| File name: | tester24.exe |
| Full analysis: | https://app.any.run/tasks/9de36932-f417-4162-8a3d-2ebc83592e5e |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 19:56:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | CCC55A779EB8229B2D0D25DC7DCA7CD6 |
| SHA1: | 87665B98EC3C206AC340F151D6DDFD7DF6F09438 |
| SHA256: | CC46727AC1B4EE6D01DCC26FFF9C11F8EAB488C108A8AF936746C041CB7C4DB9 |
| SSDEEP: | 98304:DC3CpAvVWbKQdLKbLylu/ZUmTv4I9XLDbenkuA83wpYp2twmmdgIdwT+spTx8tXh:Wwdls881mwmNuEM491+jg |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- tester24.exe (PID: 1232)
SUSPICIOUS
Process drops python dynamic module
- tester24.exe (PID: 6704)
Executable content was dropped or overwritten
- tester24.exe (PID: 6704)
Process drops legitimate windows executable
- tester24.exe (PID: 6704)
The process drops C-runtime libraries
- tester24.exe (PID: 6704)
Application launched itself
- tester24.exe (PID: 6704)
Loads Python modules
- tester24.exe (PID: 1232)
Starts CMD.EXE for commands execution
- tester24.exe (PID: 1232)
- forfiles.exe (PID: 2356)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4580)
Reads the date of Windows installation
- tester24.exe (PID: 1232)
Searches and executes a command on selected files
- forfiles.exe (PID: 2356)
Reads security settings of Internet Explorer
- tester24.exe (PID: 1232)
The process exported the data from the registry
- WSCollect.exe (PID: 4084)
Executes as Windows Service
- dllhost.exe (PID: 6368)
- msdtc.exe (PID: 4348)
There is functionality for taking screenshot (YARA)
- tester24.exe (PID: 6704)
- tester24.exe (PID: 1232)
Reads the history of recent RDP connections
- wksprt.exe (PID: 4456)
INFO
Checks supported languages
- tester24.exe (PID: 6704)
- tester24.exe (PID: 1232)
- curl.exe (PID: 5148)
- pospaymentsworker.exe (PID: 4104)
- expand.exe (PID: 5244)
- agentactivationruntimestarter.exe (PID: 5204)
- deploymentcsphelper.exe (PID: 4760)
Reads the computer name
- tester24.exe (PID: 6704)
- tester24.exe (PID: 1232)
- agentactivationruntimestarter.exe (PID: 5204)
The sample compiled with english language support
- tester24.exe (PID: 6704)
Create files in a temporary directory
- tester24.exe (PID: 6704)
- WSCollect.exe (PID: 4084)
- reg.exe (PID: 1604)
- reg.exe (PID: 728)
- FXSSVC.exe (PID: 7140)
- ddodiag.exe (PID: 5196)
Creates files or folders in the user directory
- mcbuilder.exe (PID: 1660)
- Magnify.exe (PID: 6512)
Reads the software policy settings
- TsWpfWrp.exe (PID: 6360)
Checks proxy server information
- TsWpfWrp.exe (PID: 6360)
Process checks computer location settings
- tester24.exe (PID: 1232)
Reads security settings of Internet Explorer
- TsWpfWrp.exe (PID: 6360)
- Magnify.exe (PID: 6512)
Reads the time zone
- MusNotifyIcon.exe (PID: 2972)
Execution of CURL command
- tester24.exe (PID: 1232)
Creates files in the program directory
- MusNotifyIcon.exe (PID: 2972)
Checks transactions between databases Windows and Oracle
- dllhost.exe (PID: 6368)
- msdtc.exe (PID: 4348)
- mtstocom.exe (PID: 4380)
PyInstaller has been detected (YARA)
- tester24.exe (PID: 6704)
- tester24.exe (PID: 1232)
Disables trace logs
- cmmon32.exe (PID: 320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:21 19:55:33+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 174592 |
| InitializedDataSize: | 157184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd0d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
287
Monitored processes
150
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Windows\System32\cmmon32.exe" | C:\Windows\System32\cmmon32.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Connection Manager Monitor Exit code: 0 Version: 7.2.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | "C:\Windows\System32\ieUnatt.exe" | C:\Windows\System32\ieUnatt.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IE 7.0 Unattended Install Utility Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | C:\WINDOWS\System32\reg.exe export "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters\DnsPolicyConfig" "C:\Users\admin\AppData\Local\Temp\registry_DNSPolicy.txt" /y | C:\Windows\System32\reg.exe | — | WSCollect.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | "C:\Windows\System32\winrs.exe" | C:\Windows\System32\winrs.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: winrs Exit code: 87 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | "C:\Windows\System32\dfrgui.exe" | C:\Windows\System32\dfrgui.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Drive Optimizer Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | "C:\Windows\System32\vds.exe" | C:\Windows\System32\vds.exe | tester24.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | "C:\Windows\System32\relog.exe" | C:\Windows\System32\relog.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Performance Relogging Utility Exit code: 11 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\Windows\System32\TRACERT.EXE" | C:\Windows\System32\TRACERT.EXE | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Traceroute Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | gpupdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\Windows\System32\WallpaperHost.exe" | C:\Windows\System32\WallpaperHost.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Wallpaper Host Process Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 590
Read events
20 240
Write events
330
Delete events
20
Modification events
| (PID) Process: | (1660) mcbuilder.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\CMF\Config |
| Operation: | write | Name: | SYSTEM |
Value: 3 | |||
| (PID) Process: | (1660) mcbuilder.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\CMF\Config |
| Operation: | delete value | Name: | SYSTEM-LP |
Value: | |||
| (PID) Process: | (6368) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Ole\Instrumentation |
| Operation: | write | Name: | InstrumentationLogFileDir |
Value: C:\WINDOWS\system32\com | |||
| (PID) Process: | (4216) UpgradeResultsUI.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsAnytimeUpgrade |
| Operation: | write | Name: | Status |
Value: 2 | |||
| (PID) Process: | (1128) WallpaperHost.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | TranscodedImageCount |
Value: 1 | |||
| (PID) Process: | (1128) WallpaperHost.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | delete value | Name: | TranscodedImageCache_000 |
Value: | |||
| (PID) Process: | (1128) WallpaperHost.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | LastUpdated |
Value: | |||
| (PID) Process: | (5068) BdeHdCfg.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5068) BdeHdCfg.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (5068) BdeHdCfg.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
55
Suspicious files
30
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_ctypes.pyd | executable | |
MD5:429CB0177D5AB205F289D0CC830549FF | SHA256:6E804ED42CCA2EB401A896FE9542201D4D77DF22ACBD935A3C56DC68530DAE33 | |||
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_hashlib.pyd | executable | |
MD5:692837EB1FCB73EF33A1474B18DFC7CD | SHA256:D674D53F7E2F906FBAF0D19AB871F9CFF53956D40B3CE003A2B4B44B549D4B92 | |||
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\_bz2.pyd | executable | |
MD5:51CA0713F8FD5F142625A44DF7ED7100 | SHA256:8768315B1E0E81CCD0D96C3D6A863803F5DD1DE6AF849285C439D61ABD32B647 | |||
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:E368A236F5676A3DA44E76870CD691C9 | SHA256:93C624B366BA16C643FC8933070A26F03B073AD0CF7F80173266D67536C61989 | |||
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\api-ms-win-core-fibers-l1-1-1.dll | executable | |
MD5:050A30A687E7A2FA6F086A0DB89AA131 | SHA256:FC9D86CEC621383EAB636EBC87DDD3F5C19A3CB2A33D97BE112C051D0B275429 | |||
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:226A5983AE2CBBF0C1BDA85D65948ABC | SHA256:591358EB4D1531E9563EE0813E4301C552CE364C912CE684D16576EABF195DC3 | |||
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\api-ms-win-core-fibers-l1-1-0.dll | executable | |
MD5:B5E2760C5A46DBEB8AE18C75F335707E | SHA256:91D249D7BC0E38EF6BCB17158B1FDC6DD8888DC086615C9B8B750B87E52A5FB3 | |||
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:416AA8314222DB6CBB3760856BE13D46 | SHA256:39095F59C41D76EC81BB2723D646FDE4C148E7CC3402F4980D2ADE95CB9C84F9 | |||
| 6704 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67042\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:CC228FF8D86B608E73026B1E9960B2F8 | SHA256:4CADBC0C39DA7C6722206FDCEBD670ABE5B8D261E7B041DD94F9397A89D1990D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
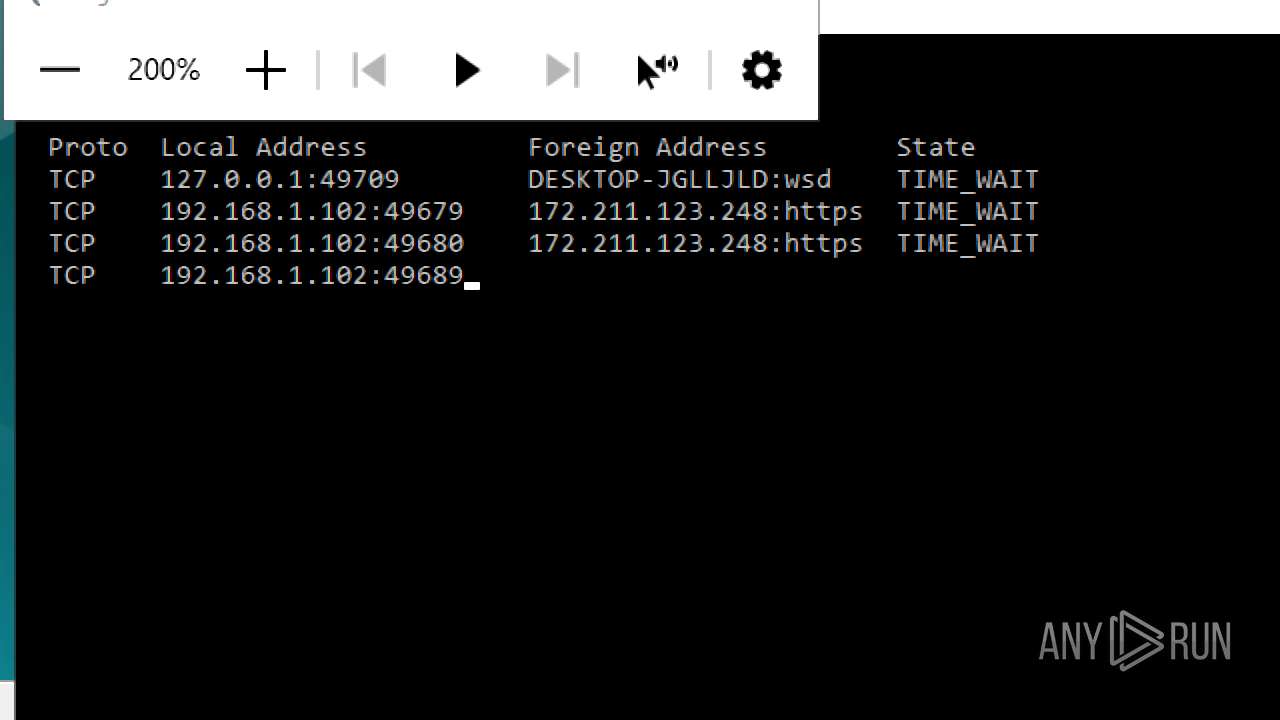
TCP/UDP connections
23
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5232 | RUXIMICS.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5232 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6360 | TsWpfWrp.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6360 | TsWpfWrp.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5232 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5232 | RUXIMICS.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
248.123.211.172.in-addr.arpa |
| unknown |
146.78.124.51.in-addr.arpa |
| unknown |
176.40.53.23.in-addr.arpa |
| unknown |
160.229.35.23.in-addr.arpa |
| unknown |
59.128.231.4.in-addr.arpa |
| unknown |
watson.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vds.exe | Error code for StartServiceCtrlDispatcher: 1063.
|
vds.exe | Error code for StartServiceCtrlDispatcher: 1063.
|