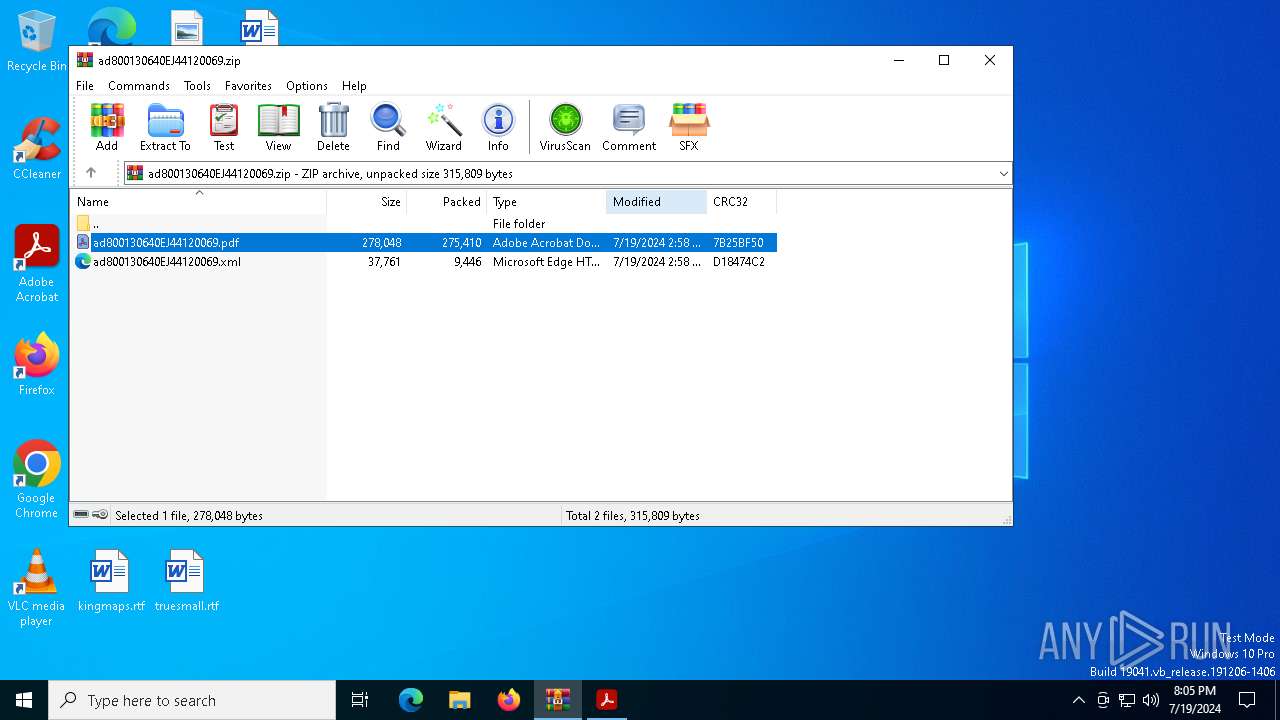
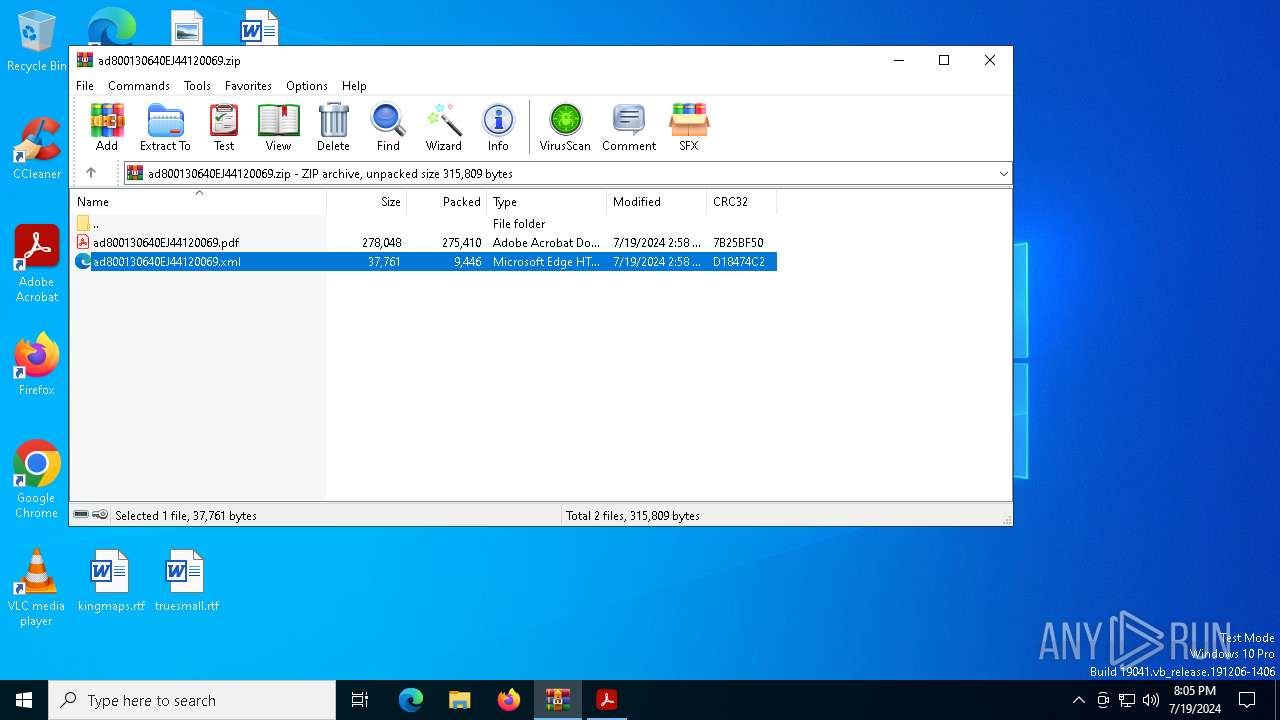
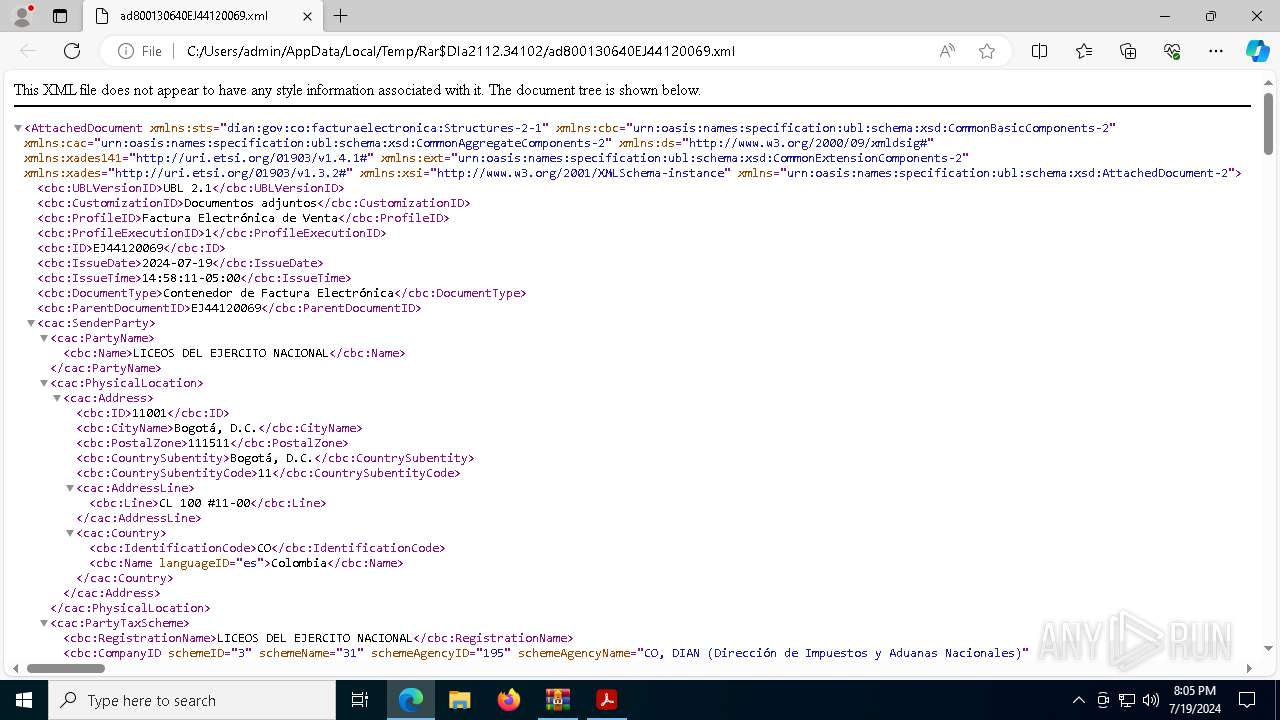
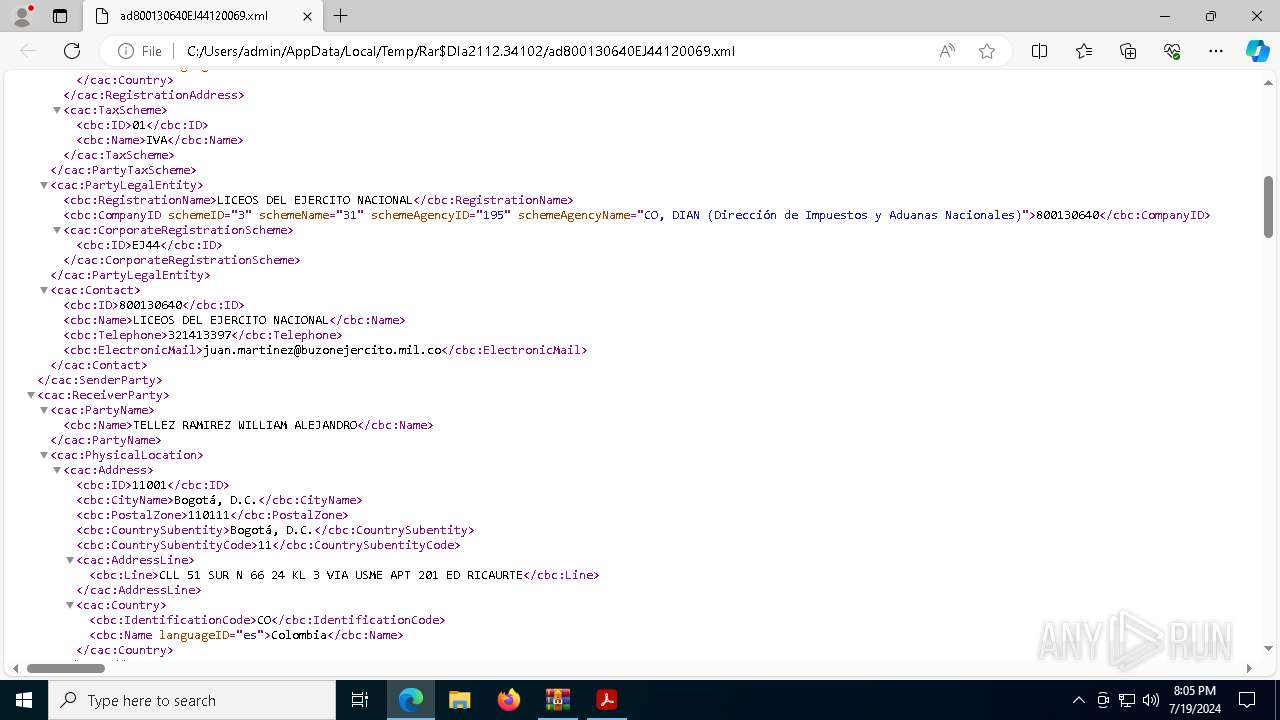
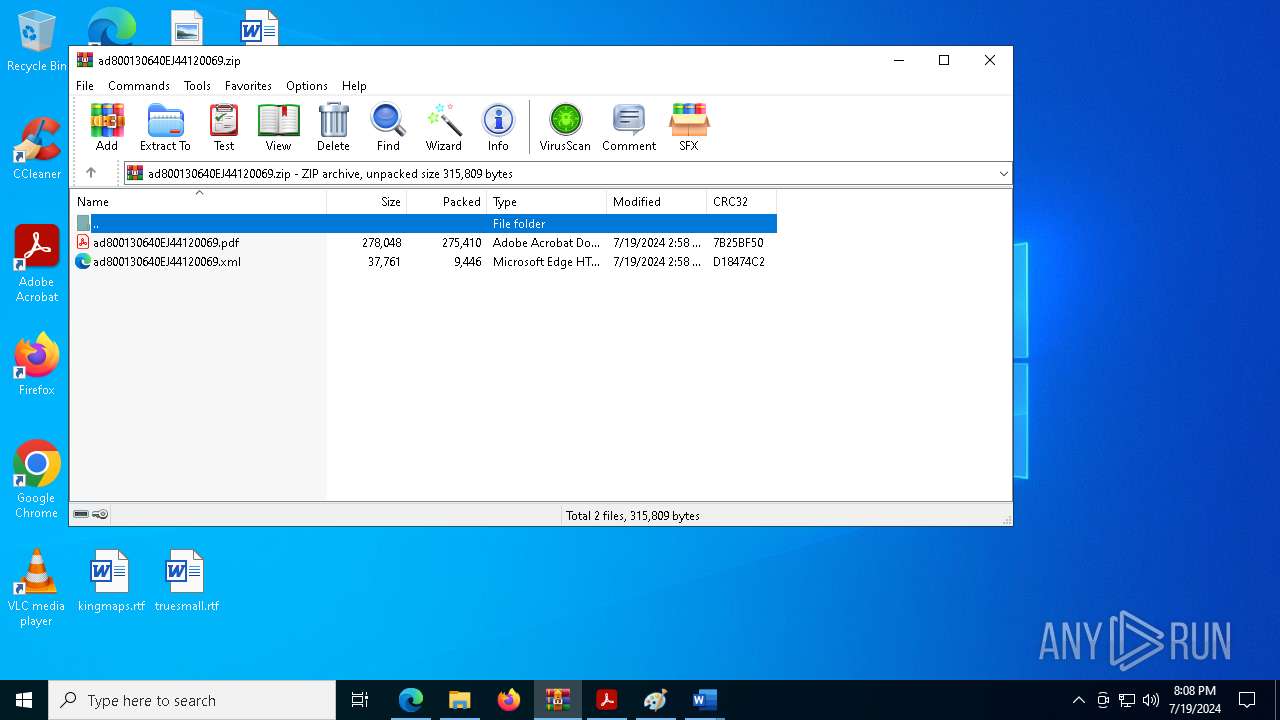
| File name: | ad800130640EJ44120069.zip |
| Full analysis: | https://app.any.run/tasks/7ea0457a-97fe-4e53-91d7-3a9b21a6bf87 |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 20:03:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 692799BE19EAE5B8B8C694C15C1D4FD3 |
| SHA1: | 99E6DFD9E047251B05A758D00287B3DD8F6B8001 |
| SHA256: | CC72A45F5675C024565F57D440B2DBF81A4FD6637ABB5645846216AFEBBC1786 |
| SSDEEP: | 6144:0MZ6uf83Li8a5gx9Yq/oj0xWt8u7wrDTT/xV9ZK5vKEji3a1CUxbdN3YzCbuj/gi:zZdaME4v/7IDoBriK17bd9YzIS/ |
MALICIOUS
Scans artifacts that could help determine the target
- OfficeClickToRun.exe (PID: 2868)
The DLL Hijacking
- OfficeClickToRun.exe (PID: 2868)
Creates a writable file in the system directory
- OfficeClickToRun.exe (PID: 2868)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2112)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 2868)
Checks Windows Trust Settings
- OfficeClickToRun.exe (PID: 2868)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 2112)
- msedge.exe (PID: 8140)
- OfficeClickToRun.exe (PID: 2868)
Application launched itself
- AcroCEF.exe (PID: 7284)
- Acrobat.exe (PID: 3068)
- msedge.exe (PID: 8140)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 3628)
Checks supported languages
- acrobat_sl.exe (PID: 6120)
- identity_helper.exe (PID: 7512)
- OfficeClickToRun.exe (PID: 2868)
Reads the computer name
- identity_helper.exe (PID: 7512)
- OfficeClickToRun.exe (PID: 2868)
Manual execution by a user
- mspaint.exe (PID: 1020)
- WINWORD.EXE (PID: 3624)
- WINWORD.EXE (PID: 6268)
- WINWORD.EXE (PID: 7516)
Process checks computer location settings
- OfficeClickToRun.exe (PID: 2868)
Reads the software policy settings
- OfficeClickToRun.exe (PID: 2868)
Reads Environment values
- OfficeClickToRun.exe (PID: 2868)
Reads CPU info
- OfficeClickToRun.exe (PID: 2868)
Reads the machine GUID from the registry
- OfficeClickToRun.exe (PID: 2868)
Checks proxy server information
- OfficeClickToRun.exe (PID: 2868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:19 14:58:12 |
| ZipCRC: | 0x7b25bf50 |
| ZipCompressedSize: | 275410 |
| ZipUncompressedSize: | 278048 |
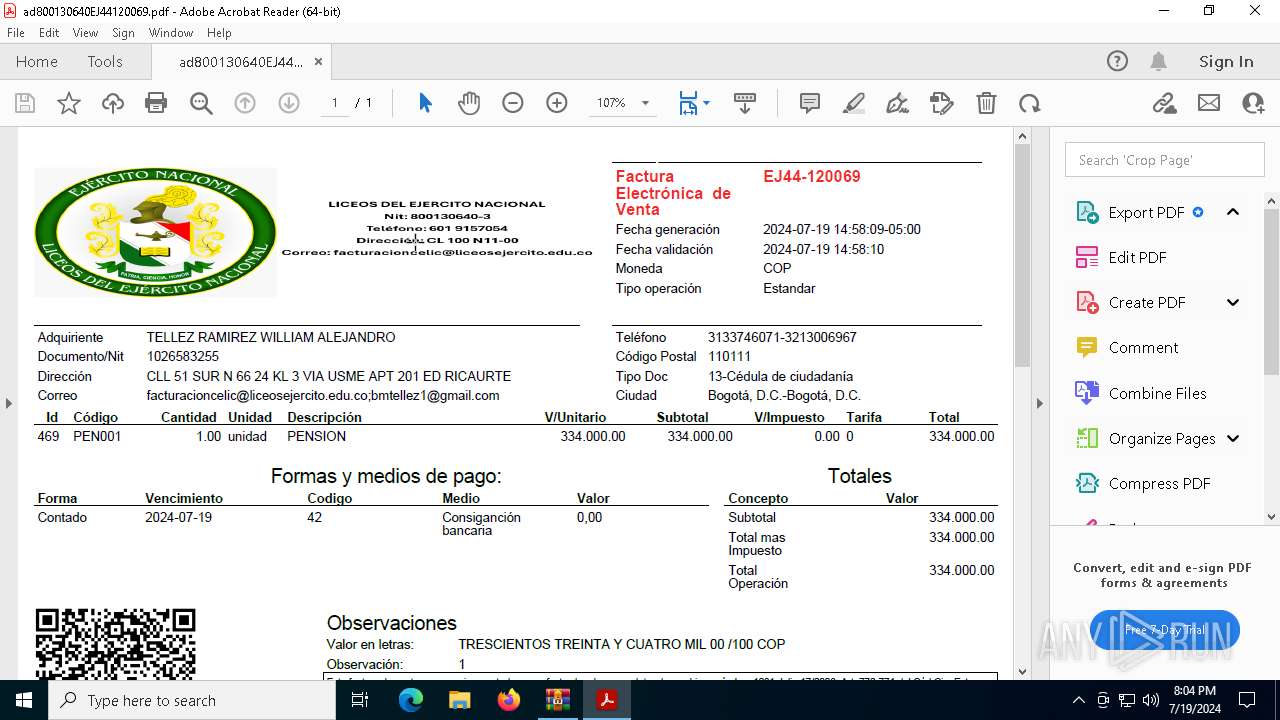
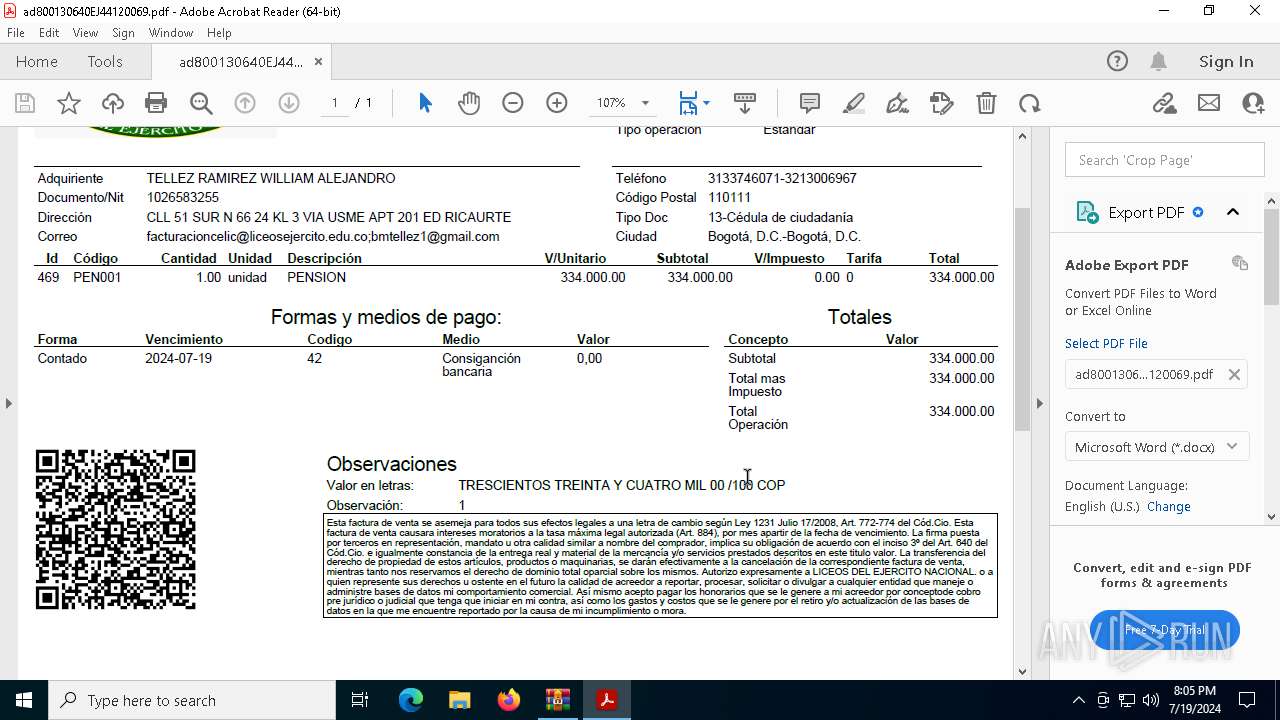
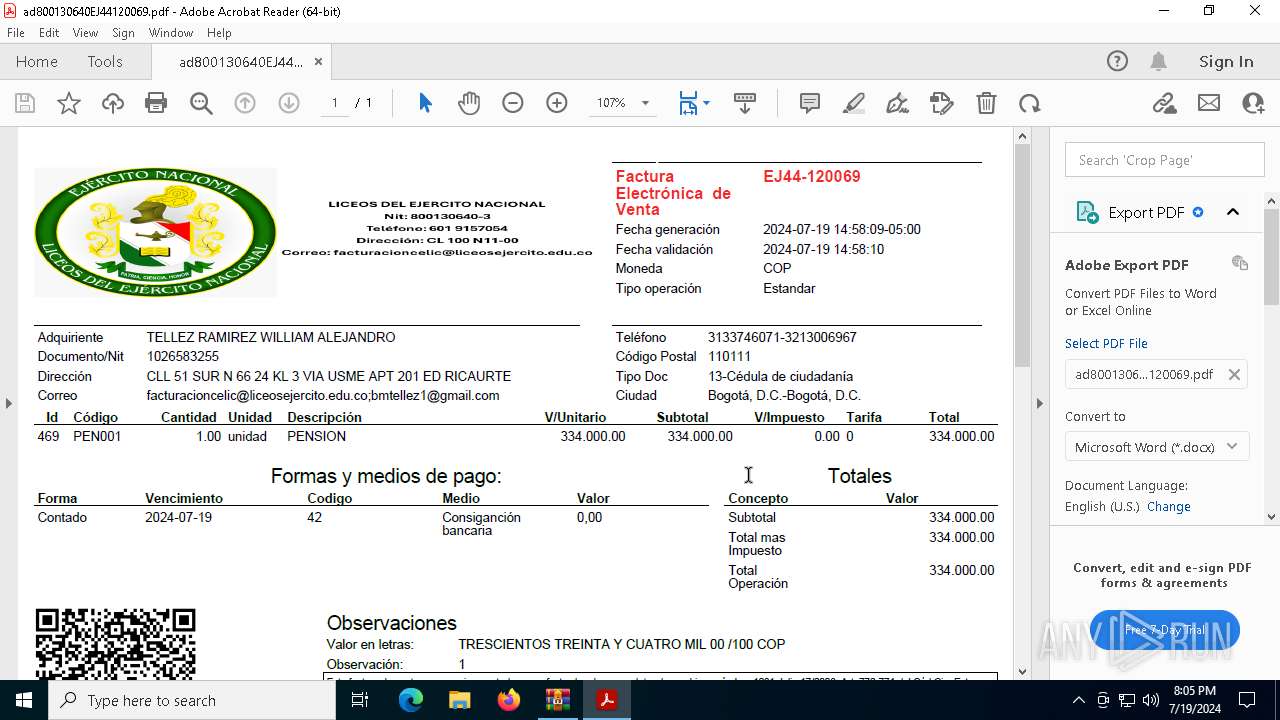
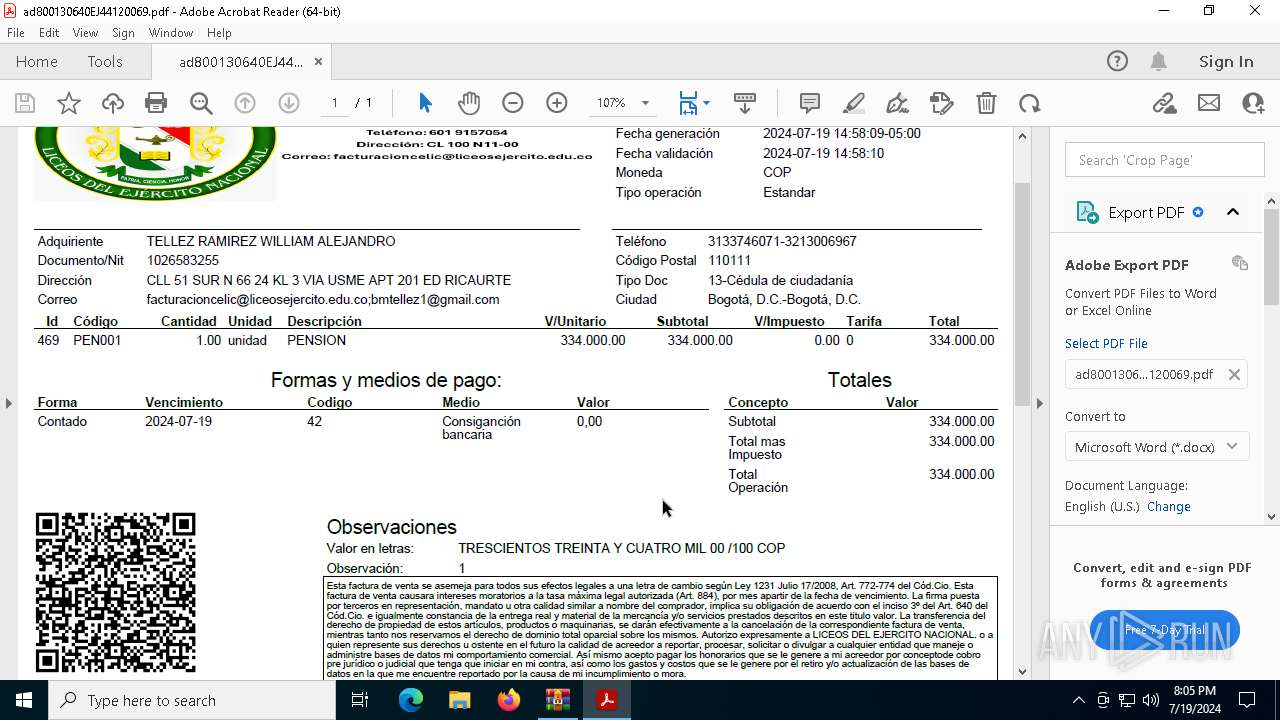
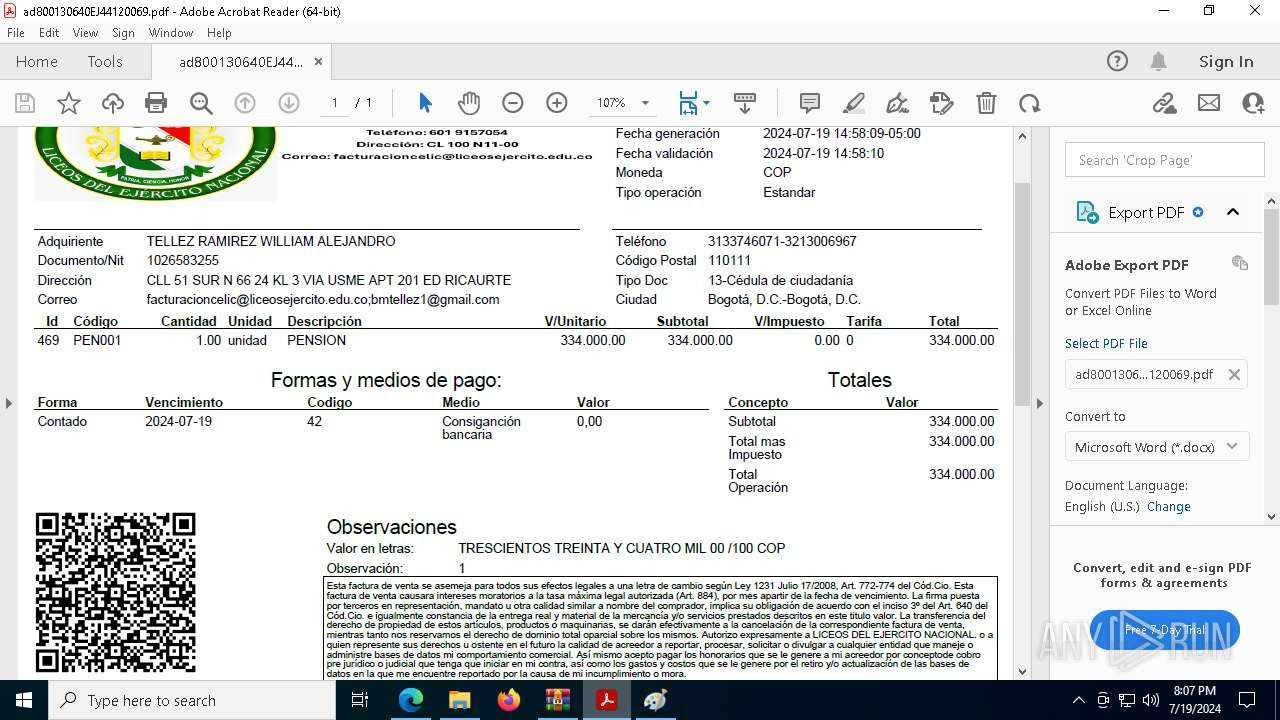
| ZipFileName: | ad800130640EJ44120069.pdf |
Total processes
204
Monitored processes
50
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Downloads\organizationsremote.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6328 --field-trial-handle=2424,i,1251545608342406848,10653750107903908607,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1220 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x2ec,0x2f0,0x2f4,0x2e8,0x2fc,0x7ffd90135fd8,0x7ffd90135fe4,0x7ffd90135ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1324 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=6480 --field-trial-handle=2424,i,1251545608342406848,10653750107903908607,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=4232 --field-trial-handle=2424,i,1251545608342406848,10653750107903908607,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1580 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2744 --field-trial-handle=2424,i,1251545608342406848,10653750107903908607,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1596 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2564 --field-trial-handle=2424,i,1251545608342406848,10653750107903908607,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1960 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2444 --field-trial-handle=1580,i,2299518483463213138,12631189324322370402,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2112 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\ad800130640EJ44120069.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2140 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1608 --field-trial-handle=1580,i,2299518483463213138,12631189324322370402,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
89 556
Read events
88 516
Write events
985
Delete events
55
Modification events
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ad800130640EJ44120069.zip | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | Acrobat.Document.DC_.pdf |
Value: 0 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.pdf\OpenWithProgids |
| Operation: | write | Name: | Acrobat.Document.DC |
Value: | |||
Executable files
2
Suspicious files
235
Text files
74
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4168 | Acrobat.exe | C:\USERS\ADMIN\APPDATA\LOCAL\ADOBE\ACROBAT\DC\SOPHIA\ACROBAT\SOPHIA.JSON | binary | |
MD5:79270D9595B259B53E39403366436A8E | SHA256:AD0552A8B392315C512F6DC945F318AD83B98FB64415C0CED694843A3C5D2083 | |||
| 4168 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\acroNGLLog.txt | text | |
MD5:15A11D20912FD39C09B557699AC08E42 | SHA256:F6B93561AD5DCCA3B3E9A5F607AA314F9CE73446780BB4EA5F0296E73EDD846A | |||
| 3068 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | ps | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 4168 | Acrobat.exe | C:\USERS\ADMIN\APPDATA\LOCAL\ADOBE\ACROBAT\DC\SHAREDDATAEVENTS | sqlite | |
MD5:7682D408BD1BC36E8C243025EC308E38 | SHA256:8422BB7439DBCC23606BB527D83C537C9A350688C4E54DA296D898F2376B1D7D | |||
| 7284 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old | text | |
MD5:EC382FFF4B7232181CDB8226E9C289C7 | SHA256:27BDA724E8E0654E4BDA2F8E98FE399EF826F052F73FBBDB19CDF78954DB9954 | |||
| 4168 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | mp3 | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 7284 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old | text | |
MD5:43D1F53B48631F8B32E040219417874B | SHA256:AA4C99C362EB18EB8B91EEB8821960807F725E7C5DE1FBABBA7B910BDA3EEEB8 | |||
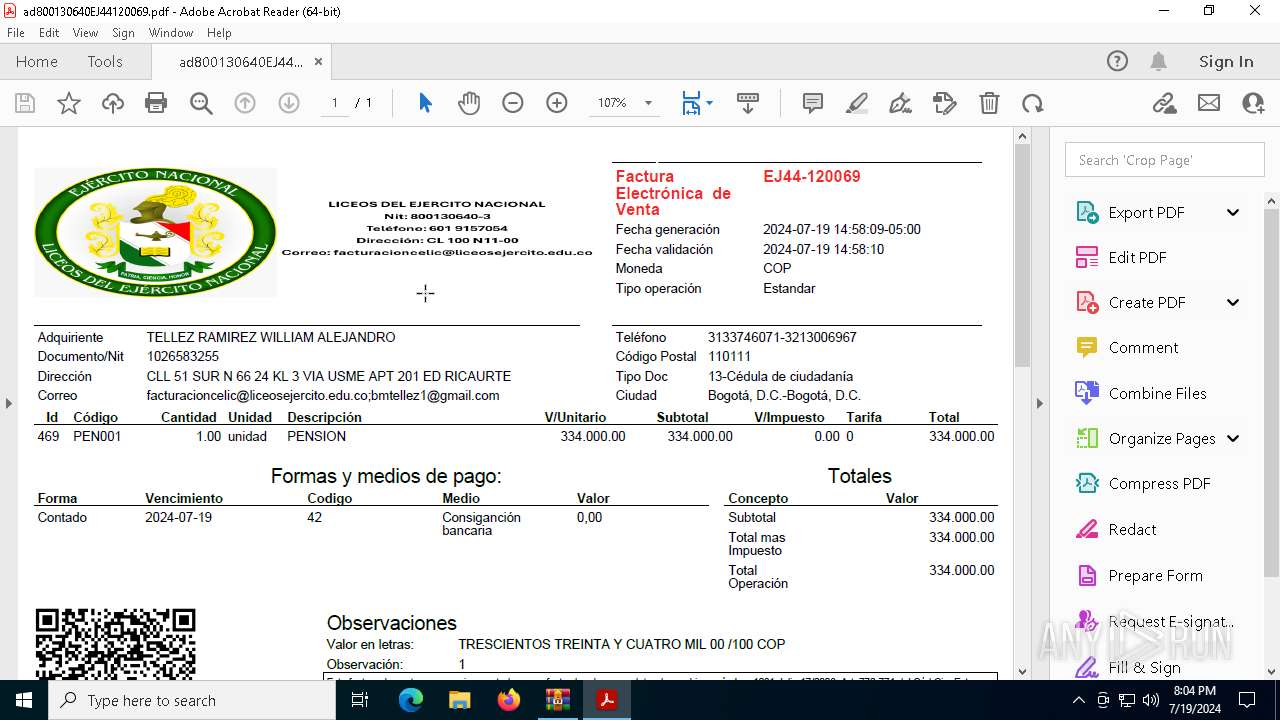
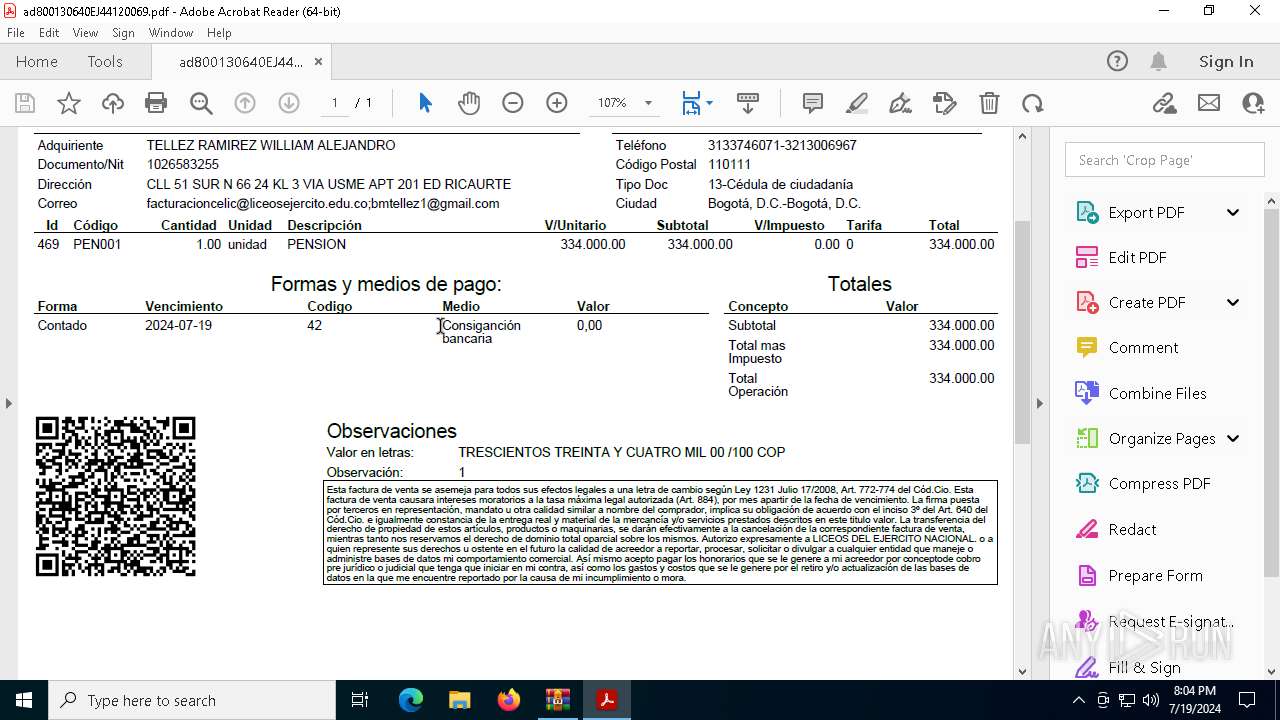
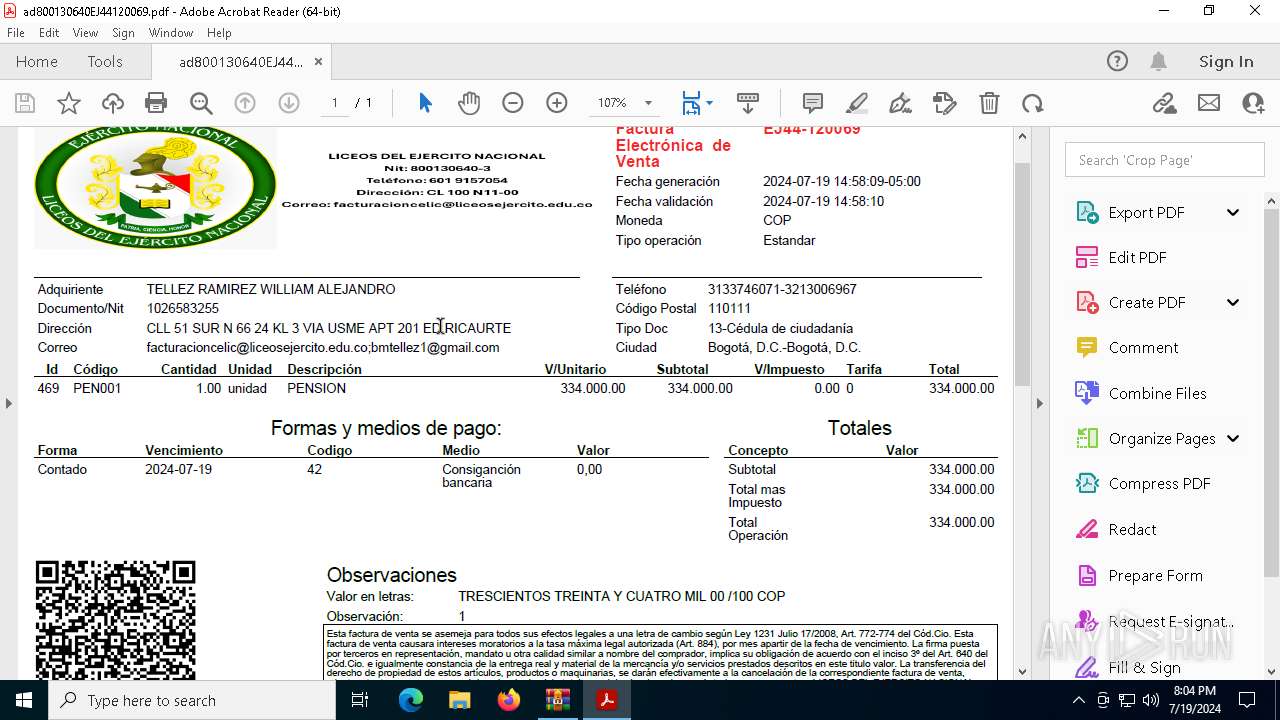
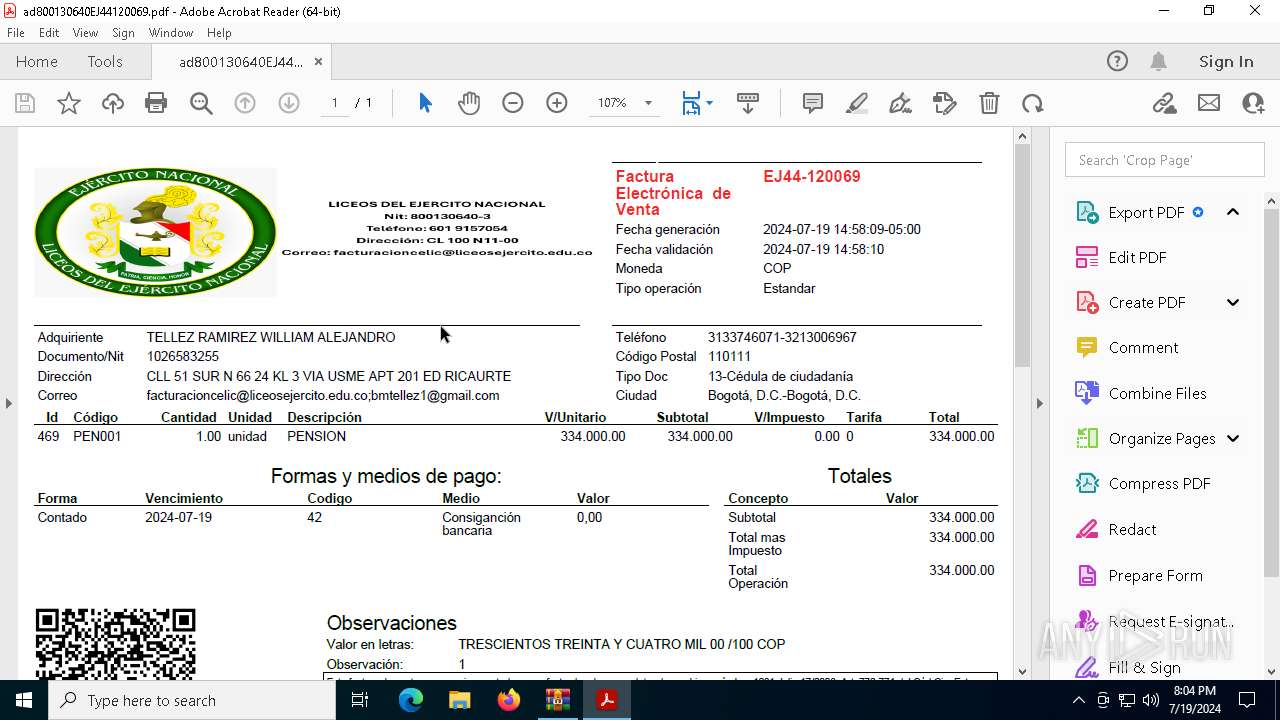
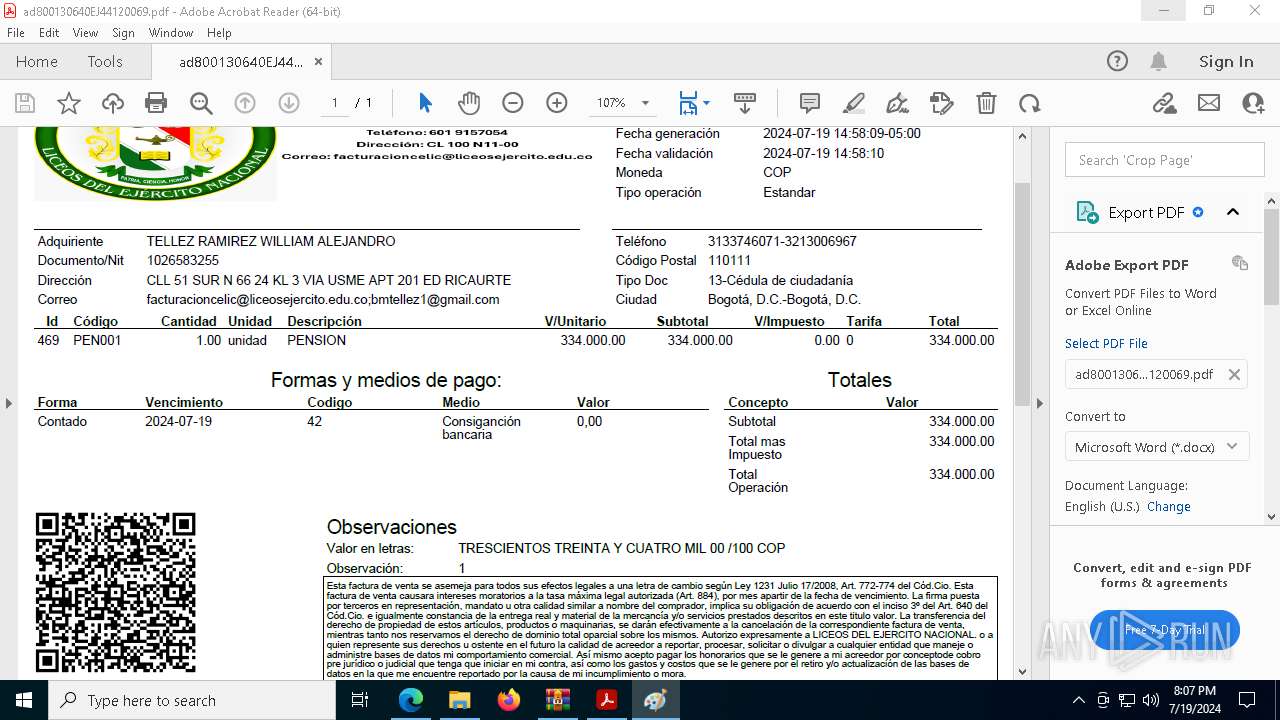
| 2112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2112.25684\ad800130640EJ44120069.pdf | ||
MD5:1B02811965B8E5E23136F71672809857 | SHA256:B0D351A2D9D6D7CC1C733F9DF3719C30DCAA806565A5D62D55EB724B3EADED88 | |||
| 7284 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old~RF42d502.TMP | text | |
MD5:E26AF4B6A1AD62E54D67510EEFE20B2C | SHA256:BF001234CF5F261254DEA1EA459BBFD4A35D15166C765CA3ED9B56D49A04BE1B | |||
| 7284 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:727E4AA0BC2CCDE2E45409FBC946C160 | SHA256:4C8D0E4EC3335F6DA6DF3C58BF273DF6D2E22217648D035851A123089E839A2C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
93
DNS requests
58
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3628 | AdobeARM.exe | GET | 304 | 23.48.23.54:80 | http://acroipm2.adobe.com/assets/Owner/arm/ProcessMAU.txt | unknown | — | — | whitelisted |
3628 | AdobeARM.exe | GET | 404 | 23.48.23.54:80 | http://acroipm2.adobe.com/assets/Owner/arm/2024/7/OwnerAPI/Rdr.txt | unknown | — | — | whitelisted |
3628 | AdobeARM.exe | GET | 404 | 23.48.23.54:80 | http://acroipm2.adobe.com/assets/Owner/arm/2024/7/UC/Other.txt | unknown | — | — | whitelisted |
3628 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
3628 | AdobeARM.exe | GET | 404 | 23.48.23.54:80 | http://acroipm2.adobe.com/assets/Owner/arm/29/adnme/NoValidReasonForAdnme.txt | unknown | — | — | whitelisted |
3068 | Acrobat.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
3624 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
3624 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3628 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA0aNA9419AA4In9uq1lIt8%3D | unknown | — | — | whitelisted |
3628 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4716 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7856 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2760 | svchost.exe | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6488 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4716 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5620 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |