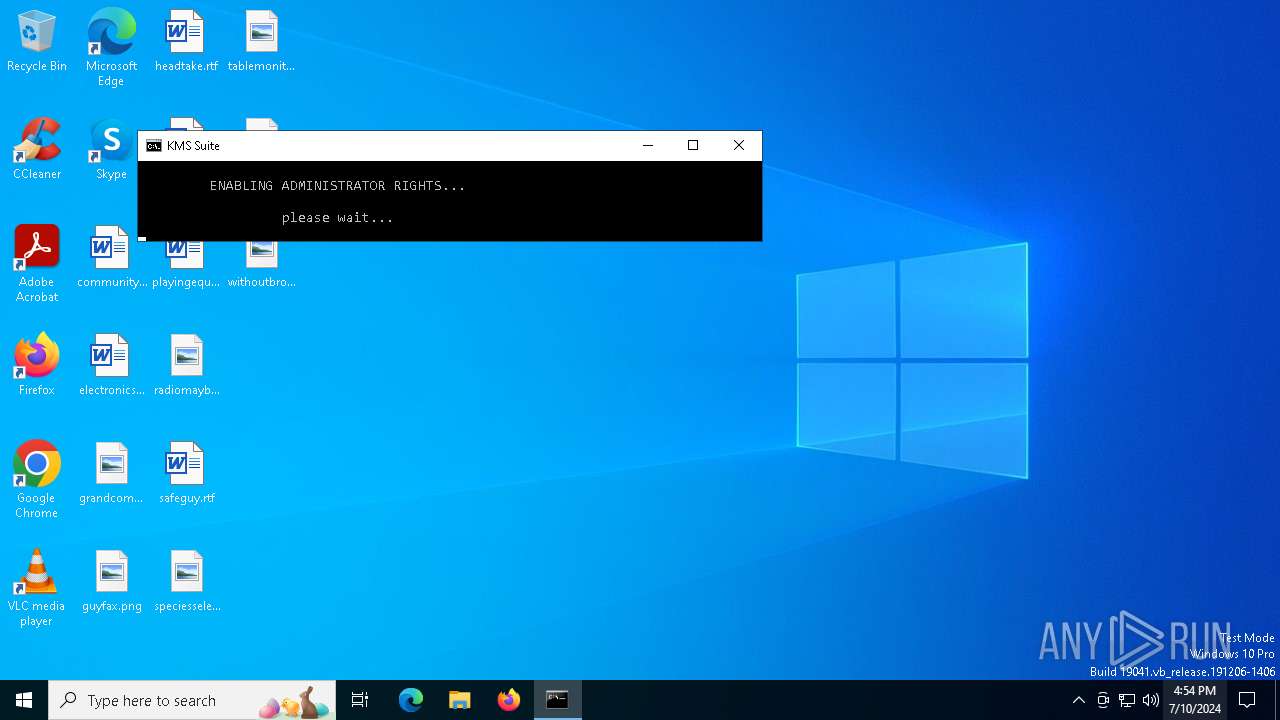
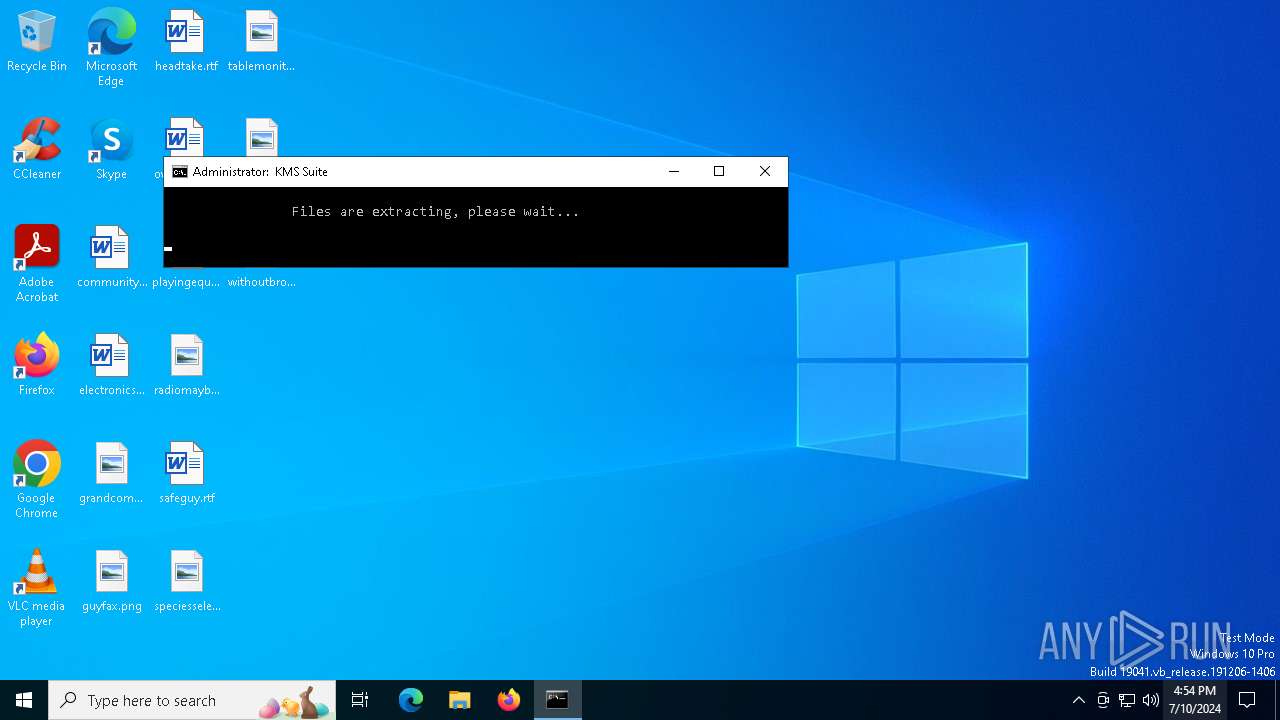
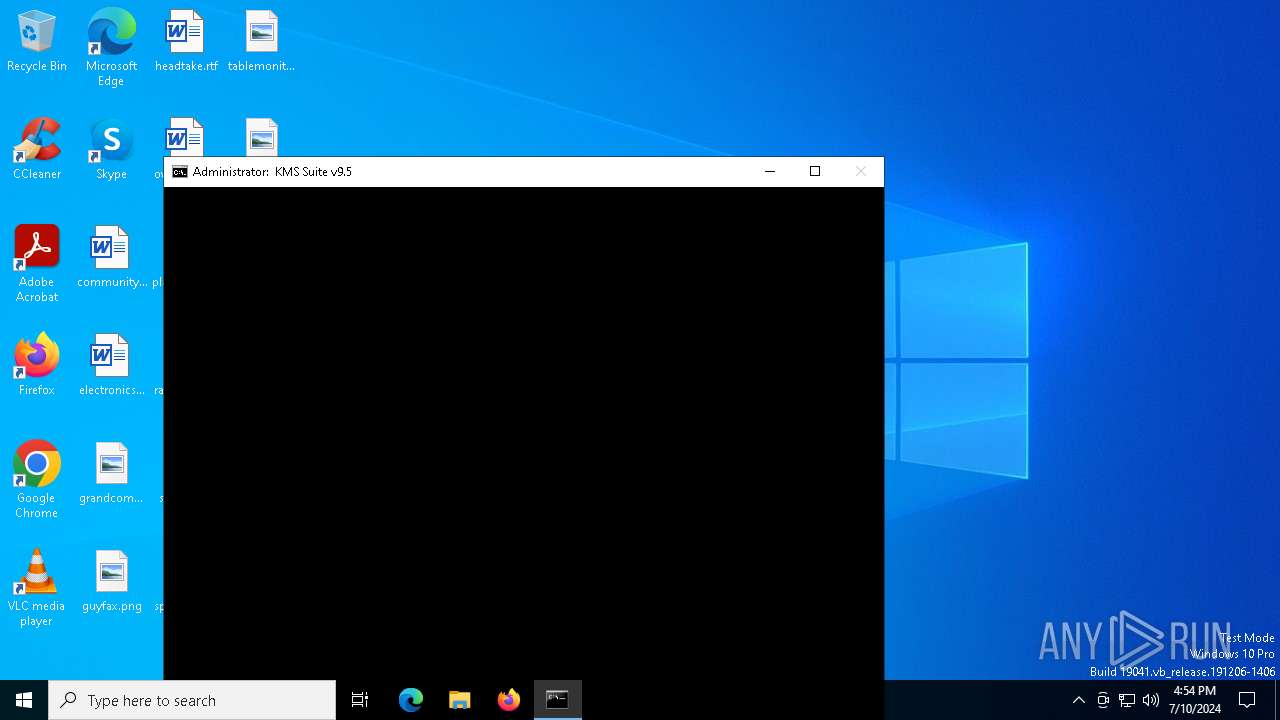
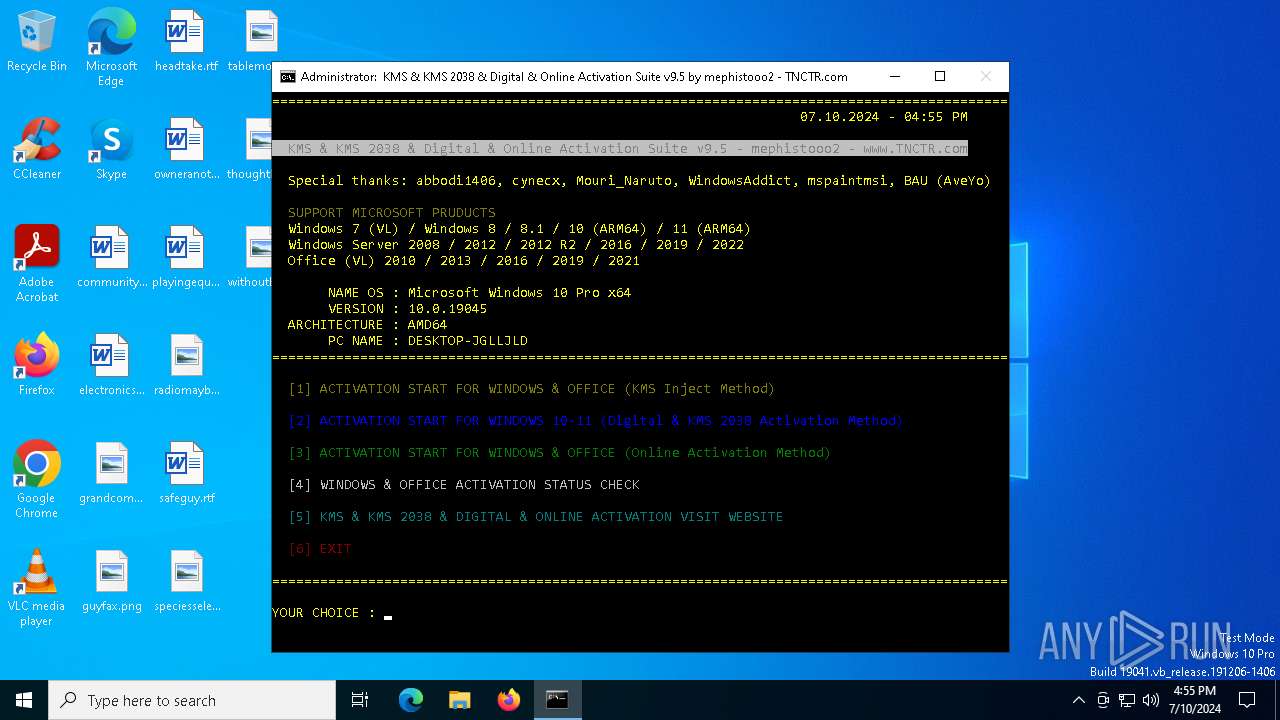
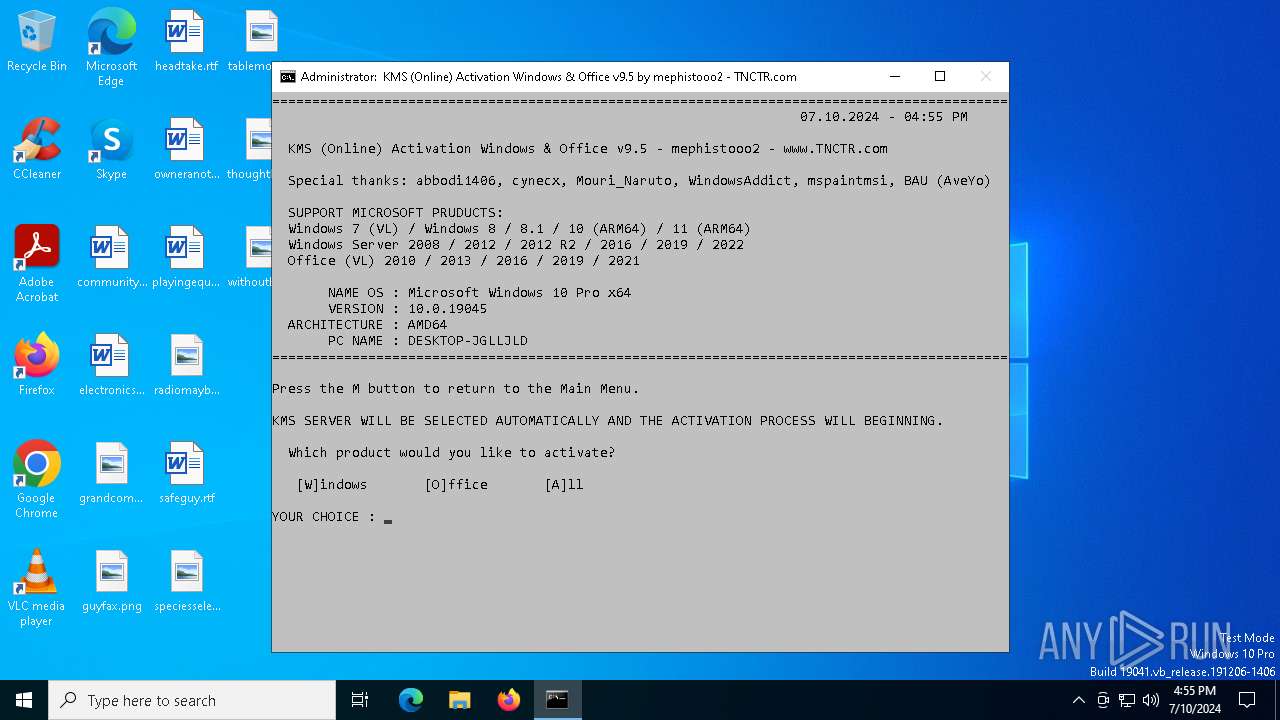
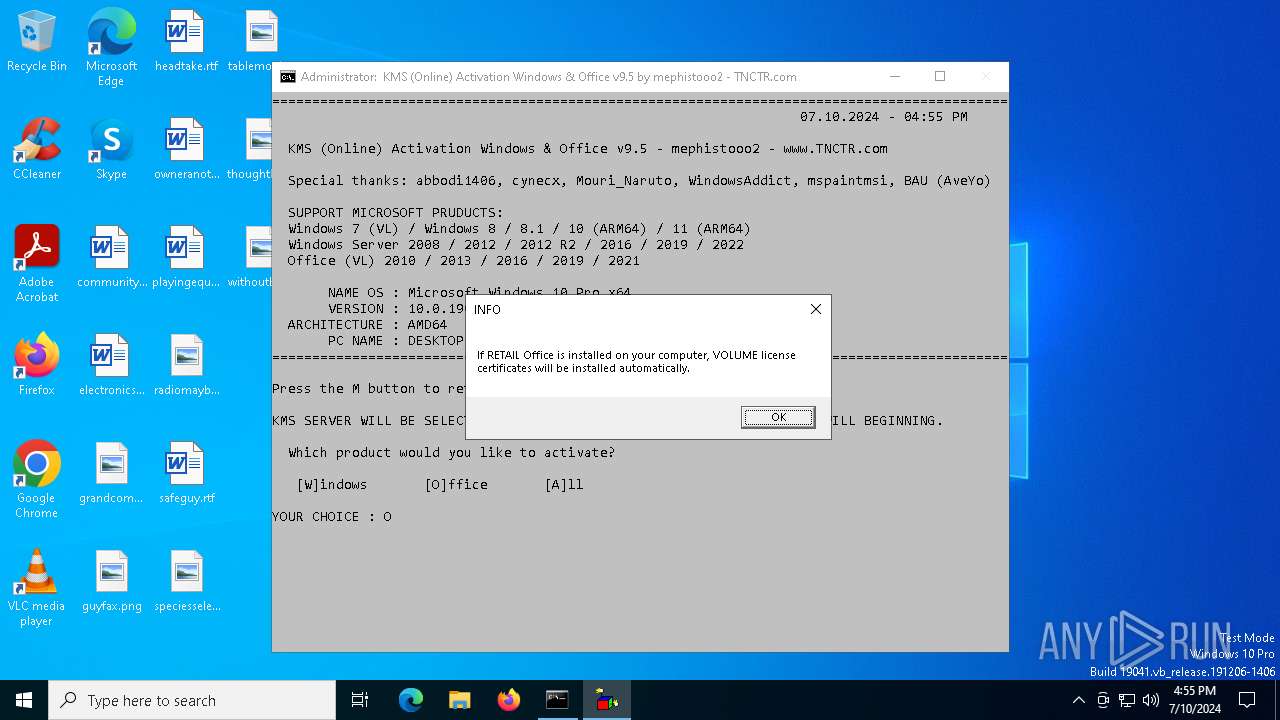
| File name: | KMS_Suite.v9.5.EN.bat |
| Full analysis: | https://app.any.run/tasks/ab947723-5533-4418-98f9-8b36f6a4ff53 |
| Verdict: | Malicious activity |
| Analysis date: | July 10, 2024, 16:54:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | AF73BF925361348072469CFF78890A4B |
| SHA1: | DCA20E41242D9398F474BABB80C971E5FC27DE69 |
| SHA256: | CC331C94FD9E4584F405BD6B03FB99ECFBB5293017293FC0A37A9B1737D31722 |
| SSDEEP: | 6144:zaGyPc7/Tg7jc4zlw6PhVMt1pOb4RKsFx+GXtO9l0X0dgJ/pGntI/:zaXEDTg84z5pVM9O0lgz70kd0pEE |
MALICIOUS
Drops the executable file immediately after the start
- csc.exe (PID: 5268)
- expand.exe (PID: 6324)
- csc.exe (PID: 5988)
- csc.exe (PID: 5252)
- csc.exe (PID: 3760)
Changes powershell execution policy (RemoteSigned)
- cmd.exe (PID: 992)
SUSPICIOUS
Executing commands from a ".bat" file
- cmd.exe (PID: 6220)
- cmd.exe (PID: 6408)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6220)
- cmd.exe (PID: 6408)
- cmd.exe (PID: 992)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6220)
- cmd.exe (PID: 6408)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6408)
- cmd.exe (PID: 992)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 6676)
- cmd.exe (PID: 6256)
- cmd.exe (PID: 1832)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6408)
- cmd.exe (PID: 992)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6408)
- cmd.exe (PID: 992)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6408)
- cmd.exe (PID: 6592)
- cmd.exe (PID: 6676)
- cmd.exe (PID: 1832)
- cmd.exe (PID: 6256)
- cmd.exe (PID: 992)
Application launched itself
- cmd.exe (PID: 6220)
- cmd.exe (PID: 6408)
- cmd.exe (PID: 992)
Executable content was dropped or overwritten
- csc.exe (PID: 5268)
- expand.exe (PID: 6324)
- xcopy.exe (PID: 2632)
- csc.exe (PID: 5988)
- csc.exe (PID: 5252)
- csc.exe (PID: 3760)
Unpacks CAB file
- expand.exe (PID: 6324)
- expand.exe (PID: 6520)
Process drops legitimate windows executable
- expand.exe (PID: 6324)
- xcopy.exe (PID: 2632)
The process executes Powershell scripts
- cmd.exe (PID: 992)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 992)
The executable file from the user directory is run by the CMD process
- center.exe (PID: 3156)
- center.exe (PID: 2448)
The process executes VB scripts
- cmd.exe (PID: 992)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 992)
Potential TCP-based PowerShell reverse shell connection
- cmd.exe (PID: 992)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 992)
INFO
Checks supported languages
- mode.com (PID: 6280)
- mode.com (PID: 6484)
- csc.exe (PID: 5268)
- cvtres.exe (PID: 6316)
- expand.exe (PID: 6324)
- cvtres.exe (PID: 6256)
- mode.com (PID: 6448)
- mode.com (PID: 3560)
- csc.exe (PID: 5988)
- mode.com (PID: 752)
- mode.com (PID: 4048)
- csc.exe (PID: 5252)
- center.exe (PID: 3156)
- cvtres.exe (PID: 3108)
- expand.exe (PID: 6520)
- csc.exe (PID: 3760)
- cvtres.exe (PID: 4084)
- center.exe (PID: 2448)
- mode.com (PID: 6584)
- mode.com (PID: 8)
- mode.com (PID: 7032)
- mode.com (PID: 2992)
Reads the machine GUID from the registry
- csc.exe (PID: 5268)
- expand.exe (PID: 6324)
- csc.exe (PID: 5988)
- csc.exe (PID: 5252)
- expand.exe (PID: 6520)
- csc.exe (PID: 3760)
Create files in a temporary directory
- csc.exe (PID: 5268)
- cvtres.exe (PID: 6316)
- expand.exe (PID: 6324)
- xcopy.exe (PID: 2632)
- csc.exe (PID: 5988)
- cvtres.exe (PID: 6256)
- csc.exe (PID: 5252)
- cvtres.exe (PID: 4084)
- expand.exe (PID: 6520)
- csc.exe (PID: 3760)
- cvtres.exe (PID: 3108)
Drops the executable file immediately after the start
- xcopy.exe (PID: 2632)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5244)
Checks operating system version
- cmd.exe (PID: 992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
232
Monitored processes
92
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | mode con cols=92 lines=35 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | C:\WINDOWS\system32\cmd.exe /c time /t | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | mode con cols=92 lines=35 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
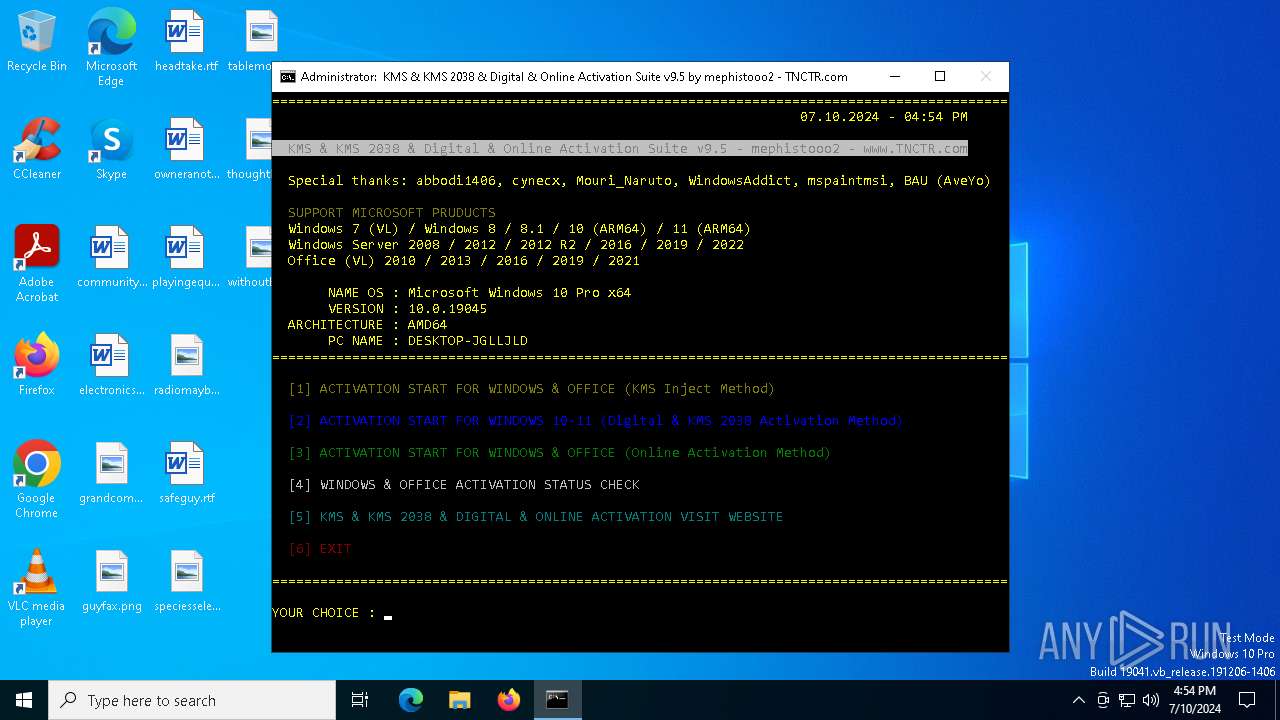
| 992 | cmd.exe /c KMS_Suite.bat -suite | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | Powershell.exe -executionpolicy remotesigned -File disablex.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | choice /C:123456 /N /M "YOUR CHOICE :" | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | findstr /v /a:78 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " KMS & KMS 2038 & Digital & Online Activation Suite v9.5 - mephistooo2 - www.TNCTR.com" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
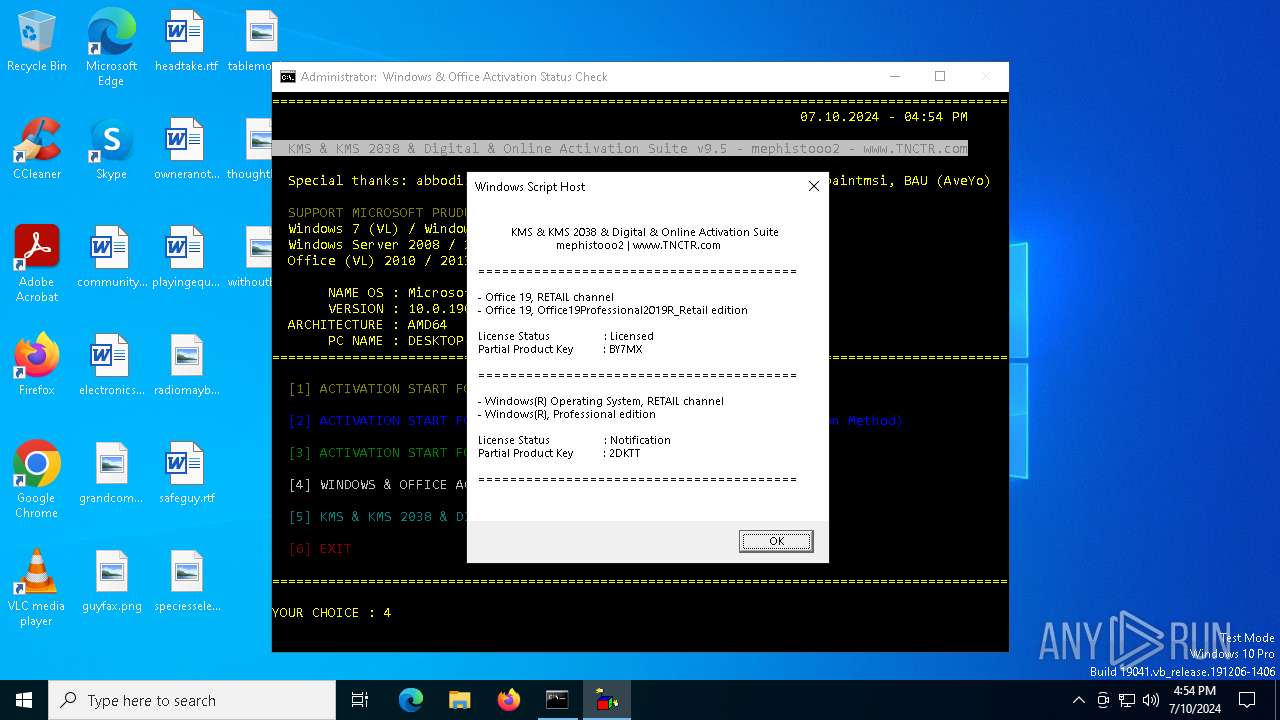
| 1272 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\27875\bin\check.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1348 | choice /C:123456 /N /M "YOUR CHOICE :" | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1384 | C:\WINDOWS\system32\cmd.exe /c "prompt #$H#$E# & echo on & for %b in (1) do rem" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
68 854
Read events
68 814
Write events
36
Delete events
4
Modification events
| (PID) Process: | (6220) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6220) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6220) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6220) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6220) cmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\system32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (6220) cmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\system32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (6556) reg.exe | Key: | HKEY_CLASSES_ROOT\.Admin\shell\runas\command |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6556) reg.exe | Key: | HKEY_CLASSES_ROOT\.Admin\shell\runas |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6556) reg.exe | Key: | HKEY_CLASSES_ROOT\.Admin\shell |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6556) reg.exe | Key: | HKEY_CLASSES_ROOT\.Admin |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
28
Suspicious files
10
Text files
81
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5268 | csc.exe | C:\Users\admin\AppData\Local\Temp\orrnp5af\CSC7D40C50F3AD441059014512A13276EB.TMP | binary | |
MD5:58099E17F9EAD7893B59B10C108ADB05 | SHA256:7D7B82E7E004C55C115DA09CC9A1DB2C2223E3CB56BE1927EC732A1E93BEE5E8 | |||
| 6576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1 | compressed | |
MD5:2B6D8E1E450072798B678F8F6A8D623F | SHA256:0297EDF9BFC2D0C9E0C479185812A95258CEC5D3A04262F5BA7B89990B32C847 | |||
| 6576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\orrnp5af\orrnp5af.0.cs | text | |
MD5:047F0CF592670E8FCA358F12E4CD5A89 | SHA256:32E77D9085AD9EA0FD1EB5A9556E29CB42F5D3016CCF9853F3C39D358F479978 | |||
| 6576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\orrnp5af\orrnp5af.cmdline | text | |
MD5:AF191CB5F32C1D8F0656A57CD273F7D1 | SHA256:683F09C04C3F5C2983A39E5EACBCD89D7834682DFC001F43DF19CC87325098A0 | |||
| 5268 | csc.exe | C:\Users\admin\AppData\Local\Temp\orrnp5af\orrnp5af.dll | executable | |
MD5:C0E4A9325B41E64BBD3E8437AED417E7 | SHA256:62C65C9AA46A9A97489526E058F6A6AAEAEDD61DBED4DDE0C83C1E9F459C9D1B | |||
| 6324 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\center.exe | executable | |
MD5:0A847EAFDDC4529388E1A1B291354CF8 | SHA256:69533D9B66B840B4764F901CD6A502D12453B604617A841F4C2C602FC87DF255 | |||
| 6576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rojs0kap.pi3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mc02ogpi.d3s.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6324 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\Digital\OEM_Digital\$OEM$\$\Setup\Scripts\digi.bat | text | |
MD5:A9D3F449DA7E990816BE1D58417D4FE6 | SHA256:11322FC30BC92EB4F1F6EA5AD6C2C9F2FE3204E017F8D7F4CDCFBF36E33E93AB | |||
| 6324 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\Digital\bin\slc.dll | executable | |
MD5:F18DD5B638590BE87CCD56FE338BED10 | SHA256:E7ECA8C7476DF70EF525AE55A0D8CCC715F22A727165A05FD4C380032CF763A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
61
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6840 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6116 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6940 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6068 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
6280 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
6116 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
6280 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6116 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1272 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4752 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4656 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6068 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6068 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.microsoft.com |
| whitelisted |