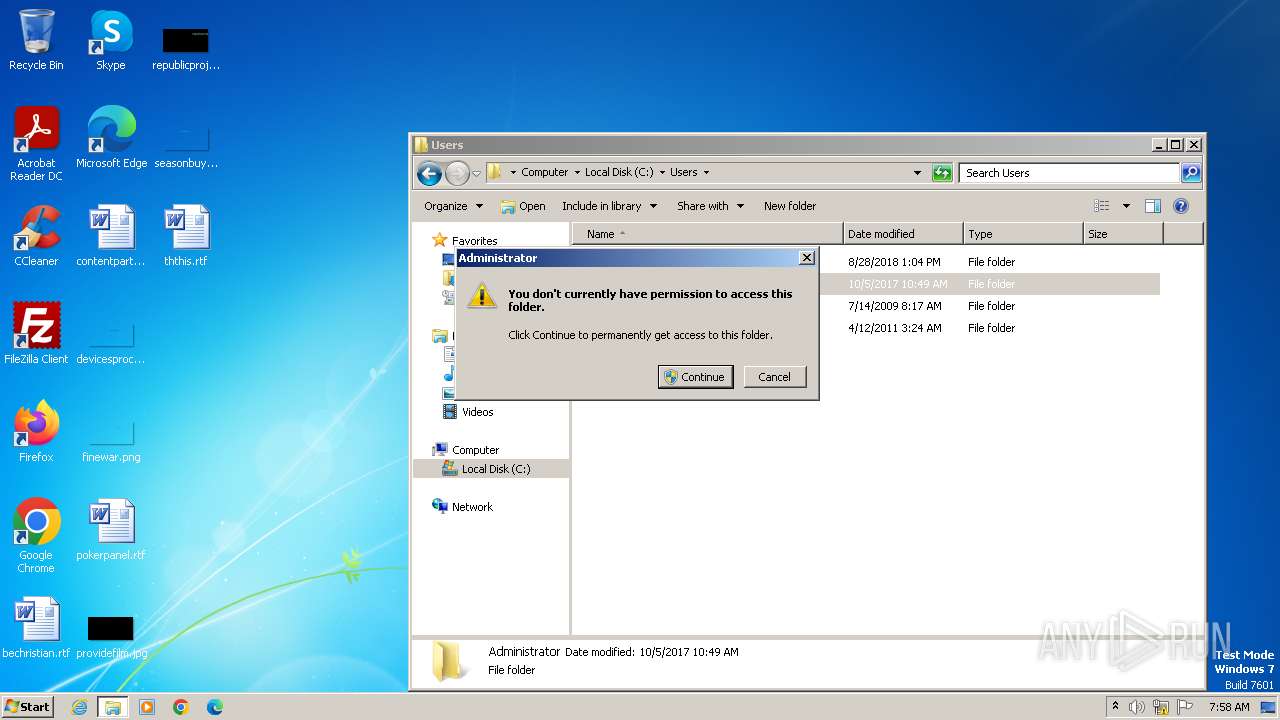
| File name: | OneNote.exe |
| Full analysis: | https://app.any.run/tasks/a043e156-10fd-460e-966b-3abdafc1e2ed |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2023, 07:57:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 5B7D2906935F7C77BB93BB3CEAD4CF46 |
| SHA1: | 200F8E14DE1480A8F24DF25192E8D5FC3FF580F8 |
| SHA256: | CC14EE47489CB2AD1AD6F49F8F1A4E8C911C3F6C7F4322418DB0BB74D6694C4D |
| SSDEEP: | 1536:VIFbydYaI9H4UQ/z026b1pHnEQPnPOdnQCKnVqPvd+d:VIFbyI4f/Q26JZEQPW9CVs |
MALICIOUS
Drops the executable file immediately after the start
- powershell.exe (PID: 2892)
SUSPICIOUS
Powershell version downgrade attack
- powershell.exe (PID: 2892)
Reads the Internet Settings
- powershell.exe (PID: 2892)
Executes as Windows Service
- OneNote.exe (PID: 3800)
Connects to unusual port
- OneNote.exe (PID: 3800)
INFO
Checks supported languages
- OneNote.exe (PID: 1996)
- OneNote.exe (PID: 3884)
- OneNote.exe (PID: 3040)
- OneNote.exe (PID: 1420)
- WerFault.exe (PID: 3792)
- OneNote.exe (PID: 1752)
- WerFault.exe (PID: 2944)
- OneNote.exe (PID: 3800)
Reads the computer name
- OneNote.exe (PID: 1996)
- OneNote.exe (PID: 3884)
- OneNote.exe (PID: 3040)
- OneNote.exe (PID: 1420)
- WerFault.exe (PID: 3792)
- OneNote.exe (PID: 1752)
- OneNote.exe (PID: 3800)
- WerFault.exe (PID: 2944)
Manual execution by a user
- explorer.exe (PID: 2632)
- OneNote.exe (PID: 3040)
- OneNote.exe (PID: 3884)
- OneNote.exe (PID: 1420)
- powershell.exe (PID: 2892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:04:05 15:54:13+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.34 |
| CodeSize: | 61440 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 86016 |
| EntryPoint: | 0x24bc0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
65
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\system32\winver.exe | C:\Windows\System32\winver.exe | — | WerFault.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Version Reporter Applet Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1420 | "C:\Users\admin\Desktop\OneNote.exe" | C:\Users\admin\Desktop\OneNote.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1752 | C:\Users\admin\AppData\Local\Temp\OneNote.exe install | C:\Users\admin\AppData\Local\Temp\OneNote.exe | — | computerdefaults.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1928 | C:\Windows\system32\computerdefaults.exe | C:\Windows\System32\computerdefaults.exe | WerFault.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Set Program Access and Computer Defaults Control Panel Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1996 | "C:\Users\admin\AppData\Local\Temp\OneNote.exe" | C:\Users\admin\AppData\Local\Temp\OneNote.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2116 | C:\Windows\system32\winver.exe | C:\Windows\System32\winver.exe | — | WerFault.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Version Reporter Applet Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2392 | C:\Windows\system32\computerdefaults.exe | C:\Windows\System32\computerdefaults.exe | WerFault.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Set Program Access and Computer Defaults Control Panel Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2632 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2892 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\OneNoteUpdate.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2944 | "C:\Users\admin\AppData\Local\Temp\WerFault.exe" 59 C:\Windows\System32\splwow64.exe | C:\Users\admin\AppData\Local\Temp\WerFault.exe | — | powershell.exe | |||||||||||
User: admin Company: Fraudware Scripting Integrity Level: MEDIUM Description: Pentesting utility Exit code: 0 Version: 3.6.4.2302 Modules
| |||||||||||||||
Total events
2 021
Read events
1 959
Write events
62
Delete events
0
Modification events
| (PID) Process: | (2892) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2892) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2892) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2892) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2892) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
2
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2892 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6G4E9PJGGW7FNW7MUR2O.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2892 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2892 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF22682a.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2892 | powershell.exe | C:\Users\admin\AppData\Local\Temp\WerFault.exe | executable | |
MD5:37C2374640C10838793924C5302957E7 | SHA256:B153F1E18CE5C2318DECA91F9CD5706391589344F46BC2AA2A270E4F8E49D4C3 | |||
| 2892 | powershell.exe | C:\Users\admin\AppData\Local\Temp\OneNote.exe | executable | |
MD5:5B7D2906935F7C77BB93BB3CEAD4CF46 | SHA256:CC14EE47489CB2AD1AD6F49F8F1A4E8C911C3F6C7F4322418DB0BB74D6694C4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
10
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3800 | OneNote.exe | 92.100.156.250:2222 | — | Rostelecom | RU | unknown |
3800 | OneNote.exe | 94.242.171.144:2222 | — | Rostelecom | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |