F68CB2801 | SHA256:C9DD581B481E198C4E83DB6BE03BEC4BAC64C02C6C6F9E3051C23C3DF6F1301E | |||
| 2524 | setup81905.exe | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\GenericSetup.exe.config | xml | |
MD5:FD63EE3928EDD99AFC5BDF17E4F1E7B6 | SHA256:2A2DDBDC4600E829AD756FD5E84A79C0401FA846AD4F2F2FB235B410E82434A9 | |||
| 2524 | setup81905.exe | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\Newtonsoft.Json.dll | executable | |
MD5:3C4D2F6FD240DC804E10BBB5F16C6182 | SHA256:1F7A328EB4FA73DF5D2996202F5DAB02530B0339458137774C72731B9F85CA2E | |||
| 2524 | setup81905.exe | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\GenericSetup.exe | executable | |
MD5:85B0A721491803F8F0208A1856241562 | SHA256:18BE33F7C9F28B0A514F3F40983F452F476470691B1BE4F2ABA5BA5E06C6A345 | |||
| 2524 | setup81905.exe | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\MyDownloader.Core.dll | executable | |
MD5:F931E960CC4ED0D2F392376525FF44DB | SHA256:1C1C5330EA35F518BF85FAD69DC2DA1A98A4DFEADBF6AC0BA0AC7CC51BBCC870 | |||
| 2524 | setup81905.exe | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\de\GenericSetup.resources.dll | executable | |
MD5:B597E0A66EAC08849CB8CA80F9F2E8B4 | SHA256:B0C5246B10D5DFAF55B2112910C1CA11815F066C2854EECD326C657A7E46AD57 | |||
| 2524 | setup81905.exe | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\es\GenericSetup.resources.dll | executable | |
MD5:BE272836941982A1A22473E27976766E | SHA256:971AE92220940AC6FBBD2AE155138C348DE9CE2E6927FC83D48E27BBD988F3CD | |||
| 2524 | setup81905.exe | C:\Users\admin\AppData\Local\Temp\7zSCD90FE43\DynActsBLL.dll | executable | |
MD5:C7151D4057D2B91DA27BFAB58415DD81 | SHA256:4263A69119AE27E65B3BF25E1552C89E1FF2DBF0FBD6865CBD69A95CF851D81B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
84
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4024 | EasyXploits_API_81905.exe | POST | 404 | 35.190.60.70:80 | http://dlsft.com/callback/geo/geo.php | US | xml | 341 b | malicious |
4024 | EasyXploits_API_81905.exe | GET | 404 | 35.190.60.70:80 | http://dlsft.com/callback/info.php?id=81905 | US | xml | 341 b | malicious |
4024 | EasyXploits_API_81905.exe | POST | 404 | 35.190.60.70:80 | http://dlsft.com/callback/?channel=&id=81905&action=completed | US | xml | 341 b | malicious |
4024 | EasyXploits_API_81905.exe | GET | 404 | 35.190.60.70:80 | http://dlsft.com/callback/offers.php | US | xml | 341 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4024 | EasyXploits_API_81905.exe | 35.190.60.70:80 | www.dlsft.com | GOOGLE | US | whitelisted |
— | — | 104.18.87.101:443 | flow.lavasoft.com | CLOUDFLARENET | — | shared |
3024 | GenericSetup.exe | 52.239.214.132:443 | offerservicefallback.blob.core.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 52.239.214.132:443 | offerservicefallback.blob.core.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4024 | EasyXploits_API_81905.exe | 35.190.60.70:443 | www.dlsft.com | GOOGLE | US | whitelisted |
3024 | GenericSetup.exe | 104.18.87.101:443 | flow.lavasoft.com | CLOUDFLARENET | — | shared |
3024 | GenericSetup.exe | 104.16.236.79:443 | sos.adaware.com | CLOUDFLARENET | — | shared |
3024 | GenericSetup.exe | 104.18.88.101:443 | flow.lavasoft.com | CLOUDFLARENET | — | shared |
3024 | GenericSetup.exe | 104.16.235.79:443 | sos.adaware.com | CLOUDFLARENET | — | shared |
— | — | 104.18.88.101:443 | flow.lavasoft.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dlsft.com |
| malicious |
www.google.com |
| malicious |
flow.lavasoft.com |
| whitelisted |
sos.adaware.com |
| whitelisted |
dlsft.com |
| malicious |
offerservicefallback.blob.core.windows.net |
| suspicious |
Threats
Process | Message |
|---|---|
GenericSetup.exe | Error: File not found - genericsetup.wrappers.sciter:console.tis
|
GenericSetup.exe | at sciter:init-script.tis
|
GenericSetup.exe | |
GenericSetup.exe | |
GenericSetup.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
GenericSetup.exe | Error: File not found - genericsetup.wrappers.sciter:console.tis
|
GenericSetup.exe | at sciter:init-script.tis
|
GenericSetup.exe | |
GenericSetup.exe | |
GenericSetup.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|