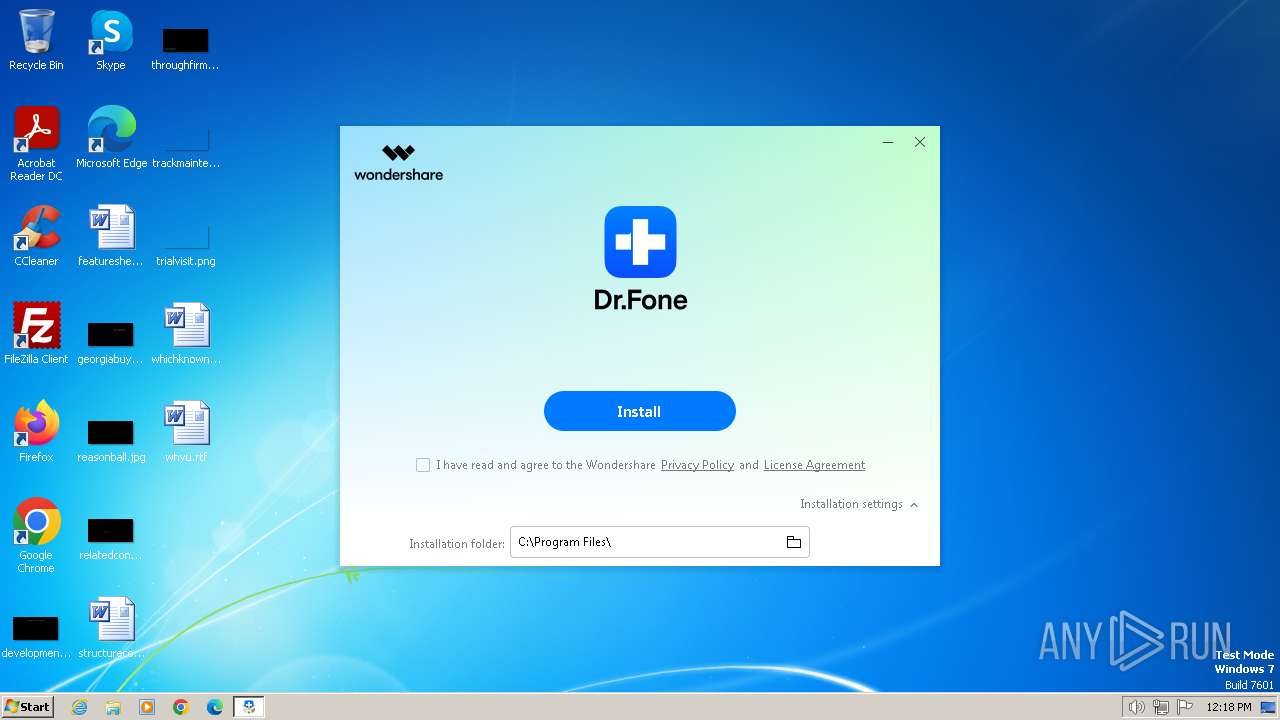
| File name: | drfone_unlock_setup_full3855.exe |
| Full analysis: | https://app.any.run/tasks/13d42669-6ccb-441e-8ddb-10d237744f2d |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2024, 11:18:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3873375A0AAEAFEBC8F2E0B037CAB4CA |
| SHA1: | 31AD239193B130C04540C514BF1F125775B942A8 |
| SHA256: | CC276D5DA0D5426558098AFE87AE7B358403ADC9160FF48CC7D7AB85D7588F73 |
| SSDEEP: | 98304:aJFfX3z+2Pwwgpzp5suNP4Uv5+/wDMXCxbNoe6Ple73U6D6VGUEGmutvDFFo5:Qq |
MALICIOUS
Drops the executable file immediately after the start
- drfone_unlock_setup_full3855.exe (PID: 3212)
SUSPICIOUS
Reads security settings of Internet Explorer
- drfone_unlock_setup_full3855.exe (PID: 3212)
Reads the Internet Settings
- drfone_unlock_setup_full3855.exe (PID: 3212)
Reads Microsoft Outlook installation path
- drfone_unlock_setup_full3855.exe (PID: 3212)
Reads Internet Explorer settings
- drfone_unlock_setup_full3855.exe (PID: 3212)
Executable content was dropped or overwritten
- drfone_unlock_setup_full3855.exe (PID: 3212)
Likely accesses (executes) a file from the Public directory
- NFWCHK.exe (PID: 2080)
Connects to unusual port
- drfone_unlock_setup_full3855.exe (PID: 3212)
INFO
Checks supported languages
- drfone_unlock_setup_full3855.exe (PID: 3212)
- NFWCHK.exe (PID: 2080)
Reads the machine GUID from the registry
- drfone_unlock_setup_full3855.exe (PID: 3212)
- NFWCHK.exe (PID: 2080)
Reads the computer name
- drfone_unlock_setup_full3855.exe (PID: 3212)
- NFWCHK.exe (PID: 2080)
Create files in a temporary directory
- drfone_unlock_setup_full3855.exe (PID: 3212)
Checks proxy server information
- drfone_unlock_setup_full3855.exe (PID: 3212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (16.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (14.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.4) |
| .exe | | | Win32 Executable (generic) (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:01:13 08:19:46+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 1278976 |
| InitializedDataSize: | 1204736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1069f0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.4.18 |
| ProductVersionNumber: | 4.0.4.18 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | drfone_setup_full3855.exe |
| FileVersion: | 4.0.4.18 |
| LegalCopyright: | Copyright©2023 Wondershare. All rights reserved. |
| ProductName: | drfone |
| ProductVersion: | 12.5.2 |
Total processes
44
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2080 | C:\Users\Public\Documents\Wondershare\NFWCHK.exe | C:\Users\Public\Documents\Wondershare\NFWCHK.exe | — | drfone_unlock_setup_full3855.exe | |||||||||||
User: admin Company: Wondershare Integrity Level: HIGH Description: .NET Framework Checker Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3212 | "C:\Users\admin\AppData\Local\Temp\drfone_unlock_setup_full3855.exe" | C:\Users\admin\AppData\Local\Temp\drfone_unlock_setup_full3855.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: drfone_setup_full3855.exe Version: 4.0.4.18 Modules
| |||||||||||||||
| 3392 | "C:\Users\admin\AppData\Local\Temp\drfone_unlock_setup_full3855.exe" | C:\Users\admin\AppData\Local\Temp\drfone_unlock_setup_full3855.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: drfone_setup_full3855.exe Exit code: 3221226540 Version: 4.0.4.18 Modules
| |||||||||||||||
Total events
1 383
Read events
1 369
Write events
14
Delete events
0
Modification events
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WafCX |
| Operation: | write | Name: | 3855 |
Value: sku-ppc | |||
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Wondershare\Wondershare Helper Compact |
| Operation: | write | Name: | ClientSign |
Value: {8d09e840-30a9-48f2-a088-99622e59d39fG} | |||
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Wondershare\WAF |
| Operation: | write | Name: | ClientSign |
Value: {8d09e840-30a9-48f2-a088-99622e59d39fG} | |||
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3212) drfone_unlock_setup_full3855.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
1
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3212 | drfone_unlock_setup_full3855.exe | C:\Users\Public\Documents\Wondershare\NFWCHK.exe.config | xml | |
MD5:5BABF2A106C883A8E216F768DB99AD51 | SHA256:9E676A617EB0D0535AC05A67C0AE0C0E12D4E998AB55AC786A031BFC25E28300 | |||
| 3212 | drfone_unlock_setup_full3855.exe | C:\Users\admin\AppData\Local\Temp\Wondershare\WAE\wsWAE.log | text | |
MD5:2FA6B8A25000919B1B0AB4B7E117B3A9 | SHA256:0627E7CBDF71D7652014E829EAFE0B6104310F0502A47DEAAC153958B2A79828 | |||
| 3212 | drfone_unlock_setup_full3855.exe | C:\Users\admin\AppData\Local\Temp\wsduilib.log | text | |
MD5:47C1A69DB73833E56A51B6B3673E01BE | SHA256:A2EBD38E783CE89932F4AEB4F7DA8C3229FAE54C51D449FBDD506D0F173D88CA | |||
| 3212 | drfone_unlock_setup_full3855.exe | C:\Users\Public\Documents\Wondershare\NFWCHK.exe | executable | |
MD5:27CFB3990872CAA5930FA69D57AEFE7B | SHA256:43881549228975C7506B050BCE4D9B671412D3CDC08C7516C9DBBB7F50C25146 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
17
DNS requests
7
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3212 | drfone_unlock_setup_full3855.exe | GET | — | 8.209.73.211:80 | http://platform.wondershare.cc/rest/v2/downloader/runtime/?client_sign={8d09e840-30a9-48f2-a088-99622e59d39fG}&product_id=3855&wae=4.0.4&platform=win_x86 | unknown | — | — | whitelisted |
3212 | drfone_unlock_setup_full3855.exe | HEAD | 200 | 2.19.126.135:80 | http://download.wondershare.net/cbs_down/drfone_full4008.exe | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3212 | drfone_unlock_setup_full3855.exe | 8.209.72.213:443 | pc-api.wondershare.cc | Alibaba US Technology Co., Ltd. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3212 | drfone_unlock_setup_full3855.exe | 8.209.73.211:80 | platform.wondershare.cc | Alibaba US Technology Co., Ltd. | DE | unknown |
3212 | drfone_unlock_setup_full3855.exe | 47.91.89.51:443 | prod-web.wondershare.cc | Alibaba US Technology Co., Ltd. | DE | unknown |
3212 | drfone_unlock_setup_full3855.exe | 2.19.126.135:80 | download.wondershare.net | Akamai International B.V. | DE | unknown |
3212 | drfone_unlock_setup_full3855.exe | 47.91.90.244:8106 | analytics.wondershare.cc | Alibaba US Technology Co., Ltd. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
pc-api.wondershare.cc |
| malicious |
platform.wondershare.cc |
| malicious |
prod-web.wondershare.cc |
| malicious |
download.wondershare.net |
| whitelisted |
analytics.wondershare.cc |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1 ETPRO signatures available at the full report