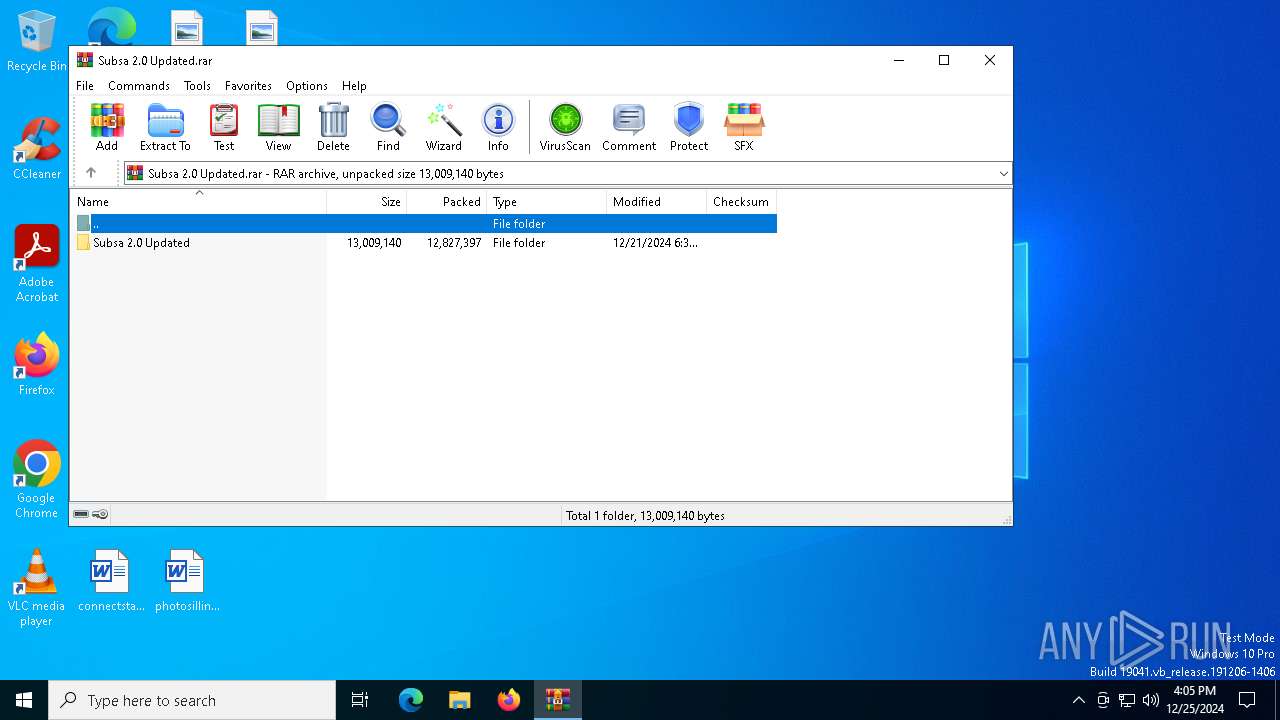
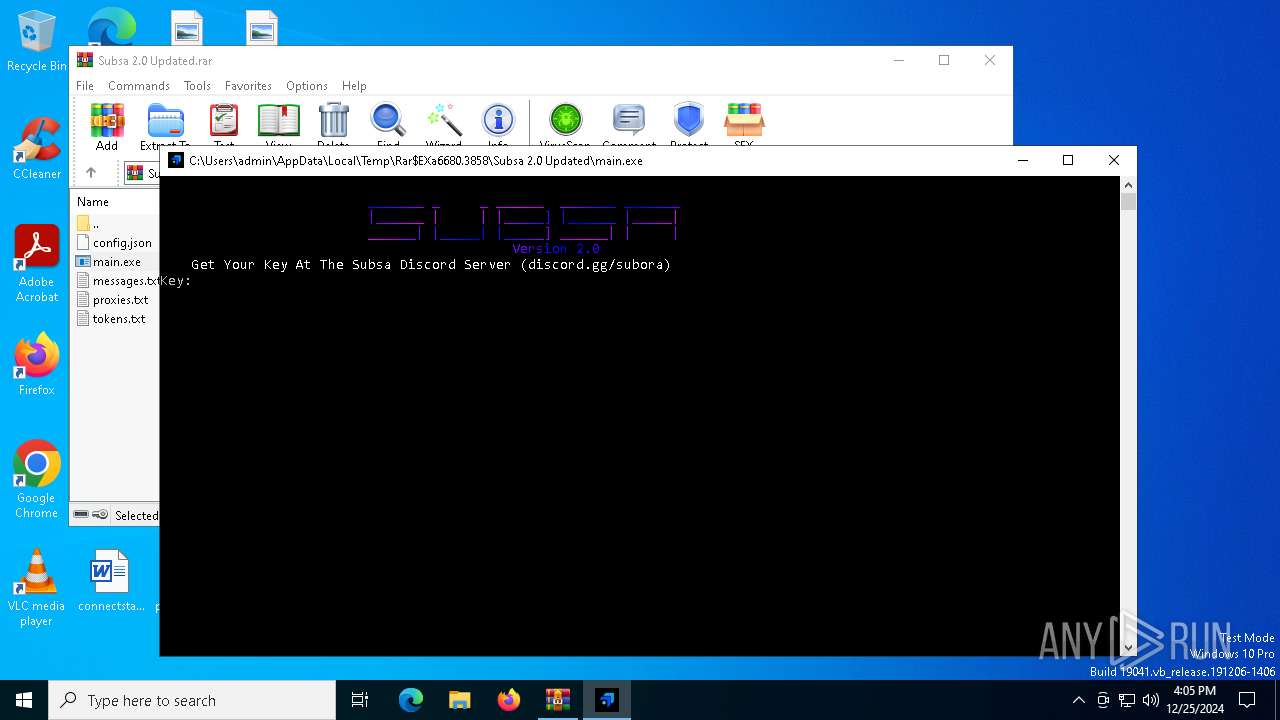
| File name: | Subsa 2.0 Updated.rar |
| Full analysis: | https://app.any.run/tasks/a62735c3-8b70-4ee1-8420-c55293d7987a |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2024, 16:05:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7873DDFD47EC81B6651D9A6079064388 |
| SHA1: | 9DAA2DBB91074193216CC26F655162FCAF3236C9 |
| SHA256: | CC04E4E1C7D6E8E5999CFF665A639B0A1EFFF8A47676133FAB0E49E1B72FFD9C |
| SSDEEP: | 98304:FhJhJneZYJDqznYYCtYU9G4/F/PRAYR+imKgm+RHH4yoYTmveECHbvXiZJd+zjxl:xaMF/HXTuNT7w8caGKok |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6680)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6680)
Process drops legitimate windows executable
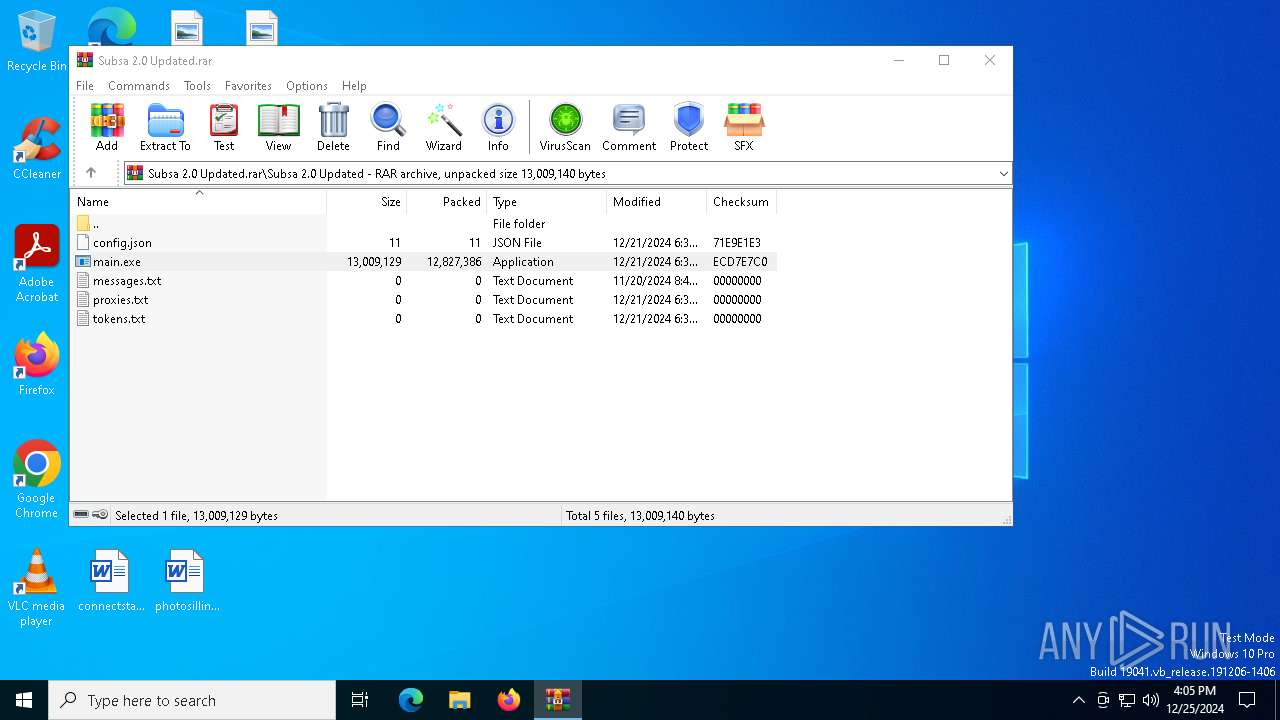
- main.exe (PID: 7112)
Process drops python dynamic module
- main.exe (PID: 7112)
Executable content was dropped or overwritten
- main.exe (PID: 7112)
The process drops C-runtime libraries
- main.exe (PID: 7112)
Application launched itself
- main.exe (PID: 7112)
Loads Python modules
- main.exe (PID: 644)
Starts CMD.EXE for commands execution
- main.exe (PID: 644)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6680)
Reads the computer name
- main.exe (PID: 7112)
- main.exe (PID: 644)
Checks supported languages
- main.exe (PID: 7112)
- main.exe (PID: 644)
The sample compiled with english language support
- main.exe (PID: 7112)
The process uses the downloaded file
- WinRAR.exe (PID: 6680)
Create files in a temporary directory
- main.exe (PID: 7112)
Reads the machine GUID from the registry
- main.exe (PID: 644)
Checks proxy server information
- main.exe (PID: 644)
PyInstaller has been detected (YARA)
- main.exe (PID: 7112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 11 |
| UncompressedSize: | 11 |
| OperatingSystem: | Win32 |
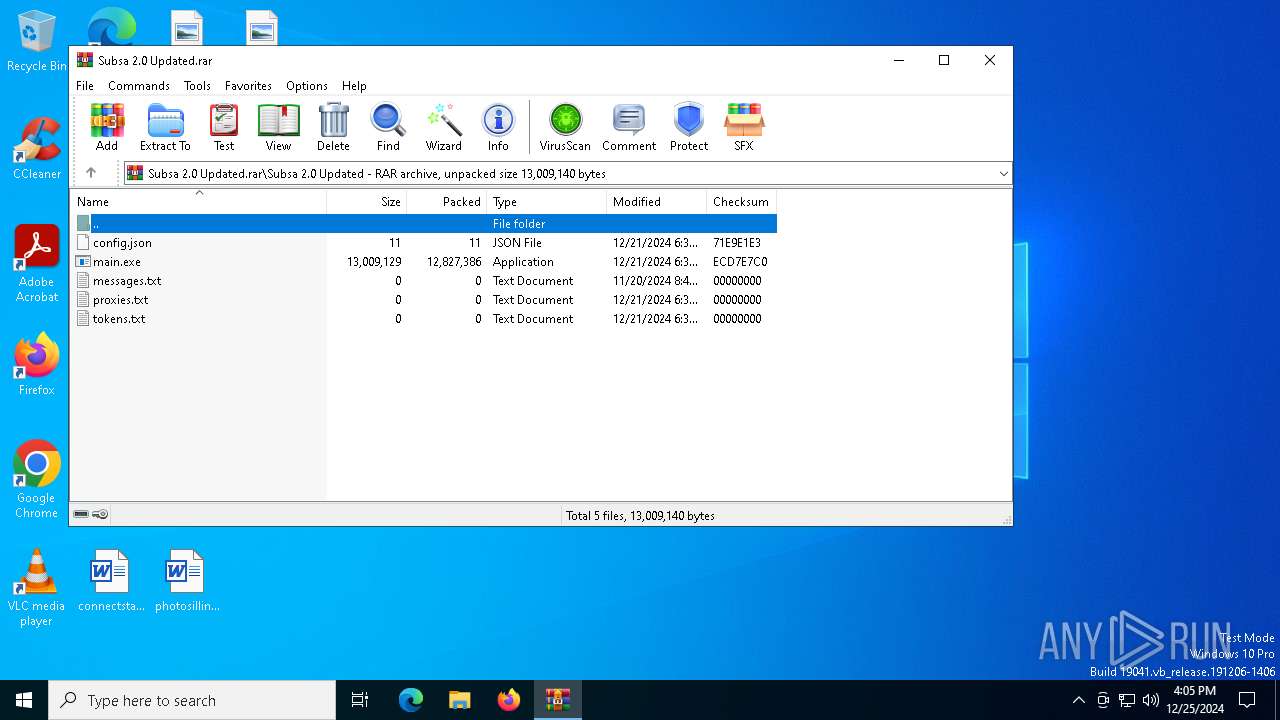
| ArchivedFileName: | Subsa 2.0 Updated/config.json |
Total processes
128
Monitored processes
7
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | C:\WINDOWS\system32\cmd.exe /c | C:\Windows\SysWOW64\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6680.3858\Subsa 2.0 Updated\main.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6680.3858\Subsa 2.0 Updated\main.exe | main.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6384 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\SysWOW64\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6448 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\SysWOW64\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6680 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Subsa 2.0 Updated.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7112 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6680.3858\Subsa 2.0 Updated\main.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6680.3858\Subsa 2.0 Updated\main.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 508
Read events
2 500
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Subsa 2.0 Updated.rar | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
38
Suspicious files
2
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7112 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71122\VCRUNTIME140.dll | executable | |
MD5:AFA8FB684EDED0D4CA6AA03AEBEA446F | SHA256:44DE8D0DC9994BFF357344C44F12E8BFFF8150442F7CA313298B98E6C23A588E | |||
| 7112 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71122\_bz2.pyd | executable | |
MD5:3894B2EA6B749B83880708BD59462A97 | SHA256:1DA79987502B5363E37F06CB952F025556B24D9DA601D49784F8DACD6799C004 | |||
| 7112 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71122\_decimal.pyd | executable | |
MD5:5C4426327478796D3FE7658EF543C5E6 | SHA256:156A787269E8E59B5F6CD882E885BF6296EF3BD43FB97AB74AAEB543A1CAB76E | |||
| 6680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6680.3858\Subsa 2.0 Updated\config.json | binary | |
MD5:C0ADCCB9105B50FB9724225E7A7FCA9B | SHA256:30428A3206C817F42E49331138BA5D36E2A29124876F75FAD011F4C1F5B94661 | |||
| 7112 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71122\_asyncio.pyd | executable | |
MD5:80583041860C6139DD48CB9CDBC303CD | SHA256:8168D94F2614AFCB9E227FEC4B1396263400B5EBED548243230DCA65B248D64A | |||
| 7112 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71122\_hashlib.pyd | executable | |
MD5:89756B9601C19F82592CA27192A05878 | SHA256:84B71DDD3F2D594EE144D421A13FF9EE01F5E4D757D28623D8C616334324D97B | |||
| 7112 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71122\_multiprocessing.pyd | executable | |
MD5:785F35C3C452D3C401721603746531C7 | SHA256:D34038F1CED0661950140BA5A6505CA6567B9CB66901B85C96A6B7CB52E6485C | |||
| 7112 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71122\_lzma.pyd | executable | |
MD5:13F3A5F3CD238887532A489A18C98F4D | SHA256:953779EAB6949F49940B7D8C9747350A51262423F640CD4B929D258CF41AA063 | |||
| 7112 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71122\_ctypes.pyd | executable | |
MD5:A1773307030425D15F9DB87AF6B00196 | SHA256:2A4C83EB7153D2174E9CA138DB451A7DB3C73C905511A887EA5DFA61CF86818A | |||
| 7112 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71122\_socket.pyd | executable | |
MD5:CBA28989EF78D6A6ADBCC4913CF14095 | SHA256:925BDACA503DD6D587C6E7AC9080044C3FC2B56C7A365C97B8D3060A63181172 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
35
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6520 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6284 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6284 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| unknown |
raw.githubusercontent.com |
| shared |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |