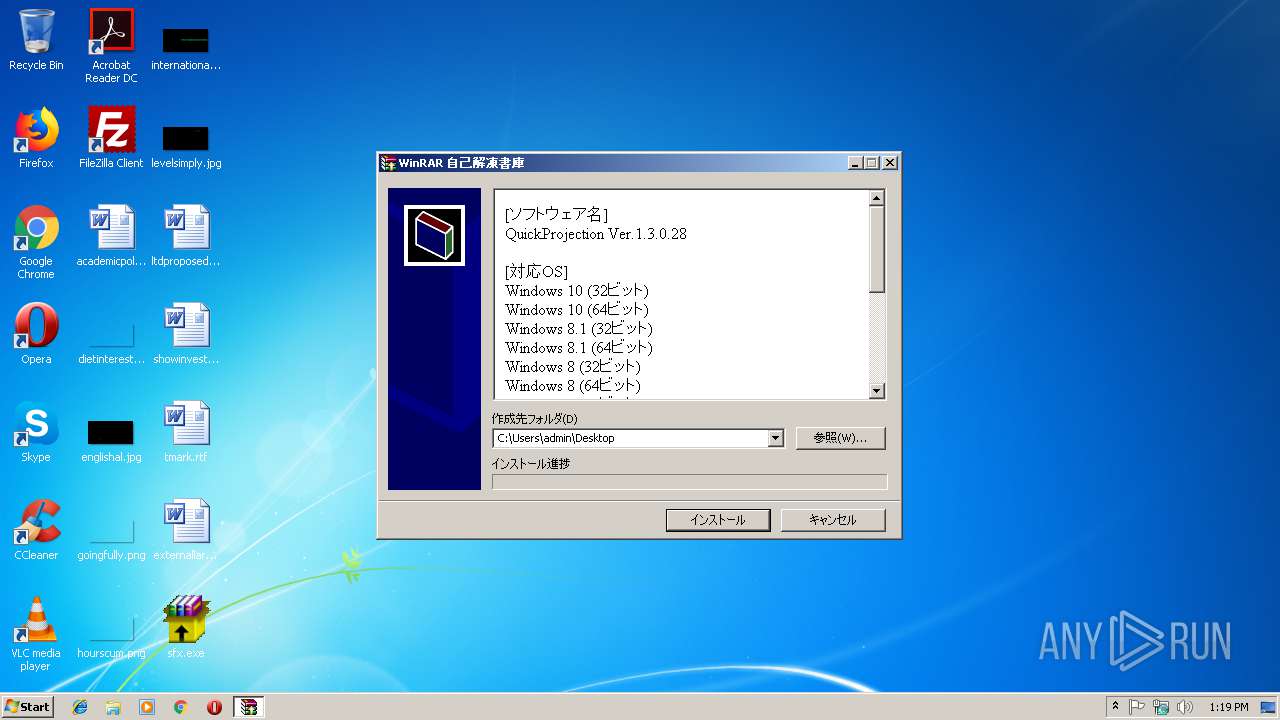
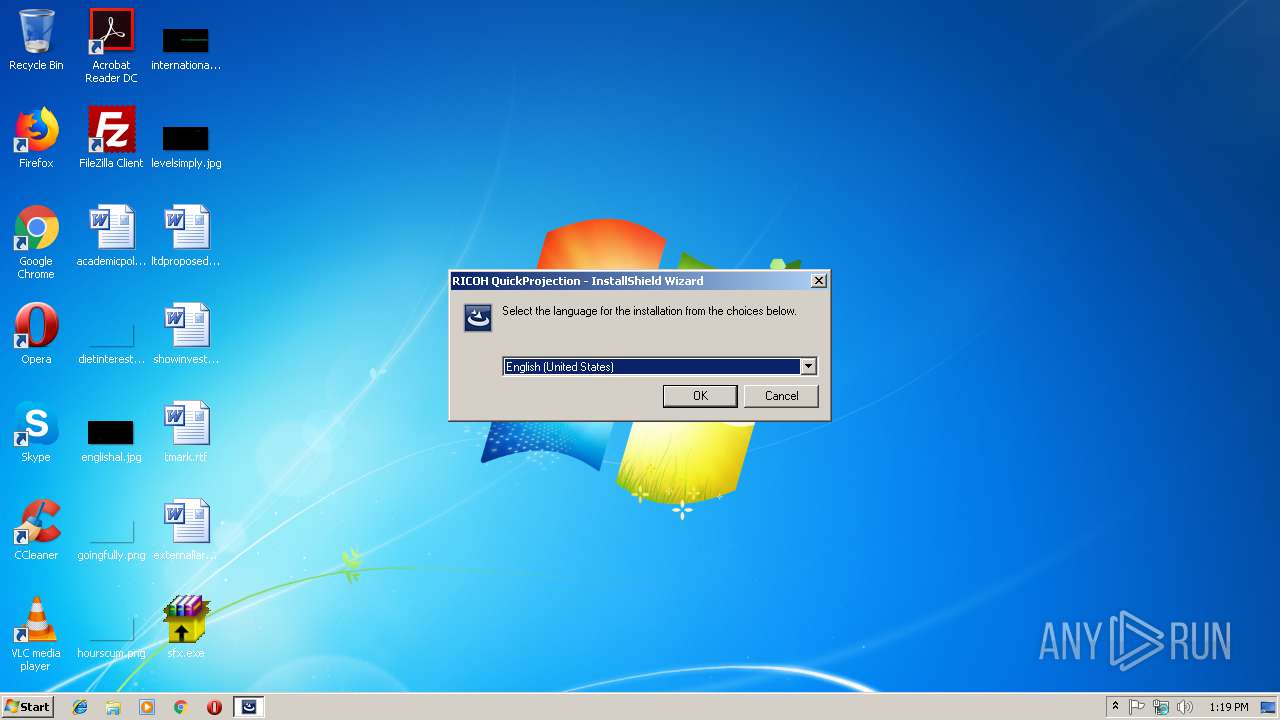
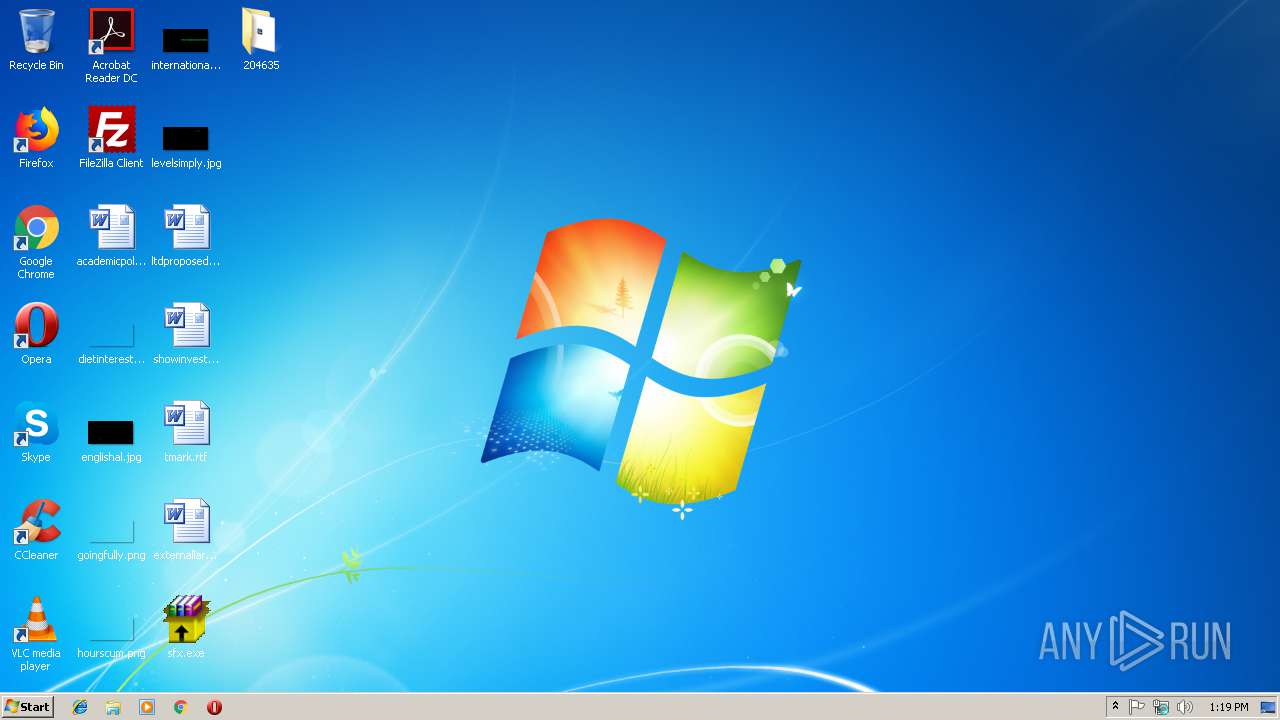
| File name: | sfx.exe |
| Full analysis: | https://app.any.run/tasks/6d35ad9c-5c94-4504-87c1-b364cd0617f8 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 13:19:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2CEADA9FF365C2270D4F5009559F6317 |
| SHA1: | FA20D954BDBCE36FC4C2A43E4D7398C5FFCF7953 |
| SHA256: | CC4AF00148C278BA5D22FBF13ABBDF0CE6832B6941B617F6794EEE6BCED60C61 |
| SSDEEP: | 49152:nJqi6DGIafdSjrBNGgMFOdJe+LvahKKBo0/0u1YwRdDEOwKGdfdZStr0+253f0ey:JD5IrR/2ONoKKBN/pyYwXKt4+25vxRlw |
MALICIOUS
Application was dropped or rewritten from another process
- setup.exe (PID: 3824)
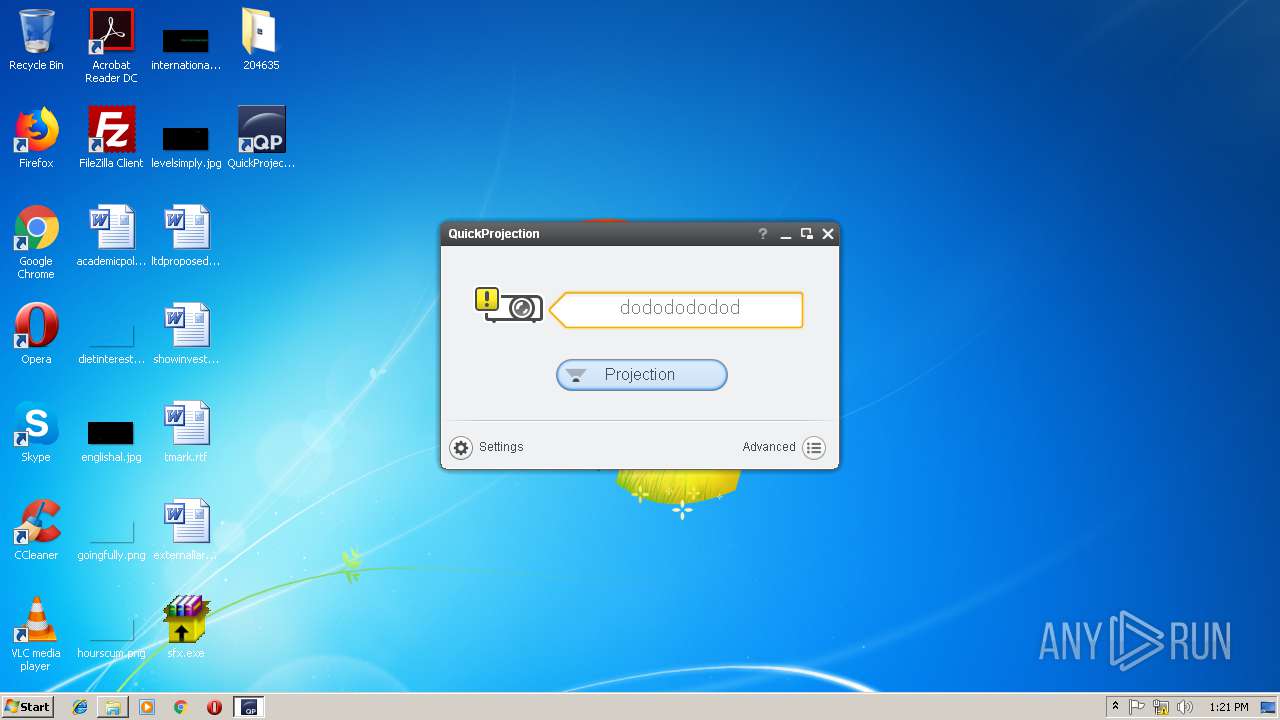
- AdhocSettingService.exe (PID: 3736)
- QuickProjection.exe (PID: 2308)
SUSPICIOUS
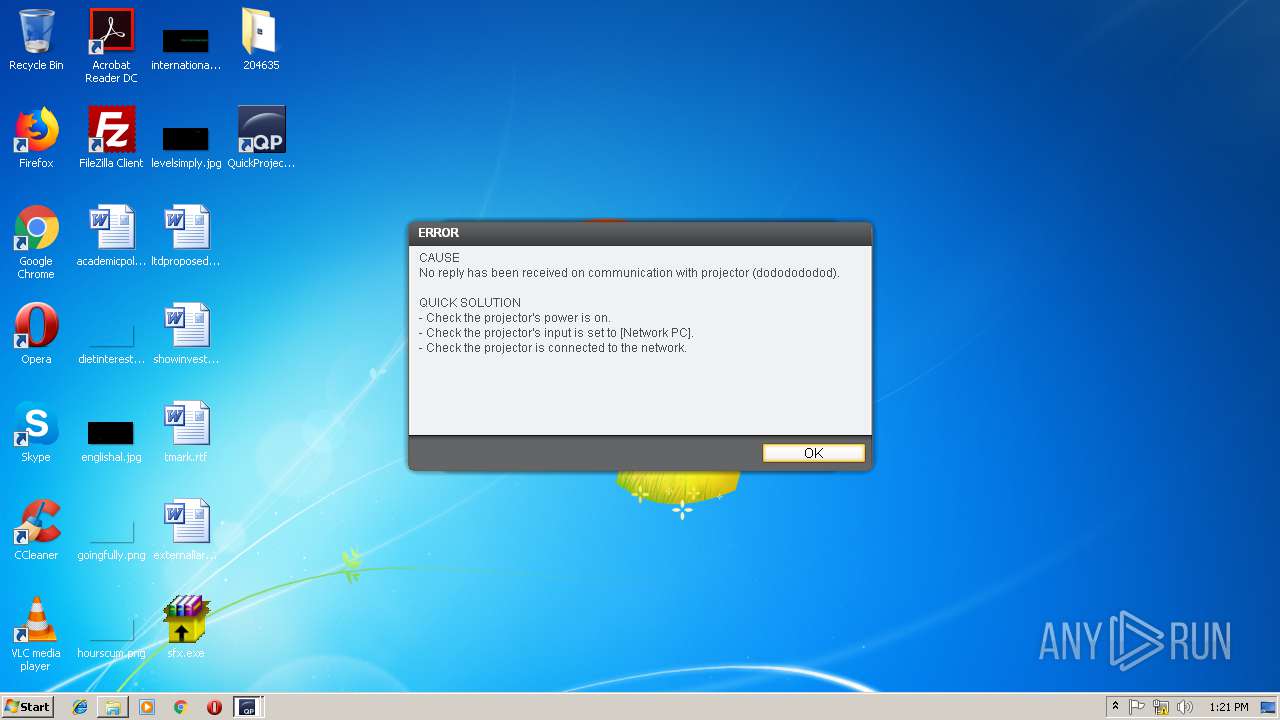
Reads internet explorer settings
- sfx.exe (PID: 3760)
Starts Microsoft Installer
- setup.exe (PID: 3824)
Executable content was dropped or overwritten
- sfx.exe (PID: 3760)
- setup.exe (PID: 3824)
- msiexec.exe (PID: 3212)
Creates files in the user directory
- QuickProjection.exe (PID: 2308)
INFO
Low-level read access rights to disk partition
- vssvc.exe (PID: 2140)
Searches for installed software
- msiexec.exe (PID: 3212)
Creates files in the program directory
- msiexec.exe (PID: 3212)
Creates a software uninstall entry
- msiexec.exe (PID: 3212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:08:14 21:15:49+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 188416 |
| InitializedDataSize: | 196096 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1cab5 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 14-Aug-2016 19:15:49 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 14-Aug-2016 19:15:49 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002DFE8 | 0x0002E000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.71025 |
.rdata | 0x0002F000 | 0x000099D0 | 0x00009A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.15287 |
.data | 0x00039000 | 0x0001F8B8 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.29547 |
.gfids | 0x00059000 | 0x000000F0 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.12367 |
.rsrc | 0x0005A000 | 0x00004680 | 0x00004800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.63811 |
.reloc | 0x0005F000 | 0x00001F8C | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.62986 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.88998 | 1384 | UNKNOWN | English - United States | RT_ICON |
3 | 4.12176 | 744 | UNKNOWN | English - United States | RT_ICON |
4 | 4.68705 | 2216 | UNKNOWN | English - United States | RT_ICON |
7 | 3.1586 | 482 | UNKNOWN | English - United States | RT_STRING |
8 | 3.11685 | 460 | UNKNOWN | English - United States | RT_STRING |
9 | 3.15447 | 494 | UNKNOWN | English - United States | RT_STRING |
10 | 2.99727 | 326 | UNKNOWN | English - United States | RT_STRING |
11 | 3.2036 | 1094 | UNKNOWN | English - United States | RT_STRING |
12 | 3.12889 | 358 | UNKNOWN | English - United States | RT_STRING |
Imports
COMCTL32.dll (delay-loaded) |
KERNEL32.dll |
Total processes
42
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2140 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
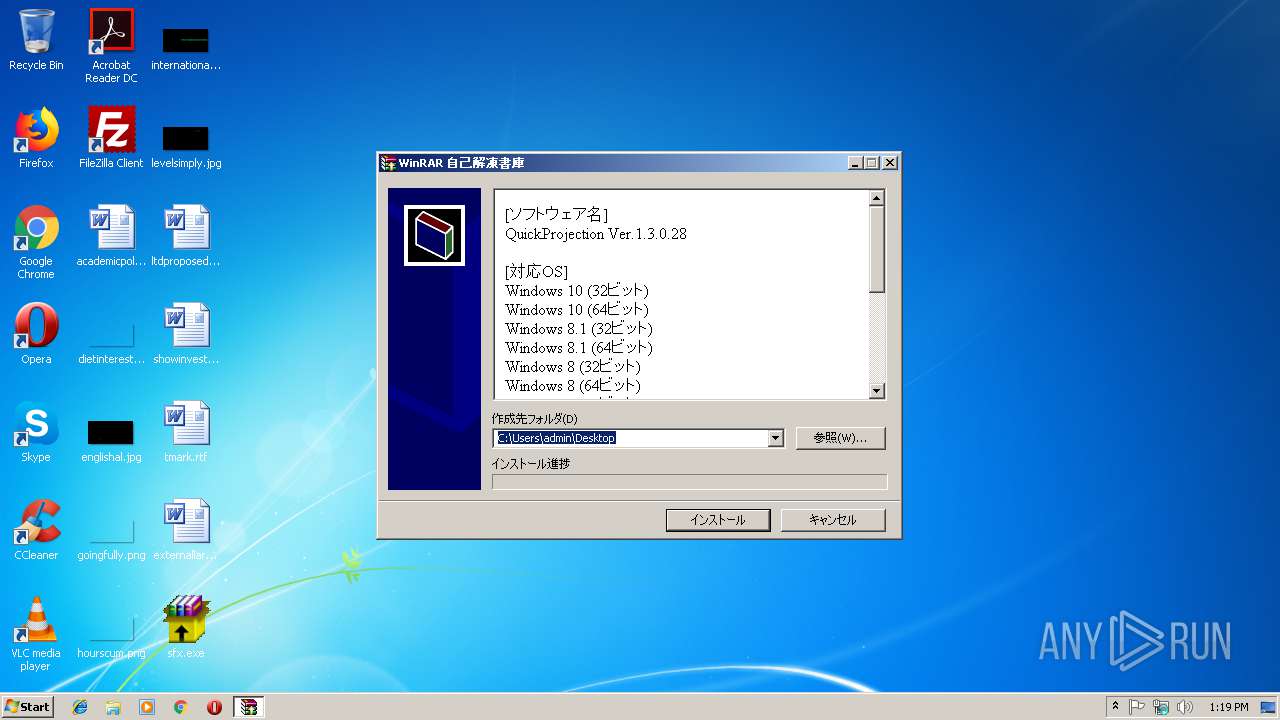
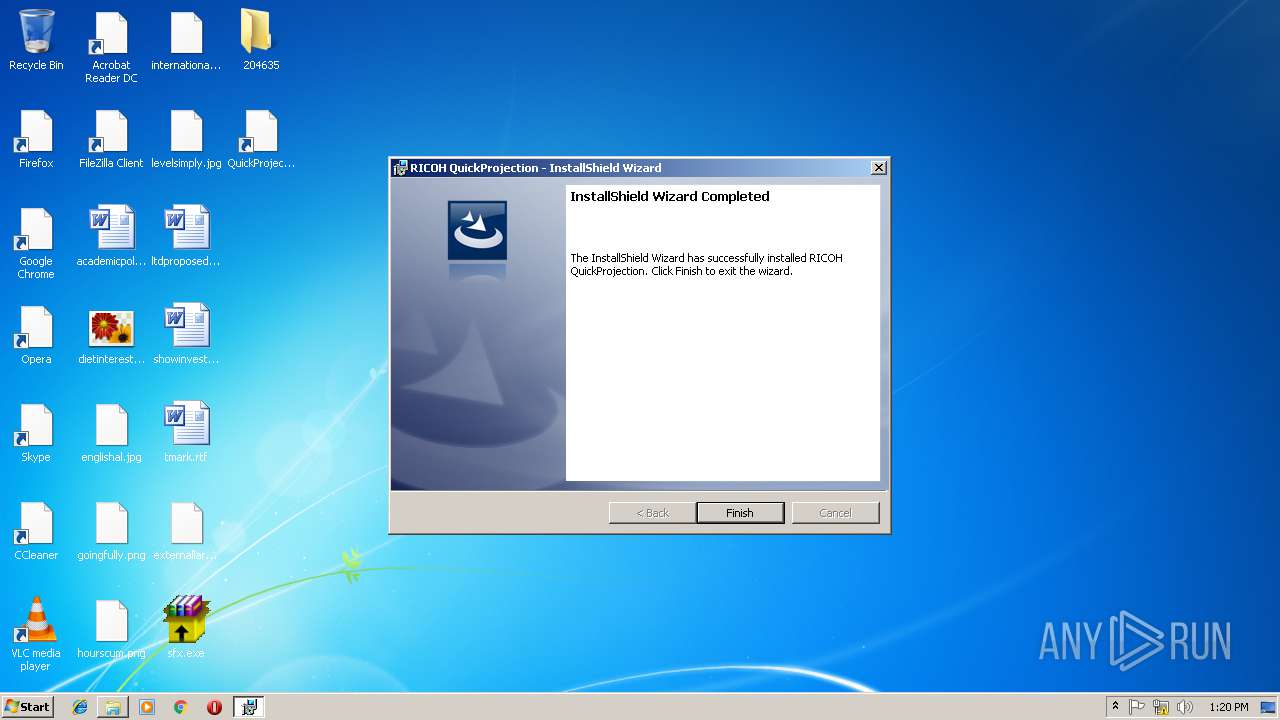
| 2308 | "C:\Program Files\Ricoh\QuickProjection\QuickProjection.exe" | C:\Program Files\Ricoh\QuickProjection\QuickProjection.exe | explorer.exe | ||||||||||||
User: admin Company: RICOH Integrity Level: MEDIUM Description: QuickProjection Exit code: 0 Version: 1.3.0.28 Modules
| |||||||||||||||
| 3096 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "00000550" "00000330" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3212 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3736 | "C:\Program Files\Ricoh\QuickProjection\AdhocSettingService.exe" | C:\Program Files\Ricoh\QuickProjection\AdhocSettingService.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 3760 | "C:\Users\admin\Desktop\sfx.exe" | C:\Users\admin\Desktop\sfx.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3824 | "C:\Users\admin\Desktop\204635\setup.exe" -i | C:\Users\admin\Desktop\204635\setup.exe | sfx.exe | ||||||||||||
User: admin Company: Ricoh Integrity Level: MEDIUM Description: Setup Launcher Unicode Exit code: 0 Version: 1.3.0.28 Modules
| |||||||||||||||
| 4012 | MSIEXEC.EXE /i "C:\Users\admin\AppData\Local\Temp\{BD343DB5-63FC-43A3-82C1-0D442A34B730}\RICOH QuickProjection.msi" TRANSFORMS="C:\Users\admin\AppData\Local\Temp\{BD343DB5-63FC-43A3-82C1-0D442A34B730}\1033.MST" SETUPEXEDIR="C:\Users\admin\Desktop\204635" SETUPEXENAME="setup.exe" | C:\Windows\system32\MSIEXEC.EXE | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
726
Read events
466
Write events
246
Delete events
14
Modification events
| (PID) Process: | (3760) sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3760) sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3212) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000FAE68669668DD4018C0C0000340F0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3212) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000FAE68669668DD4018C0C0000340F0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3212) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 20 | |||
| (PID) Process: | (3212) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000F6A5076A668DD4018C0C0000340F0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3212) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000050080A6A668DD4018C0C0000E80D0000E8030000010000000000000000000000403345210F1C374387E6E33A5F735D200000000000000000 | |||
| (PID) Process: | (2140) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000088A4266A668DD4015C0800005C0E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2140) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000088A4266A668DD4015C080000440A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2140) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000088A4266A668DD4015C080000740E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
10
Suspicious files
12
Text files
414
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isD811.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isD812.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isD823.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isD824.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isD825.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isD826.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isD836.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isD837.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isD838.tmp | — | |
MD5:— | SHA256:— | |||
| 3824 | setup.exe | C:\Users\admin\AppData\Local\Temp\_isFC5C.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report